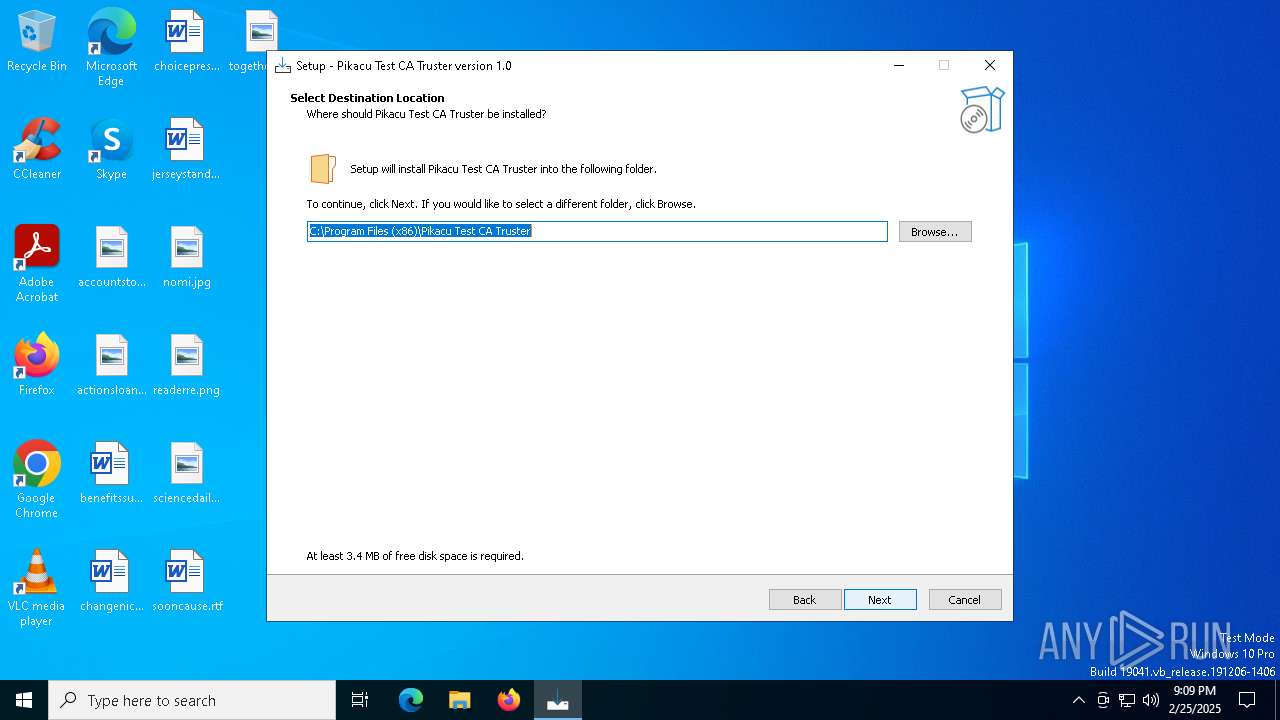
| File name: | CrypticSetup.exe |
| Full analysis: | https://app.any.run/tasks/600693b2-3542-48cf-ab9b-20f70d973860 |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2025, 21:08:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | A64517503ADB2A1BB8A2F58CA8A661DE |
| SHA1: | F8A5A7F0F6A974559E63EC744402A497A45150E2 |
| SHA256: | 11F4F22EABB173D8C37E80A3DE3BA1D321805FB6D5ADAE498C6628145811EF2E |
| SSDEEP: | 49152:67HecD4dnbibBlb+D7rP4jsbmLApne0Fop4R2uXB3iyLT/ex4XrL7P42DpJXWZnJ:q+cD4dni2P4IkWnXFopLQ3iUrex4vkYc |
MALICIOUS
Executing a file with an untrusted certificate
- Certmgr.exe (PID: 5656)
- Certmgr.exe (PID: 4608)
- Certmgr.exe (PID: 1240)
- Certmgr.exe (PID: 5968)
- Certmgr.exe (PID: 5956)
- Certmgr.exe (PID: 2892)
- Certmgr.exe (PID: 2664)
- Certmgr.exe (PID: 2316)
- Certmgr.exe (PID: 5400)
- Certmgr.exe (PID: 1132)
- Certmgr.exe (PID: 4976)
- Certmgr.exe (PID: 2644)
- Certmgr.exe (PID: 5428)
- Certmgr.exe (PID: 5032)
- Certmgr.exe (PID: 32)
- Certmgr.exe (PID: 1096)
- Certmgr.exe (PID: 6828)
- Certmgr.exe (PID: 6756)
- Certmgr.exe (PID: 1312)
- Certmgr.exe (PID: 5428)
- Certmgr.exe (PID: 6828)
- Certmgr.exe (PID: 5956)
- Certmgr.exe (PID: 6840)
- Certmgr.exe (PID: 2664)
- Certmgr.exe (PID: 3180)
- Certmgr.exe (PID: 4996)
- Certmgr.exe (PID: 5656)
- Certmgr.exe (PID: 5488)
- Certmgr.exe (PID: 6340)
- Certmgr.exe (PID: 7148)
- Certmgr.exe (PID: 5428)
- Certmgr.exe (PID: 5772)
- Certmgr.exe (PID: 2664)
- Certmgr.exe (PID: 5400)
- Certmgr.exe (PID: 5032)
- Certmgr.exe (PID: 5960)
- Certmgr.exe (PID: 6108)
- Certmgr.exe (PID: 5772)
- Certmgr.exe (PID: 3180)
- Certmgr.exe (PID: 5640)
- Certmgr.exe (PID: 4228)
- Certmgr.exe (PID: 5988)
- Certmgr.exe (PID: 4976)
- Certmgr.exe (PID: 6172)
- Certmgr.exe (PID: 3760)
- Certmgr.exe (PID: 5640)
- Certmgr.exe (PID: 3332)
- Certmgr.exe (PID: 6760)
- Certmgr.exe (PID: 4380)
- Certmgr.exe (PID: 5428)
- Certmgr.exe (PID: 1072)
- Certmgr.exe (PID: 6876)
- Certmgr.exe (PID: 3896)
SUSPICIOUS
Reads security settings of Internet Explorer
- CrypticSetup.tmp (PID: 2096)
Executable content was dropped or overwritten
- CrypticSetup.exe (PID: 6496)
- CrypticSetup.exe (PID: 1188)
- CrypticSetup.tmp (PID: 5116)
Process drops legitimate windows executable
- CrypticSetup.tmp (PID: 5116)
Starts CMD.EXE for commands execution
- CrypticSetup.tmp (PID: 5116)
Executing commands from a ".bat" file
- CrypticSetup.tmp (PID: 5116)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 536)
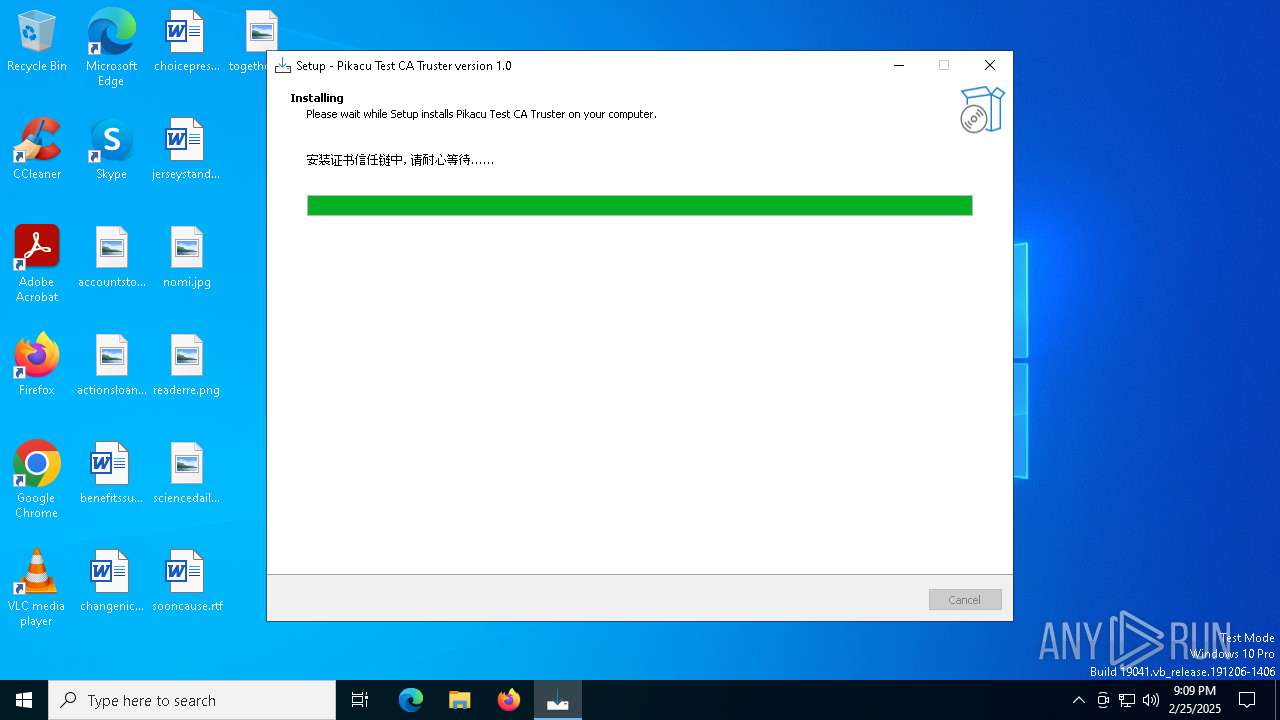
Adds/modifies Windows certificates
- Certmgr.exe (PID: 1240)
- Certmgr.exe (PID: 2664)
- Certmgr.exe (PID: 4976)
INFO
Checks supported languages
- CrypticSetup.exe (PID: 6496)
- CrypticSetup.exe (PID: 1188)
- CrypticSetup.tmp (PID: 2096)
- CrypticSetup.tmp (PID: 5116)
- mode.com (PID: 2316)
- Certmgr.exe (PID: 5656)
- Certmgr.exe (PID: 5968)
- Certmgr.exe (PID: 5956)
- Certmgr.exe (PID: 2664)
Process checks computer location settings
- CrypticSetup.tmp (PID: 2096)
Reads the computer name
- CrypticSetup.tmp (PID: 2096)
- CrypticSetup.tmp (PID: 5116)
Create files in a temporary directory
- CrypticSetup.exe (PID: 6496)
- CrypticSetup.exe (PID: 1188)
- CrypticSetup.tmp (PID: 5116)
Compiled with Borland Delphi (YARA)
- CrypticSetup.exe (PID: 6496)
- CrypticSetup.tmp (PID: 2096)
- CrypticSetup.exe (PID: 1188)
- CrypticSetup.tmp (PID: 5116)
Detects InnoSetup installer (YARA)
- CrypticSetup.exe (PID: 6496)
- CrypticSetup.tmp (PID: 2096)
- CrypticSetup.exe (PID: 1188)
- CrypticSetup.tmp (PID: 5116)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 1240)
- BackgroundTransferHost.exe (PID: 4884)
- BackgroundTransferHost.exe (PID: 5280)
- BackgroundTransferHost.exe (PID: 1096)
- BackgroundTransferHost.exe (PID: 5640)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 1240)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 1240)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 1240)
The sample compiled with english language support
- CrypticSetup.tmp (PID: 5116)
Creates files in the program directory
- CrypticSetup.tmp (PID: 5116)
Creates a software uninstall entry
- CrypticSetup.tmp (PID: 5116)
Starts MODE.COM to configure console settings
- mode.com (PID: 2316)
Reads the machine GUID from the registry
- Certmgr.exe (PID: 5968)
- Certmgr.exe (PID: 5956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
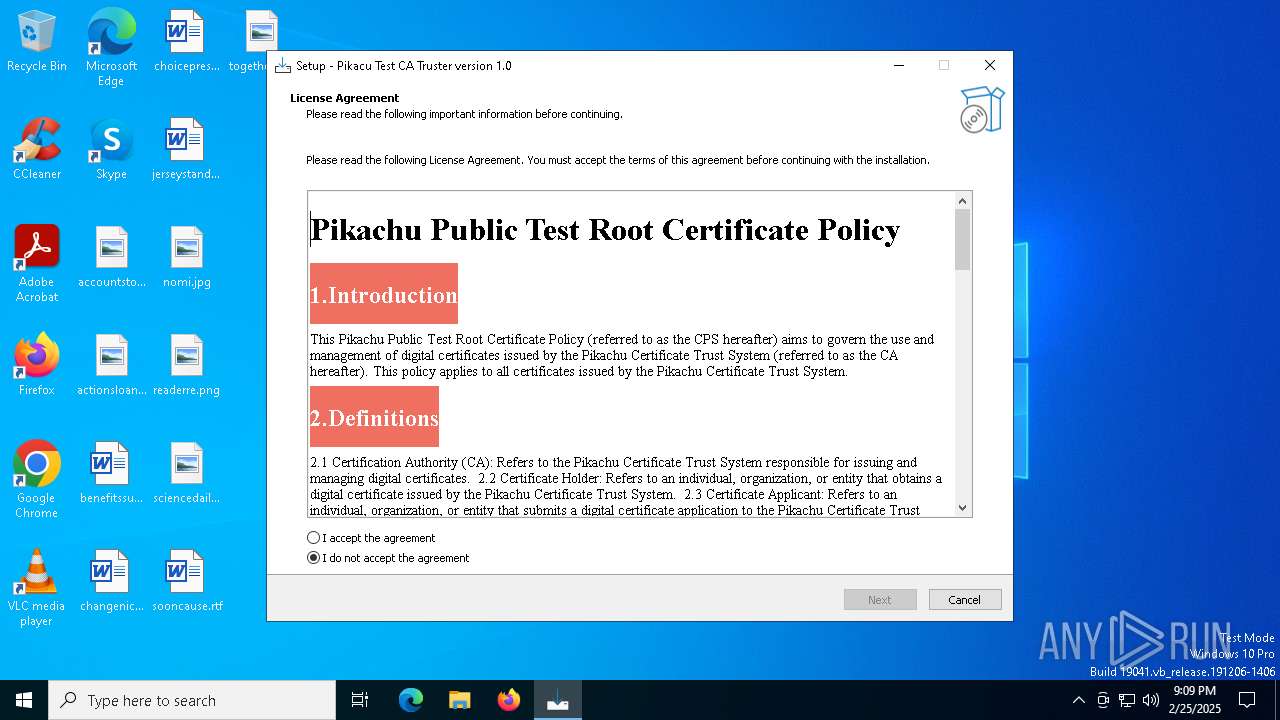
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Pikachu Software |
| FileDescription: | Pikacu Test CA Truster Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Pikacu Test CA Truster |
| ProductVersion: | 1.0 |
Total processes
208
Monitored processes
70
Malicious processes
5
Suspicious processes
53
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | certmgr.exe -crl -add /all .\3-Pikachu_UEFI_Sub_CA-G2.crl -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 536 | "C:\WINDOWS\system32\cmd.exe" /C ""C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\CA-INSTALL.bat"" | C:\Windows\SysWOW64\cmd.exe | — | CrypticSetup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 4294967295 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | certmgr.exe -crl -add /all .\8-Pikachu_Sign_Sub_CA-G2.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1096 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | certmgr.exe -crl -add /all .\4-Pikachu_Code_Sub_CA-G1.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1132 | certmgr.exe -crl -add /all .\2-Pikachu_Time_Sub_CA-G1.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1188 | "C:\Users\admin\AppData\Local\Temp\CrypticSetup.exe" /SPAWNWND=$80076 /NOTIFYWND=$8014C | C:\Users\admin\AppData\Local\Temp\CrypticSetup.exe | CrypticSetup.tmp | ||||||||||||
User: admin Company: Pikachu Software Integrity Level: HIGH Description: Pikacu Test CA Truster Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1240 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | certmgr.exe -crl -add /all .\0-Pikachu_Test_CA_RSA-G1.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
Total events
71 276
Read events
71 170
Write events
68
Delete events
38
Modification events
| (PID) Process: | (4884) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4884) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4884) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1240) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5280) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5280) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1096) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1096) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
8
Suspicious files
8
Text files
64
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1240 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\a9394abe-0fa1-4039-9730-91af3e1dd9fc.down_data | — | |
MD5:— | SHA256:— | |||
| 1240 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:8DDD7C6D4A3AB775235E44297C251885 | SHA256:9AB98597EE66662FE13E1D1ABDFA73756608C345060DA9D7842C851EDE3D7992 | |||
| 1240 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\a9394abe-0fa1-4039-9730-91af3e1dd9fc.45ab53b5-17a4-4705-afe6-66513f0b4b16.down_meta | binary | |
MD5:16FAABD3549AC41F09E9B902279301F7 | SHA256:4E1448C3A47E9409BEBED71F42E6E08849E5D67F3B1CCF958B1C7D0EF8BCE089 | |||
| 6496 | CrypticSetup.exe | C:\Users\admin\AppData\Local\Temp\is-AODSI.tmp\CrypticSetup.tmp | executable | |
MD5:2F129949F1A82013642BE1E44EC00CFC | SHA256:9CBF6C1DDC60CF30D4A3E096373B605989A0F7D66A77CE5EA9FD5CDECF847878 | |||
| 5116 | CrypticSetup.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\is-F84C2.tmp | executable | |
MD5:80D9E21D632513BD35001AFD753DD9C8 | SHA256:9226E6EE21D8AB76F82E8B83D7ED3008A52B696AF2715DAD70D70D61FB8DFCC7 | |||
| 5116 | CrypticSetup.tmp | C:\Users\admin\AppData\Local\Temp\is-DCJ7N.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1188 | CrypticSetup.exe | C:\Users\admin\AppData\Local\Temp\is-M4QVH.tmp\CrypticSetup.tmp | executable | |
MD5:2F129949F1A82013642BE1E44EC00CFC | SHA256:9CBF6C1DDC60CF30D4A3E096373B605989A0F7D66A77CE5EA9FD5CDECF847878 | |||
| 1240 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:A7C4FC91502C67AAF1FE0258BDADA99F | SHA256:0F1874268CA753EB8BD7BEBCD76FEFD972B3BBA4DCDF8B784F462D156C3364CA | |||
| 1240 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f50cae69-0c10-444b-96b3-a5dd835671b3.up_meta_secure | binary | |
MD5:95BCFDBEE4A07E0E021A0951DE86C926 | SHA256:8EE897F71E22DA0531F3D10FB69A2683A0C680A11DFE9A0FAD09574AD46B00C2 | |||
| 1240 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f50cae69-0c10-444b-96b3-a5dd835671b3.45ab53b5-17a4-4705-afe6-66513f0b4b16.down_meta | binary | |
MD5:16FAABD3549AC41F09E9B902279301F7 | SHA256:4E1448C3A47E9409BEBED71F42E6E08849E5D67F3B1CCF958B1C7D0EF8BCE089 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
38
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6228 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1240 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2316 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
760 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2924 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4880 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
404 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6228 | backgroundTaskHost.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6228 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |