| File name: | UWPHook.exe |
| Full analysis: | https://app.any.run/tasks/86efb48e-158b-4f83-93ad-ca5c55ee2b21 |
| Verdict: | Malicious activity |
| Analysis date: | March 23, 2024, 11:22:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | E5A337AC3CA27FC79E65AE99D4BFB2A4 |
| SHA1: | 744C7560A1BE5636420908C3F4E7EC94EC029150 |
| SHA256: | 11F318737CBCFAC1CDA6B0EC062DEEEA6F5C01CF754408A8E26CCE4422A2DF87 |
| SSDEEP: | 98304:oM4lw9a3eo5vLe8OJjjfST3HkrDyCSNQGMxFnKmkvaVHa6gSr4BzyxZkkhDSgG32:COV5hVTfmPUjr |
MALICIOUS
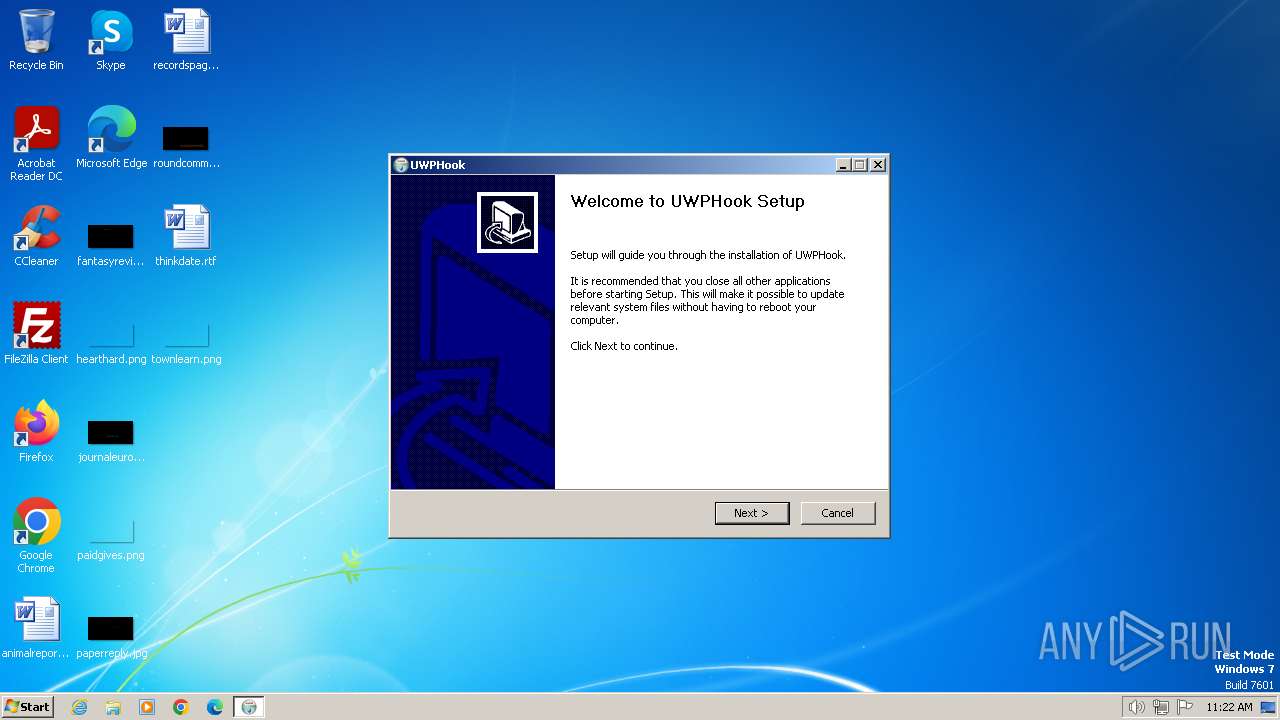
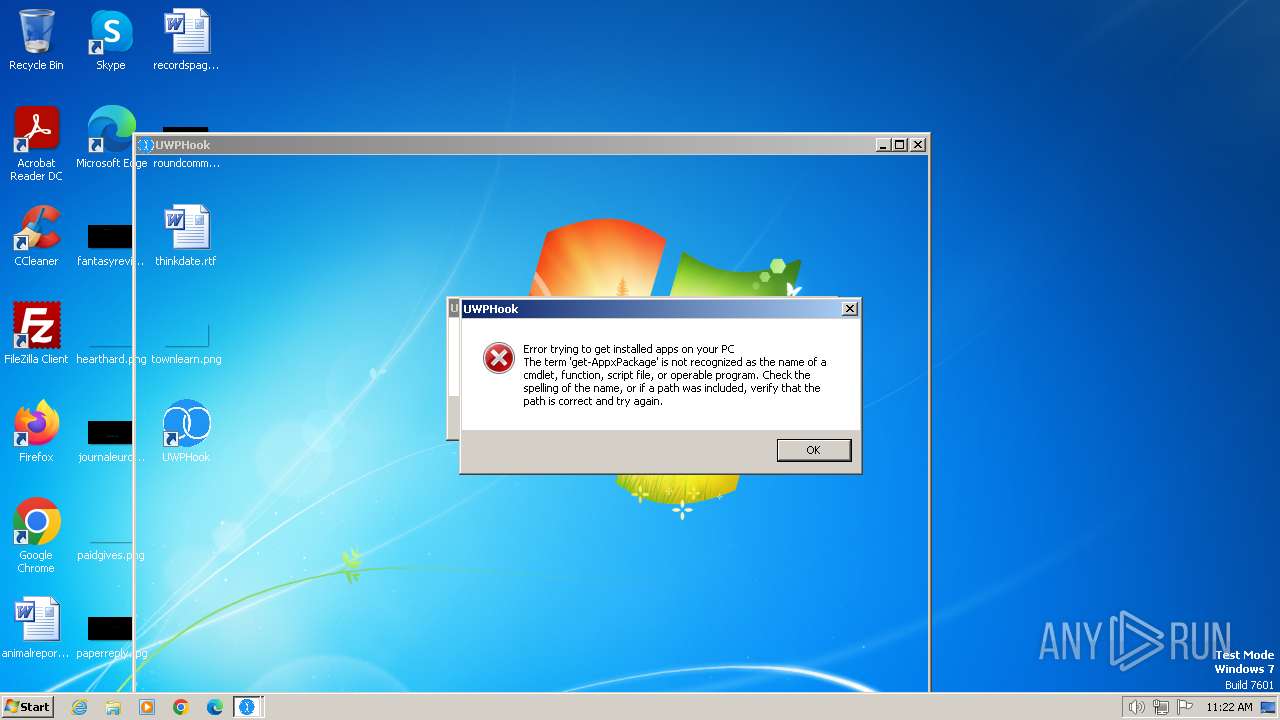
Drops the executable file immediately after the start
- UWPHook.exe (PID: 2408)
SUSPICIOUS
Process drops legitimate windows executable
- UWPHook.exe (PID: 2408)
Creates a software uninstall entry
- UWPHook.exe (PID: 2408)
Malware-specific behavior (creating "System.dll" in Temp)
- UWPHook.exe (PID: 2408)
The process creates files with name similar to system file names
- UWPHook.exe (PID: 2408)
Executable content was dropped or overwritten
- UWPHook.exe (PID: 2408)
Reads the Internet Settings
- UWPHook.exe (PID: 3164)
Reads security settings of Internet Explorer
- UWPHook.exe (PID: 3164)
Checks Windows Trust Settings
- UWPHook.exe (PID: 3164)
INFO
Checks supported languages
- UWPHook.exe (PID: 2408)
- UWPHook.exe (PID: 3164)
Create files in a temporary directory
- UWPHook.exe (PID: 2408)
- UWPHook.exe (PID: 3164)
Reads the computer name
- UWPHook.exe (PID: 2408)
- UWPHook.exe (PID: 3164)
Creates files or folders in the user directory
- UWPHook.exe (PID: 2408)
- UWPHook.exe (PID: 3164)
Reads the machine GUID from the registry
- UWPHook.exe (PID: 3164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.13.0.0 |
| ProductVersionNumber: | 2.13.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Briano |
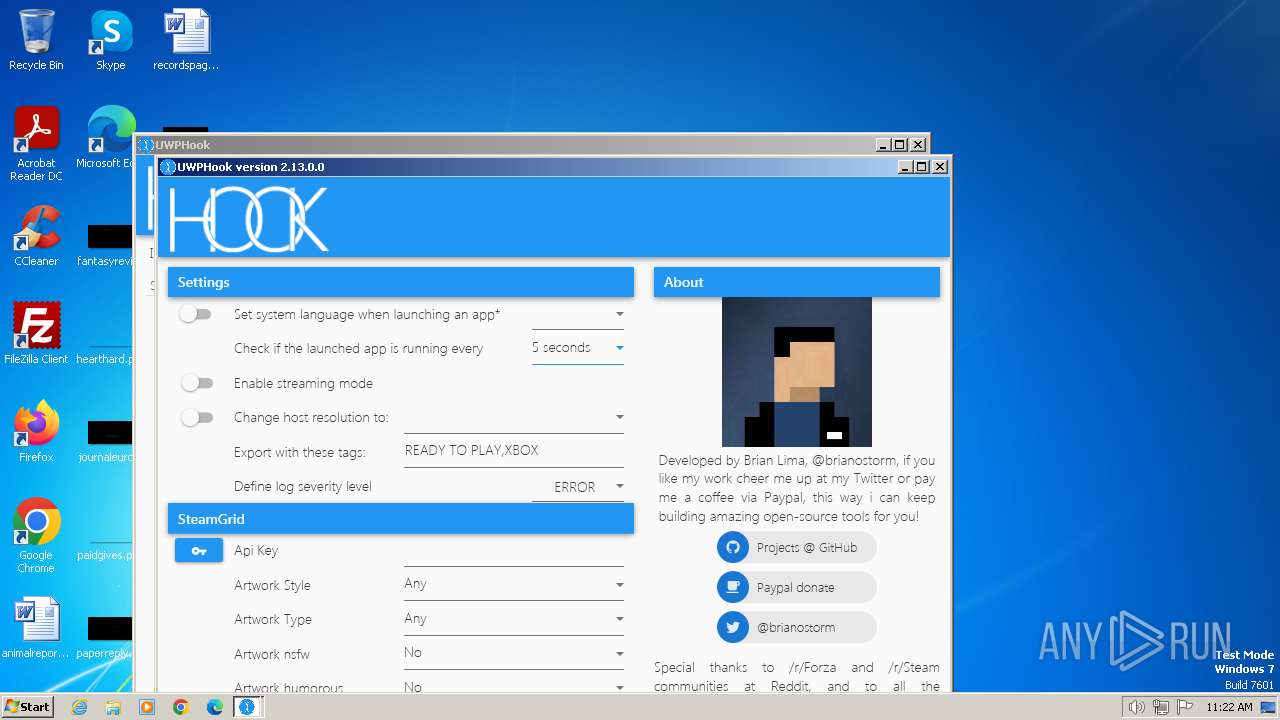
| FileDescription: | The easy way to add UWP and XGP games to Steam |
| FileVersion: | 2.13.00.00 |
| LegalCopyright: | Briano � 2020 2021 2022 |
| ProductName: | UWPHook |
Total processes
42
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2408 | "C:\Users\admin\AppData\Local\Temp\UWPHook.exe" | C:\Users\admin\AppData\Local\Temp\UWPHook.exe | explorer.exe | ||||||||||||
User: admin Company: Briano Integrity Level: HIGH Description: The easy way to add UWP and XGP games to Steam Exit code: 0 Version: 2.13.00.00 Modules
| |||||||||||||||
| 3164 | "C:\Users\admin\AppData\Roaming\Briano\UWPHook\UWPHook.exe" | C:\Users\admin\AppData\Roaming\Briano\UWPHook\UWPHook.exe | — | UWPHook.exe | |||||||||||
User: admin Company: Briano Integrity Level: HIGH Description: UWPHook Version: 2.13.0.0 Modules
| |||||||||||||||
| 3936 | "C:\Users\admin\AppData\Local\Temp\UWPHook.exe" | C:\Users\admin\AppData\Local\Temp\UWPHook.exe | — | explorer.exe | |||||||||||
User: admin Company: Briano Integrity Level: MEDIUM Description: The easy way to add UWP and XGP games to Steam Exit code: 3221226540 Version: 2.13.00.00 Modules
| |||||||||||||||
Total events
5 303
Read events
5 287
Write events
16
Delete events
0
Modification events
| (PID) Process: | (2408) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\UWPHook |
| Operation: | write | Name: | Start Menu Folder |
Value: UWPHook | |||
| (PID) Process: | (2408) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\UWPHook |
| Operation: | write | Name: | DisplayName |
Value: UWPHook | |||
| (PID) Process: | (2408) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\UWPHook |
| Operation: | write | Name: | UninstallString |
Value: C:\Users\admin\AppData\Roaming\Briano\UWPHook\uninstall.exe | |||
| (PID) Process: | (2408) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\UWPHook |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Roaming\Briano\UWPHook\UWPHook.exe | |||
| (PID) Process: | (2408) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\UWPHook |
| Operation: | write | Name: | DisplayVersion |
Value: 2.13.00.00 | |||
| (PID) Process: | (2408) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\UWPHook |
| Operation: | write | Name: | Publisher |
Value: Briano | |||
| (PID) Process: | (2408) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\UWPHook |
| Operation: | write | Name: | URLInfoAbout |
Value: https://briano.dev | |||
| (PID) Process: | (3164) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: UWPHook.exe | |||
| (PID) Process: | (3164) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3164) UWPHook.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
16
Suspicious files
5
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Roaming\Briano\UWPHook\Serilog.Sinks.File.dll | executable | |
MD5:C25357A7950DCFC7F85EE9D593CB1A24 | SHA256:5B70DC2EECEB1963F9C3690C1CC8FFA793B280E903FA9A31780E6A7BB0BDFCF9 | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Roaming\Briano\UWPHook\Serilog.Sinks.Console.dll | executable | |
MD5:A43DBE6F78CBB5C009170394713E3353 | SHA256:061F651AF1A705A08E2CC76A9FB35DBF2703EE2D997A259370E2248DD3C36FE5 | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Roaming\Briano\UWPHook\Serilog.dll | executable | |
MD5:35B1B9F1538CBDAB039F4A79826041FE | SHA256:5C2F34412502F6C5A5AA9226B71F4809AA73BF90F46C79FAEB97172955178B26 | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Roaming\Briano\UWPHook\SharpSteam.dll | executable | |
MD5:B13E5FA89D43E6A77B6FDD0512550D08 | SHA256:91608BA25605EE76AB39F23777D665986D3B477F4348EFC2DDD50EEB6202F18F | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Roaming\Briano\UWPHook\System.Net.Http.Formatting.dll | executable | |
MD5:4A7816CB1067972450045E4AFA50A0B8 | SHA256:00664130B963ACE5F1243AE4786926EA81BC181086FC7149D6123567C304D35B | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Roaming\Briano\UWPHook\VDFParser.dll | executable | |
MD5:F0703B2C4AC41420884D1D8678C236EB | SHA256:E3A8BE27A08A2FB5465C38AE4E677EF1BACAD59265B914ED2EFE70C4606E64E8 | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Roaming\Briano\UWPHook\MaterialDesignThemes.Wpf.dll | executable | |
MD5:D08228BB1C4DD939844963C34BC1853C | SHA256:47113A39A1BE07BA3FF5D1615ED77F82758FCF1CCC5617BD014BF031F8788187 | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Local\Temp\nsm1FF7.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Local\Temp\nsm1FF7.tmp\InstallOptions.dll | executable | |
MD5:ECE25721125D55AA26CDFE019C871476 | SHA256:C7FEF6457989D97FECC0616A69947927DA9D8C493F7905DC8475C748F044F3CF | |||
| 2408 | UWPHook.exe | C:\Users\admin\AppData\Roaming\Briano\UWPHook\Crc32.NET.dll | executable | |
MD5:CCE714483B5568F140C904C30A38BCE6 | SHA256:9EAFBEC3431A3DDC072D870DD71F96D4FD421EFF27B3F855FB29DDE31463803A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |