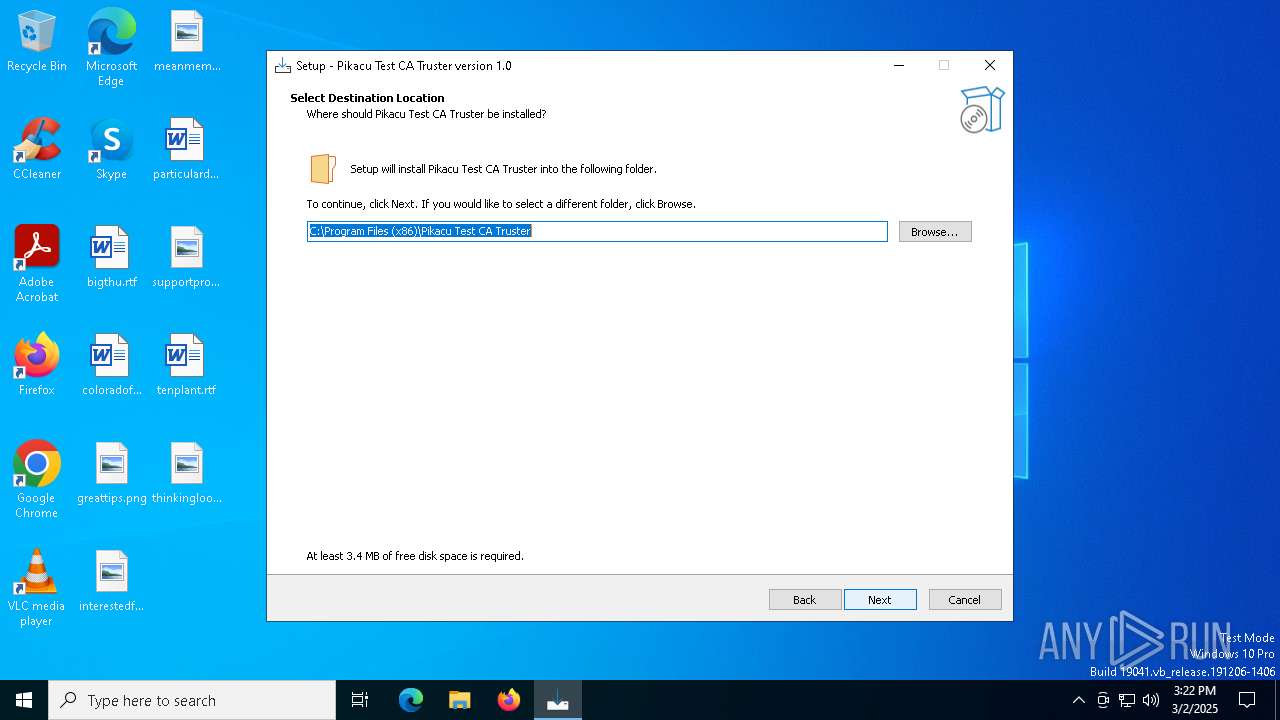
| File name: | certx.exe |
| Full analysis: | https://app.any.run/tasks/b0b3b711-328c-4ea5-afc4-712fce4aee49 |
| Verdict: | Malicious activity |
| Analysis date: | March 02, 2025, 15:22:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | A64517503ADB2A1BB8A2F58CA8A661DE |
| SHA1: | F8A5A7F0F6A974559E63EC744402A497A45150E2 |
| SHA256: | 11F4F22EABB173D8C37E80A3DE3BA1D321805FB6D5ADAE498C6628145811EF2E |
| SSDEEP: | 49152:67HecD4dnbibBlb+D7rP4jsbmLApne0Fop4R2uXB3iyLT/ex4XrL7P42DpJXWZnJ:q+cD4dni2P4IkWnXFopLQ3iUrex4vkYc |
MALICIOUS
Executing a file with an untrusted certificate
- Certmgr.exe (PID: 7992)
- Certmgr.exe (PID: 1388)
- Certmgr.exe (PID: 2240)
- Certmgr.exe (PID: 6080)
- Certmgr.exe (PID: 7928)
- Certmgr.exe (PID: 7960)
- Certmgr.exe (PID: 5436)
- Certmgr.exe (PID: 6576)
- Certmgr.exe (PID: 7872)
- Certmgr.exe (PID: 7860)
- Certmgr.exe (PID: 7824)
- Certmgr.exe (PID: 5400)
- Certmgr.exe (PID: 7800)
- Certmgr.exe (PID: 208)
- Certmgr.exe (PID: 8176)
- Certmgr.exe (PID: 1760)
- Certmgr.exe (PID: 3304)
- Certmgr.exe (PID: 2284)
- Certmgr.exe (PID: 7432)
- Certmgr.exe (PID: 8056)
- Certmgr.exe (PID: 4892)
- Certmgr.exe (PID: 1188)
- Certmgr.exe (PID: 5608)
- Certmgr.exe (PID: 6644)
- Certmgr.exe (PID: 2516)
- Certmgr.exe (PID: 6584)
- Certmgr.exe (PID: 2316)
- Certmgr.exe (PID: 4408)
- Certmgr.exe (PID: 7312)
- Certmgr.exe (PID: 7436)
- Certmgr.exe (PID: 7524)
- Certmgr.exe (PID: 5116)
- Certmgr.exe (PID: 6564)
- Certmgr.exe (PID: 5960)
- Certmgr.exe (PID: 7576)
- Certmgr.exe (PID: 7716)
- Certmgr.exe (PID: 7736)
- Certmgr.exe (PID: 6488)
- Certmgr.exe (PID: 7652)
- Certmgr.exe (PID: 1244)
- Certmgr.exe (PID: 4268)
- Certmgr.exe (PID: 7944)
- Certmgr.exe (PID: 7980)
- Certmgr.exe (PID: 8000)
- Certmgr.exe (PID: 2420)
- Certmgr.exe (PID: 5720)
- Certmgr.exe (PID: 7876)
- Certmgr.exe (PID: 8020)
- Certmgr.exe (PID: 8036)
- Certmgr.exe (PID: 736)
- Certmgr.exe (PID: 5756)
- Certmgr.exe (PID: 2552)
- Certmgr.exe (PID: 7852)
- Certmgr.exe (PID: 7832)
SUSPICIOUS
Executable content was dropped or overwritten
- certx.exe (PID: 2392)
- certx.exe (PID: 7192)
- certx.tmp (PID: 7216)
Reads security settings of Internet Explorer
- certx.tmp (PID: 6640)
Reads the Windows owner or organization settings
- certx.tmp (PID: 7216)
Executing commands from a ".bat" file
- certx.tmp (PID: 7216)
Process drops legitimate windows executable
- certx.tmp (PID: 7216)
Starts CMD.EXE for commands execution
- certx.tmp (PID: 7216)
Changes settings of the software policy
- regedit.exe (PID: 7904)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7720)
INFO
Create files in a temporary directory
- certx.exe (PID: 2392)
- certx.exe (PID: 7192)
- certx.tmp (PID: 7216)
Checks supported languages
- certx.exe (PID: 2392)
- certx.tmp (PID: 6640)
- certx.exe (PID: 7192)
- certx.tmp (PID: 7216)
- mode.com (PID: 7876)
- Certmgr.exe (PID: 7960)
- Certmgr.exe (PID: 7992)
- Certmgr.exe (PID: 1388)
- Certmgr.exe (PID: 2240)
- Certmgr.exe (PID: 6080)
- Certmgr.exe (PID: 7928)
- Certmgr.exe (PID: 6576)
- Certmgr.exe (PID: 5436)
- Certmgr.exe (PID: 7860)
- Certmgr.exe (PID: 7872)
- Certmgr.exe (PID: 5400)
- Certmgr.exe (PID: 7432)
- Certmgr.exe (PID: 7800)
- Certmgr.exe (PID: 208)
- Certmgr.exe (PID: 8176)
- Certmgr.exe (PID: 1760)
- Certmgr.exe (PID: 7824)
- Certmgr.exe (PID: 3304)
- Certmgr.exe (PID: 4892)
- Certmgr.exe (PID: 2284)
- Certmgr.exe (PID: 8056)
- Certmgr.exe (PID: 2516)
- Certmgr.exe (PID: 5608)
- Certmgr.exe (PID: 6644)
- Certmgr.exe (PID: 1188)
- Certmgr.exe (PID: 6584)
- Certmgr.exe (PID: 2316)
- Certmgr.exe (PID: 4408)
- Certmgr.exe (PID: 7436)
- Certmgr.exe (PID: 5960)
- Certmgr.exe (PID: 7312)
- Certmgr.exe (PID: 7524)
- Certmgr.exe (PID: 5116)
- Certmgr.exe (PID: 7576)
- Certmgr.exe (PID: 7716)
- Certmgr.exe (PID: 7736)
- Certmgr.exe (PID: 7652)
- Certmgr.exe (PID: 6488)
- Certmgr.exe (PID: 6564)
- Certmgr.exe (PID: 1244)
- Certmgr.exe (PID: 7876)
- Certmgr.exe (PID: 5720)
- Certmgr.exe (PID: 4268)
- Certmgr.exe (PID: 7944)
- Certmgr.exe (PID: 7980)
- Certmgr.exe (PID: 8000)
- Certmgr.exe (PID: 2420)
- Certmgr.exe (PID: 8020)
- Certmgr.exe (PID: 8036)
- Certmgr.exe (PID: 5756)
- Certmgr.exe (PID: 2552)
- Certmgr.exe (PID: 736)
- Certmgr.exe (PID: 7832)
- Certmgr.exe (PID: 7852)
Reads the computer name
- certx.tmp (PID: 6640)
- certx.tmp (PID: 7216)
Process checks computer location settings
- certx.tmp (PID: 6640)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 8124)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8124)
- BackgroundTransferHost.exe (PID: 7836)
- BackgroundTransferHost.exe (PID: 4724)
- BackgroundTransferHost.exe (PID: 6564)
- BackgroundTransferHost.exe (PID: 7480)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 8124)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 8124)
Detects InnoSetup installer (YARA)
- certx.exe (PID: 2392)
- certx.tmp (PID: 6640)
Compiled with Borland Delphi (YARA)
- certx.exe (PID: 2392)
- certx.tmp (PID: 6640)
Creates files in the program directory
- certx.tmp (PID: 7216)
The sample compiled with english language support
- certx.tmp (PID: 7216)
Creates a software uninstall entry
- certx.tmp (PID: 7216)
Starts MODE.COM to configure console settings
- mode.com (PID: 7876)
Reads the machine GUID from the registry
- Certmgr.exe (PID: 7960)
- Certmgr.exe (PID: 7992)
- Certmgr.exe (PID: 1388)
- Certmgr.exe (PID: 2240)
- Certmgr.exe (PID: 6080)
- Certmgr.exe (PID: 7928)
- Certmgr.exe (PID: 5400)
- Certmgr.exe (PID: 5436)
- Certmgr.exe (PID: 6576)
- Certmgr.exe (PID: 7872)
- Certmgr.exe (PID: 7860)
- Certmgr.exe (PID: 7824)
- Certmgr.exe (PID: 7800)
- Certmgr.exe (PID: 8176)
- Certmgr.exe (PID: 208)
- Certmgr.exe (PID: 1760)
- Certmgr.exe (PID: 3304)
- Certmgr.exe (PID: 7432)
- Certmgr.exe (PID: 2284)
- Certmgr.exe (PID: 4892)
- Certmgr.exe (PID: 8056)
- Certmgr.exe (PID: 1188)
- Certmgr.exe (PID: 2516)
- Certmgr.exe (PID: 5608)
- Certmgr.exe (PID: 6644)
- Certmgr.exe (PID: 6584)
- Certmgr.exe (PID: 2316)
- Certmgr.exe (PID: 4408)
- Certmgr.exe (PID: 5960)
- Certmgr.exe (PID: 7312)
- Certmgr.exe (PID: 7436)
- Certmgr.exe (PID: 7524)
- Certmgr.exe (PID: 5116)
- Certmgr.exe (PID: 6564)
- Certmgr.exe (PID: 7716)
- Certmgr.exe (PID: 7736)
- Certmgr.exe (PID: 7576)
- Certmgr.exe (PID: 7652)
- Certmgr.exe (PID: 6488)
- Certmgr.exe (PID: 1244)
- Certmgr.exe (PID: 4268)
- Certmgr.exe (PID: 7876)
- Certmgr.exe (PID: 7944)
- Certmgr.exe (PID: 7980)
- Certmgr.exe (PID: 2420)
- Certmgr.exe (PID: 8000)
- Certmgr.exe (PID: 5720)
- Certmgr.exe (PID: 8020)
- Certmgr.exe (PID: 5756)
- Certmgr.exe (PID: 2552)
- Certmgr.exe (PID: 736)
- Certmgr.exe (PID: 8036)
- Certmgr.exe (PID: 7832)
- Certmgr.exe (PID: 7852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
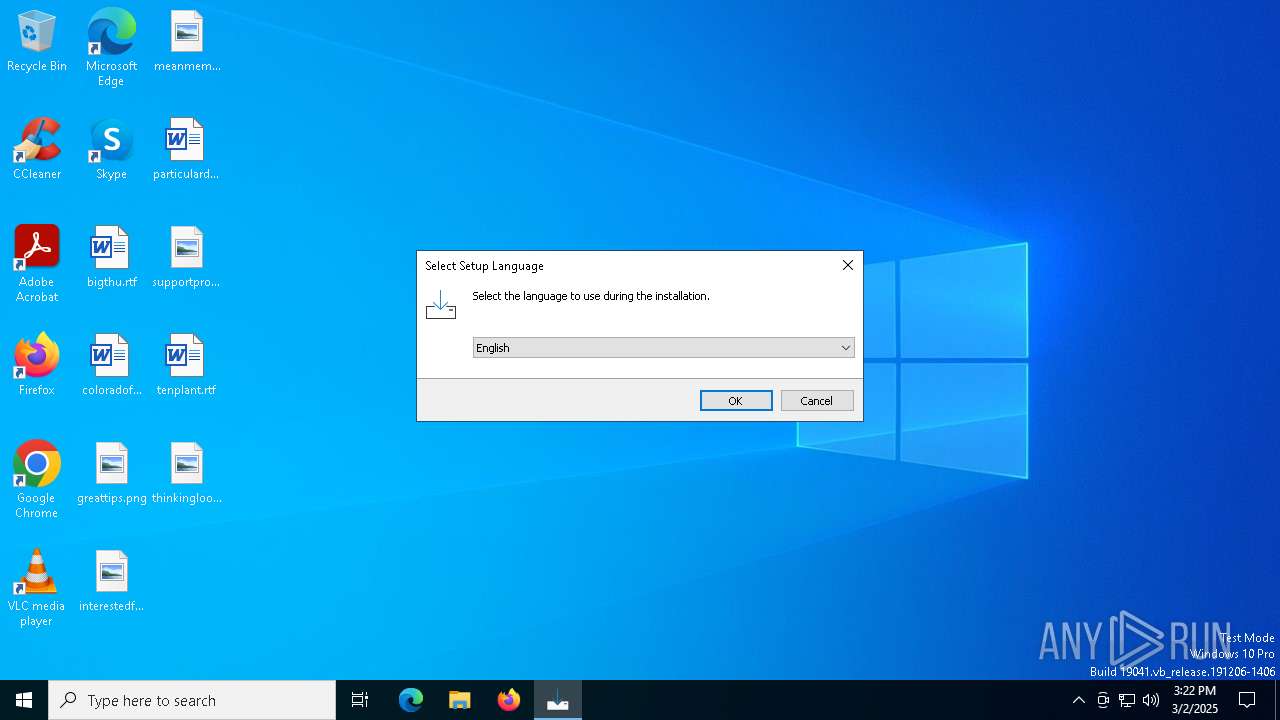
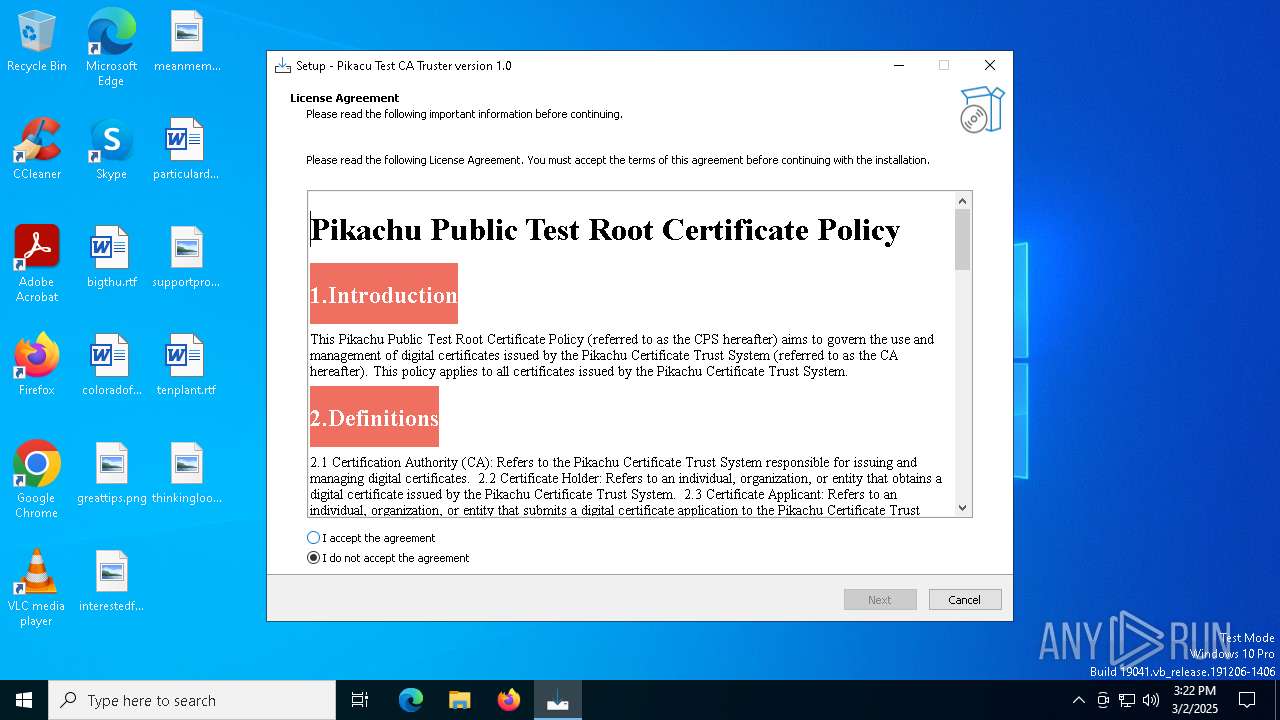
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Pikachu Software |
| FileDescription: | Pikacu Test CA Truster Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Pikacu Test CA Truster |
| ProductVersion: | 1.0 |
Total processes
201
Monitored processes
69
Malicious processes
5
Suspicious processes
54
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | certmgr.exe -crl -add /all .\3-Pikachu_UEFI_Sub_CA-G1.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 736 | certmgr.exe -crl -add /all .\9-Pikachu_Auth_Sub_CA-G1.crl -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1188 | certmgr.exe -crl -add /all .\4-Pikachu_Code_Sub_CA-G1.crl -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1244 | certmgr.exe -crl -add /all .\6-Pikachu_File_Sub_CA-G2.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1388 | certmgr.exe -crl -add /all .\0-Pikachu_Test_CA_RSA-G1.crl -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1760 | certmgr.exe -crl -add /all .\3-Pikachu_UEFI_Sub_CA-G2.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 2240 | certmgr.exe -crl -add /all .\0-Pikachu_Test_CA_RSA-G2.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 2284 | certmgr.exe -add /all .\4-Pikachu_Code_Sub_CA.crt -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 2316 | certmgr.exe -crl -add /all .\5-Pikachu_mTLS_Sub_CA-G1.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 2392 | "C:\Users\admin\AppData\Local\Temp\certx.exe" | C:\Users\admin\AppData\Local\Temp\certx.exe | explorer.exe | ||||||||||||
User: admin Company: Pikachu Software Integrity Level: MEDIUM Description: Pikacu Test CA Truster Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
70 491
Read events
70 385
Write events
68
Delete events
38
Modification events
| (PID) Process: | (7836) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7836) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7836) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8124) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8124) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8124) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4724) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4724) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4724) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6564) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
8
Suspicious files
8
Text files
64
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8124 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\63a0dd77-6de6-4334-a9d8-35e77830823b.down_data | — | |
MD5:— | SHA256:— | |||
| 2392 | certx.exe | C:\Users\admin\AppData\Local\Temp\is-GOPIM.tmp\certx.tmp | executable | |
MD5:2F129949F1A82013642BE1E44EC00CFC | SHA256:9CBF6C1DDC60CF30D4A3E096373B605989A0F7D66A77CE5EA9FD5CDECF847878 | |||
| 8124 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:E0B3999A065973D66514A2D37F4A4256 | SHA256:E74D60061991F2BA11A38D137BC501D43EFF15A3F6E9AFE187E4D5FAC20CE5A5 | |||
| 8124 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\3ce79ab9-fb1a-4d81-bd0e-9e729fee304f.up_meta_secure | binary | |
MD5:85C8BDF681591AC47630F23BF0E091AD | SHA256:34BE9DD22D35D9EE27CE3024D96C92DB504793D3293300846DB9F6070D19FF00 | |||
| 8124 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:CA6173FC5E87CAB1BEF55DAC3B19CB8F | SHA256:2784FA484E6E373A9A1451396BA9BF7E52CB1D3208E446A62EE6FC9E9D3D73D1 | |||
| 7216 | certx.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\is-9PMJT.tmp | executable | |
MD5:80D9E21D632513BD35001AFD753DD9C8 | SHA256:9226E6EE21D8AB76F82E8B83D7ED3008A52B696AF2715DAD70D70D61FB8DFCC7 | |||
| 7216 | certx.tmp | C:\Users\admin\AppData\Local\Temp\is-K0LAD.tmp\_isetup\_isdecmp.dll | executable | |
MD5:077CB4461A2767383B317EB0C50F5F13 | SHA256:8287D0E287A66EE78537C8D1D98E426562B95C50F569B92CEA9CE36A9FA57E64 | |||
| 8124 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\63a0dd77-6de6-4334-a9d8-35e77830823b.a9dcbfdc-f8eb-4a97-8d42-134e8ca7a768.down_meta | binary | |
MD5:DD3BA506927D456E7C71F78FEE480894 | SHA256:3C1C8BD24BBE1E3FF3E605732E4F85BAFF2AD7072CD1702074847497404FFC47 | |||
| 7216 | certx.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\is-QGHBL.tmp | text | |
MD5:9E19758E4FBBE5C3D4CAAD46E3647F6C | SHA256:1BBEFD27048316D71F413EF1BFA225E647B198F73D5B5AE54753484665C3CEBD | |||
| 7216 | certx.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\License.rtf | text | |
MD5:9E19758E4FBBE5C3D4CAAD46E3647F6C | SHA256:1BBEFD27048316D71F413EF1BFA225E647B198F73D5B5AE54753484665C3CEBD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8124 | BackgroundTransferHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7252 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8124 | BackgroundTransferHost.exe | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
8124 | BackgroundTransferHost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
8140 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |