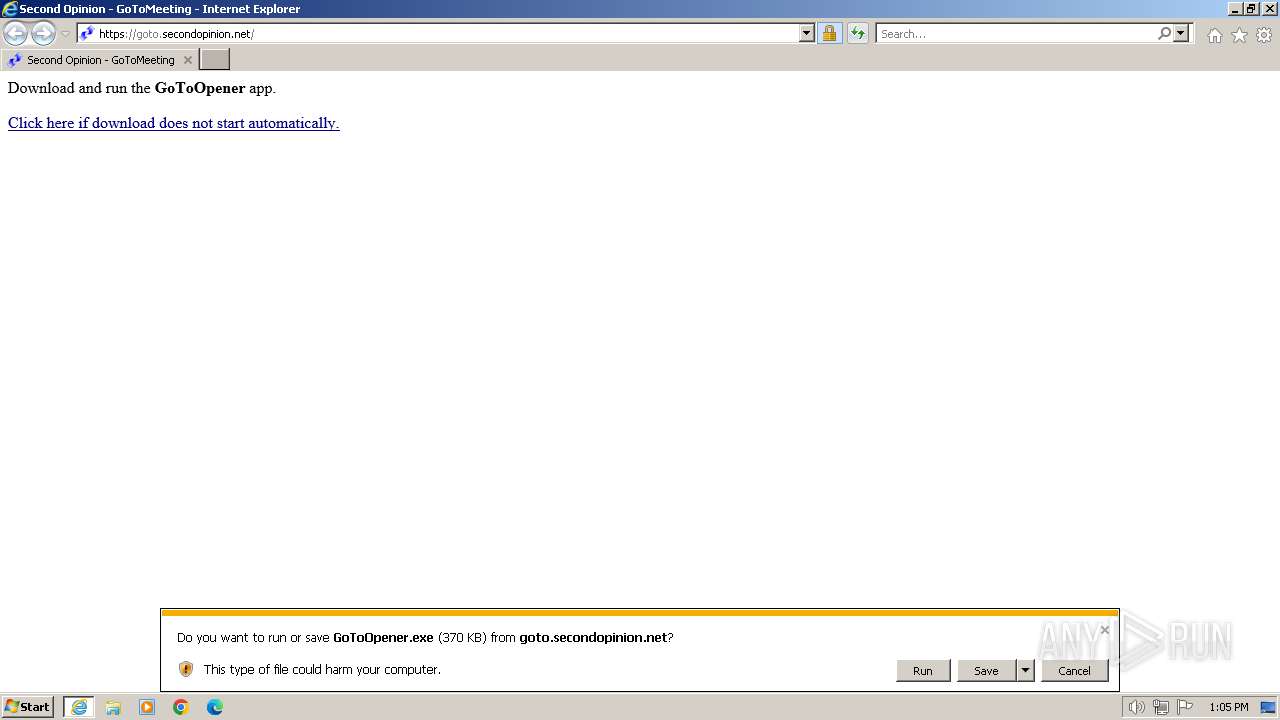
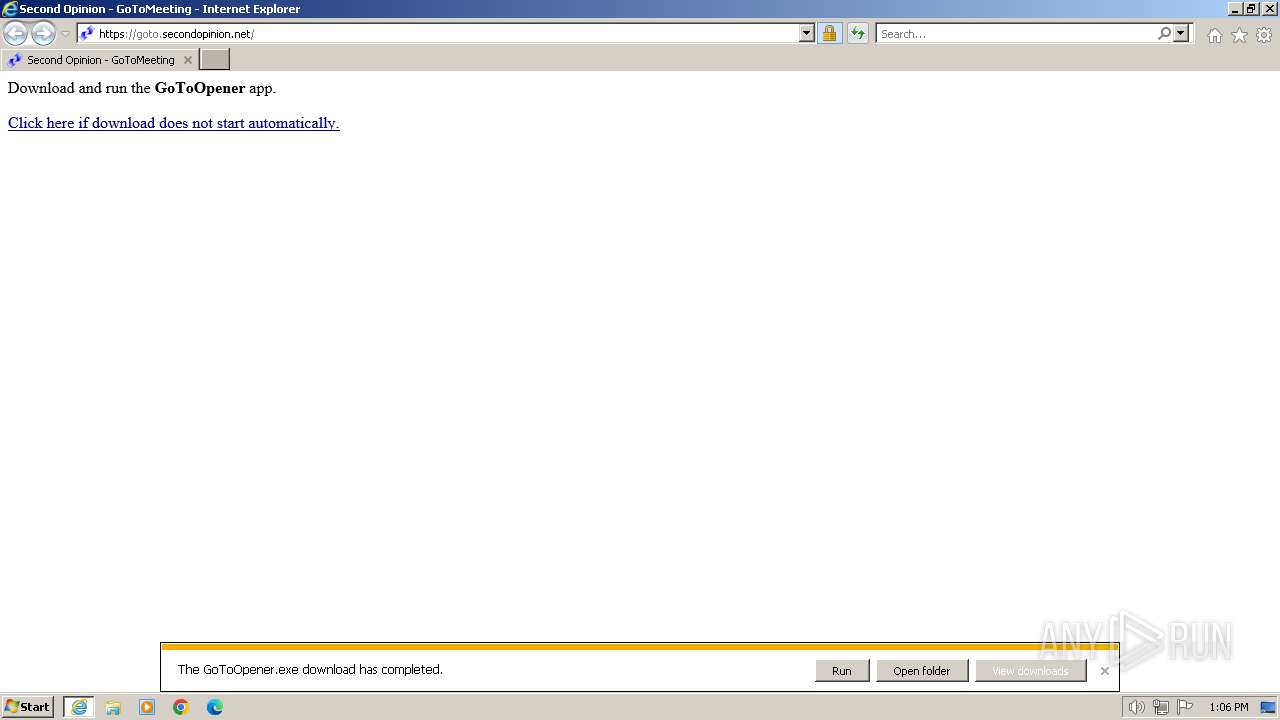
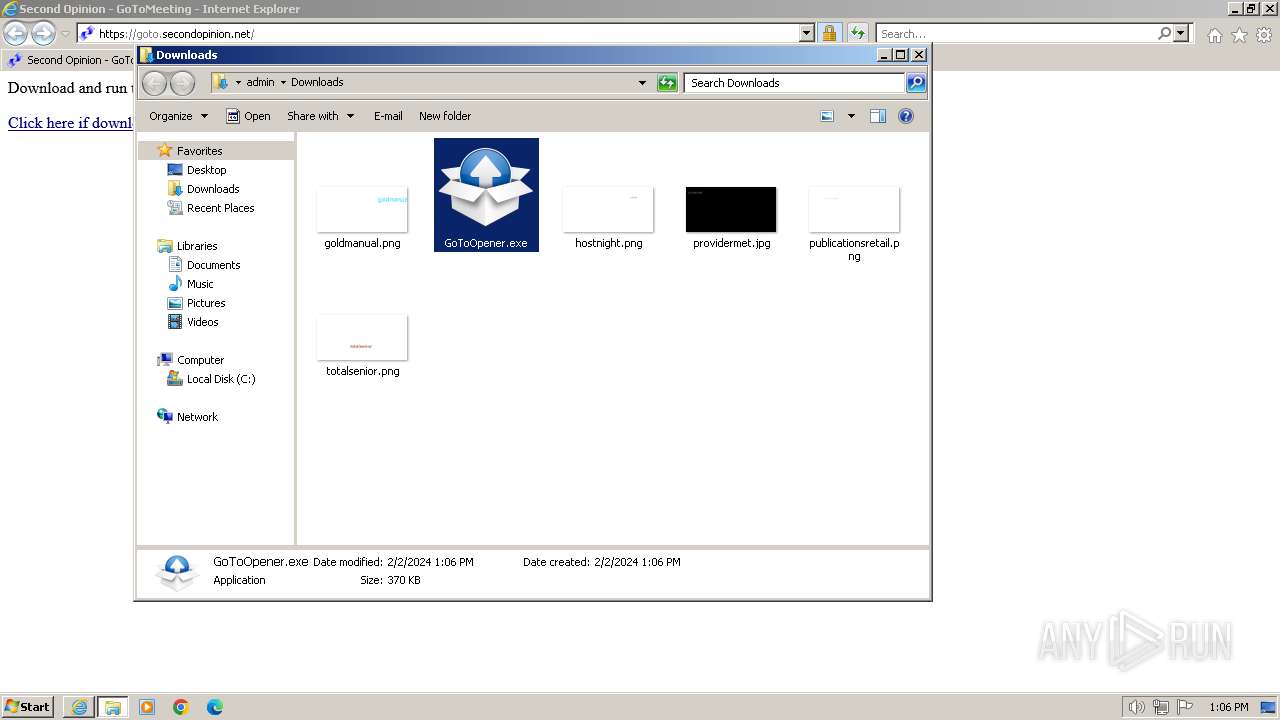
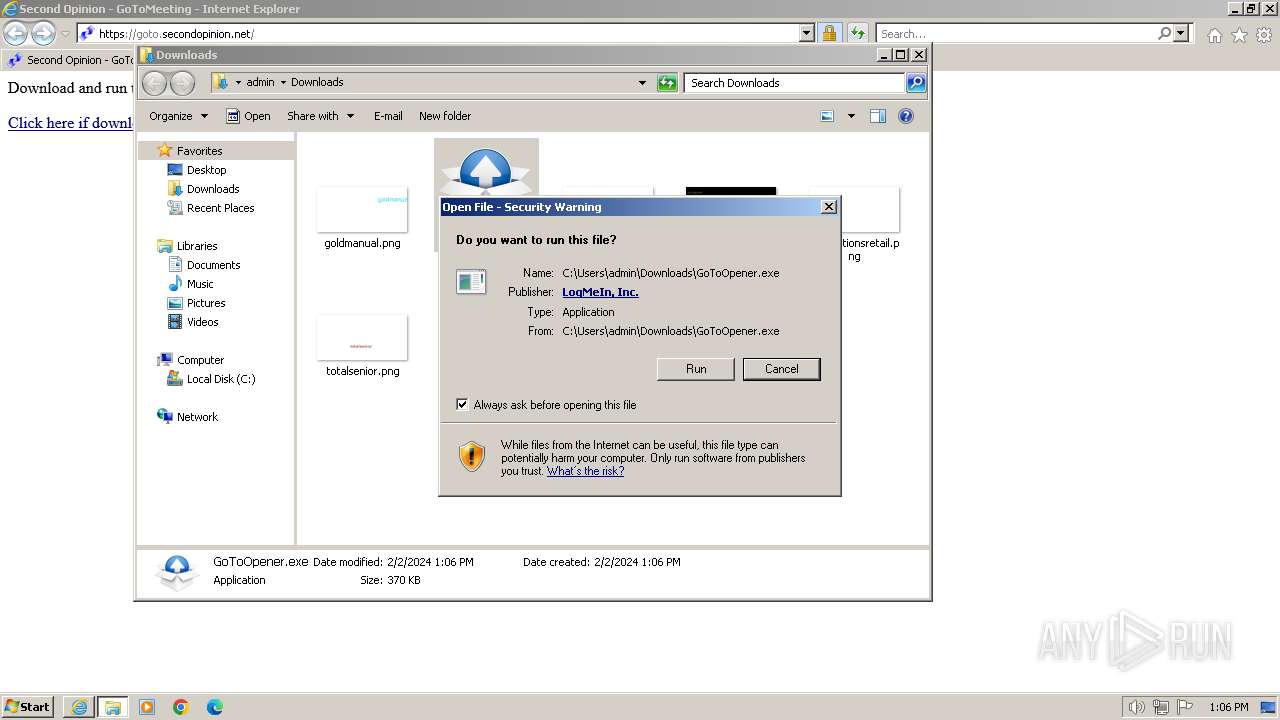
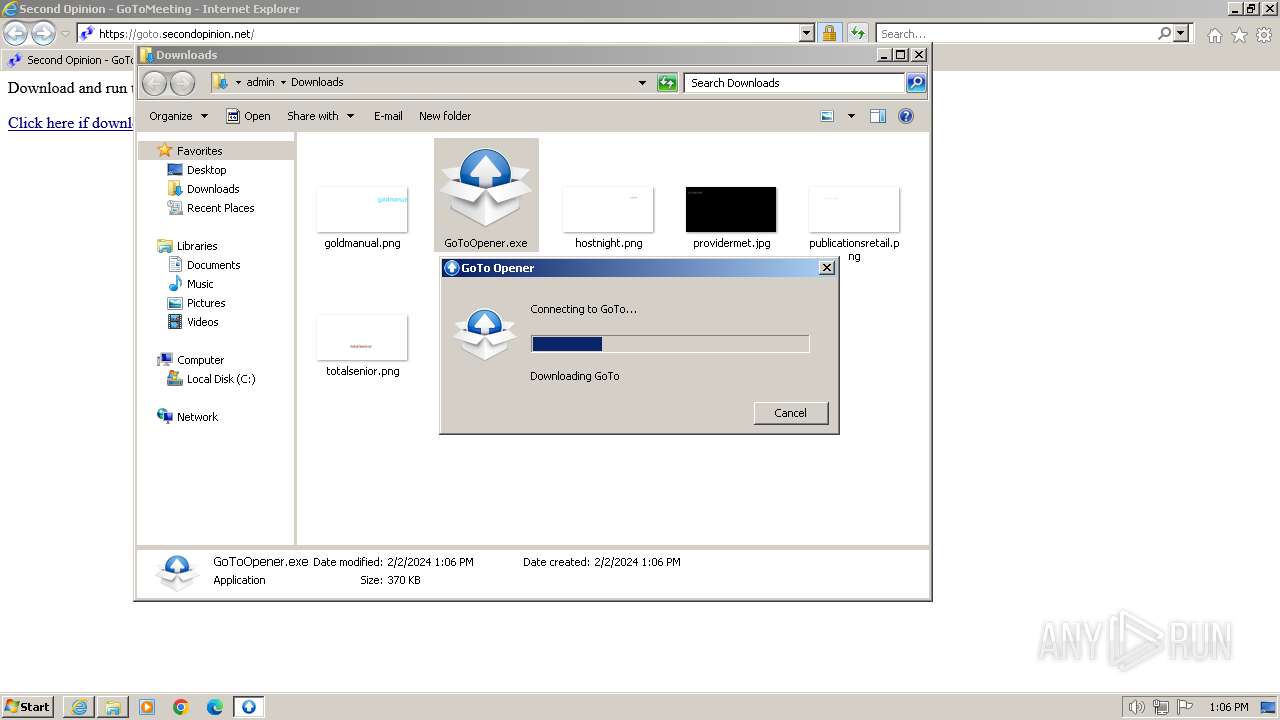
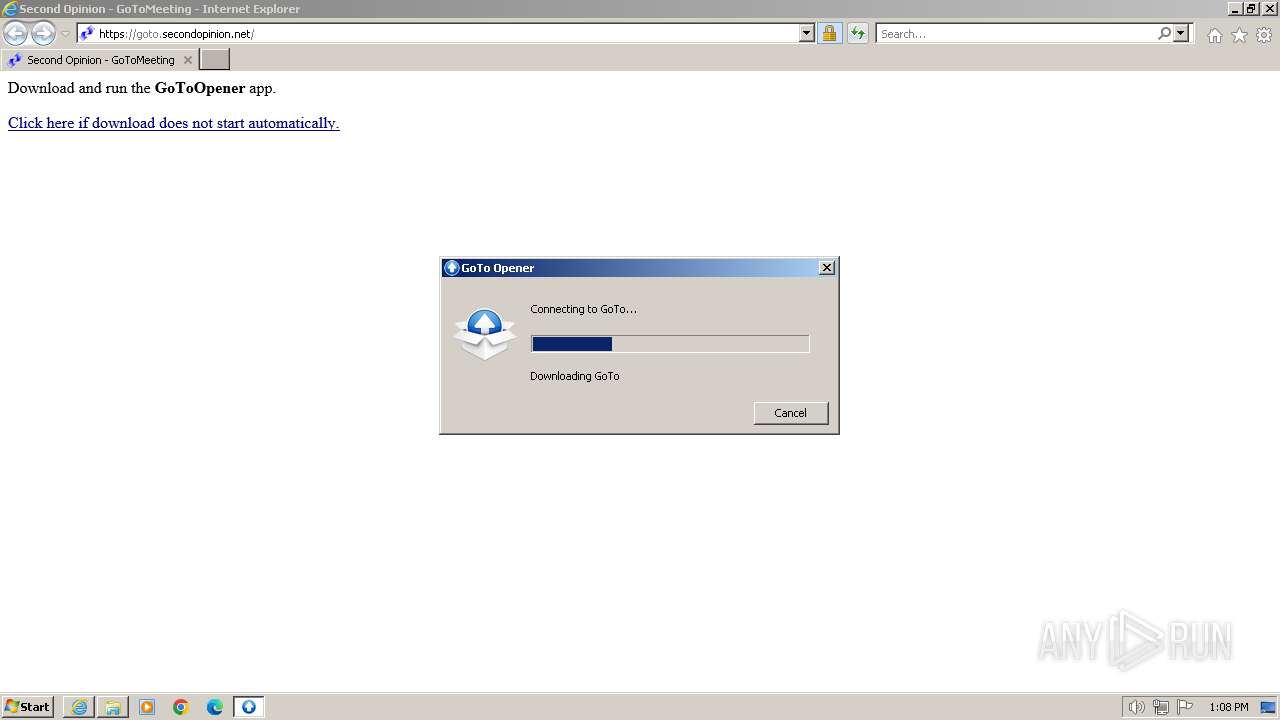
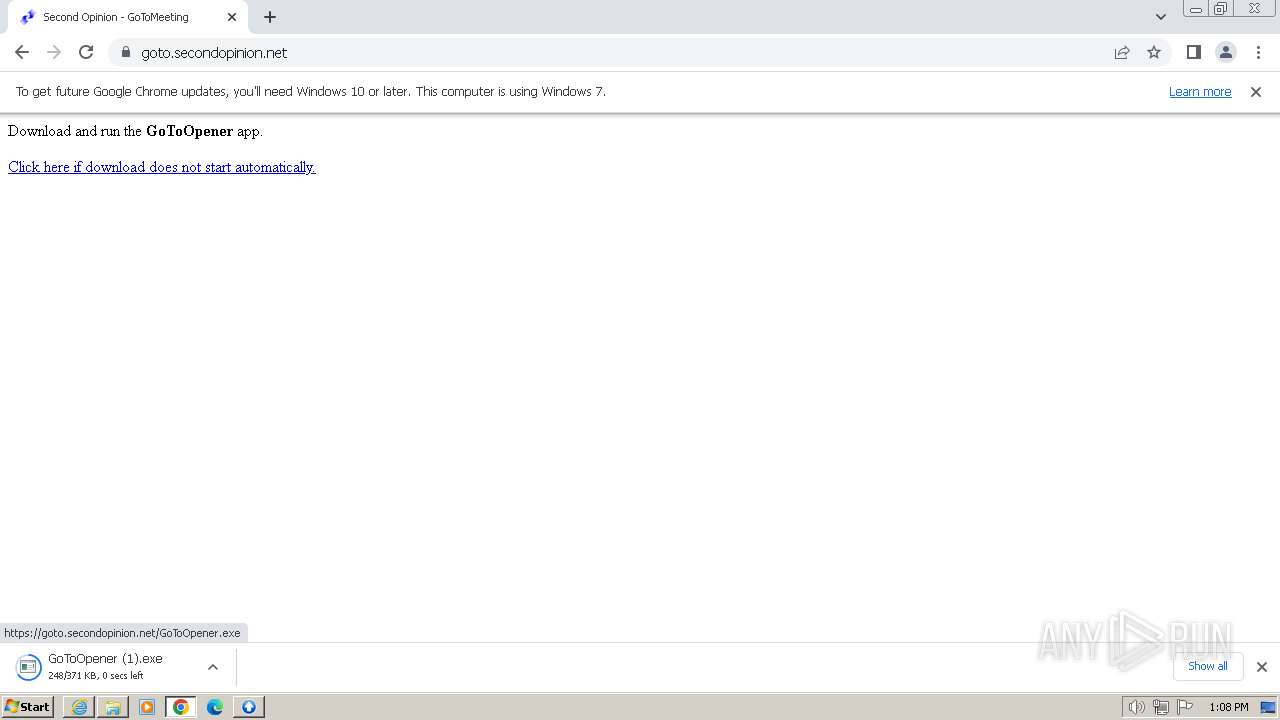
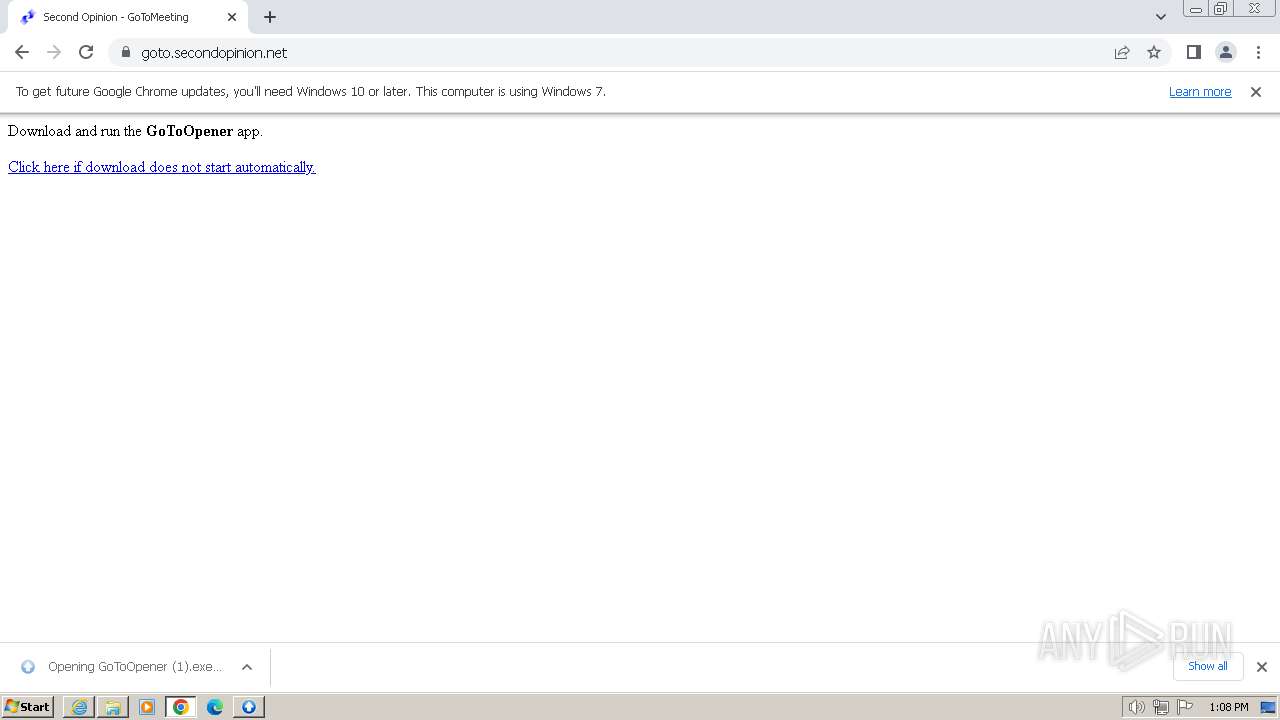
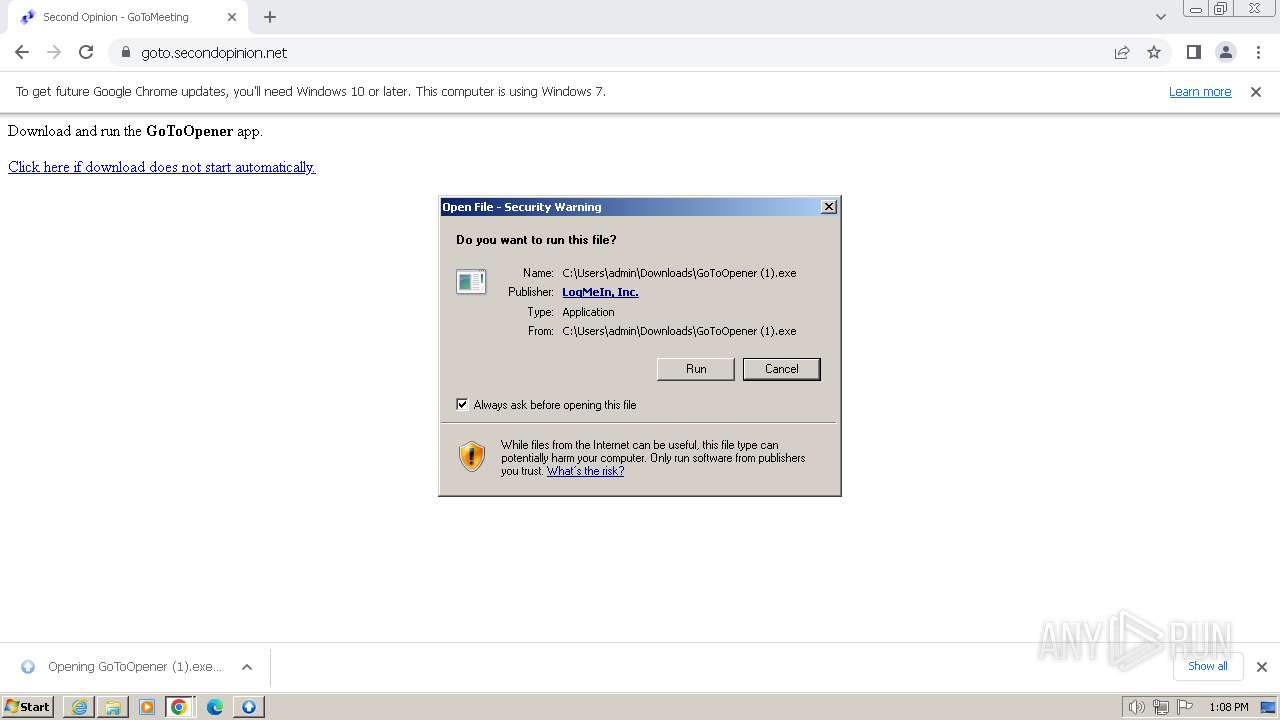
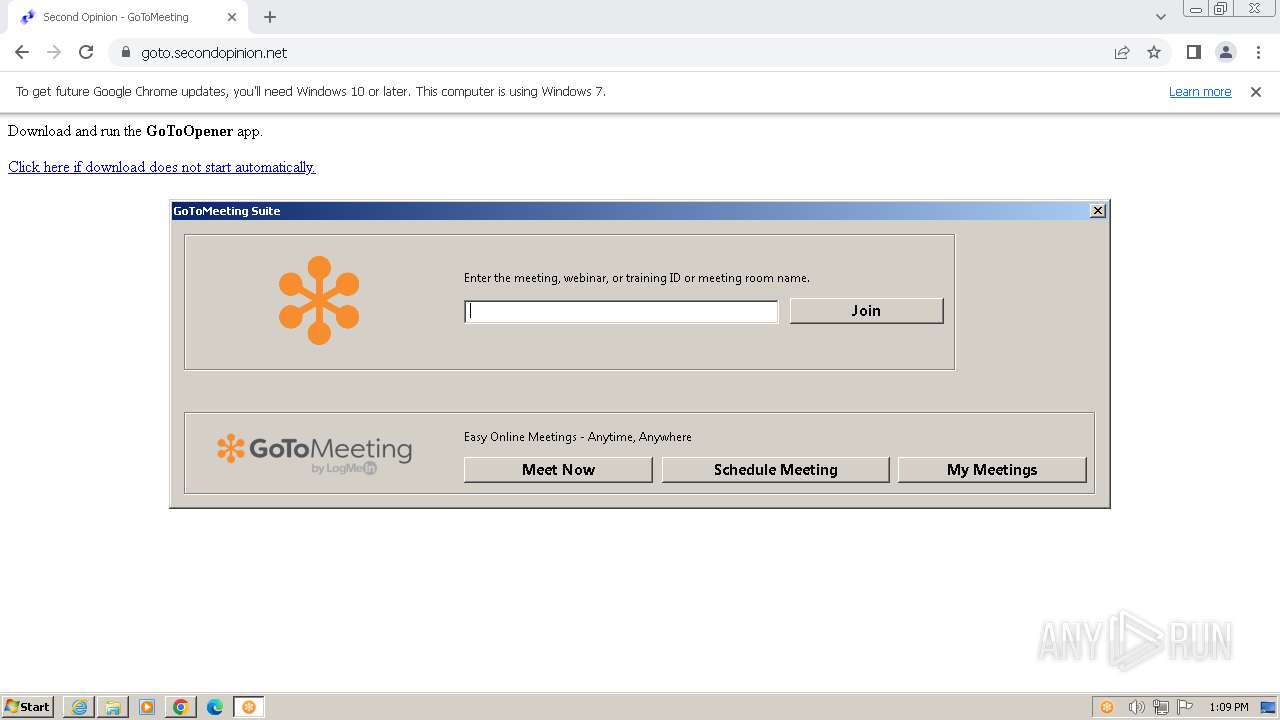
| URL: | https://goto.secondopinion.net/ |
| Full analysis: | https://app.any.run/tasks/2739119c-9220-4f05-828a-81c97ccd87d0 |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2024, 13:05:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E8F51EBEDDD20FE6BDB492FE99A15E0C |
| SHA1: | ECF14B85D75A4B1AA0CB111DA49C5C4D3C5D2DEE |
| SHA256: | 124041E5BC544B4AB3463AD2FEBC67F0269DD65C84970EB815DC719F83139EE3 |
| SSDEEP: | 3:N8ryd1H0Kn:24zn |
MALICIOUS
Drops the executable file immediately after the start
- GoToOpener.exe (PID: 3636)
- G2MCoreInstExtractor.exe (PID: 2936)
- G2MInstaller.exe (PID: 3272)
Registers / Runs the DLL via REGSVR32.EXE
- g2mlauncher.exe (PID: 3020)
- g2mlauncher.exe (PID: 2780)
Steals credentials from Web Browsers
- g2mcomm.exe (PID: 3056)
Actions looks like stealing of personal data
- g2mcomm.exe (PID: 3056)
SUSPICIOUS
Reads the Internet Settings
- GoToOpener.exe (PID: 3636)
- GoToOpener (1).exe (PID: 3688)
- G2MCoreInstExtractor.exe (PID: 2936)
- g2mlauncher.exe (PID: 3020)
- g2mcomm.exe (PID: 3056)
- g2mlauncher.exe (PID: 2780)
Executable content was dropped or overwritten
- GoToOpener.exe (PID: 3636)
- G2MCoreInstExtractor.exe (PID: 2936)
- G2MInstaller.exe (PID: 3272)
Checks Windows Trust Settings
- GoToOpener.exe (PID: 3636)
- g2mlauncher.exe (PID: 3020)
- g2mlauncher.exe (PID: 2780)
Reads security settings of Internet Explorer
- GoToOpener.exe (PID: 3636)
- g2mlauncher.exe (PID: 2780)
- g2mlauncher.exe (PID: 3020)
Reads settings of System Certificates
- GoToOpener.exe (PID: 3636)
- g2mcomm.exe (PID: 3056)
- g2mlauncher.exe (PID: 3020)
- g2mcomm.exe (PID: 3572)
- g2mlauncher.exe (PID: 2780)
Starts itself from another location
- G2MInstaller.exe (PID: 3272)
Uses RUNDLL32.EXE to load library
- G2MInstaller.exe (PID: 3272)
Connects to unusual port
- g2mcomm.exe (PID: 3056)
Executing commands from a ".bat" file
- GoToOpener.exe (PID: 3636)
Starts CMD.EXE for commands execution
- GoToOpener.exe (PID: 3636)
Reads Microsoft Outlook installation path
- g2mlauncher.exe (PID: 3020)
- g2mlauncher.exe (PID: 2780)
Reads Internet Explorer settings
- g2mlauncher.exe (PID: 3020)
- g2mlauncher.exe (PID: 2780)
INFO
Checks supported languages
- GoToOpener.exe (PID: 3636)
- GoToOpener (1).exe (PID: 3688)
- G2MInstaller.exe (PID: 3272)
- G2MInstaller.exe (PID: 2136)
- g2mstart.exe (PID: 1548)
- g2mcomm.exe (PID: 3056)
- g2mlauncher.exe (PID: 3020)
- g2mcomm.exe (PID: 3572)
- g2mlauncher.exe (PID: 2780)
- g2mstart.exe (PID: 2976)
- g2mupload.exe (PID: 2968)
- G2MCoreInstExtractor.exe (PID: 2936)
- g2mupload.exe (PID: 1056)
Manual execution by a user
- GoToOpener.exe (PID: 3636)
- chrome.exe (PID: 2996)
- g2mstart.exe (PID: 2976)
Drops the executable file immediately after the start
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 1604)
- chrome.exe (PID: 2996)
- chrome.exe (PID: 2844)
Reads the computer name
- GoToOpener.exe (PID: 3636)
- GoToOpener (1).exe (PID: 3688)
- G2MCoreInstExtractor.exe (PID: 2936)
- G2MInstaller.exe (PID: 3272)
- G2MInstaller.exe (PID: 2136)
- g2mstart.exe (PID: 1548)
- g2mcomm.exe (PID: 3056)
- g2mlauncher.exe (PID: 3020)
- g2mupload.exe (PID: 1056)
- g2mcomm.exe (PID: 3572)
- g2mlauncher.exe (PID: 2780)
- g2mstart.exe (PID: 2976)
- g2mupload.exe (PID: 2968)
Create files in a temporary directory
- GoToOpener.exe (PID: 3636)
- G2MCoreInstExtractor.exe (PID: 2936)
- G2MInstaller.exe (PID: 3272)
- g2mstart.exe (PID: 1548)
- g2mcomm.exe (PID: 3056)
- g2mlauncher.exe (PID: 3020)
- g2mupload.exe (PID: 1056)
- g2mcomm.exe (PID: 3572)
- g2mlauncher.exe (PID: 2780)
- g2mstart.exe (PID: 2976)
- g2mupload.exe (PID: 2968)
Process checks whether UAC notifications are on
- GoToOpener.exe (PID: 3636)
- GoToOpener (1).exe (PID: 3688)
- G2MCoreInstExtractor.exe (PID: 2936)
- G2MInstaller.exe (PID: 3272)
- g2mstart.exe (PID: 1548)
- g2mcomm.exe (PID: 3056)
- g2mlauncher.exe (PID: 3020)
- g2mcomm.exe (PID: 3572)
- g2mstart.exe (PID: 2976)
- g2mupload.exe (PID: 2968)
- g2mupload.exe (PID: 1056)
- g2mlauncher.exe (PID: 2780)
Reads the machine GUID from the registry
- GoToOpener.exe (PID: 3636)
- g2mcomm.exe (PID: 3056)
- g2mlauncher.exe (PID: 3020)
- g2mcomm.exe (PID: 3572)
- g2mlauncher.exe (PID: 2780)
- g2mupload.exe (PID: 2968)
- g2mupload.exe (PID: 1056)
Checks proxy server information
- GoToOpener.exe (PID: 3636)
- GoToOpener (1).exe (PID: 3688)
- g2mlauncher.exe (PID: 3020)
- g2mcomm.exe (PID: 3056)
- g2mlauncher.exe (PID: 2780)
Executable content was dropped or overwritten
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 1604)
- chrome.exe (PID: 2844)
- chrome.exe (PID: 2996)
Application launched itself
- iexplore.exe (PID: 572)
- chrome.exe (PID: 2996)
The process uses the downloaded file
- iexplore.exe (PID: 572)
- chrome.exe (PID: 392)
- chrome.exe (PID: 2996)
Creates files or folders in the user directory
- GoToOpener.exe (PID: 3636)
- G2MInstaller.exe (PID: 3272)
- g2mlauncher.exe (PID: 3020)
- g2mlauncher.exe (PID: 2780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
88
Monitored processes
40
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3852 --field-trial-handle=1172,i,2687131422317442279,5042769410788993151,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://goto.secondopinion.net/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\AppData\Local\GoToMeeting\19228\g2mupload.exe" "Action=GenCrashDump&ExPointers=02B2F880&HEventReady=G2MExceptionHandler-89A2D1A9-FDD2-47A7-81A9-7829F2BBDC63&LogFolder=c%3a%5cusers%5cadmin%5cappdata%5clocal%5ctemp%5clogmeinlogs%5cgotomeeting%5c19228%5c2024-02-02_13.09.15.221%5c&ProcessId=3020&ThreadId=3432" | C:\Users\admin\AppData\Local\GoToMeeting\19228\g2mupload.exe | — | g2mlauncher.exe | |||||||||||
User: admin Company: LogMeIn, Inc. Integrity Level: MEDIUM Description: GoToMeeting Exit code: 0 Version: 10.15.0 Build 19228 Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=2836 --field-trial-handle=1172,i,2687131422317442279,5042769410788993151,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1548 | "C:\Users\admin\AppData\Local\GoToMeeting\19228\g2mstart.exe" "/Action Host" "/Defaults 831" "/DidInstall True" "/EGWAddress 216.115.208.230" "/EGWDNS egwglobal.gotomeeting.com" "/EGWPort 80,443,8200" "/MeetingEnabled true" "/Mode normal" "/Product g2m" "/colClientUiReadyEvent Global\29B5D331-0A8A-4231-8B6D-0703112E3838" "/env live" "/sessionTrackingId clsInstall-a0f761f4-3578-421c-8695-7e38bcc0b77c" | C:\Users\admin\AppData\Local\GoToMeeting\19228\g2mstart.exe | — | G2MInstaller.exe | |||||||||||
User: admin Company: LogMeIn, Inc. Integrity Level: MEDIUM Description: GoToMeeting Exit code: 0 Version: 10.15.0 Build 19228 Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:572 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2144 --field-trial-handle=1172,i,2687131422317442279,5042769410788993151,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1808 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3656 --field-trial-handle=1172,i,2687131422317442279,5042769410788993151,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1480 --field-trial-handle=1172,i,2687131422317442279,5042769410788993151,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1100 --field-trial-handle=1172,i,2687131422317442279,5042769410788993151,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
52 452
Read events
52 057
Write events
380
Delete events
15
Modification events
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (572) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
58
Suspicious files
99
Text files
68
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\GoToOpener[1].exe | executable | |
MD5:43AD0D4441DBF73628E7B90C9DDA161C | SHA256:32D871F628DA3FC3BC1EB7E6073B6EB6324DA5700F84EBF2826291AAAB6F2107 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:E38D32113B8D4F89E452CE180A7D6257 | SHA256:2CF781F07FC6DA0DA6A56AFE37E61D930C502DC5B6F639569F99690DE18E5E58 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\jquery-1.7.1.min[1].js | html | |
MD5:DDB84C1587287B2DF08966081EF063BF | SHA256:88171413FC76DDA23AB32BAA17B11E4FFF89141C633ECE737852445F1BA6C1BD | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:608B181C27D81F1EB67E52A62A5B27A6 | SHA256:3127900225518FD7C717266520271F7399DF506820E50105D31B0CA0FEFA3188 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:2C635DABC8EADD28B9E394EEFC853D99 | SHA256:C4133A51A1FEB8D0353EB34A2F8C790368D66999CE177E51BCEAE9911FE58797 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon-32x32[1].png | image | |
MD5:E8895937D32B58D8D630834AAAC99005 | SHA256:F50A063657210CEE553D2BE21B214F8CE2201D66402A0A5048535F1D538C597F | |||
| 572 | iexplore.exe | C:\Users\admin\Downloads\GoToOpener.exe.phxv2j1.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\1GB91UC5.htm | html | |
MD5:980BDBDA6D1FD6249DCCDDD5D8C37442 | SHA256:281BEA14548A51258B6B3A94600C980FA5EA94C477E399754CE01F3F2E6B219D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
74
DNS requests
59
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1604 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
1604 | iexplore.exe | GET | 304 | 23.32.238.209:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bd6d7f2a69dae365 | unknown | — | — | unknown |
1604 | iexplore.exe | GET | 304 | 23.32.238.209:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?245ab6ffaf4de696 | unknown | — | — | unknown |
572 | iexplore.exe | GET | 304 | 23.32.238.209:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3867b918e511e106 | unknown | — | — | unknown |
572 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
1080 | svchost.exe | GET | 200 | 23.32.238.233:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fc91d912a85a08d5 | unknown | compressed | 65.2 Kb | unknown |
3636 | GoToOpener.exe | GET | 200 | 108.138.34.92:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
572 | iexplore.exe | GET | 304 | 23.32.238.209:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2f21ede4db813e6d | unknown | — | — | unknown |
572 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
572 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1604 | iexplore.exe | 13.56.64.10:443 | goto.secondopinion.net | AMAZON-02 | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1604 | iexplore.exe | 23.32.238.209:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1604 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
572 | iexplore.exe | 13.56.64.10:443 | goto.secondopinion.net | AMAZON-02 | US | unknown |
572 | iexplore.exe | 23.32.238.209:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
572 | iexplore.exe | 23.36.162.68:443 | www.bing.com | Akamai International B.V. | DE | unknown |
572 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
goto.secondopinion.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
launch.getgo.com |
| whitelisted |
join.servers.getgo.com |
| unknown |
Threats
Process | Message |
|---|---|
GoToOpener.exe | C:\Windows\system32\USER32.DLL |
GoToOpener.exe | C:\Windows\system32\SECUR32.DLL |
GoToOpener.exe | |
GoToOpener.exe | C:\Windows\system32\RPCRT4.DLL |
GoToOpener.exe | |
GoToOpener.exe | C:\Windows\system32\SECUR32.DLL |
GoToOpener.exe | C:\Windows\system32\WINTYPES.DLL |
GoToOpener.exe | C:\Windows\system32\MSVCRT.DLL |
GoToOpener.exe | |
GoToOpener.exe | |