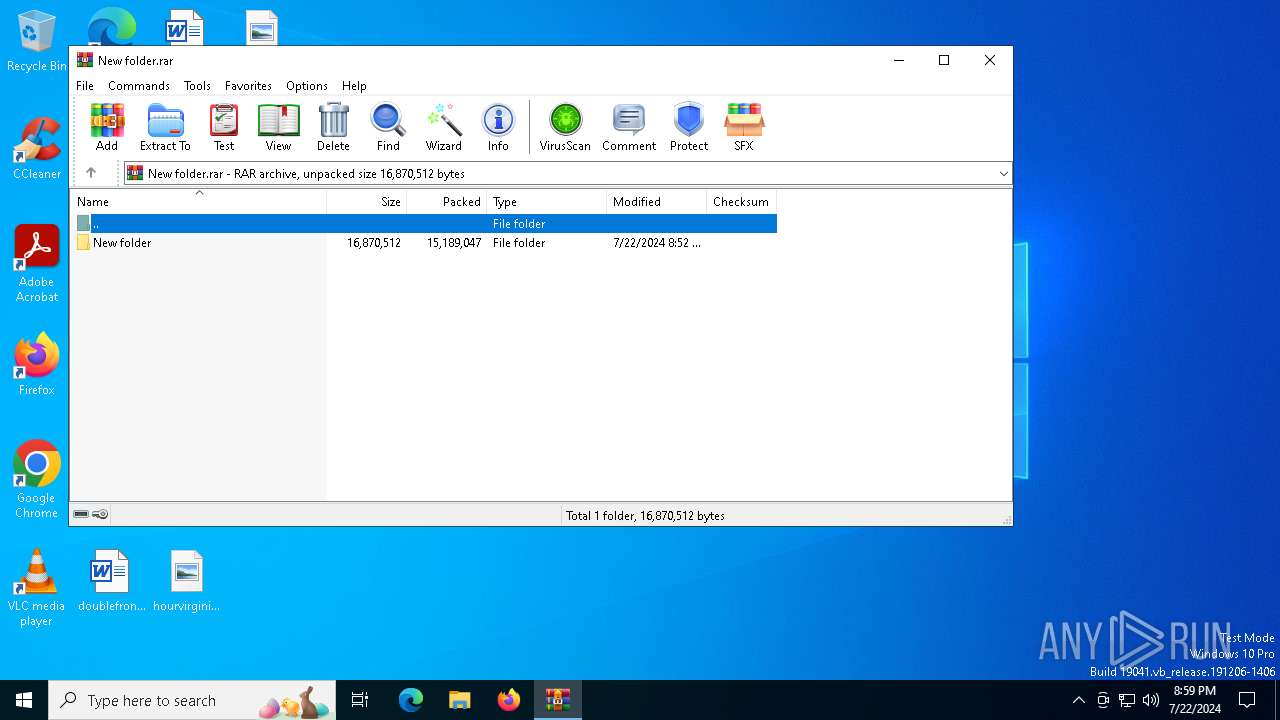
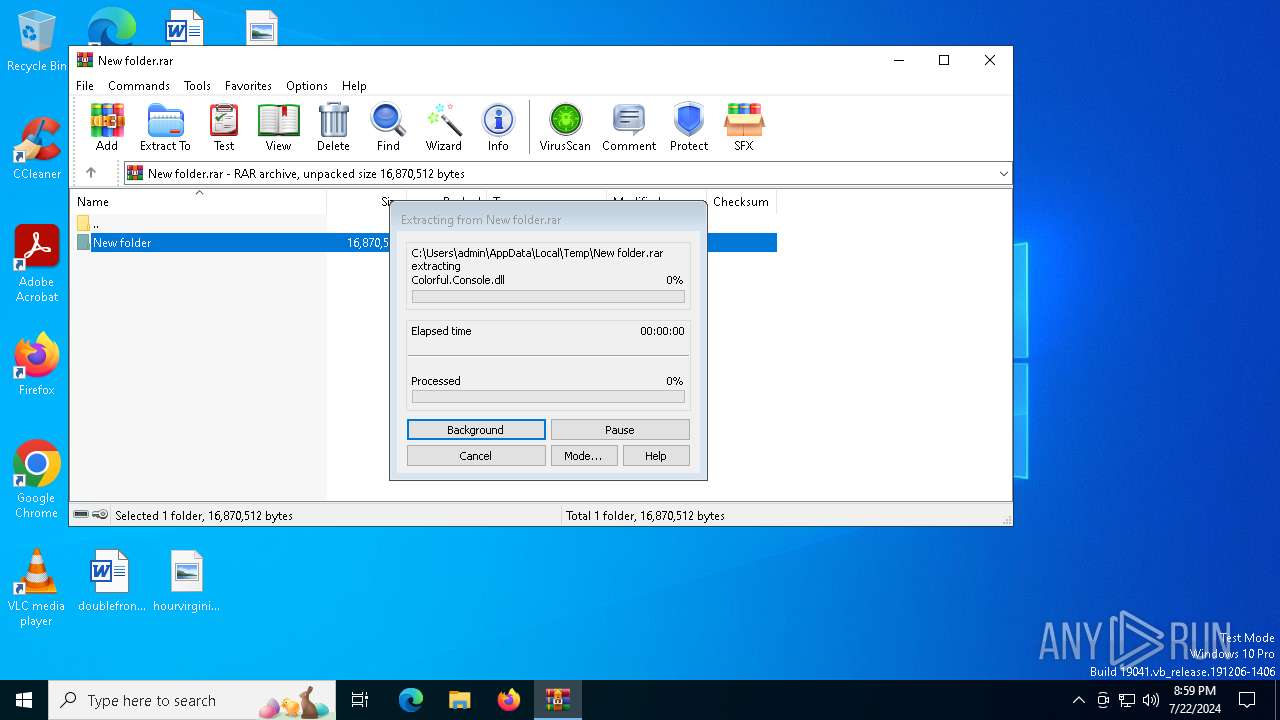
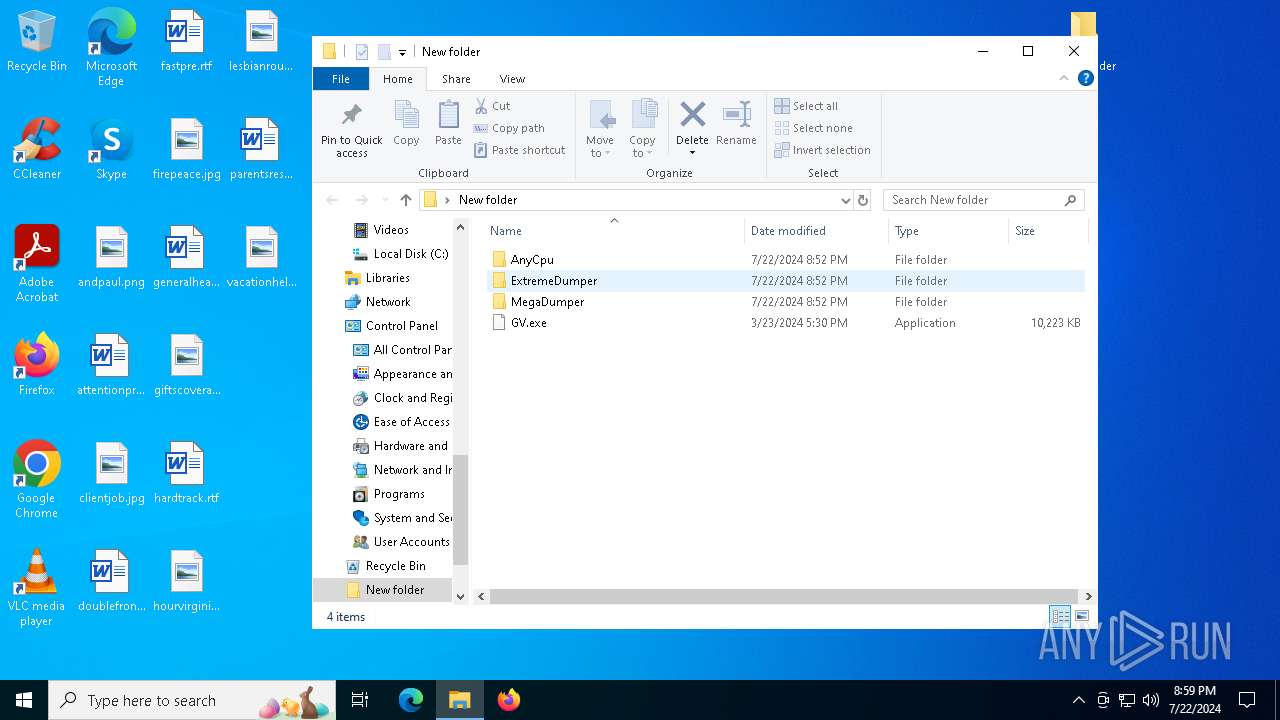
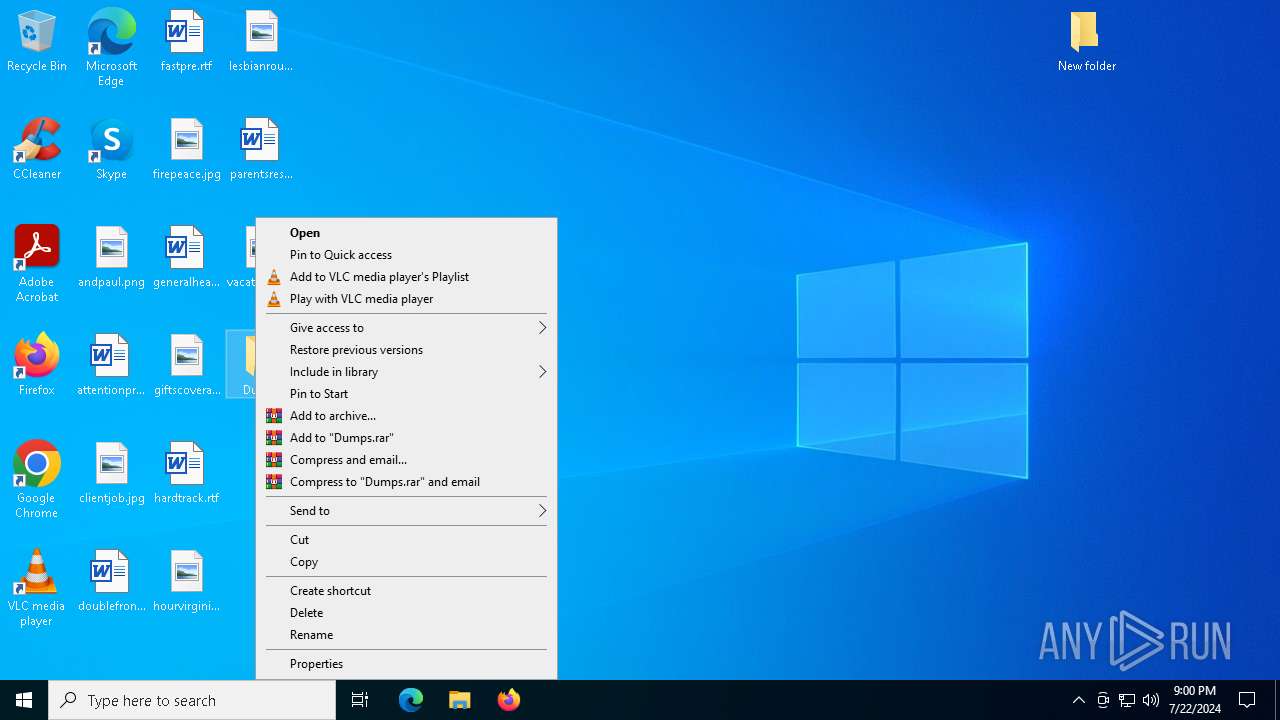
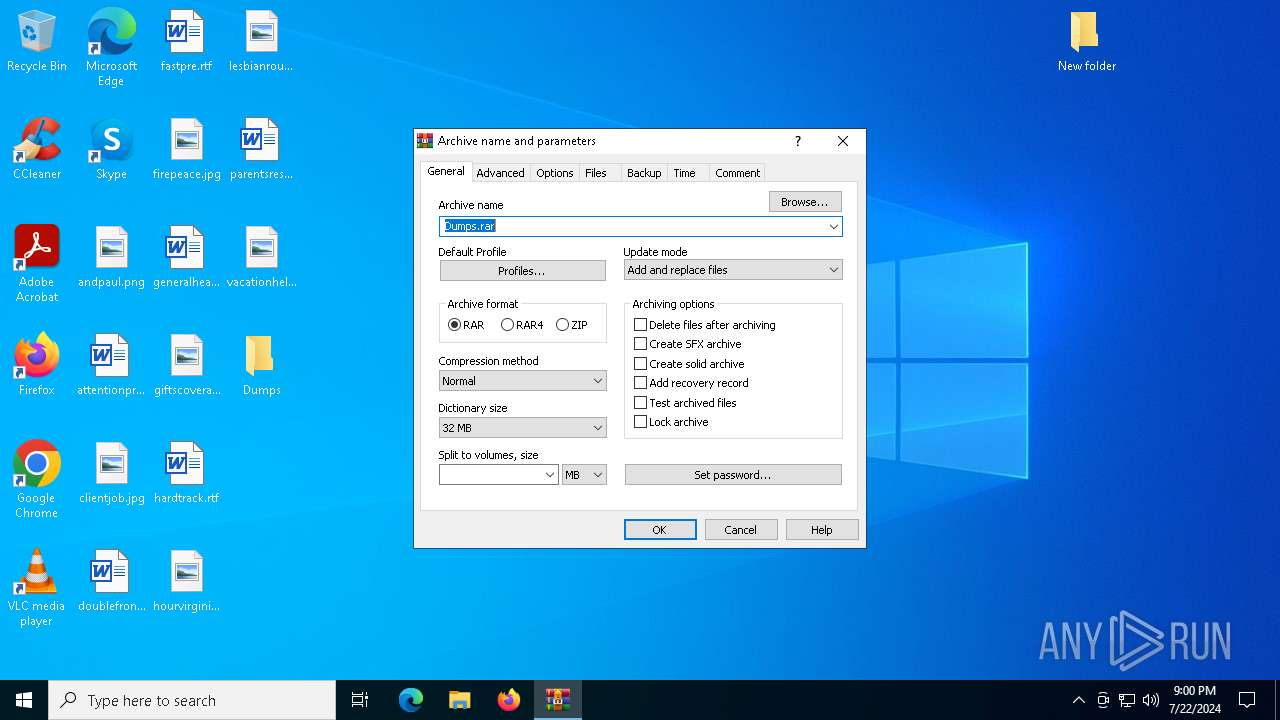
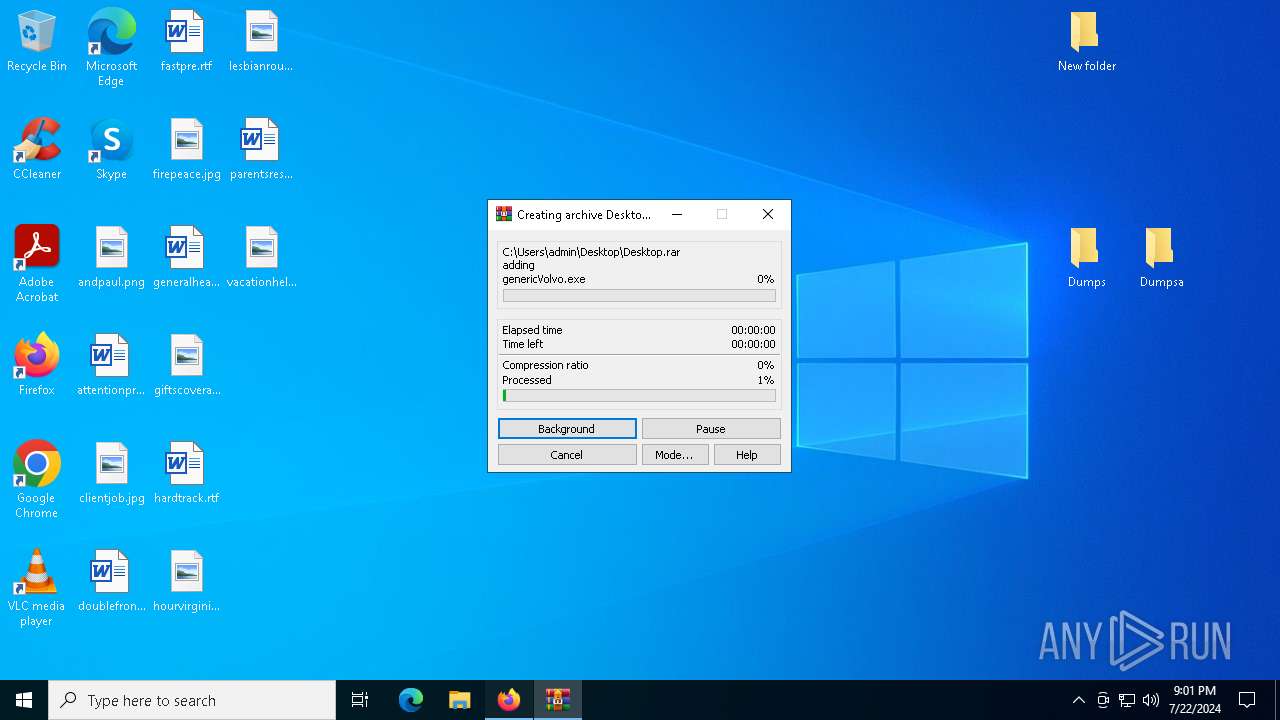
| File name: | New folder.rar |
| Full analysis: | https://app.any.run/tasks/bda36c1b-7bac-4dae-ae1d-c3b20087ebb4 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2024, 20:58:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F271F5DC715E54BF2512E879FA3213B3 |
| SHA1: | 0E69E10DE4ED16E875D819779629D51A60758EEC |
| SHA256: | 11D38AEB5398CC5AF77D4D87C35595090A70F4FE348325CD00B9CBC9B2C5B56B |
| SSDEEP: | 196608:zByaJfq+6F9yVbRohs8Ew8kU23MzVAegxa:8aRzbRoqHw8ZOMzuVxa |
MALICIOUS
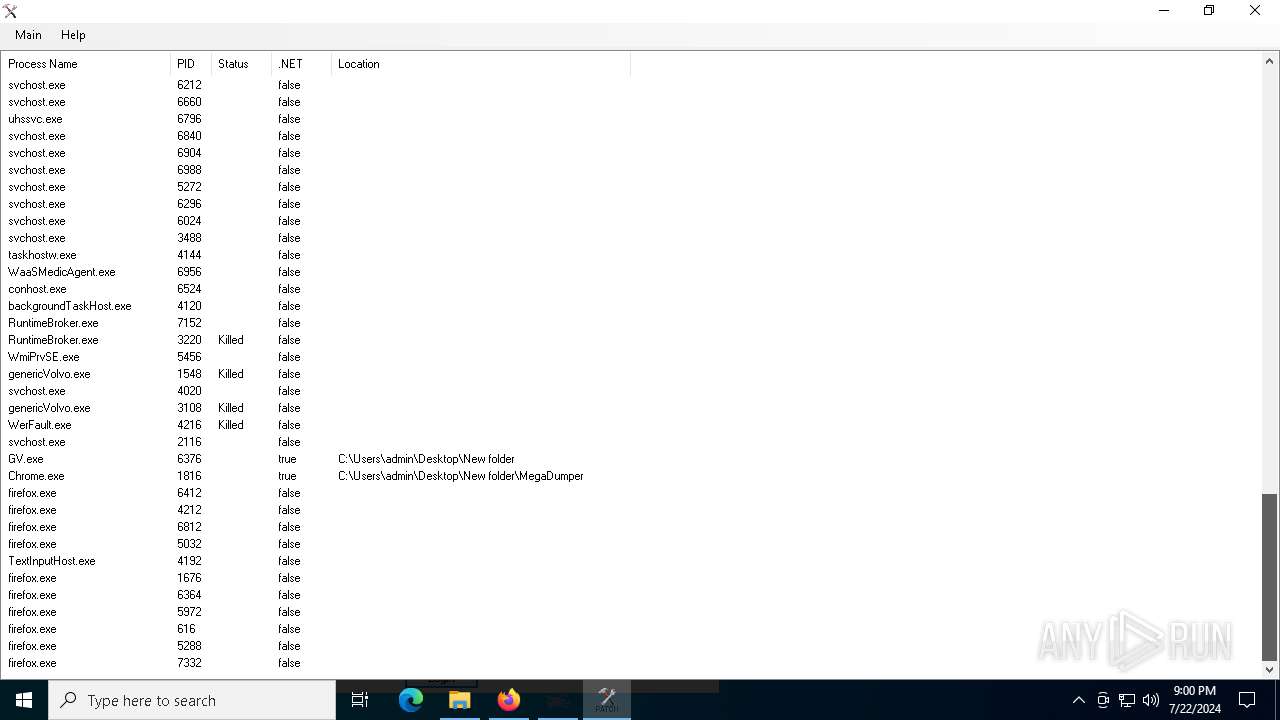
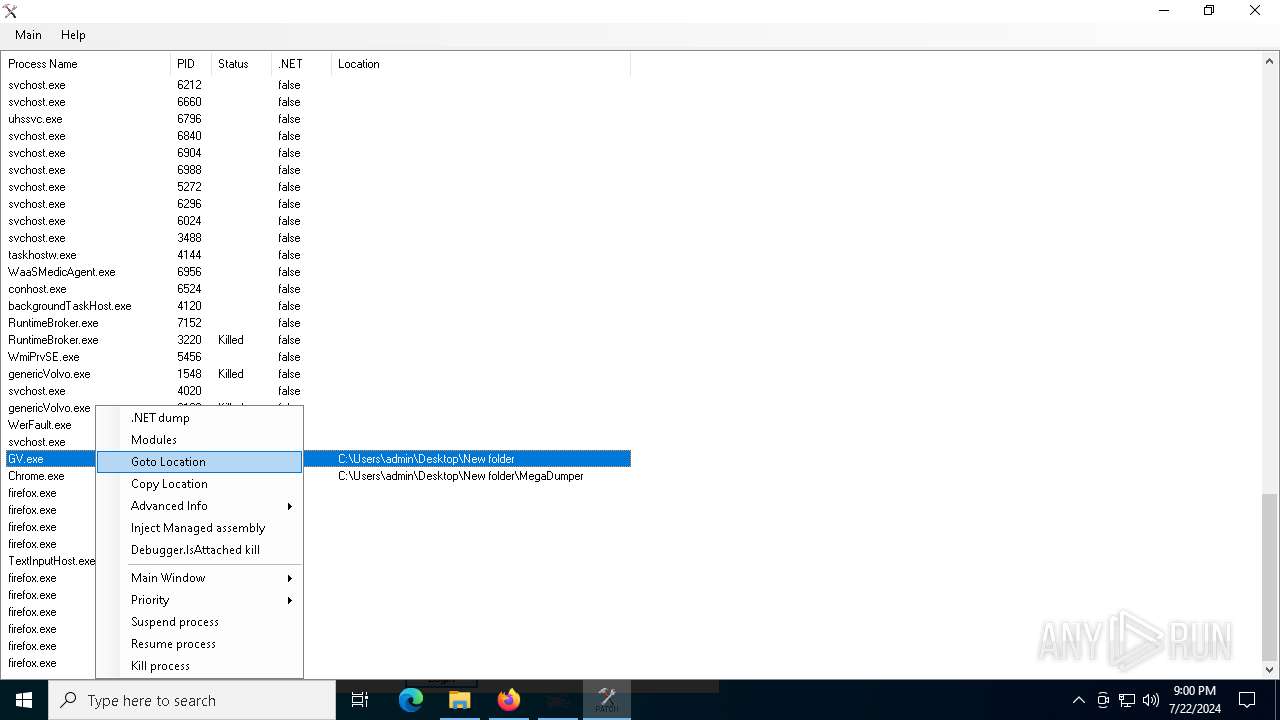
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5196)
- Boomx86.exe (PID: 1128)
- Chrome.exe (PID: 1816)
SUSPICIOUS
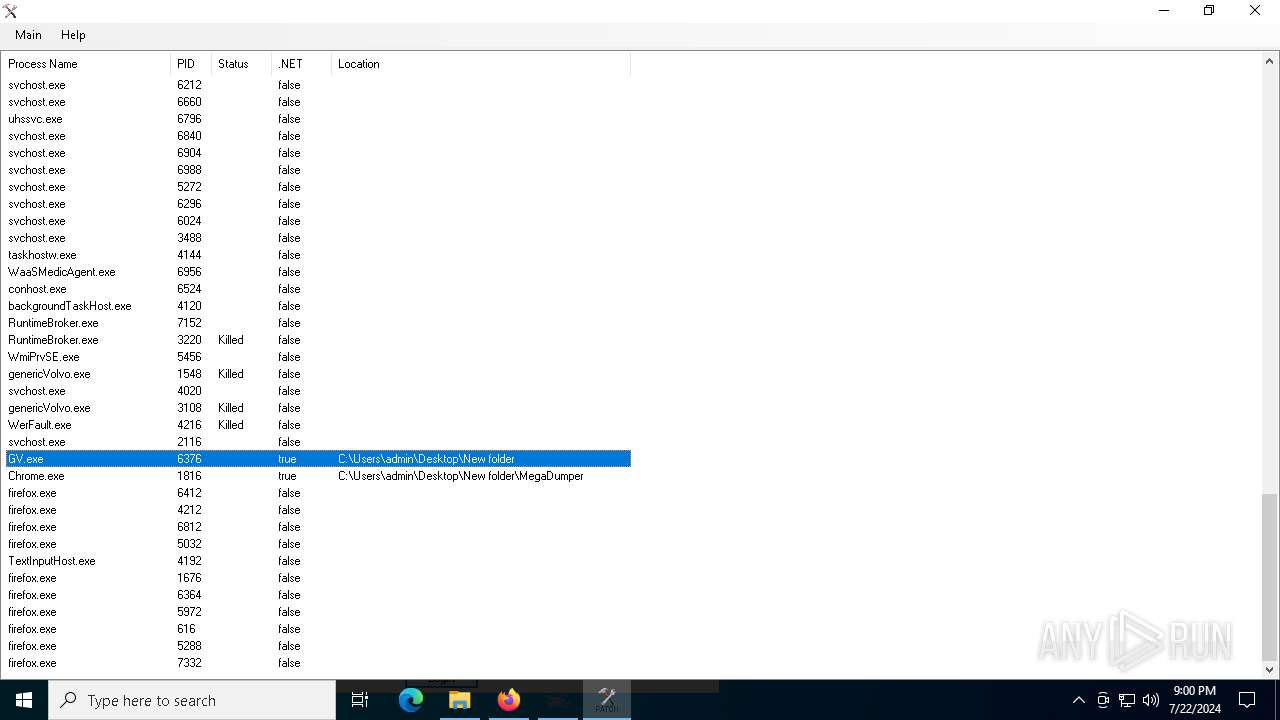
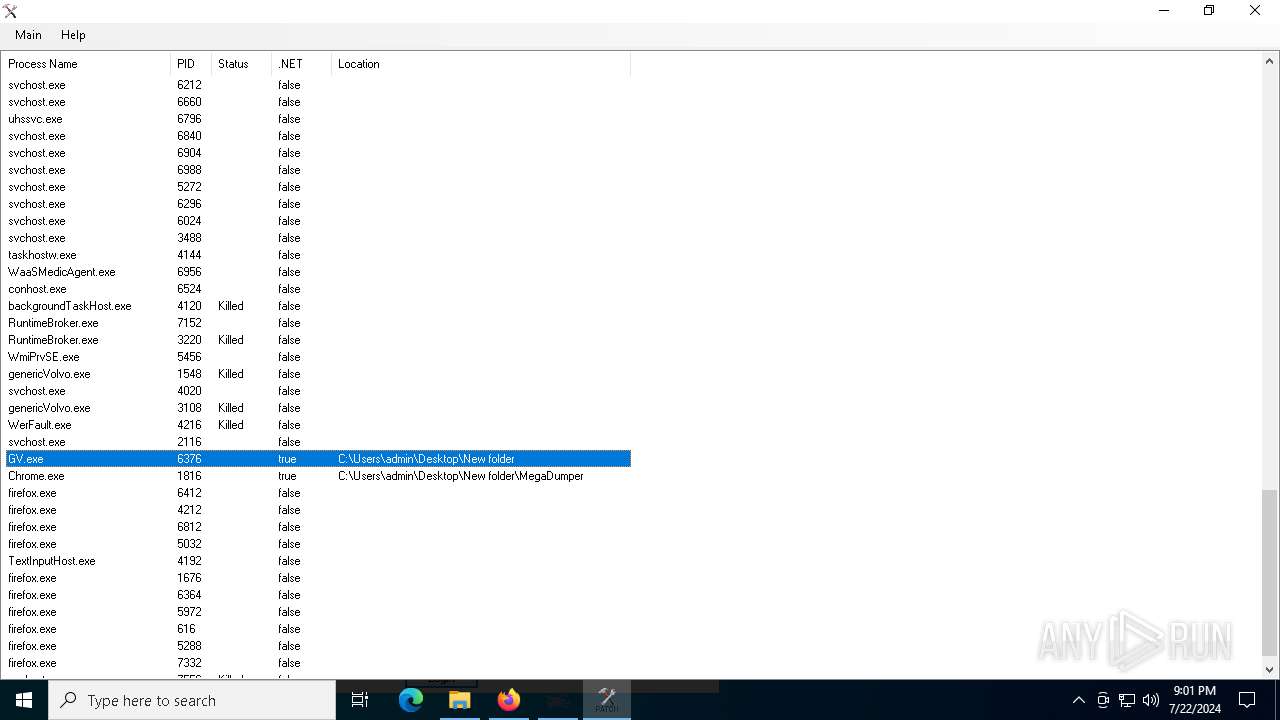
Reads the BIOS version
- GV.exe (PID: 6588)
- GV.exe (PID: 6376)
Executes application which crashes
- genericVolvo.exe (PID: 1548)
Executable content was dropped or overwritten
- Chrome.exe (PID: 1816)
- Boomx86.exe (PID: 1128)
Process drops legitimate windows executable
- Chrome.exe (PID: 1816)
Reads security settings of Internet Explorer
- Boomx86.exe (PID: 1128)
INFO
Reads the software policy settings
- slui.exe (PID: 1180)
Checks proxy server information
- slui.exe (PID: 1180)
- WerFault.exe (PID: 4216)
Manual execution by a user
- genericVolvo.exe (PID: 1548)
- JITFreezer.exe (PID: 2656)
- Boomx86.exe (PID: 1128)
- WinRAR.exe (PID: 6040)
- Chrome.exe (PID: 1816)
- firefox.exe (PID: 1264)
- GV.exe (PID: 6376)
- WinRAR.exe (PID: 7672)
Checks supported languages
- JITFreezer.exe (PID: 2656)
- GV.exe (PID: 6588)
- Boomx86.exe (PID: 1128)
- genericVolvo.exe (PID: 1548)
- Chrome.exe (PID: 1816)
- GV.exe (PID: 6376)
- TextInputHost.exe (PID: 4192)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5196)
- firefox.exe (PID: 6412)
Reads the computer name
- GV.exe (PID: 6588)
- JITFreezer.exe (PID: 2656)
- Boomx86.exe (PID: 1128)
- genericVolvo.exe (PID: 1548)
- Chrome.exe (PID: 1816)
- GV.exe (PID: 6376)
- TextInputHost.exe (PID: 4192)
Create files in a temporary directory
- Boomx86.exe (PID: 1128)
Reads the machine GUID from the registry
- genericVolvo.exe (PID: 1548)
- GV.exe (PID: 6376)
- JITFreezer.exe (PID: 2656)
- Boomx86.exe (PID: 1128)
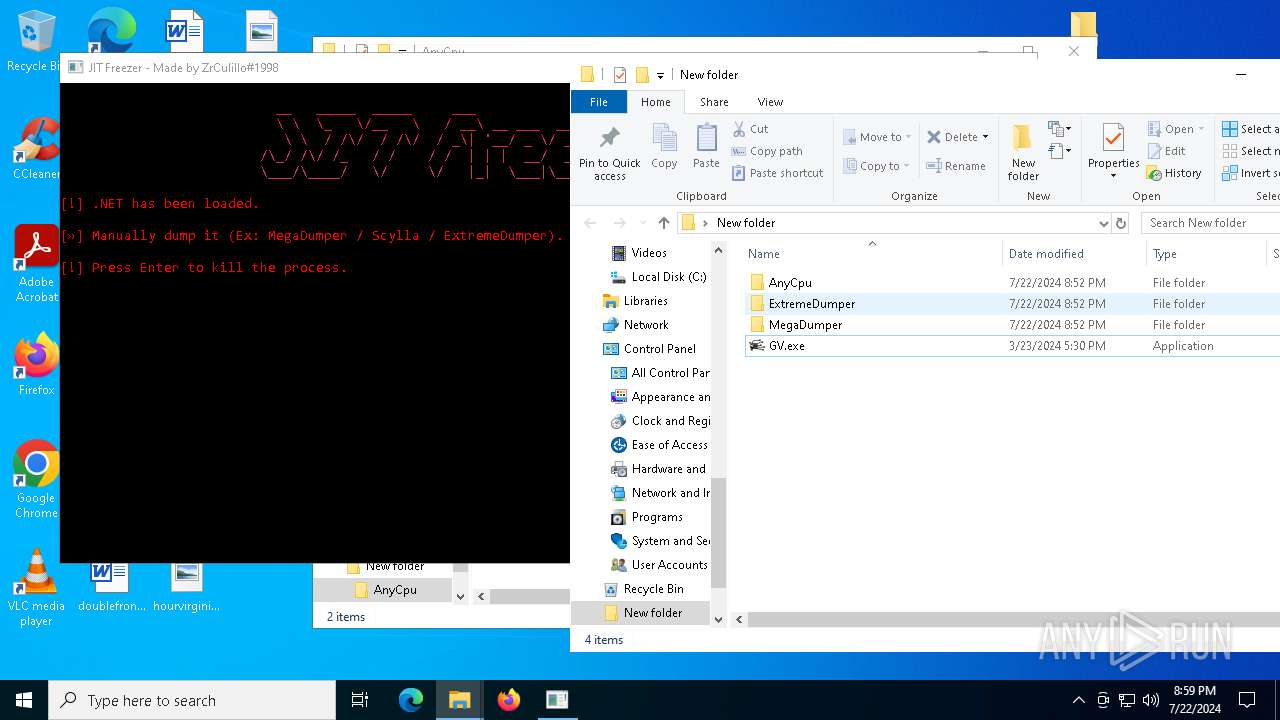
.NET Reactor protector has been detected
- genericVolvo.exe (PID: 1548)
- GV.exe (PID: 6376)
Application launched itself
- firefox.exe (PID: 1264)
- firefox.exe (PID: 6412)
Reads Microsoft Office registry keys
- firefox.exe (PID: 6412)
Creates files or folders in the user directory
- WerFault.exe (PID: 4216)
Drops the executable file immediately after the start
- firefox.exe (PID: 6412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
165
Monitored processes
27
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5824 -childID 4 -isForBrowser -prefsHandle 5868 -prefMapHandle 5864 -prefsLen 31207 -prefMapSize 244343 -jsInitHandle 1440 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {db69bcdf-4f9a-4f90-b20b-f5ea80114879} 6412 "\\.\pipe\gecko-crash-server-pipe.6412" 221091e5d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
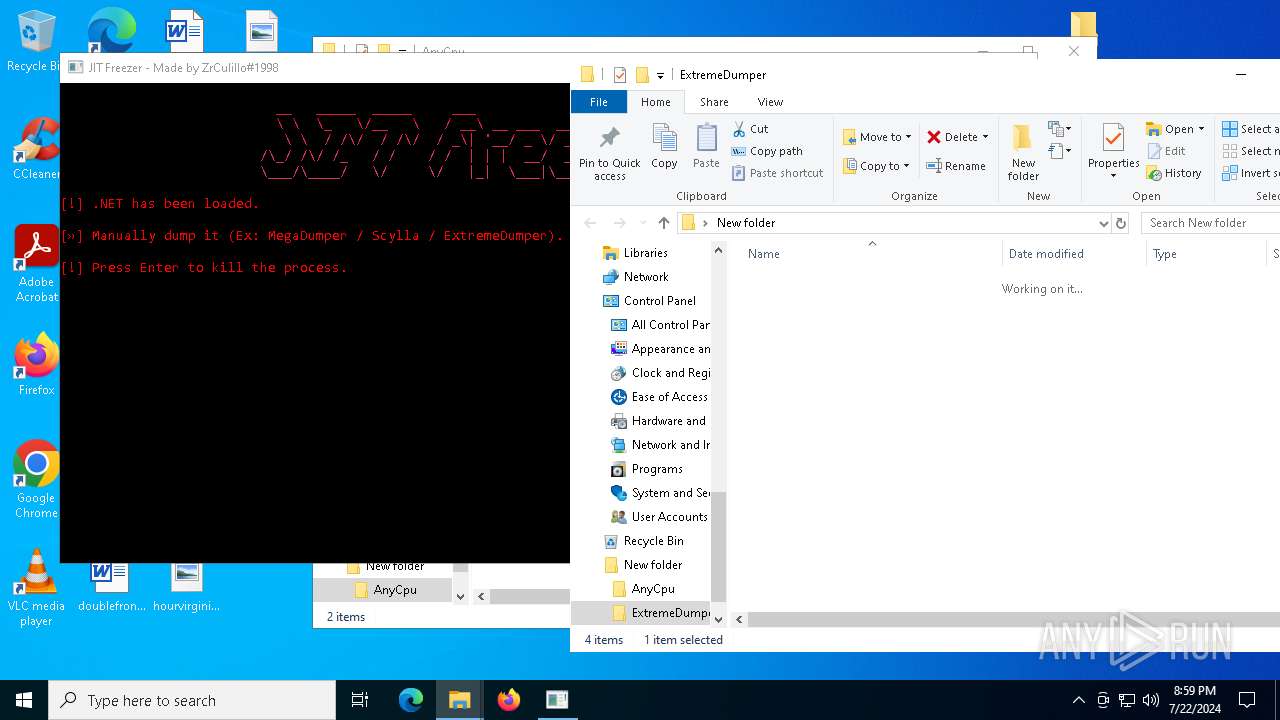
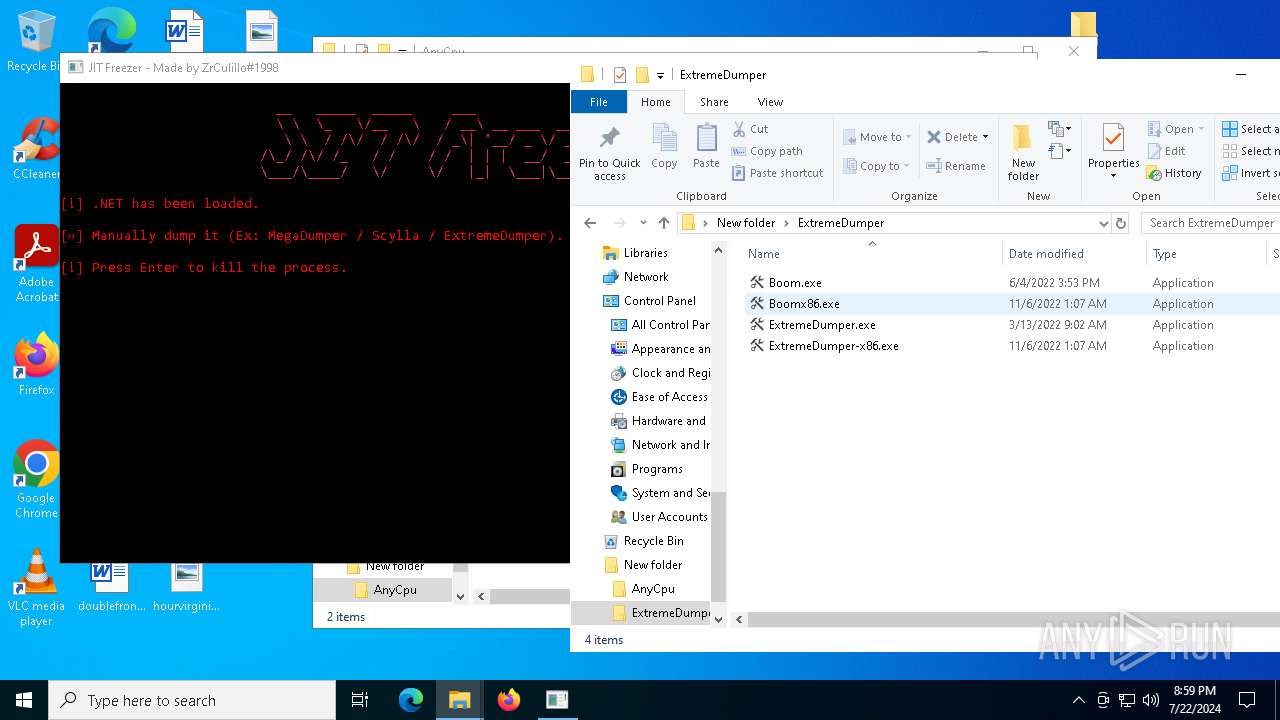
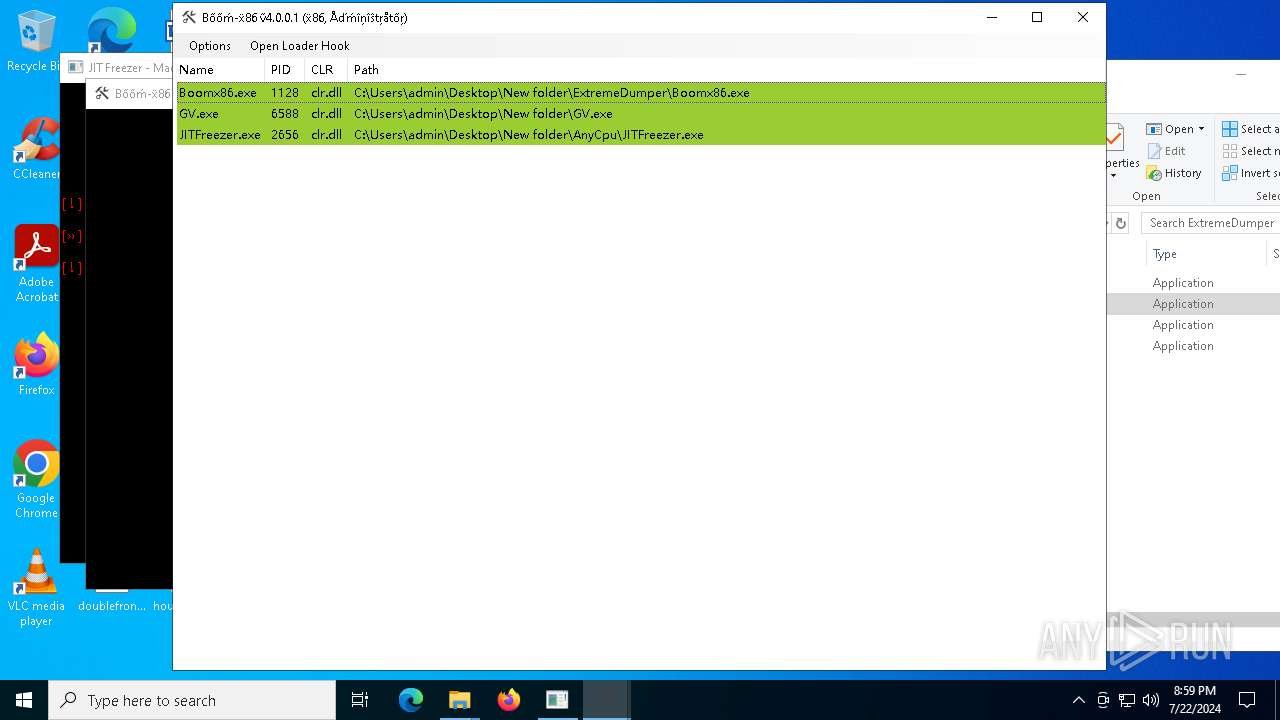
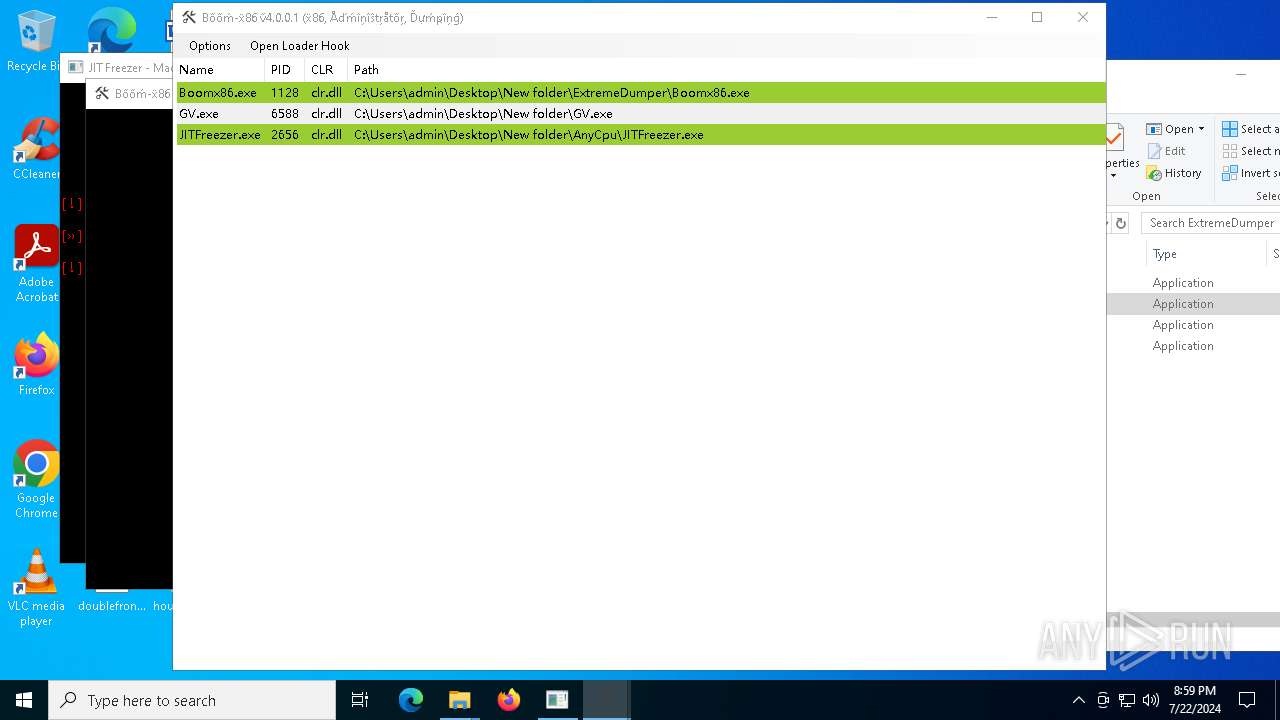
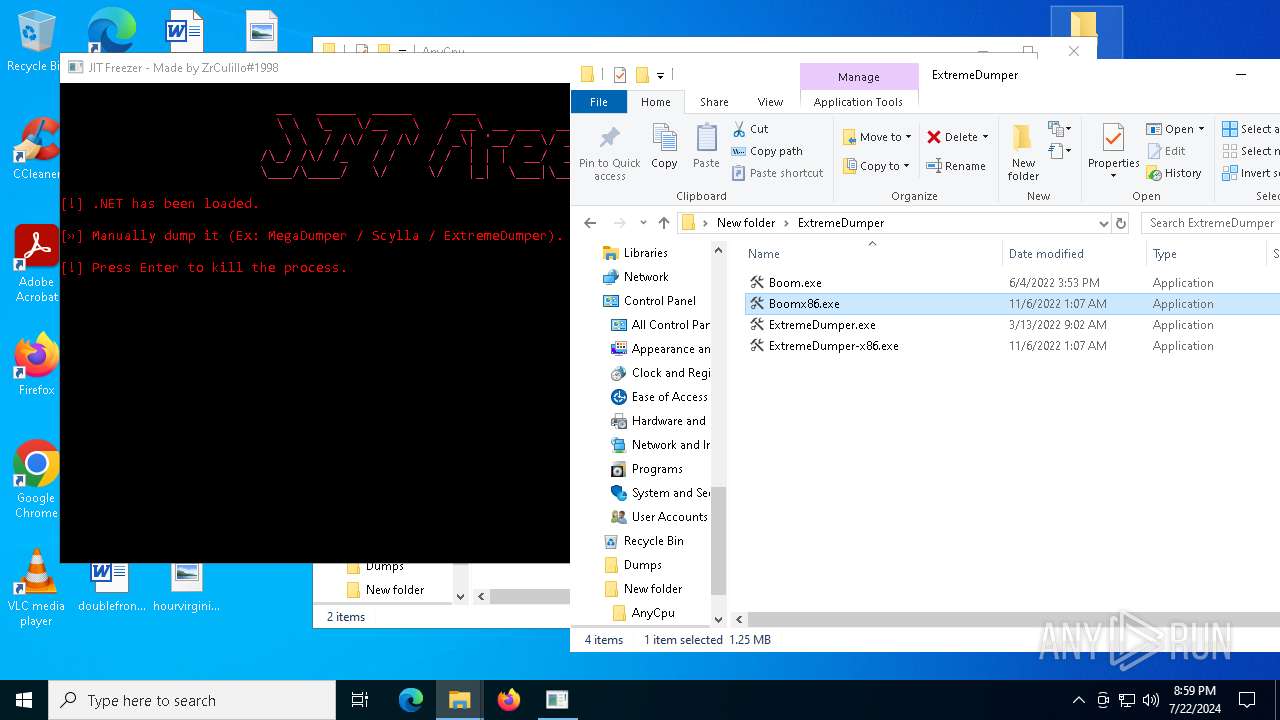
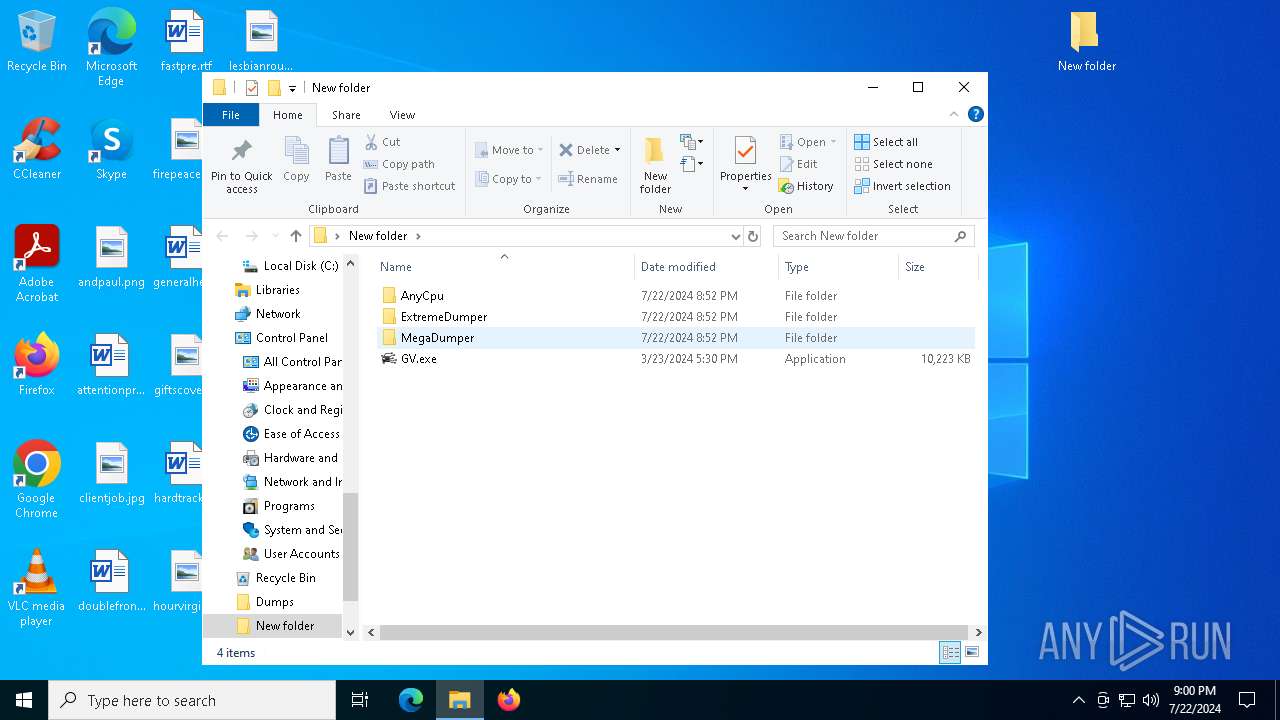
| 1128 | "C:\Users\admin\Desktop\New folder\ExtremeDumper\Boomx86.exe" | C:\Users\admin\Desktop\New folder\ExtremeDumper\Boomx86.exe | explorer.exe | ||||||||||||
User: admin Company: ExtremeDumper-x86 Integrity Level: HIGH Description: ExtremeDumper-x86 Exit code: 3221225786 Version: 4.0.0.1 Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1548 | "C:\Users\admin\Desktop\Dumps\genericVolvo.exe" | C:\Users\admin\Desktop\Dumps\genericVolvo.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: genericVolvo Exit code: 3762504530 Version: 0.2.6.0 Modules
| |||||||||||||||
| 1676 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4680 -childID 2 -isForBrowser -prefsHandle 2608 -prefMapHandle 4656 -prefsLen 36263 -prefMapSize 244343 -jsInitHandle 1440 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b2679479-220c-40db-8faa-fb09a3ed4f72} 6412 "\\.\pipe\gecko-crash-server-pipe.6412" 2210723ebd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1816 | "C:\Users\admin\Desktop\New folder\MegaDumper\Chrome.exe" | C:\Users\admin\Desktop\New folder\MegaDumper\Chrome.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: MegaDumper Exit code: 0 Version: 1.0.5565.36604 Modules
| |||||||||||||||
| 2656 | "C:\Users\admin\Desktop\New folder\AnyCpu\JITFreezer.exe" "C:\Users\admin\Desktop\New folder\GV.exe" | C:\Users\admin\Desktop\New folder\AnyCpu\JITFreezer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: JITFreezer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3484 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Boomx86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
42 276
Read events
42 040
Write events
226
Delete events
10
Modification events
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\New folder.rar | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5196) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
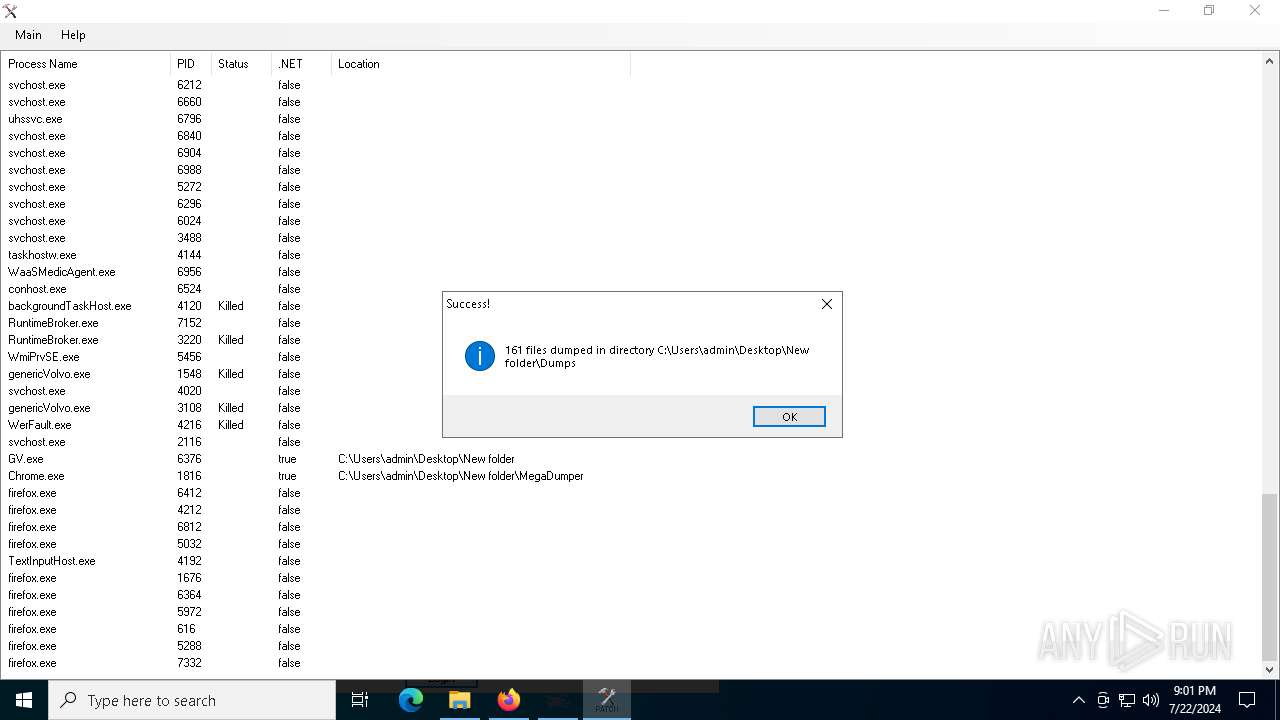
Executable files
335
Suspicious files
189
Text files
54
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5196.25419\New folder\AnyCpu\JITFreezer.exe | executable | |
MD5:BC4AE350615A090BD94A149793C93894 | SHA256:8D9078E493A9782148D6840D5A1FA20EDDE54C23A41526995C2C63CC23835F91 | |||
| 5196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5196.25419\New folder\ExtremeDumper\Boom.exe | executable | |
MD5:5B59AEC378E0A011FE24A911090E85C0 | SHA256:42774BB3D8196E410A74F896567EA65156FEB63E3228BFDF54AB5A539293DC57 | |||
| 5196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5196.25419\New folder\ExtremeDumper\ExtremeDumper.exe | executable | |
MD5:58DB100B228FF17F83726D4C2738990E | SHA256:F407B67A008FC2186329D5FEFFE830F7EEAD7A11F3B169D0D90099495EDFCF2E | |||
| 5196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5196.25419\New folder\GV.exe | executable | |
MD5:38FBF447F5F781E08F28A18B48F9A3C3 | SHA256:B07BC26CE810EB2C36E6001454C875B9B95E35AD0082E583D7DB4A4DE3DBF3FB | |||
| 5196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5196.25419\New folder\MegaDumper\Chrome.exe | executable | |
MD5:F24EB16D357C8466B0D39609290E701B | SHA256:1190F0340F7F211C0AB417FFB125AA7F8781342D1D1FFADA6A48659B6E76429B | |||
| 4216 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER17A7.tmp.xml | xml | |
MD5:1DDCBD6BB19606250E4531B79B9EB19C | SHA256:E086C1D51F905F99CE681B55E326FB65D3FC5E3CDC0D5A5206924E36D039AAB4 | |||
| 4216 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER167C.tmp.dmp | binary | |
MD5:749943107D274B1AD89B5D6A6F1DF0BF | SHA256:4DA23DA9C7E232AD69C3553268684885006EC2DD5758235826668006C370BD83 | |||
| 4216 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1777.tmp.WERInternalMetadata.xml | xml | |
MD5:1993051811184C746401F2734BE3F6F5 | SHA256:C62D469730E723A237468EC2F8CC0D6266CB90B29BCB9B145549A9AE4648C1AF | |||
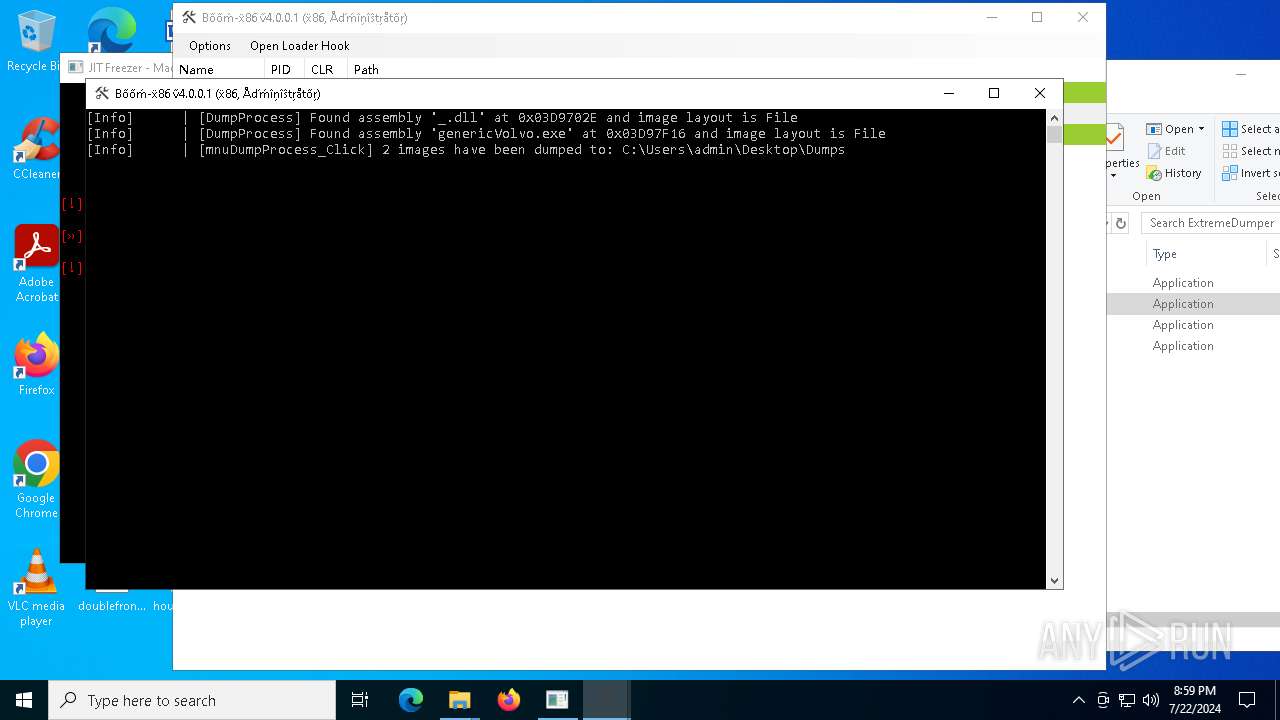
| 1128 | Boomx86.exe | C:\Users\admin\Desktop\Dumps\genericVolvo.exe | executable | |
MD5:52AFF448D8A9923C92708AC2B94CC6AD | SHA256:AEA733E8DA26042798BB4EF2257BDEDBCABB08607564D91A9DE8F28B2A42B44C | |||
| 1128 | Boomx86.exe | C:\Users\admin\Desktop\Dumps\_.dll | executable | |
MD5:27A438E3E38E4992FE8D15D4931AC437 | SHA256:9C267142C645EE688FBADC4349DF045468BEB5A430A4346F9EF4371915E642D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
119
DNS requests
162
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6412 | firefox.exe | POST | 200 | 184.24.77.67:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 184.24.77.67:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 184.24.77.67:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 184.24.77.67:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 184.24.77.67:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 184.24.77.67:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6412 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4288 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3488 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4748 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3488 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1180 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2284 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |