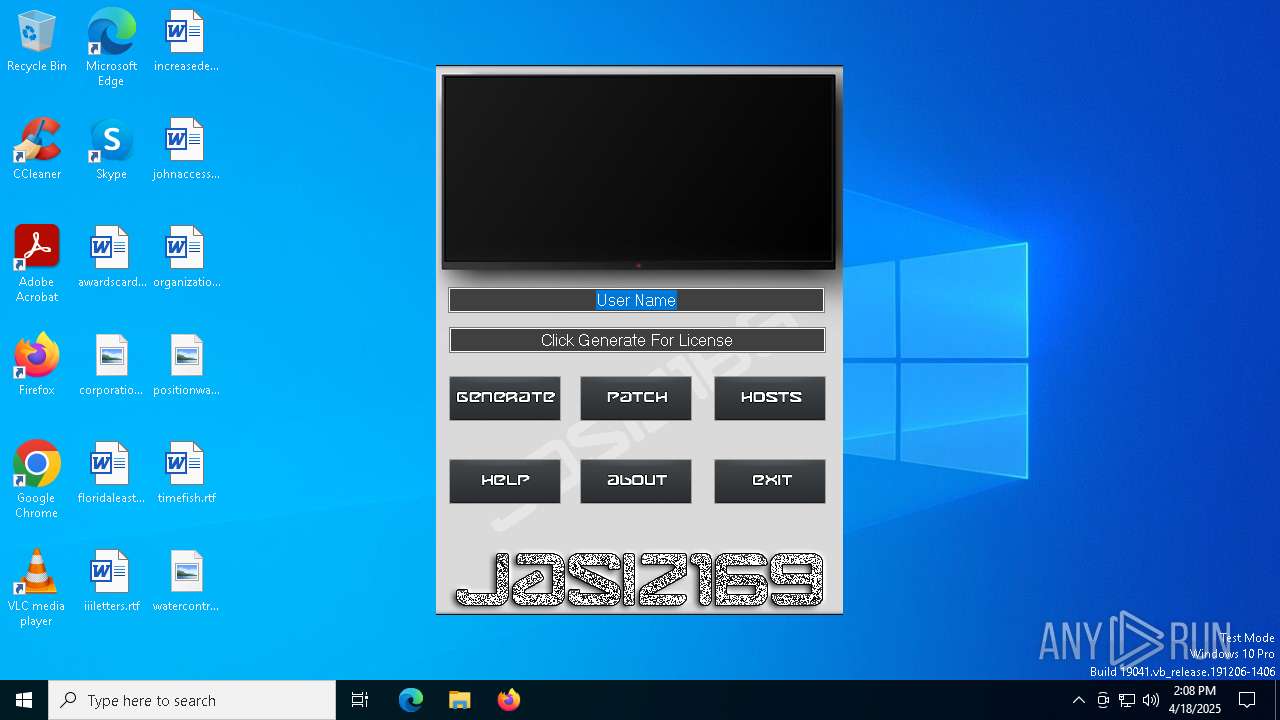
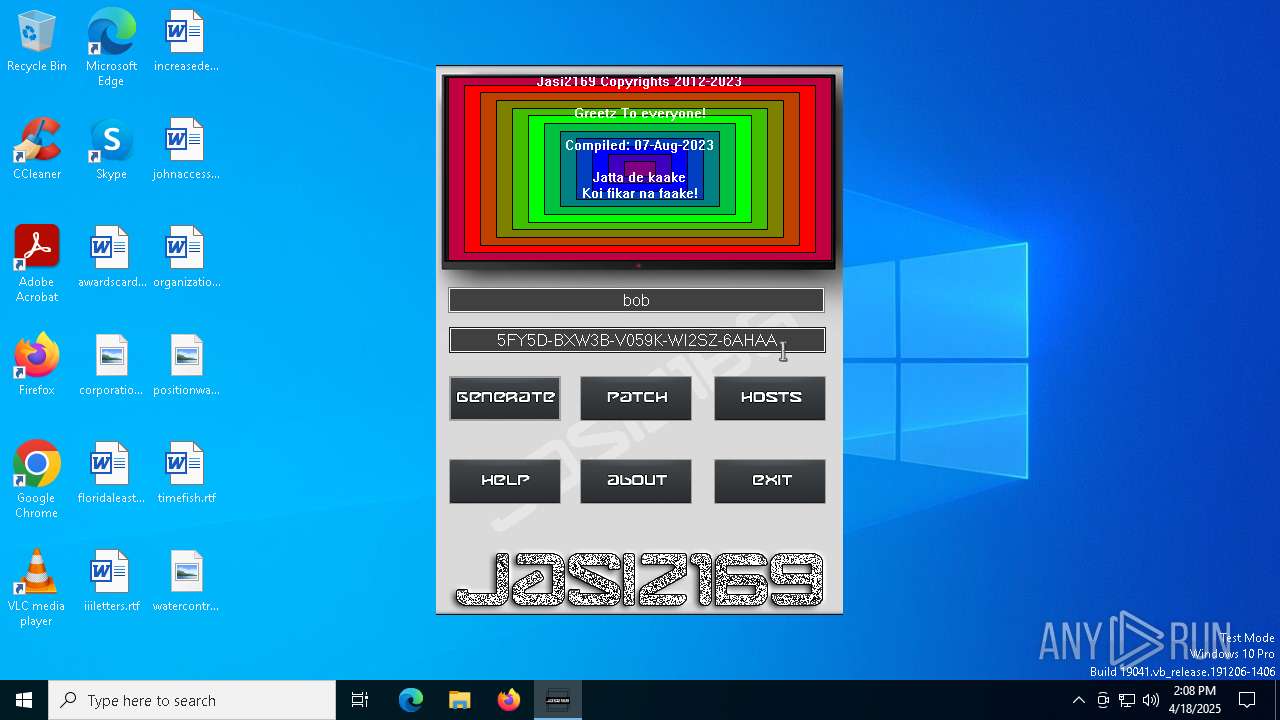
| File name: | NetLimiter Keygen v1.3.exe |
| Full analysis: | https://app.any.run/tasks/e0374ee4-7cc2-4178-a008-c23aa62dde13 |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2025, 14:08:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 403CE52E780C06D2869145AD4461B567 |
| SHA1: | 026DAB4630EAF49C77944CD8BBEBD8F506E979BB |
| SHA256: | 124E9A0FB03FCEB4DD2ED5820C5A8D8381A2BFE6922A6CF8B630C29D3BEF564A |
| SSDEEP: | 98304:edjZ9lWXWbnMGhEaW+0Am9sZBd2s1oPkvo5wdQ6RvtLDVKk4sfIgtjNQOAxf1gS3:empZydn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- NetLimiter Keygen v1.3.exe (PID: 1348)
Executable content was dropped or overwritten
- NetLimiter Keygen v1.3.exe (PID: 1348)
Reads security settings of Internet Explorer
- NetLimiter Keygen v1.3.exe (PID: 1348)
There is functionality for taking screenshot (YARA)
- NetLimiter Keygen v1.3.exe (PID: 1348)
INFO
Checks supported languages
- NetLimiter Keygen v1.3.exe (PID: 1348)
Process checks whether UAC notifications are on
- NetLimiter Keygen v1.3.exe (PID: 1348)
Create files in a temporary directory
- NetLimiter Keygen v1.3.exe (PID: 1348)
Reads the machine GUID from the registry
- NetLimiter Keygen v1.3.exe (PID: 1348)
Reads the computer name
- NetLimiter Keygen v1.3.exe (PID: 1348)
Creates files in the program directory
- NetLimiter Keygen v1.3.exe (PID: 1348)
Themida protector has been detected
- NetLimiter Keygen v1.3.exe (PID: 1348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:08:31 16:38:45+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 607744 |
| InitializedDataSize: | 629760 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x620058 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | NetLimiter 5.x |
| CompanyName: | Jasi2169 |
| FileDescription: | Netlimiter Keygen By Jasi2169 |
| FileVersion: | 1.0.0.0 |
| InternalName: | Netlimiter Keygen.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | All Rights Reserved |
| OriginalFileName: | Netlimiter Keygen.exe |
| ProductName: | Netlimiter Keygen |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
136
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | "C:\Users\admin\AppData\Local\Temp\NetLimiter Keygen v1.3.exe" | C:\Users\admin\AppData\Local\Temp\NetLimiter Keygen v1.3.exe | explorer.exe | ||||||||||||
User: admin Company: Jasi2169 Integrity Level: HIGH Description: Netlimiter Keygen By Jasi2169 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\AppData\Local\Temp\NetLimiter Keygen v1.3.exe" | C:\Users\admin\AppData\Local\Temp\NetLimiter Keygen v1.3.exe | — | explorer.exe | |||||||||||
User: admin Company: Jasi2169 Integrity Level: MEDIUM Description: Netlimiter Keygen By Jasi2169 Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6488 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 635
Read events
3 600
Write events
34
Delete events
1
Modification events
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Sort |
Value: 000000000000000000000000000000000100000030F125B7EF471A10A5F102608C9EEBAC0A00000001000000 | |||
| (PID) Process: | (1348) NetLimiter Keygen v1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | ColInfo |
Value: 00000000000000000000000000000000FDDFDFFD100000000000000000000000040000001800000030F125B7EF471A10A5F102608C9EEBAC0A0000001001000030F125B7EF471A10A5F102608C9EEBAC0E0000007800000030F125B7EF471A10A5F102608C9EEBAC040000007800000030F125B7EF471A10A5F102608C9EEBAC0C00000050000000 | |||
Executable files
2
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1348 | NetLimiter Keygen v1.3.exe | C:\Users\admin\AppData\Local\Temp\Netlimiter Keygen.X86.1.0.0.0\keygen_cursor.cur | binary | |
MD5:FC9B2E18A0E21C712E227E88248882C1 | SHA256:FE802DB4DE68C9340F7A211DDF694109FD983478454CCB925A06F68851276C69 | |||
| 1348 | NetLimiter Keygen v1.3.exe | C:\Users\admin\AppData\Local\Temp\Netlimiter Keygen.X86.1.0.0.0\Native.dll | executable | |
MD5:36FDE2466FEA08328EDB8744EE01981E | SHA256:AC3D757539AF3AC2103803F5F058FCF05D4082498DCB02F42EBF322A5AC9D9D6 | |||
| 1348 | NetLimiter Keygen v1.3.exe | C:\Windows\SysWOW64\bassmod.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
| 1348 | NetLimiter Keygen v1.3.exe | C:\ProgramData\Locktime\NetLimiter\5\license.json | binary | |
MD5:7B8677963E3D0A35C1FCA3B50DD755F6 | SHA256:3E0C3A62296D39E39FA8F6D10E7470E61058179AC18944F808DBE78DA07737B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7792 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7792 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7792 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7792 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |