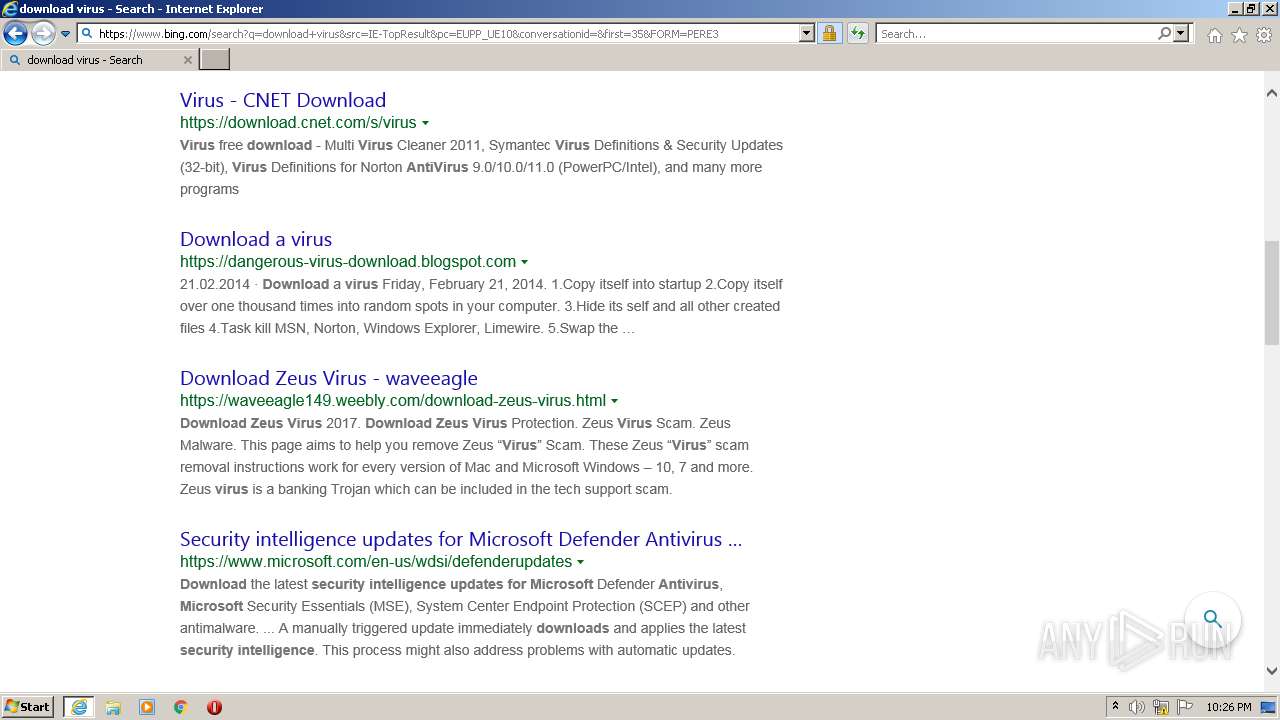
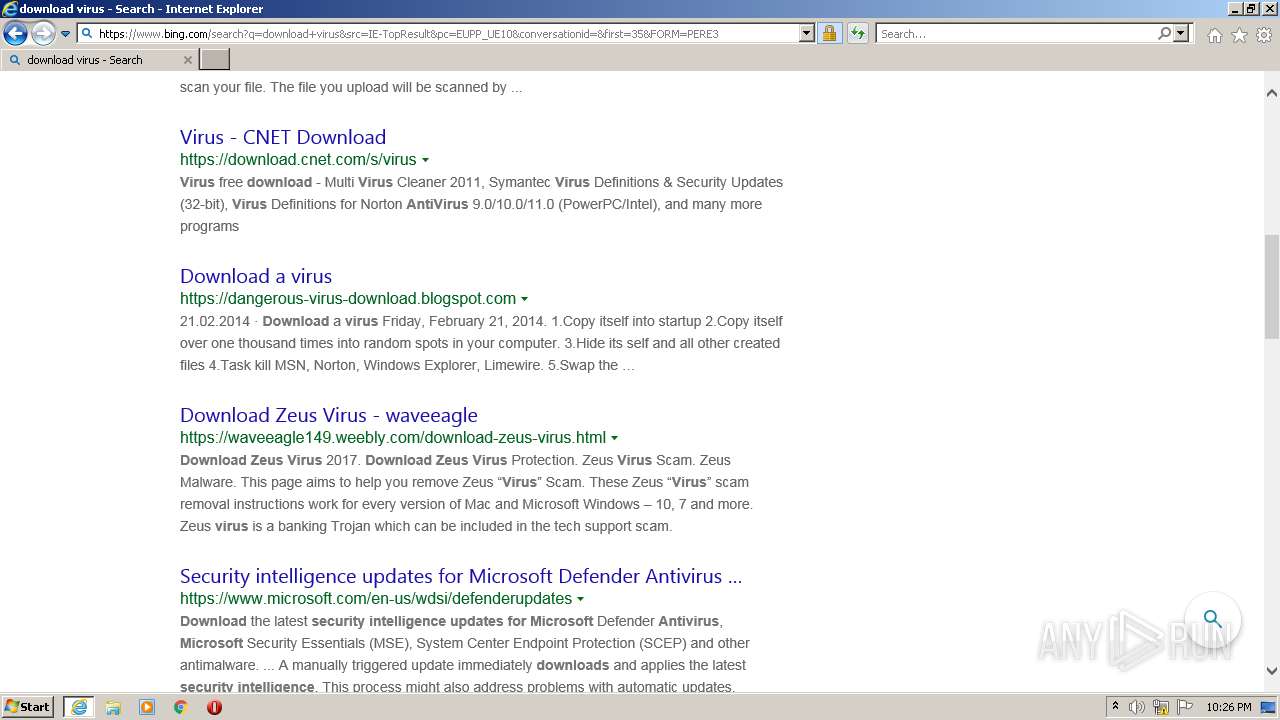
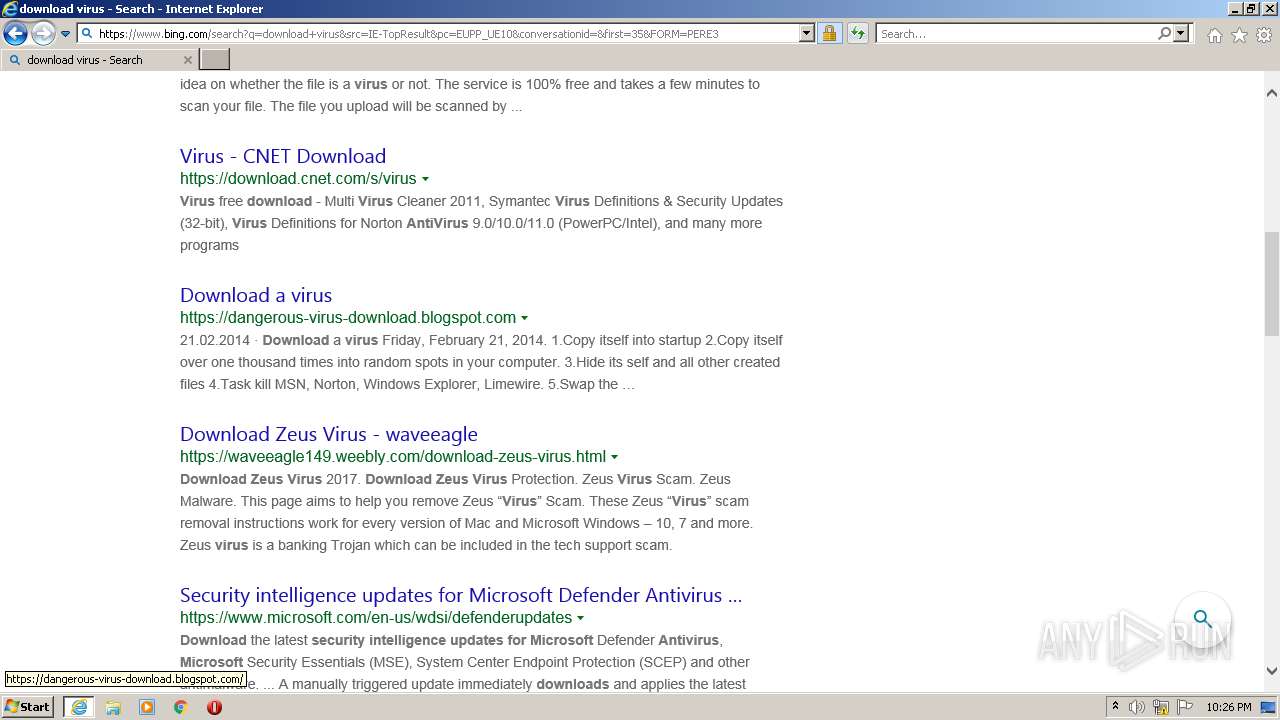
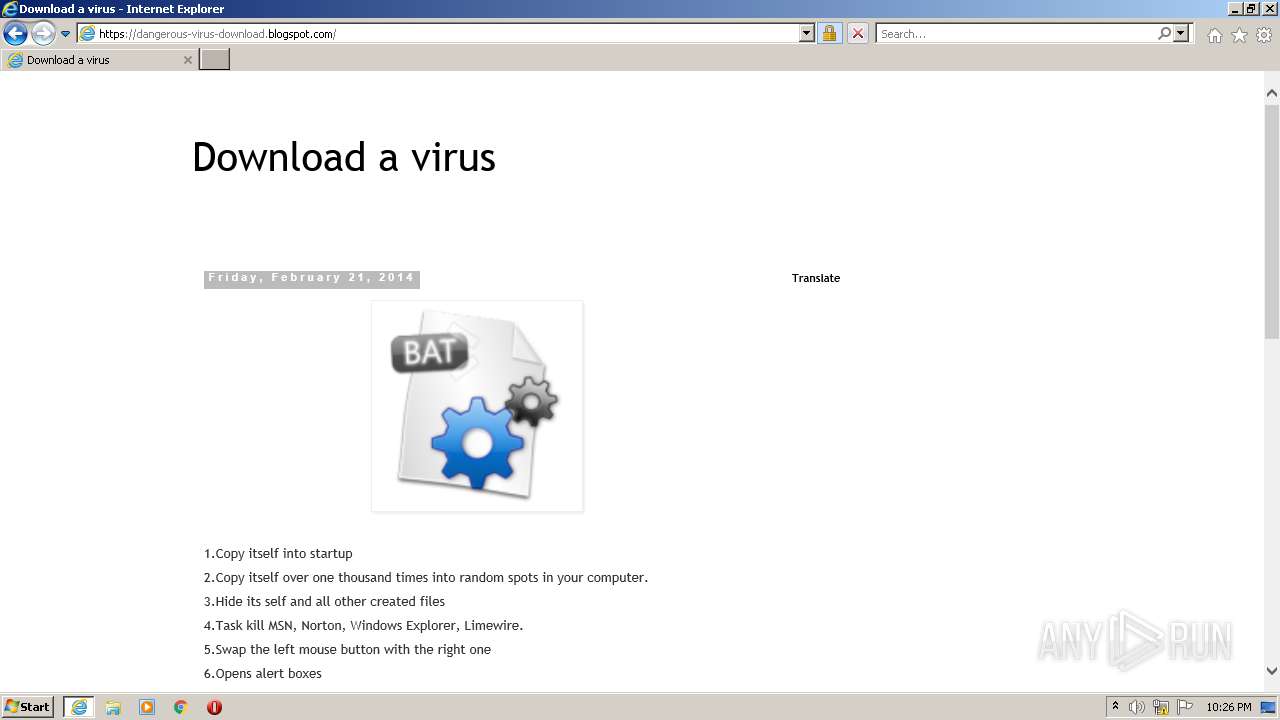
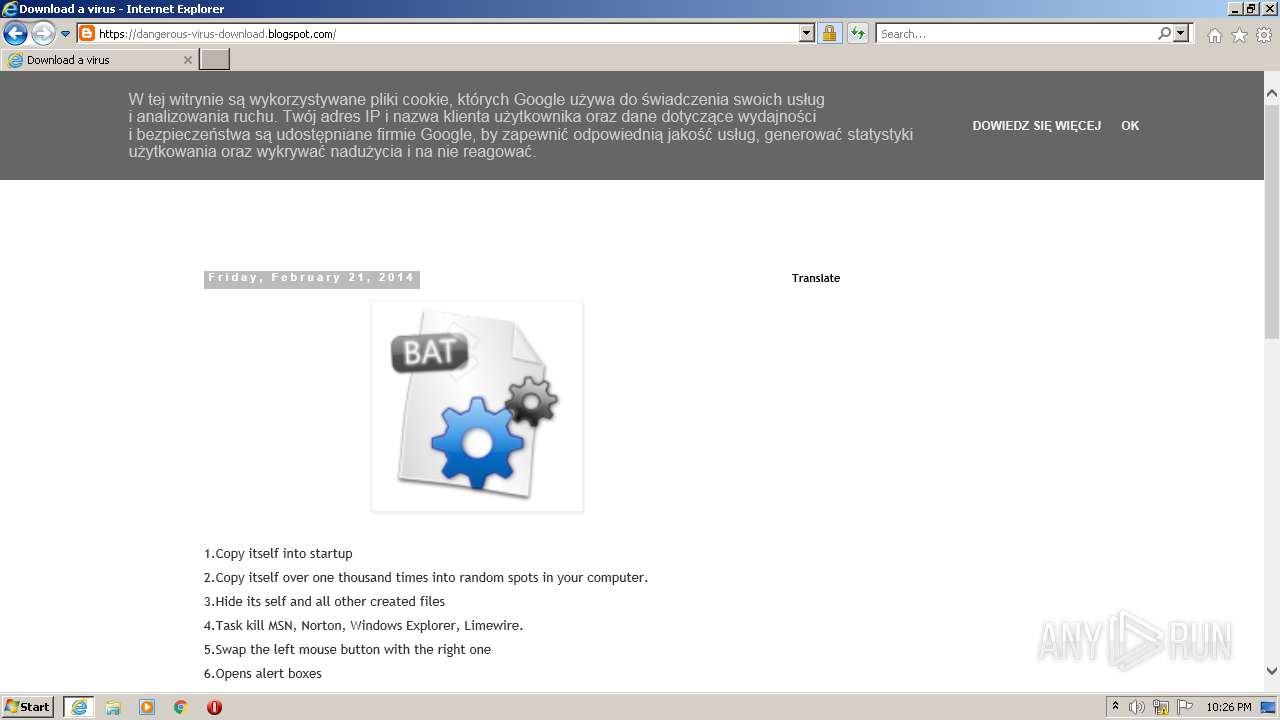
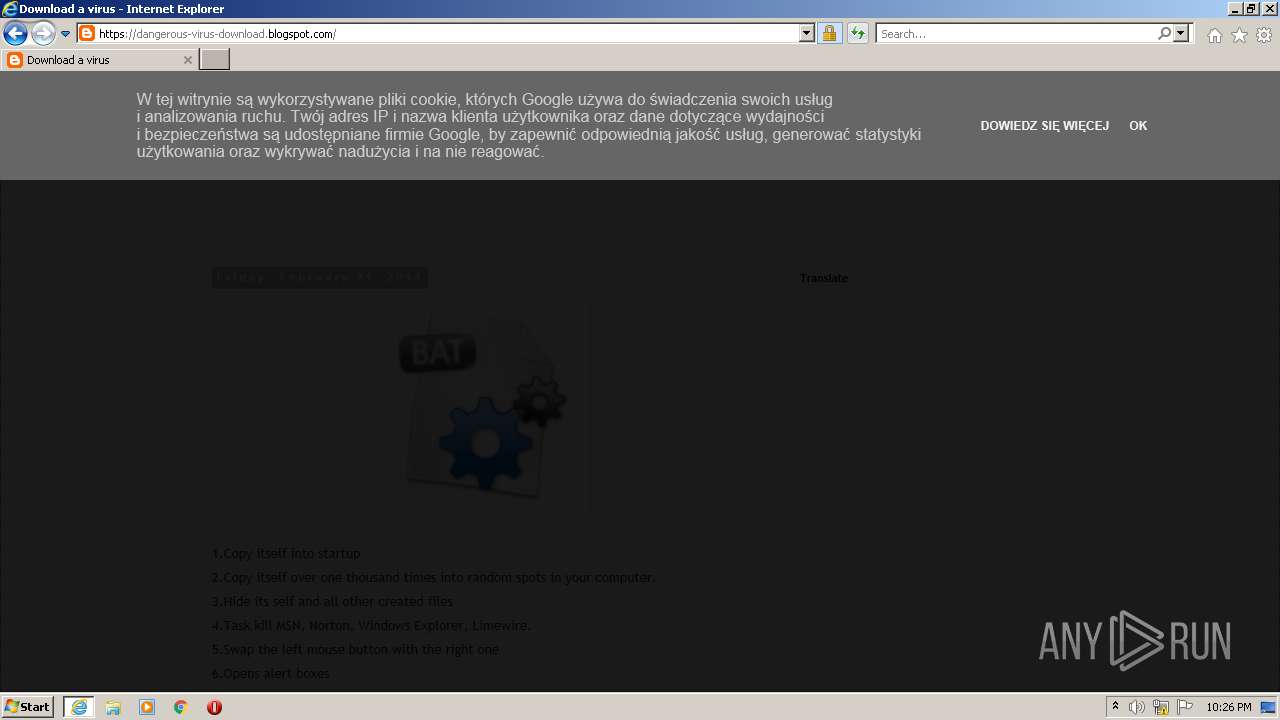
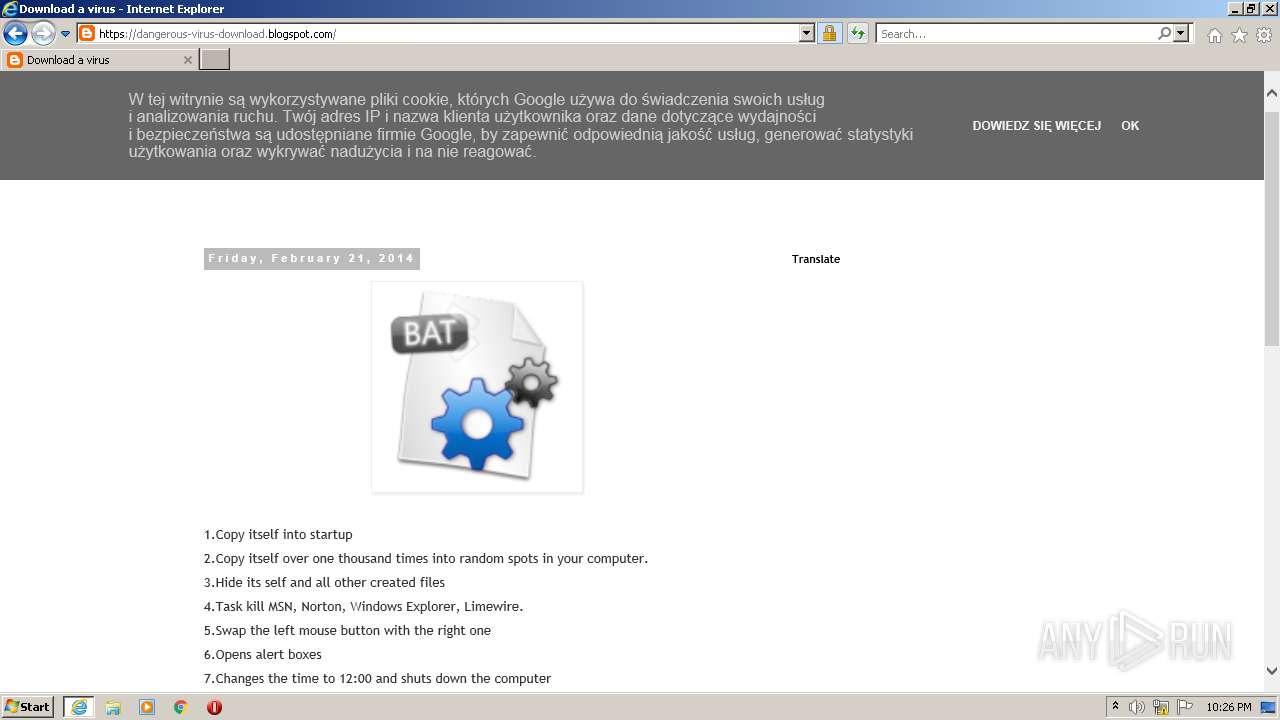
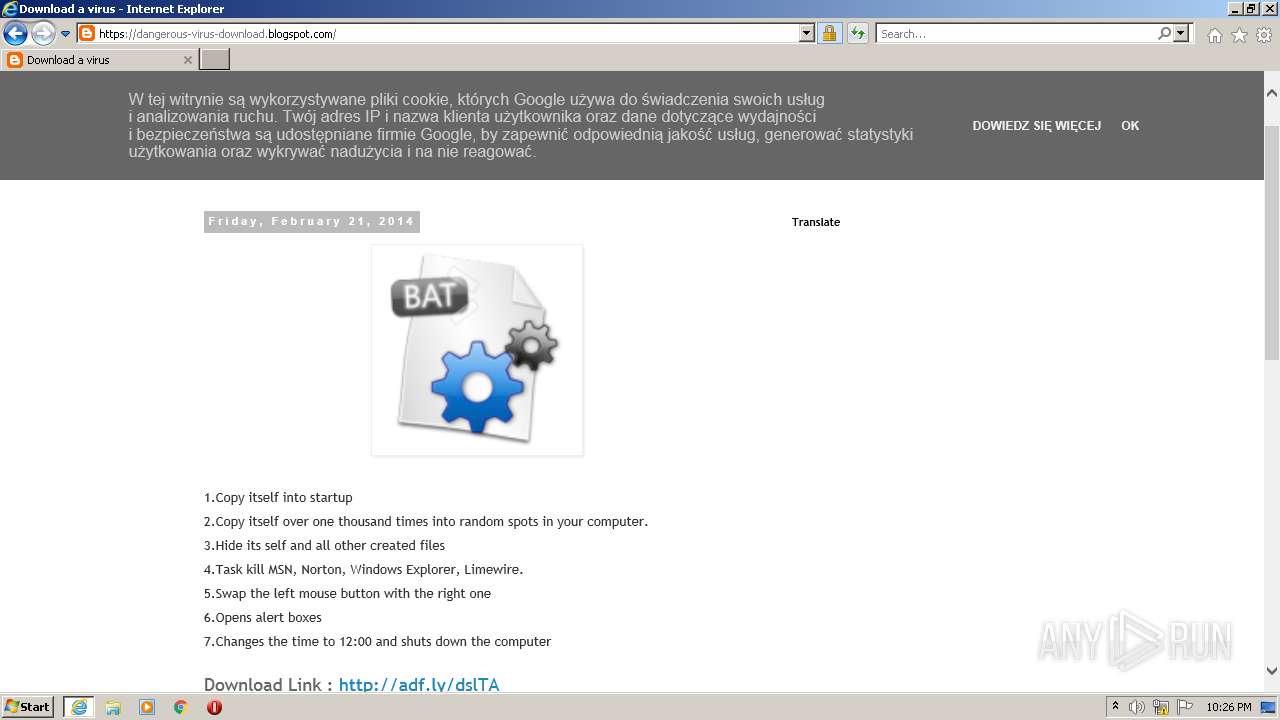
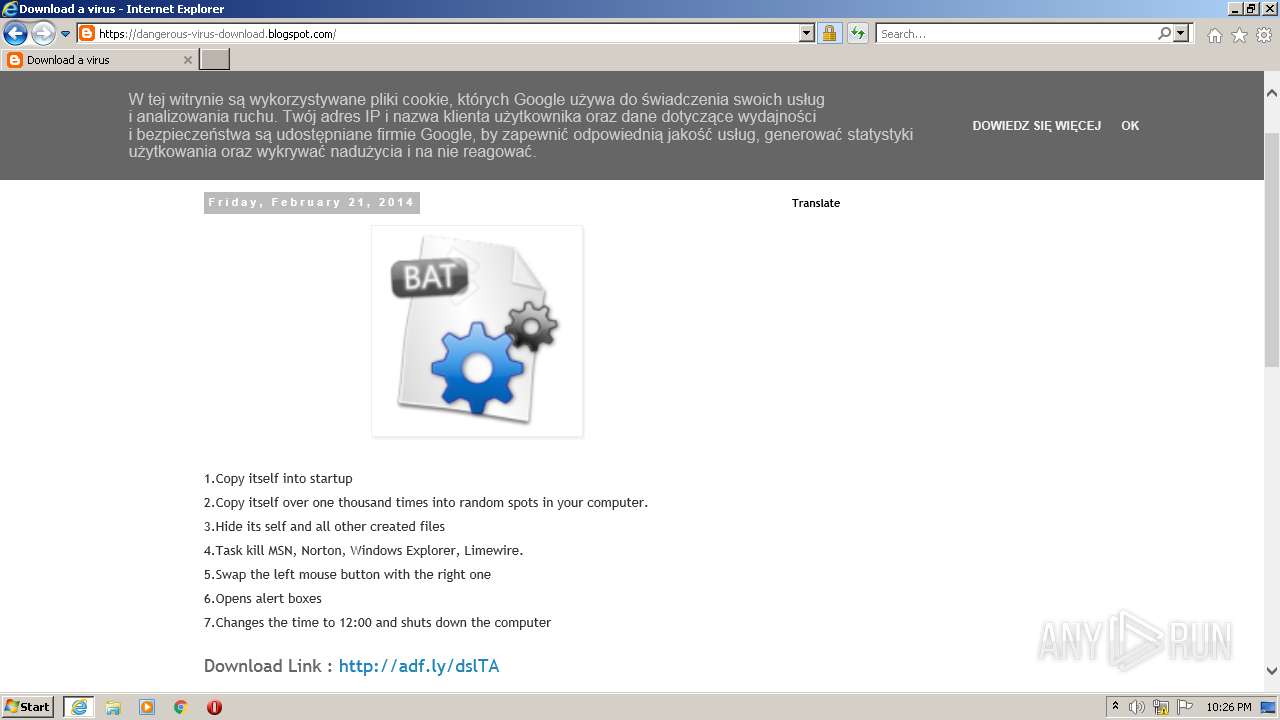
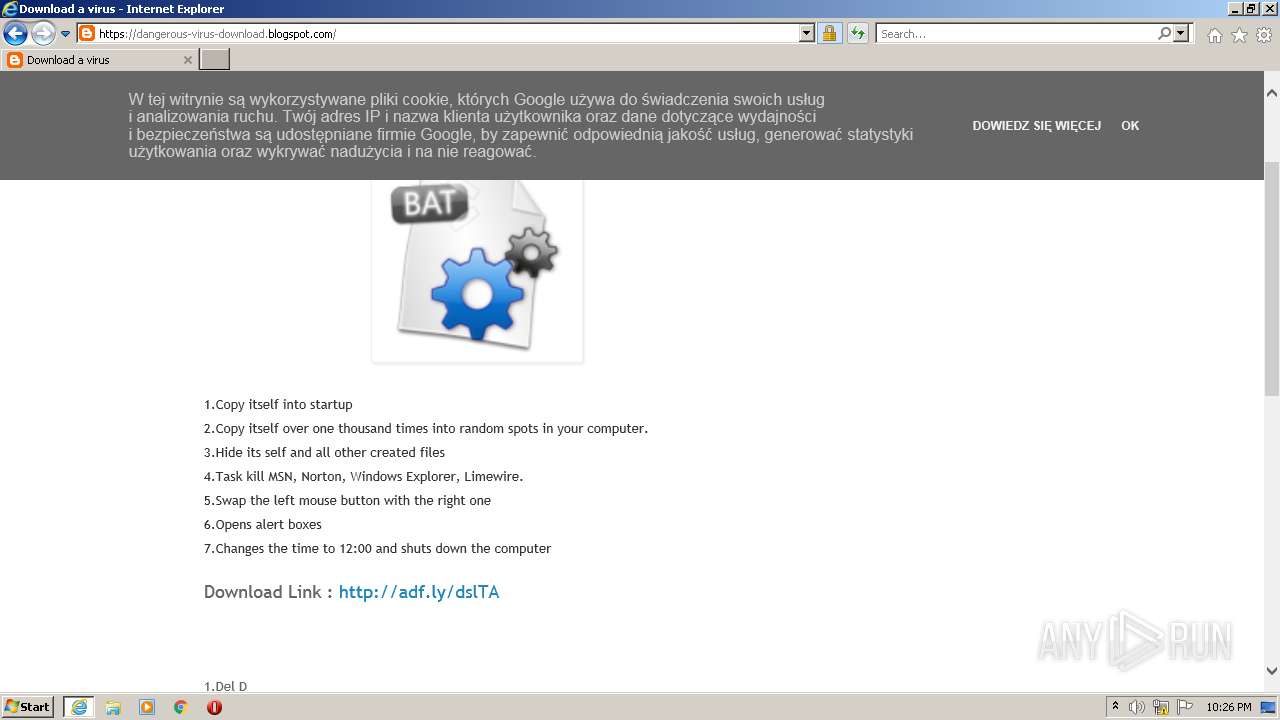
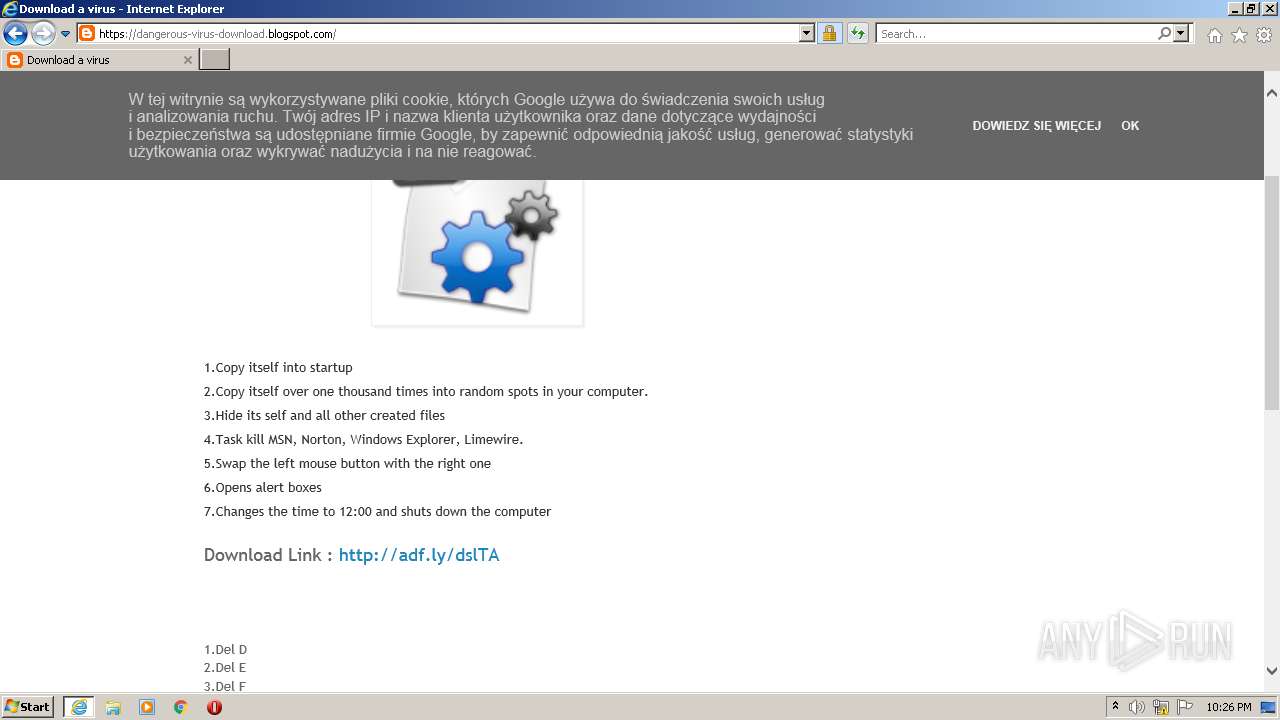
| URL: | https://doxbin.com |
| Full analysis: | https://app.any.run/tasks/6adec26f-05df-45c6-a366-adf3c140a4be |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2022, 21:24:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C07D8B45DE0546D662AB7421B83FC674 |
| SHA1: | B43CEAD161A84A3ECE07579063D9DD55C0771AD3 |
| SHA256: | 1276B9B5F3E71CFEEE6ABEAA6A75C44519A92D67314B2C580BAA27E80C92B1AF |
| SSDEEP: | 3:N8S9KI:2SV |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 3124)
- iexplore.exe (PID: 500)
INFO
Reads the computer name
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 3124)
- iexplore.exe (PID: 500)
Reads settings of System Certificates
- iexplore.exe (PID: 3124)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 500)
Creates files in the user directory
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 3124)
- iexplore.exe (PID: 500)
Checks supported languages
- iexplore.exe (PID: 3124)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 500)
Application launched itself
- iexplore.exe (PID: 3124)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3040)
Changes internet zones settings
- iexplore.exe (PID: 3124)
Checks Windows Trust Settings
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 3124)
- iexplore.exe (PID: 500)
Reads internet explorer settings
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 500)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3124)
Changes settings of System certificates
- iexplore.exe (PID: 3124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 500 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3124 CREDAT:1185044 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3124 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3124 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://doxbin.com" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
22 589
Read events
22 388
Write events
195
Delete events
6
Modification events
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30972049 | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30972049 | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
27
Text files
248
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\283828D566CA06F073380A6DC1380330 | der | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\283828D566CA06F073380A6DC1380330 | binary | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SYLB5X53.txt | text | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab51F1.tmp | compressed | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar51F2.tmp | cat | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\SC78ZBIT.htm | html | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
115
DNS requests
45
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
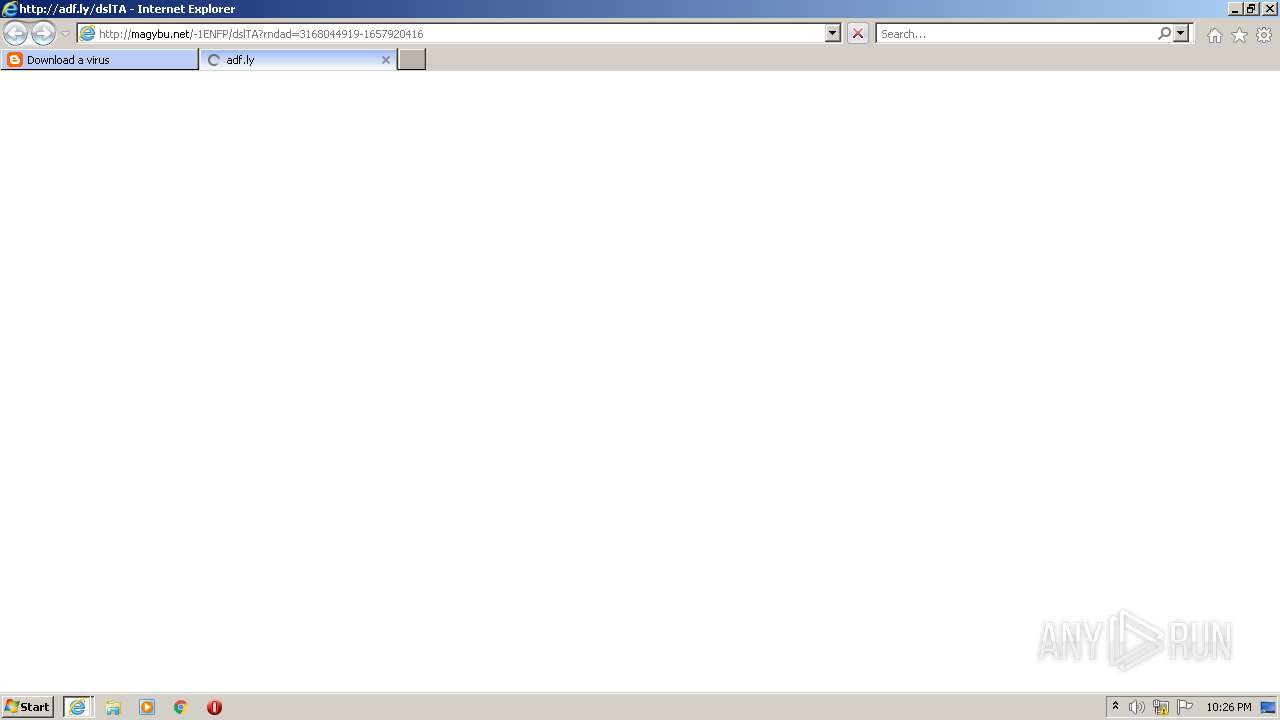
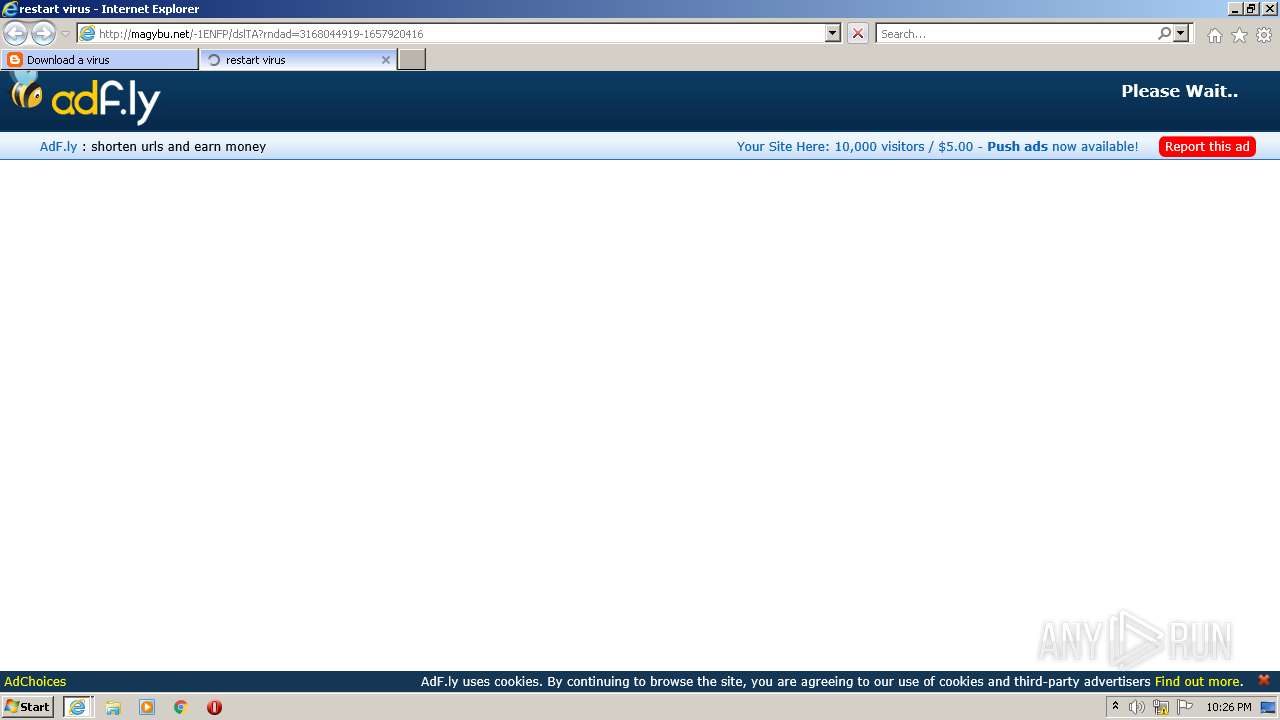
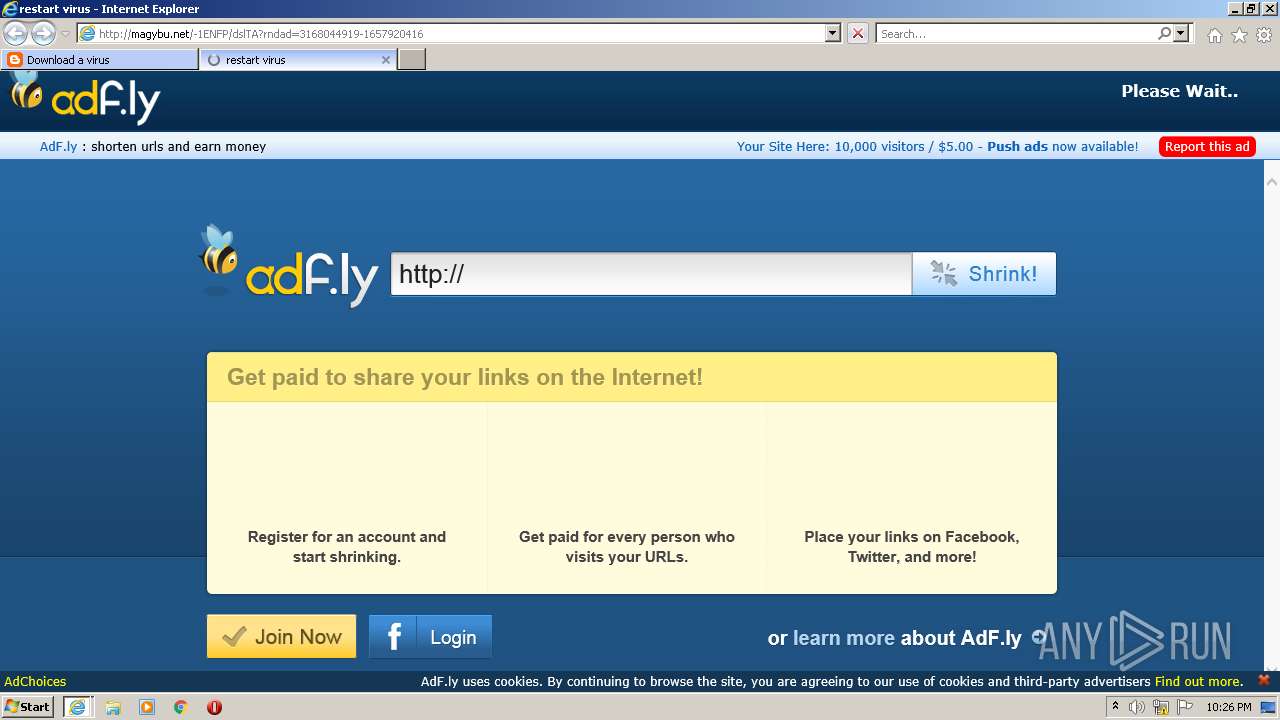
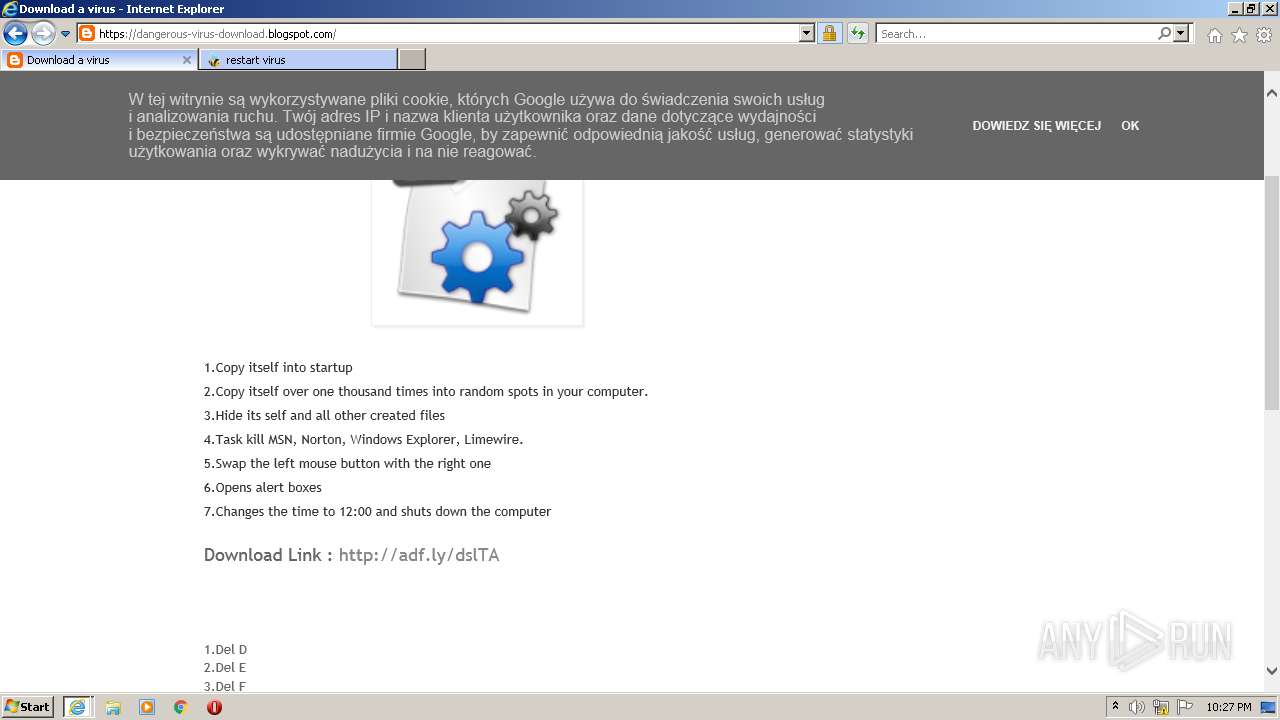
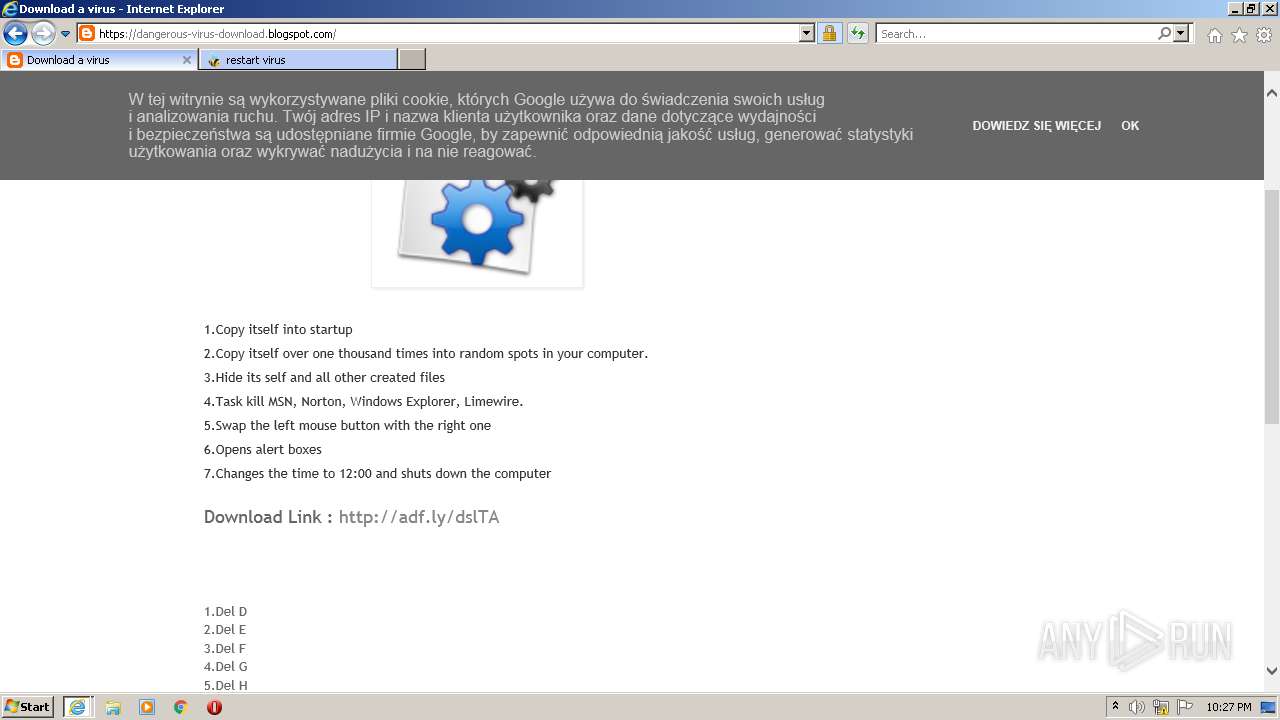
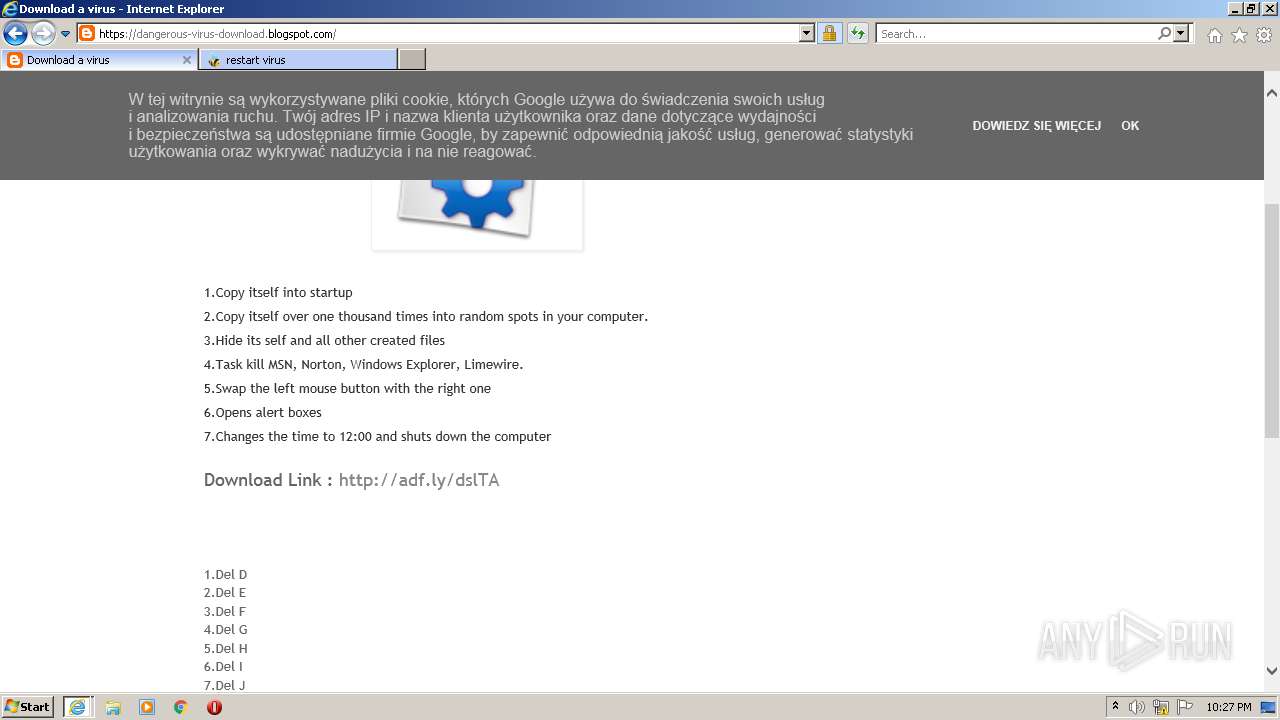
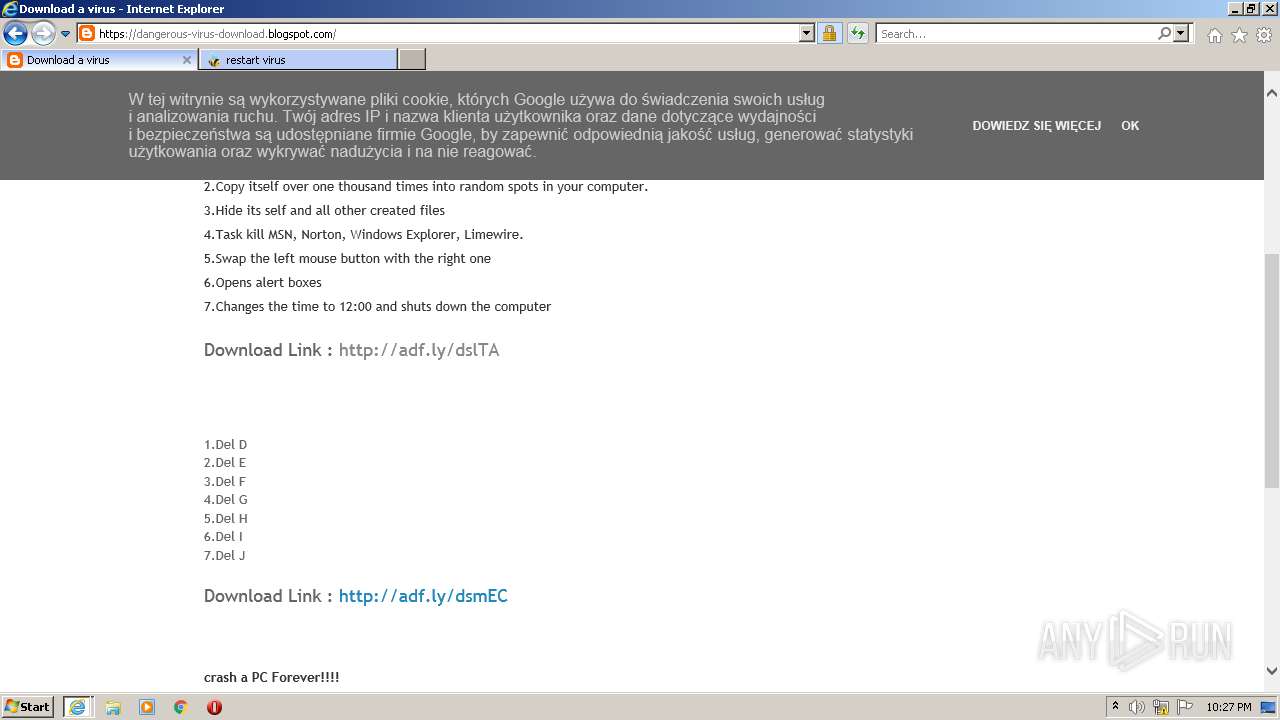
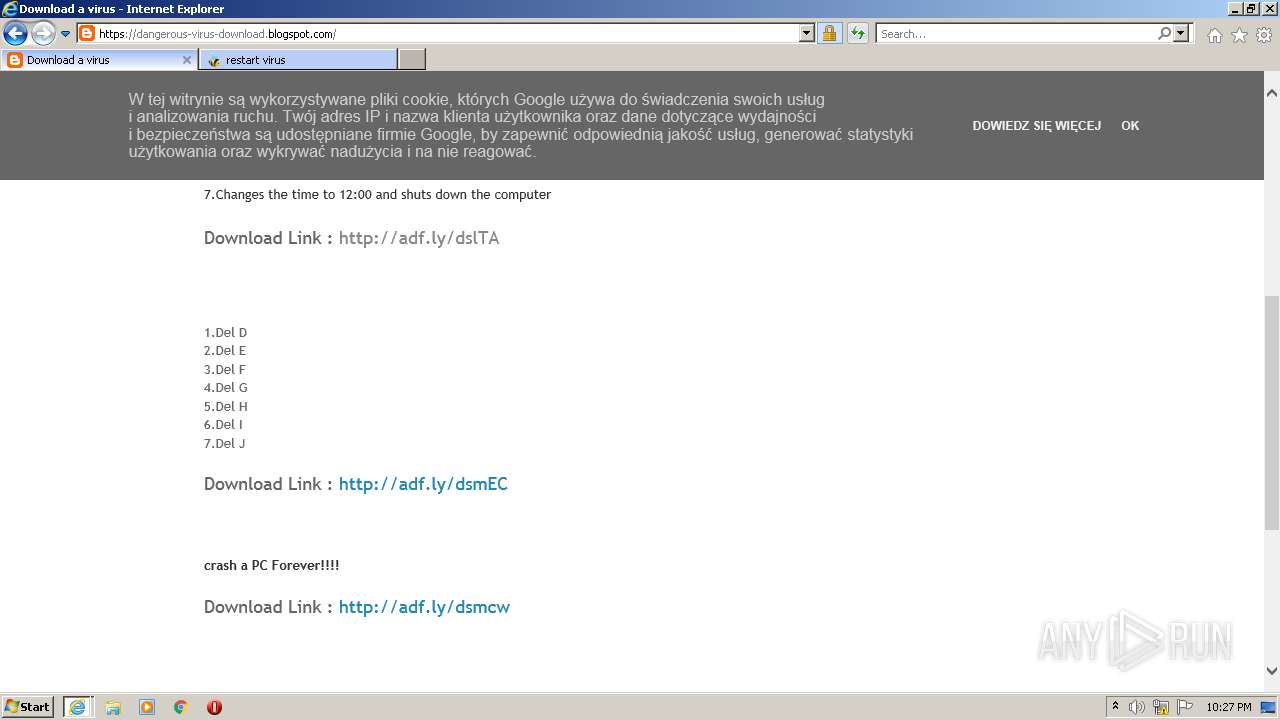
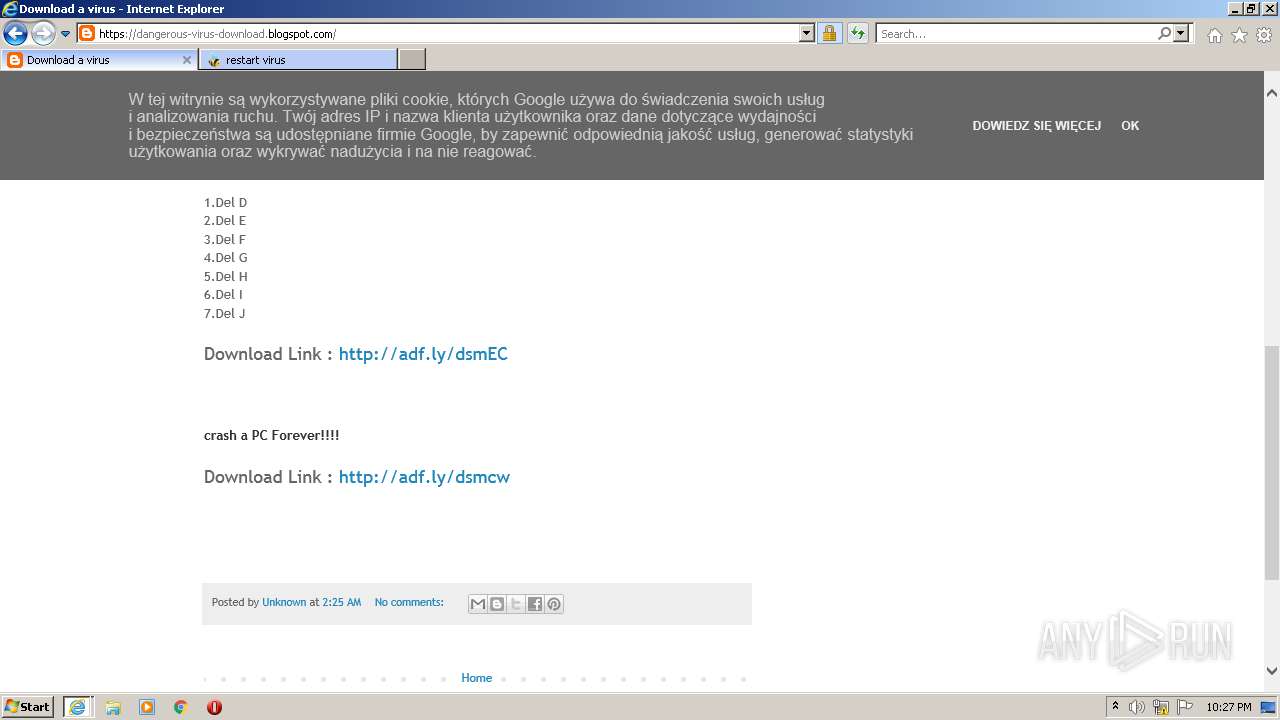
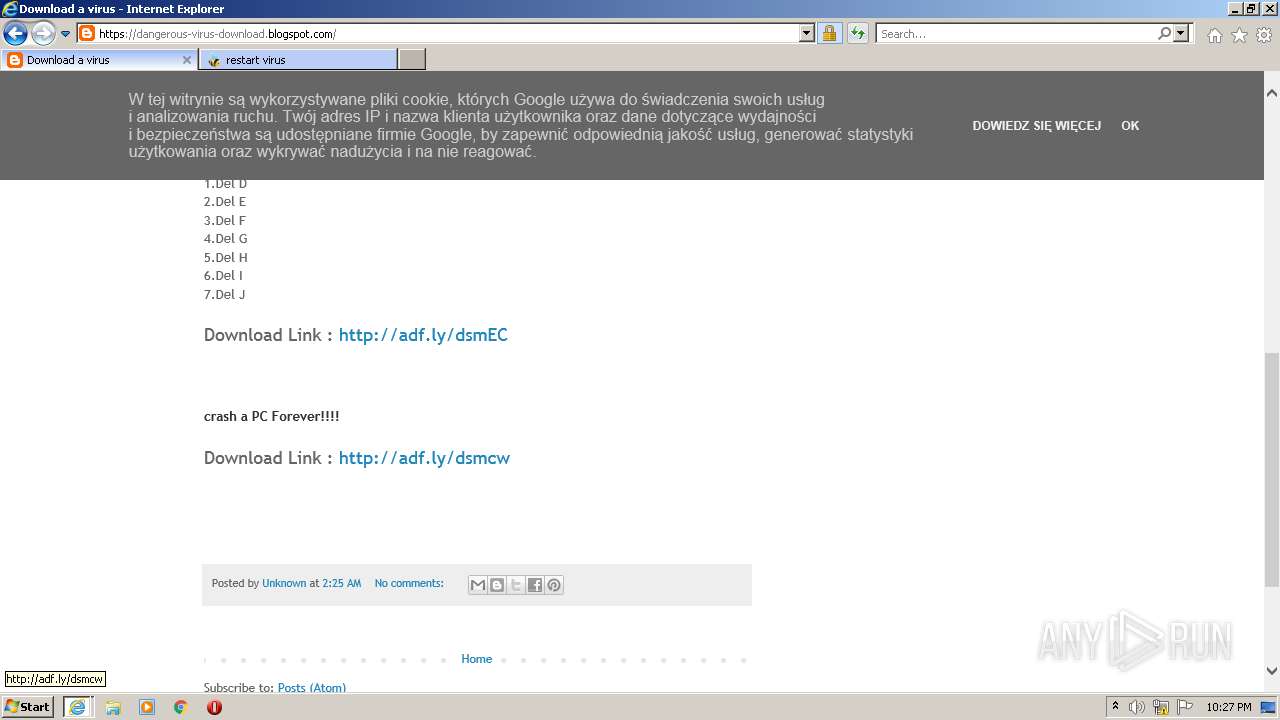
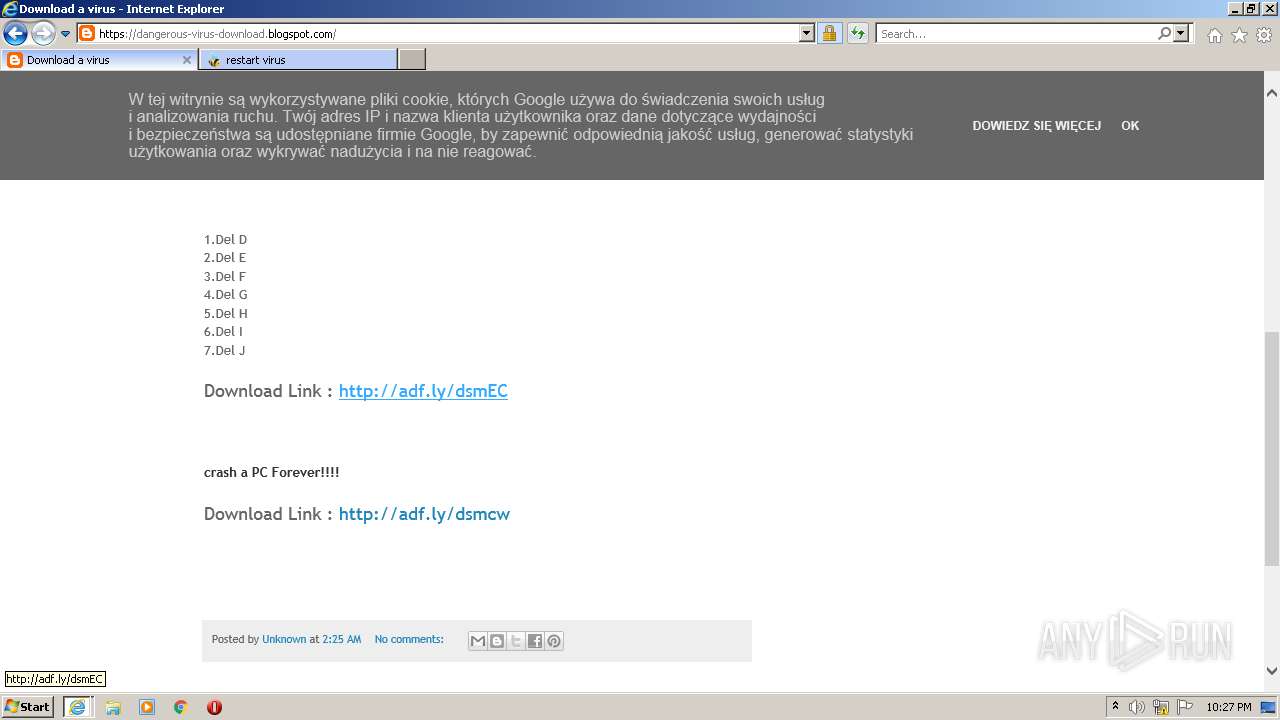
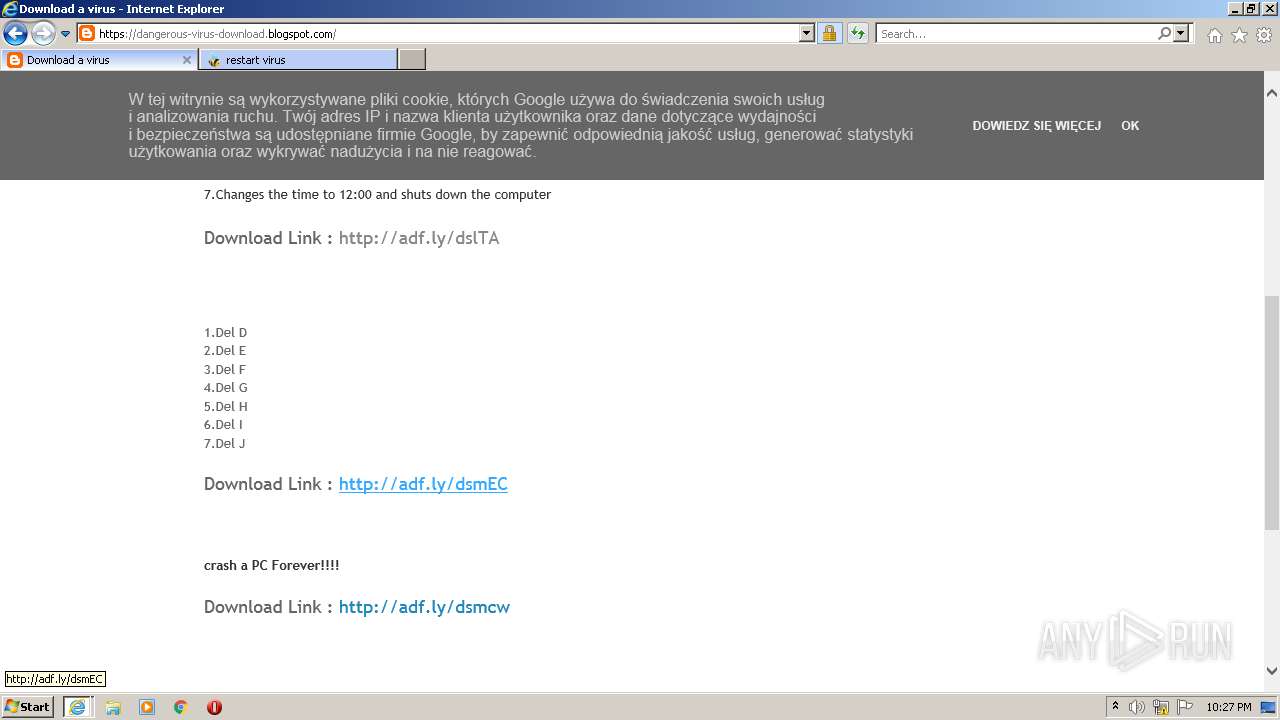
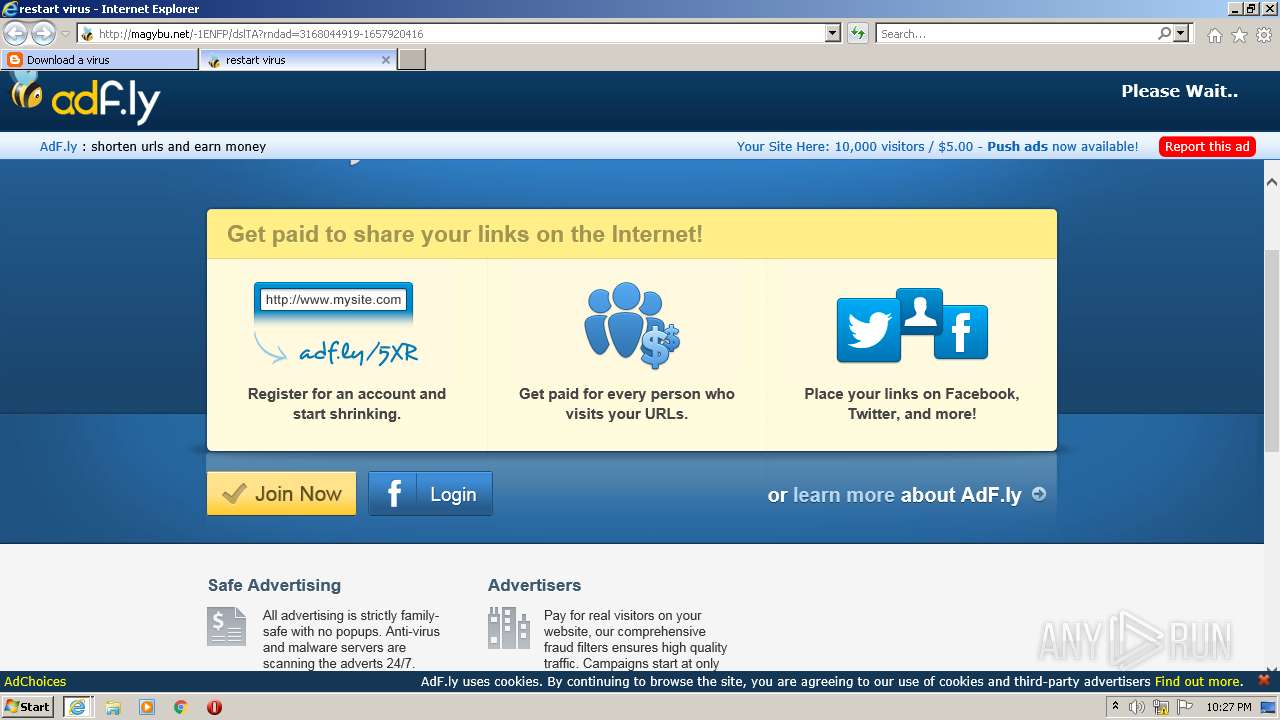
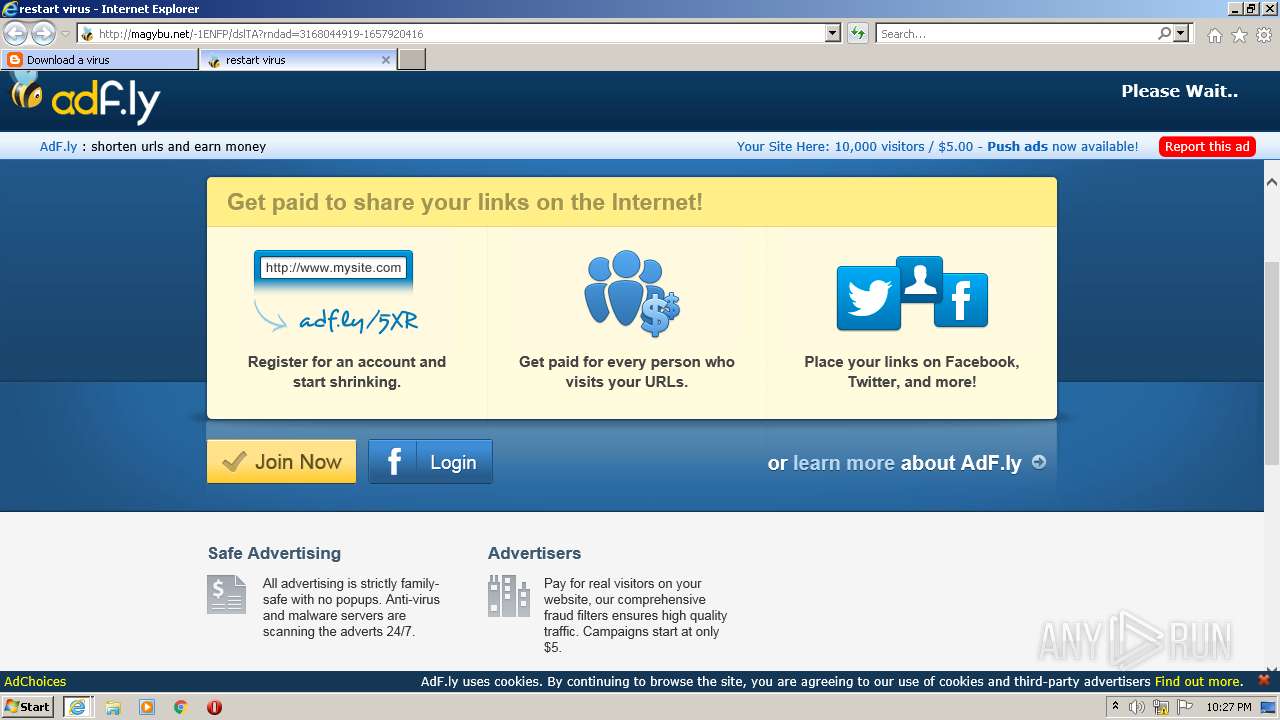
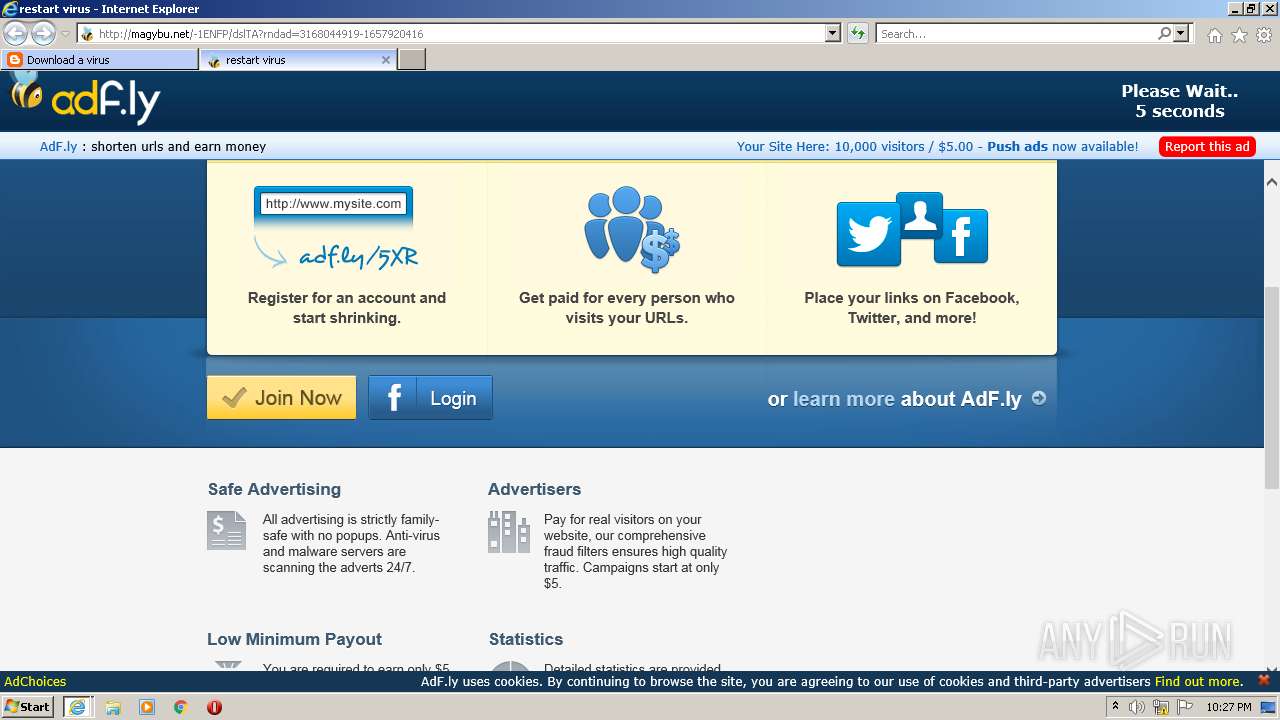
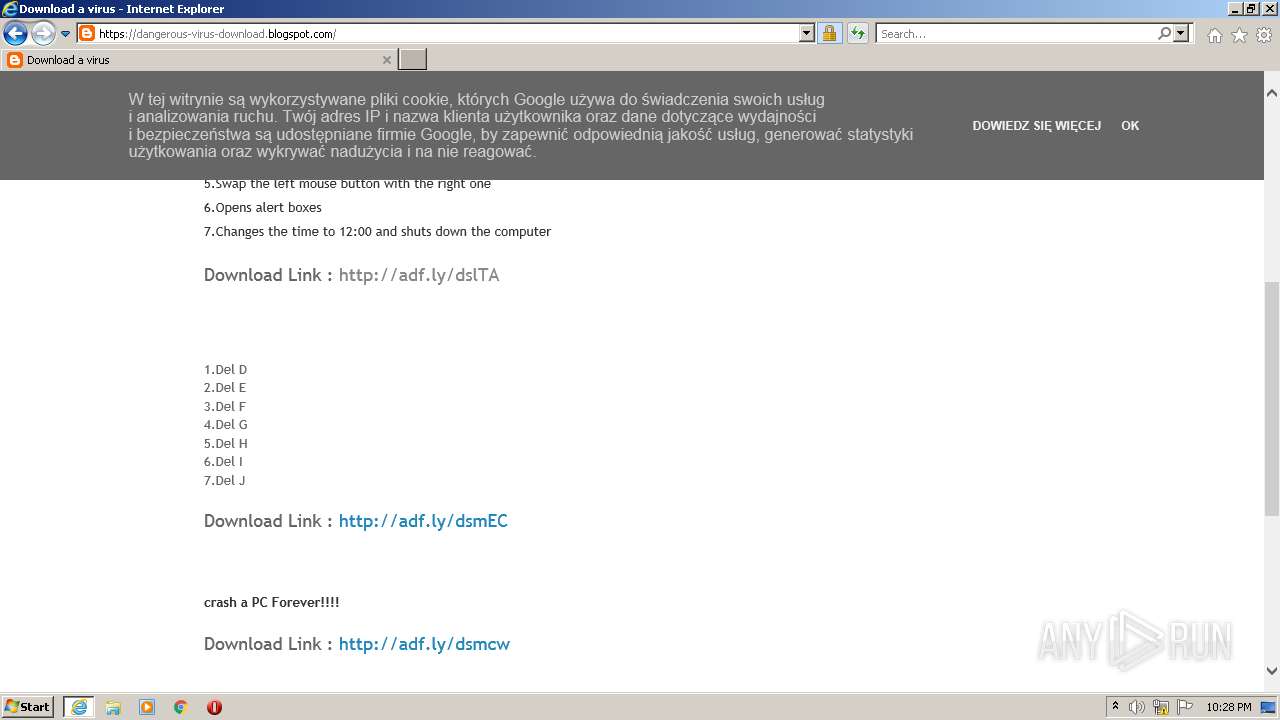
500 | iexplore.exe | GET | 301 | 104.20.67.244:80 | http://adf.ly/dslTA | US | — | — | shared |
3124 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
3040 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDV8vrp%2FmHnTApoOnh%2B0sMH | US | der | 472 b | whitelisted |
3124 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
3040 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC8LbKC6DMw9BLG%2BP%2FsrywD | US | der | 472 b | whitelisted |
3040 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3124 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3040 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGDPbUjTbuxYEgUDCZGttxQ%3D | US | der | 471 b | whitelisted |
3040 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFEXqDlk0KpHEjSOBz6OhEI%3D | US | der | 471 b | whitelisted |
3040 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?8ecb17faef894749 | US | compressed | 60.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3040 | iexplore.exe | 190.115.31.91:443 | doxbin.com | DANCOM LTD | BZ | suspicious |
3040 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3124 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3124 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3124 | iexplore.exe | 190.115.31.91:443 | doxbin.com | DANCOM LTD | BZ | suspicious |
3040 | iexplore.exe | 107.160.74.131:443 | files.catbox.moe | Psychz Networks | US | suspicious |
3124 | iexplore.exe | 96.16.143.41:443 | go.microsoft.com | Akamai International B.V. | US | whitelisted |
3124 | iexplore.exe | 204.79.197.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
3124 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3124 | iexplore.exe | 20.25.53.147:443 | query.prod.cms.msn.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
doxbin.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r3.o.lencr.org |
| shared |
files.catbox.moe |
| suspicious |
crl3.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
2 ETPRO signatures available at the full report