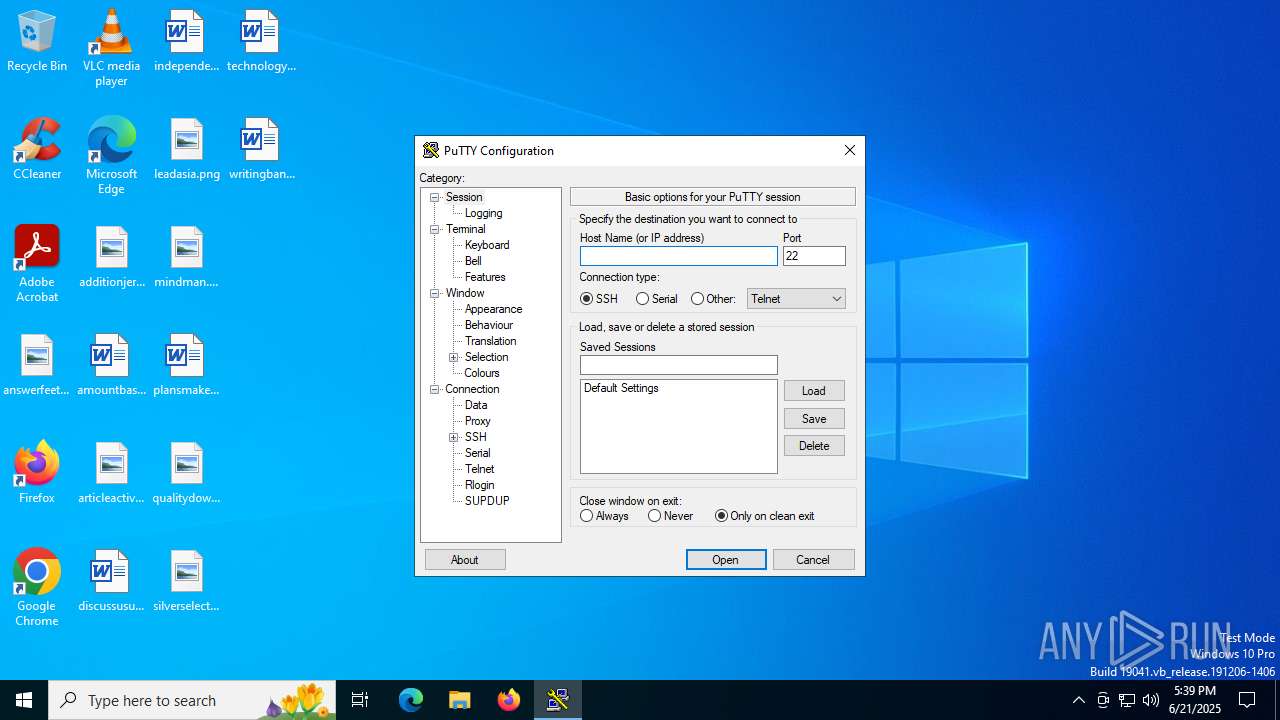
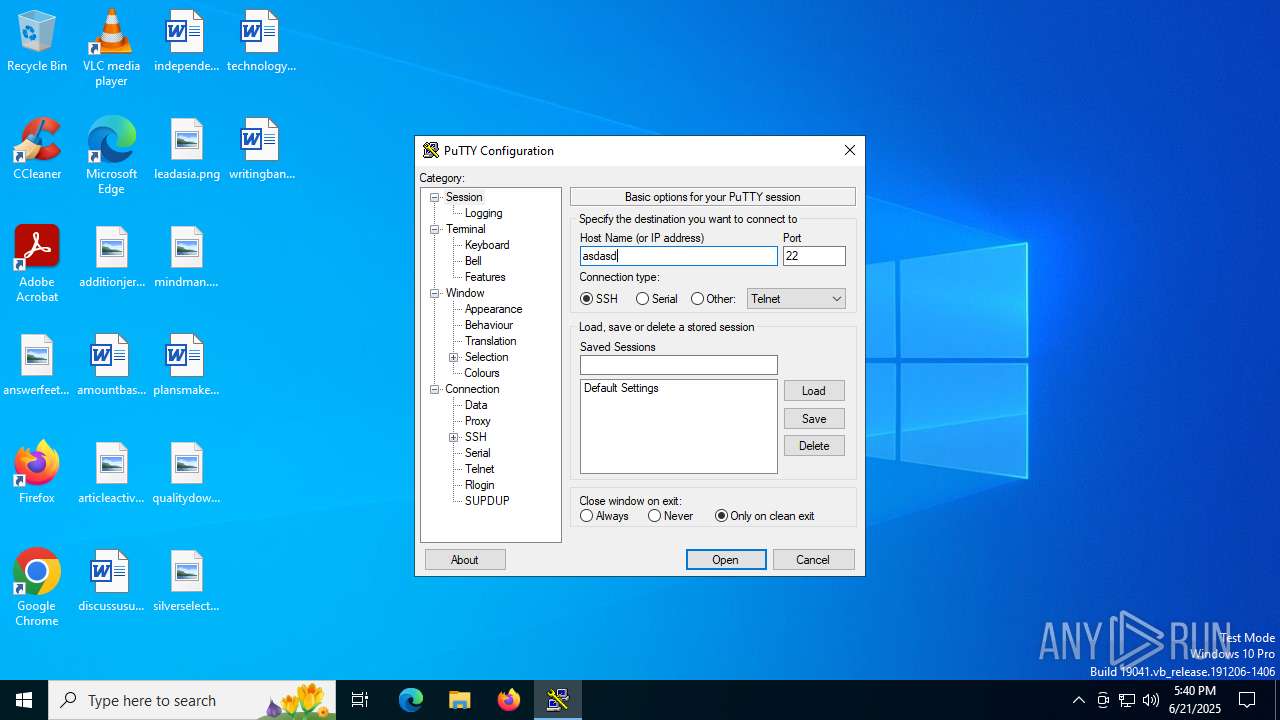
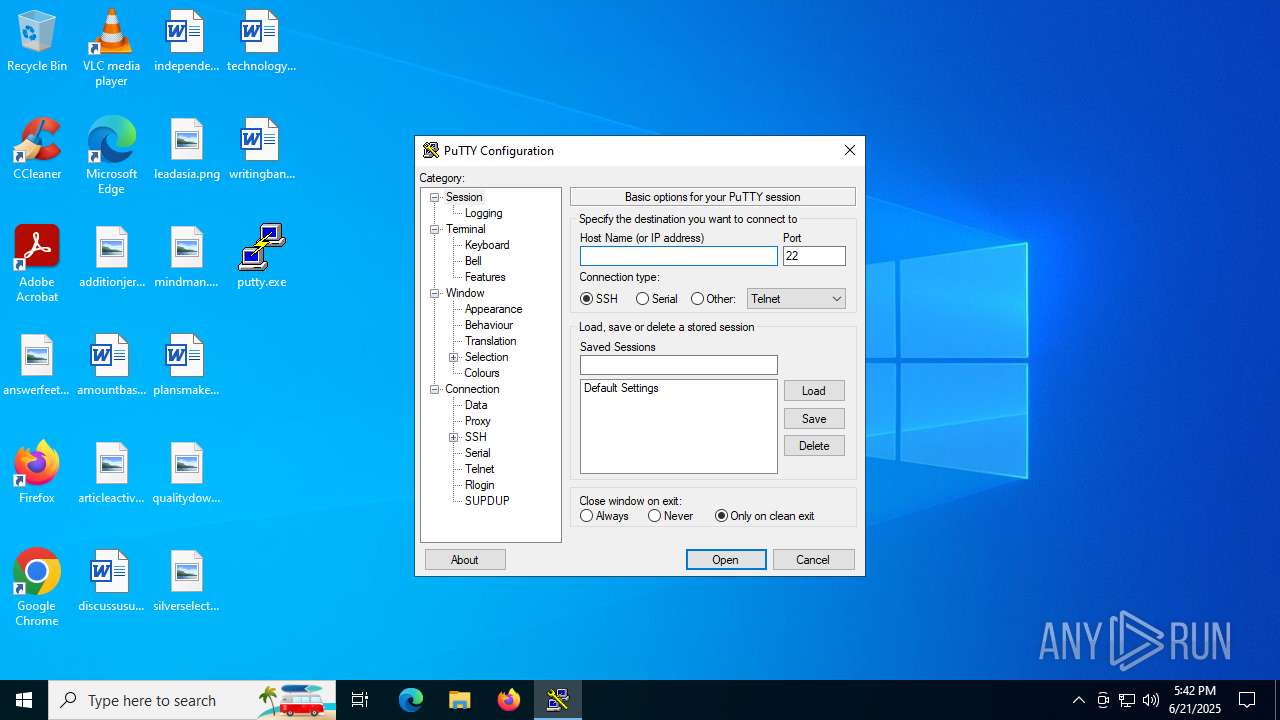
| File name: | putty.exe |
| Full analysis: | https://app.any.run/tasks/53872cdc-d7f1-4031-b290-4faec4b7990b |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 17:39:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 10 sections |
| MD5: | 1AE35BDD854D111BE585881A7D4EC2C3 |
| SHA1: | F1041EB39A713B1BA7564651D47462A995BBBB20 |
| SHA256: | 12498D4E4BF07747A9A52D6803D3211FD731DED6473B41CF4795AC56947D0366 |
| SSDEEP: | 49152:5EHBCJFkonGPavKwSDQYBvcgexU282Cdn8KpOEgn31s:WGSDQkr2D8n8KpOEeC |
MALICIOUS
No malicious indicators.SUSPICIOUS
PUTTY has been detected
- putty.exe (PID: 4192)
- putty.exe (PID: 4100)
Connects to SSH
- putty.exe (PID: 4192)
- putty.exe (PID: 4100)
INFO
Checks supported languages
- putty.exe (PID: 4192)
- SearchApp.exe (PID: 5328)
- putty.exe (PID: 4100)
Creates files or folders in the user directory
- putty.exe (PID: 4192)
Checks proxy server information
- slui.exe (PID: 1192)
Reads the computer name
- putty.exe (PID: 4192)
- putty.exe (PID: 4100)
The sample compiled with english language support
- putty.exe (PID: 4192)
Process checks computer location settings
- SearchApp.exe (PID: 5328)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5328)
- putty.exe (PID: 4192)
- putty.exe (PID: 4100)
Reads the software policy settings
- slui.exe (PID: 1192)
- SearchApp.exe (PID: 5328)
Manual execution by a user
- putty.exe (PID: 4100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:01 11:22:06+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 966144 |
| InitializedDataSize: | 348672 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbe504 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.83.0.0 |
| ProductVersionNumber: | 0.83.0.0 |
| FileFlagsMask: | 0x000b |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| CompanyName: | Simon Tatham |
| ProductName: | PuTTY suite |
| FileDescription: | SSH, Telnet, Rlogin, and SUPDUP client |
| InternalName: | PuTTY |
| OriginalFileName: | PuTTY |
| FileVersion: | Release 0.83 (without embedded help) |
| ProductVersion: | Release 0.83 |
| LegalCopyright: | Copyright © 1997-2025 Simon Tatham. |
Total processes
176
Monitored processes
4
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1192 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4100 | "C:\Users\admin\Desktop\putty.exe" | C:\Users\admin\Desktop\putty.exe | explorer.exe | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet, Rlogin, and SUPDUP client Version: Release 0.83 (without embedded help) Modules
| |||||||||||||||
| 4192 | "C:\Users\admin\AppData\Local\Temp\putty.exe" | C:\Users\admin\AppData\Local\Temp\putty.exe | explorer.exe | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet, Rlogin, and SUPDUP client Exit code: 0 Version: Release 0.83 (without embedded help) Modules
| |||||||||||||||
| 5328 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 107
Read events
9 955
Write events
148
Delete events
4
Modification events
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsAADCloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | CortanaStateLastRun |
Value: E5EE566800000000 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 73746 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | write | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | \REGISTRY\A\{33bbf253-2489-7544-6fed-a8e530b47e4d}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 0000F3F913C9D3E2DB01 | |||
| (PID) Process: | (5328) SearchApp.exe | Key: | \REGISTRY\A\{33bbf253-2489-7544-6fed-a8e530b47e4d}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 0000F3F913C9D3E2DB01 | |||
Executable files
0
Suspicious files
116
Text files
128
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4192 | putty.exe | C:\Users\admin\AppData\Local\PUTTY.RND | binary | |
MD5:841715FD802A567F126FFD5231A3604C | SHA256:98B5082325F0F66DC12FC7DAD01A18F343B6B45465D60ECD1E3855F023DFE4D7 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\tUCiVcVWZ-go7BLlq95YW6bKHZE[1].css | text | |
MD5:445D78544E0CFC11EFC1E172DA3ECBBC | SHA256:76EFEBABB82AE8342985C99A498137C04B3E46BC59D78191F0DA44C660B980F5 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:4E0E75684C84C0102CED12948B95609B | SHA256:4D18E491B2DE4DA34F6C15F0574911613E902F791FE72501E4404802760D1BCA | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:1E6BFCF5CB4BEFA357827DD38F0700B3 | SHA256:6920BF90F85D28CB6986A0F0208A7E35D6DD5322FEF5ABA3E54570FE53DA1BAC | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\4BpQ1bD8vX1mXuJObN-gg9RqkyQ.br[1].js | binary | |
MD5:8465A334065673EB6A6487C8D87539DB | SHA256:84ED6C495B322B0F2213CC33EC6C652D84D82E010C928B1141DB2290D4365F3D | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:908111EB0FFB1360D5DD61279C21703E | SHA256:1ED87CF425DED994B05A842271AB4D28A76F399E571688CF2E7B186F70DC3059 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\NajusmjIqB4kdLn9FmVxeS4xi2o[1].css | text | |
MD5:73D1CEBD8E3B6C7246F422D624EDF803 | SHA256:0674786CF9978A1F9065F57D98E986070C7CBB5177F154F40E8A924C0E0C13F2 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\EZWKAkzgKyOdhH1NT8zm80mcnH4.br[1].js | binary | |
MD5:E0DB109CD3BF2BBCF672924FF79ECC28 | SHA256:AE2216ED30AF488A3A771EB9C0DFF0F2DBBDB00FAA70743A4E43566EA4EA9644 | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\LJVpDXTkWDgGwVlLgxLZkLutWKw[1].css | text | |
MD5:B9727BBC2A77C4A60AADDCA163365575 | SHA256:8B23E288F4D6BF19C88B4F60AF45515C1D637D795430F150E4BC7C76FAD95CBD | |||
| 5328 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\3-X3h7uDMtfcne46mFDSZyqDAWs.br[1].js | binary | |
MD5:E766B650487DC4BC853C0DF56D828A34 | SHA256:5294321F5371681E306FE4FB2D8FD9E6E4829BB27FB6338C6F3FABF19DF2FCBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
96
DNS requests
83
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7020 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6340 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6340 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1136 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7020 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7020 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
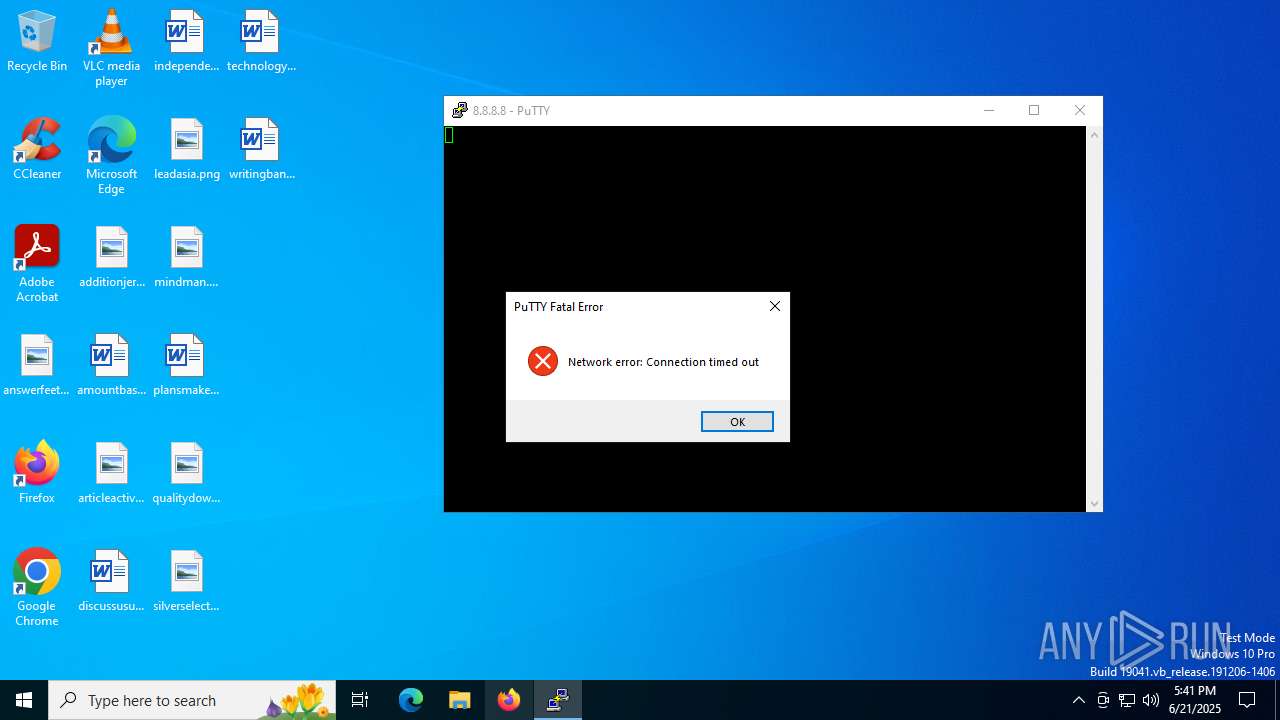
4192 | putty.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |