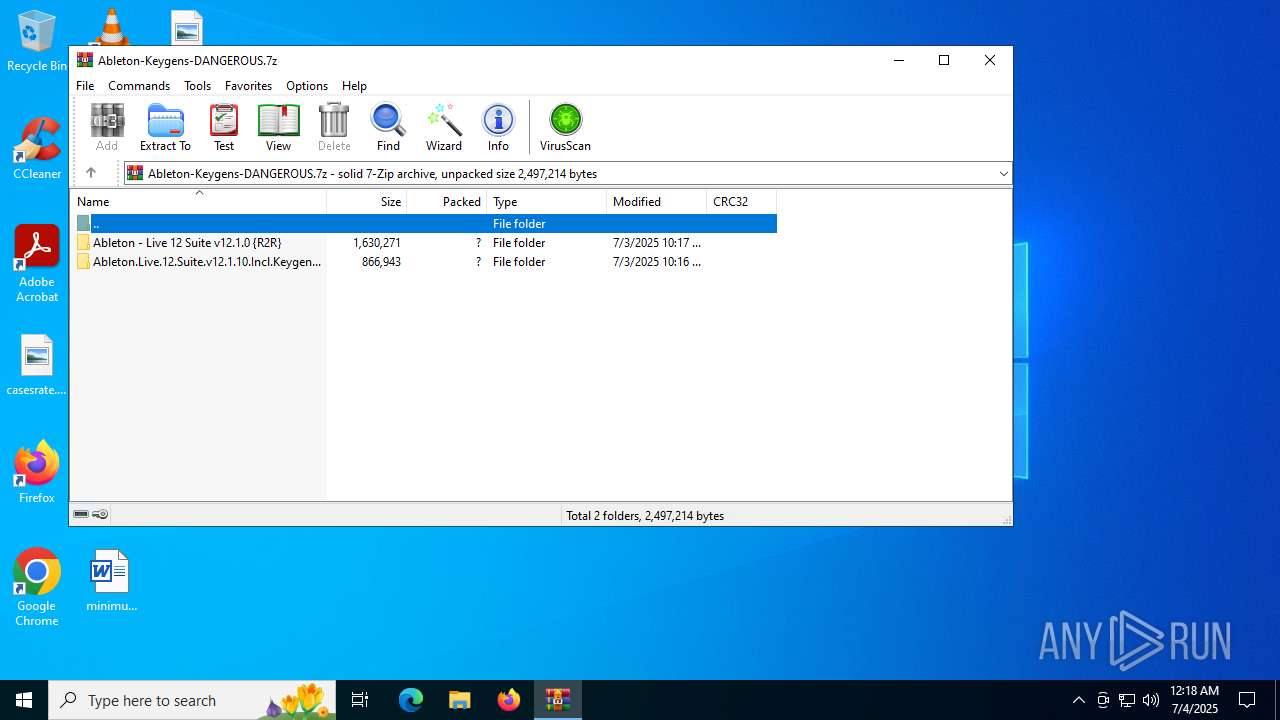
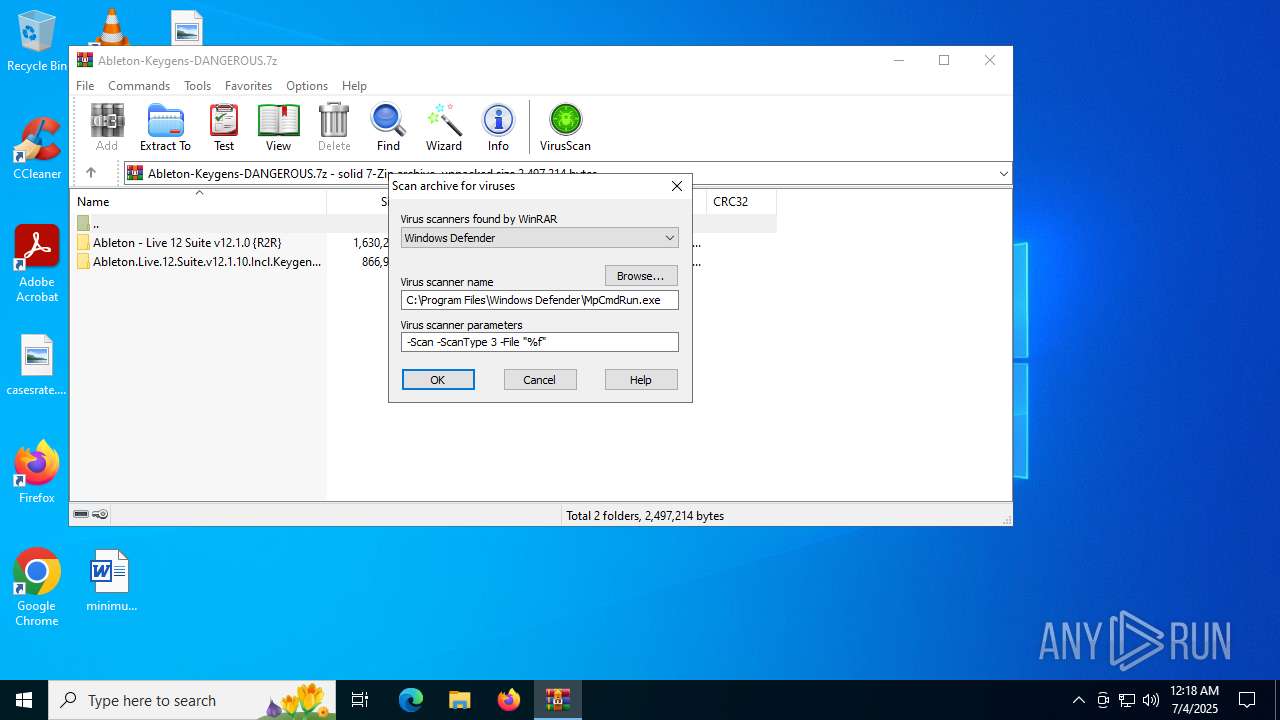
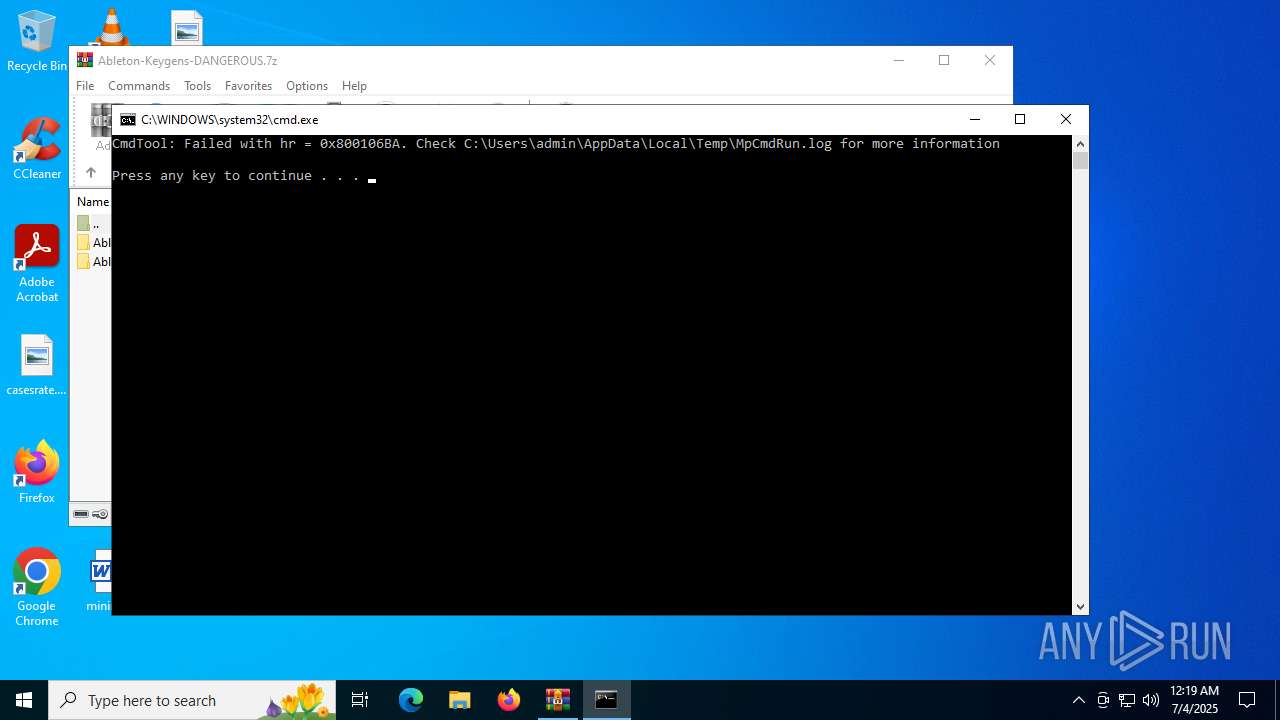
| File name: | Ableton-Keygens-DANGEROUS.7z |
| Full analysis: | https://app.any.run/tasks/7f0352e3-2fc5-4477-ba07-d3448ee5a541 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2025, 00:18:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | EDC8F910B9E754C547530208BC29CE43 |
| SHA1: | 64785FBCA919D062216E8160C1A46BF37E735668 |
| SHA256: | 1242DF3909757091B19001311ED965550430DD81D0B77335675D579AF065213E |
| SSDEEP: | 98304:zMtGLQCK7zxNsopAKCGWb2n9NBshOdHbMZmdKJWWqD7zkNUotjPCGWl2QONLilIv:zOY |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 4692)
SUSPICIOUS
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4692)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4692)
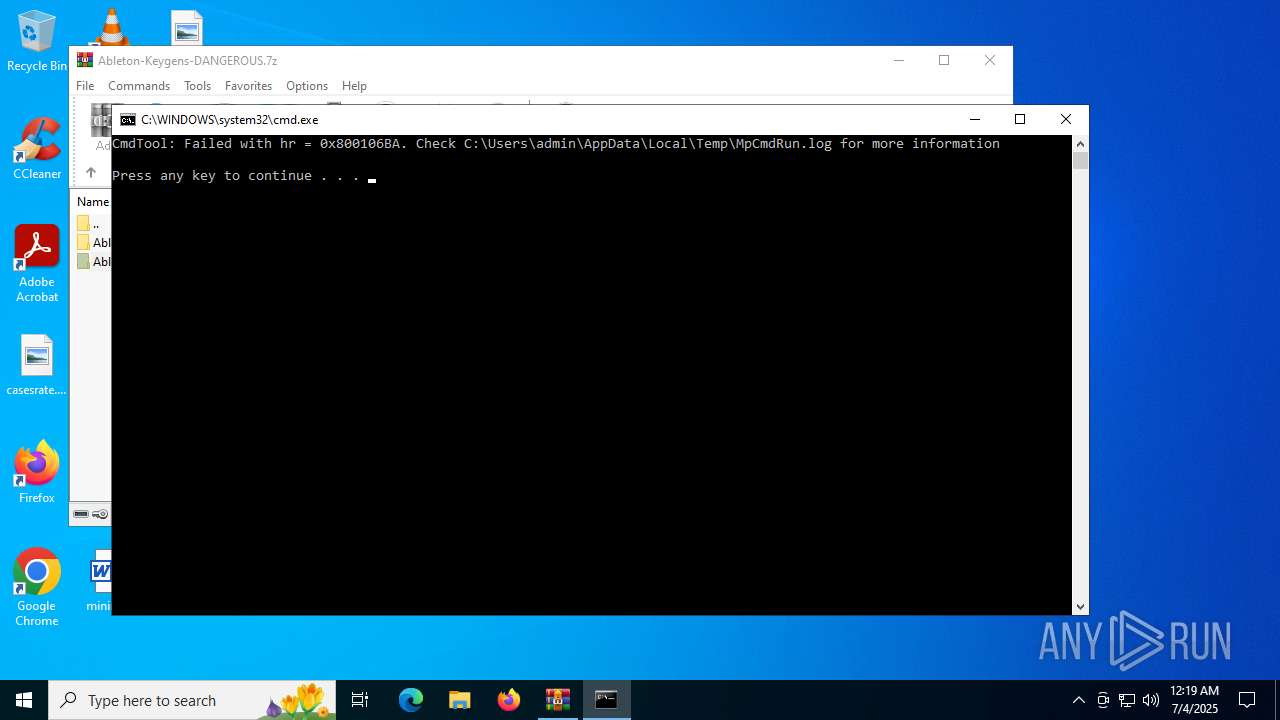
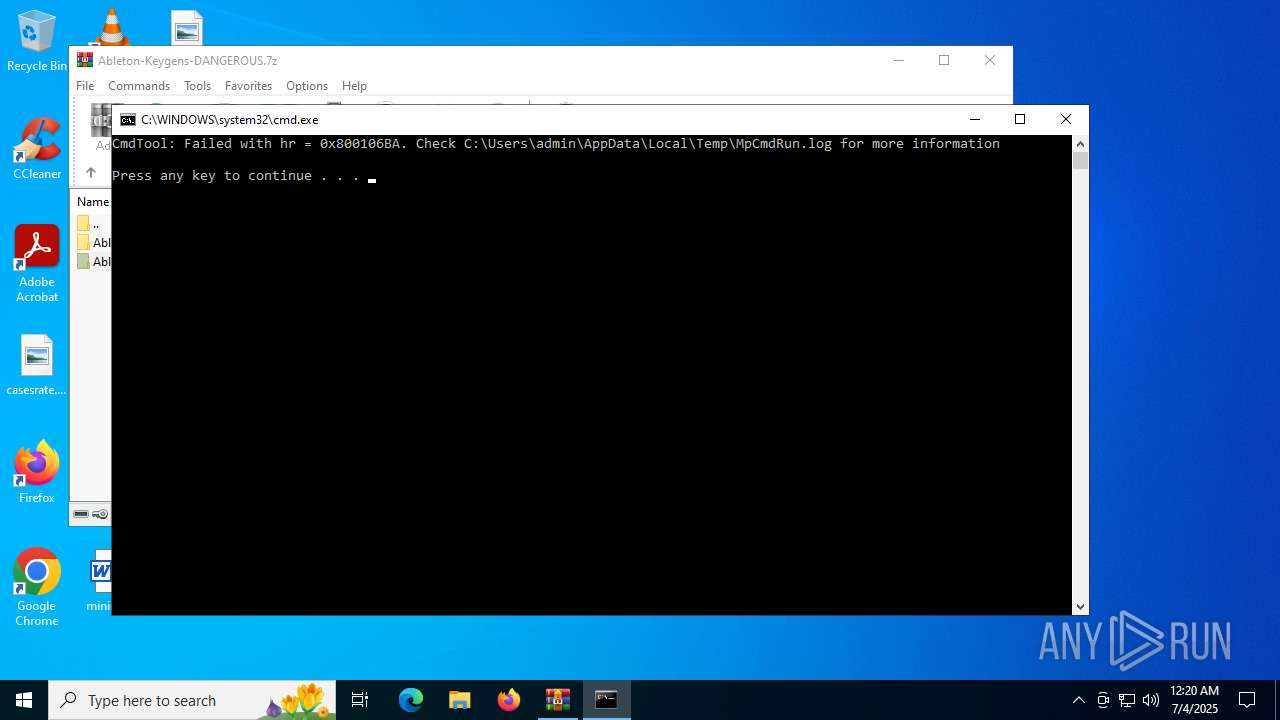
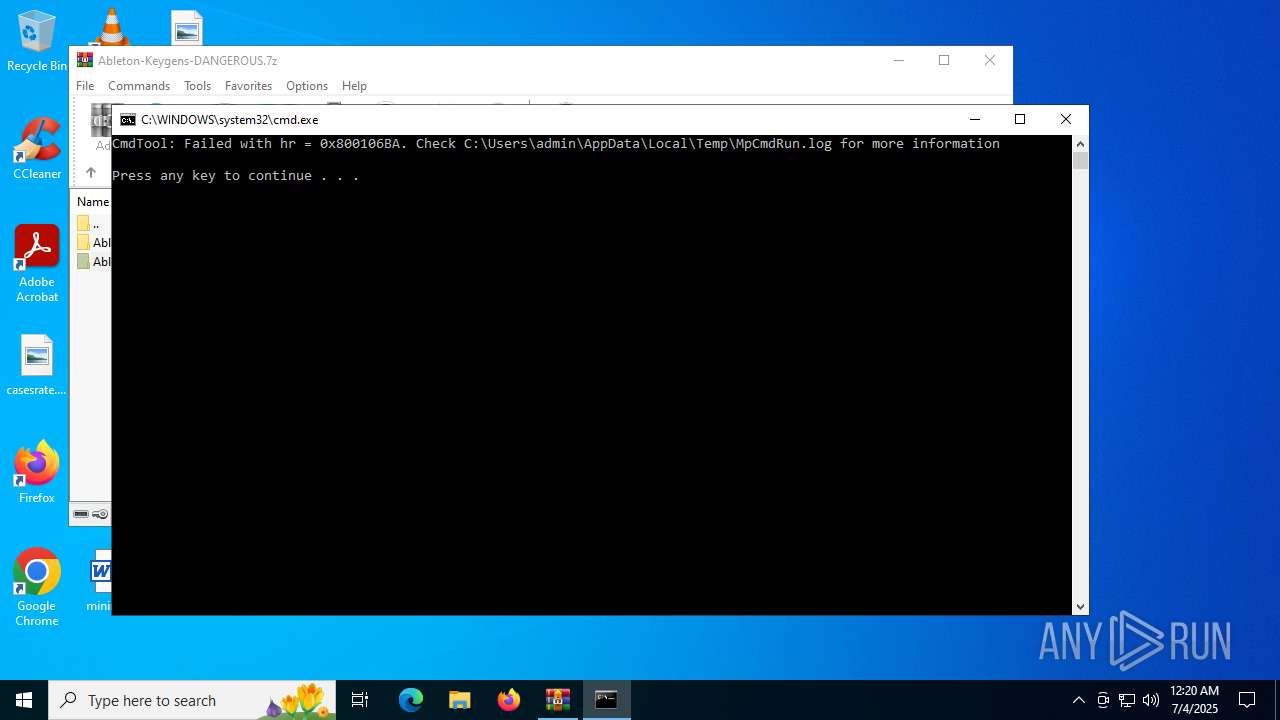
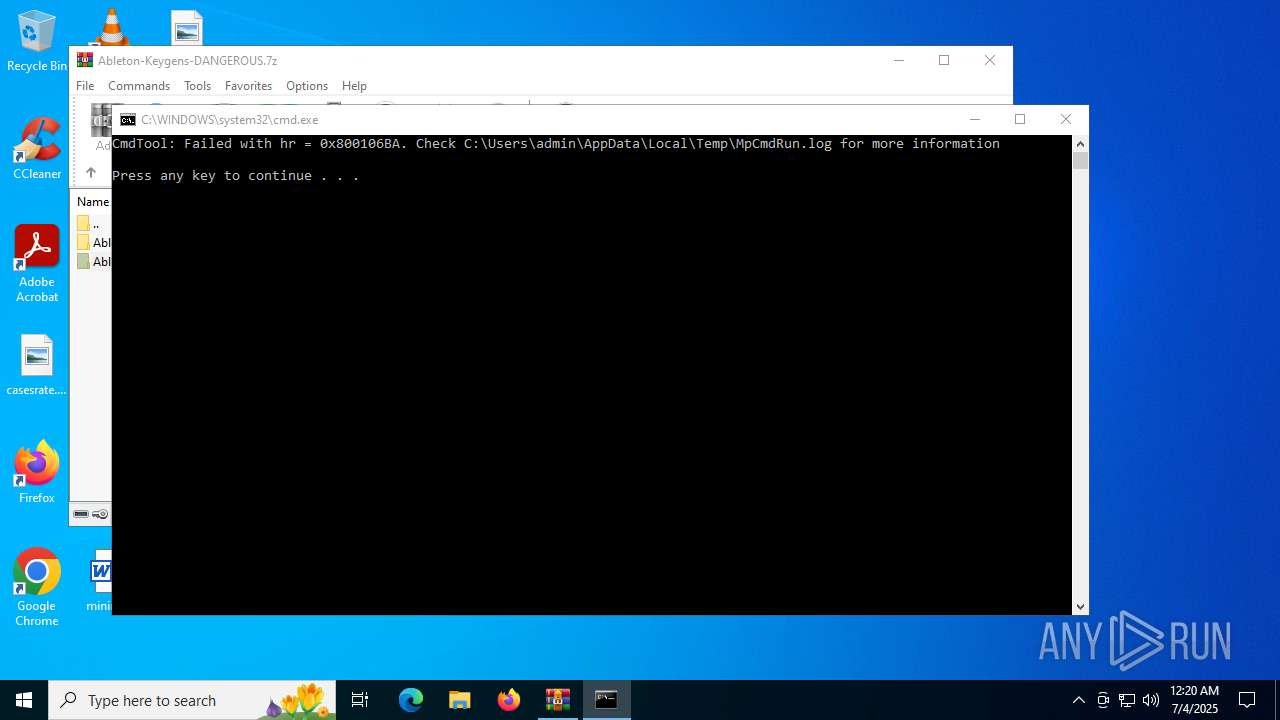
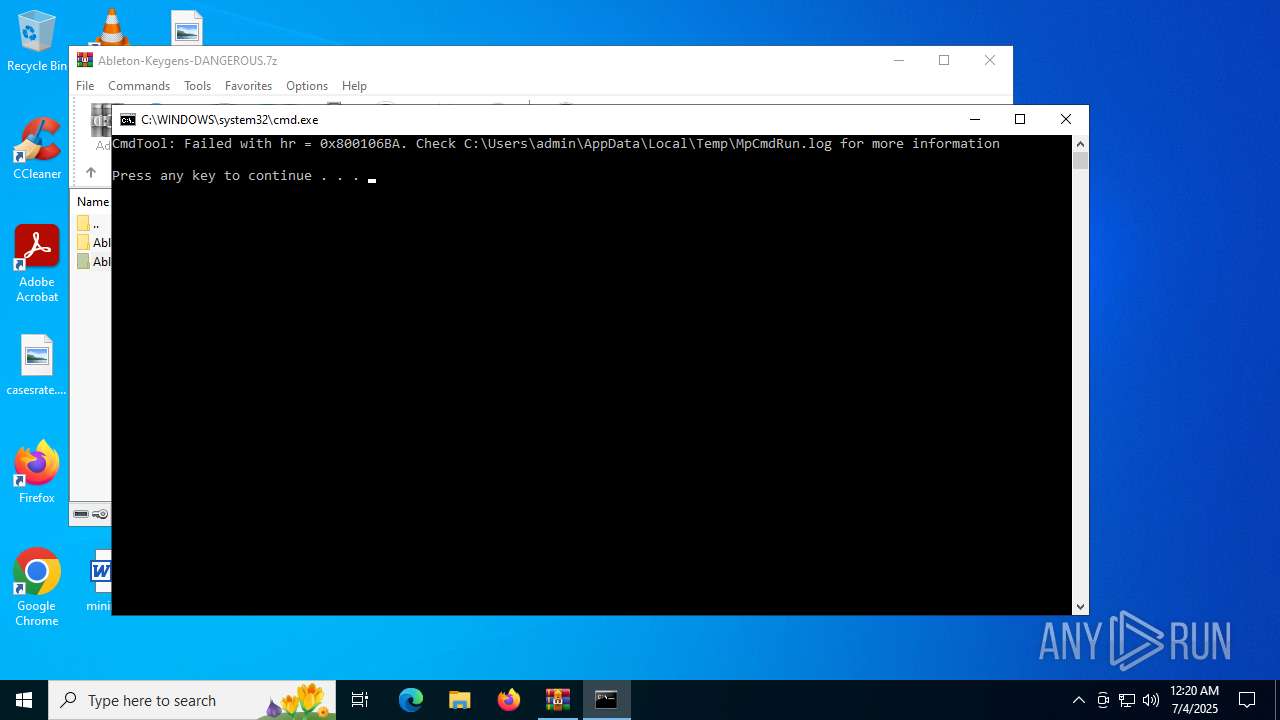
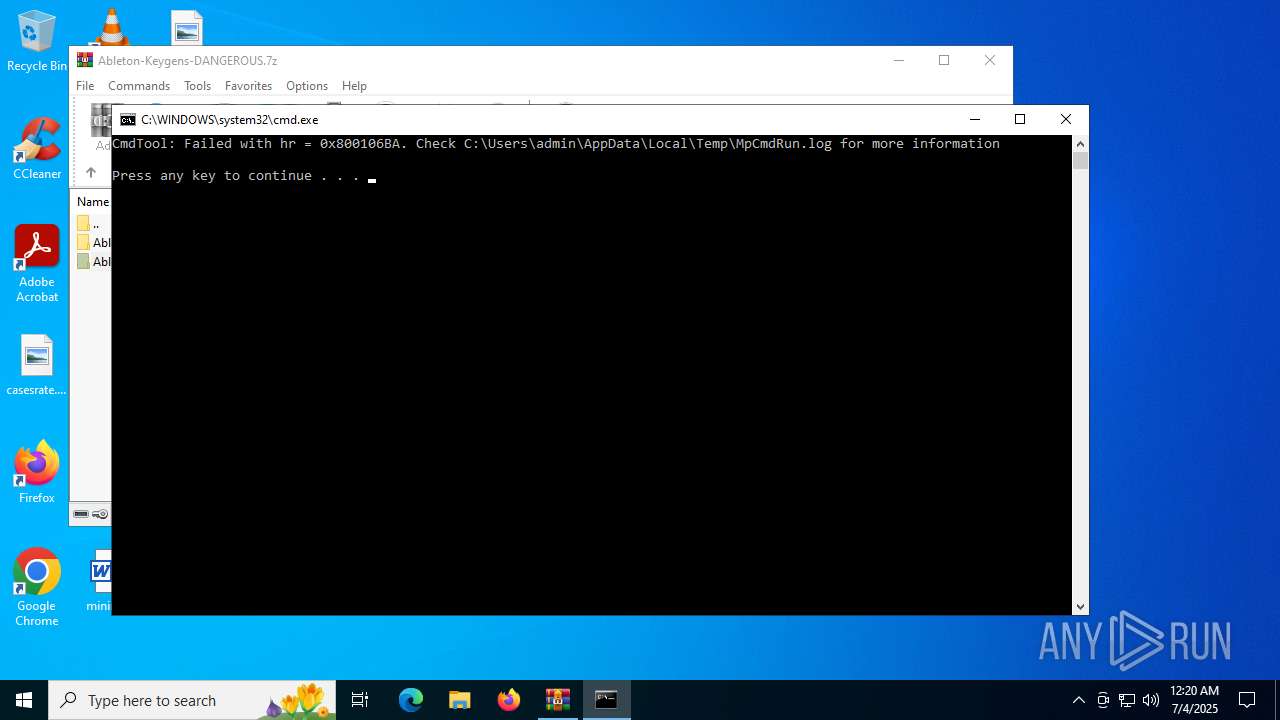
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4692)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4692)
Checks proxy server information
- slui.exe (PID: 4748)
Checks supported languages
- MpCmdRun.exe (PID: 6688)
Reads the computer name
- MpCmdRun.exe (PID: 6688)
Reads the software policy settings
- slui.exe (PID: 4748)
Create files in a temporary directory
- MpCmdRun.exe (PID: 6688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:07:03 22:17:06+00:00 |
| ArchivedFileName: | Ableton - Live 12 Suite v12.1.0 {R2R} |
Total processes
139
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1300 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Rar$Scan36115.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4692 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Ableton-Keygens-DANGEROUS.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4748 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6688 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 012
Read events
5 003
Write events
9
Delete events
0
Modification events
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Ableton-Keygens-DANGEROUS.7z | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
4
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton.Live.12.Suite.v12.1.10.Incl.Keygen-R2R\R2R\R2R.txt | text | |
MD5:2E4DB7AA5355A5684CF88CFB698C247B | SHA256:AA84A65A36C4A313E72D65A7625DC13EA23897E7B716FBD407F03C3939DBC241 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton - Live 12 Suite v12.1.0 {R2R}\Rutracker.nfo | text | |
MD5:96D222EC4DF8178BFB5E1CE269221976 | SHA256:BBFE3A060FBD016CA47EE5A64EEEBF20F780C419738EF8574BAD6039B9B793CF | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton - Live 12 Suite v12.1.0 {R2R}\R2R\R2R.txt | text | |
MD5:2E4DB7AA5355A5684CF88CFB698C247B | SHA256:AA84A65A36C4A313E72D65A7625DC13EA23897E7B716FBD407F03C3939DBC241 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton - Live 12 Suite v12.1.0 {R2R}\R2R\Keygen+VCRuntime Backup.7z | compressed | |
MD5:A84BA956733883BD35F863893A60C48D | SHA256:1074AA2F7827C1981A231F82732AFF9EF57A008B93C261799B58C38D5D55AFD6 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton.Live.12.Suite.v12.1.10.Incl.Keygen-R2R\R2R.nfo | text | |
MD5:E8C8200B310C5290BE948C1A6390184D | SHA256:F7357197FB2011968CC5C93A89888936E652CFA5CC62CC0D29283E328CF8A7B7 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton - Live 12 Suite v12.1.0 {R2R}\R2R\Ableton_KeyGen.exe | executable | |
MD5:E411DD01187DF2E61A273E651107B524 | SHA256:D613BBF19A5003A2C514056665F79C7C2C3AFF9D3712639F13078734FFFCAE5B | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton.Live.12.Suite.v12.1.10.Incl.Keygen-R2R\R2R\Ableton_KeyGen.exe | executable | |
MD5:7E1329F086BE6599D92CC72DE9BB7092 | SHA256:3E5A4418610A7B376714A235A49082645524B4162DDA27AE04529C21C26530B5 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton - Live 12 Suite v12.1.0 {R2R}\R2R\vcruntime140_1.dll | executable | |
MD5:F38BBB2DCEA08BE0AE9E8C4447E9CD58 | SHA256:A9D61D9FCEE0D83656757EB36A8586DE44D1E4F47BEBD13AFDBD474A47B82209 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Ableton-Keygens-DANGEROUS.7z\Ableton - Live 12 Suite v12.1.0 {R2R}\R2R\R2R.nfo | text | |
MD5:D06446E549804262BC9139FE4EAC079F | SHA256:2BD7496164C542F4216E31934B01DFB990D911AB95AB1809F1583E31B372721D | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4692.17128\Rar$Scan36115.bat | text | |
MD5:6740CA4011529CB23F68526F1A17ACA9 | SHA256:E0649EFA318400C1B33DC20F47BA67CE182102242EACF66991DCBD1C65B88818 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
45
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.4:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 52.165.164.15:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | POST | 200 | 40.126.31.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.131:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6024 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2292 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4572 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |