| File name: | Carenado_activator_v2.exe |
| Full analysis: | https://app.any.run/tasks/aca2c345-6ca9-4dfc-813a-5ca2fabab332 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 13:42:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 7EDDFC855203889A0A70C115F218FA9C |
| SHA1: | A302FCB5FD32BC684EDAAB6670BD027EF0E0837D |
| SHA256: | 1220C11F7AAD4D339C4ED450BED920A2786472B63361BFCF94E89B3E373A8BC2 |
| SSDEEP: | 1536:OF4n4SIF9xh33YJ5+dCWb3gwrPhAZpts4LavWnptbAueN/HF0EA9Z5Di9Oj86wXH:K44jdw2/0ePOoUIgEA9Z5DqOj8FXMY |
MALICIOUS
Writes to the hosts file
- Carenado_activator_v2.exe (PID: 1112)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by user
- chrome.exe (PID: 2580)
Reads the hosts file
- Carenado_activator_v2.exe (PID: 1112)
- chrome.exe (PID: 2580)
- chrome.exe (PID: 2344)
Application launched itself
- chrome.exe (PID: 2580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2085:08:10 00:01:33+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 36864 |
| InitializedDataSize: | 79872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2400a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
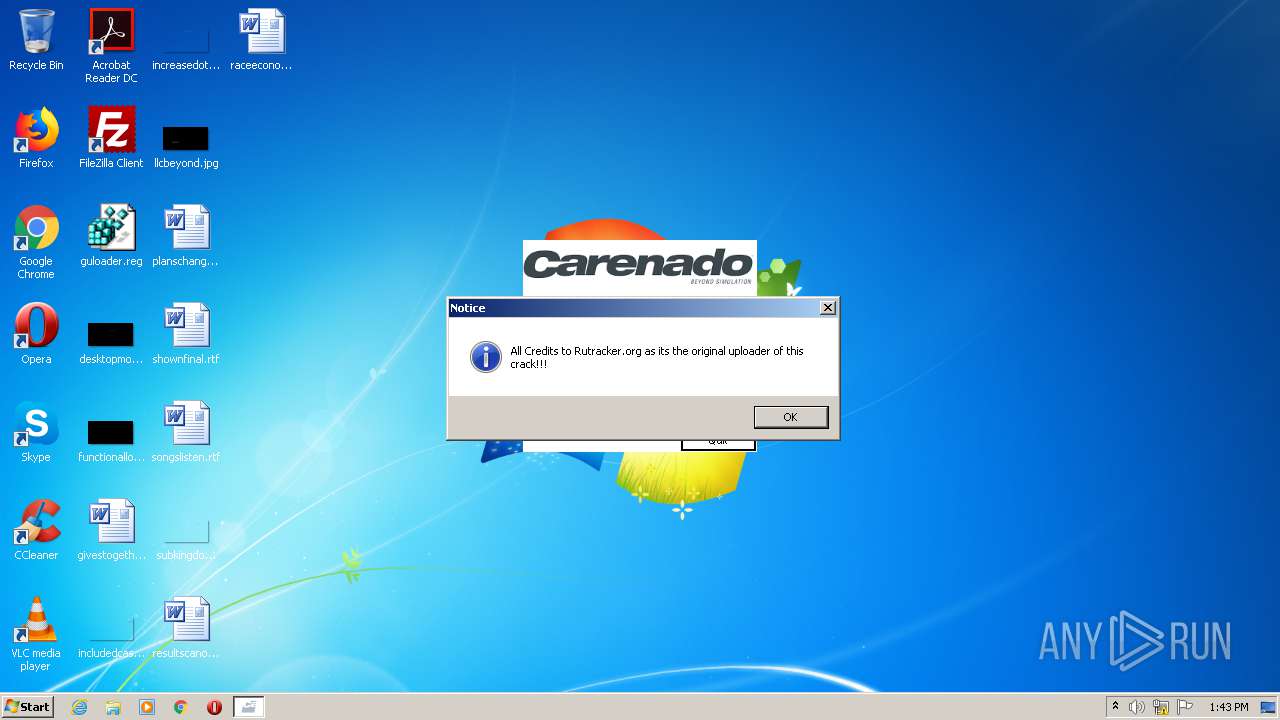
| FileDescription: | Carenado Activator v2 |
| FileVersion: | 2.0.0.0 |
| InternalName: | Carenado activator v2.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | - |
| OriginalFileName: | Carenado activator v2.exe |
| ProductName: | Carenado Activator v2 |
| ProductVersion: | 2.0.0.0 |
| AssemblyVersion: | 2.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 04-Jul-1949 15:33:17 |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Carenado Activator v2 |
| FileVersion: | 2.0.0.0 |
| InternalName: | Carenado activator v2.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | - |
| OriginalFilename: | Carenado activator v2.exe |
| ProductName: | Carenado Activator v2 |
| ProductVersion: | 2.0.0.0 |
| Assembly Version: | 2.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 04-Jul-1949 15:33:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
l7\x02NDGi}\xd4#\x01 | 0x00002000 | 0x000123D4 | 0x00012400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99728 |
.text | 0x00016000 | 0x00008CC8 | 0x00008E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.12437 |
.rsrc | 0x00020000 | 0x00001080 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.80805 |
.reloc | 0x00022000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0980042 |
0x00024000 | 0x00000010 | 0x00000200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0.142636 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00692 | 3169 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
51
Monitored processes
14
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1112 | "C:\Users\admin\AppData\Local\Temp\Carenado_activator_v2.exe" | C:\Users\admin\AppData\Local\Temp\Carenado_activator_v2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Carenado Activator v2 Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2584 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,13648918014056001169,15707654304684585616,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11859452274365076738 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1724 | "C:\Users\admin\AppData\Local\Temp\Carenado_activator_v2.exe" | C:\Users\admin\AppData\Local\Temp\Carenado_activator_v2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Carenado Activator v2 Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,13648918014056001169,15707654304684585616,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12481725218739011717 --mojo-platform-channel-handle=3312 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,13648918014056001169,15707654304684585616,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2677436734660496144 --mojo-platform-channel-handle=3816 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,13648918014056001169,15707654304684585616,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=13595859522596938893 --mojo-platform-channel-handle=1632 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,13648918014056001169,15707654304684585616,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3331831412755173868 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2512 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,13648918014056001169,15707654304684585616,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1317334637016764694 --mojo-platform-channel-handle=3432 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
202
Read events
160
Write events
39
Delete events
3
Modification events
| (PID) Process: | (1236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2580-13251131021111750 |
Value: 259 | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2580) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
19
Text files
55
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FC3A58D-A14.pma | — | |
MD5:— | SHA256:— | |||
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\19b2e132-126a-45a2-99d7-0532d590e7ac.tmp | — | |
MD5:— | SHA256:— | |||
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1112 | Carenado_activator_v2.exe | C:\Windows\system32\drivers\etc\hosts | text | |
MD5:— | SHA256:— | |||
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF14c3db.TMP | text | |
MD5:— | SHA256:— | |||
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF14c458.TMP | text | |
MD5:— | SHA256:— | |||
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT~RF14c477.TMP | text | |
MD5:— | SHA256:— | |||
| 2580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2344 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
2344 | chrome.exe | 142.250.74.195:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2344 | chrome.exe | 216.58.212.142:443 | apis.google.com | Google Inc. | US | whitelisted |
2344 | chrome.exe | 172.217.23.110:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
2344 | chrome.exe | 216.58.212.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2344 | chrome.exe | 216.58.204.14:443 | ogs.google.se | Google Inc. | US | whitelisted |
2344 | chrome.exe | 172.217.12.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2344 | chrome.exe | 172.217.22.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2344 | chrome.exe | 172.217.12.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
— | — | 216.58.213.3:443 | www.google.se | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com.ua |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.google.com |
| malicious |
www.google.se |
| whitelisted |