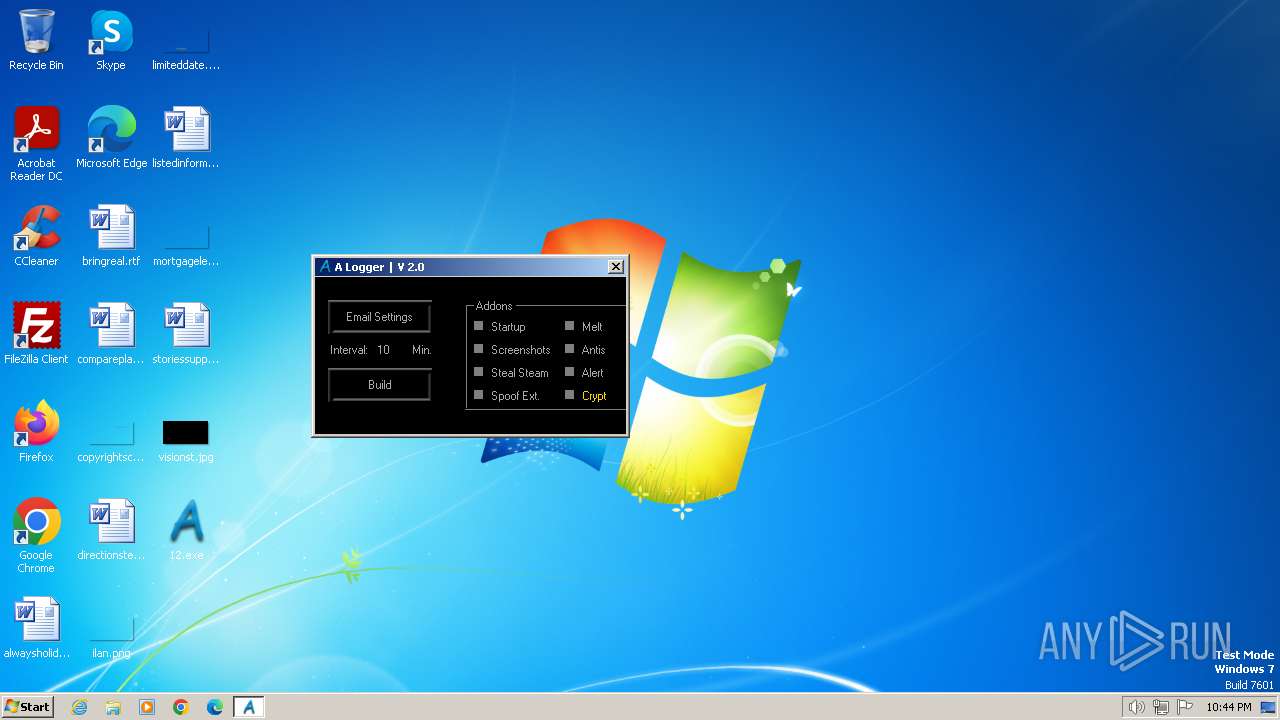
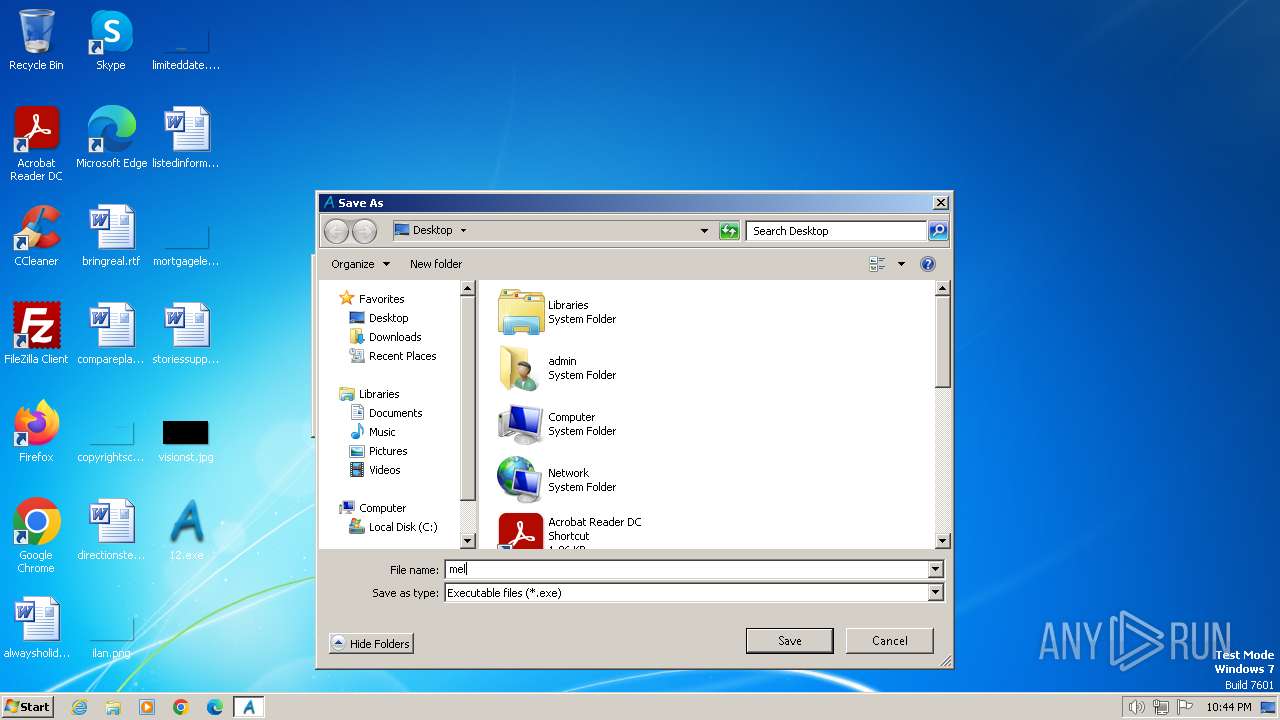
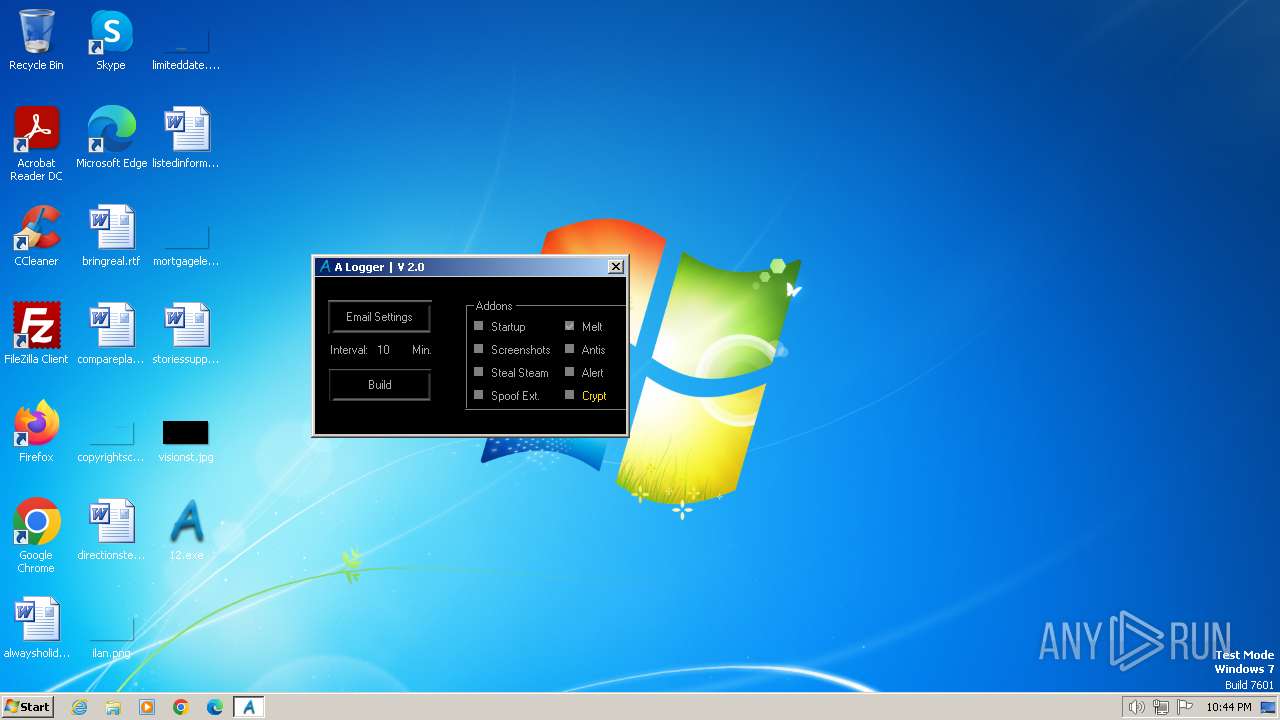
| File name: | 12.exe |
| Full analysis: | https://app.any.run/tasks/bbd39655-98a2-4da4-affd-dfd375672c2f |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2024, 21:44:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 192830B3974FA27116C067F019747B38 |
| SHA1: | 469FD8A31D9F82438AB37413DAE81EB25D275804 |
| SHA256: | 116E5F36546B2EC14ABA42FF69F2C9E18ECDE3B64ABB44797AC9EFC6C6472BFF |
| SSDEEP: | 3072:DNWEVgmcebG4mZw4I4mZmET3N60YkEFP2TW4mZ5:DLgm9bGjZw4IjZmETXqjZ5 |
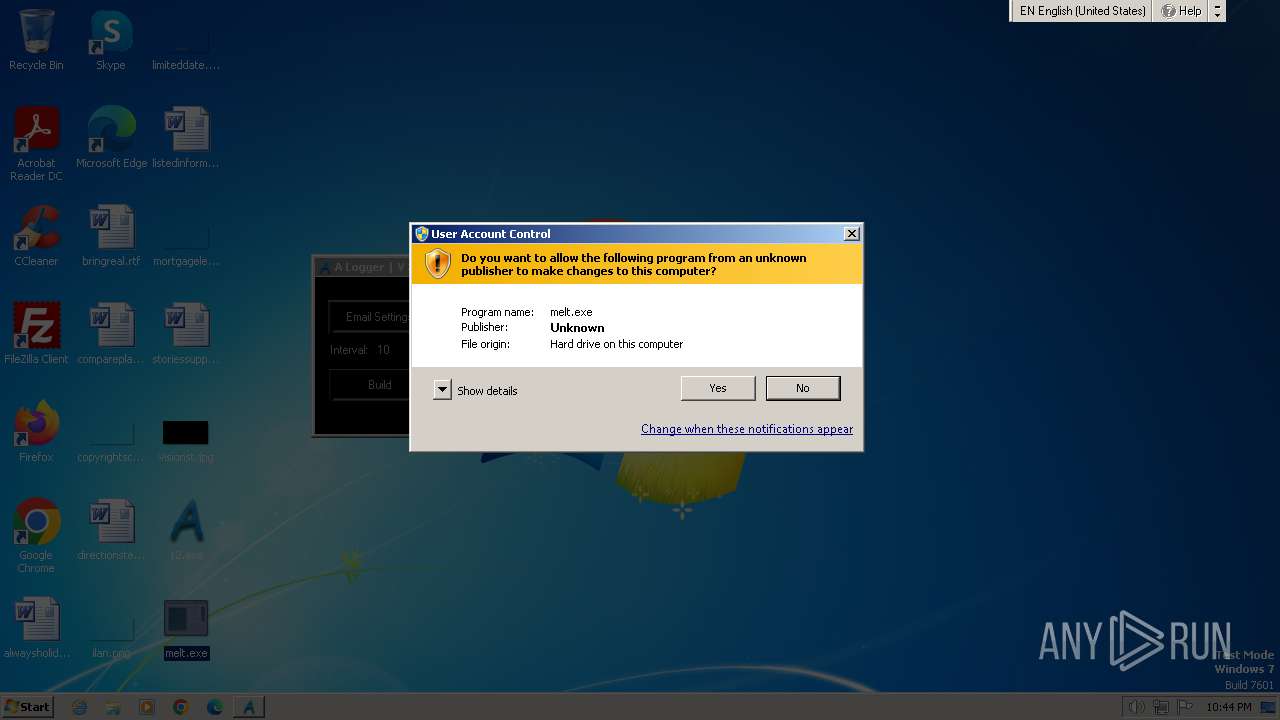
MALICIOUS
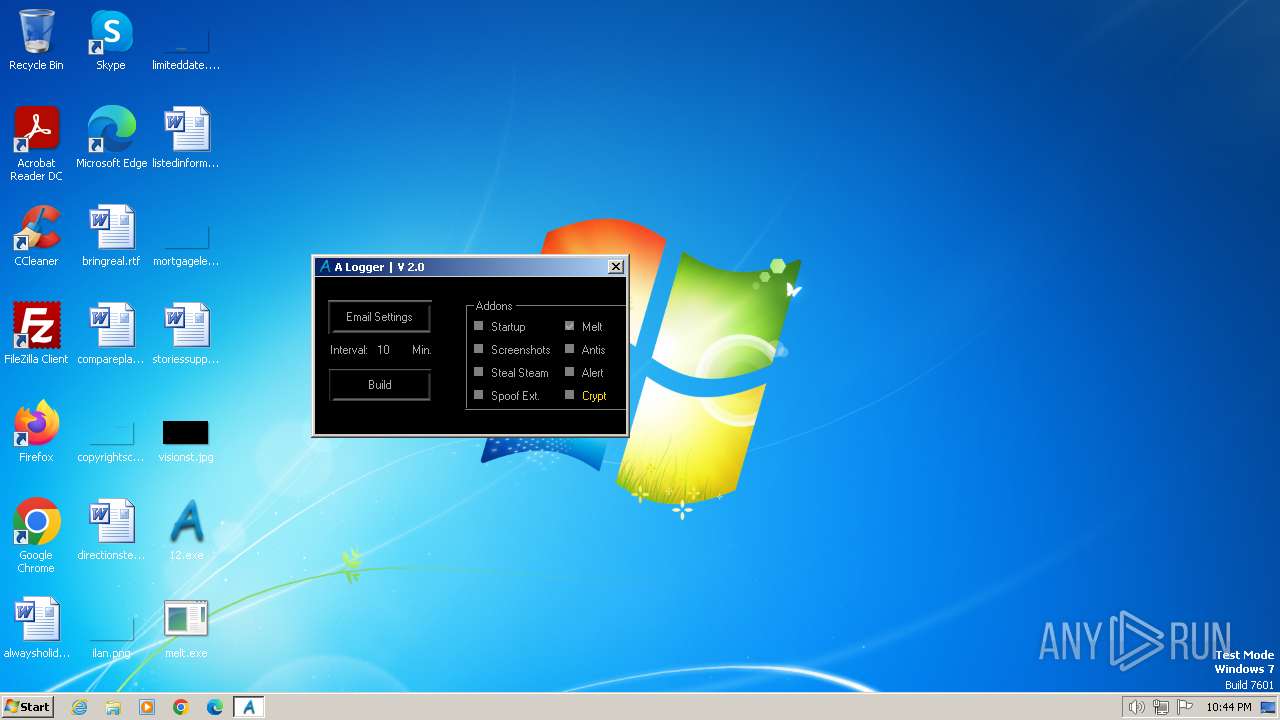
Drops the executable file immediately after the start
- 12.exe (PID: 3268)
- csc.exe (PID: 3196)
- melt.exe (PID: 3612)
Starts Visual C# compiler
- 12.exe (PID: 3268)
SUSPICIOUS
Reads the Internet Settings
- melt.exe (PID: 3612)
- 12.exe (PID: 3268)
Executable content was dropped or overwritten
- csc.exe (PID: 3196)
- melt.exe (PID: 3612)
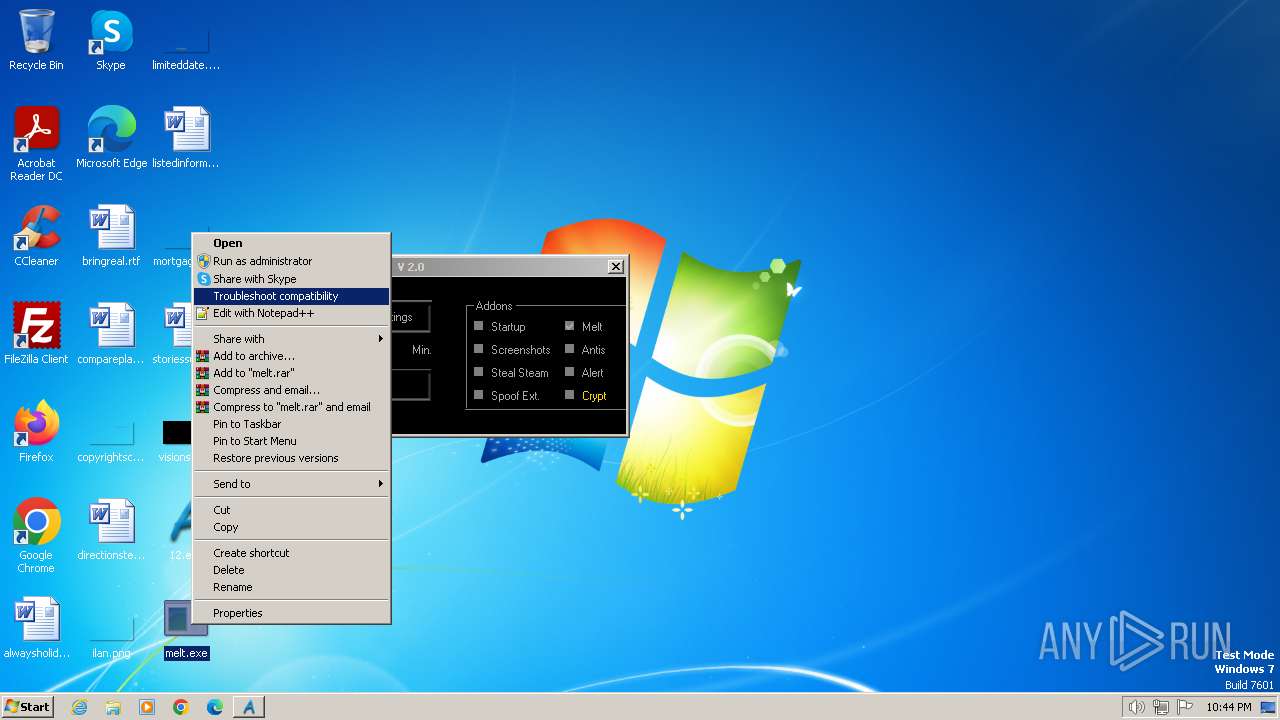
Starts itself from another location
- melt.exe (PID: 3612)
Reads security settings of Internet Explorer
- melt.exe (PID: 3612)
Uses .NET C# to load dll
- 12.exe (PID: 3268)
INFO
Checks supported languages
- csc.exe (PID: 3196)
- 12.exe (PID: 3268)
- cvtres.exe (PID: 2108)
- melt.exe (PID: 3612)
- Google-Update.exe (PID: 3132)
Create files in a temporary directory
- cvtres.exe (PID: 2108)
- 12.exe (PID: 3268)
Reads the computer name
- 12.exe (PID: 3268)
- melt.exe (PID: 3612)
- Google-Update.exe (PID: 3132)
Reads the machine GUID from the registry
- cvtres.exe (PID: 2108)
- melt.exe (PID: 3612)
- 12.exe (PID: 3268)
Manual execution by a user
- melt.exe (PID: 3612)
Creates files or folders in the user directory
- melt.exe (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:08:11 09:23:30+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 173056 |
| InitializedDataSize: | 34304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2c30e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
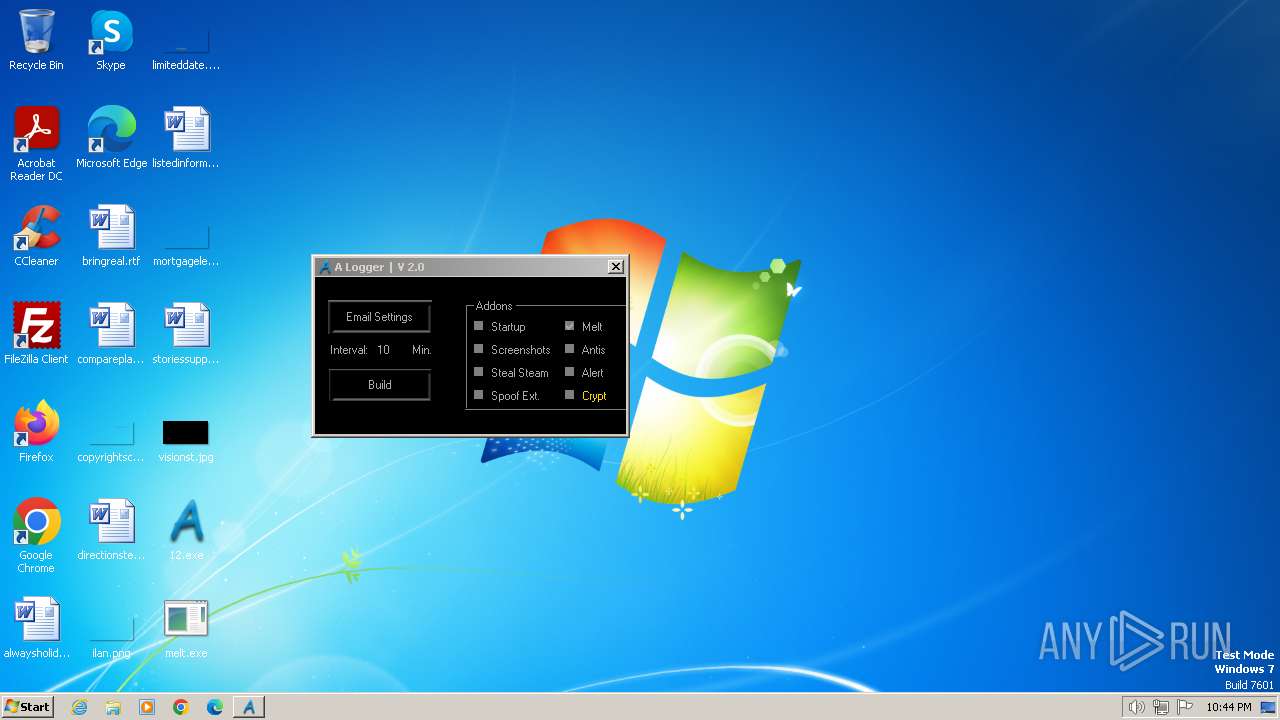
| CompanyName: | TickTack HF |
| FileDescription: | A Logger |
| FileVersion: | 1.0.0.0 |
| InternalName: | A Logger.exe |
| LegalCopyright: | Copyright © 2013 |
| OriginalFileName: | A Logger.exe |
| ProductName: | A Logger |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
47
Monitored processes
5
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2108 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES6A2C.tmp" "c:\Users\admin\Desktop\CSC6A2B.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3132 | "C:\Users\admin\AppData\Local\Google-Update.exe" | C:\Users\admin\AppData\Local\Google-Update.exe | — | melt.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 3196 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\_vosvgbw.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | 12.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\Desktop\12.exe" | C:\Users\admin\Desktop\12.exe | — | explorer.exe | |||||||||||
User: admin Company: TickTack HF Integrity Level: MEDIUM Description: A Logger Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3612 | "C:\Users\admin\Desktop\melt.exe" | C:\Users\admin\Desktop\melt.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
7 439
Read events
7 387
Write events
47
Delete events
5
Modification events
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 5 |
Value: 310032002E0065007800650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 07000000000000000100000002000000060000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | 4 |
Value: 310032002E0065007800650000000000 | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000003000000000000000200000001000000FFFFFFFF | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | 0 |
Value: 56003200000000000000000080006D656C742E65786500003E0008000400EFBE00000000000000002A000000000000000000000000000000000000000000000000006D0065006C0074002E00650078006500000018000000 | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (3268) 12.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | 14 |
Value: 56003200000000000000000080006D656C742E65786500003E0008000400EFBE00000000000000002A000000000000000000000000000000000000000000000000006D0065006C0074002E00650078006500000018000000 | |||
Executable files
2
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3612 | melt.exe | C:\Users\admin\AppData\Local\Google-Update.exe | executable | |
MD5:C8C39DC5456A48A2DE23F9E981C82E9F | SHA256:B16BCF25FC3ACE1AC1F03BC8BEC3FC458213198AB00A77655EF037F004874DF9 | |||
| 3612 | melt.exe | C:\Users\admin\AppData\Local\location.txt | text | |
MD5:DE2C8F80599EBBD2D36103B7BE91E733 | SHA256:A1D2FC7831FA41EADEF9B2D47ABB77508AEFDC64E0076799E2A66D23F176CA68 | |||
| 3196 | csc.exe | C:\Users\admin\Desktop\CSC6A2B.tmp | res | |
MD5:4D83CDD9D62E586EE3A343F34F62B0F6 | SHA256:224F76BC130D9BBD7DF3CF2EC43E9C9E680361335CA973893A8F201496B223FC | |||
| 3268 | 12.exe | C:\Users\admin\AppData\Local\Temp\_vosvgbw.cmdline | text | |
MD5:51F9893182CDFC8648EAB7F7E0E96835 | SHA256:DE6B55B48411D0778A8C6724930536295E5B5EF3BC3B6325796F83DC2BF3B5F8 | |||
| 3196 | csc.exe | C:\Users\admin\Desktop\melt.exe | executable | |
MD5:C8C39DC5456A48A2DE23F9E981C82E9F | SHA256:B16BCF25FC3ACE1AC1F03BC8BEC3FC458213198AB00A77655EF037F004874DF9 | |||
| 3268 | 12.exe | C:\Users\admin\AppData\Local\Temp\_vosvgbw.0.cs | text | |
MD5:B20335CCE9FBF44CF200EF2BECD1D7D3 | SHA256:44C0D3E881EE6C0D479837C4659805F55FAF0265C5E8AB08A0A30D6DFDB5D603 | |||
| 2108 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES6A2C.tmp | binary | |
MD5:F590BED9F0AD23147FBB62325EA9E8F1 | SHA256:9FB123504144ACA28DA5C6FA924B0E8221ABEC8835CEA8ADBC5EE39D703FFE87 | |||
| 3196 | csc.exe | C:\Users\admin\AppData\Local\Temp\_vosvgbw.out | text | |
MD5:EA2B610409BD3A3628BE8A818A29113D | SHA256:FD73B6AD2B4024F2542C8340FC79C8BE9E897B29583D57EF3CA3712986A81305 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
— | — | GET | 200 | 2.16.164.128:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | — | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 2.19.126.137:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 2.16.164.128:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 2.16.100.168:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |