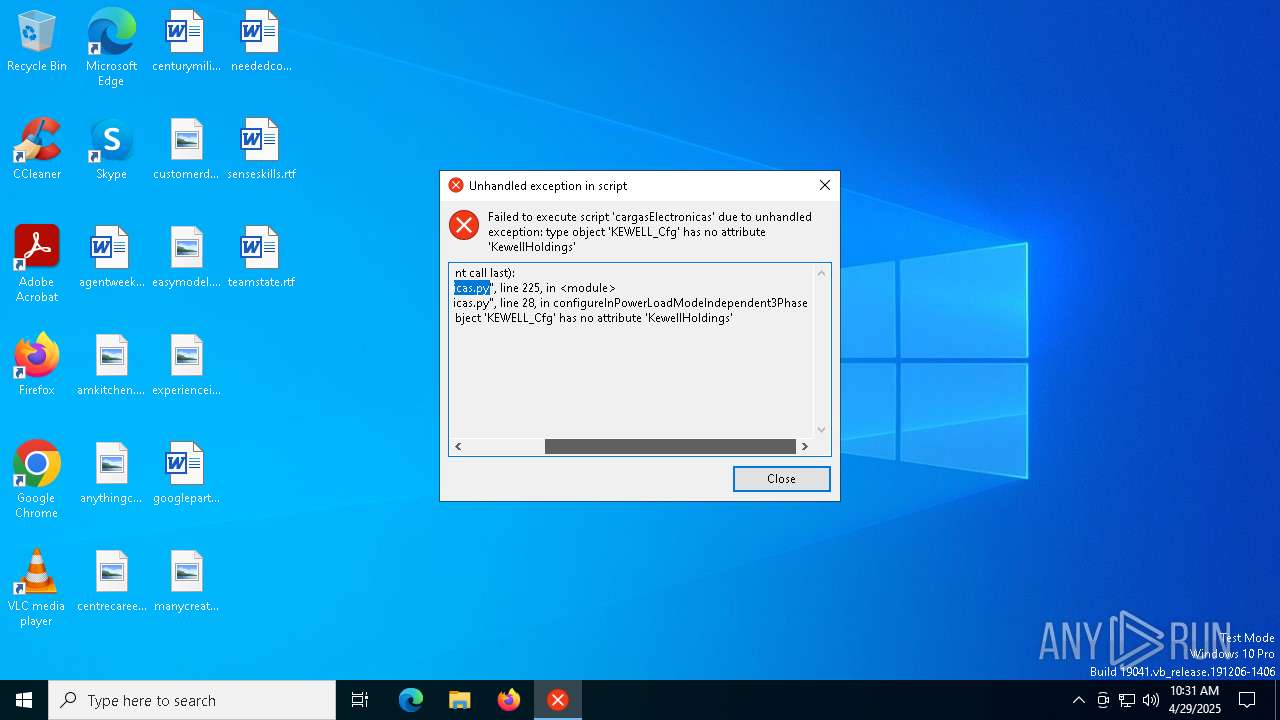
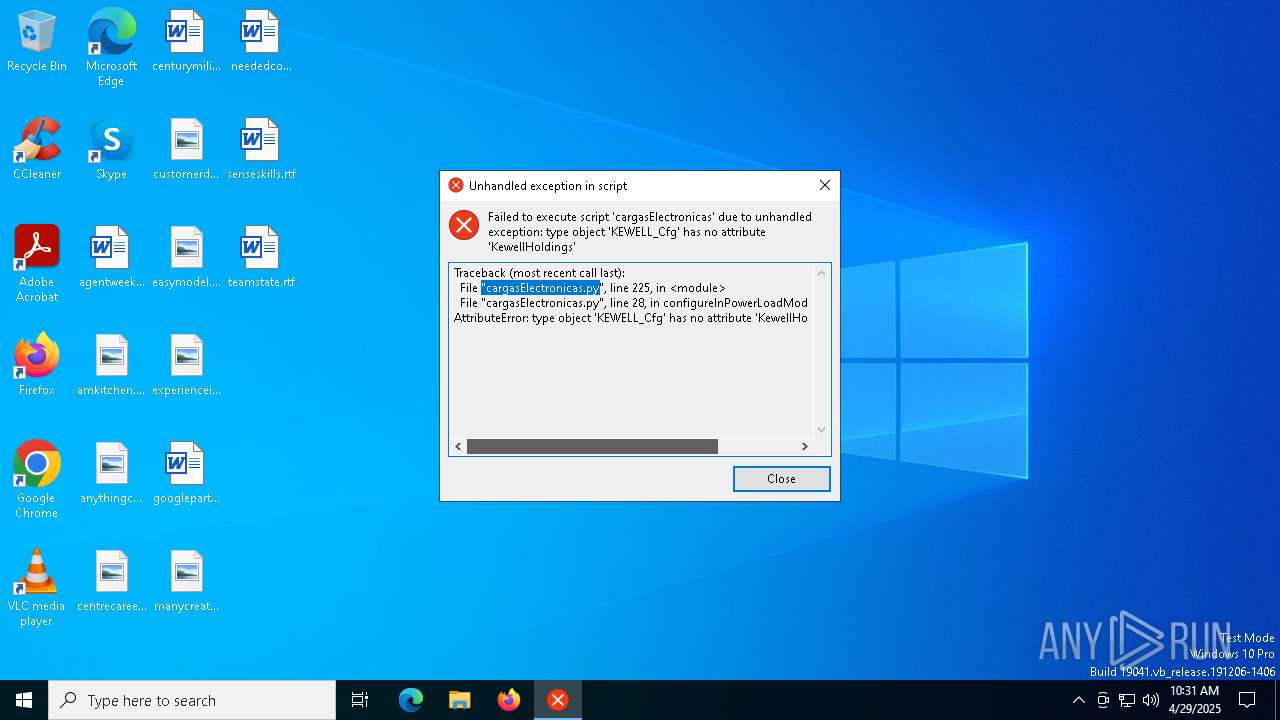
| File name: | $RLIKEJQ.exe |
| Full analysis: | https://app.any.run/tasks/6c17a175-f35c-45ae-9fb1-335af276f968 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 10:30:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | D88CDD089AD632711A6F1594A1FFC019 |
| SHA1: | CD2512A201C58322EFFBD1F4C458E7D4DB0BBD9F |
| SHA256: | 11E5284FB493BF8B82DA12F9973FA1CF30C597A9C6EB54581E06DB48D697E446 |
| SSDEEP: | 98304:cCYzBadpQWtg3Ry77bdz3HIeSe8z94IfbPwMKeXt5xUtQen/Tqv9SrLlPSPXbBVV:F2ztwkWRyn6stJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
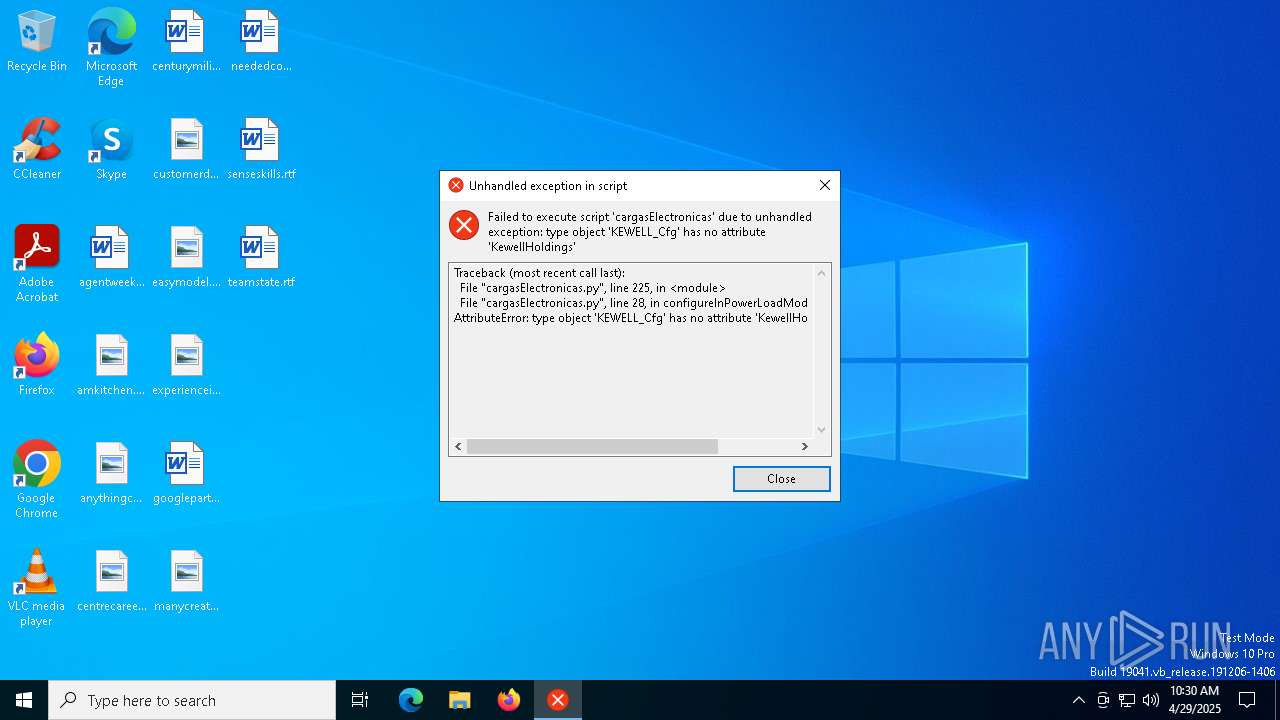
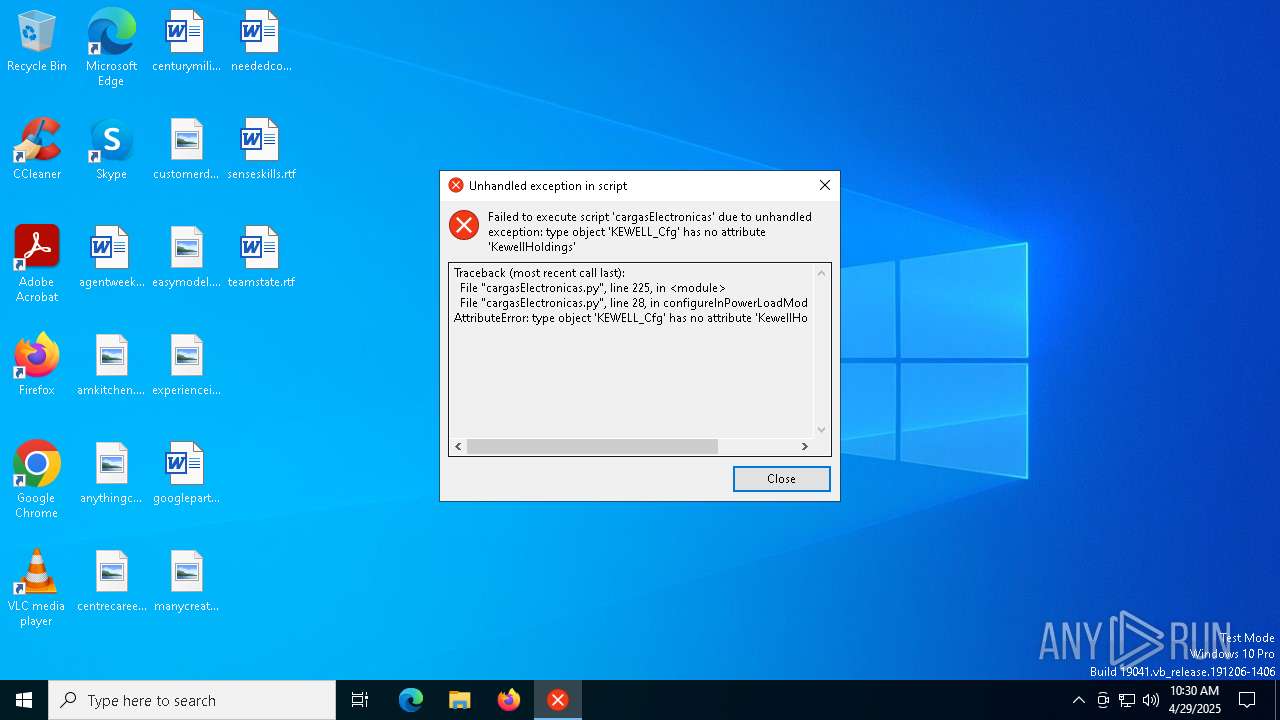
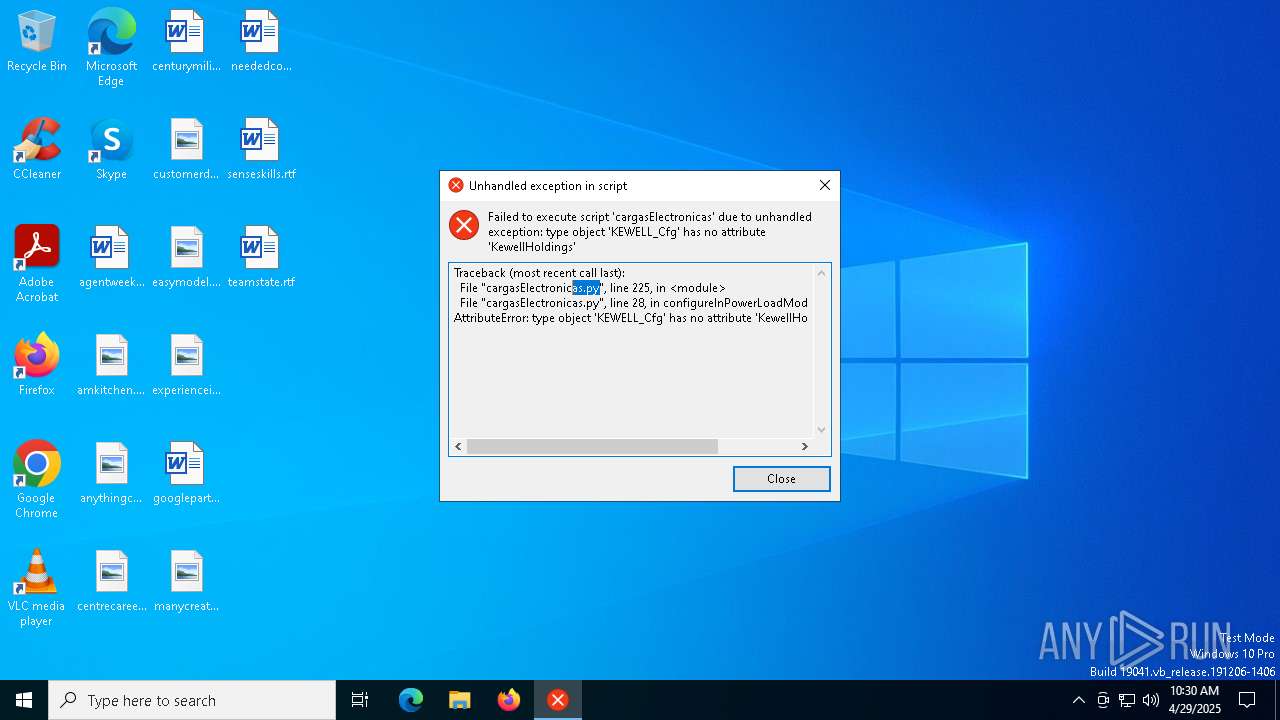
Process drops python dynamic module
- $RLIKEJQ.exe (PID: 7212)
Executable content was dropped or overwritten
- $RLIKEJQ.exe (PID: 7212)
The process drops C-runtime libraries
- $RLIKEJQ.exe (PID: 7212)
Process drops legitimate windows executable
- $RLIKEJQ.exe (PID: 7212)
Application launched itself
- $RLIKEJQ.exe (PID: 7212)
Loads Python modules
- $RLIKEJQ.exe (PID: 7248)
There is functionality for taking screenshot (YARA)
- $RLIKEJQ.exe (PID: 7212)
- $RLIKEJQ.exe (PID: 7248)
INFO
Reads the computer name
- $RLIKEJQ.exe (PID: 7212)
- $RLIKEJQ.exe (PID: 7248)
Checks supported languages
- $RLIKEJQ.exe (PID: 7212)
- $RLIKEJQ.exe (PID: 7248)
Create files in a temporary directory
- $RLIKEJQ.exe (PID: 7212)
The sample compiled with english language support
- $RLIKEJQ.exe (PID: 7212)
Reads the machine GUID from the registry
- $RLIKEJQ.exe (PID: 7248)
PyInstaller has been detected (YARA)
- $RLIKEJQ.exe (PID: 7248)
- $RLIKEJQ.exe (PID: 7212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:24 13:55:08+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 173568 |
| InitializedDataSize: | 155648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce30 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
134
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7212 | "C:\Users\admin\AppData\Local\Temp\$RLIKEJQ.exe" | C:\Users\admin\AppData\Local\Temp\$RLIKEJQ.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7248 | "C:\Users\admin\AppData\Local\Temp\$RLIKEJQ.exe" | C:\Users\admin\AppData\Local\Temp\$RLIKEJQ.exe | — | $RLIKEJQ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
197
Read events
197
Write events
0
Delete events
0
Modification events
Executable files
58
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\_bz2.pyd | executable | |
MD5:124678D21D4B747EC6F1E77357393DD6 | SHA256:9483C4853CA1DA3C5B2310DBDD3B835A44DF6066620278AA96B2E665C4B4E86B | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\_hashlib.pyd | executable | |
MD5:AE32A39887D7516223C1E7FFDC3B6911 | SHA256:7936413BC24307F01B90CAC2D2CC19F38264D396C1AB8EDA180ABBA2F77162EB | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\_decimal.pyd | executable | |
MD5:BB70FC3EB76B6801ED7228B6869017B2 | SHA256:831E4CE99F469FA94567482444AF492891B7BF327853E92DD4BB2CE092021E74 | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\_lzma.pyd | executable | |
MD5:A77C9A75ED7D9F455E896B8FB09B494C | SHA256:4797AAF192EB56B32CA4FEBD1FAD5BE9E01A24E42BF6AF2D04FCDF74C8D36FA5 | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\_multiprocessing.pyd | executable | |
MD5:090756C9D9317A92830E81A0493A1767 | SHA256:A55C37779772A36BFB5811CC349DCDC2429EF1FBAB40FE4CFEA9D7FCD23173AB | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\_overlapped.pyd | executable | |
MD5:22AC38D86314E8BC4A6F7932223F3594 | SHA256:FD9E9467E1353F9DC02143481085F2440F25286D0A4630AA8B1D8919CBB50B8F | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\_ctypes.pyd | executable | |
MD5:7AB242D7C026DAD5E5837B4579BD4EDA | SHA256:1548506345D220D68E9089B9A68B42A9D796141EB6236E600283951CB206EAA1 | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\_asyncio.pyd | executable | |
MD5:3510357B9885A59B08FA557E3BAED3CE | SHA256:3AD5F4BD4361DF0C077122A91D180DCF9B68B0249FC6B39EDDA5DD4ECE6F23F1 | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:2DB5666D3600A4ABCE86BE0099C6B881 | SHA256:46079C0A1B660FC187AAFD760707F369D0B60D424D878C57685545A3FCE95819 | |||
| 7212 | $RLIKEJQ.exe | C:\Users\admin\AppData\Local\Temp\_MEI72122\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:624401F31A706B1AE2245EB19264DC7F | SHA256:58A8D69DF60ECBEE776CD9A74B2A32B14BF2B0BD92D527EC5F19502A0D3EB8E9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.15:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7828 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7828 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6708 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.15:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |