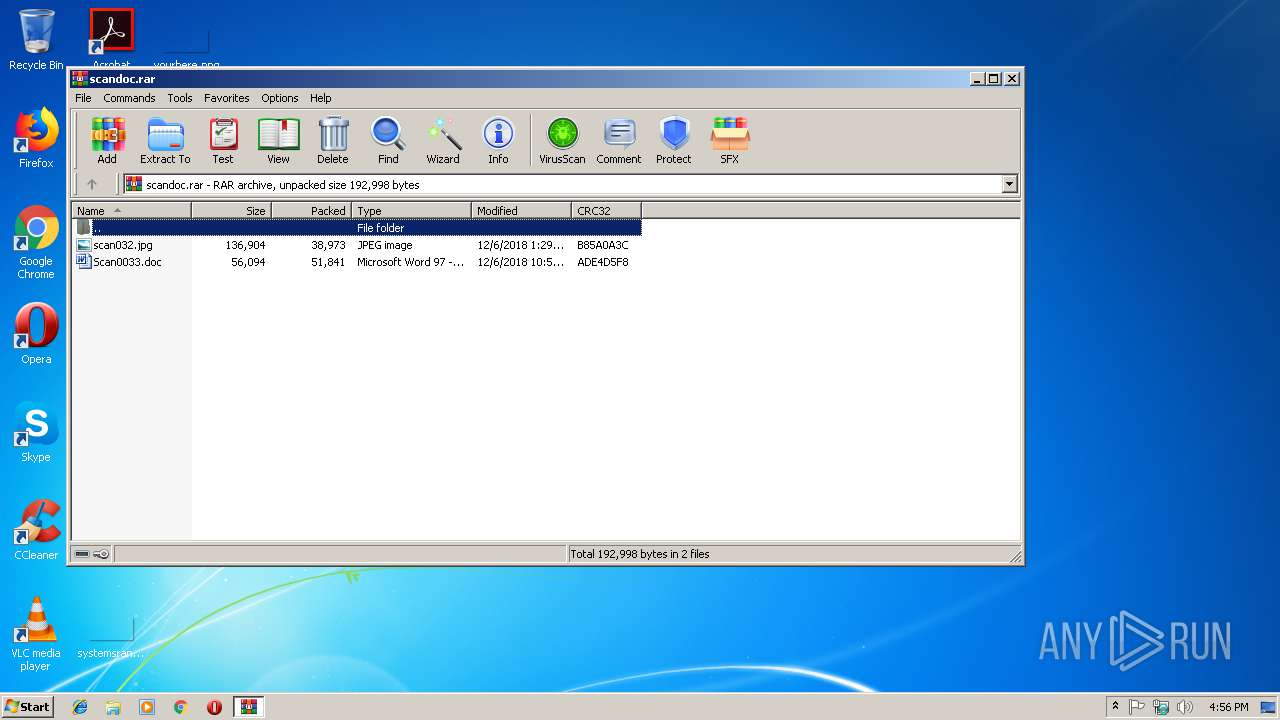
| File name: | scandoc.rar |
| Full analysis: | https://app.any.run/tasks/d3ae3a44-8b55-47b7-bf83-60925dcd1e7f |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 16:56:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 63F8B148B240503F8A7B93A83DDDC04B |
| SHA1: | 8A11A2D727695A9FDFC8B19A84D3E60066EBB84F |
| SHA256: | 1232402BEF625DC8328ECE768E9943667389AED97207CF24F5215FE88B5F88EC |
| SSDEEP: | 1536:01jMMIu/7LPqqvQ7fh+FTB9dYsnEguWz79ALasPmQEhW5xf7nzGMO:qMcDLiqIl+F7GWfaLasedwjf/Gd |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3148)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3148)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 2960)
Executable content was dropped or overwritten
- Rar.exe (PID: 3080)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3148)
Creates files in the user directory
- WINWORD.EXE (PID: 3148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1376 | C:\WINDOWS\system32\cmd.exe /c set path=%ProgramFiles(x86)%\WinRAR;C:\Program Files\WinRAR; && cd /d %~dp0 & rar.exe e -o+ -r -inul *.rar scan032.jpg & rar.exe e -o+ -r -inul scan032.jpg backup.exe & backup.exe | C:\WINDOWS\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2960 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\scandoc.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3048 | rar.exe e -o+ -r -inul scan032.jpg backup.exe | C:\Program Files\WinRAR\Rar.exe | — | cmd.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: Command line RAR Exit code: 10 Version: 5.60.0 Modules
| |||||||||||||||
| 3080 | rar.exe e -o+ -r -inul *.rar scan032.jpg | C:\Program Files\WinRAR\Rar.exe | cmd.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: Command line RAR Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3148 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIa2960.41029\Scan0033.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 316
Read events
1 256
Write events
56
Delete events
4
Modification events
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\scandoc.rar | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1300627479 | |||
| (PID) Process: | (3148) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | v0 |
Value: 763020004C0C0000010000000000000000000000 | |||
Executable files
1
Suspicious files
1
Text files
0
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3148 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB876.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3148 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C053A636.png | — | |
MD5:— | SHA256:— | |||
| 3148 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\9BE59C25.wmf | — | |
MD5:— | SHA256:— | |||
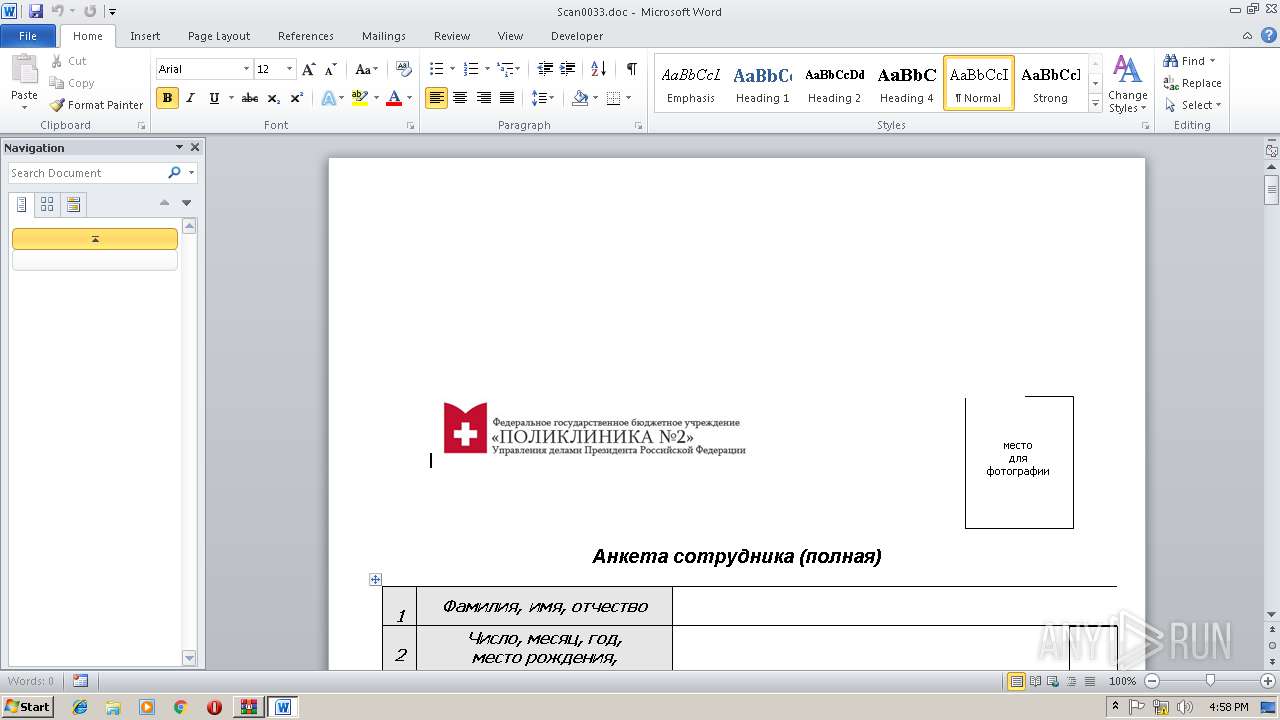
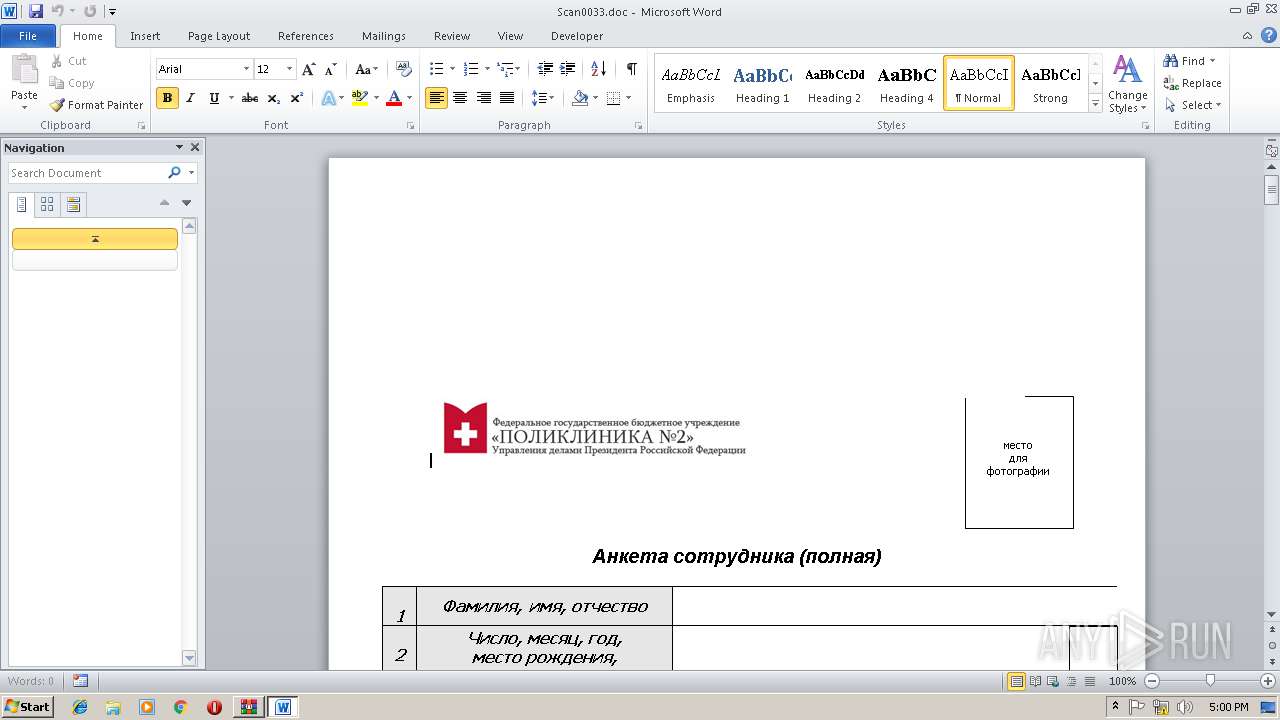
| 2960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2960.41029\Scan0033.doc | document | |
MD5:— | SHA256:— | |||
| 3148 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol | sol | |
MD5:— | SHA256:— | |||
| 3148 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIa2960.41029\~$an0033.doc | pgc | |
MD5:— | SHA256:— | |||
| 3148 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3148 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sxx | sol | |
MD5:0DD3631A4DF7BED11E4B389AC2E95882 | SHA256:F06E531C2FEB84B511F7FEED945C13936122AA2A6DCE287776F724398D27394A | |||
| 3148 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\ShockwaveFlashObjects.exd | tlb | |
MD5:— | SHA256:— | |||
| 3080 | Rar.exe | C:\Users\admin\AppData\Local\Temp\scan032.jpg | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report