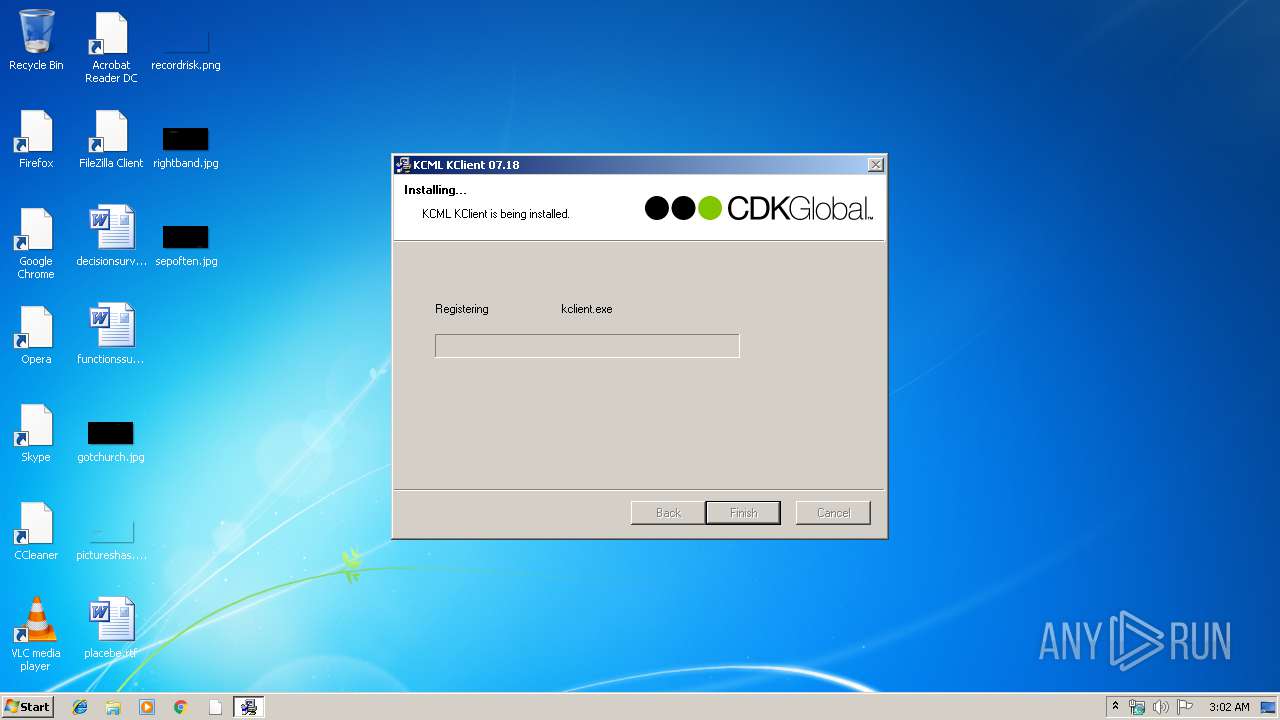
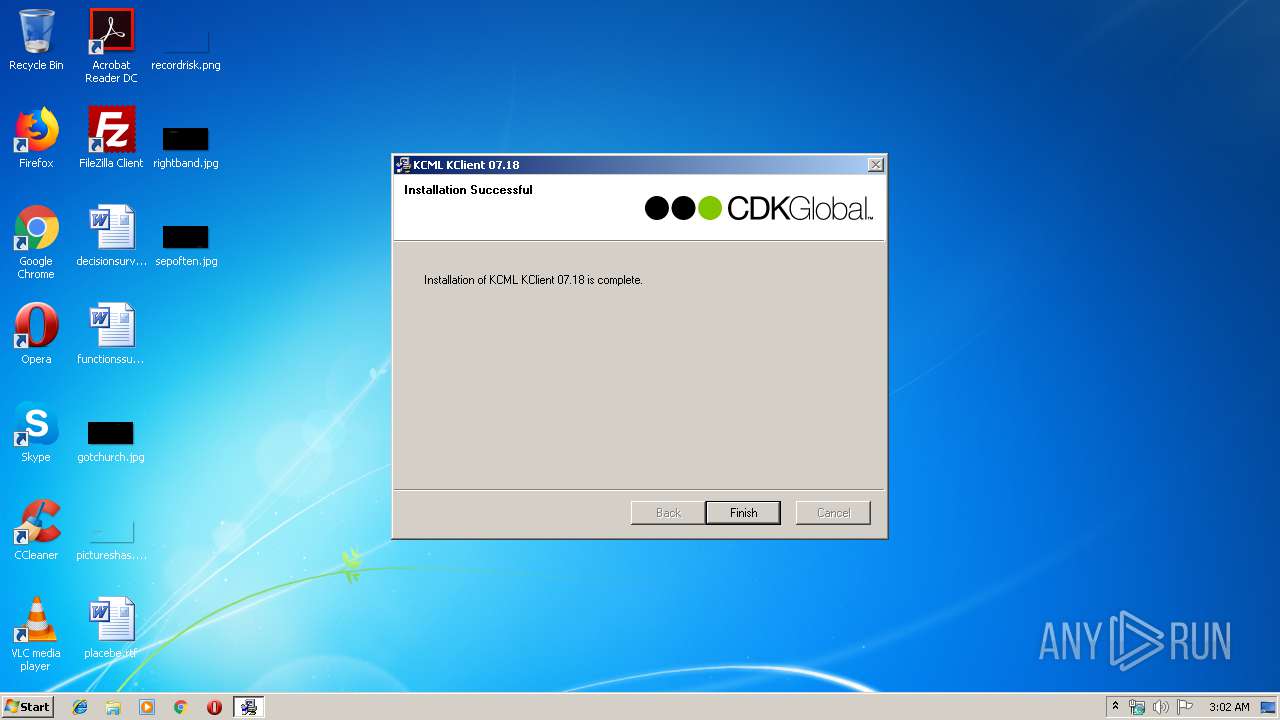
| File name: | KClient.exe |
| Full analysis: | https://app.any.run/tasks/3c9ebaa7-7d30-4f48-bd3d-774eebc86986 |
| Verdict: | Malicious activity |
| Analysis date: | January 03, 2020, 03:01:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B7E8AFE9A74013C326C986950E78541E |
| SHA1: | A4195B9B60E958B18575B1228966A98887C25ED8 |
| SHA256: | 122FF66D88BDB0B1DDE6F8F2F2392FD646D39B6E6CFD100D1D5E15BD6F648BAE |
| SSDEEP: | 49152:cYHJVCTQIgLccYMBnNX3K8ixlWDv3sNY3BJ53q6gbToOCDiEYP:cAJ2cYmo8+olv5a6WMo |
MALICIOUS
Application was dropped or rewritten from another process
- kclient.exe (PID: 1788)
- registerdll.exe (PID: 3172)
- kclient.exe (PID: 944)
- registerdll.exe (PID: 388)
- kuninstall.exe (PID: 3144)
Loads dropped or rewritten executable
- KClient.exe (PID: 3852)
- registerdll.exe (PID: 3172)
- registerdll.exe (PID: 388)
SUSPICIOUS
Modifies the open verb of a shell class
- kclient.exe (PID: 1788)
- kclient.exe (PID: 944)
Executable content was dropped or overwritten
- KClient.exe (PID: 3852)
Creates COM task schedule object
- registerdll.exe (PID: 3172)
- registerdll.exe (PID: 388)
Creates files in the program directory
- KClient.exe (PID: 3852)
Creates a software uninstall entry
- KClient.exe (PID: 3852)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:09:22 01:18:32+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 188928 |
| InitializedDataSize: | 2347008 |
| UninitializedDataSize: | 7680 |
| EntryPoint: | 0x1e573 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.18.1.24265 |
| ProductVersionNumber: | 7.18.1.24265 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | CDK Global |
| FileDescription: | KCML KClient Installer |
| FileVersion: | 07.18.01.24265 |
| DisplayVersion: | 07.18.01.24265 |
| InternalName: | KCML KClient |
| LegalTrademarks: | KCML is a trademark of CDK Global (UK) Limited |
| OriginalFileName: | KCML KClient |
| ProductName: | KCML |
| ProductVersion: | 07.18.01.24265 |
| LegalCopyright: | © CDK Global (UK) Limited 1999-2018 |
| CopyrightStatement: | This software is protected by copyright law and international treaties. Unauthorised reproduction and distribution of this program, or portions of it, may result in severe civil and criminal penalties and prosecution to the maximum extent of the law. |
| Tag041203B5: | - |
| Tag080404B0: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 21-Sep-2018 23:18:32 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | CDK Global |
| FileDescription: | KCML KClient Installer |
| FileVersion: | 07.18.01.24265 |
| DisplayVersion: | 07.18.01.24265 |
| InternalName: | KCML KClient |
| LegalTrademarks: | KCML is a trademark of CDK Global (UK) Limited |
| OriginalFilename: | KCML KClient |
| ProductName: | KCML |
| ProductVersion: | 07.18.01.24265 |
| LegalCopyright: | © CDK Global (UK) Limited 1999-2018 |
| CopyrightStatement: | This software is protected by copyright law and international treaties. Unauthorised reproduction and distribution of this program, or portions of it, may result in severe civil and criminal penalties and prosecution to the maximum extent of the law. |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 21-Sep-2018 23:18:32 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002E0F7 | 0x0002E200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.60616 |
K_BSS | 0x00030000 | 0x00001C98 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00032000 | 0x0001A556 | 0x0001A600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.46355 |
.data | 0x0004D000 | 0x000037E4 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.79146 |
K_DATA | 0x00051000 | 0x0000181C | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.363736 |
_text | 0x00053000 | 0x00000001 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.0203931 |
.rsrc | 0x00054000 | 0x00217230 | 0x00217400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.98604 |
.reloc | 0x0026C000 | 0x000061C6 | 0x00006200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 3.87608 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21133 | 991 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 2.94765 | 744 | UNKNOWN | English - United States | RT_ICON |
3 | 2.9915 | 296 | UNKNOWN | English - United States | RT_ICON |
126 | 3.72009 | 404 | UNKNOWN | English - United States | RT_STRING |
2001 | 2.16096 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
2002 | 2.47702 | 34 | UNKNOWN | English - United States | RT_GROUP_ICON |
2003 | 2.29056 | 25792 | UNKNOWN | English - United States | RT_BITMAP |
19000 | 7.99669 | 2158489 | UNKNOWN | English - United States | UNKNOWN |
29765 | 0 | 4 | UNKNOWN | English - United States | RT_RCDATA |
Imports
ADVAPI32.dll |
COMDLG32.dll |
Cabinet.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
WS2_32.dll |
Total processes
47
Monitored processes
7
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | "C:\Program Files\CDK\KCML\registerdll.exe" regserver "C:\Program Files\CDK\KCML\kccpropu.dll" | C:\Program Files\CDK\KCML\registerdll.exe | — | KClient.exe | |||||||||||
User: admin Company: CDK Global Integrity Level: HIGH Description: registerdll Exit code: 0 Version: 07.18.01.24265 Modules
| |||||||||||||||
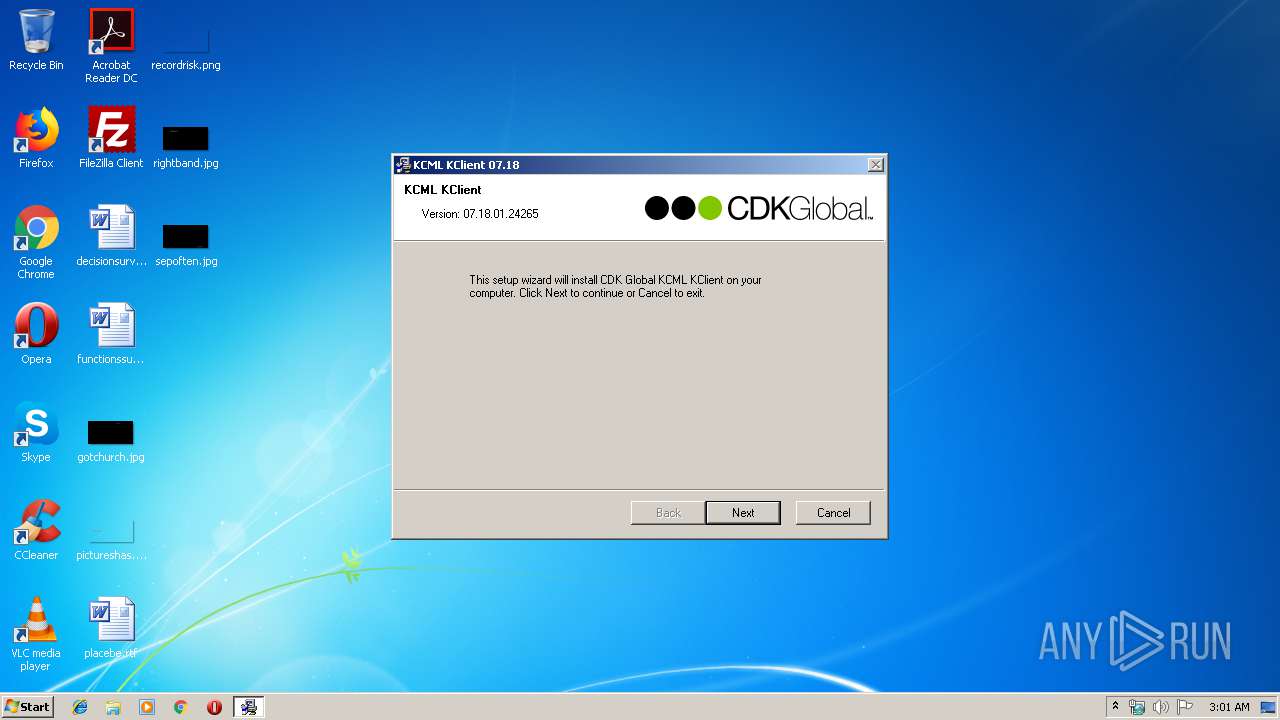
| 516 | "C:\Users\admin\AppData\Local\Temp\KClient.exe" | C:\Users\admin\AppData\Local\Temp\KClient.exe | — | explorer.exe | |||||||||||
User: admin Company: CDK Global Integrity Level: MEDIUM Description: KCML KClient Installer Exit code: 3221226540 Version: 07.18.01.24265 Modules
| |||||||||||||||
| 944 | "C:\Program Files\CDK\KCML\kclient.exe" -regserver | C:\Program Files\CDK\KCML\kclient.exe | — | KClient.exe | |||||||||||
User: admin Company: CDK Global Integrity Level: HIGH Description: KCML client Exit code: 0 Version: 07.18.01.24265U Modules
| |||||||||||||||
| 1788 | C:\Users\admin\AppData\Local\Temp\cab_data\kclient.exe -regserversandbox | C:\Users\admin\AppData\Local\Temp\cab_data\kclient.exe | — | KClient.exe | |||||||||||
User: admin Company: CDK Global Integrity Level: HIGH Description: KCML client Exit code: 0 Version: 07.18.01.24265U Modules
| |||||||||||||||
| 3144 | "C:\Program Files\CDK\KCML\kuninstall.exe" -regserver | C:\Program Files\CDK\KCML\kuninstall.exe | — | KClient.exe | |||||||||||
User: admin Company: CDK Global Integrity Level: HIGH Description: CDK Global Un-Installer Exit code: 0 Version: 07.18.01.24265 Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\AppData\Local\Temp\cab_data\registerdll.exe" regserversandbox "C:\Users\admin\AppData\Local\Temp\cab_data\kccpropu.dll" | C:\Users\admin\AppData\Local\Temp\cab_data\registerdll.exe | — | KClient.exe | |||||||||||
User: admin Company: CDK Global Integrity Level: HIGH Description: registerdll Exit code: 0 Version: 07.18.01.24265 Modules
| |||||||||||||||
| 3852 | "C:\Users\admin\AppData\Local\Temp\KClient.exe" | C:\Users\admin\AppData\Local\Temp\KClient.exe | explorer.exe | ||||||||||||
User: admin Company: CDK Global Integrity Level: HIGH Description: KCML KClient Installer Exit code: 0 Version: 07.18.01.24265 Modules
| |||||||||||||||
Total events
216
Read events
59
Write events
99
Delete events
58
Modification events
| (PID) Process: | (3852) KClient.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\AlwaysUnloadDLL |
| Operation: | write | Name: | |
Value: 1 | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_LOCAL_MACHINE\SOFTWARE\Kerridge\Documentation\KCMLclient |
| Operation: | write | Name: | Menu |
Value: &Client help | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_LOCAL_MACHINE\SOFTWARE\Kerridge\Documentation\KCMLclient |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\AppData\Local\Temp\cab_data\kclient.chm | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_CLASSES_ROOT\.kcc |
| Operation: | write | Name: | |
Value: KCLIENT | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_CLASSES_ROOT\.kcc\ShellNew |
| Operation: | write | Name: | Command |
Value: "C:\Users\admin\AppData\Local\Temp\cab_data\kclient.exe" -W "%1" | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_CLASSES_ROOT\.kcc\ShellNew |
| Operation: | write | Name: | IconPath |
Value: C:\Users\admin\AppData\Local\Temp\cab_data\kclient.exe | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_CLASSES_ROOT\.kcc\ShellNew |
| Operation: | write | Name: | NullFile |
Value: | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_CLASSES_ROOT\KCLIENT |
| Operation: | write | Name: | |
Value: KCML Client | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_CLASSES_ROOT\KCLIENT |
| Operation: | write | Name: | NeverShowExt |
Value: | |||
| (PID) Process: | (1788) kclient.exe | Key: | HKEY_CURRENT_USER\Software\Kerridge\setup\sandbox\HKEY_CLASSES_ROOT\KCLIENT |
| Operation: | write | Name: | URL Protocol |
Value: | |||
Executable files
12
Suspicious files
0
Text files
9
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\CompilerError.png | image | |
MD5:4C4CB619CC1C52DC6BD355438724827C | SHA256:4AB2D92C63ACB818FE3E5A753418A164193EDC1D2ADE1EF654BB78CE341CC297 | |||
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\CompilerInfo.png | image | |
MD5:0E9410BD4277E5C590ACA60C1DCB7475 | SHA256:23894C002853A26380088B277AD09C34902490F609547A983433DADA5E63C0A2 | |||
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\kclient.ttf | ttf | |
MD5:1B01000E95DF5980A853A9CFBA07B21E | SHA256:35AB479E1953D78191722A2B9AA94944B250427A105808DF1323C6A04EA34D59 | |||
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\kclient_unicode.log | — | |
MD5:— | SHA256:— | |||
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\registerdll.exe | executable | |
MD5:21C56E09E47E7BC5385E55ADB397B385 | SHA256:85DDB7AD1226B0002C5FE1678C515DDA8EADDA6E5DCD29B552347D8DACE80120 | |||
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\CompilerWarning.png | image | |
MD5:5DF789F5CDA112BA63BE5A292D91AFCC | SHA256:CCDD7ABEBB094C3838E60B617C14D0B0523069CDAB8DA4038C699899CAD258DF | |||
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\registerdll64.exe | executable | |
MD5:8CBAD8BE833C77B14E97CD481D7EF83F | SHA256:46E5B3845C24E7EA95AD9747159A02CABF828F575BD3236C2D73735DCA5B3BCB | |||
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\kclient.exe | executable | |
MD5:0428D0FC75FC537413EFB0FFCE9CACE0 | SHA256:D78E69D17F6737CED39A78BDEF8047DA424AACED7E2376BC048DD0194FAD0196 | |||
| 3852 | KClient.exe | C:\Users\admin\AppData\Local\Temp\cab_data\kccpropu.dll | executable | |
MD5:2CE15855C0F938064A52B8330F5163CB | SHA256:D98CA5AA630C5E5544A9926BE5FF27AFB9659ABD8DF91648BFBAC97FD6A1043F | |||
| 3852 | KClient.exe | C:\Program Files\CDK\KCML\kclient.exe | executable | |
MD5:0428D0FC75FC537413EFB0FFCE9CACE0 | SHA256:D78E69D17F6737CED39A78BDEF8047DA424AACED7E2376BC048DD0194FAD0196 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report