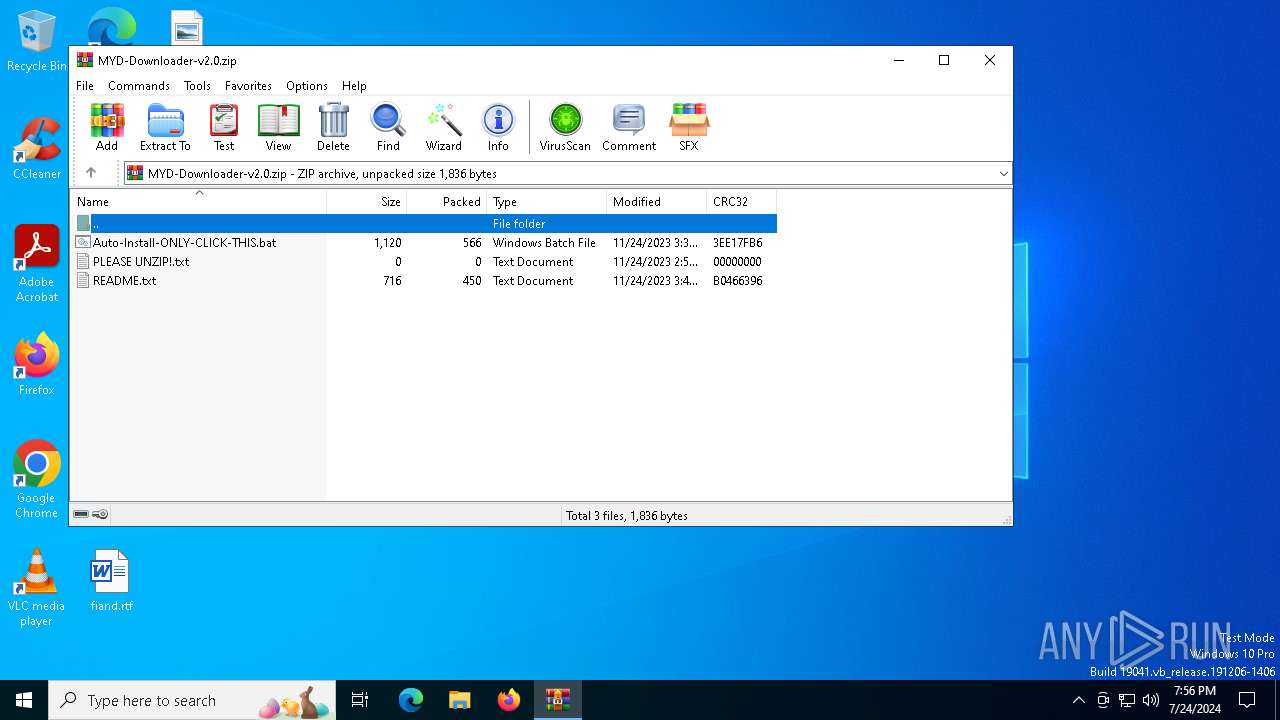
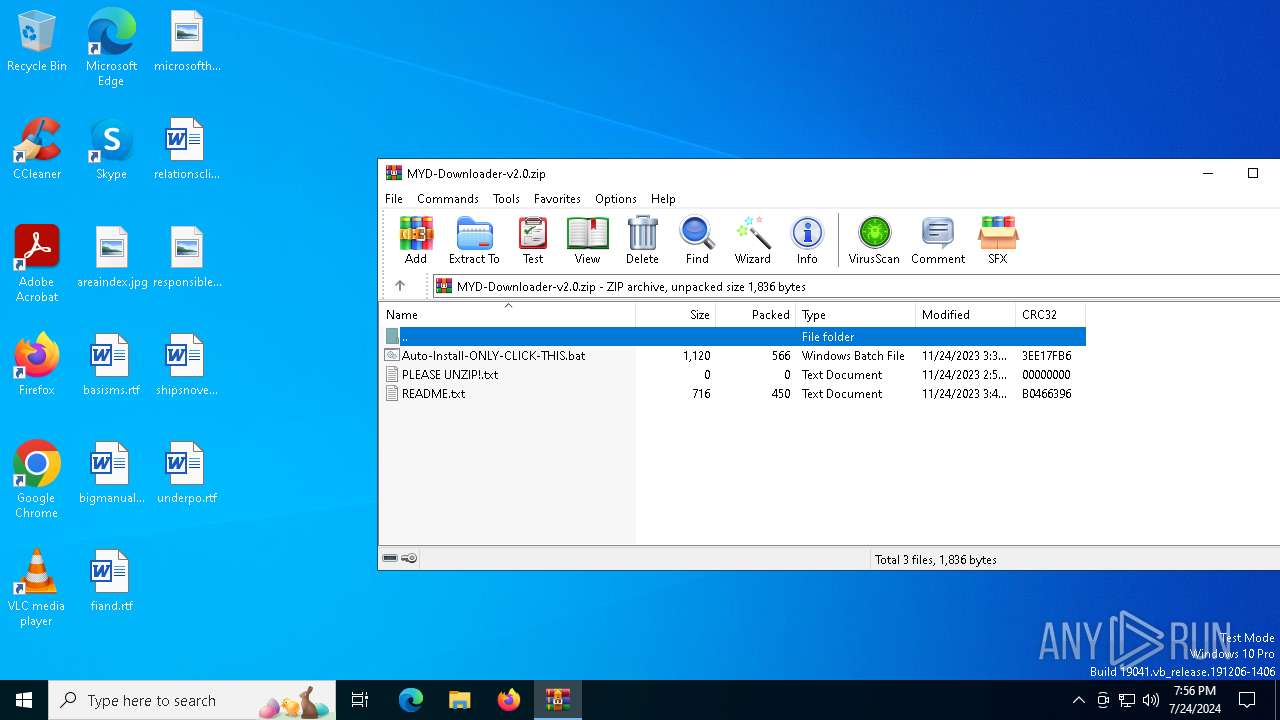
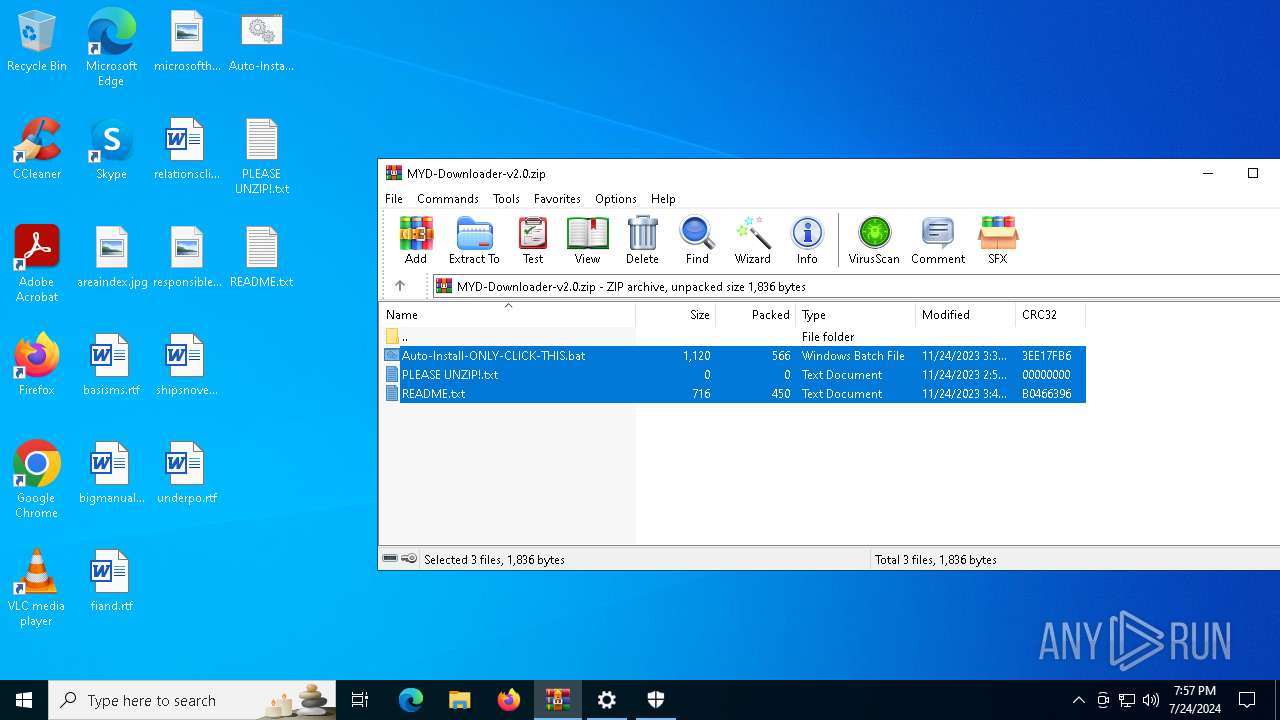
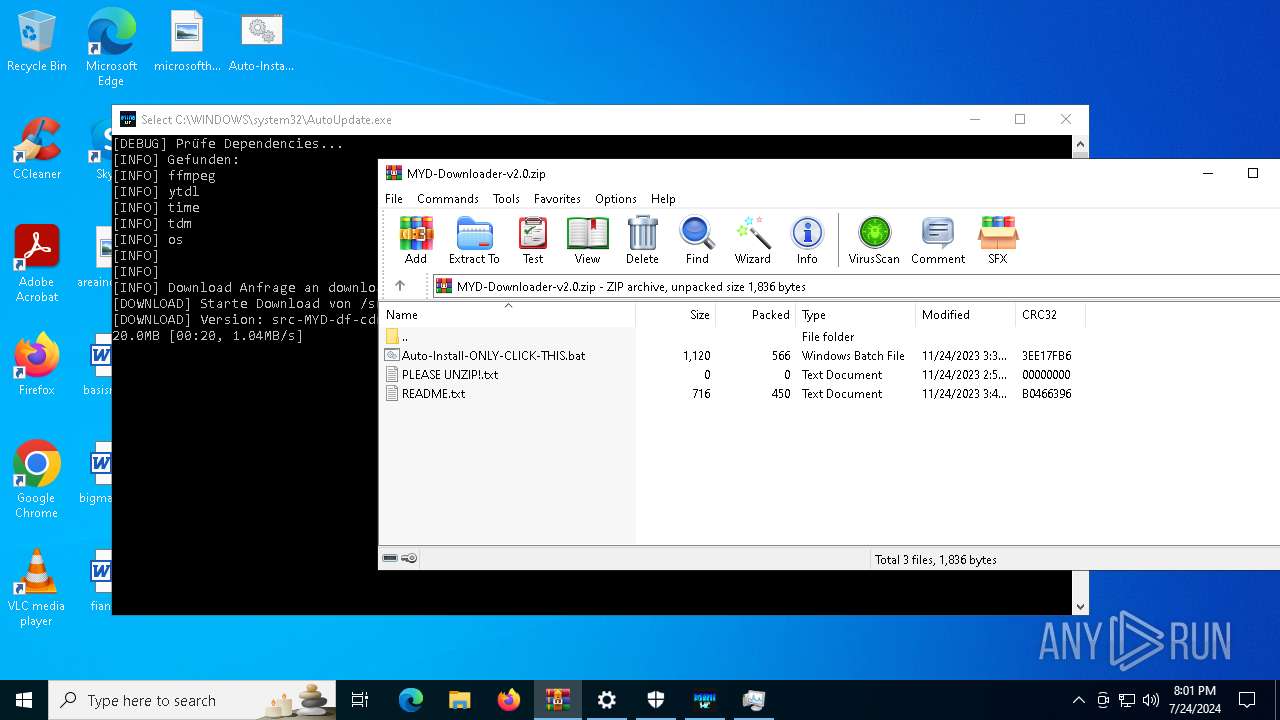
| File name: | MYD-Downloader-v2.0.zip |
| Full analysis: | https://app.any.run/tasks/8a916f58-8cd1-4940-b31e-a70d25d4e11a |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | July 24, 2024, 19:56:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BCD611C945F2976150AFEB200147E1F2 |
| SHA1: | 514C8EE3ACBB8F7F2EF071B679910D412528444F |
| SHA256: | 11660830311F8F7BC7B1CD76E491725D9376E2471FA1015391397CA4DF736233 |
| SSDEEP: | 48:9+d9+Lku9GIIzZwqQU18hLQnVDbPR+OlRwP6FQ0sBqxD9:0Lu9GIINDZ8qVfp7n1Q0sC9 |
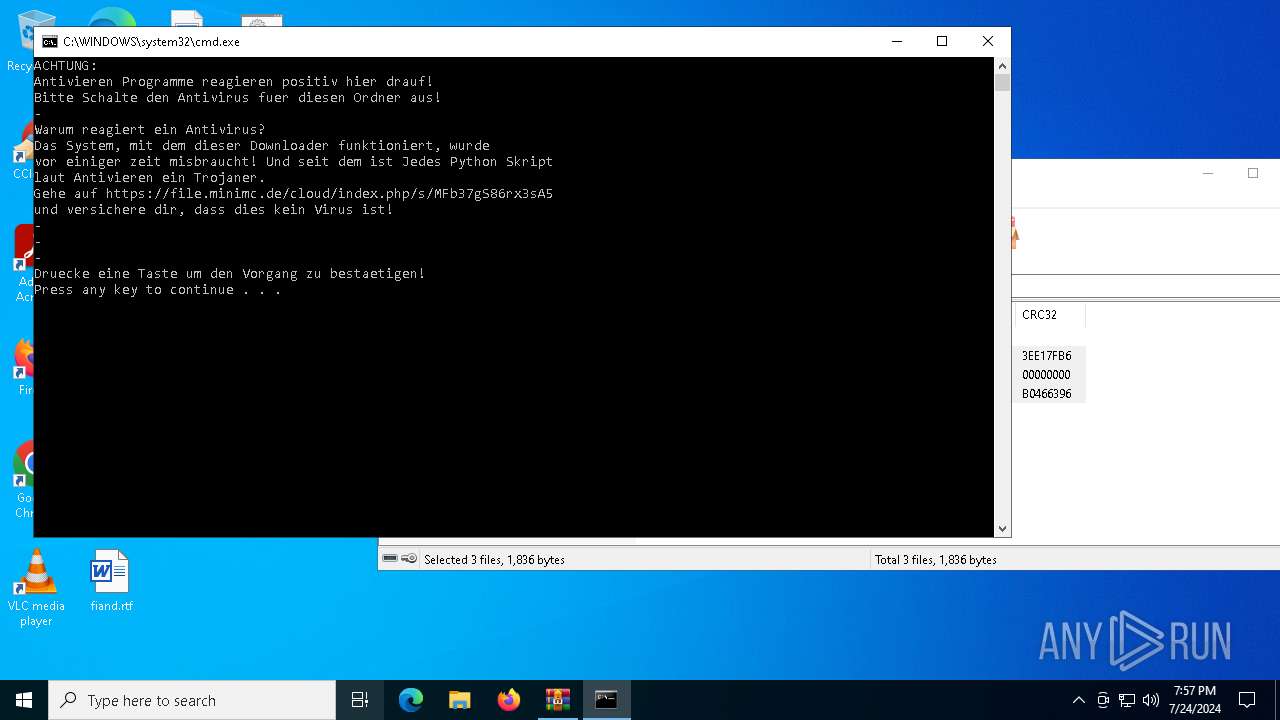
MALICIOUS
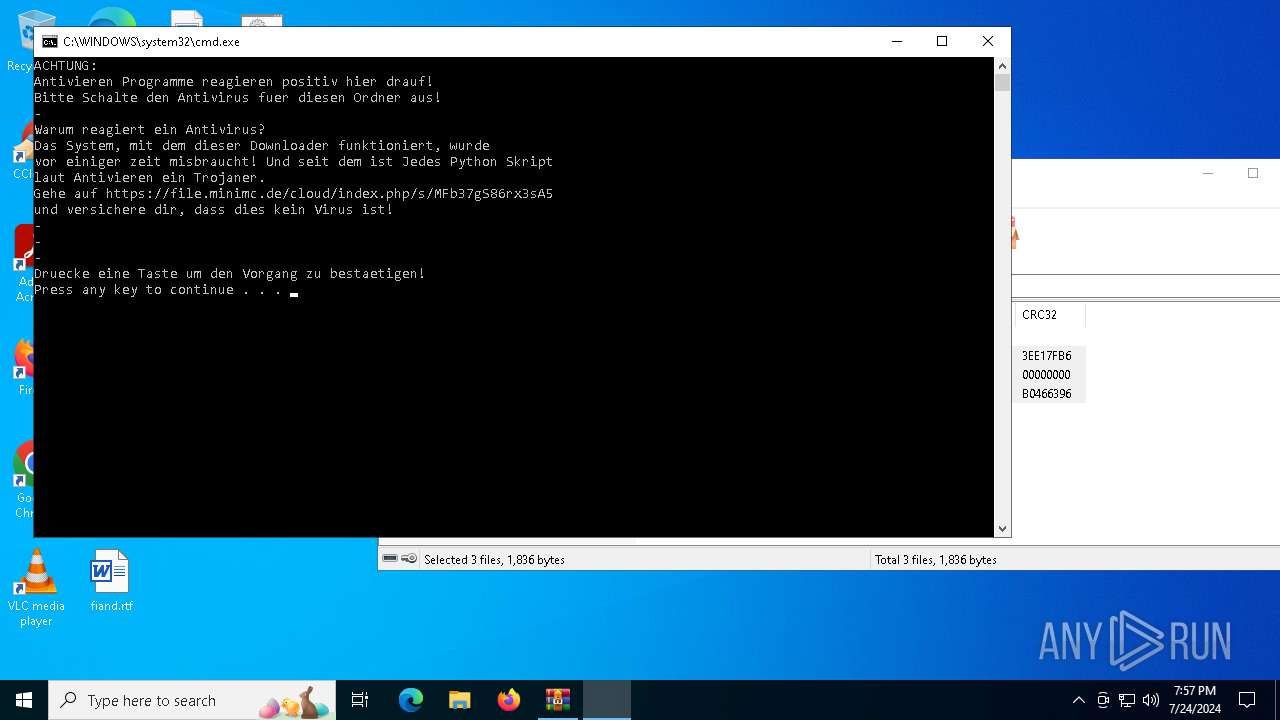
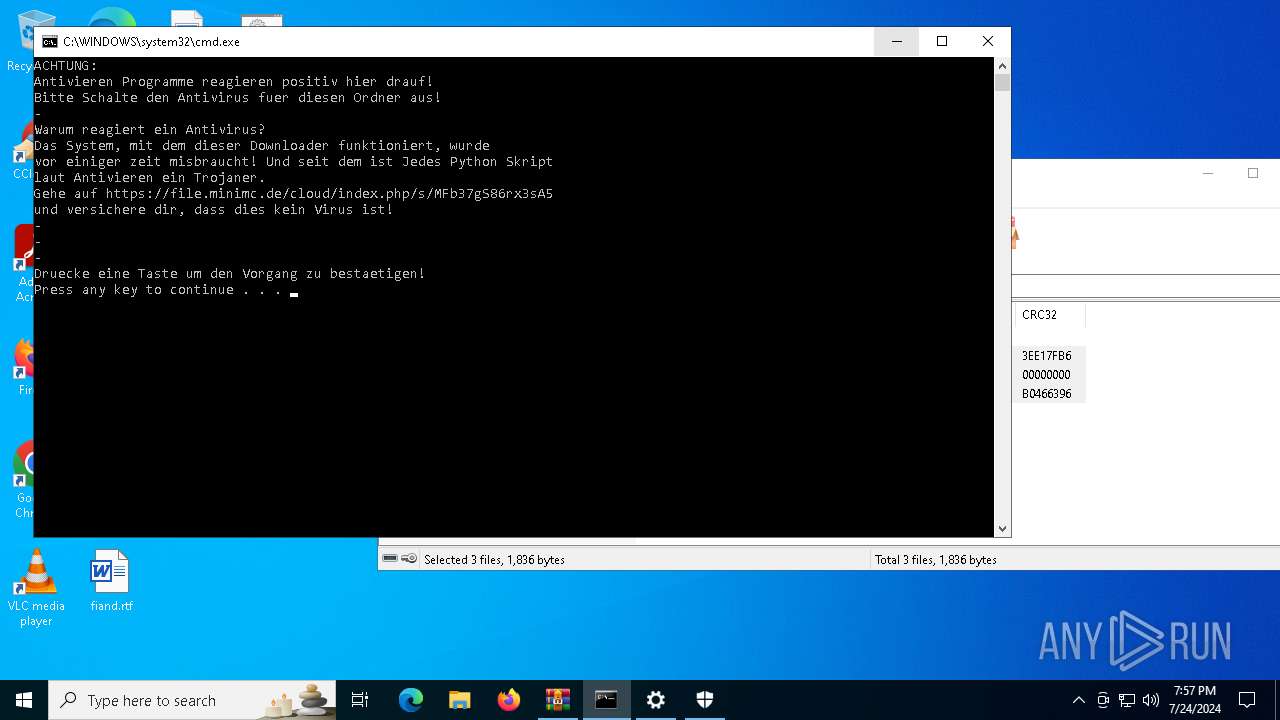
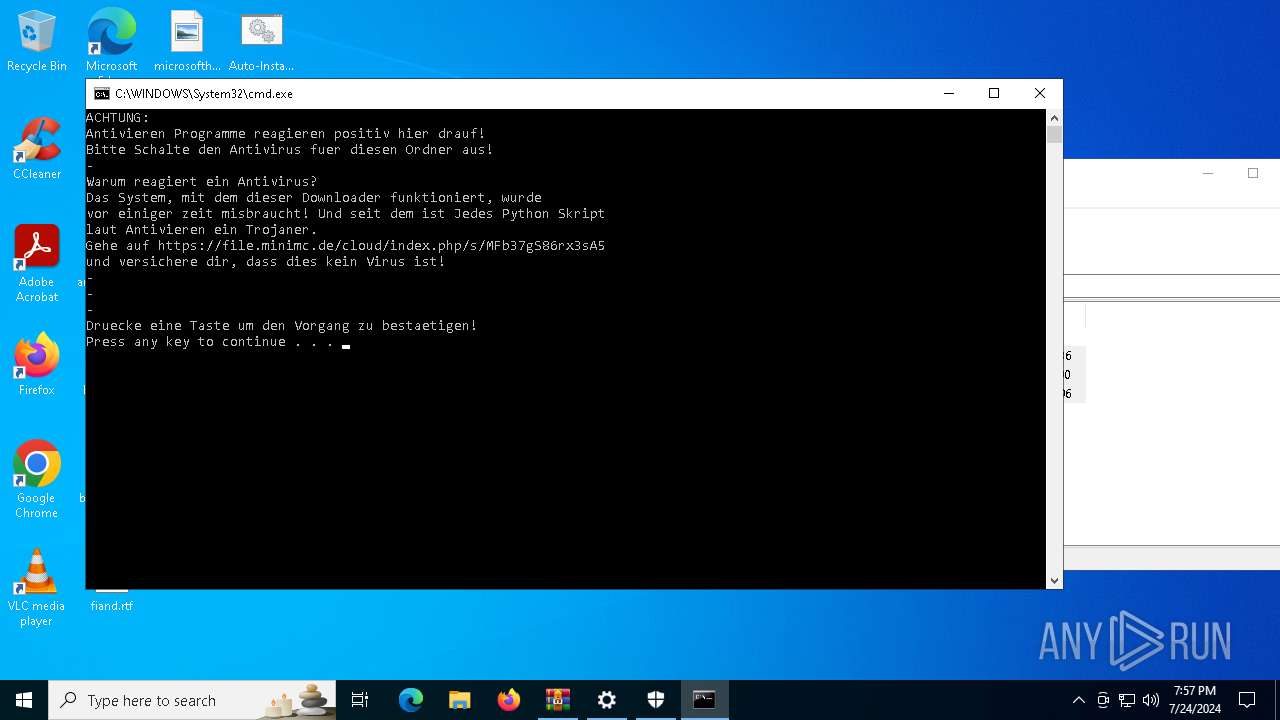
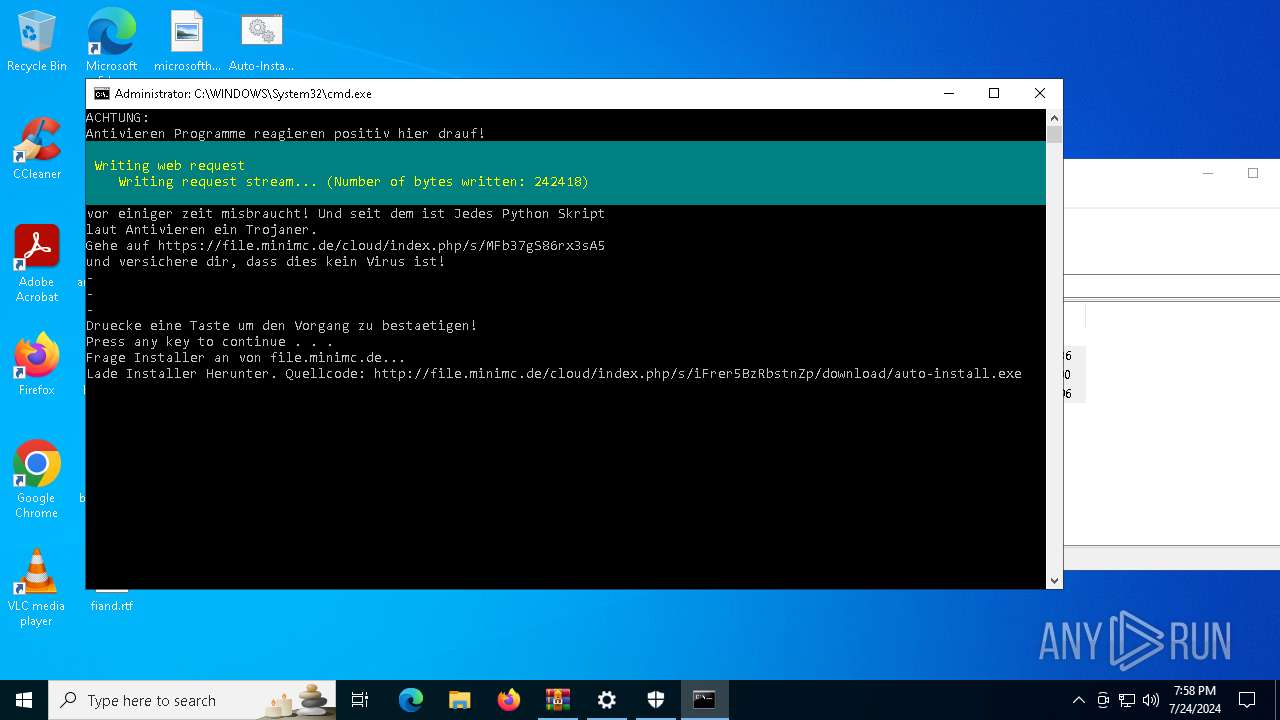
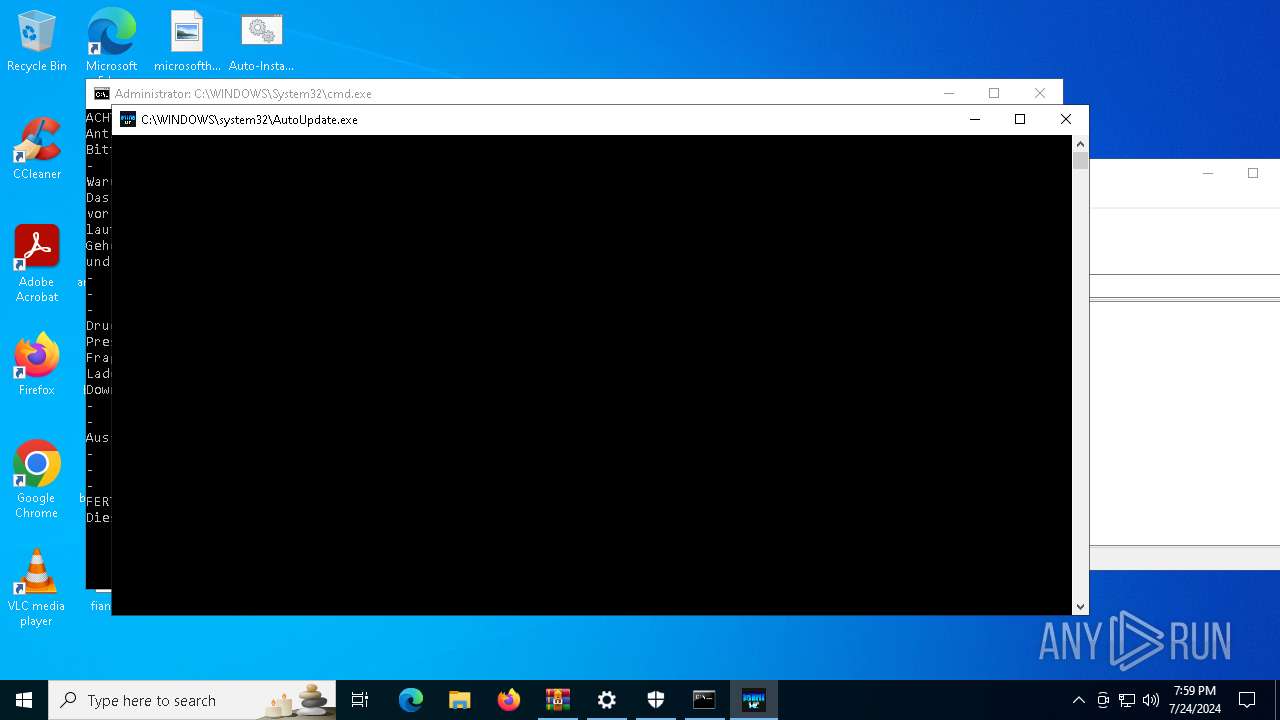
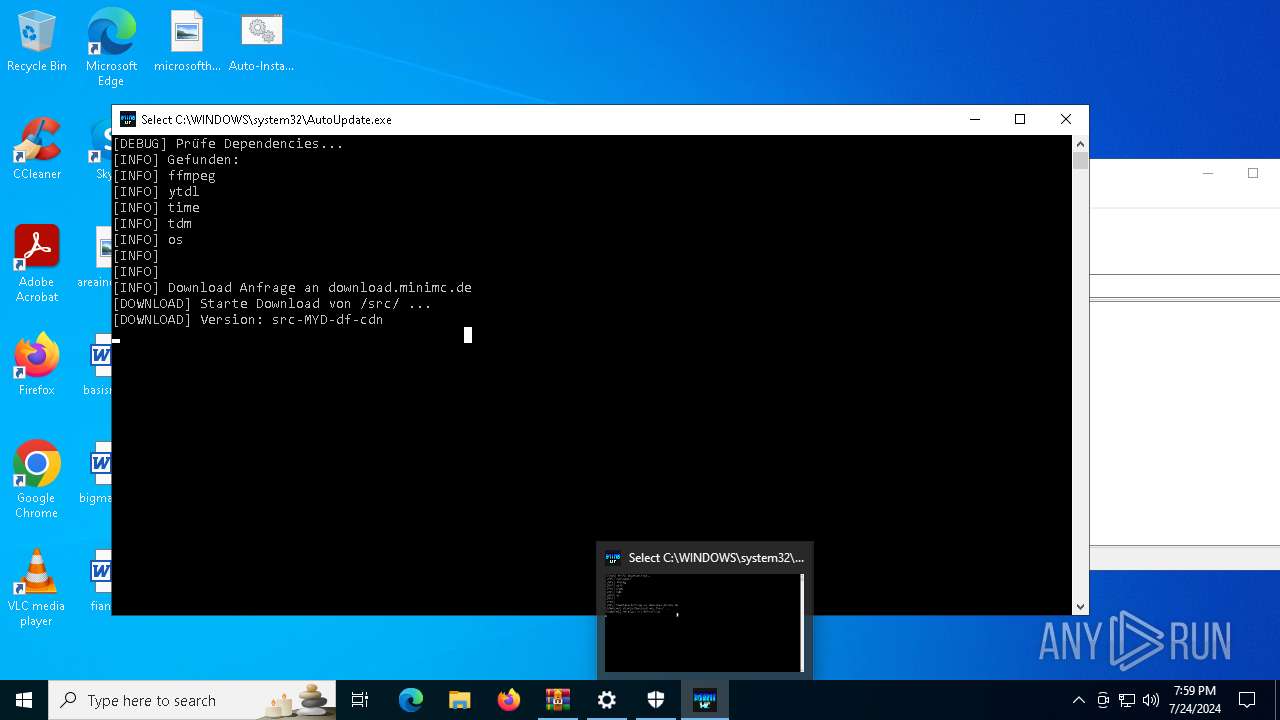
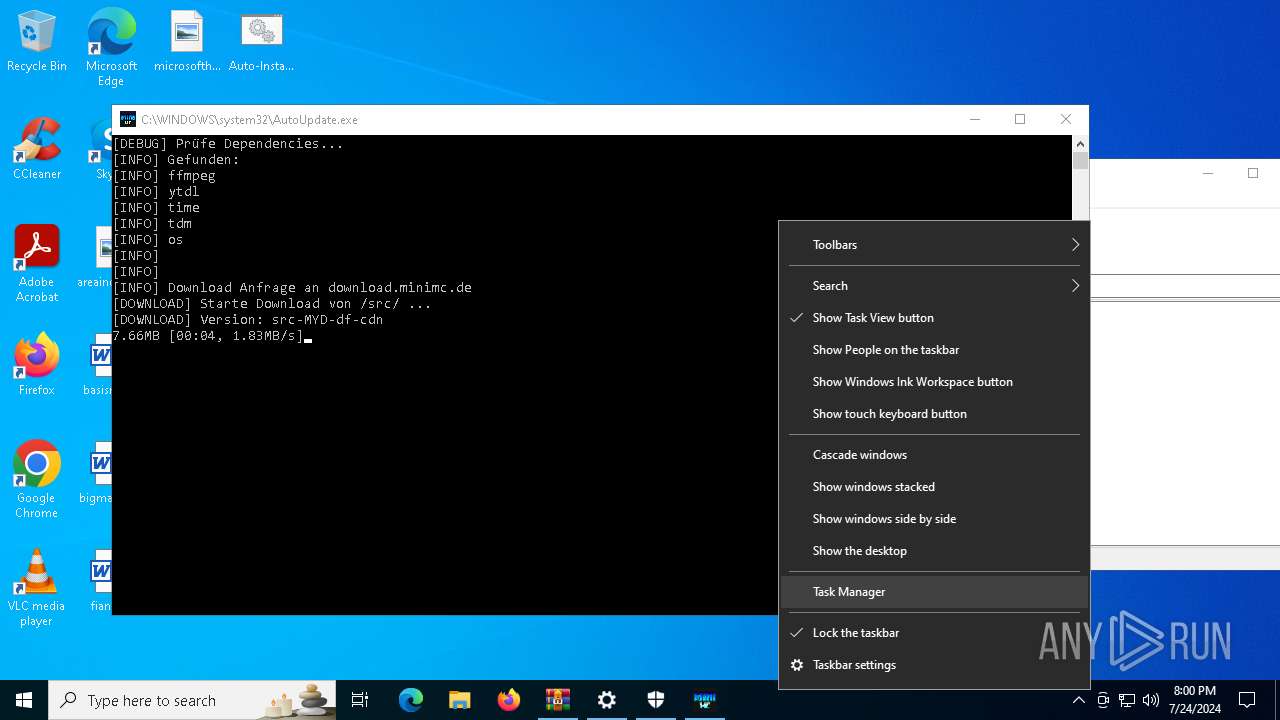
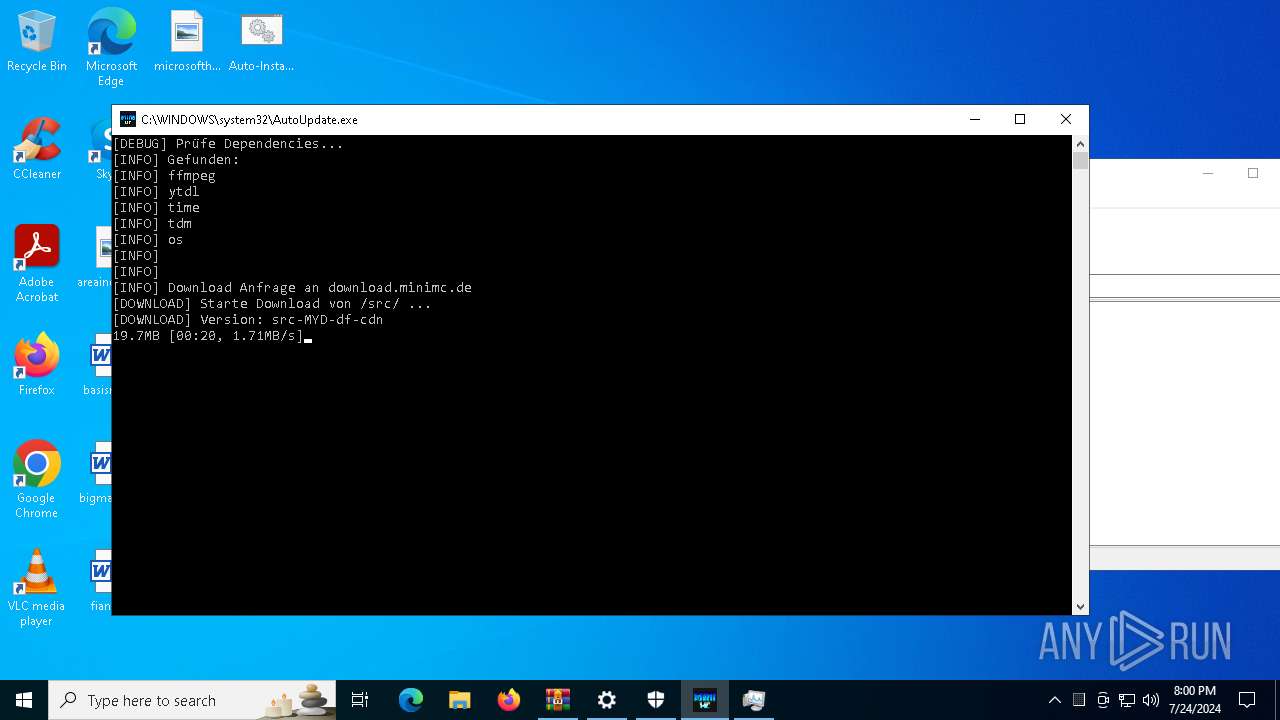
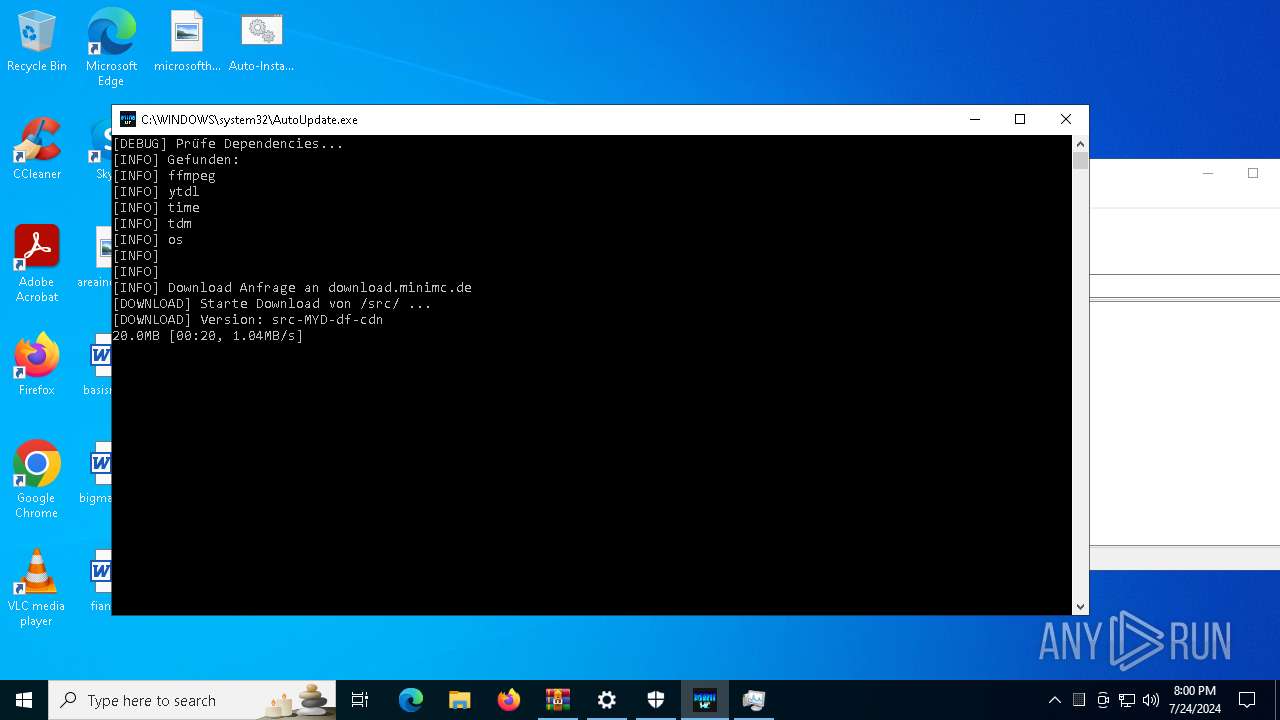
Drops the executable file immediately after the start
- powershell.exe (PID: 8104)
- AutoUpdate.exe (PID: 7532)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 8104)
SUSPICIOUS
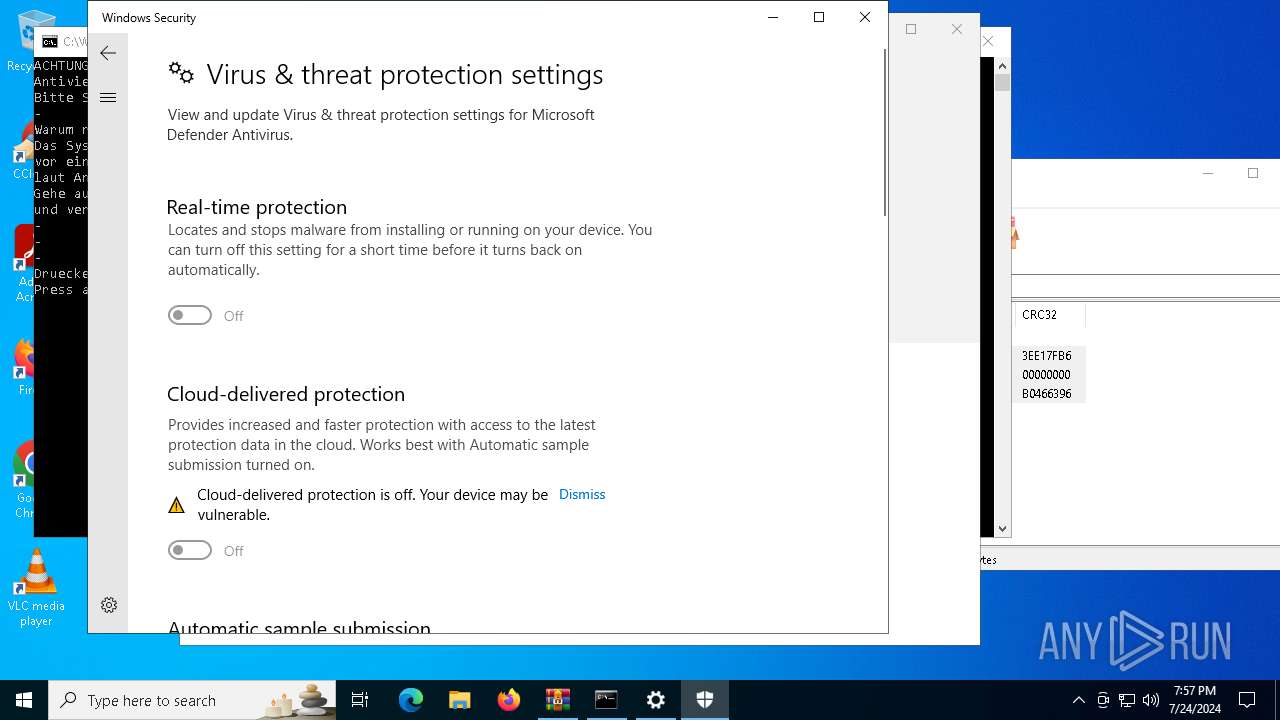
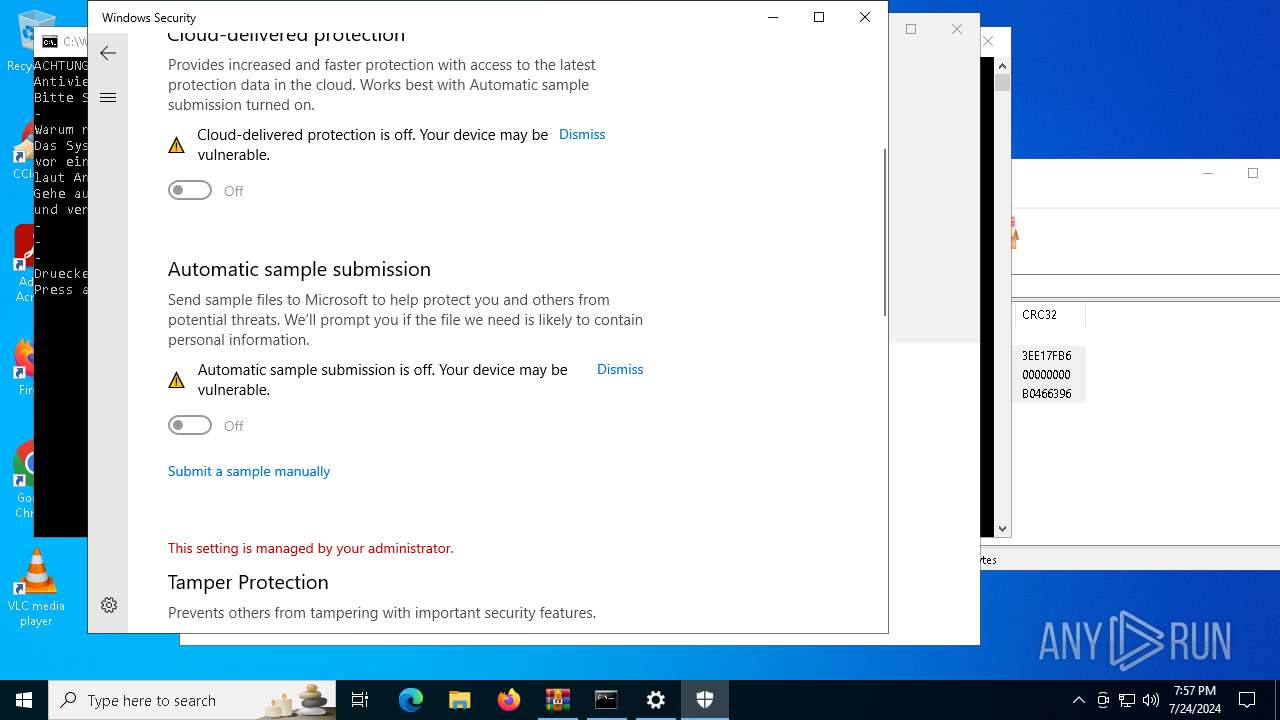
Reads security settings of Internet Explorer
- SecHealthUI.exe (PID: 5236)
Executable content was dropped or overwritten
- powershell.exe (PID: 8104)
- AutoUpdate.exe (PID: 7532)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7708)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7708)
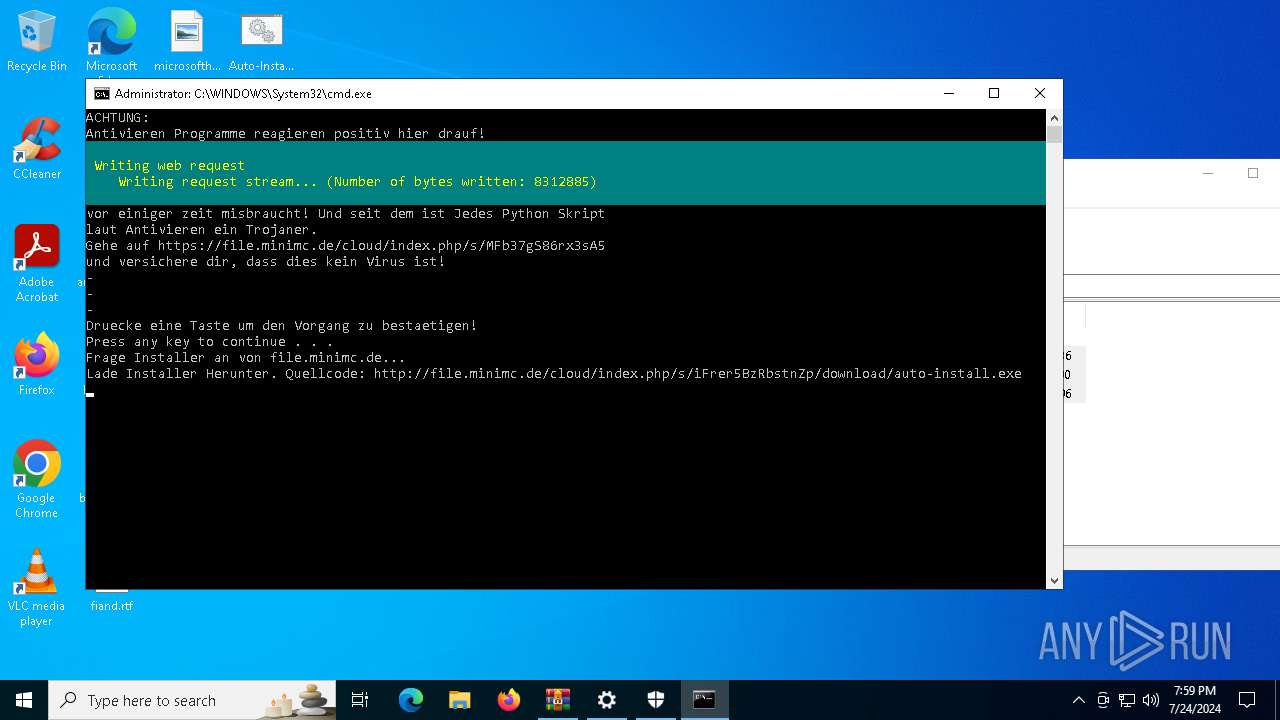
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 7708)
Potential Corporate Privacy Violation
- powershell.exe (PID: 8104)
- AutoUpdate.exe (PID: 2816)
Process drops legitimate windows executable
- AutoUpdate.exe (PID: 7532)
Application launched itself
- AutoUpdate.exe (PID: 7532)
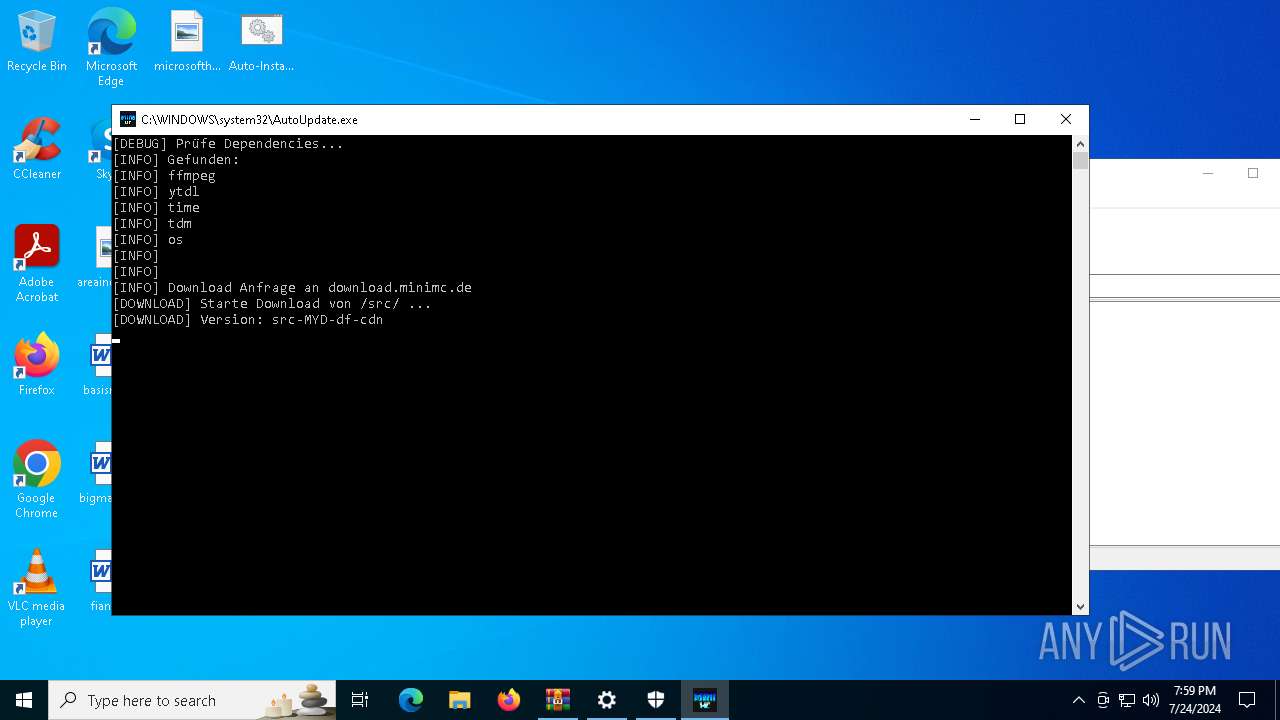
Process drops python dynamic module
- AutoUpdate.exe (PID: 7532)
Loads Python modules
- AutoUpdate.exe (PID: 2816)
Process requests binary or script from the Internet
- powershell.exe (PID: 8104)
The process drops C-runtime libraries
- AutoUpdate.exe (PID: 7532)
INFO
Reads the computer name
- TextInputHost.exe (PID: 4028)
- SecHealthUI.exe (PID: 5236)
- AutoUpdate.exe (PID: 7532)
- AutoUpdate.exe (PID: 2816)
Manual execution by a user
- cmd.exe (PID: 4036)
- cmd.exe (PID: 7708)
- Taskmgr.exe (PID: 7500)
- Taskmgr.exe (PID: 7524)
Checks supported languages
- SecHealthUI.exe (PID: 5236)
- TextInputHost.exe (PID: 4028)
- AutoUpdate.exe (PID: 7532)
- AutoUpdate.exe (PID: 2816)
Disables trace logs
- powershell.exe (PID: 8104)
Checks proxy server information
- slui.exe (PID: 4296)
- powershell.exe (PID: 8104)
- AutoUpdate.exe (PID: 2816)
Create files in a temporary directory
- AutoUpdate.exe (PID: 7532)
Reads the software policy settings
- slui.exe (PID: 4296)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:24 16:36:28 |
| ZipCRC: | 0x3ee17fb6 |
| ZipCompressedSize: | 566 |
| ZipUncompressedSize: | 1120 |
| ZipFileName: | Auto-Install-ONLY-CLICK-THIS.bat |
Total processes
165
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1328 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\MYD-Downloader-v2.0.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2816 | AutoUpdate.exe | C:\Windows\System32\AutoUpdate.exe | AutoUpdate.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4028 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 4036 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Auto-Install-ONLY-CLICK-THIS.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4296 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4452 | C:\Windows\System32\SecurityHealthHost.exe {E041C90B-68BA-42C9-991E-477B73A75C90} -Embedding | C:\Windows\System32\SecurityHealthHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Security Health Host Exit code: 0 Version: 4.18.1907.16384 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4656 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | "C:\WINDOWS\SystemApps\Microsoft.Windows.SecHealthUI_cw5n1h2txyewy\SecHealthUI.exe" -ServerName:SecHealthUI.AppXep4x2tbtjws1v9qqs0rmb3hxykvkpqtn.mca | C:\Windows\SystemApps\Microsoft.Windows.SecHealthUI_cw5n1h2txyewy\SecHealthUI.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Defender application Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5792 | timeout 10 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7220 | C:\Windows\System32\SecurityHealthHost.exe {E041C90B-68BA-42C9-991E-477B73A75C90} -Embedding | C:\Windows\System32\SecurityHealthHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Security Health Host Exit code: 0 Version: 4.18.1907.16384 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 123
Read events
18 097
Write events
25
Delete events
1
Modification events
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MYD-Downloader-v2.0.zip | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (4452) SecurityHealthHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%systemroot%\system32\SecurityHealthAgent.dll,-12001 |
Value: Windows Security | |||
Executable files
24
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7532 | AutoUpdate.exe | C:\Users\admin\AppData\Local\Temp\_MEI75322\_hashlib.pyd | executable | |
MD5:1C88B53C50B5F2BB687B554A2FC7685D | SHA256:19DD3B5EBB840885543974A4CB6C8EA4539D76E3672BE0F390A3A82443391778 | |||
| 8104 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:9F14CED7ED5F95A6896370BF79BD2805 | SHA256:5C046D30BF62D394E5C48F3BE371317B90BAC088DD9BD16EE8336B34E2BA38F2 | |||
| 7532 | AutoUpdate.exe | C:\Users\admin\AppData\Local\Temp\_MEI75322\_bz2.pyd | executable | |
MD5:A8A37BA5E81D967433809BF14D34E81D | SHA256:50E21CE62F8D9BAB92F6A7E9B39A86406C32D2DF18408BB52FFB3D245C644C7B | |||
| 1328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1328.32882\Auto-Install-ONLY-CLICK-THIS.bat | text | |
MD5:C53D943C26D84A4D3E7169447A2FECA3 | SHA256:7747F3DB7E3ACC60799070D77904189BC82D0E26A40FBC8665ECC149C1511868 | |||
| 7532 | AutoUpdate.exe | C:\Users\admin\AppData\Local\Temp\_MEI75322\_queue.pyd | executable | |
MD5:E0CC8C12F0B289EA87C436403BC357C1 | SHA256:9517689D7D97816DEE9E6C01FFD35844A3AF6CDE3FF98F3A709D52157B1ABE03 | |||
| 7532 | AutoUpdate.exe | C:\Users\admin\AppData\Local\Temp\_MEI75322\_decimal.pyd | executable | |
MD5:5E8AA9CD4742A51ACC5B2155770241D5 | SHA256:59FEE7A8D0A85ED98BBF5DFB7A0AD64B60CBE88427EFD98B3C9FAAD3E4421A87 | |||
| 7532 | AutoUpdate.exe | C:\Users\admin\AppData\Local\Temp\_MEI75322\VCRUNTIME140.dll | executable | |
MD5:870FEA4E961E2FBD00110D3783E529BE | SHA256:76FDB83FDE238226B5BEBAF3392EE562E2CB7CA8D3EF75983BF5F9D6C7119644 | |||
| 7532 | AutoUpdate.exe | C:\Users\admin\AppData\Local\Temp\_MEI75322\_socket.pyd | executable | |
MD5:290DBF92268AEBDE8B9507B157BEF602 | SHA256:E05C5342D55CB452E88E041061FABA492D6DD9268A7F67614A8143540ACA2BFE | |||
| 7532 | AutoUpdate.exe | C:\Users\admin\AppData\Local\Temp\_MEI75322\_lzma.pyd | executable | |
MD5:BC07D7AC5FDC92DB1E23395FDE3420F2 | SHA256:AB822F7E846D4388B6F435D788A028942096BA1344297E0B7005C9D50814981B | |||
| 7532 | AutoUpdate.exe | C:\Users\admin\AppData\Local\Temp\_MEI75322\_multiprocessing.pyd | executable | |
MD5:15291D70D00D36BA9B079A4AF91EFB1A | SHA256:25CF4173FB40A3BB197C877742CB5AD13B6EF591B8195D5429A71DC7689F9AB5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
66
DNS requests
31
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6344 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1000 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2816 | AutoUpdate.exe | GET | — | 188.114.97.3:80 | http://download.minimc.de/cloud/index.php/s/LTewaiRDNdFrgdG/download | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8104 | powershell.exe | GET | 200 | 188.114.97.3:80 | http://file.minimc.de/cloud/index.php/s/iFrer5BzRbstnZp/download/auto-install.exe | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3656 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2628 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4204 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2628 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3948 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5368 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8104 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
8104 | powershell.exe | Misc activity | ET INFO Request for EXE via Powershell |
8104 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
8104 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
8104 | powershell.exe | Misc activity | ET INFO EXE - Served Inline HTTP |
1 ETPRO signatures available at the full report