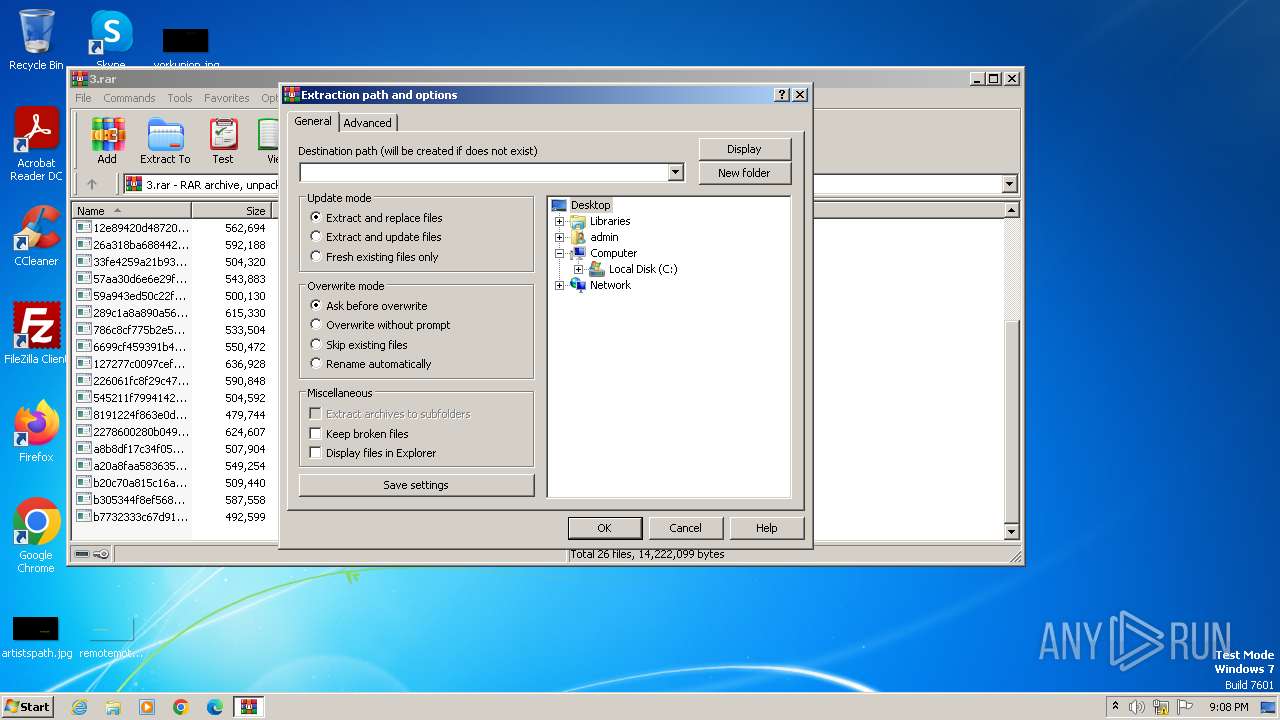
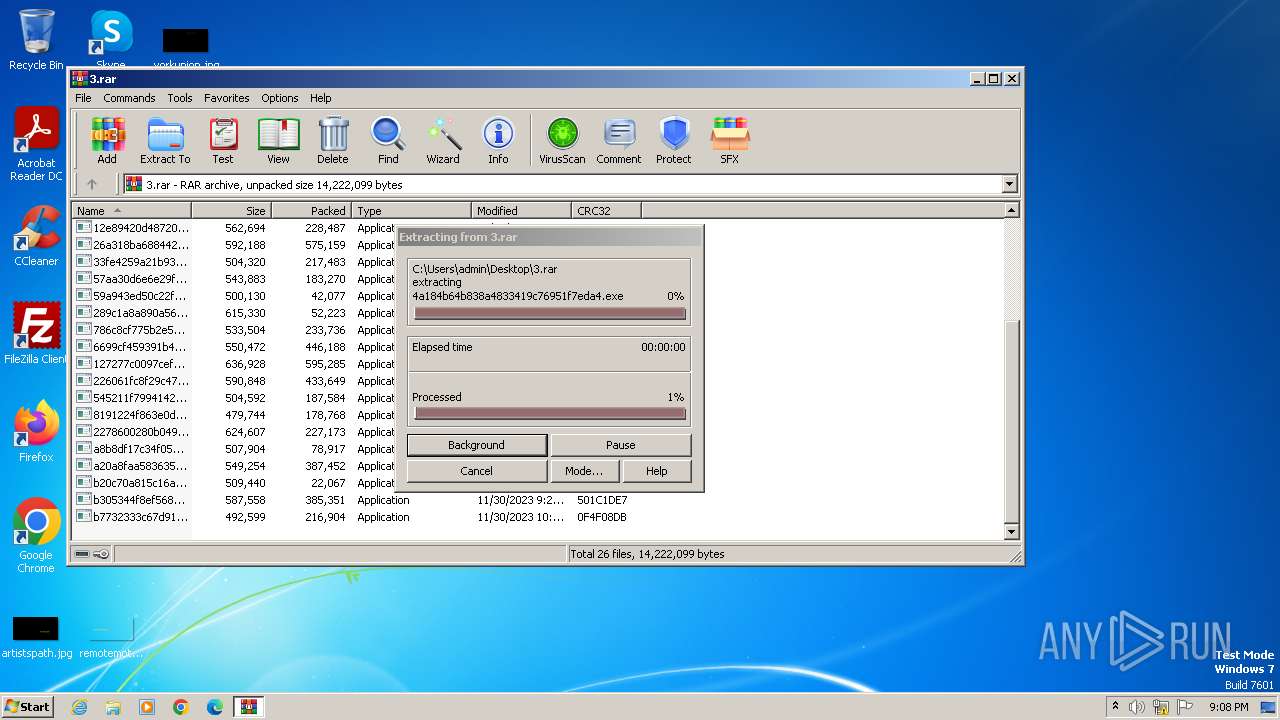
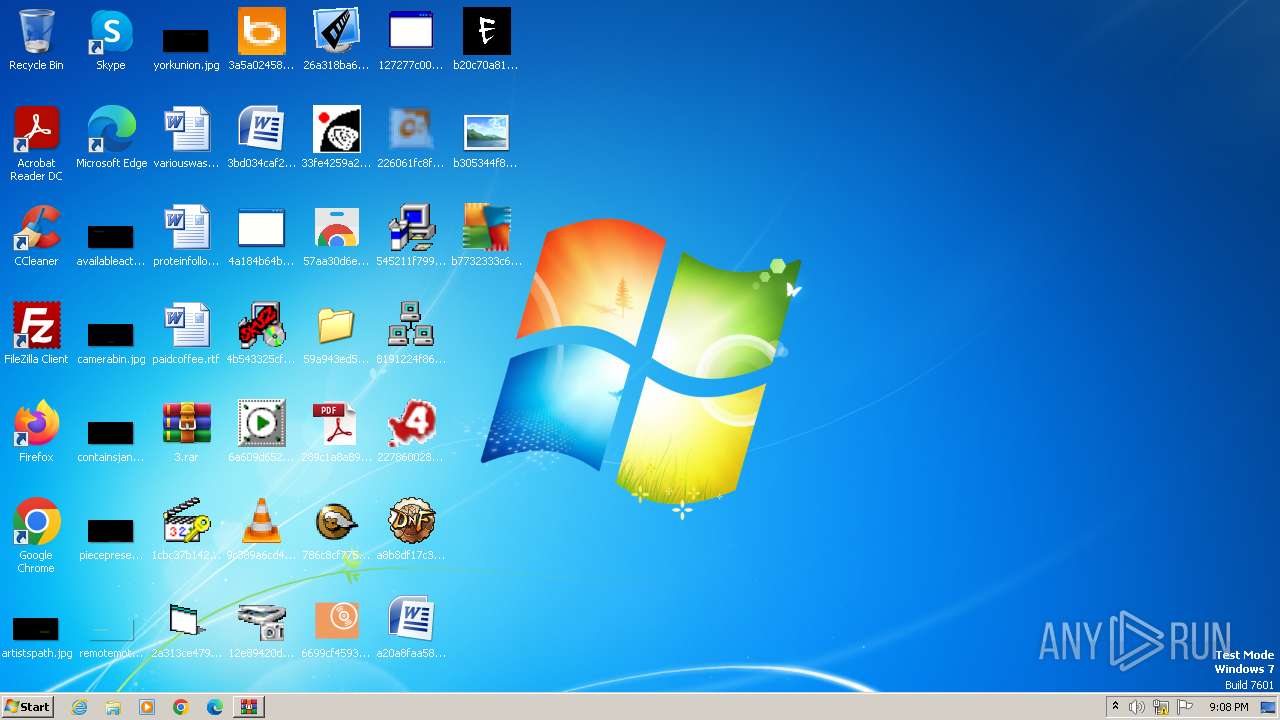
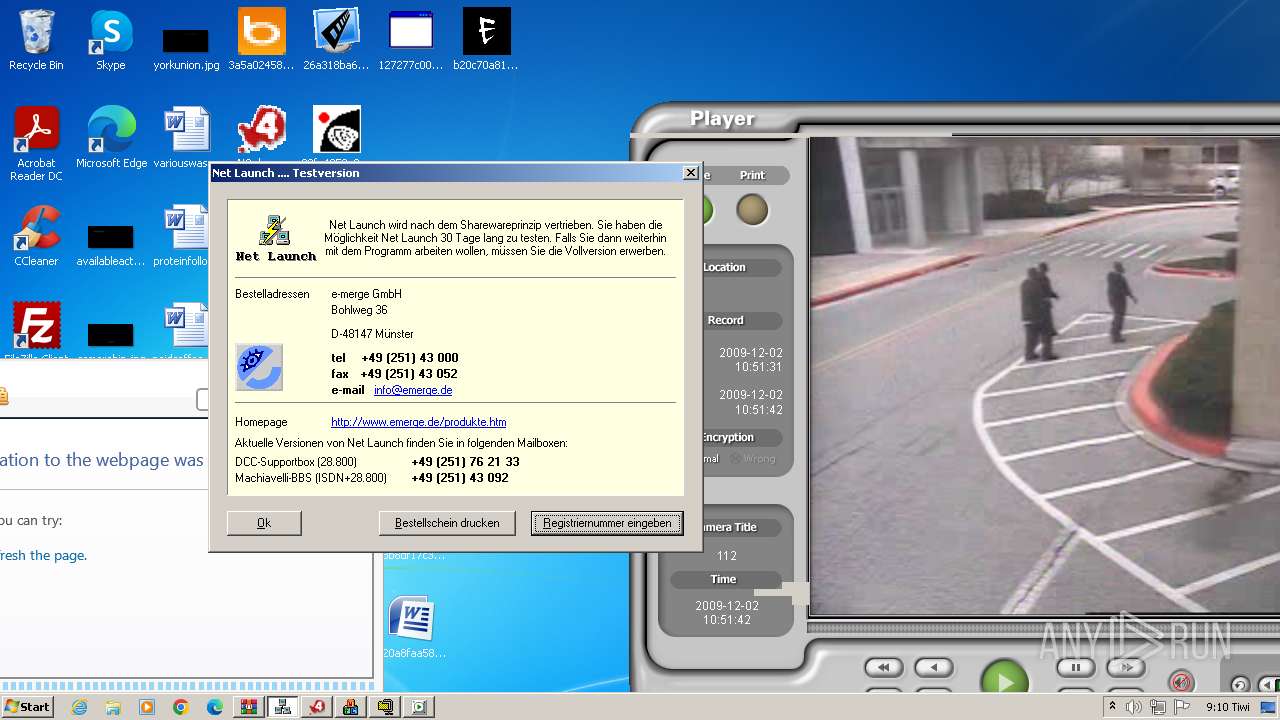
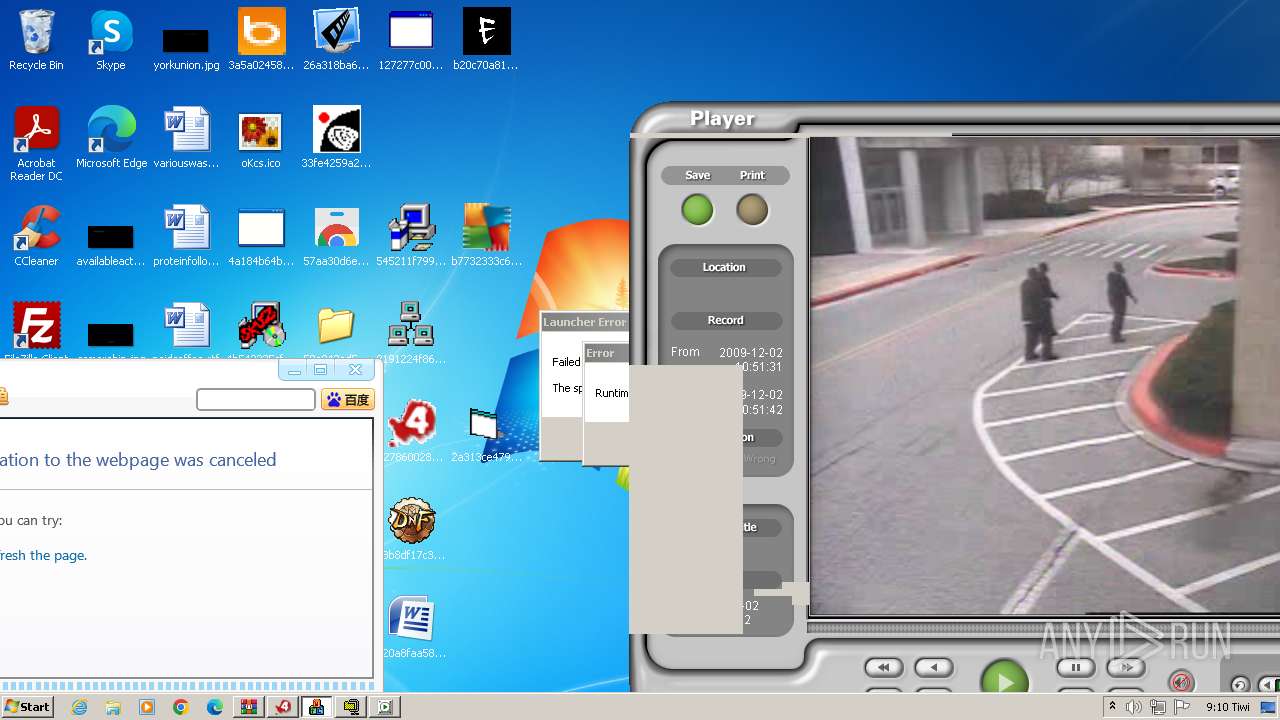
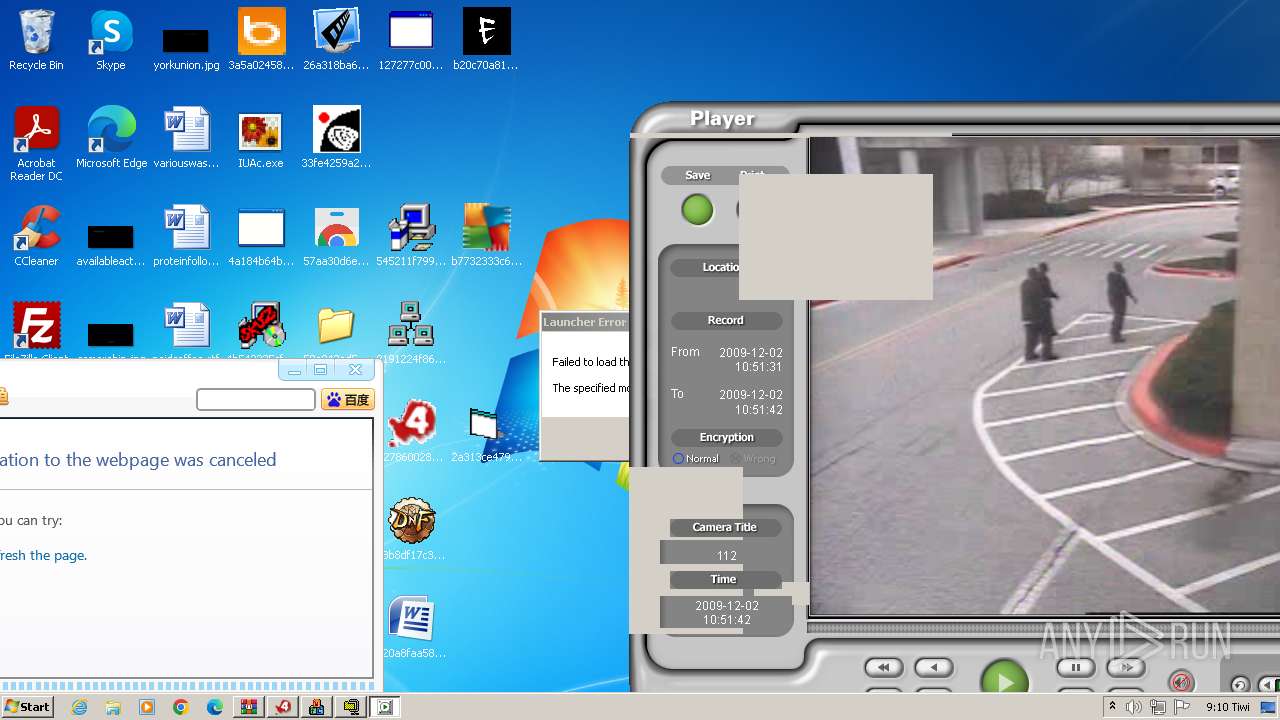
| File name: | 3.rar |
| Full analysis: | https://app.any.run/tasks/3de40d48-bcba-43e0-b499-93db36031e42 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 21:08:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 3C2D3ACCA0A6F4AA1DBDDB3F9F56672D |
| SHA1: | 78D668626AE46490976AA9A806C6FF13E8AA7D17 |
| SHA256: | 125C4B80F91917F505CFECE73AE6F73B1300CF0A0C11B455BDC078B091C5CD1A |
| SSDEEP: | 98304:ZYFGwzKocBggxk0MZwwkZVt++gsBlBP5FZ0k/pLU3bgLMmGAfYP0sp2KE/1pkOVW:6Xx2uQScYgwscEuxDAfnh4Whc |
MALICIOUS
Drops the executable file immediately after the start
- a20a8faa583635241f71dbed54116e37.exe (PID: 2292)
- b305344f8ef568505c2d78ef9fa3840b.exe (PID: 2544)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- F8DB.tmp (PID: 2300)
- 226061fc8f29c47dbf807957e4c7edaa.exe (PID: 2084)
- 2a313ce479edd2ba234cd6c7975da5bf.exe (PID: 1608)
- F996.tmp (PID: 3964)
- 127277c0097cef5ce18f0002a2456f84.exe (PID: 3784)
- FA52.tmp (PID: 3388)
- FADF.tmp (PID: 2536)
- FB7B.tmp (PID: 3092)
- FBD9.tmp (PID: 3972)
- FCA4.tmp (PID: 3408)
- FD01.tmp (PID: 3652)
- FD7E.tmp (PID: 3124)
- FDEC.tmp (PID: 3724)
- FEA7.tmp (PID: 2128)
- FFA1.tmp (PID: 3356)
- FFFF.tmp (PID: 3400)
- FF05.tmp (PID: 3336)
- 5D.tmp (PID: 2368)
- 128.tmp (PID: 1436)
- CA.tmp (PID: 2092)
- 1B5.tmp (PID: 1808)
- 29F.tmp (PID: 1032)
- 32C.tmp (PID: 3524)
- 3E7.tmp (PID: 1816)
- 779297.exe (PID: 2924)
- 464.tmp (PID: 4052)
- 53F.tmp (PID: 3748)
- 6a609d65263f2c95ab44b534255b53c9.exe (PID: 1348)
- 5CB.tmp (PID: 552)
- 658.tmp (PID: 2052)
- 6699cf459391b430d49cbc80b2722bee.exe (PID: 2460)
- 733.tmp (PID: 2232)
- 86B.tmp (PID: 824)
- 8F8.tmp (PID: 1008)
- 975.tmp (PID: 2776)
- 57aa30d6e6e29f4d34629179dcac75b7.exe (PID: 2384)
- 289c1a8a890a567f4f70235ced85f763.exe (PID: 2344)
- AAD.tmp (PID: 3980)
- BC7.tmp (PID: 1924)
- 4a184b64b838a4833419c76951f7eda4.exe (PID: 1820)
- C53.tmp (PID: 2196)
- D2E.tmp (PID: 2920)
- DF9.tmp (PID: 2532)
- F03.tmp (PID: 1696)
- E86.tmp (PID: 3216)
- 101C.tmp (PID: 3340)
- A40.tmp (PID: 2648)
- F9F.tmp (PID: 2896)
- 107A.tmp (PID: 2820)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- 10F7.tmp (PID: 3608)
- 11B2.tmp (PID: 2932)
- 1164.tmp (PID: 1296)
- 122F.tmp (PID: 3516)
- 12AC.tmp (PID: 2608)
- 12e89420d487205e997bbd25011d45fa.exe (PID: 2392)
- 158B.tmp (PID: 3876)
- 150E.tmp (PID: 3192)
- 15F8.tmp (PID: 3540)
- 1656.tmp (PID: 2316)
- 16D3.tmp (PID: 284)
- 1750.tmp (PID: 752)
- 17CD.tmp (PID: 1508)
- 9c389a6cd41fe1c54c505115125ddce8.exe (PID: 2088)
- 1905.tmp (PID: 528)
- ZaccMoMY.exe (PID: 3140)
- 19E0.tmp (PID: 2676)
- 1A7C.tmp (PID: 2040)
- 786c8cf775b2e5c53c79864e33f30060.exe (PID: 2684)
- 1BC4.tmp (PID: 2952)
- 1C61.tmp (PID: 948)
- 1D0D.tmp (PID: 304)
- 1DE7.tmp (PID: 2400)
- 1E64.tmp (PID: 1528)
- 1F2F.tmp (PID: 3076)
- 20E5.tmp (PID: 4036)
- 221D.tmp (PID: 3496)
- 227B.tmp (PID: 4008)
- 21CF.tmp (PID: 3000)
- 2337.tmp (PID: 4068)
- 2440.tmp (PID: 1872)
- 2598.tmp (PID: 3424)
- 2663.tmp (PID: 2584)
- 24FC.tmp (PID: 1496)
- 27AB.tmp (PID: 2888)
- 26E0.tmp (PID: 644)
- 28A5.tmp (PID: 1904)
- 28F3.tmp (PID: 2380)
- 2838.tmp (PID: 968)
- 2A2C.tmp (PID: 3796)
- 2A7A.tmp (PID: 2972)
- 2980.tmp (PID: 3096)
- 2AD8.tmp (PID: 2140)
- 2B64.tmp (PID: 1460)
- 2C3F.tmp (PID: 2440)
- 2BD2.tmp (PID: 2156)
- 2D2A.tmp (PID: 1848)
- 2D87.tmp (PID: 3396)
- 2C8D.tmp (PID: 3040)
- 2E24.tmp (PID: 2976)
- 2E91.tmp (PID: 2868)
- 2F5C.tmp (PID: 3344)
- 2F9B.tmp (PID: 3276)
- 2EEF.tmp (PID: 3348)
- 3037.tmp (PID: 3880)
- 30A4.tmp (PID: 2084)
- 31BD.tmp (PID: 3864)
- 322B.tmp (PID: 4016)
- 32F6.tmp (PID: 3408)
- 3373.tmp (PID: 3724)
- 3538.tmp (PID: 3924)
- 35E4.tmp (PID: 3524)
- 3661.tmp (PID: 1804)
- 377A.tmp (PID: 2052)
- 3A0A.tmp (PID: 1696)
- 3845.tmp (PID: 2292)
- 3B24.tmp (PID: 2392)
- 3B91.tmp (PID: 3540)
- 3A87.tmp (PID: 3608)
- 3BFE.tmp (PID: 1528)
- 3D37.tmp (PID: 2072)
- 3DF2.tmp (PID: 3936)
- 3E41.tmp (PID: 3016)
- 3F2B.tmp (PID: 1868)
- 3F79.tmp (PID: 3728)
- 3FC7.tmp (PID: 3584)
- 4015.tmp (PID: 2760)
- 4073.tmp (PID: 1496)
- 40B2.tmp (PID: 3424)
- 412F.tmp (PID: 2584)
- 418C.tmp (PID: 2456)
- 4248.tmp (PID: 968)
- 42D4.tmp (PID: 1904)
- 41DA.tmp (PID: 2888)
- 43A0.tmp (PID: 3096)
- 4342.tmp (PID: 2380)
- 43FD.tmp (PID: 2436)
- 445B.tmp (PID: 2972)
- 4536.tmp (PID: 1460)
- 449A.tmp (PID: 2140)
- 4584.tmp (PID: 536)
- 45D2.tmp (PID: 1996)
- 4611.tmp (PID: 1968)
- 466E.tmp (PID: 3808)
- 46DC.tmp (PID: 2540)
- 4739.tmp (PID: 1900)
- 4788.tmp (PID: 1420)
- 47F5.tmp (PID: 2860)
- 48A1.tmp (PID: 3680)
- 4843.tmp (PID: 3832)
- 48EF.tmp (PID: 2536)
- 491E.tmp (PID: 2492)
- 49AA.tmp (PID: 2368)
- 49F9.tmp (PID: 3756)
- 497C.tmp (PID: 3864)
- 4A47.tmp (PID: 2128)
- 4AB4.tmp (PID: 1032)
- 4B7F.tmp (PID: 552)
- 4C4A.tmp (PID: 2552)
- 4B12.tmp (PID: 1816)
- 4CD7.tmp (PID: 3328)
- 4D35.tmp (PID: 1588)
- 4DA2.tmp (PID: 3816)
- 4E00.tmp (PID: 2348)
- 4E5E.tmp (PID: 3824)
- 4EDB.tmp (PID: 3616)
- 4F58.tmp (PID: 788)
- 4F96.tmp (PID: 2052)
- 50AF.tmp (PID: 2932)
- 52A3.tmp (PID: 3876)
- 5003.tmp (PID: 3340)
- 5311.tmp (PID: 1636)
- 536E.tmp (PID: 752)
- 53BD.tmp (PID: 3668)
- 54C6.tmp (PID: 2964)
- 5468.tmp (PID: 3204)
- 5514.tmp (PID: 2236)
- 5562.tmp (PID: 3000)
- 55C0.tmp (PID: 3172)
- 561E.tmp (PID: 2100)
- 567C.tmp (PID: 2904)
- 5708.tmp (PID: 3684)
- 5766.tmp (PID: 3268)
- 56BA.tmp (PID: 1984)
- 5841.tmp (PID: 3424)
- 57D3.tmp (PID: 1496)
- 590C.tmp (PID: 1872)
- 589F.tmp (PID: 3812)
- 5A44.tmp (PID: 2456)
- 5AB2.tmp (PID: 2888)
- 5B00.tmp (PID: 968)
- 5B5E.tmp (PID: 2944)
- 5BFA.tmp (PID: 3096)
- 5BAC.tmp (PID: 2792)
- 5C96.tmp (PID: 2972)
- 5CE4.tmp (PID: 2140)
- 5C48.tmp (PID: 2436)
- 5DBF.tmp (PID: 536)
- 5E0D.tmp (PID: 2624)
- 5D61.tmp (PID: 2784)
- 5E5B.tmp (PID: 2440)
- 5EC9.tmp (PID: 2468)
- 5F17.tmp (PID: 2092)
- 5FA3.tmp (PID: 2976)
- 6011.tmp (PID: 2868)
- 60DC.tmp (PID: 2404)
- 607E.tmp (PID: 944)
- 612A.tmp (PID: 1360)
- 61D6.tmp (PID: 3276)
- 6224.tmp (PID: 3680)
- 6197.tmp (PID: 2776)
- 6272.tmp (PID: 1556)
- 62EF.tmp (PID: 4080)
- 635D.tmp (PID: 3092)
- 639B.tmp (PID: 3408)
- 6447.tmp (PID: 2368)
- 6495.tmp (PID: 1808)
- 63E9.tmp (PID: 2096)
- 64E3.tmp (PID: 2128)
- 659F.tmp (PID: 3524)
- 6541.tmp (PID: 2900)
- 67B2.tmp (PID: 124)
- 66D7.tmp (PID: 3320)
- 689C.tmp (PID: 4004)
- 683F.tmp (PID: 3112)
- 6948.tmp (PID: 2344)
- 6996.tmp (PID: 1932)
- 68FA.tmp (PID: 1884)
- 6A71.tmp (PID: 3100)
- 6ADE.tmp (PID: 3216)
- 6A04.tmp (PID: 3824)
- 6B6B.tmp (PID: 788)
- 6BE8.tmp (PID: 2052)
- 6C36.tmp (PID: 1296)
- 6CB3.tmp (PID: 3516)
- 6D8E.tmp (PID: 3360)
- 6E0B.tmp (PID: 3540)
- 6D30.tmp (PID: 2608)
- 6E59.tmp (PID: 1528)
- 6F53.tmp (PID: 3676)
- 6E98.tmp (PID: 2520)
- 6FEF.tmp (PID: 1016)
- 706C.tmp (PID: 3000)
- 7128.tmp (PID: 3728)
- 7186.tmp (PID: 3744)
- 71E3.tmp (PID: 4064)
- 7260.tmp (PID: 3684)
- 73C8.tmp (PID: 3268)
- 7464.tmp (PID: 1496)
- 7510.tmp (PID: 3424)
- 757D.tmp (PID: 3812)
- 75DB.tmp (PID: 1872)
- 7648.tmp (PID: 2456)
- 7696.tmp (PID: 2888)
- 7704.tmp (PID: 968)
- 7781.tmp (PID: 1492)
- 787B.tmp (PID: 3920)
- 77EE.tmp (PID: 2792)
- 783C.tmp (PID: 3096)
- 78B9.tmp (PID: 2672)
- 7907.tmp (PID: 844)
- 79C3.tmp (PID: 300)
- 7A11.tmp (PID: 1432)
- 7965.tmp (PID: 2884)
- 7AFB.tmp (PID: 3396)
- 7B98.tmp (PID: 3856)
- 7A5F.tmp (PID: 1848)
- 7CE0.tmp (PID: 3536)
- 7D2E.tmp (PID: 1208)
- 7DBB.tmp (PID: 3348)
- 7DF9.tmp (PID: 3208)
- 7D7C.tmp (PID: 1420)
- 7E57.tmp (PID: 2956)
- 7EB5.tmp (PID: 3832)
- 7FCE.tmp (PID: 3080)
- 804B.tmp (PID: 2084)
- 7F41.tmp (PID: 2620)
Changes the autorun value in the registry
- ZaccMoMY.exe (PID: 3140)
UAC/LUA settings modification
- 779297.exe (PID: 2924)
Changes firewall settings
- 779297.exe (PID: 2924)
Creates or modifies Windows services
- 779297.exe (PID: 2924)
Create files in the Startup directory
- 779297.exe (PID: 2924)
Creates a writable file in the system directory
- 779297.exe (PID: 2924)
Changes the login/logoff helper path in the registry
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- 12e89420d487205e997bbd25011d45fa.exe (PID: 2392)
Changes image file execution options
- 779297.exe (PID: 2924)
Deletes the SafeBoot registry key
- 779297.exe (PID: 2924)
Changes appearance of the Explorer extensions
- 779297.exe (PID: 2924)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
Actions looks like stealing of personal data
- 779297.exe (PID: 2924)
- 127277c0097cef5ce18f0002a2456f84.exe (PID: 3784)
- ZaccMoMY.exe (PID: 3140)
Connects to the CnC server
- 127277c0097cef5ce18f0002a2456f84.exe (PID: 3784)
Probably malicious OneNote attachment is found
- ZaccMoMY.exe (PID: 3140)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3060)
- a20a8faa583635241f71dbed54116e37.exe (PID: 2292)
- F8DB.tmp (PID: 2300)
- F996.tmp (PID: 3964)
- 127277c0097cef5ce18f0002a2456f84.exe (PID: 3784)
- FA52.tmp (PID: 3388)
- FADF.tmp (PID: 2536)
- FB7B.tmp (PID: 3092)
- FBD9.tmp (PID: 3972)
- FCA4.tmp (PID: 3408)
- FD01.tmp (PID: 3652)
- FDEC.tmp (PID: 3724)
- FD7E.tmp (PID: 3124)
- FEA7.tmp (PID: 2128)
- FFFF.tmp (PID: 3400)
- FFA1.tmp (PID: 3356)
- FF05.tmp (PID: 3336)
- 5D.tmp (PID: 2368)
- CA.tmp (PID: 2092)
- 128.tmp (PID: 1436)
- 29F.tmp (PID: 1032)
- 32C.tmp (PID: 3524)
- 1B5.tmp (PID: 1808)
- 3E7.tmp (PID: 1816)
- 464.tmp (PID: 4052)
- 53F.tmp (PID: 3748)
- 5CB.tmp (PID: 552)
- 658.tmp (PID: 2052)
- 733.tmp (PID: 2232)
- 86B.tmp (PID: 824)
- 8F8.tmp (PID: 1008)
- 975.tmp (PID: 2776)
- A40.tmp (PID: 2648)
- AAD.tmp (PID: 3980)
- BC7.tmp (PID: 1924)
- D2E.tmp (PID: 2920)
- C53.tmp (PID: 2196)
- DF9.tmp (PID: 2532)
- E86.tmp (PID: 3216)
- F03.tmp (PID: 1696)
- F9F.tmp (PID: 2896)
- 101C.tmp (PID: 3340)
- 10F7.tmp (PID: 3608)
- 107A.tmp (PID: 2820)
- 11B2.tmp (PID: 2932)
- 1164.tmp (PID: 1296)
- 12AC.tmp (PID: 2608)
- 122F.tmp (PID: 3516)
- 150E.tmp (PID: 3192)
- 158B.tmp (PID: 3876)
- 16D3.tmp (PID: 284)
- 15F8.tmp (PID: 3540)
- 1750.tmp (PID: 752)
- 1656.tmp (PID: 2316)
- 1905.tmp (PID: 528)
- 17CD.tmp (PID: 1508)
- 1A7C.tmp (PID: 2040)
- 19E0.tmp (PID: 2676)
- 1BC4.tmp (PID: 2952)
- 1C61.tmp (PID: 948)
- 1E64.tmp (PID: 1528)
- 1D0D.tmp (PID: 304)
- 1DE7.tmp (PID: 2400)
- 1F2F.tmp (PID: 3076)
- 20E5.tmp (PID: 4036)
- 21CF.tmp (PID: 3000)
- 221D.tmp (PID: 3496)
- 227B.tmp (PID: 4008)
- 57aa30d6e6e29f4d34629179dcac75b7.exe (PID: 2384)
- 2337.tmp (PID: 4068)
- 2440.tmp (PID: 1872)
- 9c389a6cd41fe1c54c505115125ddce8.exe (PID: 2088)
- 2598.tmp (PID: 3424)
- 2663.tmp (PID: 2584)
- 24FC.tmp (PID: 1496)
- 2838.tmp (PID: 968)
- 26E0.tmp (PID: 644)
- 27AB.tmp (PID: 2888)
- 28A5.tmp (PID: 1904)
- 28F3.tmp (PID: 2380)
- 2980.tmp (PID: 3096)
- 2A2C.tmp (PID: 3796)
- 2A7A.tmp (PID: 2972)
- 2B64.tmp (PID: 1460)
- 2AD8.tmp (PID: 2140)
- 2BD2.tmp (PID: 2156)
- 2C3F.tmp (PID: 2440)
- 2C8D.tmp (PID: 3040)
- 2D2A.tmp (PID: 1848)
- 2D87.tmp (PID: 3396)
- 2E91.tmp (PID: 2868)
- 2E24.tmp (PID: 2976)
- 2EEF.tmp (PID: 3348)
- 2F5C.tmp (PID: 3344)
- 2F9B.tmp (PID: 3276)
- 3037.tmp (PID: 3880)
- 30A4.tmp (PID: 2084)
- 31BD.tmp (PID: 3864)
- 322B.tmp (PID: 4016)
- 32F6.tmp (PID: 3408)
- 3373.tmp (PID: 3724)
- 3538.tmp (PID: 3924)
- 35E4.tmp (PID: 3524)
- 3661.tmp (PID: 1804)
- 377A.tmp (PID: 2052)
- 3845.tmp (PID: 2292)
- 3A0A.tmp (PID: 1696)
- 3B24.tmp (PID: 2392)
- 3B91.tmp (PID: 3540)
- 3A87.tmp (PID: 3608)
- 3BFE.tmp (PID: 1528)
- 3D37.tmp (PID: 2072)
- 3E41.tmp (PID: 3016)
- 3F2B.tmp (PID: 1868)
- 3DF2.tmp (PID: 3936)
- 3FC7.tmp (PID: 3584)
- 3F79.tmp (PID: 3728)
- 4015.tmp (PID: 2760)
- 4073.tmp (PID: 1496)
- 40B2.tmp (PID: 3424)
- 418C.tmp (PID: 2456)
- 412F.tmp (PID: 2584)
- 41DA.tmp (PID: 2888)
- 4248.tmp (PID: 968)
- 4342.tmp (PID: 2380)
- 43A0.tmp (PID: 3096)
- 42D4.tmp (PID: 1904)
- 43FD.tmp (PID: 2436)
- 445B.tmp (PID: 2972)
- 4536.tmp (PID: 1460)
- 449A.tmp (PID: 2140)
- 45D2.tmp (PID: 1996)
- 4584.tmp (PID: 536)
- 4611.tmp (PID: 1968)
- 466E.tmp (PID: 3808)
- 4739.tmp (PID: 1900)
- 4788.tmp (PID: 1420)
- 46DC.tmp (PID: 2540)
- 47F5.tmp (PID: 2860)
- 4843.tmp (PID: 3832)
- 48A1.tmp (PID: 3680)
- 48EF.tmp (PID: 2536)
- 491E.tmp (PID: 2492)
- 497C.tmp (PID: 3864)
- 49AA.tmp (PID: 2368)
- 49F9.tmp (PID: 3756)
- 4A47.tmp (PID: 2128)
- 4AB4.tmp (PID: 1032)
- 4B7F.tmp (PID: 552)
- 4C4A.tmp (PID: 2552)
- 4B12.tmp (PID: 1816)
- 4CD7.tmp (PID: 3328)
- 4DA2.tmp (PID: 3816)
- 4D35.tmp (PID: 1588)
- 4E00.tmp (PID: 2348)
- 4E5E.tmp (PID: 3824)
- 4EDB.tmp (PID: 3616)
- 4F96.tmp (PID: 2052)
- 4F58.tmp (PID: 788)
- 5003.tmp (PID: 3340)
- 50AF.tmp (PID: 2932)
- 52A3.tmp (PID: 3876)
- 5311.tmp (PID: 1636)
- 536E.tmp (PID: 752)
- 53BD.tmp (PID: 3668)
- 5468.tmp (PID: 3204)
- 54C6.tmp (PID: 2964)
- 5514.tmp (PID: 2236)
- 5562.tmp (PID: 3000)
- 55C0.tmp (PID: 3172)
- 561E.tmp (PID: 2100)
- 567C.tmp (PID: 2904)
- 5766.tmp (PID: 3268)
- 56BA.tmp (PID: 1984)
- 5708.tmp (PID: 3684)
- 5841.tmp (PID: 3424)
- 57D3.tmp (PID: 1496)
- 590C.tmp (PID: 1872)
- 5A44.tmp (PID: 2456)
- 589F.tmp (PID: 3812)
- 5AB2.tmp (PID: 2888)
- 5B5E.tmp (PID: 2944)
- 5B00.tmp (PID: 968)
- 5BFA.tmp (PID: 3096)
- 5BAC.tmp (PID: 2792)
- 5C96.tmp (PID: 2972)
- 5CE4.tmp (PID: 2140)
- 5C48.tmp (PID: 2436)
- 5DBF.tmp (PID: 536)
- 5E0D.tmp (PID: 2624)
- 5D61.tmp (PID: 2784)
- 5E5B.tmp (PID: 2440)
- 5EC9.tmp (PID: 2468)
- 5F17.tmp (PID: 2092)
- 5FA3.tmp (PID: 2976)
- 6011.tmp (PID: 2868)
- 60DC.tmp (PID: 2404)
- 612A.tmp (PID: 1360)
- 607E.tmp (PID: 944)
- 61D6.tmp (PID: 3276)
- 6197.tmp (PID: 2776)
- 6272.tmp (PID: 1556)
- 62EF.tmp (PID: 4080)
- 6224.tmp (PID: 3680)
- 635D.tmp (PID: 3092)
- 639B.tmp (PID: 3408)
- 6447.tmp (PID: 2368)
- 6495.tmp (PID: 1808)
- 63E9.tmp (PID: 2096)
- 6541.tmp (PID: 2900)
- 659F.tmp (PID: 3524)
- 64E3.tmp (PID: 2128)
- 66D7.tmp (PID: 3320)
- 67B2.tmp (PID: 124)
- 689C.tmp (PID: 4004)
- 683F.tmp (PID: 3112)
- 6948.tmp (PID: 2344)
- 6996.tmp (PID: 1932)
- 68FA.tmp (PID: 1884)
- 6A71.tmp (PID: 3100)
- 6ADE.tmp (PID: 3216)
- 6A04.tmp (PID: 3824)
- 6B6B.tmp (PID: 788)
- 6BE8.tmp (PID: 2052)
- 6CB3.tmp (PID: 3516)
- 6C36.tmp (PID: 1296)
- 6D8E.tmp (PID: 3360)
- 6D30.tmp (PID: 2608)
- 6E0B.tmp (PID: 3540)
- 6E59.tmp (PID: 1528)
- 6E98.tmp (PID: 2520)
- 6F53.tmp (PID: 3676)
- 6FEF.tmp (PID: 1016)
- 706C.tmp (PID: 3000)
- 7128.tmp (PID: 3728)
- 7186.tmp (PID: 3744)
- 71E3.tmp (PID: 4064)
- 7260.tmp (PID: 3684)
- 73C8.tmp (PID: 3268)
- 7464.tmp (PID: 1496)
- 75DB.tmp (PID: 1872)
- 7510.tmp (PID: 3424)
- 757D.tmp (PID: 3812)
- 7648.tmp (PID: 2456)
- 7696.tmp (PID: 2888)
- 7704.tmp (PID: 968)
- 7781.tmp (PID: 1492)
- 787B.tmp (PID: 3920)
- 77EE.tmp (PID: 2792)
- 783C.tmp (PID: 3096)
- 78B9.tmp (PID: 2672)
- 7907.tmp (PID: 844)
- 7A11.tmp (PID: 1432)
- 7965.tmp (PID: 2884)
- 79C3.tmp (PID: 300)
- 7A5F.tmp (PID: 1848)
- 7B98.tmp (PID: 3856)
- 7AFB.tmp (PID: 3396)
- 7D2E.tmp (PID: 1208)
- 7CE0.tmp (PID: 3536)
- 7DBB.tmp (PID: 3348)
- 7D7C.tmp (PID: 1420)
- 7E57.tmp (PID: 2956)
- 7EB5.tmp (PID: 3832)
- 7DF9.tmp (PID: 3208)
- 7FCE.tmp (PID: 3080)
- 804B.tmp (PID: 2084)
- 7F41.tmp (PID: 2620)
Reads the Windows owner or organization settings
- 545211f79941424f26866b9f00ad361b.exe (PID: 3676)
Starts itself from another location
- a20a8faa583635241f71dbed54116e37.exe (PID: 2292)
- b305344f8ef568505c2d78ef9fa3840b.exe (PID: 2544)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- F8DB.tmp (PID: 2300)
- F996.tmp (PID: 3964)
- FA52.tmp (PID: 3388)
- FB7B.tmp (PID: 3092)
- FADF.tmp (PID: 2536)
- FBD9.tmp (PID: 3972)
- FCA4.tmp (PID: 3408)
- FD01.tmp (PID: 3652)
- FD7E.tmp (PID: 3124)
- 2a313ce479edd2ba234cd6c7975da5bf.exe (PID: 1608)
- FDEC.tmp (PID: 3724)
- FEA7.tmp (PID: 2128)
- FF05.tmp (PID: 3336)
- FFFF.tmp (PID: 3400)
- FFA1.tmp (PID: 3356)
- 5D.tmp (PID: 2368)
- CA.tmp (PID: 2092)
- 128.tmp (PID: 1436)
- 1B5.tmp (PID: 1808)
- 29F.tmp (PID: 1032)
- 32C.tmp (PID: 3524)
- 3E7.tmp (PID: 1816)
- 464.tmp (PID: 4052)
- 53F.tmp (PID: 3748)
- 5CB.tmp (PID: 552)
- 658.tmp (PID: 2052)
- 733.tmp (PID: 2232)
- 86B.tmp (PID: 824)
- 8F8.tmp (PID: 1008)
- 975.tmp (PID: 2776)
- 289c1a8a890a567f4f70235ced85f763.exe (PID: 2344)
- A40.tmp (PID: 2648)
- AAD.tmp (PID: 3980)
- BC7.tmp (PID: 1924)
- 4a184b64b838a4833419c76951f7eda4.exe (PID: 1820)
- C53.tmp (PID: 2196)
- D2E.tmp (PID: 2920)
- DF9.tmp (PID: 2532)
- E86.tmp (PID: 3216)
- F03.tmp (PID: 1696)
- F9F.tmp (PID: 2896)
- 101C.tmp (PID: 3340)
- 107A.tmp (PID: 2820)
- 10F7.tmp (PID: 3608)
- 11B2.tmp (PID: 2932)
- 1164.tmp (PID: 1296)
- 122F.tmp (PID: 3516)
- 12AC.tmp (PID: 2608)
- 158B.tmp (PID: 3876)
- 150E.tmp (PID: 3192)
- 1656.tmp (PID: 2316)
- 16D3.tmp (PID: 284)
- 15F8.tmp (PID: 3540)
- 1750.tmp (PID: 752)
- 17CD.tmp (PID: 1508)
- 1905.tmp (PID: 528)
- 1A7C.tmp (PID: 2040)
- 19E0.tmp (PID: 2676)
- 1BC4.tmp (PID: 2952)
- 1C61.tmp (PID: 948)
- 1DE7.tmp (PID: 2400)
- 1D0D.tmp (PID: 304)
- 1F2F.tmp (PID: 3076)
- 20E5.tmp (PID: 4036)
- 1E64.tmp (PID: 1528)
- 21CF.tmp (PID: 3000)
- 221D.tmp (PID: 3496)
- 227B.tmp (PID: 4008)
- 2337.tmp (PID: 4068)
- 2440.tmp (PID: 1872)
- 2598.tmp (PID: 3424)
- 2663.tmp (PID: 2584)
- 24FC.tmp (PID: 1496)
- 26E0.tmp (PID: 644)
- 27AB.tmp (PID: 2888)
- 2838.tmp (PID: 968)
- 28A5.tmp (PID: 1904)
- 28F3.tmp (PID: 2380)
- 2980.tmp (PID: 3096)
- 2A2C.tmp (PID: 3796)
- 2AD8.tmp (PID: 2140)
- 2B64.tmp (PID: 1460)
- 2A7A.tmp (PID: 2972)
- 2C3F.tmp (PID: 2440)
- 2BD2.tmp (PID: 2156)
- 2C8D.tmp (PID: 3040)
- 2D2A.tmp (PID: 1848)
- 2D87.tmp (PID: 3396)
- 2E24.tmp (PID: 2976)
- 2E91.tmp (PID: 2868)
- 2EEF.tmp (PID: 3348)
- 2F5C.tmp (PID: 3344)
- 2F9B.tmp (PID: 3276)
- 30A4.tmp (PID: 2084)
- 3037.tmp (PID: 3880)
- 31BD.tmp (PID: 3864)
- 322B.tmp (PID: 4016)
- 32F6.tmp (PID: 3408)
- 3538.tmp (PID: 3924)
- 3373.tmp (PID: 3724)
- 3661.tmp (PID: 1804)
- 377A.tmp (PID: 2052)
- 35E4.tmp (PID: 3524)
- 3845.tmp (PID: 2292)
- 3A0A.tmp (PID: 1696)
- 3A87.tmp (PID: 3608)
- 3B24.tmp (PID: 2392)
- 3BFE.tmp (PID: 1528)
- 3B91.tmp (PID: 3540)
- 3D37.tmp (PID: 2072)
- 3DF2.tmp (PID: 3936)
- 3E41.tmp (PID: 3016)
- 3F79.tmp (PID: 3728)
- 3FC7.tmp (PID: 3584)
- 3F2B.tmp (PID: 1868)
- 4073.tmp (PID: 1496)
- 4015.tmp (PID: 2760)
- 412F.tmp (PID: 2584)
- 418C.tmp (PID: 2456)
- 40B2.tmp (PID: 3424)
- 41DA.tmp (PID: 2888)
- 4248.tmp (PID: 968)
- 4342.tmp (PID: 2380)
- 43A0.tmp (PID: 3096)
- 42D4.tmp (PID: 1904)
- 43FD.tmp (PID: 2436)
- 445B.tmp (PID: 2972)
- 4536.tmp (PID: 1460)
- 449A.tmp (PID: 2140)
- 4584.tmp (PID: 536)
- 45D2.tmp (PID: 1996)
- 4611.tmp (PID: 1968)
- 466E.tmp (PID: 3808)
- 46DC.tmp (PID: 2540)
- 4739.tmp (PID: 1900)
- 4788.tmp (PID: 1420)
- 47F5.tmp (PID: 2860)
- 4843.tmp (PID: 3832)
- 48A1.tmp (PID: 3680)
- 48EF.tmp (PID: 2536)
- 491E.tmp (PID: 2492)
- 49AA.tmp (PID: 2368)
- 497C.tmp (PID: 3864)
- 49F9.tmp (PID: 3756)
- 4A47.tmp (PID: 2128)
- 4AB4.tmp (PID: 1032)
- 4B7F.tmp (PID: 552)
- 4C4A.tmp (PID: 2552)
- 4B12.tmp (PID: 1816)
- 4CD7.tmp (PID: 3328)
- 4DA2.tmp (PID: 3816)
- 4D35.tmp (PID: 1588)
- 4E00.tmp (PID: 2348)
- 4E5E.tmp (PID: 3824)
- 4F96.tmp (PID: 2052)
- 4EDB.tmp (PID: 3616)
- 4F58.tmp (PID: 788)
- 5003.tmp (PID: 3340)
- 50AF.tmp (PID: 2932)
- 5311.tmp (PID: 1636)
- 536E.tmp (PID: 752)
- 52A3.tmp (PID: 3876)
- 53BD.tmp (PID: 3668)
- 5468.tmp (PID: 3204)
- 54C6.tmp (PID: 2964)
- 5514.tmp (PID: 2236)
- 5562.tmp (PID: 3000)
- 561E.tmp (PID: 2100)
- 567C.tmp (PID: 2904)
- 55C0.tmp (PID: 3172)
- 56BA.tmp (PID: 1984)
- 5708.tmp (PID: 3684)
- 5766.tmp (PID: 3268)
- 57D3.tmp (PID: 1496)
- 5841.tmp (PID: 3424)
- 589F.tmp (PID: 3812)
- 590C.tmp (PID: 1872)
- 5A44.tmp (PID: 2456)
- 5AB2.tmp (PID: 2888)
- 5B00.tmp (PID: 968)
- 5B5E.tmp (PID: 2944)
- 5BAC.tmp (PID: 2792)
- 5BFA.tmp (PID: 3096)
- 5CE4.tmp (PID: 2140)
- 5C96.tmp (PID: 2972)
- 5C48.tmp (PID: 2436)
- 5D61.tmp (PID: 2784)
- 5DBF.tmp (PID: 536)
- 5E0D.tmp (PID: 2624)
- 5E5B.tmp (PID: 2440)
- 5EC9.tmp (PID: 2468)
- 5FA3.tmp (PID: 2976)
- 6011.tmp (PID: 2868)
- 5F17.tmp (PID: 2092)
- 607E.tmp (PID: 944)
- 60DC.tmp (PID: 2404)
- 6197.tmp (PID: 2776)
- 61D6.tmp (PID: 3276)
- 612A.tmp (PID: 1360)
- 6272.tmp (PID: 1556)
- 62EF.tmp (PID: 4080)
- 6224.tmp (PID: 3680)
- 635D.tmp (PID: 3092)
- 639B.tmp (PID: 3408)
- 6447.tmp (PID: 2368)
- 6495.tmp (PID: 1808)
- 63E9.tmp (PID: 2096)
- 64E3.tmp (PID: 2128)
- 6541.tmp (PID: 2900)
- 66D7.tmp (PID: 3320)
- 67B2.tmp (PID: 124)
- 659F.tmp (PID: 3524)
- 689C.tmp (PID: 4004)
- 68FA.tmp (PID: 1884)
- 683F.tmp (PID: 3112)
- 6948.tmp (PID: 2344)
- 6996.tmp (PID: 1932)
- 6ADE.tmp (PID: 3216)
- 6A71.tmp (PID: 3100)
- 6A04.tmp (PID: 3824)
- 6B6B.tmp (PID: 788)
- 6BE8.tmp (PID: 2052)
- 6CB3.tmp (PID: 3516)
- 6C36.tmp (PID: 1296)
- 6D8E.tmp (PID: 3360)
- 6D30.tmp (PID: 2608)
- 6E59.tmp (PID: 1528)
- 6E0B.tmp (PID: 3540)
- 6F53.tmp (PID: 3676)
- 6E98.tmp (PID: 2520)
- 6FEF.tmp (PID: 1016)
- 706C.tmp (PID: 3000)
- 7128.tmp (PID: 3728)
- 7186.tmp (PID: 3744)
- 71E3.tmp (PID: 4064)
- 7260.tmp (PID: 3684)
- 73C8.tmp (PID: 3268)
- 7464.tmp (PID: 1496)
- 757D.tmp (PID: 3812)
- 75DB.tmp (PID: 1872)
- 7510.tmp (PID: 3424)
- 7648.tmp (PID: 2456)
- 7696.tmp (PID: 2888)
- 7704.tmp (PID: 968)
- 7781.tmp (PID: 1492)
- 783C.tmp (PID: 3096)
- 77EE.tmp (PID: 2792)
- 78B9.tmp (PID: 2672)
- 7907.tmp (PID: 844)
- 787B.tmp (PID: 3920)
- 79C3.tmp (PID: 300)
- 7965.tmp (PID: 2884)
- 7A11.tmp (PID: 1432)
- 7A5F.tmp (PID: 1848)
- 7AFB.tmp (PID: 3396)
- 7CE0.tmp (PID: 3536)
- 7D2E.tmp (PID: 1208)
- 7B98.tmp (PID: 3856)
- 7D7C.tmp (PID: 1420)
- 7DBB.tmp (PID: 3348)
- 7EB5.tmp (PID: 3832)
- 7DF9.tmp (PID: 3208)
- 7E57.tmp (PID: 2956)
- 7F41.tmp (PID: 2620)
- 804B.tmp (PID: 2084)
- 7FCE.tmp (PID: 3080)
- 80E7.tmp (PID: 3520)
- 81A3.tmp (PID: 4080)
- 8200.tmp (PID: 3864)
- 824E.tmp (PID: 2096)
- 831A.tmp (PID: 2368)
- 8481.tmp (PID: 2128)
- 83C5.tmp (PID: 2736)
- 84DF.tmp (PID: 2900)
- 852D.tmp (PID: 1036)
- 858B.tmp (PID: 552)
- 85F8.tmp (PID: 2552)
- 8646.tmp (PID: 3164)
- 8694.tmp (PID: 1588)
- 86E2.tmp (PID: 3280)
- 876F.tmp (PID: 2472)
- 8721.tmp (PID: 1988)
- 87BD.tmp (PID: 3120)
- 880B.tmp (PID: 1248)
- 884A.tmp (PID: 2232)
- 8898.tmp (PID: 2292)
- 88E6.tmp (PID: 2896)
- 8973.tmp (PID: 3192)
- 8934.tmp (PID: 2840)
- 89E0.tmp (PID: 3876)
- 8B18.tmp (PID: 4036)
- 8BB5.tmp (PID: 2076)
- 8C22.tmp (PID: 1892)
- 8C70.tmp (PID: 3156)
- 8CCE.tmp (PID: 3936)
- 8D7A.tmp (PID: 3760)
- 8D2C.tmp (PID: 3556)
- 8F10.tmp (PID: 3160)
- 8DC8.tmp (PID: 2904)
- 8E64.tmp (PID: 4076)
- 8FCC.tmp (PID: 3248)
- 901A.tmp (PID: 2584)
- 8F8D.tmp (PID: 2892)
- 9104.tmp (PID: 1616)
- 9162.tmp (PID: 3020)
- 91C0.tmp (PID: 1888)
- 9077.tmp (PID: 4056)
- 925C.tmp (PID: 2116)
- 92F8.tmp (PID: 2380)
- 9365.tmp (PID: 1328)
- 93D3.tmp (PID: 732)
- 946F.tmp (PID: 2972)
- 94AE.tmp (PID: 1460)
- 950B.tmp (PID: 916)
- 9421.tmp (PID: 1212)
- 95B7.tmp (PID: 1244)
- 96A2.tmp (PID: 1432)
- 9559.tmp (PID: 2720)
- 97DA.tmp (PID: 3260)
- 973E.tmp (PID: 1848)
- 979C.tmp (PID: 2512)
- 9828.tmp (PID: 2460)
- 98D4.tmp (PID: 2860)
- 9913.tmp (PID: 1936)
- 9886.tmp (PID: 2868)
- 99BE.tmp (PID: 3388)
- 9A4B.tmp (PID: 2996)
- 9B07.tmp (PID: 884)
- 9BC2.tmp (PID: 1556)
- 9951.tmp (PID: 3232)
- 9C2F.tmp (PID: 3972)
- 9C7E.tmp (PID: 3520)
- 9CDB.tmp (PID: 4020)
- 9DB6.tmp (PID: 3724)
- 9E04.tmp (PID: 2368)
- 9E62.tmp (PID: 3620)
- 9D49.tmp (PID: 3756)
- 9EB0.tmp (PID: 664)
- 9F3D.tmp (PID: 1008)
- 9F8B.tmp (PID: 552)
- 9EFE.tmp (PID: 1804)
- 9FE9.tmp (PID: 2552)
- A037.tmp (PID: 3848)
- A085.tmp (PID: 1444)
- A18E.tmp (PID: 3012)
- A0D3.tmp (PID: 2344)
- A121.tmp (PID: 3104)
- A325.tmp (PID: 1696)
- A24A.tmp (PID: 3912)
- A2C7.tmp (PID: 2820)
- A373.tmp (PID: 2384)
- A4CB.tmp (PID: 3540)
- A41F.tmp (PID: 3516)
- A46D.tmp (PID: 1636)
- A557.tmp (PID: 1528)
- A5B5.tmp (PID: 2520)
- A632.tmp (PID: 3956)
- A69F.tmp (PID: 2912)
- A6FD.tmp (PID: 3000)
- A3C1.tmp (PID: 2932)
- A799.tmp (PID: 3744)
- A7E7.tmp (PID: 1984)
- A855.tmp (PID: 3684)
- A8B3.tmp (PID: 3732)
- A9BC.tmp (PID: 1668)
- A8F1.tmp (PID: 2500)
- A94F.tmp (PID: 644)
- AA58.tmp (PID: 984)
- A75B.tmp (PID: 3728)
- AB04.tmp (PID: 2888)
- ABEF.tmp (PID: 3796)
- AB52.tmp (PID: 968)
- ABA1.tmp (PID: 2116)
- AC9B.tmp (PID: 732)
- ACE9.tmp (PID: 2940)
- AD46.tmp (PID: 844)
- AAB6.tmp (PID: 1448)
- AC3D.tmp (PID: 1328)
- AEEC.tmp (PID: 1968)
- AF2B.tmp (PID: 1244)
- AF89.tmp (PID: 1432)
- AFE6.tmp (PID: 3808)
- B092.tmp (PID: 1900)
- B044.tmp (PID: 3856)
- ADF2.tmp (PID: 2884)
- AE8F.tmp (PID: 300)
- B19C.tmp (PID: 2860)
- B219.tmp (PID: 1936)
- B267.tmp (PID: 3232)
- B303.tmp (PID: 2996)
- B2A5.tmp (PID: 3388)
- B3AF.tmp (PID: 1556)
- B371.tmp (PID: 884)
- B14E.tmp (PID: 2868)
- B0E0.tmp (PID: 2976)
- B45B.tmp (PID: 3520)
- B4A9.tmp (PID: 4020)
- B4F7.tmp (PID: 3756)
- B555.tmp (PID: 3724)
- B5F1.tmp (PID: 3620)
- B5B3.tmp (PID: 2368)
- B64F.tmp (PID: 664)
- B68D.tmp (PID: 1036)
- B6EB.tmp (PID: 1008)
- B3FD.tmp (PID: 3972)
- B739.tmp (PID: 552)
- B787.tmp (PID: 2552)
- B7D6.tmp (PID: 3848)
- B843.tmp (PID: 1444)
- B8A1.tmp (PID: 1736)
- B8FE.tmp (PID: 3104)
- B96C.tmp (PID: 3012)
- BA37.tmp (PID: 2820)
- BCA8.tmp (PID: 1636)
- BE6D.tmp (PID: 3956)
- BC4A.tmp (PID: 3516)
- BCF6.tmp (PID: 3540)
- BDD1.tmp (PID: 1528)
- BECB.tmp (PID: 2912)
- BE2F.tmp (PID: 2520)
- BA85.tmp (PID: 1696)
- BB9E.tmp (PID: 2384)
- B9E9.tmp (PID: 3912)
- BBFC.tmp (PID: 2932)
- BF19.tmp (PID: 3000)
- BF86.tmp (PID: 3728)
- BFE4.tmp (PID: 3744)
- C0DE.tmp (PID: 3732)
- C12C.tmp (PID: 2500)
- C080.tmp (PID: 3684)
- C19A.tmp (PID: 644)
- C032.tmp (PID: 1984)
- C265.tmp (PID: 984)
- C2F1.tmp (PID: 2888)
- C294.tmp (PID: 1448)
- C33F.tmp (PID: 968)
- C38E.tmp (PID: 2116)
- C3DC.tmp (PID: 3796)
- C41A.tmp (PID: 1328)
- C468.tmp (PID: 3148)
- C1F7.tmp (PID: 1668)
- C582.tmp (PID: 2464)
- C5DF.tmp (PID: 3804)
- C61E.tmp (PID: 1784)
- C66C.tmp (PID: 1996)
- C718.tmp (PID: 3444)
- C6CA.tmp (PID: 2020)
- C776.tmp (PID: 3396)
- C4B6.tmp (PID: 2672)
- C543.tmp (PID: 2156)
- C8BE.tmp (PID: 3272)
- C812.tmp (PID: 2512)
- C979.tmp (PID: 2332)
- C860.tmp (PID: 1208)
- C91B.tmp (PID: 944)
- CA06.tmp (PID: 1756)
- C9C7.tmp (PID: 2956)
- C7C4.tmp (PID: 2540)
- CB4E.tmp (PID: 3492)
- CB00.tmp (PID: 2084)
- CB9C.tmp (PID: 3092)
- CBEA.tmp (PID: 3312)
- CC48.tmp (PID: 3768)
- CCC5.tmp (PID: 2804)
- CA44.tmp (PID: 3276)
- CAA2.tmp (PID: 3404)
- CDDE.tmp (PID: 2368)
- CE2C.tmp (PID: 3620)
- CF26.tmp (PID: 3164)
- CE8A.tmp (PID: 296)
- CED8.tmp (PID: 124)
- CF65.tmp (PID: 2552)
- CFB3.tmp (PID: 3848)
- CD52.tmp (PID: 2736)
- CD90.tmp (PID: 3748)
- D0CC.tmp (PID: 3104)
- D159.tmp (PID: 3912)
- D1A7.tmp (PID: 3340)
- D1E5.tmp (PID: 1696)
- D291.tmp (PID: 2400)
- D2DF.tmp (PID: 3516)
- CFF1.tmp (PID: 1444)
- D040.tmp (PID: 1736)
- D10B.tmp (PID: 3012)
- D243.tmp (PID: 2384)
- D32E.tmp (PID: 1636)
- D36C.tmp (PID: 3668)
- D3D9.tmp (PID: 1528)
- D4A5.tmp (PID: 4008)
- D428.tmp (PID: 2520)
- D476.tmp (PID: 3508)
- D4F3.tmp (PID: 2904)
- D550.tmp (PID: 3584)
- D6D7.tmp (PID: 3812)
- D735.tmp (PID: 3460)
- D7E1.tmp (PID: 3940)
- D783.tmp (PID: 1760)
- D83E.tmp (PID: 1752)
- D8CB.tmp (PID: 2948)
- D58F.tmp (PID: 3160)
- D5CD.tmp (PID: 1496)
- D62B.tmp (PID: 2892)
- D679.tmp (PID: 292)
- D919.tmp (PID: 1492)
- DA61.tmp (PID: 2436)
- D958.tmp (PID: 128)
- D9B5.tmp (PID: 3096)
- DB5B.tmp (PID: 844)
- DA04.tmp (PID: 3304)
- DABF.tmp (PID: 3920)
- DB0D.tmp (PID: 2940)
- DD01.tmp (PID: 3780)
- DD4F.tmp (PID: 2440)
- DD8E.tmp (PID: 988)
- DDDC.tmp (PID: 2092)
- DE2A.tmp (PID: 1416)
- DE88.tmp (PID: 3980)
- DEC6.tmp (PID: 3348)
- DBA9.tmp (PID: 2720)
- DBF8.tmp (PID: 300)
- DC94.tmp (PID: 1968)
- E1A5.tmp (PID: 3520)
- DF91.tmp (PID: 1360)
- DFEF.tmp (PID: 2776)
- E05D.tmp (PID: 2996)
- E0BA.tmp (PID: 3964)
- E118.tmp (PID: 1556)
- E157.tmp (PID: 3492)
- DF05.tmp (PID: 3208)
- DF43.tmp (PID: 1936)
- E2CE.tmp (PID: 2736)
- E241.tmp (PID: 3768)
- E28F.tmp (PID: 2804)
- E3A8.tmp (PID: 3620)
- E31C.tmp (PID: 3748)
- E36A.tmp (PID: 2368)
- E3E7.tmp (PID: 296)
- E1F3.tmp (PID: 3052)
- E5EA.tmp (PID: 1884)
- E667.tmp (PID: 2344)
- E713.tmp (PID: 2648)
- E6C5.tmp (PID: 3120)
- E752.tmp (PID: 3216)
- E473.tmp (PID: 124)
- E58D.tmp (PID: 2300)
- E629.tmp (PID: 3848)
- E86B.tmp (PID: 2840)
- E8B9.tmp (PID: 3876)
- E955.tmp (PID: 752)
- E9C3.tmp (PID: 2076)
- EA11.tmp (PID: 3540)
- E7A0.tmp (PID: 2896)
- E81D.tmp (PID: 2820)
- E907.tmp (PID: 2608)
- ECEF.tmp (PID: 3596)
- EC92.tmp (PID: 2988)
- EB88.tmp (PID: 3656)
- ED3D.tmp (PID: 3248)
- ED8C.tmp (PID: 3424)
- EA5F.tmp (PID: 3676)
- EAAD.tmp (PID: 1016)
- EAEC.tmp (PID: 188)
- EB3A.tmp (PID: 3760)
- EC15.tmp (PID: 880)
- EE28.tmp (PID: 3844)
- EE76.tmp (PID: 1616)
- EEC4.tmp (PID: 1904)
- EF12.tmp (PID: 1448)
- EF70.tmp (PID: 2792)
- EDDA.tmp (PID: 4056)
- EFDD.tmp (PID: 1672)
- F21F.tmp (PID: 2464)
- F1C2.tmp (PID: 916)
- F25E.tmp (PID: 2624)
- F03B.tmp (PID: 1948)
- F089.tmp (PID: 2268)
- F0D7.tmp (PID: 3580)
- F125.tmp (PID: 2972)
- F174.tmp (PID: 1460)
- F481.tmp (PID: 3856)
- F3E5.tmp (PID: 1432)
- F433.tmp (PID: 3396)
- F4CF.tmp (PID: 3260)
- F51D.tmp (PID: 2976)
- F56B.tmp (PID: 3272)
- F2BC.tmp (PID: 1784)
- F2FA.tmp (PID: 3928)
- F358.tmp (PID: 348)
- F5B9.tmp (PID: 2444)
Starts application with an unusual extension
- b305344f8ef568505c2d78ef9fa3840b.exe (PID: 2544)
- a20a8faa583635241f71dbed54116e37.exe (PID: 2292)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- F8DB.tmp (PID: 2300)
- F996.tmp (PID: 3964)
- FA52.tmp (PID: 3388)
- FADF.tmp (PID: 2536)
- FB7B.tmp (PID: 3092)
- FCA4.tmp (PID: 3408)
- FD01.tmp (PID: 3652)
- FBD9.tmp (PID: 3972)
- FD7E.tmp (PID: 3124)
- FDEC.tmp (PID: 3724)
- FEA7.tmp (PID: 2128)
- FF05.tmp (PID: 3336)
- FFFF.tmp (PID: 3400)
- FFA1.tmp (PID: 3356)
- CA.tmp (PID: 2092)
- 5D.tmp (PID: 2368)
- 128.tmp (PID: 1436)
- 1B5.tmp (PID: 1808)
- 29F.tmp (PID: 1032)
- 32C.tmp (PID: 3524)
- 3E7.tmp (PID: 1816)
- 464.tmp (PID: 4052)
- 53F.tmp (PID: 3748)
- 5CB.tmp (PID: 552)
- 658.tmp (PID: 2052)
- 733.tmp (PID: 2232)
- 86B.tmp (PID: 824)
- 8F8.tmp (PID: 1008)
- 975.tmp (PID: 2776)
- A40.tmp (PID: 2648)
- AAD.tmp (PID: 3980)
- BC7.tmp (PID: 1924)
- C53.tmp (PID: 2196)
- D2E.tmp (PID: 2920)
- DF9.tmp (PID: 2532)
- E86.tmp (PID: 3216)
- F03.tmp (PID: 1696)
- F9F.tmp (PID: 2896)
- 101C.tmp (PID: 3340)
- 107A.tmp (PID: 2820)
- 10F7.tmp (PID: 3608)
- 1164.tmp (PID: 1296)
- 11B2.tmp (PID: 2932)
- 12AC.tmp (PID: 2608)
- 122F.tmp (PID: 3516)
- 150E.tmp (PID: 3192)
- 158B.tmp (PID: 3876)
- 15F8.tmp (PID: 3540)
- 1656.tmp (PID: 2316)
- 16D3.tmp (PID: 284)
- 17CD.tmp (PID: 1508)
- 1750.tmp (PID: 752)
- 1905.tmp (PID: 528)
- 19E0.tmp (PID: 2676)
- 1A7C.tmp (PID: 2040)
- 1BC4.tmp (PID: 2952)
- 1C61.tmp (PID: 948)
- 1DE7.tmp (PID: 2400)
- 1D0D.tmp (PID: 304)
- 1F2F.tmp (PID: 3076)
- 20E5.tmp (PID: 4036)
- 1E64.tmp (PID: 1528)
- 21CF.tmp (PID: 3000)
- 221D.tmp (PID: 3496)
- 227B.tmp (PID: 4008)
- 2337.tmp (PID: 4068)
- 2440.tmp (PID: 1872)
- 24FC.tmp (PID: 1496)
- 2598.tmp (PID: 3424)
- 26E0.tmp (PID: 644)
- 27AB.tmp (PID: 2888)
- 2663.tmp (PID: 2584)
- 28A5.tmp (PID: 1904)
- 28F3.tmp (PID: 2380)
- 2838.tmp (PID: 968)
- 2980.tmp (PID: 3096)
- 2A2C.tmp (PID: 3796)
- 2AD8.tmp (PID: 2140)
- 2B64.tmp (PID: 1460)
- 2A7A.tmp (PID: 2972)
- 2BD2.tmp (PID: 2156)
- 2C3F.tmp (PID: 2440)
- 2D2A.tmp (PID: 1848)
- 2D87.tmp (PID: 3396)
- 2C8D.tmp (PID: 3040)
- 2E24.tmp (PID: 2976)
- 2E91.tmp (PID: 2868)
- 2EEF.tmp (PID: 3348)
- 2F5C.tmp (PID: 3344)
- 2F9B.tmp (PID: 3276)
- 3037.tmp (PID: 3880)
- 30A4.tmp (PID: 2084)
- 31BD.tmp (PID: 3864)
- 322B.tmp (PID: 4016)
- 32F6.tmp (PID: 3408)
- 3373.tmp (PID: 3724)
- 3538.tmp (PID: 3924)
- 35E4.tmp (PID: 3524)
- 3661.tmp (PID: 1804)
- 377A.tmp (PID: 2052)
- 3A0A.tmp (PID: 1696)
- 3845.tmp (PID: 2292)
- 3B24.tmp (PID: 2392)
- 3A87.tmp (PID: 3608)
- 3BFE.tmp (PID: 1528)
- 3D37.tmp (PID: 2072)
- 3B91.tmp (PID: 3540)
- 3DF2.tmp (PID: 3936)
- 3E41.tmp (PID: 3016)
- 3F2B.tmp (PID: 1868)
- 3F79.tmp (PID: 3728)
- 3FC7.tmp (PID: 3584)
- 4073.tmp (PID: 1496)
- 4015.tmp (PID: 2760)
- 412F.tmp (PID: 2584)
- 418C.tmp (PID: 2456)
- 40B2.tmp (PID: 3424)
- 41DA.tmp (PID: 2888)
- 4248.tmp (PID: 968)
- 43A0.tmp (PID: 3096)
- 42D4.tmp (PID: 1904)
- 4342.tmp (PID: 2380)
- 445B.tmp (PID: 2972)
- 43FD.tmp (PID: 2436)
- 4536.tmp (PID: 1460)
- 449A.tmp (PID: 2140)
- 4584.tmp (PID: 536)
- 45D2.tmp (PID: 1996)
- 4611.tmp (PID: 1968)
- 466E.tmp (PID: 3808)
- 46DC.tmp (PID: 2540)
- 4739.tmp (PID: 1900)
- 4788.tmp (PID: 1420)
- 47F5.tmp (PID: 2860)
- 4843.tmp (PID: 3832)
- 48A1.tmp (PID: 3680)
- 48EF.tmp (PID: 2536)
- 491E.tmp (PID: 2492)
- 497C.tmp (PID: 3864)
- 49AA.tmp (PID: 2368)
- 49F9.tmp (PID: 3756)
- 4A47.tmp (PID: 2128)
- 4AB4.tmp (PID: 1032)
- 4B7F.tmp (PID: 552)
- 4C4A.tmp (PID: 2552)
- 4B12.tmp (PID: 1816)
- 4CD7.tmp (PID: 3328)
- 4D35.tmp (PID: 1588)
- 4DA2.tmp (PID: 3816)
- 4E00.tmp (PID: 2348)
- 4E5E.tmp (PID: 3824)
- 4F58.tmp (PID: 788)
- 4F96.tmp (PID: 2052)
- 4EDB.tmp (PID: 3616)
- 5003.tmp (PID: 3340)
- 50AF.tmp (PID: 2932)
- 5311.tmp (PID: 1636)
- 536E.tmp (PID: 752)
- 52A3.tmp (PID: 3876)
- 53BD.tmp (PID: 3668)
- 5468.tmp (PID: 3204)
- 54C6.tmp (PID: 2964)
- 5514.tmp (PID: 2236)
- 5562.tmp (PID: 3000)
- 55C0.tmp (PID: 3172)
- 567C.tmp (PID: 2904)
- 561E.tmp (PID: 2100)
- 5766.tmp (PID: 3268)
- 56BA.tmp (PID: 1984)
- 5708.tmp (PID: 3684)
- 57D3.tmp (PID: 1496)
- 5841.tmp (PID: 3424)
- 590C.tmp (PID: 1872)
- 5A44.tmp (PID: 2456)
- 589F.tmp (PID: 3812)
- 5B00.tmp (PID: 968)
- 5B5E.tmp (PID: 2944)
- 5AB2.tmp (PID: 2888)
- 5BAC.tmp (PID: 2792)
- 5BFA.tmp (PID: 3096)
- 5C48.tmp (PID: 2436)
- 5CE4.tmp (PID: 2140)
- 5C96.tmp (PID: 2972)
- 5D61.tmp (PID: 2784)
- 5DBF.tmp (PID: 536)
- 5E0D.tmp (PID: 2624)
- 5E5B.tmp (PID: 2440)
- 5EC9.tmp (PID: 2468)
- 5FA3.tmp (PID: 2976)
- 5F17.tmp (PID: 2092)
- 6011.tmp (PID: 2868)
- 607E.tmp (PID: 944)
- 60DC.tmp (PID: 2404)
- 6197.tmp (PID: 2776)
- 61D6.tmp (PID: 3276)
- 612A.tmp (PID: 1360)
- 6272.tmp (PID: 1556)
- 62EF.tmp (PID: 4080)
- 6224.tmp (PID: 3680)
- 635D.tmp (PID: 3092)
- 639B.tmp (PID: 3408)
- 6447.tmp (PID: 2368)
- 6495.tmp (PID: 1808)
- 63E9.tmp (PID: 2096)
- 64E3.tmp (PID: 2128)
- 6541.tmp (PID: 2900)
- 659F.tmp (PID: 3524)
- 66D7.tmp (PID: 3320)
- 67B2.tmp (PID: 124)
- 683F.tmp (PID: 3112)
- 68FA.tmp (PID: 1884)
- 689C.tmp (PID: 4004)
- 6996.tmp (PID: 1932)
- 6948.tmp (PID: 2344)
- 6A71.tmp (PID: 3100)
- 6ADE.tmp (PID: 3216)
- 6A04.tmp (PID: 3824)
- 6B6B.tmp (PID: 788)
- 6BE8.tmp (PID: 2052)
- 6CB3.tmp (PID: 3516)
- 6C36.tmp (PID: 1296)
- 6D30.tmp (PID: 2608)
- 6D8E.tmp (PID: 3360)
- 6E0B.tmp (PID: 3540)
- 6E59.tmp (PID: 1528)
- 6E98.tmp (PID: 2520)
- 6F53.tmp (PID: 3676)
- 6FEF.tmp (PID: 1016)
- 706C.tmp (PID: 3000)
- 7128.tmp (PID: 3728)
- 7186.tmp (PID: 3744)
- 71E3.tmp (PID: 4064)
- 7260.tmp (PID: 3684)
- 73C8.tmp (PID: 3268)
- 7464.tmp (PID: 1496)
- 757D.tmp (PID: 3812)
- 75DB.tmp (PID: 1872)
- 7510.tmp (PID: 3424)
- 7648.tmp (PID: 2456)
- 7696.tmp (PID: 2888)
- 7704.tmp (PID: 968)
- 7781.tmp (PID: 1492)
- 783C.tmp (PID: 3096)
- 77EE.tmp (PID: 2792)
- 78B9.tmp (PID: 2672)
- 7907.tmp (PID: 844)
- 787B.tmp (PID: 3920)
- 7965.tmp (PID: 2884)
- 79C3.tmp (PID: 300)
- 7A11.tmp (PID: 1432)
- 7A5F.tmp (PID: 1848)
- 7AFB.tmp (PID: 3396)
- 7CE0.tmp (PID: 3536)
- 7D2E.tmp (PID: 1208)
- 7B98.tmp (PID: 3856)
- 7D7C.tmp (PID: 1420)
- 7DBB.tmp (PID: 3348)
- 7EB5.tmp (PID: 3832)
- 7DF9.tmp (PID: 3208)
- 7E57.tmp (PID: 2956)
- 7F41.tmp (PID: 2620)
- 7FCE.tmp (PID: 3080)
- 804B.tmp (PID: 2084)
- 80E7.tmp (PID: 3520)
- 81A3.tmp (PID: 4080)
- 8200.tmp (PID: 3864)
- 824E.tmp (PID: 2096)
- 831A.tmp (PID: 2368)
- 83C5.tmp (PID: 2736)
- 8481.tmp (PID: 2128)
- 84DF.tmp (PID: 2900)
- 852D.tmp (PID: 1036)
- 858B.tmp (PID: 552)
- 85F8.tmp (PID: 2552)
- 8646.tmp (PID: 3164)
- 8694.tmp (PID: 1588)
- 86E2.tmp (PID: 3280)
- 8721.tmp (PID: 1988)
- 876F.tmp (PID: 2472)
- 884A.tmp (PID: 2232)
- 8898.tmp (PID: 2292)
- 87BD.tmp (PID: 3120)
- 880B.tmp (PID: 1248)
- 8934.tmp (PID: 2840)
- 8973.tmp (PID: 3192)
- 89E0.tmp (PID: 3876)
- 88E6.tmp (PID: 2896)
- 8BB5.tmp (PID: 2076)
- 8C22.tmp (PID: 1892)
- 8B18.tmp (PID: 4036)
- 8CCE.tmp (PID: 3936)
- 8D2C.tmp (PID: 3556)
- 8D7A.tmp (PID: 3760)
- 8C70.tmp (PID: 3156)
- 8F10.tmp (PID: 3160)
- 8E64.tmp (PID: 4076)
- 8DC8.tmp (PID: 2904)
- 8FCC.tmp (PID: 3248)
- 901A.tmp (PID: 2584)
- 9077.tmp (PID: 4056)
- 8F8D.tmp (PID: 2892)
- 9104.tmp (PID: 1616)
- 9162.tmp (PID: 3020)
- 91C0.tmp (PID: 1888)
- 9365.tmp (PID: 1328)
- 93D3.tmp (PID: 732)
- 925C.tmp (PID: 2116)
- 92F8.tmp (PID: 2380)
- 9421.tmp (PID: 1212)
- 946F.tmp (PID: 2972)
- 94AE.tmp (PID: 1460)
- 950B.tmp (PID: 916)
- 9559.tmp (PID: 2720)
- 95B7.tmp (PID: 1244)
- 973E.tmp (PID: 1848)
- 96A2.tmp (PID: 1432)
- 979C.tmp (PID: 2512)
- 97DA.tmp (PID: 3260)
- 9828.tmp (PID: 2460)
- 98D4.tmp (PID: 2860)
- 9951.tmp (PID: 3232)
- 9913.tmp (PID: 1936)
- 9886.tmp (PID: 2868)
- 99BE.tmp (PID: 3388)
- 9A4B.tmp (PID: 2996)
- 9B07.tmp (PID: 884)
- 9C2F.tmp (PID: 3972)
- 9C7E.tmp (PID: 3520)
- 9CDB.tmp (PID: 4020)
- 9DB6.tmp (PID: 3724)
- 9E04.tmp (PID: 2368)
- 9E62.tmp (PID: 3620)
- 9D49.tmp (PID: 3756)
- 9BC2.tmp (PID: 1556)
- 9EFE.tmp (PID: 1804)
- 9EB0.tmp (PID: 664)
- 9F3D.tmp (PID: 1008)
- 9FE9.tmp (PID: 2552)
- A085.tmp (PID: 1444)
- A037.tmp (PID: 3848)
- 9F8B.tmp (PID: 552)
- A24A.tmp (PID: 3912)
- A18E.tmp (PID: 3012)
- A121.tmp (PID: 3104)
- A2C7.tmp (PID: 2820)
- A325.tmp (PID: 1696)
- A373.tmp (PID: 2384)
- A0D3.tmp (PID: 2344)
- A46D.tmp (PID: 1636)
- A4CB.tmp (PID: 3540)
- A557.tmp (PID: 1528)
- A5B5.tmp (PID: 2520)
- A632.tmp (PID: 3956)
- A69F.tmp (PID: 2912)
- A6FD.tmp (PID: 3000)
- A3C1.tmp (PID: 2932)
- A41F.tmp (PID: 3516)
- A8B3.tmp (PID: 3732)
- A855.tmp (PID: 3684)
- A8F1.tmp (PID: 2500)
- A94F.tmp (PID: 644)
- A9BC.tmp (PID: 1668)
- AA58.tmp (PID: 984)
- AAB6.tmp (PID: 1448)
- A75B.tmp (PID: 3728)
- A799.tmp (PID: 3744)
- A7E7.tmp (PID: 1984)
- ABA1.tmp (PID: 2116)
- ABEF.tmp (PID: 3796)
- AC9B.tmp (PID: 732)
- ACE9.tmp (PID: 2940)
- AD46.tmp (PID: 844)
- AB04.tmp (PID: 2888)
- AB52.tmp (PID: 968)
- AC3D.tmp (PID: 1328)
- AE8F.tmp (PID: 300)
- AEEC.tmp (PID: 1968)
- B044.tmp (PID: 3856)
- AF2B.tmp (PID: 1244)
- AF89.tmp (PID: 1432)
- AFE6.tmp (PID: 3808)
- B092.tmp (PID: 1900)
- ADF2.tmp (PID: 2884)
- B267.tmp (PID: 3232)
- B219.tmp (PID: 1936)
- B2A5.tmp (PID: 3388)
- B303.tmp (PID: 2996)
- B371.tmp (PID: 884)
- B3AF.tmp (PID: 1556)
- B14E.tmp (PID: 2868)
- B19C.tmp (PID: 2860)
- B0E0.tmp (PID: 2976)
- B4A9.tmp (PID: 4020)
- B555.tmp (PID: 3724)
- B4F7.tmp (PID: 3756)
- B64F.tmp (PID: 664)
- B5B3.tmp (PID: 2368)
- B5F1.tmp (PID: 3620)
- B6EB.tmp (PID: 1008)
- B68D.tmp (PID: 1036)
- B3FD.tmp (PID: 3972)
- B45B.tmp (PID: 3520)
- B739.tmp (PID: 552)
- B787.tmp (PID: 2552)
- B7D6.tmp (PID: 3848)
- B8A1.tmp (PID: 1736)
- B843.tmp (PID: 1444)
- B8FE.tmp (PID: 3104)
- B96C.tmp (PID: 3012)
- B9E9.tmp (PID: 3912)
- BA37.tmp (PID: 2820)
- BB9E.tmp (PID: 2384)
- BBFC.tmp (PID: 2932)
- BCA8.tmp (PID: 1636)
- BC4A.tmp (PID: 3516)
- BDD1.tmp (PID: 1528)
- BCF6.tmp (PID: 3540)
- BE2F.tmp (PID: 2520)
- BE6D.tmp (PID: 3956)
- BA85.tmp (PID: 1696)
- BF19.tmp (PID: 3000)
- BF86.tmp (PID: 3728)
- C032.tmp (PID: 1984)
- C080.tmp (PID: 3684)
- C0DE.tmp (PID: 3732)
- C12C.tmp (PID: 2500)
- C19A.tmp (PID: 644)
- BECB.tmp (PID: 2912)
- BFE4.tmp (PID: 3744)
- C2F1.tmp (PID: 2888)
- C33F.tmp (PID: 968)
- C38E.tmp (PID: 2116)
- C3DC.tmp (PID: 3796)
- C41A.tmp (PID: 1328)
- C1F7.tmp (PID: 1668)
- C265.tmp (PID: 984)
- C294.tmp (PID: 1448)
- C582.tmp (PID: 2464)
- C543.tmp (PID: 2156)
- C718.tmp (PID: 3444)
- C66C.tmp (PID: 1996)
- C6CA.tmp (PID: 2020)
- C468.tmp (PID: 3148)
- C4B6.tmp (PID: 2672)
- C5DF.tmp (PID: 3804)
- C61E.tmp (PID: 1784)
- C8BE.tmp (PID: 3272)
- C812.tmp (PID: 2512)
- C860.tmp (PID: 1208)
- C91B.tmp (PID: 944)
- C979.tmp (PID: 2332)
- C9C7.tmp (PID: 2956)
- C776.tmp (PID: 3396)
- C7C4.tmp (PID: 2540)
- CAA2.tmp (PID: 3404)
- CB00.tmp (PID: 2084)
- CB4E.tmp (PID: 3492)
- CB9C.tmp (PID: 3092)
- CBEA.tmp (PID: 3312)
- CC48.tmp (PID: 3768)
- CCC5.tmp (PID: 2804)
- CD52.tmp (PID: 2736)
- CA06.tmp (PID: 1756)
- CA44.tmp (PID: 3276)
- CDDE.tmp (PID: 2368)
- CE2C.tmp (PID: 3620)
- CE8A.tmp (PID: 296)
- CED8.tmp (PID: 124)
- CF26.tmp (PID: 3164)
- CF65.tmp (PID: 2552)
- CFB3.tmp (PID: 3848)
- CFF1.tmp (PID: 1444)
- CD90.tmp (PID: 3748)
- D10B.tmp (PID: 3012)
- D159.tmp (PID: 3912)
- D1A7.tmp (PID: 3340)
- D1E5.tmp (PID: 1696)
- D243.tmp (PID: 2384)
- D2DF.tmp (PID: 3516)
- D291.tmp (PID: 2400)
- D040.tmp (PID: 1736)
- D0CC.tmp (PID: 3104)
- D36C.tmp (PID: 3668)
- D3D9.tmp (PID: 1528)
- D428.tmp (PID: 2520)
- D476.tmp (PID: 3508)
- D4A5.tmp (PID: 4008)
- D4F3.tmp (PID: 2904)
- D550.tmp (PID: 3584)
- D32E.tmp (PID: 1636)
- D62B.tmp (PID: 2892)
- D6D7.tmp (PID: 3812)
- D679.tmp (PID: 292)
- D735.tmp (PID: 3460)
- D7E1.tmp (PID: 3940)
- D8CB.tmp (PID: 2948)
- D58F.tmp (PID: 3160)
- D5CD.tmp (PID: 1496)
- D783.tmp (PID: 1760)
- D83E.tmp (PID: 1752)
- D919.tmp (PID: 1492)
- DA04.tmp (PID: 3304)
- D9B5.tmp (PID: 3096)
- DA61.tmp (PID: 2436)
- DABF.tmp (PID: 3920)
- DB0D.tmp (PID: 2940)
- DB5B.tmp (PID: 844)
- D958.tmp (PID: 128)
- DC94.tmp (PID: 1968)
- DD8E.tmp (PID: 988)
- DD4F.tmp (PID: 2440)
- DDDC.tmp (PID: 2092)
- DE2A.tmp (PID: 1416)
- DE88.tmp (PID: 3980)
- DBA9.tmp (PID: 2720)
- DBF8.tmp (PID: 300)
- DD01.tmp (PID: 3780)
- E118.tmp (PID: 1556)
- E0BA.tmp (PID: 3964)
- DF91.tmp (PID: 1360)
- E05D.tmp (PID: 2996)
- E157.tmp (PID: 3492)
- DEC6.tmp (PID: 3348)
- DF05.tmp (PID: 3208)
- DF43.tmp (PID: 1936)
- DFEF.tmp (PID: 2776)
- E241.tmp (PID: 3768)
- E28F.tmp (PID: 2804)
- E2CE.tmp (PID: 2736)
- E31C.tmp (PID: 3748)
- E1A5.tmp (PID: 3520)
- E1F3.tmp (PID: 3052)
- E36A.tmp (PID: 2368)
- E3A8.tmp (PID: 3620)
- E58D.tmp (PID: 2300)
- E5EA.tmp (PID: 1884)
- E667.tmp (PID: 2344)
- E629.tmp (PID: 3848)
- E6C5.tmp (PID: 3120)
- E713.tmp (PID: 2648)
- E752.tmp (PID: 3216)
- E3E7.tmp (PID: 296)
- E473.tmp (PID: 124)
- E86B.tmp (PID: 2840)
- E81D.tmp (PID: 2820)
- E955.tmp (PID: 752)
- E907.tmp (PID: 2608)
- E9C3.tmp (PID: 2076)
- EA11.tmp (PID: 3540)
- EA5F.tmp (PID: 3676)
- E7A0.tmp (PID: 2896)
- E8B9.tmp (PID: 3876)
- EAEC.tmp (PID: 188)
- EC92.tmp (PID: 2988)
- EB3A.tmp (PID: 3760)
- EC15.tmp (PID: 880)
- ECEF.tmp (PID: 3596)
- ED3D.tmp (PID: 3248)
- ED8C.tmp (PID: 3424)
- EAAD.tmp (PID: 1016)
- EB88.tmp (PID: 3656)
- EE76.tmp (PID: 1616)
- EFDD.tmp (PID: 1672)
- EF12.tmp (PID: 1448)
- EF70.tmp (PID: 2792)
- F03B.tmp (PID: 1948)
- EDDA.tmp (PID: 4056)
- EE28.tmp (PID: 3844)
- EEC4.tmp (PID: 1904)
- F174.tmp (PID: 1460)
- F1C2.tmp (PID: 916)
- F21F.tmp (PID: 2464)
- F25E.tmp (PID: 2624)
- F2BC.tmp (PID: 1784)
- F089.tmp (PID: 2268)
- F0D7.tmp (PID: 3580)
- F125.tmp (PID: 2972)
- F481.tmp (PID: 3856)
- F358.tmp (PID: 348)
- F3E5.tmp (PID: 1432)
- F433.tmp (PID: 3396)
- F51D.tmp (PID: 2976)
- F56B.tmp (PID: 3272)
- F2FA.tmp (PID: 3928)
- F4CF.tmp (PID: 3260)
- F5B9.tmp (PID: 2444)
Application launched itself
- 2a313ce479edd2ba234cd6c7975da5bf.exe (PID: 3832)
- 779297.exe (PID: 3088)
- 779297.exe (PID: 788)
Reads the Internet Settings
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- 2a313ce479edd2ba234cd6c7975da5bf.exe (PID: 1608)
- 779297.exe (PID: 2924)
- 4b543325cf0e11dee26d58cc1ac38cf5.exe (PID: 2500)
- budha.exe (PID: 3872)
- 4a184b64b838a4833419c76951f7eda4.exe (PID: 1820)
Reads Microsoft Outlook installation path
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- 779297.exe (PID: 2924)
Starts CMD.EXE for commands execution
- 226061fc8f29c47dbf807957e4c7edaa.exe (PID: 2084)
Uses REG/REGEDIT.EXE to modify registry
- 226061fc8f29c47dbf807957e4c7edaa.exe (PID: 2084)
The process creates files with name similar to system file names
- 779297.exe (PID: 2924)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
Creates files in the driver directory
- 779297.exe (PID: 2924)
Reads Internet Explorer settings
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- 779297.exe (PID: 2924)
Checks Windows Trust Settings
- s5534.exe (PID: 1556)
- budha.exe (PID: 3872)
Reads security settings of Internet Explorer
- s5534.exe (PID: 1556)
- budha.exe (PID: 3872)
Reads settings of System Certificates
- s5534.exe (PID: 1556)
- budha.exe (PID: 3872)
Changes the Home page of Internet Explorer
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- 779297.exe (PID: 2924)
Changes the title of the Internet Explorer window
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- 779297.exe (PID: 2924)
Connects to unusual port
- ykxim.exe (PID: 2524)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3060)
Manual execution by a user
- 127277c0097cef5ce18f0002a2456f84.exe (PID: 3784)
- 226061fc8f29c47dbf807957e4c7edaa.exe (PID: 2084)
- 545211f79941424f26866b9f00ad361b.exe (PID: 3676)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- 8191224f863e0d5287aafa7a08cdcdb3.exe (PID: 1352)
- a20a8faa583635241f71dbed54116e37.exe (PID: 2292)
- b305344f8ef568505c2d78ef9fa3840b.exe (PID: 2544)
- b7732333c67d9155ebe9c3a11f966143.exe (PID: 2332)
- 2a313ce479edd2ba234cd6c7975da5bf.exe (PID: 3832)
- b20c70a815c16a1ce1dc0e3335f462b7.exe (PID: 1036)
- 3a5a024582f9c0a6a08e5ff3b3e1ea7e.exe (PID: 2068)
- 4b543325cf0e11dee26d58cc1ac38cf5.exe (PID: 2500)
- 4a184b64b838a4833419c76951f7eda4.exe (PID: 1820)
- 6a609d65263f2c95ab44b534255b53c9.exe (PID: 1348)
- 9c389a6cd41fe1c54c505115125ddce8.exe (PID: 2088)
- 12e89420d487205e997bbd25011d45fa.exe (PID: 2392)
- 26a318ba688442470eb1f247da7d76c1.exe (PID: 3580)
- 57aa30d6e6e29f4d34629179dcac75b7.exe (PID: 2384)
- 33fe4259a21b93c20ef6a920b6311b8f.exe (PID: 3912)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- 289c1a8a890a567f4f70235ced85f763.exe (PID: 2344)
- 786c8cf775b2e5c53c79864e33f30060.exe (PID: 2684)
- 6699cf459391b430d49cbc80b2722bee.exe (PID: 2460)
- wmpnscfg.exe (PID: 3264)
Checks supported languages
- 226061fc8f29c47dbf807957e4c7edaa.exe (PID: 2084)
- 127277c0097cef5ce18f0002a2456f84.exe (PID: 3784)
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- 545211f79941424f26866b9f00ad361b.exe (PID: 3676)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- 8191224f863e0d5287aafa7a08cdcdb3.exe (PID: 1352)
- b20c70a815c16a1ce1dc0e3335f462b7.exe (PID: 1036)
- a20a8faa583635241f71dbed54116e37.exe (PID: 2292)
- b305344f8ef568505c2d78ef9fa3840b.exe (PID: 2544)
- F8DB.tmp (PID: 2300)
- b7732333c67d9155ebe9c3a11f966143.exe (PID: 2332)
- F948.tmp (PID: 3924)
- 2a313ce479edd2ba234cd6c7975da5bf.exe (PID: 3832)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 3144)
- 2a313ce479edd2ba234cd6c7975da5bf.exe (PID: 1608)
- F996.tmp (PID: 3964)
- ZaccMoMY.exe (PID: 3140)
- FA52.tmp (PID: 3388)
- icsys.icn.exe (PID: 3080)
- FADF.tmp (PID: 2536)
- SkQQcsYU.exe (PID: 1276)
- cinst.exe (PID: 4016)
- FBD9.tmp (PID: 3972)
- FB7B.tmp (PID: 3092)
- FCA4.tmp (PID: 3408)
- FD01.tmp (PID: 3652)
- FDEC.tmp (PID: 3724)
- 779297.exe (PID: 3088)
- 779297.exe (PID: 2924)
- FD7E.tmp (PID: 3124)
- FF05.tmp (PID: 3336)
- FEA7.tmp (PID: 2128)
- FFFF.tmp (PID: 3400)
- FFA1.tmp (PID: 3356)
- CA.tmp (PID: 2092)
- 5D.tmp (PID: 2368)
- 1B5.tmp (PID: 1808)
- 128.tmp (PID: 1436)
- 32C.tmp (PID: 3524)
- 3E7.tmp (PID: 1816)
- 29F.tmp (PID: 1032)
- 464.tmp (PID: 4052)
- 3a5a024582f9c0a6a08e5ff3b3e1ea7e.exe (PID: 2068)
- 4b543325cf0e11dee26d58cc1ac38cf5.exe (PID: 2500)
- 4a184b64b838a4833419c76951f7eda4.exe (PID: 1820)
- 6a609d65263f2c95ab44b534255b53c9.exe (PID: 1348)
- 53F.tmp (PID: 3748)
- 9c389a6cd41fe1c54c505115125ddce8.exe (PID: 2088)
- 5CB.tmp (PID: 552)
- 12e89420d487205e997bbd25011d45fa.exe (PID: 2392)
- 658.tmp (PID: 2052)
- 26a318ba688442470eb1f247da7d76c1.exe (PID: 3580)
- 57aa30d6e6e29f4d34629179dcac75b7.exe (PID: 2384)
- 6699cf459391b430d49cbc80b2722bee.exe (PID: 2460)
- 786c8cf775b2e5c53c79864e33f30060.exe (PID: 2684)
- 289c1a8a890a567f4f70235ced85f763.exe (PID: 2344)
- 733.tmp (PID: 2232)
- ~1701551366.exe (PID: 1876)
- 86B.tmp (PID: 824)
- 8F8.tmp (PID: 1008)
- 975.tmp (PID: 2776)
- A40.tmp (PID: 2648)
- AAD.tmp (PID: 3980)
- budha.exe (PID: 3872)
- BC7.tmp (PID: 1924)
- wmpnscfg.exe (PID: 3264)
- C53.tmp (PID: 2196)
- s5534.exe (PID: 1556)
- D2E.tmp (PID: 2920)
- ykxim.exe (PID: 2524)
- 779297.exe (PID: 788)
- DF9.tmp (PID: 2532)
- E86.tmp (PID: 3216)
- F03.tmp (PID: 1696)
- F9F.tmp (PID: 2896)
- 101C.tmp (PID: 3340)
- 107A.tmp (PID: 2820)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- 10F7.tmp (PID: 3608)
- 1164.tmp (PID: 1296)
- 11B2.tmp (PID: 2932)
- 122F.tmp (PID: 3516)
- 12AC.tmp (PID: 2608)
- 158B.tmp (PID: 3876)
- 15F8.tmp (PID: 3540)
- 150E.tmp (PID: 3192)
- 1656.tmp (PID: 2316)
- 16D3.tmp (PID: 284)
- 1750.tmp (PID: 752)
- 17CD.tmp (PID: 1508)
- 1905.tmp (PID: 528)
- 19E0.tmp (PID: 2676)
- 1A7C.tmp (PID: 2040)
- 1BC4.tmp (PID: 2952)
- 1C61.tmp (PID: 948)
- 1D0D.tmp (PID: 304)
- 1E64.tmp (PID: 1528)
- 1DE7.tmp (PID: 2400)
- 20E5.tmp (PID: 4036)
- 21CF.tmp (PID: 3000)
- 1F2F.tmp (PID: 3076)
- 221D.tmp (PID: 3496)
- 227B.tmp (PID: 4008)
- 24FC.tmp (PID: 1496)
- 2337.tmp (PID: 4068)
- 2440.tmp (PID: 1872)
- 2663.tmp (PID: 2584)
- 2598.tmp (PID: 3424)
- 27AB.tmp (PID: 2888)
- 2838.tmp (PID: 968)
- 26E0.tmp (PID: 644)
- 28F3.tmp (PID: 2380)
- 2980.tmp (PID: 3096)
- 28A5.tmp (PID: 1904)
- 2A2C.tmp (PID: 3796)
- 2A7A.tmp (PID: 2972)
- 2AD8.tmp (PID: 2140)
- 2BD2.tmp (PID: 2156)
- 2B64.tmp (PID: 1460)
- 2C3F.tmp (PID: 2440)
- 2C8D.tmp (PID: 3040)
- 2D87.tmp (PID: 3396)
- 2D2A.tmp (PID: 1848)
- 2E91.tmp (PID: 2868)
- 2EEF.tmp (PID: 3348)
- 2E24.tmp (PID: 2976)
- 2F5C.tmp (PID: 3344)
- 2F9B.tmp (PID: 3276)
- 30A4.tmp (PID: 2084)
- 31BD.tmp (PID: 3864)
- 3037.tmp (PID: 3880)
- 32F6.tmp (PID: 3408)
- 3373.tmp (PID: 3724)
- 322B.tmp (PID: 4016)
- 3538.tmp (PID: 3924)
- 35E4.tmp (PID: 3524)
- 3661.tmp (PID: 1804)
- 377A.tmp (PID: 2052)
- 3A0A.tmp (PID: 1696)
- 3A87.tmp (PID: 3608)
- 3845.tmp (PID: 2292)
- 3B91.tmp (PID: 3540)
- 3B24.tmp (PID: 2392)
- 3D37.tmp (PID: 2072)
- 3DF2.tmp (PID: 3936)
- 3BFE.tmp (PID: 1528)
- 3E41.tmp (PID: 3016)
- 3F2B.tmp (PID: 1868)
- 4015.tmp (PID: 2760)
- 3FC7.tmp (PID: 3584)
- 3F79.tmp (PID: 3728)
- 4073.tmp (PID: 1496)
- 40B2.tmp (PID: 3424)
- 412F.tmp (PID: 2584)
- 41DA.tmp (PID: 2888)
- 418C.tmp (PID: 2456)
- 4248.tmp (PID: 968)
- 42D4.tmp (PID: 1904)
- 4342.tmp (PID: 2380)
- 43FD.tmp (PID: 2436)
- 43A0.tmp (PID: 3096)
- 449A.tmp (PID: 2140)
- 445B.tmp (PID: 2972)
- 4536.tmp (PID: 1460)
- 4584.tmp (PID: 536)
- 45D2.tmp (PID: 1996)
- 4611.tmp (PID: 1968)
- 466E.tmp (PID: 3808)
- 46DC.tmp (PID: 2540)
- 4788.tmp (PID: 1420)
- 4739.tmp (PID: 1900)
- 4843.tmp (PID: 3832)
- 48A1.tmp (PID: 3680)
- 47F5.tmp (PID: 2860)
- 48EF.tmp (PID: 2536)
- 491E.tmp (PID: 2492)
- 497C.tmp (PID: 3864)
- 49AA.tmp (PID: 2368)
- 49F9.tmp (PID: 3756)
- 4A47.tmp (PID: 2128)
- 4AB4.tmp (PID: 1032)
- 4B12.tmp (PID: 1816)
- 4B7F.tmp (PID: 552)
- 4C4A.tmp (PID: 2552)
- 4CD7.tmp (PID: 3328)
- 4D35.tmp (PID: 1588)
- 4DA2.tmp (PID: 3816)
- 4EDB.tmp (PID: 3616)
- 4E00.tmp (PID: 2348)
- 4E5E.tmp (PID: 3824)
- 4F58.tmp (PID: 788)
- 4F96.tmp (PID: 2052)
- 5003.tmp (PID: 3340)
- 50AF.tmp (PID: 2932)
- 52A3.tmp (PID: 3876)
- 536E.tmp (PID: 752)
- 5311.tmp (PID: 1636)
- 53BD.tmp (PID: 3668)
- 5468.tmp (PID: 3204)
- 54C6.tmp (PID: 2964)
- 5514.tmp (PID: 2236)
- 5562.tmp (PID: 3000)
- 55C0.tmp (PID: 3172)
- 567C.tmp (PID: 2904)
- 56BA.tmp (PID: 1984)
- 561E.tmp (PID: 2100)
- 5708.tmp (PID: 3684)
- 57D3.tmp (PID: 1496)
- 5766.tmp (PID: 3268)
- 5841.tmp (PID: 3424)
- 589F.tmp (PID: 3812)
- 590C.tmp (PID: 1872)
- 5A44.tmp (PID: 2456)
- 5AB2.tmp (PID: 2888)
- 5B5E.tmp (PID: 2944)
- 5B00.tmp (PID: 968)
- 5BFA.tmp (PID: 3096)
- 5C48.tmp (PID: 2436)
- 5BAC.tmp (PID: 2792)
- 5C96.tmp (PID: 2972)
- 5CE4.tmp (PID: 2140)
- 5D61.tmp (PID: 2784)
- 5DBF.tmp (PID: 536)
- 5E0D.tmp (PID: 2624)
- 5EC9.tmp (PID: 2468)
- 5F17.tmp (PID: 2092)
- 5E5B.tmp (PID: 2440)
- 607E.tmp (PID: 944)
- 5FA3.tmp (PID: 2976)
- 6011.tmp (PID: 2868)
- 60DC.tmp (PID: 2404)
- 612A.tmp (PID: 1360)
- 61D6.tmp (PID: 3276)
- 6224.tmp (PID: 3680)
- 6197.tmp (PID: 2776)
- 62EF.tmp (PID: 4080)
- 635D.tmp (PID: 3092)
- 6272.tmp (PID: 1556)
- 639B.tmp (PID: 3408)
- 63E9.tmp (PID: 2096)
- 6447.tmp (PID: 2368)
- 6495.tmp (PID: 1808)
- 64E3.tmp (PID: 2128)
- 6541.tmp (PID: 2900)
- 659F.tmp (PID: 3524)
- 67B2.tmp (PID: 124)
- 683F.tmp (PID: 3112)
- 66D7.tmp (PID: 3320)
- 689C.tmp (PID: 4004)
- 68FA.tmp (PID: 1884)
- 6996.tmp (PID: 1932)
- 6A04.tmp (PID: 3824)
- 6948.tmp (PID: 2344)
- 6A71.tmp (PID: 3100)
- 6ADE.tmp (PID: 3216)
- 6BE8.tmp (PID: 2052)
- 6B6B.tmp (PID: 788)
- 6CB3.tmp (PID: 3516)
- 6D30.tmp (PID: 2608)
- 6C36.tmp (PID: 1296)
- 6D8E.tmp (PID: 3360)
- 6E0B.tmp (PID: 3540)
- 6E98.tmp (PID: 2520)
- 6E59.tmp (PID: 1528)
- 6F53.tmp (PID: 3676)
- 6FEF.tmp (PID: 1016)
- 706C.tmp (PID: 3000)
- 7128.tmp (PID: 3728)
- 7186.tmp (PID: 3744)
- 71E3.tmp (PID: 4064)
- 7260.tmp (PID: 3684)
- 73C8.tmp (PID: 3268)
- 7464.tmp (PID: 1496)
- 7510.tmp (PID: 3424)
- 757D.tmp (PID: 3812)
- 75DB.tmp (PID: 1872)
- 7696.tmp (PID: 2888)
- 7648.tmp (PID: 2456)
- 7704.tmp (PID: 968)
- 7781.tmp (PID: 1492)
- 77EE.tmp (PID: 2792)
- 783C.tmp (PID: 3096)
- 787B.tmp (PID: 3920)
- 7907.tmp (PID: 844)
- 7965.tmp (PID: 2884)
- 78B9.tmp (PID: 2672)
- 79C3.tmp (PID: 300)
- 7A11.tmp (PID: 1432)
- 7A5F.tmp (PID: 1848)
- 7AFB.tmp (PID: 3396)
- 7B98.tmp (PID: 3856)
- 7CE0.tmp (PID: 3536)
- 7D2E.tmp (PID: 1208)
- 7D7C.tmp (PID: 1420)
- 7DBB.tmp (PID: 3348)
- 7DF9.tmp (PID: 3208)
- 7EB5.tmp (PID: 3832)
- 7F41.tmp (PID: 2620)
- 7E57.tmp (PID: 2956)
- 804B.tmp (PID: 2084)
- 7FCE.tmp (PID: 3080)
- 81A3.tmp (PID: 4080)
- 8200.tmp (PID: 3864)
- 824E.tmp (PID: 2096)
- 80E7.tmp (PID: 3520)
- 831A.tmp (PID: 2368)
- 83C5.tmp (PID: 2736)
- 8481.tmp (PID: 2128)
- 84DF.tmp (PID: 2900)
- 852D.tmp (PID: 1036)
- 858B.tmp (PID: 552)
- 8646.tmp (PID: 3164)
- 85F8.tmp (PID: 2552)
- 8694.tmp (PID: 1588)
- 86E2.tmp (PID: 3280)
- 8721.tmp (PID: 1988)
- 87BD.tmp (PID: 3120)
- 876F.tmp (PID: 2472)
- 884A.tmp (PID: 2232)
- 8898.tmp (PID: 2292)
- 88E6.tmp (PID: 2896)
- 880B.tmp (PID: 1248)
- 8934.tmp (PID: 2840)
- 8973.tmp (PID: 3192)
- 8B18.tmp (PID: 4036)
- 89E0.tmp (PID: 3876)
- 8C22.tmp (PID: 1892)
- 8C70.tmp (PID: 3156)
- 8BB5.tmp (PID: 2076)
- 8D2C.tmp (PID: 3556)
- 8D7A.tmp (PID: 3760)
- 8DC8.tmp (PID: 2904)
- 8CCE.tmp (PID: 3936)
- 8E64.tmp (PID: 4076)
- 8F10.tmp (PID: 3160)
- 8F8D.tmp (PID: 2892)
- 901A.tmp (PID: 2584)
- 9077.tmp (PID: 4056)
- 8FCC.tmp (PID: 3248)
- 9162.tmp (PID: 3020)
- 91C0.tmp (PID: 1888)
- 925C.tmp (PID: 2116)
- 9104.tmp (PID: 1616)
- 9365.tmp (PID: 1328)
- 93D3.tmp (PID: 732)
- 9421.tmp (PID: 1212)
- 92F8.tmp (PID: 2380)
- 946F.tmp (PID: 2972)
- 94AE.tmp (PID: 1460)
- 950B.tmp (PID: 916)
- 95B7.tmp (PID: 1244)
- 96A2.tmp (PID: 1432)
- 973E.tmp (PID: 1848)
- 9559.tmp (PID: 2720)
- 979C.tmp (PID: 2512)
- 97DA.tmp (PID: 3260)
- 9828.tmp (PID: 2460)
- 9886.tmp (PID: 2868)
- 98D4.tmp (PID: 2860)
- 9913.tmp (PID: 1936)
- 9951.tmp (PID: 3232)
- 9B07.tmp (PID: 884)
- 9BC2.tmp (PID: 1556)
- 99BE.tmp (PID: 3388)
- 9A4B.tmp (PID: 2996)
- 9C2F.tmp (PID: 3972)
- 9C7E.tmp (PID: 3520)
- 9CDB.tmp (PID: 4020)
- 9D49.tmp (PID: 3756)
- 9DB6.tmp (PID: 3724)
- 9E04.tmp (PID: 2368)
- 9E62.tmp (PID: 3620)
- 9EB0.tmp (PID: 664)
- 9EFE.tmp (PID: 1804)
- 9F3D.tmp (PID: 1008)
- 9F8B.tmp (PID: 552)
- A037.tmp (PID: 3848)
- A085.tmp (PID: 1444)
- A0D3.tmp (PID: 2344)
- 9FE9.tmp (PID: 2552)
- A121.tmp (PID: 3104)
Reads the computer name
- 127277c0097cef5ce18f0002a2456f84.exe (PID: 3784)
- 226061fc8f29c47dbf807957e4c7edaa.exe (PID: 2084)
- a20a8faa583635241f71dbed54116e37.exe (PID: 2292)
- b20c70a815c16a1ce1dc0e3335f462b7.exe (PID: 1036)
- F8DB.tmp (PID: 2300)
- 8191224f863e0d5287aafa7a08cdcdb3.exe (PID: 1352)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- b305344f8ef568505c2d78ef9fa3840b.exe (PID: 2544)
- F948.tmp (PID: 3924)
- b7732333c67d9155ebe9c3a11f966143.exe (PID: 2332)
- F996.tmp (PID: 3964)
- ZaccMoMY.exe (PID: 3140)
- icsys.icn.exe (PID: 3080)
- FA52.tmp (PID: 3388)
- 2a313ce479edd2ba234cd6c7975da5bf.exe (PID: 1608)
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- SkQQcsYU.exe (PID: 1276)
- FADF.tmp (PID: 2536)
- FB7B.tmp (PID: 3092)
- cinst.exe (PID: 4016)
- FBD9.tmp (PID: 3972)
- FD01.tmp (PID: 3652)
- FD7E.tmp (PID: 3124)
- FCA4.tmp (PID: 3408)
- FDEC.tmp (PID: 3724)
- FF05.tmp (PID: 3336)
- 779297.exe (PID: 2924)
- FEA7.tmp (PID: 2128)
- FFFF.tmp (PID: 3400)
- FFA1.tmp (PID: 3356)
- 5D.tmp (PID: 2368)
- CA.tmp (PID: 2092)
- 1B5.tmp (PID: 1808)
- 128.tmp (PID: 1436)
- 32C.tmp (PID: 3524)
- 3E7.tmp (PID: 1816)
- 29F.tmp (PID: 1032)
- 464.tmp (PID: 4052)
- 4b543325cf0e11dee26d58cc1ac38cf5.exe (PID: 2500)
- 53F.tmp (PID: 3748)
- 5CB.tmp (PID: 552)
- 658.tmp (PID: 2052)
- 26a318ba688442470eb1f247da7d76c1.exe (PID: 3580)
- 289c1a8a890a567f4f70235ced85f763.exe (PID: 2344)
- 733.tmp (PID: 2232)
- 6699cf459391b430d49cbc80b2722bee.exe (PID: 2460)
- 86B.tmp (PID: 824)
- 8F8.tmp (PID: 1008)
- 975.tmp (PID: 2776)
- A40.tmp (PID: 2648)
- ~1701551366.exe (PID: 1876)
- AAD.tmp (PID: 3980)
- BC7.tmp (PID: 1924)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- C53.tmp (PID: 2196)
- wmpnscfg.exe (PID: 3264)
- 4a184b64b838a4833419c76951f7eda4.exe (PID: 1820)
- D2E.tmp (PID: 2920)
- DF9.tmp (PID: 2532)
- s5534.exe (PID: 1556)
- E86.tmp (PID: 3216)
- F03.tmp (PID: 1696)
- F9F.tmp (PID: 2896)
- 107A.tmp (PID: 2820)
- 101C.tmp (PID: 3340)
- 10F7.tmp (PID: 3608)
- 1164.tmp (PID: 1296)
- budha.exe (PID: 3872)
- 11B2.tmp (PID: 2932)
- 122F.tmp (PID: 3516)
- 12AC.tmp (PID: 2608)
- 158B.tmp (PID: 3876)
- ykxim.exe (PID: 2524)
- 150E.tmp (PID: 3192)
- 15F8.tmp (PID: 3540)
- 1656.tmp (PID: 2316)
- 1750.tmp (PID: 752)
- 16D3.tmp (PID: 284)
- 17CD.tmp (PID: 1508)
- 9c389a6cd41fe1c54c505115125ddce8.exe (PID: 2088)
- 1905.tmp (PID: 528)
- 19E0.tmp (PID: 2676)
- 1BC4.tmp (PID: 2952)
- 786c8cf775b2e5c53c79864e33f30060.exe (PID: 2684)
- 1A7C.tmp (PID: 2040)
- 1C61.tmp (PID: 948)
- 1D0D.tmp (PID: 304)
- 1DE7.tmp (PID: 2400)
- 1E64.tmp (PID: 1528)
- 20E5.tmp (PID: 4036)
- 21CF.tmp (PID: 3000)
- 1F2F.tmp (PID: 3076)
- 221D.tmp (PID: 3496)
- 227B.tmp (PID: 4008)
- 2337.tmp (PID: 4068)
- 2440.tmp (PID: 1872)
- 24FC.tmp (PID: 1496)
- 2598.tmp (PID: 3424)
- 2663.tmp (PID: 2584)
- 27AB.tmp (PID: 2888)
- 2838.tmp (PID: 968)
- 26E0.tmp (PID: 644)
- 28F3.tmp (PID: 2380)
- 2980.tmp (PID: 3096)
- 2A2C.tmp (PID: 3796)
- 2A7A.tmp (PID: 2972)
- 2AD8.tmp (PID: 2140)
- 2B64.tmp (PID: 1460)
- 2C3F.tmp (PID: 2440)
- 2C8D.tmp (PID: 3040)
- 2BD2.tmp (PID: 2156)
- 2D87.tmp (PID: 3396)
- 2D2A.tmp (PID: 1848)
- 2E24.tmp (PID: 2976)
- 2E91.tmp (PID: 2868)
- 2EEF.tmp (PID: 3348)
- 2F5C.tmp (PID: 3344)
- 2F9B.tmp (PID: 3276)
- 3037.tmp (PID: 3880)
- 30A4.tmp (PID: 2084)
- 31BD.tmp (PID: 3864)
- 322B.tmp (PID: 4016)
- 32F6.tmp (PID: 3408)
- 3538.tmp (PID: 3924)
- 3373.tmp (PID: 3724)
- 35E4.tmp (PID: 3524)
- 3661.tmp (PID: 1804)
- 377A.tmp (PID: 2052)
- 3A0A.tmp (PID: 1696)
- 3A87.tmp (PID: 3608)
- 3845.tmp (PID: 2292)
- 3B24.tmp (PID: 2392)
- 3B91.tmp (PID: 3540)
- 3BFE.tmp (PID: 1528)
- 3D37.tmp (PID: 2072)
- 3E41.tmp (PID: 3016)
- 3F2B.tmp (PID: 1868)
- 3DF2.tmp (PID: 3936)
- 4015.tmp (PID: 2760)
- 3F79.tmp (PID: 3728)
- 3FC7.tmp (PID: 3584)
- 4073.tmp (PID: 1496)
- 40B2.tmp (PID: 3424)
- 412F.tmp (PID: 2584)
- 418C.tmp (PID: 2456)
- 4248.tmp (PID: 968)
- 42D4.tmp (PID: 1904)
- 41DA.tmp (PID: 2888)
- 28A5.tmp (PID: 1904)
- 43A0.tmp (PID: 3096)
- 4342.tmp (PID: 2380)
- 445B.tmp (PID: 2972)
- 449A.tmp (PID: 2140)
- 43FD.tmp (PID: 2436)
- 4536.tmp (PID: 1460)
- 4584.tmp (PID: 536)
- 45D2.tmp (PID: 1996)
- 4611.tmp (PID: 1968)
- 466E.tmp (PID: 3808)
- 46DC.tmp (PID: 2540)
- 4739.tmp (PID: 1900)
- 4788.tmp (PID: 1420)
- 4843.tmp (PID: 3832)
- 48A1.tmp (PID: 3680)
- 47F5.tmp (PID: 2860)
- 48EF.tmp (PID: 2536)
- 491E.tmp (PID: 2492)
- 497C.tmp (PID: 3864)
- 49AA.tmp (PID: 2368)
- 49F9.tmp (PID: 3756)
- 4A47.tmp (PID: 2128)
- 4AB4.tmp (PID: 1032)
- 4B12.tmp (PID: 1816)
- 4B7F.tmp (PID: 552)
- 4C4A.tmp (PID: 2552)
- 4CD7.tmp (PID: 3328)
- 4D35.tmp (PID: 1588)
- 4DA2.tmp (PID: 3816)
- 4E00.tmp (PID: 2348)
- 4E5E.tmp (PID: 3824)
- 4EDB.tmp (PID: 3616)
- 4F58.tmp (PID: 788)
- 4F96.tmp (PID: 2052)
- 5003.tmp (PID: 3340)
- 50AF.tmp (PID: 2932)
- 52A3.tmp (PID: 3876)
- 536E.tmp (PID: 752)
- 53BD.tmp (PID: 3668)
- 5311.tmp (PID: 1636)
- 5468.tmp (PID: 3204)
- 54C6.tmp (PID: 2964)
- 5514.tmp (PID: 2236)
- 5562.tmp (PID: 3000)
- 55C0.tmp (PID: 3172)
- 56BA.tmp (PID: 1984)
- 567C.tmp (PID: 2904)
- 561E.tmp (PID: 2100)
- 5708.tmp (PID: 3684)
- 5766.tmp (PID: 3268)
- 5841.tmp (PID: 3424)
- 589F.tmp (PID: 3812)
- 57D3.tmp (PID: 1496)
- 590C.tmp (PID: 1872)
- 5A44.tmp (PID: 2456)
- 5AB2.tmp (PID: 2888)
- 5B00.tmp (PID: 968)
- 5B5E.tmp (PID: 2944)
- 5BFA.tmp (PID: 3096)
- 5C48.tmp (PID: 2436)
- 5BAC.tmp (PID: 2792)
- 5C96.tmp (PID: 2972)
- 5CE4.tmp (PID: 2140)
- 5DBF.tmp (PID: 536)
- 5E0D.tmp (PID: 2624)
- 5D61.tmp (PID: 2784)
- 5E5B.tmp (PID: 2440)
- 5EC9.tmp (PID: 2468)
- 5F17.tmp (PID: 2092)
- 5FA3.tmp (PID: 2976)
- 6011.tmp (PID: 2868)
- 607E.tmp (PID: 944)
- 60DC.tmp (PID: 2404)
- 612A.tmp (PID: 1360)
- 61D6.tmp (PID: 3276)
- 6224.tmp (PID: 3680)
- 6197.tmp (PID: 2776)
- 6272.tmp (PID: 1556)
- 62EF.tmp (PID: 4080)
- 639B.tmp (PID: 3408)
- 63E9.tmp (PID: 2096)
- 635D.tmp (PID: 3092)
- 64E3.tmp (PID: 2128)
- 6495.tmp (PID: 1808)
- 6447.tmp (PID: 2368)
- 659F.tmp (PID: 3524)
- 6541.tmp (PID: 2900)
- 67B2.tmp (PID: 124)
- 683F.tmp (PID: 3112)
- 66D7.tmp (PID: 3320)
- 689C.tmp (PID: 4004)
- 68FA.tmp (PID: 1884)
- 6948.tmp (PID: 2344)
- 6996.tmp (PID: 1932)
- 6A04.tmp (PID: 3824)
- 6A71.tmp (PID: 3100)
- 6ADE.tmp (PID: 3216)
- 6B6B.tmp (PID: 788)
- 6BE8.tmp (PID: 2052)
- 6D30.tmp (PID: 2608)
- 6CB3.tmp (PID: 3516)
- 6C36.tmp (PID: 1296)
- 6D8E.tmp (PID: 3360)
- 6E0B.tmp (PID: 3540)
- 6E98.tmp (PID: 2520)
- 6E59.tmp (PID: 1528)
- 6F53.tmp (PID: 3676)
- 6FEF.tmp (PID: 1016)
- 706C.tmp (PID: 3000)
- 7128.tmp (PID: 3728)
- 7186.tmp (PID: 3744)
- 71E3.tmp (PID: 4064)
- 7260.tmp (PID: 3684)
- 73C8.tmp (PID: 3268)
- 7464.tmp (PID: 1496)
- 7510.tmp (PID: 3424)
- 75DB.tmp (PID: 1872)
- 757D.tmp (PID: 3812)
- 7696.tmp (PID: 2888)
- 7648.tmp (PID: 2456)
- 7704.tmp (PID: 968)
- 7781.tmp (PID: 1492)
- 77EE.tmp (PID: 2792)
- 787B.tmp (PID: 3920)
- 783C.tmp (PID: 3096)
- 78B9.tmp (PID: 2672)
- 7907.tmp (PID: 844)
- 7965.tmp (PID: 2884)
- 79C3.tmp (PID: 300)
- 7A11.tmp (PID: 1432)
- 7AFB.tmp (PID: 3396)
- 7B98.tmp (PID: 3856)
- 7A5F.tmp (PID: 1848)
- 7CE0.tmp (PID: 3536)
- 7D2E.tmp (PID: 1208)
- 7DBB.tmp (PID: 3348)
- 7DF9.tmp (PID: 3208)
- 7D7C.tmp (PID: 1420)
- 7E57.tmp (PID: 2956)
- 7EB5.tmp (PID: 3832)
- 7F41.tmp (PID: 2620)
- 7FCE.tmp (PID: 3080)
- 804B.tmp (PID: 2084)
- 81A3.tmp (PID: 4080)
- 8200.tmp (PID: 3864)
- 824E.tmp (PID: 2096)
- 80E7.tmp (PID: 3520)
- 831A.tmp (PID: 2368)
- 83C5.tmp (PID: 2736)
- 8481.tmp (PID: 2128)
- 84DF.tmp (PID: 2900)
- 852D.tmp (PID: 1036)
- 858B.tmp (PID: 552)
- 85F8.tmp (PID: 2552)
- 8646.tmp (PID: 3164)
- 8694.tmp (PID: 1588)
- 86E2.tmp (PID: 3280)
- 8721.tmp (PID: 1988)
- 876F.tmp (PID: 2472)
- 87BD.tmp (PID: 3120)
- 884A.tmp (PID: 2232)
- 8898.tmp (PID: 2292)
- 88E6.tmp (PID: 2896)
- 880B.tmp (PID: 1248)
- 8934.tmp (PID: 2840)
- 8973.tmp (PID: 3192)
- 89E0.tmp (PID: 3876)
- 8B18.tmp (PID: 4036)
- 8BB5.tmp (PID: 2076)
- 8C22.tmp (PID: 1892)
- 8C70.tmp (PID: 3156)
- 8D2C.tmp (PID: 3556)
- 8D7A.tmp (PID: 3760)
- 8DC8.tmp (PID: 2904)
- 8CCE.tmp (PID: 3936)
- 8F10.tmp (PID: 3160)
- 8F8D.tmp (PID: 2892)
- 901A.tmp (PID: 2584)
- 9077.tmp (PID: 4056)
- 8FCC.tmp (PID: 3248)
- 8E64.tmp (PID: 4076)
- 9162.tmp (PID: 3020)
- 91C0.tmp (PID: 1888)
- 925C.tmp (PID: 2116)
- 9104.tmp (PID: 1616)
- 92F8.tmp (PID: 2380)
- 9365.tmp (PID: 1328)
- 93D3.tmp (PID: 732)
- 9421.tmp (PID: 1212)
- 94AE.tmp (PID: 1460)
- 950B.tmp (PID: 916)
- 946F.tmp (PID: 2972)
- 95B7.tmp (PID: 1244)
- 96A2.tmp (PID: 1432)
- 973E.tmp (PID: 1848)
- 9559.tmp (PID: 2720)
- 979C.tmp (PID: 2512)
- 97DA.tmp (PID: 3260)
- 9828.tmp (PID: 2460)
- 9913.tmp (PID: 1936)
- 9951.tmp (PID: 3232)
- 9886.tmp (PID: 2868)
- 98D4.tmp (PID: 2860)
- 99BE.tmp (PID: 3388)
- 9B07.tmp (PID: 884)
- 9BC2.tmp (PID: 1556)
- 9A4B.tmp (PID: 2996)
- 9C2F.tmp (PID: 3972)
- 9C7E.tmp (PID: 3520)
- 9D49.tmp (PID: 3756)
- 9CDB.tmp (PID: 4020)
- 9DB6.tmp (PID: 3724)
- 9E04.tmp (PID: 2368)
- 9E62.tmp (PID: 3620)
- 9EFE.tmp (PID: 1804)
- 9F3D.tmp (PID: 1008)
- 9F8B.tmp (PID: 552)
- 9FE9.tmp (PID: 2552)
- A037.tmp (PID: 3848)
- A085.tmp (PID: 1444)
- 9EB0.tmp (PID: 664)
- A121.tmp (PID: 3104)
- A0D3.tmp (PID: 2344)
Creates files or folders in the user directory
- 127277c0097cef5ce18f0002a2456f84.exe (PID: 3784)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- 779297.exe (PID: 2924)
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- 3a5a024582f9c0a6a08e5ff3b3e1ea7e.exe (PID: 2068)
- 57aa30d6e6e29f4d34629179dcac75b7.exe (PID: 2384)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- 9c389a6cd41fe1c54c505115125ddce8.exe (PID: 2088)
- 786c8cf775b2e5c53c79864e33f30060.exe (PID: 2684)
- budha.exe (PID: 3872)
- ZaccMoMY.exe (PID: 3140)
Creates files in the program directory
- 226061fc8f29c47dbf807957e4c7edaa.exe (PID: 2084)
- 779297.exe (PID: 2924)
- ZaccMoMY.exe (PID: 3140)
Reads the machine GUID from the registry
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- a20a8faa583635241f71dbed54116e37.exe (PID: 2292)
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- b305344f8ef568505c2d78ef9fa3840b.exe (PID: 2544)
- F8DB.tmp (PID: 2300)
- b7732333c67d9155ebe9c3a11f966143.exe (PID: 2332)
- icsys.icn.exe (PID: 3080)
- F996.tmp (PID: 3964)
- FA52.tmp (PID: 3388)
- FADF.tmp (PID: 2536)
- FB7B.tmp (PID: 3092)
- FBD9.tmp (PID: 3972)
- FD01.tmp (PID: 3652)
- FCA4.tmp (PID: 3408)
- FD7E.tmp (PID: 3124)
- FDEC.tmp (PID: 3724)
- FEA7.tmp (PID: 2128)
- 779297.exe (PID: 2924)
- FF05.tmp (PID: 3336)
- FFA1.tmp (PID: 3356)
- FFFF.tmp (PID: 3400)
- 5D.tmp (PID: 2368)
- CA.tmp (PID: 2092)
- 128.tmp (PID: 1436)
- 1B5.tmp (PID: 1808)
- 32C.tmp (PID: 3524)
- 3E7.tmp (PID: 1816)
- 29F.tmp (PID: 1032)
- 464.tmp (PID: 4052)
- 53F.tmp (PID: 3748)
- 5CB.tmp (PID: 552)
- 658.tmp (PID: 2052)
- 733.tmp (PID: 2232)
- 86B.tmp (PID: 824)
- 8F8.tmp (PID: 1008)
- 975.tmp (PID: 2776)
- A40.tmp (PID: 2648)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- AAD.tmp (PID: 3980)
- BC7.tmp (PID: 1924)
- C53.tmp (PID: 2196)
- s5534.exe (PID: 1556)
- D2E.tmp (PID: 2920)
- budha.exe (PID: 3872)
- DF9.tmp (PID: 2532)
- E86.tmp (PID: 3216)
- F03.tmp (PID: 1696)
- 101C.tmp (PID: 3340)
- 107A.tmp (PID: 2820)
- F9F.tmp (PID: 2896)
- 10F7.tmp (PID: 3608)
- 1164.tmp (PID: 1296)
- 11B2.tmp (PID: 2932)
- 122F.tmp (PID: 3516)
- 12AC.tmp (PID: 2608)
- 158B.tmp (PID: 3876)
- 150E.tmp (PID: 3192)
- 15F8.tmp (PID: 3540)
- 16D3.tmp (PID: 284)
- 1750.tmp (PID: 752)
- 1656.tmp (PID: 2316)
- 17CD.tmp (PID: 1508)
- 1905.tmp (PID: 528)
- 1A7C.tmp (PID: 2040)
- 1BC4.tmp (PID: 2952)
- 19E0.tmp (PID: 2676)
- 1D0D.tmp (PID: 304)
- 1C61.tmp (PID: 948)
- 1DE7.tmp (PID: 2400)
- 1E64.tmp (PID: 1528)
- 1F2F.tmp (PID: 3076)
- 20E5.tmp (PID: 4036)
- 221D.tmp (PID: 3496)
- 227B.tmp (PID: 4008)
- 21CF.tmp (PID: 3000)
- 2337.tmp (PID: 4068)
- 24FC.tmp (PID: 1496)
- 2440.tmp (PID: 1872)
- 2663.tmp (PID: 2584)
- 2598.tmp (PID: 3424)
- 26E0.tmp (PID: 644)
- 27AB.tmp (PID: 2888)
- 2838.tmp (PID: 968)
- 28A5.tmp (PID: 1904)
- 28F3.tmp (PID: 2380)
- 2A2C.tmp (PID: 3796)
- 2A7A.tmp (PID: 2972)
- 2980.tmp (PID: 3096)
- 2AD8.tmp (PID: 2140)
- 2B64.tmp (PID: 1460)
- 2C3F.tmp (PID: 2440)
- 2C8D.tmp (PID: 3040)
- 2BD2.tmp (PID: 2156)
- 2D2A.tmp (PID: 1848)
- 2D87.tmp (PID: 3396)
- 2E24.tmp (PID: 2976)
- 2E91.tmp (PID: 2868)
- 2EEF.tmp (PID: 3348)
- 2F5C.tmp (PID: 3344)
- 2F9B.tmp (PID: 3276)
- 30A4.tmp (PID: 2084)
- 31BD.tmp (PID: 3864)
- 3037.tmp (PID: 3880)
- 322B.tmp (PID: 4016)
- 32F6.tmp (PID: 3408)
- 3538.tmp (PID: 3924)
- 35E4.tmp (PID: 3524)
- 3373.tmp (PID: 3724)
- 377A.tmp (PID: 2052)
- 3661.tmp (PID: 1804)
- 3A87.tmp (PID: 3608)
- 3A0A.tmp (PID: 1696)
- 3845.tmp (PID: 2292)
- 3B24.tmp (PID: 2392)
- 3B91.tmp (PID: 3540)
- 3BFE.tmp (PID: 1528)
- 3D37.tmp (PID: 2072)
- 3E41.tmp (PID: 3016)
- 3F2B.tmp (PID: 1868)
- 3DF2.tmp (PID: 3936)
- 3F79.tmp (PID: 3728)
- 3FC7.tmp (PID: 3584)
- 4073.tmp (PID: 1496)
- 40B2.tmp (PID: 3424)
- 4015.tmp (PID: 2760)
- 418C.tmp (PID: 2456)
- 412F.tmp (PID: 2584)
- 4248.tmp (PID: 968)
- 42D4.tmp (PID: 1904)
- 41DA.tmp (PID: 2888)
- 4342.tmp (PID: 2380)
- 43A0.tmp (PID: 3096)
- 445B.tmp (PID: 2972)
- 43FD.tmp (PID: 2436)
- 4536.tmp (PID: 1460)
- 449A.tmp (PID: 2140)
- 4584.tmp (PID: 536)
- 45D2.tmp (PID: 1996)
- 4611.tmp (PID: 1968)
- 466E.tmp (PID: 3808)
- 46DC.tmp (PID: 2540)
- 4739.tmp (PID: 1900)
- 4788.tmp (PID: 1420)
- 4843.tmp (PID: 3832)
- 48A1.tmp (PID: 3680)
- 47F5.tmp (PID: 2860)
- 48EF.tmp (PID: 2536)
- 491E.tmp (PID: 2492)
- 49AA.tmp (PID: 2368)
- 49F9.tmp (PID: 3756)
- 497C.tmp (PID: 3864)
- 4A47.tmp (PID: 2128)
- 4AB4.tmp (PID: 1032)
- 4B12.tmp (PID: 1816)
- 4B7F.tmp (PID: 552)
- 4C4A.tmp (PID: 2552)
- 4CD7.tmp (PID: 3328)
- 4D35.tmp (PID: 1588)
- 4DA2.tmp (PID: 3816)
- 4E5E.tmp (PID: 3824)
- 4EDB.tmp (PID: 3616)
- 4E00.tmp (PID: 2348)
- 4F58.tmp (PID: 788)
- 4F96.tmp (PID: 2052)
- 50AF.tmp (PID: 2932)
- 52A3.tmp (PID: 3876)
- 5003.tmp (PID: 3340)
- 5311.tmp (PID: 1636)
- 536E.tmp (PID: 752)
- 53BD.tmp (PID: 3668)
- 54C6.tmp (PID: 2964)
- 5468.tmp (PID: 3204)
- 5562.tmp (PID: 3000)
- 55C0.tmp (PID: 3172)
- 5514.tmp (PID: 2236)
- 561E.tmp (PID: 2100)
- 56BA.tmp (PID: 1984)
- 567C.tmp (PID: 2904)
- 5708.tmp (PID: 3684)
- 5766.tmp (PID: 3268)
- 57D3.tmp (PID: 1496)
- 5841.tmp (PID: 3424)
- 589F.tmp (PID: 3812)
- 590C.tmp (PID: 1872)
- 5A44.tmp (PID: 2456)
- 5B00.tmp (PID: 968)
- 5B5E.tmp (PID: 2944)
- 5AB2.tmp (PID: 2888)
- 5BAC.tmp (PID: 2792)
- 5BFA.tmp (PID: 3096)
- 5C48.tmp (PID: 2436)
- 5C96.tmp (PID: 2972)
- 5CE4.tmp (PID: 2140)
- 5DBF.tmp (PID: 536)
- 5E0D.tmp (PID: 2624)
- 5D61.tmp (PID: 2784)
- 5EC9.tmp (PID: 2468)
- 5F17.tmp (PID: 2092)
- 5E5B.tmp (PID: 2440)
- 5FA3.tmp (PID: 2976)
- 6011.tmp (PID: 2868)
- 60DC.tmp (PID: 2404)
- 612A.tmp (PID: 1360)
- 607E.tmp (PID: 944)
- 61D6.tmp (PID: 3276)
- 6224.tmp (PID: 3680)
- 6197.tmp (PID: 2776)
- 6272.tmp (PID: 1556)
- 62EF.tmp (PID: 4080)
- 63E9.tmp (PID: 2096)
- 639B.tmp (PID: 3408)
- 635D.tmp (PID: 3092)
- 6447.tmp (PID: 2368)
- 6495.tmp (PID: 1808)
- 64E3.tmp (PID: 2128)
- 6541.tmp (PID: 2900)
- 659F.tmp (PID: 3524)
- 66D7.tmp (PID: 3320)
- 67B2.tmp (PID: 124)
- 689C.tmp (PID: 4004)
- 68FA.tmp (PID: 1884)
- 683F.tmp (PID: 3112)
- 6948.tmp (PID: 2344)
- 6996.tmp (PID: 1932)
- 6A04.tmp (PID: 3824)
- 6A71.tmp (PID: 3100)
- 6ADE.tmp (PID: 3216)
- 6B6B.tmp (PID: 788)
- 6BE8.tmp (PID: 2052)
- 6CB3.tmp (PID: 3516)
- 6C36.tmp (PID: 1296)
- 6E0B.tmp (PID: 3540)
- 6D8E.tmp (PID: 3360)
- 6D30.tmp (PID: 2608)
- 6E59.tmp (PID: 1528)
- 6E98.tmp (PID: 2520)
- 6F53.tmp (PID: 3676)
- 6FEF.tmp (PID: 1016)
- 706C.tmp (PID: 3000)
- 7128.tmp (PID: 3728)
- 7186.tmp (PID: 3744)
- 71E3.tmp (PID: 4064)
- 7260.tmp (PID: 3684)
- 73C8.tmp (PID: 3268)
- 7464.tmp (PID: 1496)
- 7510.tmp (PID: 3424)
- 75DB.tmp (PID: 1872)
- 757D.tmp (PID: 3812)
- 7696.tmp (PID: 2888)
- 7648.tmp (PID: 2456)
- 7704.tmp (PID: 968)
- 7781.tmp (PID: 1492)
- 787B.tmp (PID: 3920)
- 77EE.tmp (PID: 2792)
- 783C.tmp (PID: 3096)
- 78B9.tmp (PID: 2672)
- 7907.tmp (PID: 844)
- 7965.tmp (PID: 2884)
- 79C3.tmp (PID: 300)
- 7A11.tmp (PID: 1432)
- 7A5F.tmp (PID: 1848)
- 7B98.tmp (PID: 3856)
- 7AFB.tmp (PID: 3396)
- 7CE0.tmp (PID: 3536)
- 7D2E.tmp (PID: 1208)
- 7DBB.tmp (PID: 3348)
- 7D7C.tmp (PID: 1420)
- 7DF9.tmp (PID: 3208)
- 7E57.tmp (PID: 2956)
- 7EB5.tmp (PID: 3832)
- 7F41.tmp (PID: 2620)
- 7FCE.tmp (PID: 3080)
- 804B.tmp (PID: 2084)
- 80E7.tmp (PID: 3520)
- 81A3.tmp (PID: 4080)
- 8200.tmp (PID: 3864)
- 824E.tmp (PID: 2096)
- 831A.tmp (PID: 2368)
- 8481.tmp (PID: 2128)
- 83C5.tmp (PID: 2736)
- 84DF.tmp (PID: 2900)
- 852D.tmp (PID: 1036)
- 858B.tmp (PID: 552)
- 85F8.tmp (PID: 2552)
- 8646.tmp (PID: 3164)
- 8694.tmp (PID: 1588)
- 86E2.tmp (PID: 3280)
- 8721.tmp (PID: 1988)
- 876F.tmp (PID: 2472)
- 87BD.tmp (PID: 3120)
- 884A.tmp (PID: 2232)
- 88E6.tmp (PID: 2896)
- 8898.tmp (PID: 2292)
- 880B.tmp (PID: 1248)
- 8934.tmp (PID: 2840)
- 8973.tmp (PID: 3192)
- 89E0.tmp (PID: 3876)
- 8BB5.tmp (PID: 2076)
- 8C22.tmp (PID: 1892)
- 8C70.tmp (PID: 3156)
- 8B18.tmp (PID: 4036)
- 8D2C.tmp (PID: 3556)
- 8D7A.tmp (PID: 3760)
- 8CCE.tmp (PID: 3936)
- 8F10.tmp (PID: 3160)
- 8E64.tmp (PID: 4076)
- 8F8D.tmp (PID: 2892)
- 8DC8.tmp (PID: 2904)
- 8FCC.tmp (PID: 3248)
- 901A.tmp (PID: 2584)
- 9077.tmp (PID: 4056)
- 9104.tmp (PID: 1616)
- 9162.tmp (PID: 3020)
- 91C0.tmp (PID: 1888)
- 925C.tmp (PID: 2116)
- 92F8.tmp (PID: 2380)
- 9365.tmp (PID: 1328)
- 93D3.tmp (PID: 732)
- 9421.tmp (PID: 1212)
- 946F.tmp (PID: 2972)
- 94AE.tmp (PID: 1460)
- 950B.tmp (PID: 916)
- 95B7.tmp (PID: 1244)
- 96A2.tmp (PID: 1432)
- 973E.tmp (PID: 1848)
- 9559.tmp (PID: 2720)
- 97DA.tmp (PID: 3260)
- 979C.tmp (PID: 2512)
- 9828.tmp (PID: 2460)
- 98D4.tmp (PID: 2860)
- 9913.tmp (PID: 1936)
- 9951.tmp (PID: 3232)
- 9886.tmp (PID: 2868)
- 99BE.tmp (PID: 3388)
- 9A4B.tmp (PID: 2996)
- 9B07.tmp (PID: 884)
- 9BC2.tmp (PID: 1556)
- 9C2F.tmp (PID: 3972)
- 9C7E.tmp (PID: 3520)
- 9CDB.tmp (PID: 4020)
- 9DB6.tmp (PID: 3724)
- 9E04.tmp (PID: 2368)
- 9E62.tmp (PID: 3620)
- 9D49.tmp (PID: 3756)
- 9EB0.tmp (PID: 664)
- 9EFE.tmp (PID: 1804)
- 9F3D.tmp (PID: 1008)
- 9F8B.tmp (PID: 552)
- 9FE9.tmp (PID: 2552)
- A037.tmp (PID: 3848)
- A085.tmp (PID: 1444)
- A0D3.tmp (PID: 2344)
Create files in a temporary directory
- 2278600280b0490ebf08c98c0e27e46c.exe (PID: 1840)
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- b7732333c67d9155ebe9c3a11f966143.exe (PID: 2332)
- icsys.icn.exe (PID: 3080)
- 226061fc8f29c47dbf807957e4c7edaa.exe (PID: 2084)
- 6699cf459391b430d49cbc80b2722bee.exe (PID: 2460)
- 289c1a8a890a567f4f70235ced85f763.exe (PID: 2344)
- 59a943ed50c22f23b6b4342f1e66c8c6.exe (PID: 2240)
- 4a184b64b838a4833419c76951f7eda4.exe (PID: 1820)
- budha.exe (PID: 3872)
- 779297.exe (PID: 2924)
Checks proxy server information
- a8b8df17c34f05be56406fcde37666eb.exe (PID: 1152)
- 779297.exe (PID: 2924)
- 4b543325cf0e11dee26d58cc1ac38cf5.exe (PID: 2500)
- budha.exe (PID: 3872)
Changes appearance of the Explorer extensions
- reg.exe (PID: 4080)
- reg.exe (PID: 3864)
The executable file from the user directory is run by the CMD process
- cinst.exe (PID: 4016)
Reads Environment values
- s5534.exe (PID: 1556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
685
Monitored processes
634
Malicious processes
193
Suspicious processes
181
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\AppData\Local\Temp\67B2.tmp" | C:\Users\admin\AppData\Local\Temp\67B2.tmp | — | 66D7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
| 124 | "C:\Users\admin\AppData\Local\Temp\CED8.tmp" | C:\Users\admin\AppData\Local\Temp\CED8.tmp | — | CE8A.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 | |||||||||||||||
| 124 | "C:\Users\admin\AppData\Local\Temp\E473.tmp" | C:\Users\admin\AppData\Local\Temp\E473.tmp | — | E3E7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 | |||||||||||||||
| 128 | "C:\Users\admin\AppData\Local\Temp\D958.tmp" | C:\Users\admin\AppData\Local\Temp\D958.tmp | — | D919.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 | |||||||||||||||
| 188 | "C:\Users\admin\AppData\Local\Temp\EAEC.tmp" | C:\Users\admin\AppData\Local\Temp\EAEC.tmp | — | EAAD.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 | |||||||||||||||
| 284 | "C:\Users\admin\AppData\Local\Temp\16D3.tmp" | C:\Users\admin\AppData\Local\Temp\16D3.tmp | — | 1656.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
| 292 | "C:\Users\admin\AppData\Local\Temp\D679.tmp" | C:\Users\admin\AppData\Local\Temp\D679.tmp | — | D62B.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 | |||||||||||||||
| 296 | "C:\Users\admin\AppData\Local\Temp\CE8A.tmp" | C:\Users\admin\AppData\Local\Temp\CE8A.tmp | — | CE2C.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 | |||||||||||||||
| 296 | "C:\Users\admin\AppData\Local\Temp\E3E7.tmp" | C:\Users\admin\AppData\Local\Temp\E3E7.tmp | — | E3A8.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 | |||||||||||||||
| 300 | "C:\Users\admin\AppData\Local\Temp\79C3.tmp" | C:\Users\admin\AppData\Local\Temp\79C3.tmp | — | 7965.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Word Exit code: 0 Version: 12.0.4518.1014 Modules
| |||||||||||||||
Total events
26 663
Read events
26 367
Write events
225
Delete events
71
Modification events
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2332) b7732333c67d9155ebe9c3a11f966143.exe | Key: | HKEY_CURRENT_USER\Software\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (1152) a8b8df17c34f05be56406fcde37666eb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1 792
Suspicious files
19
Text files
207
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\4b543325cf0e11dee26d58cc1ac38cf5.exe | executable | |
MD5:4B543325CF0E11DEE26D58CC1AC38CF5 | SHA256:E9EF5889CBC575FABAE55849EEBC9EFE2C14D9532C6CAFB02AAF78CC5DEE3CA0 | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\127277c0097cef5ce18f0002a2456f84.exe | executable | |
MD5:127277C0097CEF5CE18F0002A2456F84 | SHA256:E0E43B3AAAACEA4C53B4723C5A9704C7B9C0EA88A45DA58622B0EA85A5A5CDF8 | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\545211f79941424f26866b9f00ad361b.exe | executable | |
MD5:545211F79941424F26866B9F00AD361B | SHA256:235A898FFCD14C165495DEC3B265492F17D09527FE55C6B0072B25727C6A2BAB | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\a8b8df17c34f05be56406fcde37666eb.exe | executable | |
MD5:A8B8DF17C34F05BE56406FCDE37666EB | SHA256:587AF8510E8148E03E4B63EE8C80A1E8F9B96ABA3F9FD229E88AFC1B6C6BE358 | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\3bd034caf22f9d14a7d984c31f36cb67.exe | executable | |
MD5:3BD034CAF22F9D14A7D984C31F36CB67 | SHA256:017BC03A3F41D807F6A2FB437DEA72E82F27D4EEC077E48D63EA3984CB55DCB8 | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\4a184b64b838a4833419c76951f7eda4.exe | executable | |
MD5:4A184B64B838A4833419C76951F7EDA4 | SHA256:0977FAEDBC532514CBBC5DBAF1B077364555378C7094B3BB1A91095C58870775 | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\59a943ed50c22f23b6b4342f1e66c8c6.exe | executable | |
MD5:59A943ED50C22F23B6B4342F1E66C8C6 | SHA256:5F69663DDD3C274B74A7DF5E474C9F4933BCBD6A9DE14B8A1F09916031DFA64F | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\8191224f863e0d5287aafa7a08cdcdb3.exe | executable | |
MD5:8191224F863E0D5287AAFA7A08CDCDB3 | SHA256:512E198C86A1DF61FF512EFDD25106A557B9A3EB0DA264F9BC247C487F6678E1 | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\33fe4259a21b93c20ef6a920b6311b8f.exe | executable | |
MD5:33FE4259A21B93C20EF6A920B6311B8F | SHA256:3984F62C9C5E3AF60DF7278B321057FCF131B6B30887B4802F4A536277B44589 | |||
| 3060 | WinRAR.exe | C:\Users\admin\Desktop\6699cf459391b430d49cbc80b2722bee.exe | executable | |
MD5:6699CF459391B430D49CBC80B2722BEE | SHA256:6BEFC06A5DDEAF215EDBC2ECC66DE6AF13602BA316A3F724A9E32CAFA2CBAF3A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
30
DNS requests
23
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 404 | 45.56.79.23:80 | http://www.buscaid.com/?adn | unknown | text | 3 b | unknown |
1276 | SkQQcsYU.exe | GET | 302 | 142.250.186.46:80 | http://google.com/ | unknown | html | 392 b | unknown |
3140 | ZaccMoMY.exe | GET | 302 | 142.250.186.46:80 | http://google.com/ | unknown | html | 392 b | unknown |
2924 | 779297.exe | GET | 307 | 104.22.74.171:80 | http://whos.amung.us/swidget/78ejo1rdbrrt | unknown | — | — | unknown |
2924 | 779297.exe | GET | 200 | 172.67.8.141:80 | http://widgets.amung.us/small/00/1.png | unknown | image | 308 b | unknown |
3872 | budha.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7520324cc12e51a8 | unknown | compressed | 4.66 Kb | unknown |
3872 | budha.exe | GET | 200 | 23.53.40.154:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPfsP04QnEetkZKto7%2FcXU3hA%3D%3D | unknown | binary | 503 b | unknown |
3872 | budha.exe | GET | 200 | 23.49.30.152:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3872 | budha.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0fea42b38746ad67 | unknown | compressed | 65.2 Kb | unknown |
1556 | s5534.exe | GET | 200 | 76.223.26.96:80 | http://8bd8fb.api.socdn.com/installer/52fe2c91-49dc-40b7-b209-1f140a000013/12412046/config | unknown | html | 2.21 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3140 | ZaccMoMY.exe | 142.250.186.46:80 | — | GOOGLE | US | whitelisted |
3784 | 127277c0097cef5ce18f0002a2456f84.exe | 34.41.229.245:80 | pywolwnvd.biz | GOOGLE-CLOUD-PLATFORM | US | unknown |
1276 | SkQQcsYU.exe | 142.250.186.46:80 | — | GOOGLE | US | whitelisted |
2924 | 779297.exe | 104.22.74.171:80 | whos.amung.us | CLOUDFLARENET | — | unknown |
2924 | 779297.exe | 172.67.8.141:80 | whos.amung.us | CLOUDFLARENET | US | unknown |
3872 | budha.exe | 68.178.149.80:443 | gbcno.com | GO-DADDY-COM-LLC | IN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ad.much8.com |
| unknown |
pywolwnvd.biz |
| unknown |
c4ba3647.ns1.dnsdynnet.com |
| unknown |
whos.amung.us |
| whitelisted |
widgets.amung.us |
| whitelisted |
agileprepcourse.com |
| unknown |
gbcno.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
3140 | ZaccMoMY.exe | A Network Trojan was detected | ET HUNTING Terse Unencrypted Request for Google - Likely Connectivity Check |
1276 | SkQQcsYU.exe | A Network Trojan was detected | ET HUNTING Terse Unencrypted Request for Google - Likely Connectivity Check |
1276 | SkQQcsYU.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Possible automated connectivity check (www.google.com) |
2924 | 779297.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
2924 | 779297.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
1556 | s5534.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (DownloadMR) |
1556 | s5534.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (DownloadMR) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
3784 | 127277c0097cef5ce18f0002a2456f84.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value Snkz |
3 ETPRO signatures available at the full report