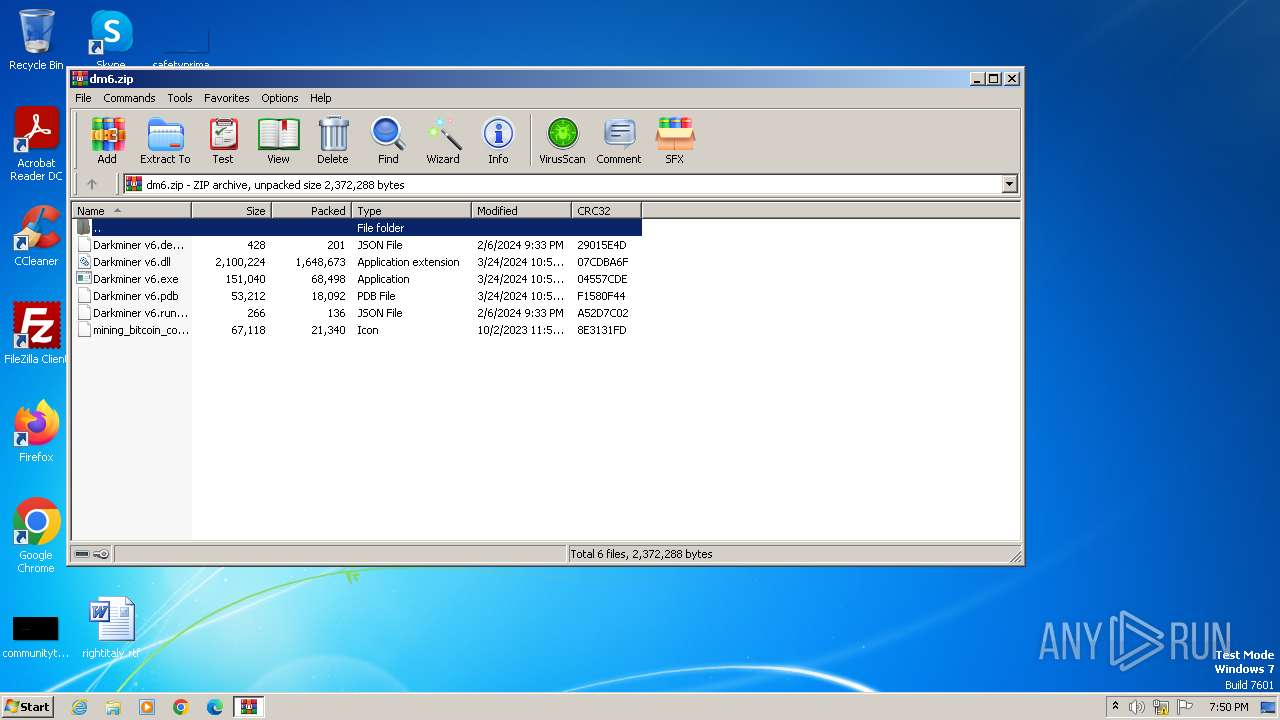
| File name: | dm6.zip |
| Full analysis: | https://app.any.run/tasks/8ceb6e7a-4ded-4a22-8c7e-51ed8af5db29 |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2024, 18:50:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
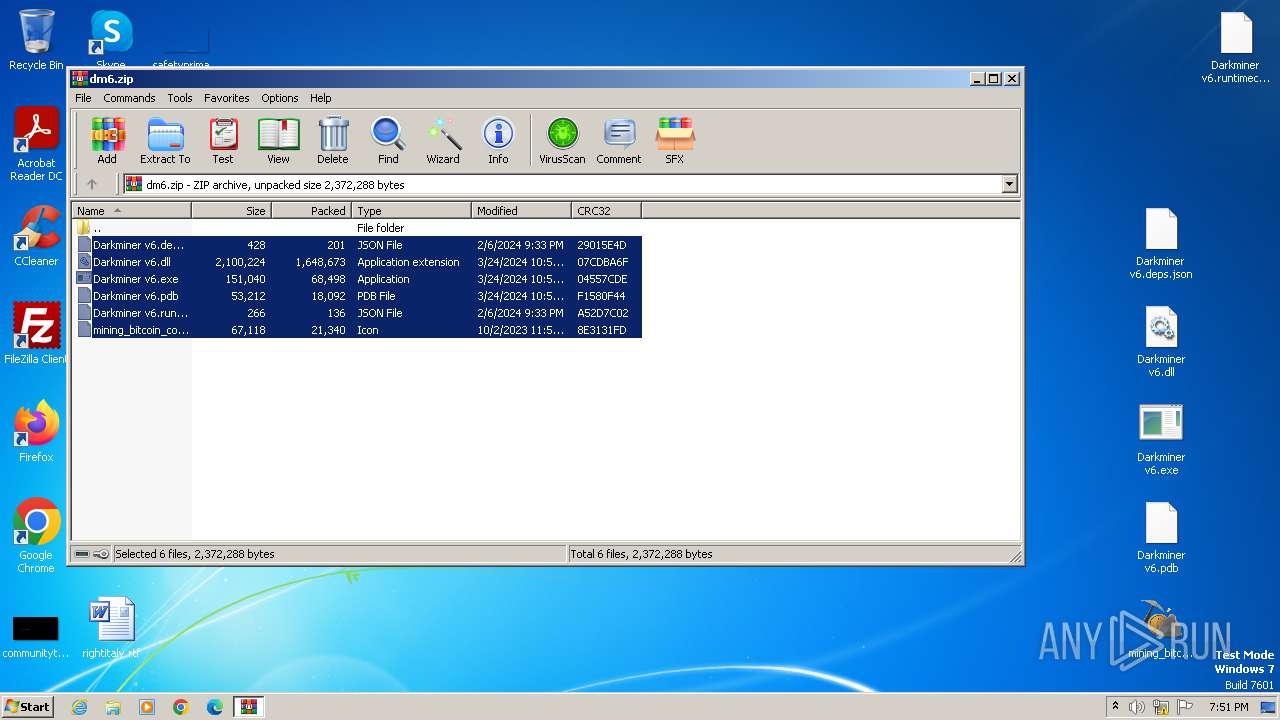
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BE994D80121000C3172A0E1F7993FFBC |
| SHA1: | 06DA727C80EE42806E862CFCDBEF61C8E7CD0373 |
| SHA256: | 11745F3FF8735C37E3E5C5F4F6215A809E5DCE353A26A431FF602EFD4EA55D75 |
| SSDEEP: | 98304:ixHnqU0D12Yi4lrBDbpWw9+TfrXrrhKBwHAjvYnme/CHuR+VkxMtz70c9qfXEoxy:Ay19 |
MALICIOUS
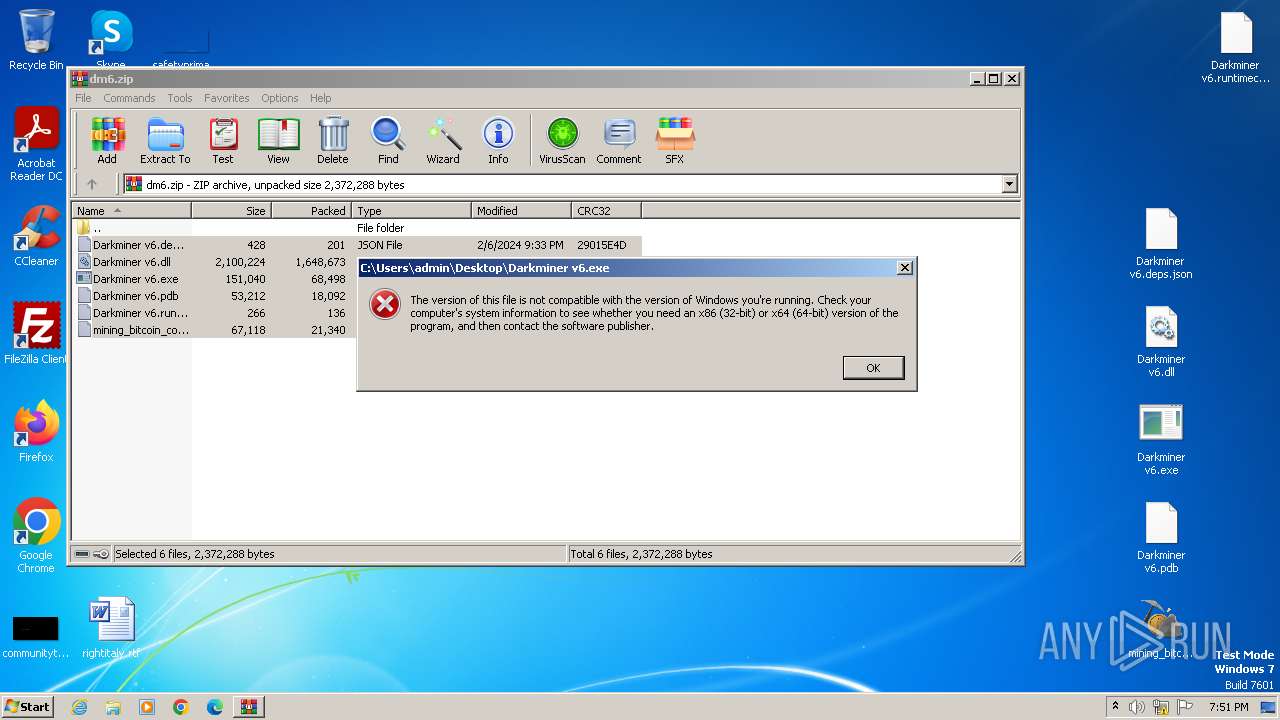
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3980)
- csc.exe (PID: 328)
- csc.exe (PID: 1292)
- csc.exe (PID: 1768)
Starts Visual C# compiler
- sdiagnhost.exe (PID: 752)
SUSPICIOUS
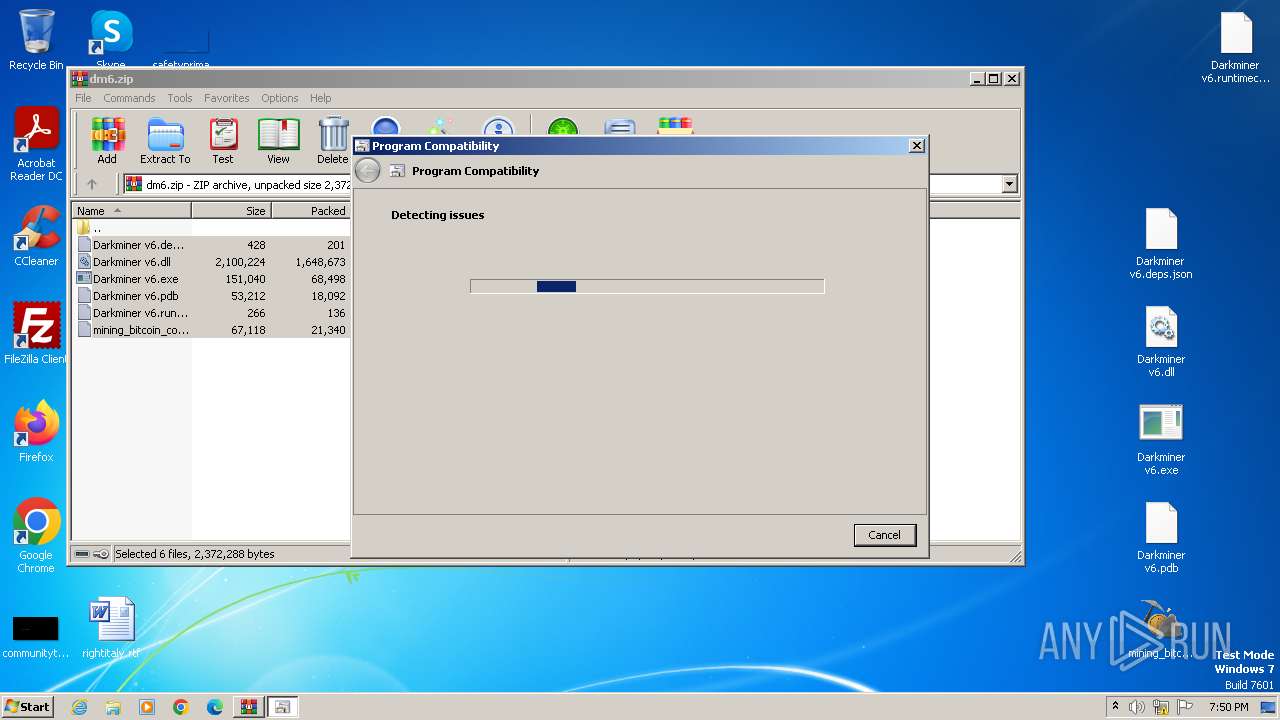
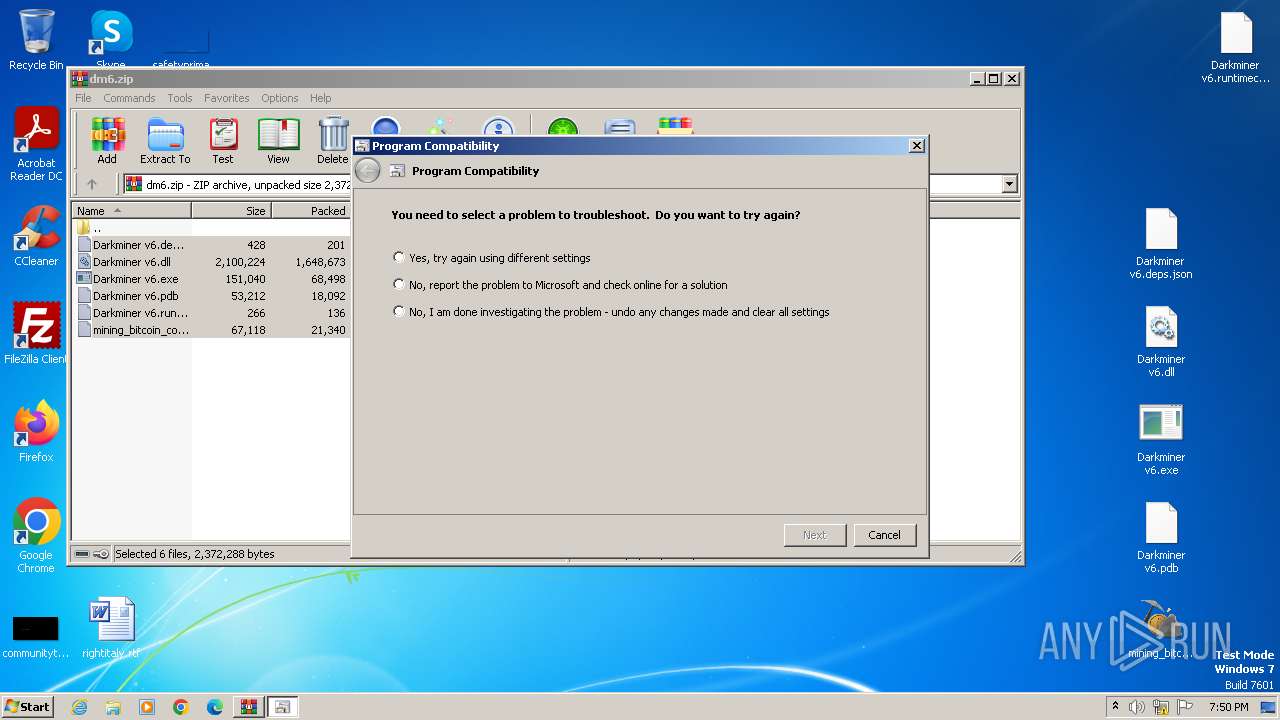
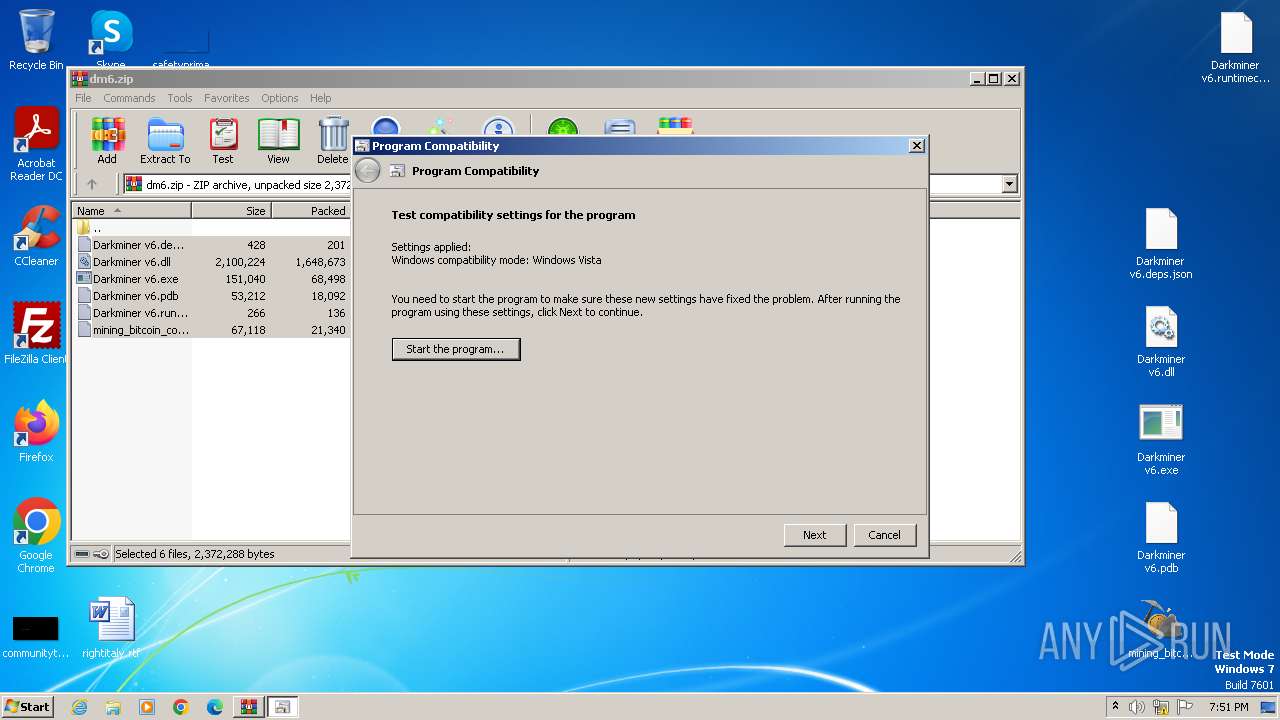
Probably uses Microsoft diagnostics tool to execute malicious payload
- pcwrun.exe (PID: 4088)
Reads the Internet Settings
- sdiagnhost.exe (PID: 752)
- msdt.exe (PID: 2072)
Uses .NET C# to load dll
- sdiagnhost.exe (PID: 752)
Executable content was dropped or overwritten
- csc.exe (PID: 1292)
- csc.exe (PID: 1768)
- csc.exe (PID: 328)
Uses RUNDLL32.EXE to load library
- msdt.exe (PID: 2072)
INFO
Create files in a temporary directory
- pcwrun.exe (PID: 4088)
- msdt.exe (PID: 2072)
- sdiagnhost.exe (PID: 752)
- csc.exe (PID: 328)
- cvtres.exe (PID: 336)
- cvtres.exe (PID: 2136)
- csc.exe (PID: 1292)
- csc.exe (PID: 1768)
- cvtres.exe (PID: 1756)
Manual execution by a user
- pcwrun.exe (PID: 4088)
Reads the software policy settings
- msdt.exe (PID: 2072)
Reads security settings of Internet Explorer
- msdt.exe (PID: 2072)
- sdiagnhost.exe (PID: 752)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3980)
Drops the executable file immediately after the start
- msdt.exe (PID: 2072)
Checks supported languages
- csc.exe (PID: 328)
- cvtres.exe (PID: 336)
- csc.exe (PID: 1292)
- cvtres.exe (PID: 2136)
- csc.exe (PID: 1768)
- cvtres.exe (PID: 1756)
Reads the machine GUID from the registry
- csc.exe (PID: 328)
- cvtres.exe (PID: 336)
- csc.exe (PID: 1292)
- csc.exe (PID: 1768)
- cvtres.exe (PID: 1756)
- cvtres.exe (PID: 2136)
Creates files or folders in the user directory
- msdt.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:06 21:33:56 |
| ZipCRC: | 0x29015e4d |
| ZipCompressedSize: | 201 |
| ZipUncompressedSize: | 428 |
| ZipFileName: | Darkminer v6.deps.json |
Total processes
44
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\smagqgmz.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 336 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES81B6.tmp" "c:\Users\admin\AppData\Local\Temp\CSC81A5.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 552 | "C:\Windows\System32\rundll32.exe" C:\Windows\system32\pcwutl.dll,CreateAndRunTask -path "C:\Users\admin\Desktop\Darkminer v6.exe" | C:\Windows\System32\rundll32.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1292 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\7fja35zo.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 1756 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES832D.tmp" "c:\Users\admin\AppData\Local\Temp\CSC832C.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 1768 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\mgijwuuk.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2072 | C:\Windows\System32\msdt.exe -path C:\Windows\diagnostics\index\PCWDiagnostic.xml -af C:\Users\admin\AppData\Local\Temp\PCW7706.xml /skip TRUE | C:\Windows\System32\msdt.exe | — | pcwrun.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2136 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8262.tmp" "c:\Users\admin\AppData\Local\Temp\CSC8251.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3980 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\dm6.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 398
Read events
10 355
Write events
42
Delete events
1
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\dm6.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
7
Suspicious files
17
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3980.15487\Darkminer v6.dll | executable | |
MD5:3798335E035A025141B731B340C6B652 | SHA256:C39A60864E0BDB45E81C1B00F234072E965F74871D9D3A7A5ECDD8D1E5CB605B | |||
| 2072 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_b6dcbfee-faa0-4a7c-abab-523de157588b\DiagPackage.diagpkg | html | |
MD5:18A906A43C1C3E27064DB30C81505234 | SHA256:041430D1F0AE14300C46BDCD917C882F4850DA3D6010E3FBF692023655BC406E | |||
| 2072 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_b6dcbfee-faa0-4a7c-abab-523de157588b\TS_ProgramCompatibilityWizard.ps1 | text | |
MD5:46E22C2582B54BE56D80D7A79FEC9BB5 | SHA256:459AF2960B08E848573D45A7350223657ADB2115F24A3C37E69FFE61DEA647F9 | |||
| 2072 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_b6dcbfee-faa0-4a7c-abab-523de157588b\VF_ProgramCompatibilityWizard.ps1 | text | |
MD5:C219205ABF50BB950B93D0824D483780 | SHA256:5284D805B918F161565150EC64B787E4EA681DE69B1AD832F316F94DB6DBCB75 | |||
| 2072 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_b6dcbfee-faa0-4a7c-abab-523de157588b\DiagPackage.dll | executable | |
MD5:4B9F845D6FF4BCED0EA8D7B0EA4AE7E7 | SHA256:21369005C8400B68D8CAB1A9A6C4D5809F5A685A8E18D311272467BB25D3D3C8 | |||
| 328 | csc.exe | C:\Users\admin\AppData\Local\Temp\smagqgmz.pdb | binary | |
MD5:0744CFA4F045BD9F5945460555DC7082 | SHA256:31E4AF212BD18EB150B4FB447C72A50764FDCA03BD1C0ED669C300D3F4F87E75 | |||
| 4088 | pcwrun.exe | C:\Users\admin\AppData\Local\Temp\PCW7706.xml | xml | |
MD5:80681B26E76818EC8BB3F99F3C1B1D97 | SHA256:B32857E34DD8099890EC37E3D642C8738D942DEBA5FB85C0EDCB09FADCB7F0C2 | |||
| 2072 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_b6dcbfee-faa0-4a7c-abab-523de157588b\en-US\DiagPackage.dll.mui | executable | |
MD5:C31BD28AB34E75BC65A5458AC8D37539 | SHA256:5FB9E280013D58043C5689478F9DCFAD3212F4681534627EB33998DDD6F63308 | |||
| 2072 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_b6dcbfee-faa0-4a7c-abab-523de157588b\en-US\CL_LocalizationData.psd1 | text | |
MD5:863DC7FD9D5E14BB639EAAF596D64416 | SHA256:97EB6F256A278FF10B200FA6E248B7A89BA956D9F533D138302C7F3721A95D8E | |||
| 336 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES81B6.tmp | binary | |
MD5:EE93DBFA6D00A7358DFCC35ACFF5C221 | SHA256:5CFFB2BD2F23DF82774D9A31C908E5D65F6B43C00F46867FA203A6E66F78D74B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|