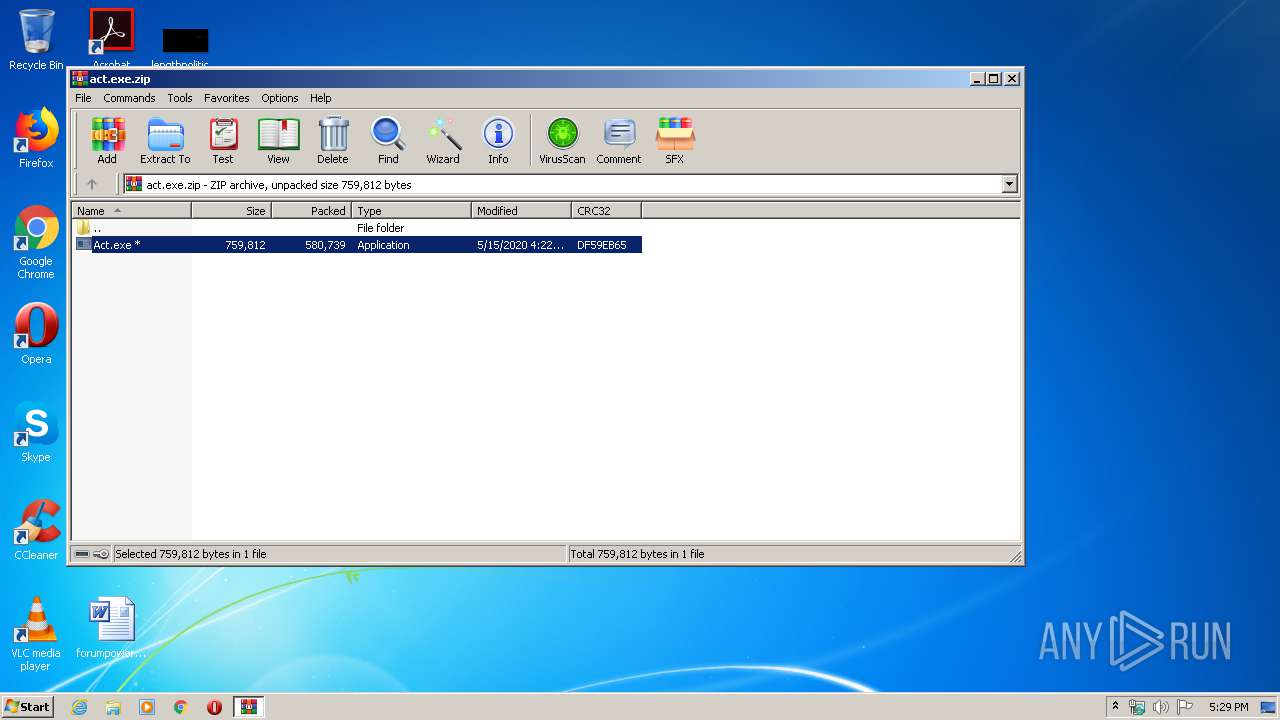
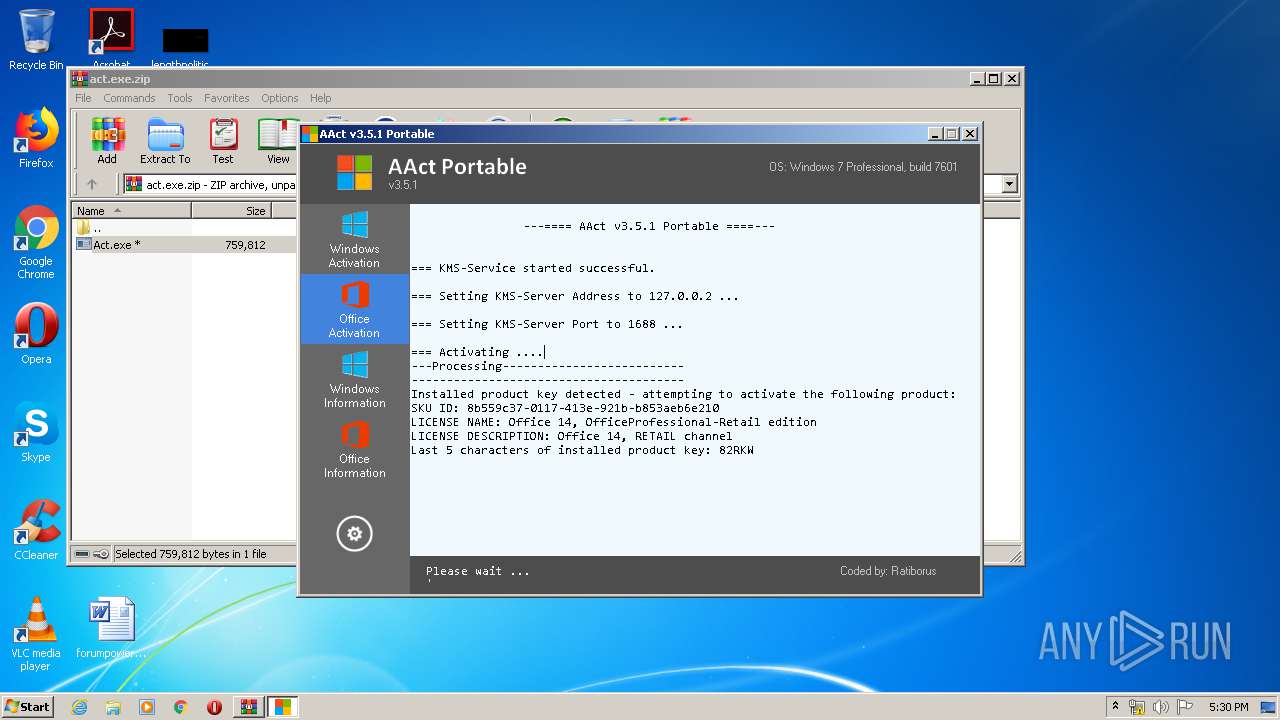
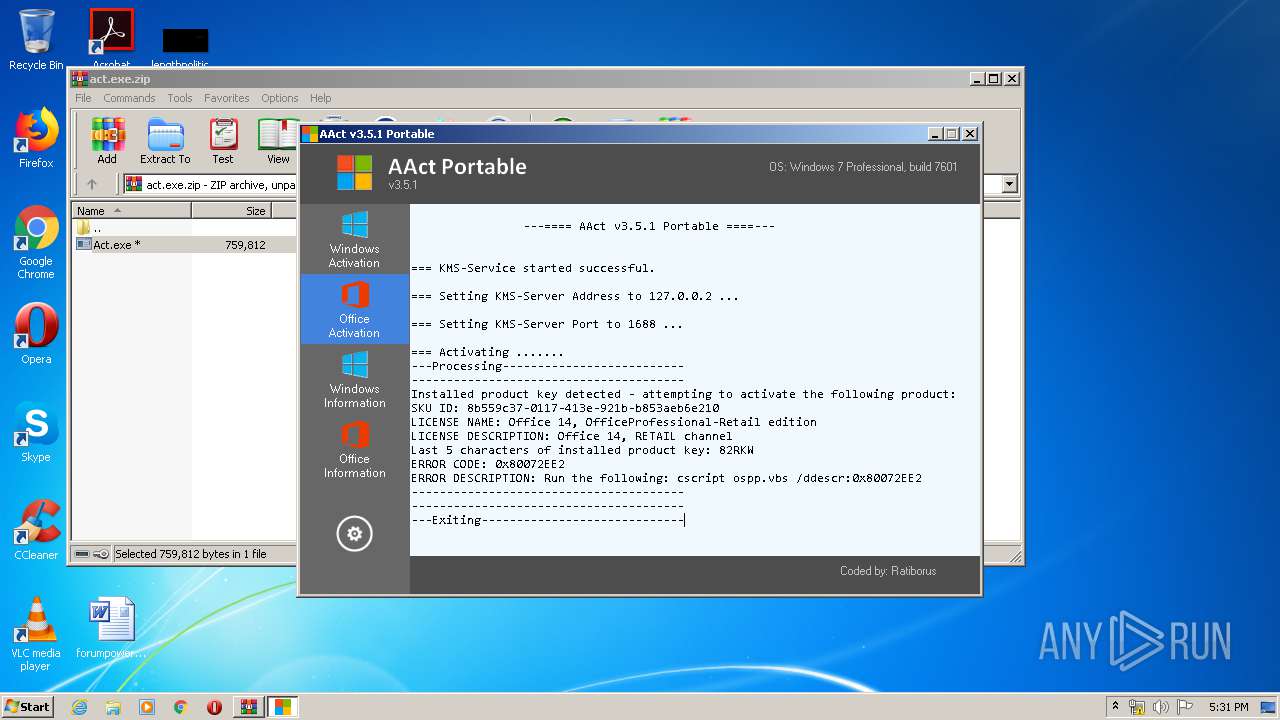
| File name: | act.exe.zip |
| Full analysis: | https://app.any.run/tasks/24a54c4f-b0b0-46d2-b4d7-bfe417427635 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2020, 16:29:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 69F900F05C797E08D8A7A80A85D2CAC4 |
| SHA1: | 457B375699659806BB4633EB888D764B2950A8DE |
| SHA256: | 117731568336B588FF6DB8756A3CB52F38B5A581AB40783B65C12F59477F6CB6 |
| SSDEEP: | 12288:Q1DKvkaxCbRrkxcUQ0lTeCpXhoXf2hUvlrKqWZTeUk1P:/v+bmaUBlTL9hsfozZTed |
MALICIOUS
Application was dropped or rewritten from another process
- Act.exe (PID: 3948)
- Act.exe (PID: 3336)
- AAct.exe (PID: 2348)
- aact.dll (PID: 1856)
Loads dropped or rewritten executable
- AAct.exe (PID: 2348)
- conhost.exe (PID: 2800)
Starts NET.EXE for service management
- cmd.exe (PID: 1780)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2404)
- Act.exe (PID: 3336)
- AAct.exe (PID: 2348)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2808)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3728)
- cmd.exe (PID: 4056)
- cmd.exe (PID: 3996)
- cmd.exe (PID: 1920)
- cmd.exe (PID: 4036)
- cmd.exe (PID: 2720)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 1412)
Starts application with an unusual extension
- AAct.exe (PID: 2348)
Starts CMD.EXE for commands execution
- AAct.exe (PID: 2348)
Uses REG.EXE to modify Windows registry
- AAct.exe (PID: 2348)
Executes scripts
- cmd.exe (PID: 2708)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 3584)
- cmd.exe (PID: 2992)
- cmd.exe (PID: 2120)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 3020)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:05:15 16:22:12 |
| ZipCRC: | 0xdf59eb65 |
| ZipCompressedSize: | 580739 |
| ZipUncompressedSize: | 759812 |
| ZipFileName: | Act.exe |
Total processes
108
Monitored processes
43
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | Netsh.exe Advfirewall Firewall delete rule name=AAct_OUT_Port_KMS protocol=TCP | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 256 | Netsh.exe Advfirewall Firewall delete rule name=AAct_IN_Port_KMS protocol=TCP | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | cscript.exe "C:\Program Files\Microsoft Office\Office14\OSPP.VBS" //NoLogo /remhst | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1332 | Netsh.exe Advfirewall Firewall delete rule name=AAct_IN_Port_KMS protocol=TCP | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1412 | "C:\Windows\System32\cmd.exe" /c Netsh.exe Advfirewall Firewall delete rule name=AAct_IN_Port_KMS protocol=TCP | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1444 | Netsh.exe Advfirewall Firewall delete rule name=AAct_OUT_Port_KMS protocol=TCP | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1500 | "C:\Windows\System32\reg.exe" DELETE "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f" /f | C:\Windows\System32\reg.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1548 | net.exe start osppsvc | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1780 | "C:\Windows\System32\cmd.exe" /c net.exe start osppsvc | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
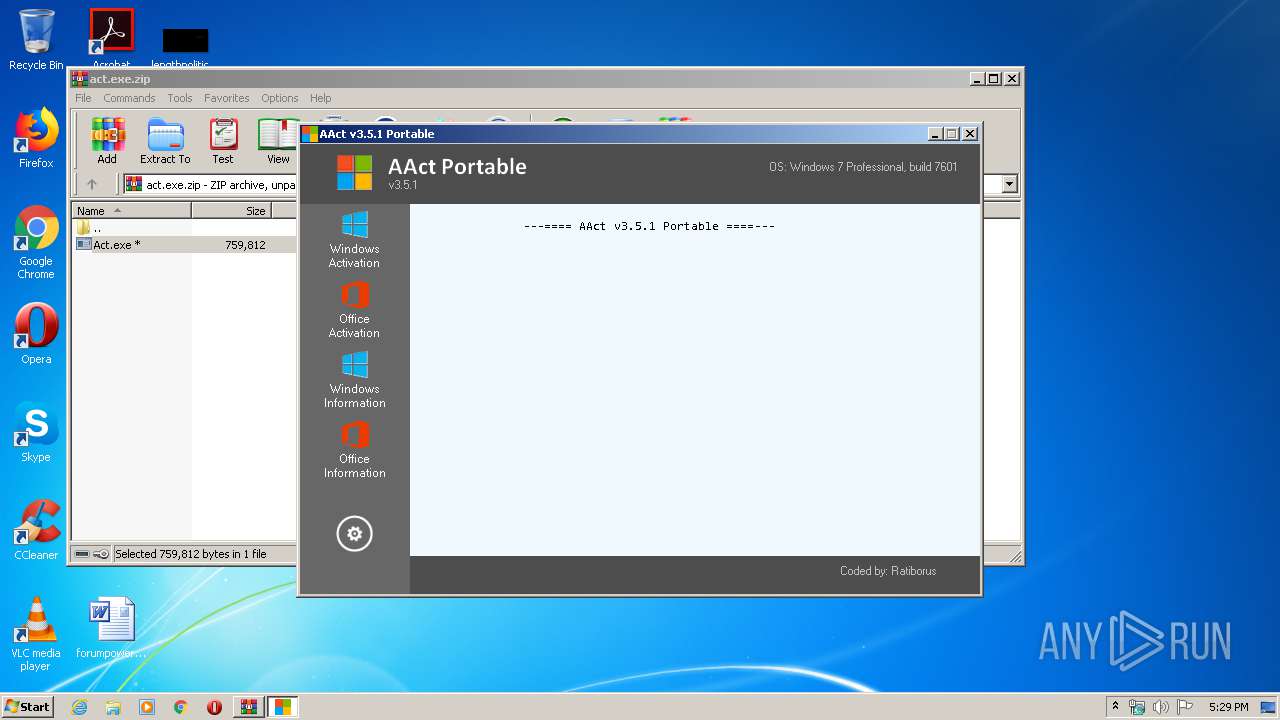
| 1856 | "C:\Users\admin\AppData\Local\Temp\aact.dll" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -PO16 RandomKMSPID | C:\Users\admin\AppData\Local\Temp\aact.dll | — | AAct.exe | |||||||||||
User: admin Company: MSFree Inc. Integrity Level: HIGH Description: KMS emulator by Ratiborus, thanks to Hotbird64. Exit code: 1 Version: 2.0.3.0 Modules
| |||||||||||||||
Total events
1 430
Read events
1 052
Write events
378
Delete events
0
Modification events
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\act.exe.zip | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2404) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3336 | Act.exe | C:\Users\admin\AppData\Local\Temp\AAct.exe | executable | |
MD5:— | SHA256:— | |||
| 2404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2404.1506\Act.exe | executable | |
MD5:— | SHA256:— | |||
| 2348 | AAct.exe | C:\Users\admin\AppData\Local\Temp\AAct.dll | executable | |
MD5:ADD80E5D9FAD482705C3807BACFE1993 | SHA256:BB3830B14DF80838FB201C611ABF0C1F3714C6B8B103ED084EAFC170036631BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3072 | wmiprvse.exe | 172.227.168.22:80 | go.microsoft.com | Akamai International B.V. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |