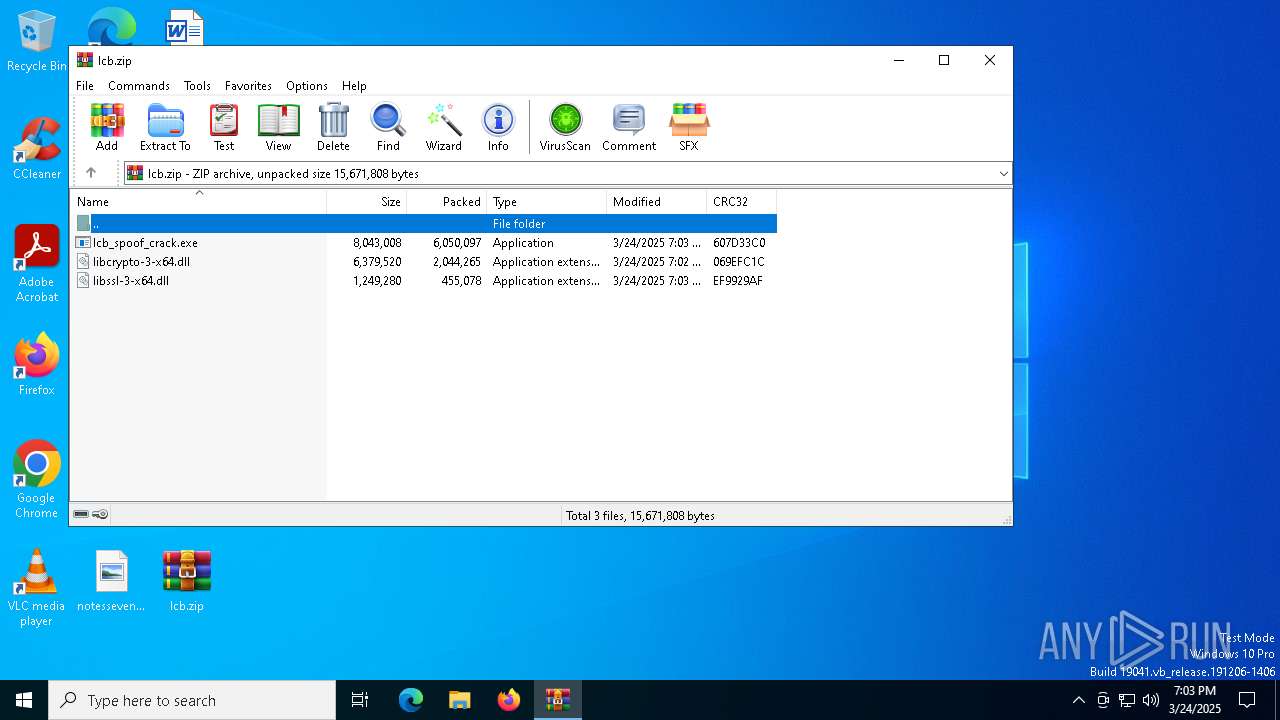
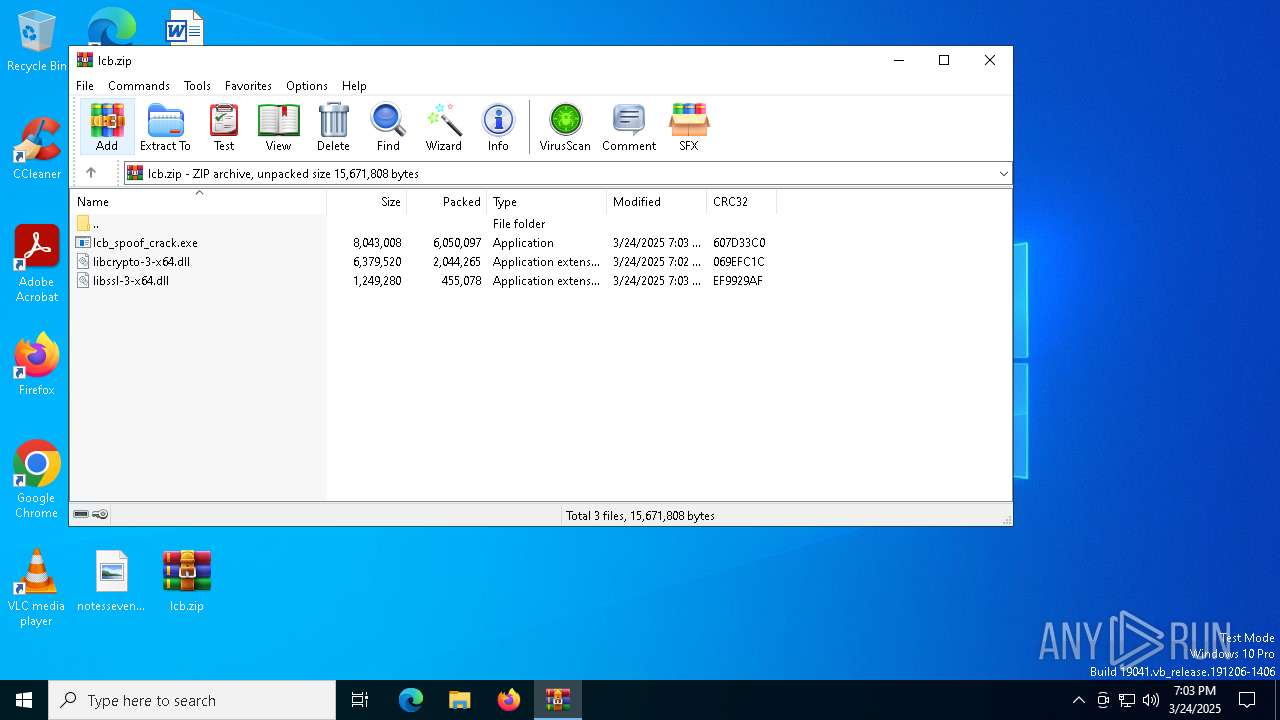
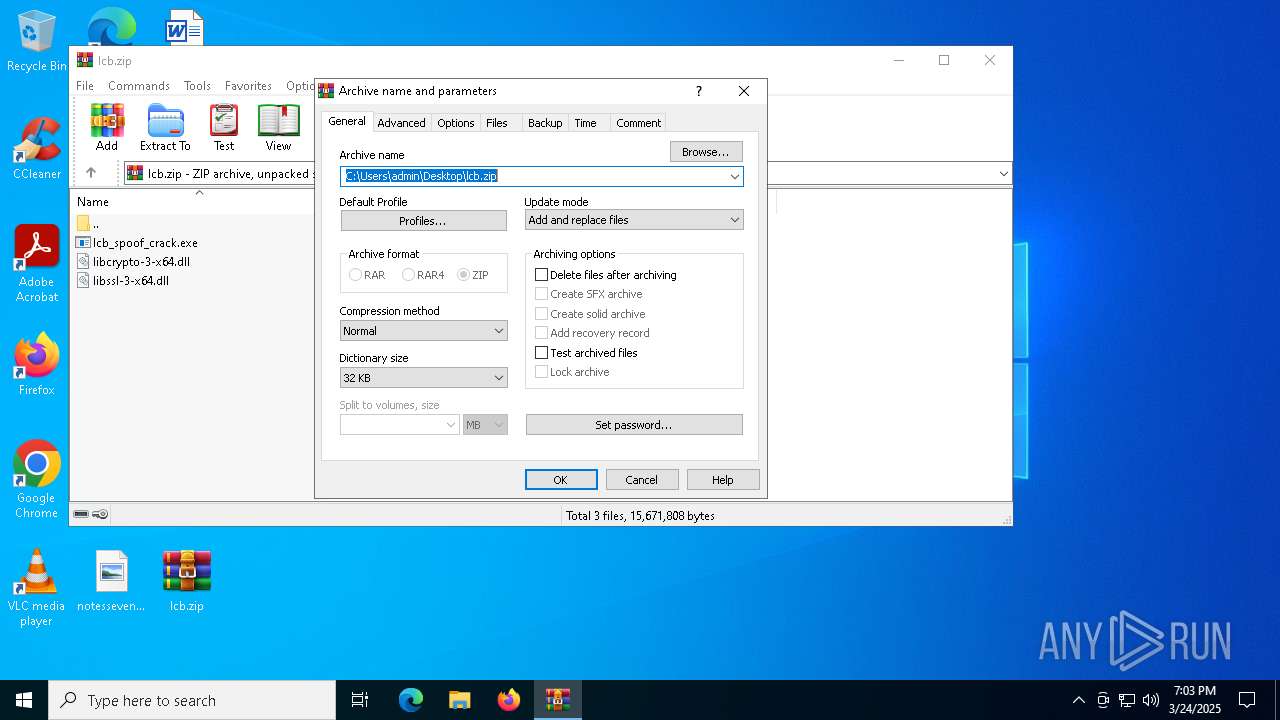
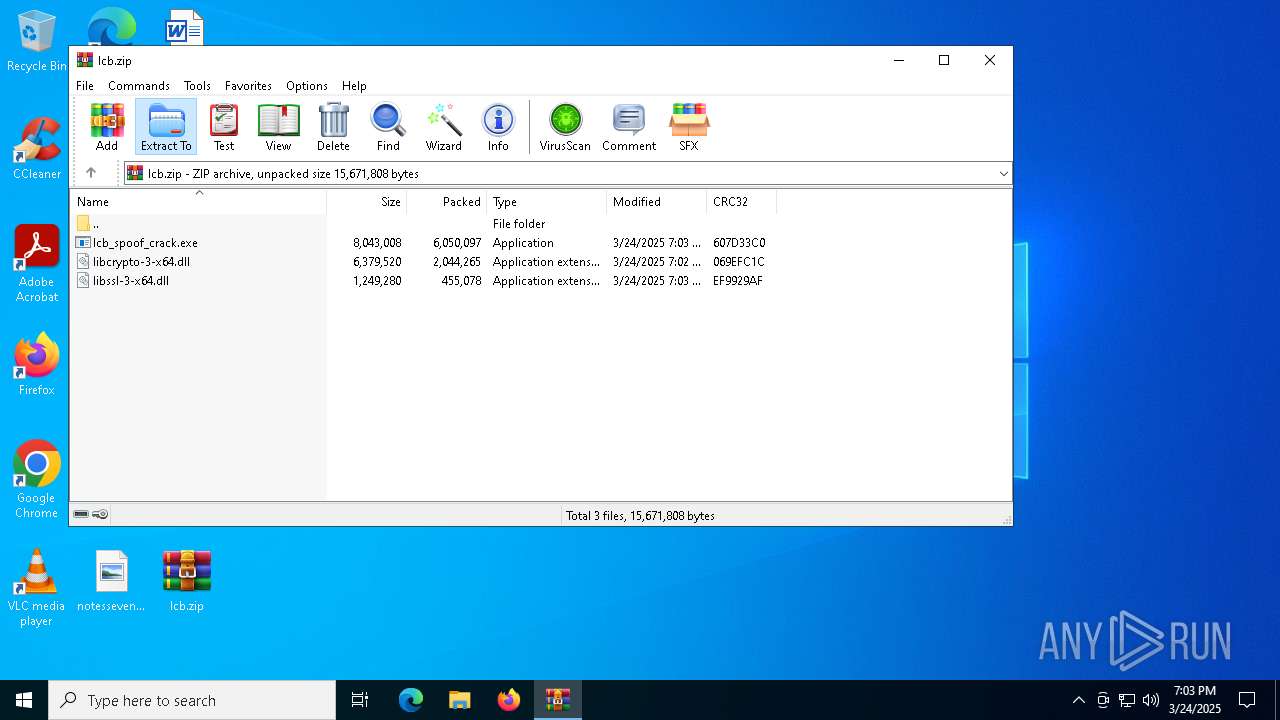
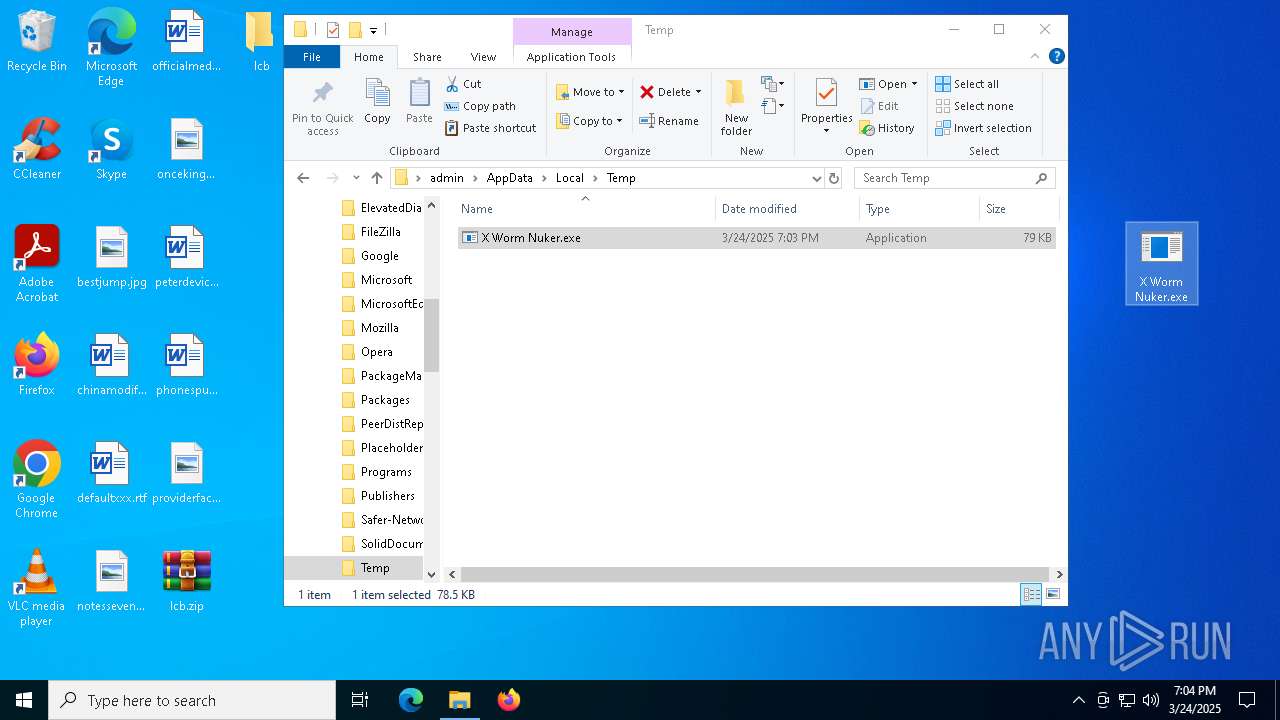
| File name: | lcb.zip |
| Full analysis: | https://app.any.run/tasks/312c8e81-fd86-4441-8e49-076042d61a3e |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | March 24, 2025, 19:03:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C786498C085F0B9F6DA9FE29F278206A |
| SHA1: | 9B4ADCBCC7B738B6E2707B2701050AB7528F5782 |
| SHA256: | 12188EB597E8A396A9F9F28E1878B53A8CE7D51B55EAE1F0ECD60285034FF5B5 |
| SSDEEP: | 98304:b+rO9T3AHCV+u+tPKkEIZXOKvEzsWUdC4C/vH/PjQpAVPQUL9MxkBgNkUOaQUb4o:aECwRR5d9EmhtW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Base64-obfuscated command line is found
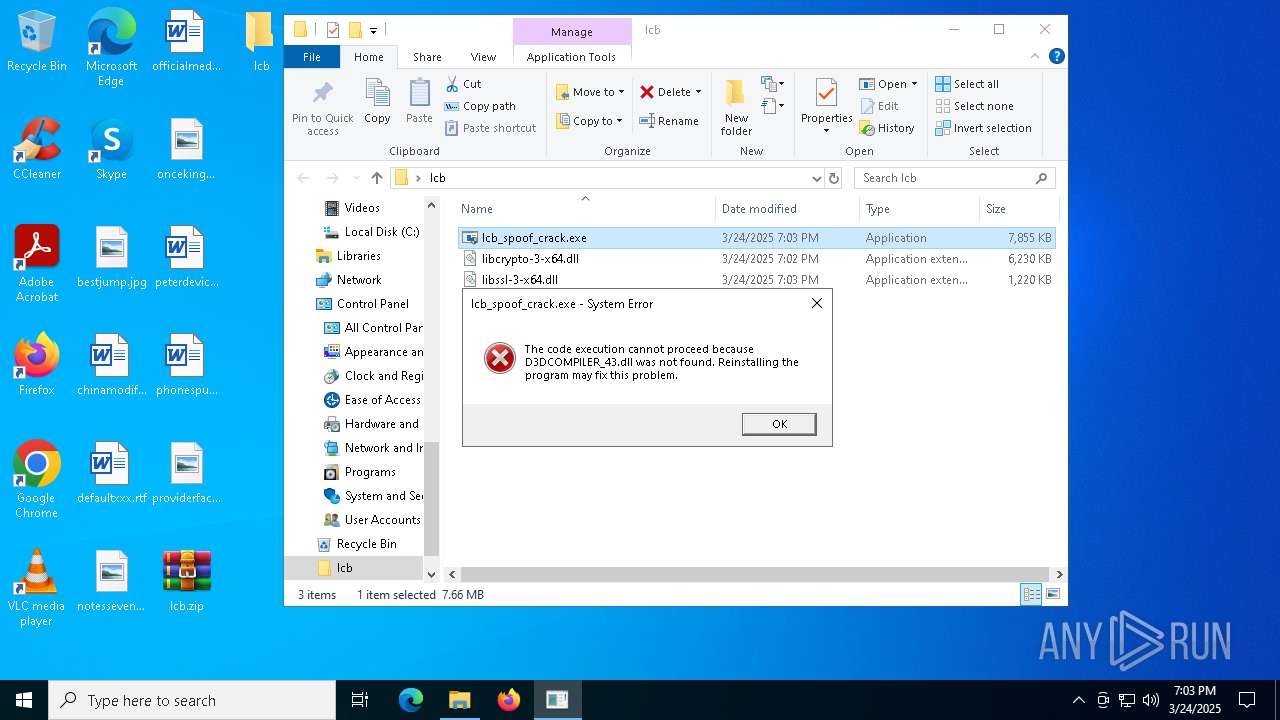
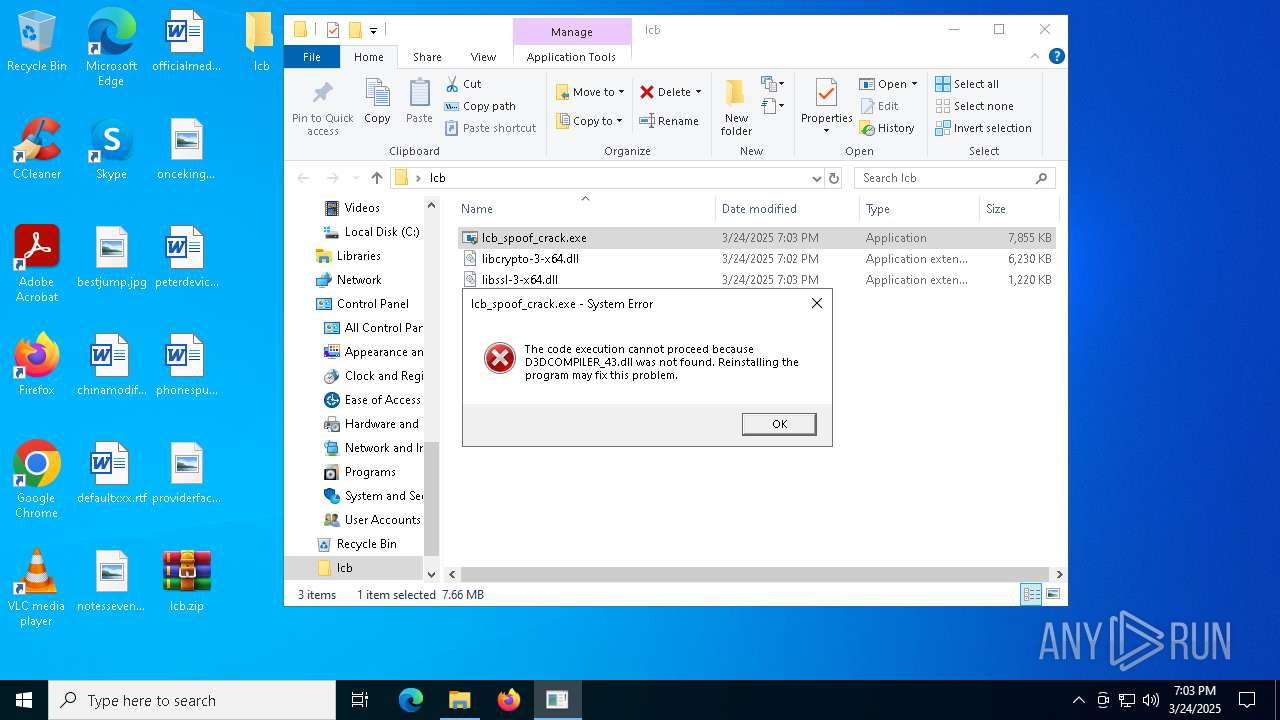
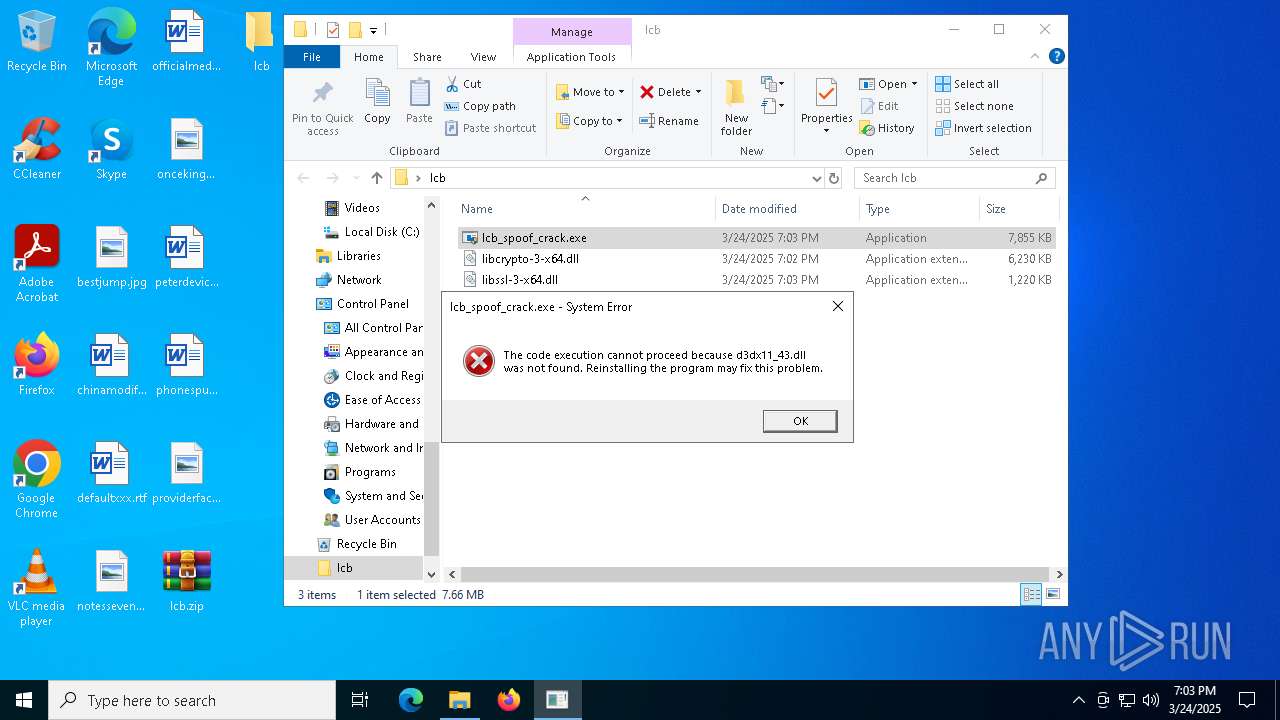
- lcb_spoof_crack.exe (PID: 2320)
Starts POWERSHELL.EXE for commands execution
- lcb_spoof_crack.exe (PID: 2320)
BASE64 encoded PowerShell command has been detected
- lcb_spoof_crack.exe (PID: 2320)
Executable content was dropped or overwritten
- lcb_spoof_crack.exe (PID: 2320)
The process connected to a server suspected of theft
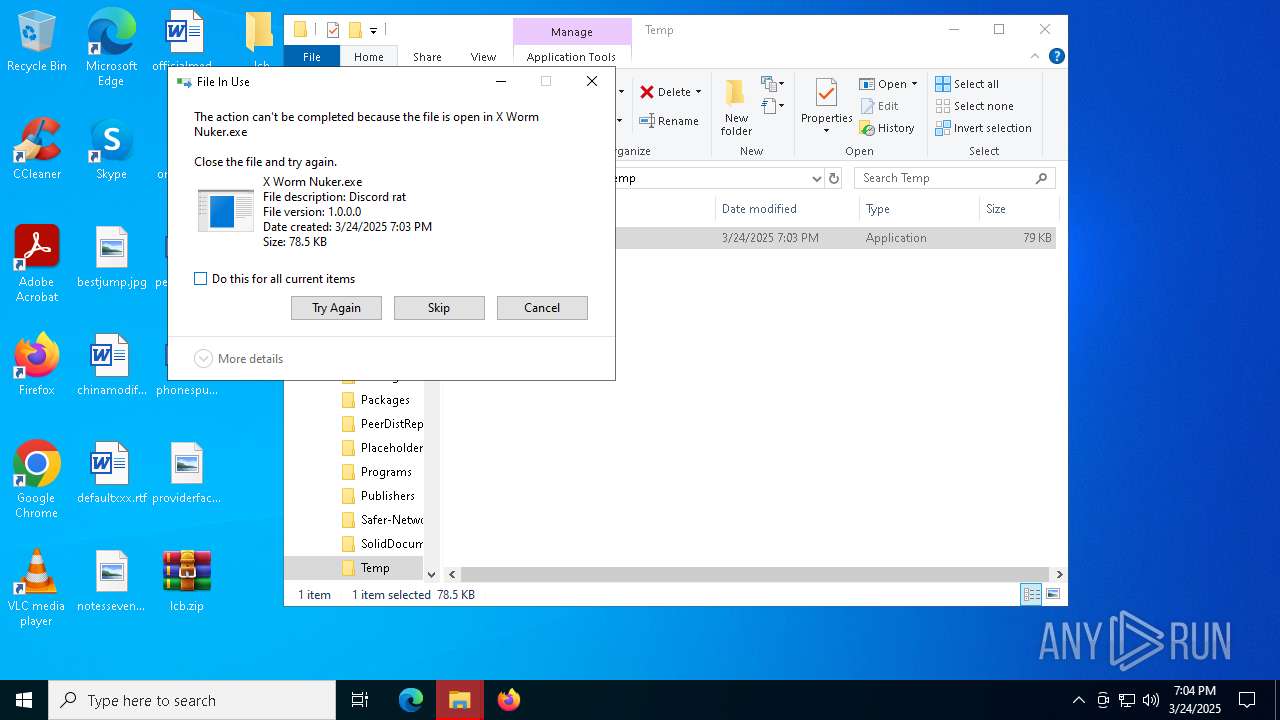
- X Worm Nuker.exe (PID: 5968)
Checks for external IP
- X Worm Nuker.exe (PID: 5968)
Starts CMD.EXE for commands execution
- X Worm Nuker.exe (PID: 5968)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7576)
The sample compiled with english language support
- WinRAR.exe (PID: 7576)
Manual execution by a user
- lcb_spoof_crack.exe (PID: 2320)
- lcb_spoof_crack.exe (PID: 8184)
- firefox.exe (PID: 2772)
Reads the computer name
- lcb_spoof_crack.exe (PID: 2320)
Checks supported languages
- lcb_spoof_crack.exe (PID: 2320)
Process checks computer location settings
- lcb_spoof_crack.exe (PID: 2320)
Application launched itself
- firefox.exe (PID: 2772)
- firefox.exe (PID: 2240)
Create files in a temporary directory
- lcb_spoof_crack.exe (PID: 2320)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7224)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .kmz | | | Google Earth saved working session (33.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (22.2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:24 19:03:04 |
| ZipCRC: | 0x607d33c0 |
| ZipCompressedSize: | 6050097 |
| ZipUncompressedSize: | 8043008 |
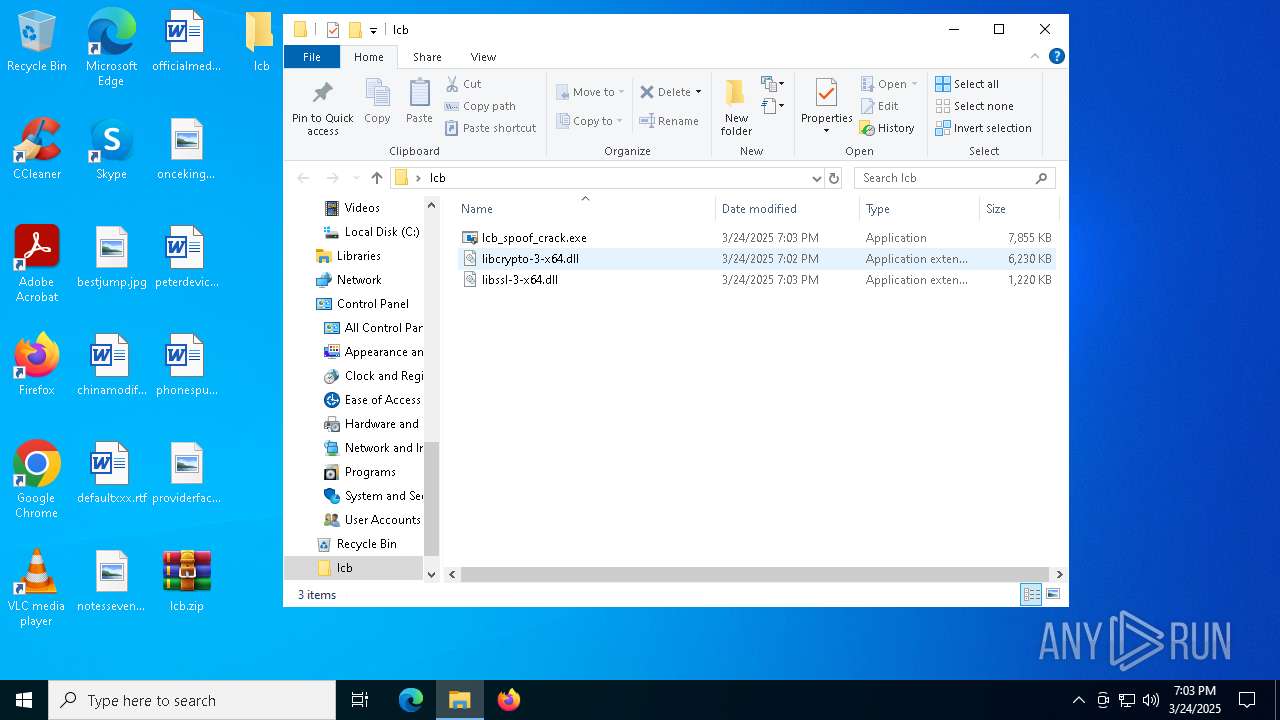
| ZipFileName: | lcb_spoof_crack.exe |
Total processes
158
Monitored processes
20
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2240 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\Desktop\lcb\lcb_spoof_crack.exe" | C:\Users\admin\Desktop\lcb\lcb_spoof_crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2772 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4352 -childID 2 -isForBrowser -prefsHandle 4340 -prefMapHandle 4336 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1396 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {fff6e93e-9d8e-42a2-b77c-7e855efe5431} 2240 "\\.\pipe\gecko-crash-server-pipe.2240" 211c94df850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3020 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4784 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4872 -prefMapHandle 4896 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {38a58439-8119-4cc5-bd75-7973258073d6} 2240 "\\.\pipe\gecko-crash-server-pipe.2240" 211cb040110 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4112 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5092 -childID 5 -isForBrowser -prefsHandle 5196 -prefMapHandle 5188 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1396 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {7136b6ad-29b7-49e5-9278-5ec30b8fbbb7} 2240 "\\.\pipe\gecko-crash-server-pipe.2240" 211ca769f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4424 | "C:\Users\admin\AppData\Local\Temp\lcb_spoof_crack.exe" | C:\Users\admin\AppData\Local\Temp\lcb_spoof_crack.exe | — | lcb_spoof_crack.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Modules
| |||||||||||||||
| 5352 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5016 -childID 3 -isForBrowser -prefsHandle 2636 -prefMapHandle 2632 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1396 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8240d24b-0a5d-4dfa-baa9-e2a1961a9b42} 2240 "\\.\pipe\gecko-crash-server-pipe.2240" 211ca769310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5968 | "C:\Users\admin\AppData\Local\Temp\X Worm Nuker.exe" | C:\Users\admin\AppData\Local\Temp\X Worm Nuker.exe | lcb_spoof_crack.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Discord rat Version: 1.0.0.0 Modules
| |||||||||||||||
| 7192 | "cmd.exe" /C rd /s /q C:\Windows\System32 | C:\Windows\System32\cmd.exe | — | X Worm Nuker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 506
Read events
20 422
Write events
69
Delete events
15
Modification events
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\lcb.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00500072006F006700720061006D002000460069006C00650073005C00570069006E005200410052005C00570069006E005200410052002E00650078006500000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070000000 | |||
Executable files
5
Suspicious files
27
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2240 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2240 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:B1B7061CC6997D1F2CC03C779F47AC1B | SHA256:AA703C5AD9ABAF4B6D517068CEDBA81688059673092076CEA5DB406330708923 | |||
| 2240 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:B1B7061CC6997D1F2CC03C779F47AC1B | SHA256:AA703C5AD9ABAF4B6D517068CEDBA81688059673092076CEA5DB406330708923 | |||
| 2240 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7224 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yecknhyn.gzu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7576 | WinRAR.exe | C:\Users\admin\Desktop\lcb\libssl-3-x64.dll | executable | |
MD5:10CBD37C4DF0AEFF2346BA2C2038B420 | SHA256:18BABFE5F3DE3D0CEAA4BD671D7D3C808C8F788CA9782117B74D5B4900A2D250 | |||
| 2240 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2240 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 2240 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2240 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
56
DNS requests
79
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.41.81:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7792 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2240 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7692 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7692 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2240 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
2240 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2240 | firefox.exe | POST | 200 | 23.32.238.82:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2240 | firefox.exe | POST | 200 | 23.32.238.27:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.41.81:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6480 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7792 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
gateway.discord.gg |
| whitelisted |
discord.com |
| whitelisted |
geolocation-db.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (gateway .discord .gg) |
5968 | X Worm Nuker.exe | Misc activity | ET INFO Observed Discord Service Domain (gateway .discord .gg) in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
5968 | X Worm Nuker.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
5968 | X Worm Nuker.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
5968 | X Worm Nuker.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Discord |
5968 | X Worm Nuker.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain in DNS Lookup (geolocation-db .com) |
5968 | X Worm Nuker.exe | Misc activity | ET INFO External IP Lookup Domain (geolocation-db .com) in TLS SNI |