| File name: | file.exe |
| Full analysis: | https://app.any.run/tasks/4036374c-f823-4945-804e-a564bdaf0017 |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2025, 18:34:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | A64517503ADB2A1BB8A2F58CA8A661DE |
| SHA1: | F8A5A7F0F6A974559E63EC744402A497A45150E2 |
| SHA256: | 11F4F22EABB173D8C37E80A3DE3BA1D321805FB6D5ADAE498C6628145811EF2E |
| SSDEEP: | 49152:67HecD4dnbibBlb+D7rP4jsbmLApne0Fop4R2uXB3iyLT/ex4XrL7P42DpJXWZnJ:q+cD4dni2P4IkWnXFopLQ3iUrex4vkYc |
MALICIOUS
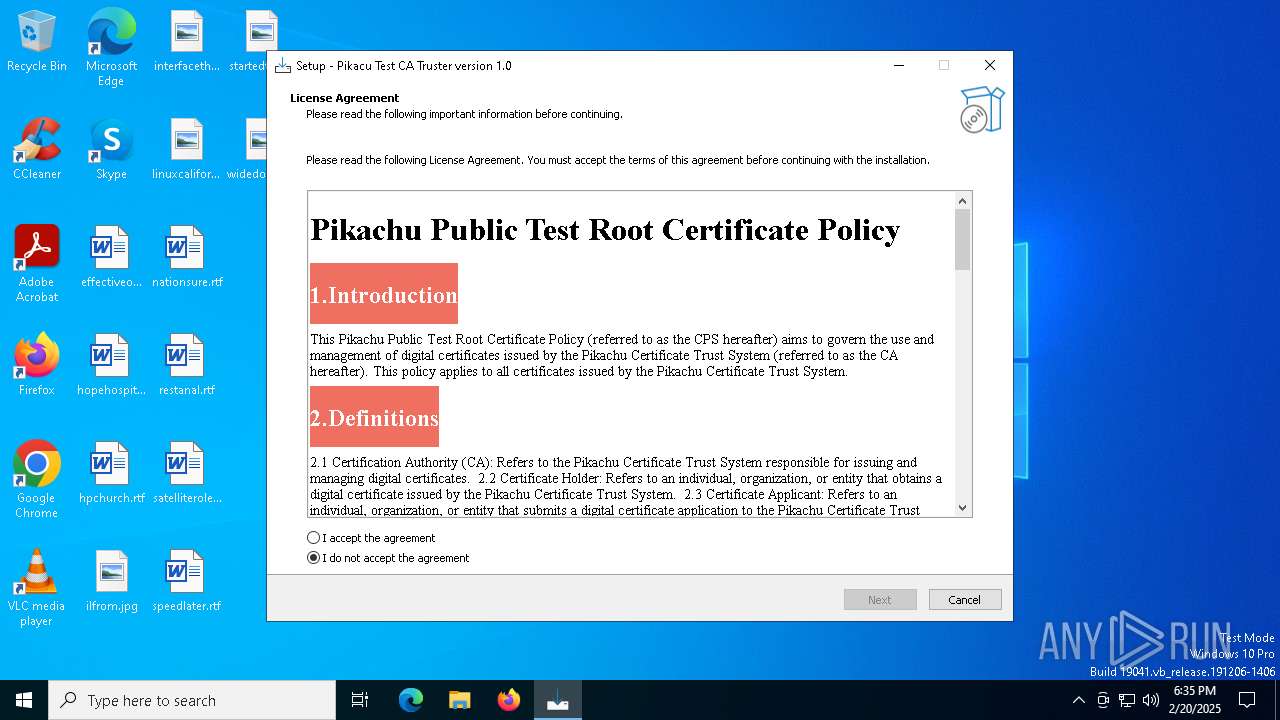
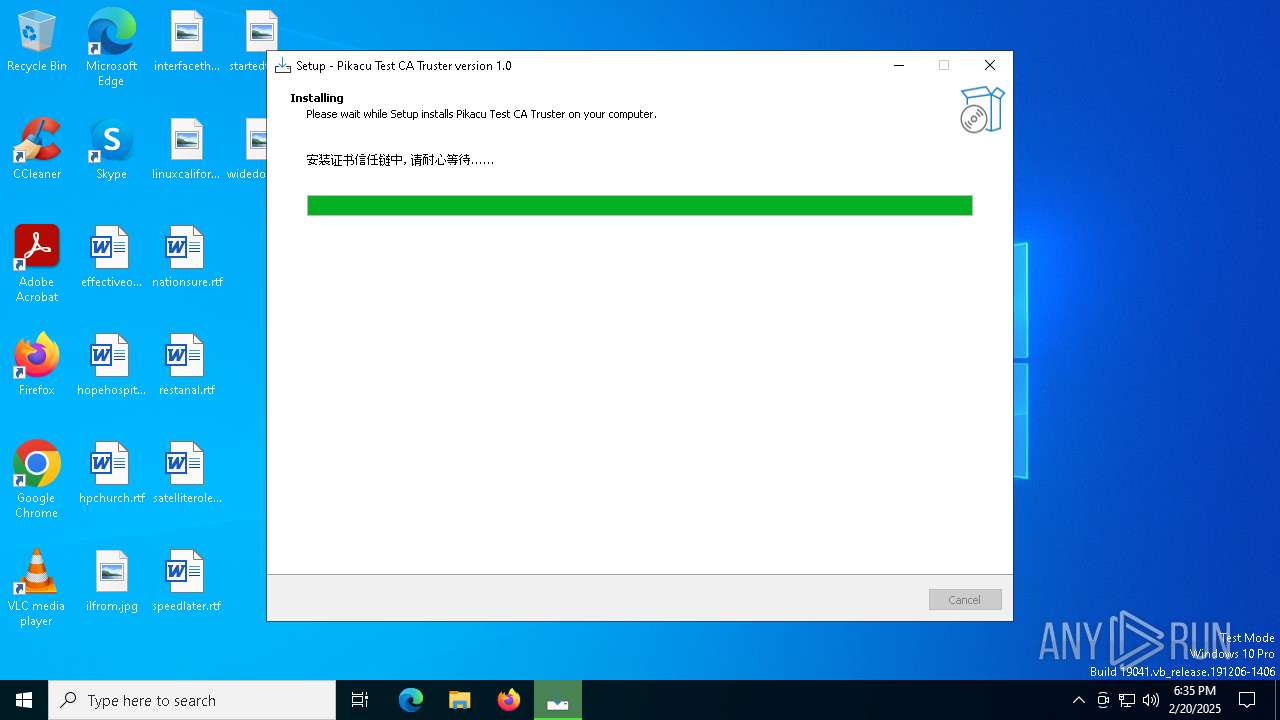
Executing a file with an untrusted certificate
- file.exe (PID: 6208)
- file.exe (PID: 6408)
- Certmgr.exe (PID: 5268)
- Certmgr.exe (PID: 5992)
- Certmgr.exe (PID: 3696)
- Certmgr.exe (PID: 4596)
- Certmgr.exe (PID: 3128)
- Certmgr.exe (PID: 5728)
- Certmgr.exe (PID: 624)
- Certmgr.exe (PID: 1580)
- Certmgr.exe (PID: 4672)
- Certmgr.exe (PID: 4188)
- Certmgr.exe (PID: 2776)
- Certmgr.exe (PID: 6580)
- Certmgr.exe (PID: 6548)
- Certmgr.exe (PID: 4164)
- Certmgr.exe (PID: 4668)
- Certmgr.exe (PID: 1200)
- Certmgr.exe (PID: 3560)
- Certmgr.exe (PID: 6800)
- Certmgr.exe (PID: 6764)
- Certmgr.exe (PID: 6656)
- Certmgr.exe (PID: 6904)
- Certmgr.exe (PID: 6808)
- Certmgr.exe (PID: 6832)
- Certmgr.exe (PID: 6784)
- Certmgr.exe (PID: 440)
- Certmgr.exe (PID: 3836)
- Certmgr.exe (PID: 6004)
- Certmgr.exe (PID: 640)
- Certmgr.exe (PID: 4704)
- Certmgr.exe (PID: 7084)
- Certmgr.exe (PID: 524)
- Certmgr.exe (PID: 5192)
- Certmgr.exe (PID: 6992)
- Certmgr.exe (PID: 7064)
- Certmgr.exe (PID: 1576)
- Certmgr.exe (PID: 396)
- Certmgr.exe (PID: 6692)
- Certmgr.exe (PID: 7140)
- Certmgr.exe (PID: 6272)
- Certmgr.exe (PID: 5556)
- Certmgr.exe (PID: 5916)
- Certmgr.exe (PID: 5460)
- Certmgr.exe (PID: 5592)
- Certmgr.exe (PID: 5604)
- Certmgr.exe (PID: 5752)
- Certmgr.exe (PID: 5472)
- Certmgr.exe (PID: 3988)
- Certmgr.exe (PID: 6464)
- Certmgr.exe (PID: 6468)
- Certmgr.exe (PID: 3436)
- Certmgr.exe (PID: 6556)
- Certmgr.exe (PID: 6588)
- Certmgr.exe (PID: 6476)
- Certmgr.exe (PID: 6552)
SUSPICIOUS
Executable content was dropped or overwritten
- file.exe (PID: 6208)
- file.exe (PID: 6408)
- file.tmp (PID: 6432)
Reads security settings of Internet Explorer
- file.tmp (PID: 6228)
Reads the Windows owner or organization settings
- file.tmp (PID: 6432)
Executing commands from a ".bat" file
- file.tmp (PID: 6432)
Process drops legitimate windows executable
- file.tmp (PID: 6432)
Starts CMD.EXE for commands execution
- file.tmp (PID: 6432)
Changes settings of the software policy
- regedit.exe (PID: 6400)
Adds/modifies Windows certificates
- Certmgr.exe (PID: 3560)
- Certmgr.exe (PID: 3696)
- Certmgr.exe (PID: 4596)
- Certmgr.exe (PID: 1580)
- Certmgr.exe (PID: 4188)
- Certmgr.exe (PID: 6580)
- Certmgr.exe (PID: 5268)
- regedit.exe (PID: 6400)
- Certmgr.exe (PID: 6476)
- Certmgr.exe (PID: 4668)
- Certmgr.exe (PID: 6832)
- Certmgr.exe (PID: 5460)
- Certmgr.exe (PID: 5472)
- Certmgr.exe (PID: 6468)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7120)
INFO
Checks supported languages
- file.exe (PID: 6208)
- file.tmp (PID: 6228)
- file.tmp (PID: 6432)
- file.exe (PID: 6408)
- mode.com (PID: 6200)
- Certmgr.exe (PID: 5268)
- Certmgr.exe (PID: 3560)
- Certmgr.exe (PID: 3696)
- Certmgr.exe (PID: 5992)
- Certmgr.exe (PID: 4596)
- Certmgr.exe (PID: 3128)
- Certmgr.exe (PID: 5728)
- Certmgr.exe (PID: 624)
- Certmgr.exe (PID: 1580)
- Certmgr.exe (PID: 4672)
- Certmgr.exe (PID: 4188)
- Certmgr.exe (PID: 2776)
- Certmgr.exe (PID: 6580)
- Certmgr.exe (PID: 6548)
- Certmgr.exe (PID: 6476)
- Certmgr.exe (PID: 4164)
- Certmgr.exe (PID: 4668)
- Certmgr.exe (PID: 1200)
- Certmgr.exe (PID: 6800)
- Certmgr.exe (PID: 6808)
- Certmgr.exe (PID: 6784)
- Certmgr.exe (PID: 6904)
- Certmgr.exe (PID: 6764)
- Certmgr.exe (PID: 6832)
- Certmgr.exe (PID: 440)
- Certmgr.exe (PID: 6004)
- Certmgr.exe (PID: 3836)
- Certmgr.exe (PID: 640)
- Certmgr.exe (PID: 4704)
- Certmgr.exe (PID: 7084)
- Certmgr.exe (PID: 524)
- Certmgr.exe (PID: 396)
- Certmgr.exe (PID: 6692)
- Certmgr.exe (PID: 5916)
- Certmgr.exe (PID: 5192)
- Certmgr.exe (PID: 5592)
- Certmgr.exe (PID: 5752)
- Certmgr.exe (PID: 3988)
- Certmgr.exe (PID: 3436)
- Certmgr.exe (PID: 6556)
Reads the computer name
- file.tmp (PID: 6228)
- file.tmp (PID: 6432)
Create files in a temporary directory
- file.exe (PID: 6208)
- file.exe (PID: 6408)
- file.tmp (PID: 6432)
Process checks computer location settings
- file.tmp (PID: 6228)
Compiled with Borland Delphi (YARA)
- file.exe (PID: 6208)
- file.tmp (PID: 6228)
- file.exe (PID: 6408)
- file.tmp (PID: 6432)
Detects InnoSetup installer (YARA)
- file.tmp (PID: 6228)
- file.exe (PID: 6408)
- file.exe (PID: 6208)
- file.tmp (PID: 6432)
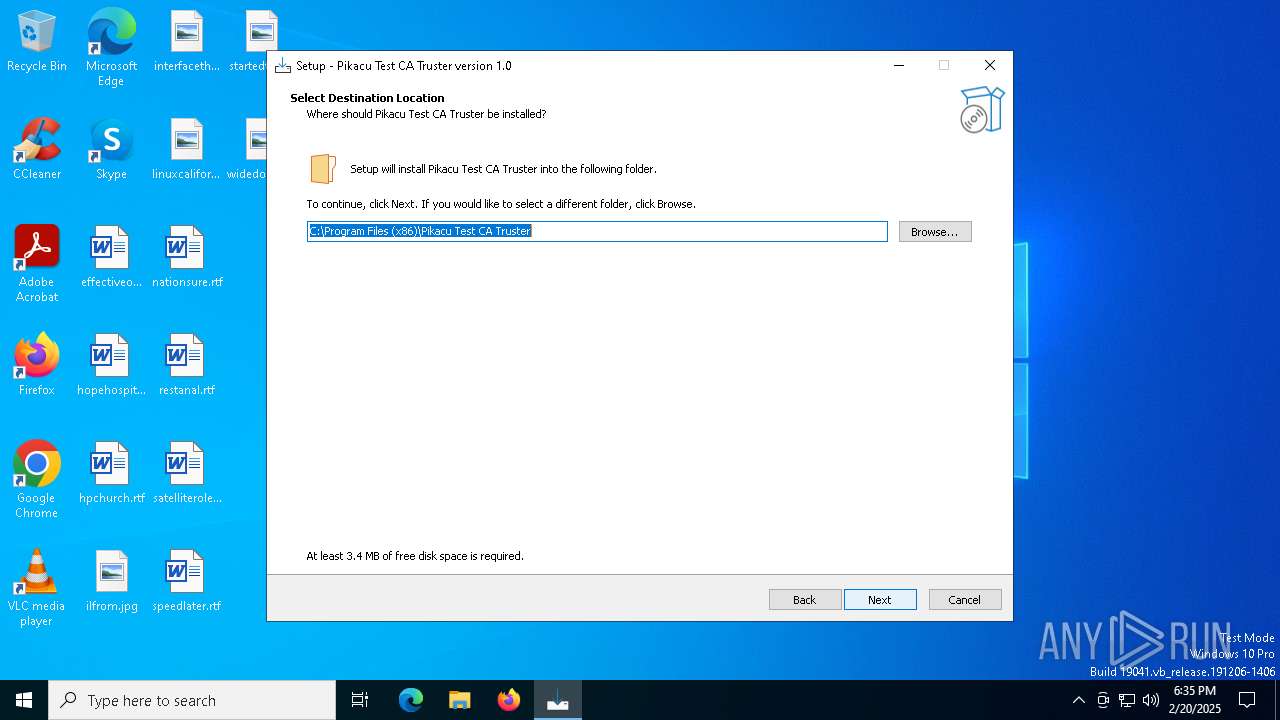
Creates files in the program directory
- file.tmp (PID: 6432)
The sample compiled with english language support
- file.tmp (PID: 6432)
Creates a software uninstall entry
- file.tmp (PID: 6432)
Starts MODE.COM to configure console settings
- mode.com (PID: 6200)
Reads the machine GUID from the registry
- Certmgr.exe (PID: 3560)
- Certmgr.exe (PID: 5268)
- Certmgr.exe (PID: 4596)
- Certmgr.exe (PID: 5992)
- Certmgr.exe (PID: 3696)
- Certmgr.exe (PID: 3128)
- Certmgr.exe (PID: 5728)
- Certmgr.exe (PID: 624)
- Certmgr.exe (PID: 1580)
- Certmgr.exe (PID: 4672)
- Certmgr.exe (PID: 4188)
- Certmgr.exe (PID: 6580)
- Certmgr.exe (PID: 2776)
- Certmgr.exe (PID: 6548)
- Certmgr.exe (PID: 4164)
- Certmgr.exe (PID: 1200)
- Certmgr.exe (PID: 4668)
- Certmgr.exe (PID: 6800)
- Certmgr.exe (PID: 6784)
- Certmgr.exe (PID: 6904)
- Certmgr.exe (PID: 6808)
- Certmgr.exe (PID: 6764)
- Certmgr.exe (PID: 6832)
- Certmgr.exe (PID: 440)
- Certmgr.exe (PID: 640)
- Certmgr.exe (PID: 7084)
- Certmgr.exe (PID: 4704)
- Certmgr.exe (PID: 524)
- Certmgr.exe (PID: 5192)
- Certmgr.exe (PID: 6692)
- Certmgr.exe (PID: 396)
- Certmgr.exe (PID: 5592)
- Certmgr.exe (PID: 5752)
- Certmgr.exe (PID: 3436)
- Certmgr.exe (PID: 6556)
- Certmgr.exe (PID: 6476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Pikachu Software |
| FileDescription: | Pikacu Test CA Truster Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Pikacu Test CA Truster |
| ProductVersion: | 1.0 |
Total processes
189
Monitored processes
62
Malicious processes
5
Suspicious processes
54
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | certmgr.exe -add /all .\7-Pikachu_Mail_Sub_CA.crt -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 440 | certmgr.exe -add /all .\5-Pikachu_mTLS_Sub_CA.crt -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 524 | certmgr.exe -add /all .\6-Pikachu_File_Sub_CA.crt -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 624 | certmgr.exe -add /all .\2-Pikachu_Time_Sub_CA.crt -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 640 | certmgr.exe -crl -add /all .\5-Pikachu_mTLS_Sub_CA-G2.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1200 | certmgr.exe -crl -add /all .\3-Pikachu_UEFI_Sub_CA-G2.crl -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1576 | certmgr.exe -crl -add /all .\6-Pikachu_File_Sub_CA-G2.crl -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 1580 | certmgr.exe -crl -add /all .\2-Pikachu_Time_Sub_CA-G1.crl -s -r localMachine AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 2776 | certmgr.exe -crl -add /all .\2-Pikachu_Time_Sub_CA-G2.crl -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
| 3128 | certmgr.exe -crl -add /all .\0-Pikachu_Test_CA_RSA-G2.crl -s -r currentUser AuthRoot | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\Certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 10.0.14393.795 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
Total events
68 835
Read events
68 744
Write events
53
Delete events
38
Modification events
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\Pikacu Test CA Truster | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Pikacu Test CA Truster\ | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Pikacu Test CA Truster | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: english | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Pikacu Test CA Truster version 1.0 | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\Pikacu Test CA Truster\unins000.exe" | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files (x86)\Pikacu Test CA Truster\unins000.exe" /SILENT | |||
| (PID) Process: | (6432) file.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7D4A8BF8-23CE-42A9-A2FB-37C8A1704FAC}_is1 |
| Operation: | write | Name: | DisplayVersion |
Value: 1.0 | |||
Executable files
8
Suspicious files
3
Text files
64
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6432 | file.tmp | C:\Users\admin\AppData\Local\Temp\is-VSLR4.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6408 | file.exe | C:\Users\admin\AppData\Local\Temp\is-73F6D.tmp\file.tmp | executable | |
MD5:2F129949F1A82013642BE1E44EC00CFC | SHA256:9CBF6C1DDC60CF30D4A3E096373B605989A0F7D66A77CE5EA9FD5CDECF847878 | |||
| 6432 | file.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\License.rtf | text | |
MD5:9E19758E4FBBE5C3D4CAAD46E3647F6C | SHA256:1BBEFD27048316D71F413EF1BFA225E647B198F73D5B5AE54753484665C3CEBD | |||
| 6432 | file.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\is-1FO1V.tmp | executable | |
MD5:322BF8029866CF3EB7F1DE33F18FB07A | SHA256:312DA44E936C59872EECF0C057F2D21F92EDFB2E712F646569513EE33BE269B0 | |||
| 6432 | file.tmp | C:\Users\admin\AppData\Local\Temp\is-VSLR4.tmp\_isetup\_isdecmp.dll | executable | |
MD5:077CB4461A2767383B317EB0C50F5F13 | SHA256:8287D0E287A66EE78537C8D1D98E426562B95C50F569B92CEA9CE36A9FA57E64 | |||
| 6432 | file.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\is-FTETJ.tmp | text | |
MD5:51F968C58DCD358393EA98DE5B0D340E | SHA256:1C83C4B49A985BA87BA0CD1BD0D65DB972F1F3FF5C4772744C16A093F7824EC5 | |||
| 6432 | file.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\is-81UPJ.tmp | text | |
MD5:C6B82192E9F8FCF65608A1A5640F706B | SHA256:D49701E4F6B57229FE7623A7355EA1B2AC14AD3D5A387D30387A3A82E403553E | |||
| 6432 | file.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\is-18NUS.tmp | text | |
MD5:D4A7EAE5025AB073E5E535B4A8BCAA2E | SHA256:36B8078C525B816A47A9F711AF22505C958DCD81786D93E67B5DB2CFD2F7C4A2 | |||
| 6432 | file.tmp | C:\Program Files (x86)\Pikacu Test CA Truster\Scripts\0-Pikachu_Test_CA_RSA.crt | text | |
MD5:C6B82192E9F8FCF65608A1A5640F706B | SHA256:D49701E4F6B57229FE7623A7355EA1B2AC14AD3D5A387D30387A3A82E403553E | |||
| 6208 | file.exe | C:\Users\admin\AppData\Local\Temp\is-K6EB6.tmp\file.tmp | executable | |
MD5:2F129949F1A82013642BE1E44EC00CFC | SHA256:9CBF6C1DDC60CF30D4A3E096373B605989A0F7D66A77CE5EA9FD5CDECF847878 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6968 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5452 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.54.122:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.54.122:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6968 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 95.101.54.122:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.54.122:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |