| File name: | PSemuX-7z2201-x64_604115.exe |
| Full analysis: | https://app.any.run/tasks/0a17e277-f4df-40a2-a546-a32940ba9996 |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2024, 21:38:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 08EA1813D6B205C446E6AE655C4E6715 |
| SHA1: | 76F4D2AF1C04EC157FC8A270DA5980EE6BCB5DEF |
| SHA256: | 12288224D26607B30D026A32FAF2AC7B49FC32ACC8950EEAF60B933F2E39F48F |
| SSDEEP: | 98304:z3eS5Ep+LVKi0ye4hrHNH3egVvkVje193KqFpF5fEJVtiwMoNijfqmm+UbN95aJG:7gD0XGd2YIB/QEZ1IVRHB0l1VpWU4yU |
MALICIOUS
Drops the executable file immediately after the start
- PSemuX-7z2201-x64_604115.exe (PID: 5000)
SUSPICIOUS
Searches for installed software
- PSemuX-7z2201-x64_604115.exe (PID: 5000)
Executable content was dropped or overwritten
- PSemuX-7z2201-x64_604115.exe (PID: 5000)
INFO
Checks supported languages
- PSemuX-7z2201-x64_604115.exe (PID: 5000)
Reads the computer name
- PSemuX-7z2201-x64_604115.exe (PID: 5000)
Checks proxy server information
- slui.exe (PID: 1320)
Reads the software policy settings
- slui.exe (PID: 1320)
Creates files or folders in the user directory
- PSemuX-7z2201-x64_604115.exe (PID: 5000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:04:19 17:02:42+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 7011840 |
| InitializedDataSize: | 433152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x61bbf0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
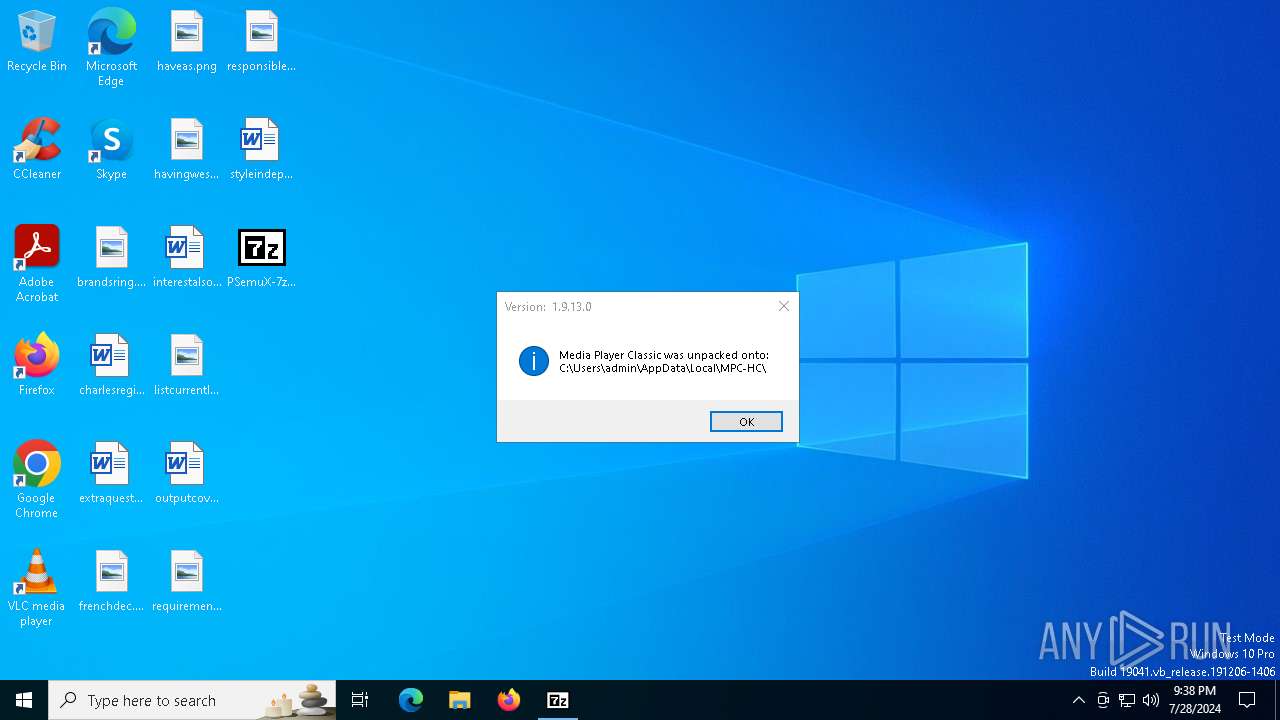
| FileVersionNumber: | 1.9.13.0 |
| ProductVersionNumber: | 1.9.13.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Jewel Utility Team |
| FileDescription: | MPC-HC Setup by Jewel Utility Team |
| FileVersion: | 1.9.13.0 |
| LegalCopyright: | Copyright 2002-2021 Jewel Utility Team |
| ProductName: | MPC-HC by Jewel Utility Team |
| ProductVersion: | 1.9.13.0 |
Total processes
134
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1320 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | "C:\Users\admin\Desktop\PSemuX-7z2201-x64_604115.exe" | C:\Users\admin\Desktop\PSemuX-7z2201-x64_604115.exe | explorer.exe | ||||||||||||
User: admin Company: Jewel Utility Team Integrity Level: MEDIUM Description: MPC-HC Setup by Jewel Utility Team Exit code: 0 Version: 1.9.13.0 Modules
| |||||||||||||||
Total events
4 064
Read events
4 064
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5000 | PSemuX-7z2201-x64_604115.exe | C:\Users\admin\AppData\Local\MPC-HC\MPC-HC.1.9.13.x86.exe | executable | |
MD5:08A6FBB57D5B456414B71B260F749C9E | SHA256:37037553E81DE20E2D0869388D4AAEEEC8D807EA0447DC4C822FE9C4A6FADA1F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
24
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 104.21.70.178:443 | https://contentworldinc.com/9BEC55CF2367EE37/39316298361/59AFA49E14E6A1FD/72220270225?AD9090DDCC9735691722202702 | unknown | text | 32 b | unknown |
— | — | POST | — | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | — | — | unknown |
— | — | POST | 200 | 51.105.71.136:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4548 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6012 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2856 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4340 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
contentworldinc.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report