| File name: | letspro-5.2.9.zip.exe |
| Full analysis: | https://app.any.run/tasks/5351811e-acce-4b25-8b42-8492478571d3 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2025, 20:16:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | DA64883698FBC3D8C8AB60A7386E8058 |
| SHA1: | 04FEB77D8166599D360DF1302E39B3C16AC71B8B |
| SHA256: | 11540A90F1DC6BAD4EC1BFA3433253D0A89DA35B1195A8284AC262AF99046CCF |
| SSDEEP: | 196608:22IPXAa3MfVmKbOkOisgbxI1VfVOuWIzU1K2zZaw8:ji8ftbOkOPgb6dOXSUFZD8 |
MALICIOUS
Executing a file with an untrusted certificate
- letspro-5.2.9.zip.exe (PID: 2104)
Antivirus name has been found in the command line (generic signature)
- powershell.exe (PID: 7440)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 456)
Changes the autorun value in the registry
- iusb3mon.exe (PID: 8020)
SUSPICIOUS
Executable content was dropped or overwritten
- letspro-5.2.9.zip.exe (PID: 1512)
- irsetup.exe (PID: 1268)
- letsvpn-latest.exe (PID: 780)
Reads security settings of Internet Explorer
- irsetup.exe (PID: 1268)
- letspro-5.2.9.zip.exe (PID: 1512)
Starts POWERSHELL.EXE for commands execution
- irsetup.exe (PID: 1268)
- iusb3mon.exe (PID: 8020)
Get information on the list of running processes
- irsetup.exe (PID: 1268)
Process drops legitimate windows executable
- irsetup.exe (PID: 1268)
The process drops C-runtime libraries
- irsetup.exe (PID: 1268)
Malware-specific behavior (creating "System.dll" in Temp)
- letsvpn-latest.exe (PID: 780)
The process creates files with name similar to system file names
- letsvpn-latest.exe (PID: 780)
Starts CMD.EXE for commands execution
- iusb3mon.exe (PID: 8020)
There is functionality for taking screenshot (YARA)
- iusb3mon.exe (PID: 8020)
- letsvpn-latest.exe (PID: 780)
There is functionality for VM detection Parallels (YARA)
- iusb3mon.exe (PID: 8020)
There is functionality for VM detection VMWare (YARA)
- iusb3mon.exe (PID: 8020)
Removes files via Powershell
- powershell.exe (PID: 4648)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 4648)
Manipulates environment variables
- powershell.exe (PID: 4648)
The process bypasses the loading of PowerShell profile settings
- iusb3mon.exe (PID: 8020)
Base64-obfuscated command line is found
- iusb3mon.exe (PID: 8020)
Probably obfuscated PowerShell command line is found
- iusb3mon.exe (PID: 8020)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4648)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 4648)
There is functionality for VM detection VirtualBox (YARA)
- iusb3mon.exe (PID: 8020)
Connects to unusual port
- iusb3mon.exe (PID: 8020)
INFO
The sample compiled with english language support
- letspro-5.2.9.zip.exe (PID: 1512)
- irsetup.exe (PID: 1268)
Process checks computer location settings
- letspro-5.2.9.zip.exe (PID: 1512)
- irsetup.exe (PID: 1268)
Reads the computer name
- irsetup.exe (PID: 1268)
- letspro-5.2.9.zip.exe (PID: 1512)
- letsvpn-latest.exe (PID: 780)
Checks supported languages
- letspro-5.2.9.zip.exe (PID: 1512)
- irsetup.exe (PID: 1268)
- iusb3mon.exe (PID: 8020)
- letsvpn-latest.exe (PID: 780)
- iusb3mon.exe (PID: 6560)
Create files in a temporary directory
- letspro-5.2.9.zip.exe (PID: 1512)
- irsetup.exe (PID: 1268)
- letsvpn-latest.exe (PID: 780)
- iusb3mon.exe (PID: 8020)
- SecEdit.exe (PID: 7460)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7980)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 7444)
- powershell.exe (PID: 7440)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 8136)
UPX packer has been detected
- irsetup.exe (PID: 1268)
- iusb3mon.exe (PID: 8020)
The process uses Lua
- irsetup.exe (PID: 1268)
The sample compiled with chinese language support
- irsetup.exe (PID: 1268)
Creates files or folders in the user directory
- irsetup.exe (PID: 1268)
Creates files in the program directory
- irsetup.exe (PID: 1268)
Launch of the file from Registry key
- iusb3mon.exe (PID: 8020)
Manual execution by a user
- iusb3mon.exe (PID: 6560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:06:14 16:16:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 22528 |
| InitializedDataSize: | 48128 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x29e1 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.1.0.0 |
| ProductVersionNumber: | 9.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Created with Setup Factory |
| FileDescription: | Setup Application |
| FileVersion: | 9.1.0.0 |
| InternalName: | suf_launch |
| LegalCopyright: | Setup Engine Copyright © 2004-2012 Indigo Rose Corporation |
| LegalTrademarks: | Setup Factory is a trademark of Indigo Rose Corporation. |
| OriginalFileName: | suf_launch.exe |
| ProductName: | Setup Factory Runtime |
| ProductVersion: | 9.1.0.0 |
Total processes
154
Monitored processes
29
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | cmd.exe /c schtasks.exe /create /tn "Intel USB 3.0 eXtensible Host Controller" /xml "C:\Users\admin\AppData\Local\Temp\1200015_t.xml" | C:\Windows\SysWOW64\cmd.exe | — | iusb3mon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
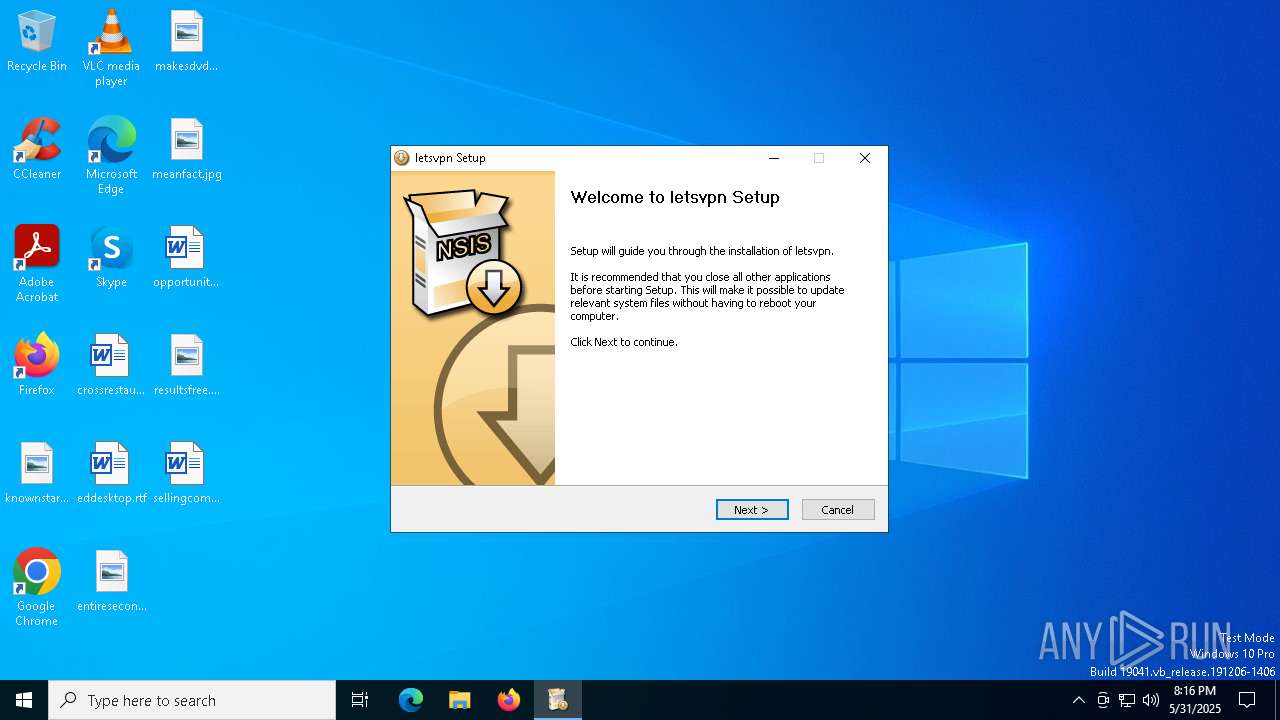
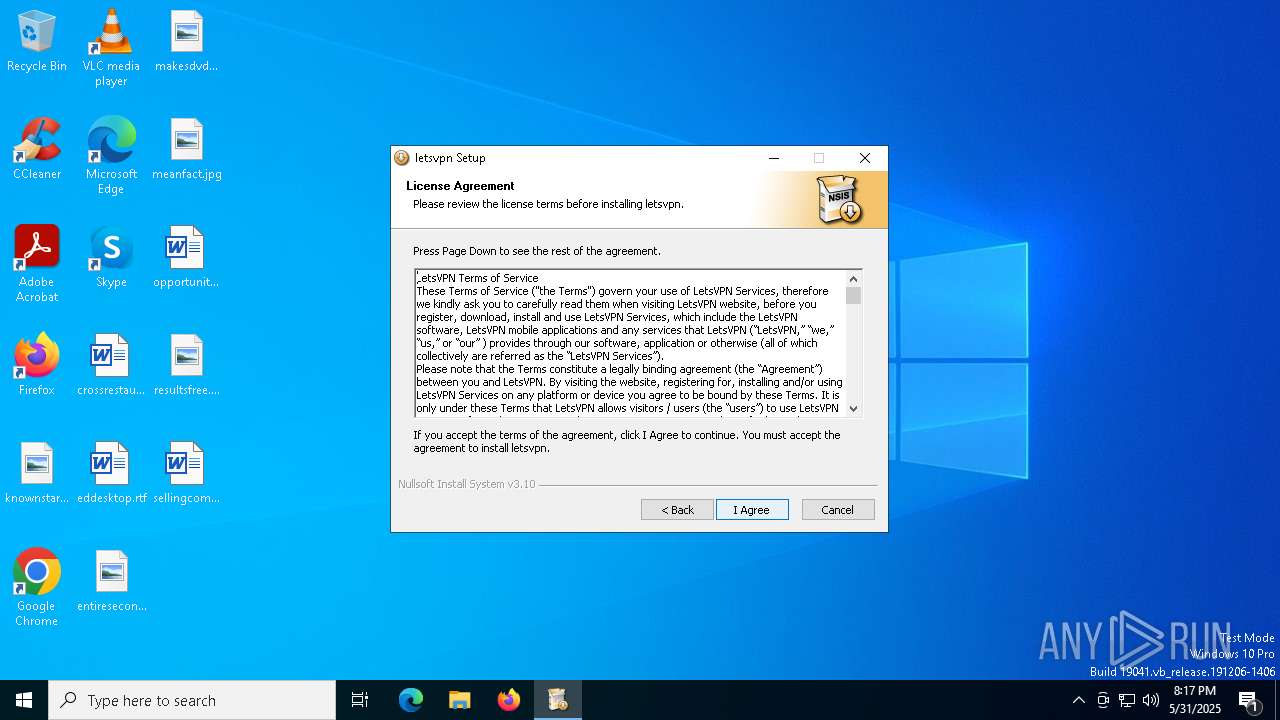
| 780 | "C:\Program Files (x86)\Your Product\letsvpn-latest.exe" | C:\Program Files (x86)\Your Product\letsvpn-latest.exe | irsetup.exe | ||||||||||||
User: admin Company: Letsgo Network Incorporated Integrity Level: HIGH Description: LetsVPN Setup EXE Version: 3.12.0.0 Modules
| |||||||||||||||
| 1056 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" $ppid=(Get-WmiObject -Query 'select ParentProcessId from Win32_Process where ProcessId=1512').ParentProcessId;exit $ppid | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 5492 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1268 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe" __IRAOFF:1742194 "__IRAFN:C:\Users\admin\AppData\Local\Temp\letspro-5.2.9.zip.exe" "__IRCT:0" "__IRTSS:0" "__IRSID:S-1-5-21-1693682860-607145093-2874071422-1001" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | letspro-5.2.9.zip.exe | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: HIGH Description: Setup Application Exit code: 0 Version: 9.1.0.0 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\AppData\Local\Temp\letspro-5.2.9.zip.exe" | C:\Users\admin\AppData\Local\Temp\letspro-5.2.9.zip.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup Application Exit code: 0 Version: 9.1.0.0 Modules
| |||||||||||||||
| 2104 | "C:\Users\admin\AppData\Local\Temp\letspro-5.2.9.zip.exe" | C:\Users\admin\AppData\Local\Temp\letspro-5.2.9.zip.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Application Exit code: 3221226540 Version: 9.1.0.0 Modules
| |||||||||||||||
| 2384 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3124 | schtasks.exe /create /tn "Intel USB 3.0 eXtensible Host Controller" /xml "C:\Users\admin\AppData\Local\Temp\1200015_t.xml" | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 791
Read events
36 782
Write events
8
Delete events
1
Modification events
| (PID) Process: | (8020) iusb3mon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftUSBMonitor |
Value: C:\Users\admin\AppData\Local\AppData\iusb3mon.exe | |||
| (PID) Process: | (8020) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftUSBMonitor |
Value: C:\Users\admin\AppData\Local\AppData\iusb3mon.exe | |||
| (PID) Process: | (7460) SecEdit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SecEdit |
| Operation: | delete value | Name: | LastWinlogonConfig |
Value: | |||
| (PID) Process: | (8020) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (8020) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (8020) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
| (PID) Process: | (208) ShellExperienceHost.exe | Key: | \REGISTRY\A\{7f0e2a45-7213-f653-9a0a-5e24406a09ad}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000363E6AFD68D2DB01 | |||
| (PID) Process: | (8020) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableLockWorkstation |
Value: 0 | |||
Executable files
12
Suspicious files
5
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7440 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ibk5cvuh.xec.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p1rvvybj.2hd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_a4s3hypd.z5v.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8136 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_czhti2im.4h3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1268 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.dat | binary | |
MD5:BAE8DA65578B2F27F37CF2914178D928 | SHA256:0C049ACA113D19E9232F005ACB39AFFFB1CBCF294BD3FD0D50F18337409CCE21 | |||
| 1244 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qzxnpt1i.jrm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1268 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG2.JPG | image | |
MD5:AC40DED6736E08664F2D86A65C47EF60 | SHA256:F35985FE1E46A767BE7DCEA35F8614E1EDD60C523442E6C2C2397D1E23DBD3EA | |||
| 1512 | letspro-5.2.9.zip.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\lua5.1.dll | executable | |
MD5:B5FC476C1BF08D5161346CC7DD4CB0BA | SHA256:12CB9B8F59C00EF40EA8F28BFC59A29F12DC28332BF44B1A5D8D6A8823365650 | |||
| 4560 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_a52d2oqa.3dw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1244 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bmzrqbzt.dac.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7504 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2416 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
jjiiee.com |
| unknown |