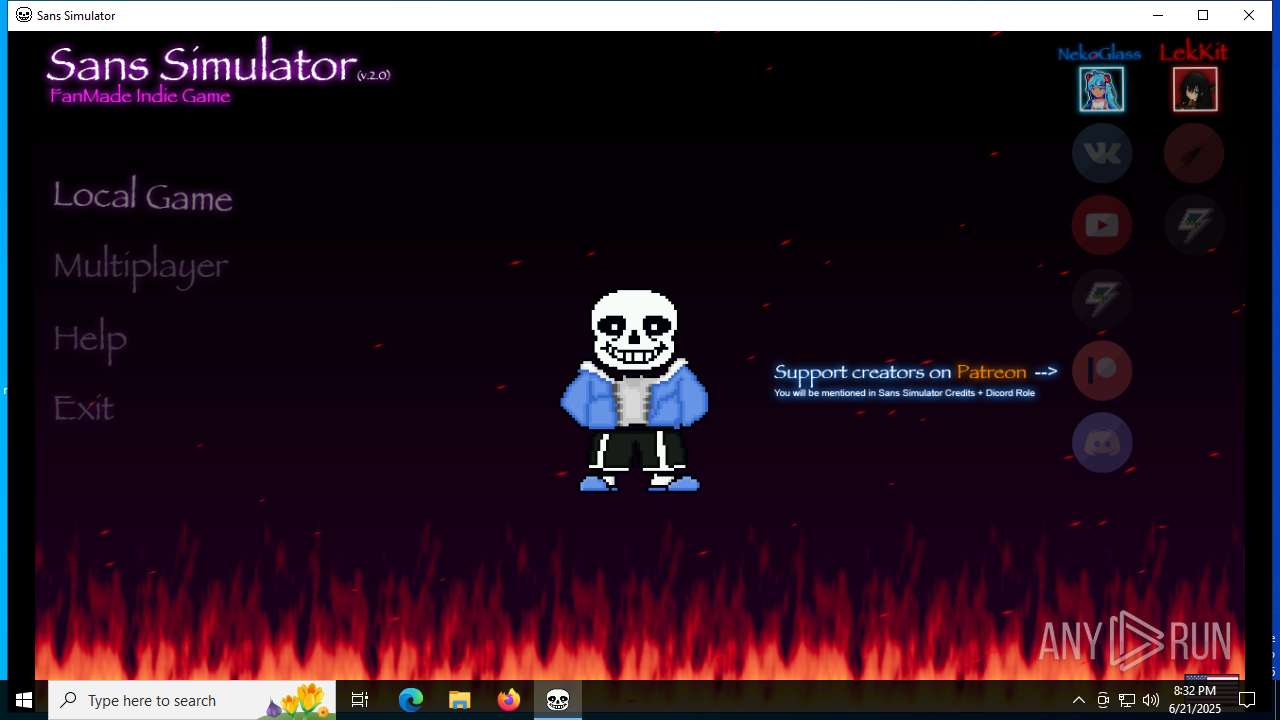
| File name: | sans-simulator.exe |
| Full analysis: | https://app.any.run/tasks/24a68970-8b24-4abc-8d65-09ccdf813885 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 20:32:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 60EF884EE30D22F73DF6A12F1D8B45D6 |
| SHA1: | 68644DC4EC055CDB1A9540D89E823B860DCB792B |
| SHA256: | 125DDAD93CF41DB0444D4A9470586BFC77672C964443E2C26F491F9EB85C95FD |
| SSDEEP: | 196608:knR0spogYseU9GwbGFr09c2letV3pEOSn//LchsskTsVkpwJN+zJbM9Ck4B:knSsppYsKws0OHF0ohss1JN+FQUk4B |
MALICIOUS
Executing a file with an untrusted certificate
- sans-simulator.exe (PID: 2628)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- sans-simulator.exe (PID: 2072)
Executable content was dropped or overwritten
- sans-simulator.exe (PID: 2072)
INFO
Create files in a temporary directory
- sans-simulator.exe (PID: 2072)
Reads the software policy settings
- slui.exe (PID: 3936)
Checks supported languages
- sans-simulator.exe (PID: 2072)
The sample compiled with english language support
- sans-simulator.exe (PID: 2072)
Reads the computer name
- sans-simulator.exe (PID: 2072)
Checks proxy server information
- slui.exe (PID: 3936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:12:10 16:58:55+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 525312 |
| InitializedDataSize: | 435712 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5faa5 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Process default |
| CharacterSet: | Unicode |
| CompanyName: | Neko'mmunity |
| FileDescription: | Sans Simulator Release |
| FileVersion: | 2.0.0 |
| LegalCopyright: | NekoGlass |
Total processes
137
Monitored processes
3
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2072 | "C:\Users\admin\Desktop\sans-simulator.exe" | C:\Users\admin\Desktop\sans-simulator.exe | explorer.exe | ||||||||||||
User: admin Company: Neko'mmunity Integrity Level: HIGH Description: Sans Simulator Release Version: 2.0.0 Modules
| |||||||||||||||
| 2628 | "C:\Users\admin\Desktop\sans-simulator.exe" | C:\Users\admin\Desktop\sans-simulator.exe | — | explorer.exe | |||||||||||
User: admin Company: Neko'mmunity Integrity Level: MEDIUM Description: Sans Simulator Release Exit code: 3221226540 Version: 2.0.0 Modules
| |||||||||||||||
| 3936 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 895
Read events
3 886
Write events
9
Delete events
0
Modification events
| (PID) Process: | (2072) sans-simulator.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (2072) sans-simulator.exe | Key: | HKEY_CURRENT_USER\System\CurrentControlSet\Control\MediaProperties\PrivateProperties\DirectInput\VID_0627&PID_0001\Calibration\0 |
| Operation: | write | Name: | GUID |
Value: 10B3C5DEDE4EF0118001444553540000 | |||
| (PID) Process: | (2072) sans-simulator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Version |
Value: 0A050000 | |||
| (PID) Process: | (2072) sans-simulator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: SANS-SIMULATOR.EXE | |||
| (PID) Process: | (2072) sans-simulator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Id |
Value: SANS-SIMULATOR.EXE5FD253CF019FCBB0 | |||
| (PID) Process: | (2072) sans-simulator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | MostRecentStart |
Value: 1B301CA1EBE2DB01 | |||
Executable files
12
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\kcedit.mfx | executable | |
MD5:11A493B3D84A7E8A017A7151FFADD97D | SHA256:451C843C89CA05F37E77468BC6B1A63E78B92D2D4DAC630AD7F6555D9BC4AD38 | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\mmfs2.dll | executable | |
MD5:09FEB373CFCF9FD9A618D0A38759E297 | SHA256:4DE2B0753A286D3572574D6C03F769176973B9E2EB53F5B6645B32854983EFF0 | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\mmf2d3d9.dll | executable | |
MD5:3AE47534F1224C4797176107A9A41683 | SHA256:53EDF5138930D52B473104CE0D085413248D15A4AA891AC02A718E89625DE6EF | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\mp3flt.sft | executable | |
MD5:DADC138BE9D36E6E4B8E4BF9EF2DE4BC | SHA256:DDEAFDA7B28BF7545E3BA164AA4A74219EB961C36BB974E0F5085A07DAF18F44 | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\kcfile.mfx | executable | |
MD5:E6F27F3F2F0CE7898678C76C4FC77B21 | SHA256:A8F34971CE7D054C2C9FB5E6495ECE25ABB20E82210C3E8DE632517982DA7E2A | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\Key.mfx | executable | |
MD5:19836CE4FB47847489F3C2C4D14A4A87 | SHA256:869C07C4A74D958EBFF04AD3E5046E9F5AB3CDA63E12EDACB15D9DD8D443A74B | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\RedRelayClient.mfx | executable | |
MD5:46B8A621E8BC1E420FE746236E1CCB98 | SHA256:2461D59C1768158D2F5DF209D1F0ED67E6D6F2FC1CB4E4946A642989FD4ADA56 | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\joystick.mfx | executable | |
MD5:9394A05326BF57420B77AC9712B9944B | SHA256:2B4346EAB390370DB0F7ED1261E3C38D36D749C078B235F63BE62A4317E33EEA | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\oggflt.sft | executable | |
MD5:0C8C1EE3BA92189F4CE21D1B396A2765 | SHA256:9E589F86317D840DF9BB74F6EE20C24CA65AFE58F4009740382F63A0F5531941 | |||
| 2072 | sans-simulator.exe | C:\Users\admin\AppData\Local\Temp\ce7a99ff-b344-489c-b586-f1e8c60c9aa9.FusionApp\mmf2d3d8.dll | executable | |
MD5:FA439EDEB7D0BF6F637670F14CEBD157 | SHA256:B558A04FD67D0D7CD71170A2B7A1BFD004F0B5BCC268E7B38C3A12FE72CA26D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
39
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.128:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
2468 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 23.9 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.66:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
592 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2468 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2468 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
sans-simulator.exe | Start app
|
sans-simulator.exe | Start Frame 0
|
sans-simulator.exe | End Frame 0
|
sans-simulator.exe | Start Frame 1
|