| File name: | VPWSSetup_V2112.exe |
| Full analysis: | https://app.any.run/tasks/3f5d97b0-6875-4097-9086-ead9bdd3abac |
| Verdict: | Malicious activity |
| Analysis date: | October 11, 2024, 00:39:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A3743560EAE9E40281062CD35E9306FD |
| SHA1: | B7D2FD287276C97E27291E899EF0181F6722D38B |
| SHA256: | 11321A0A434E25B9C9B629DA15643E5C512FAEA244F42443310EDB472E6DEF6B |
| SSDEEP: | 98304:qnm6Y824UhaslUJHz6F1yGOV1eoUE074sGmmhjlCzxsmr0fwcrbTcgSk6+QxtB8b:6ZtcNazSezpaLib8ue83DRAvd44zE |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- VPWSSetup_V2112.exe (PID: 3844)
- VPWSSetup.exe (PID: 528)
Executable content was dropped or overwritten
- VPWSSetup_V2112.exe (PID: 3844)
- VPWSSetup.exe (PID: 528)
Process drops legitimate windows executable
- VPWSSetup_V2112.exe (PID: 3844)
- VPWSSetup.exe (PID: 528)
The process drops C-runtime libraries
- VPWSSetup_V2112.exe (PID: 3844)
- VPWSSetup.exe (PID: 528)
Reads security settings of Internet Explorer
- VPWSSetup_V2112.exe (PID: 3844)
- VPWSSetup.exe (PID: 528)
Checks Windows Trust Settings
- VPWSSetup.exe (PID: 528)
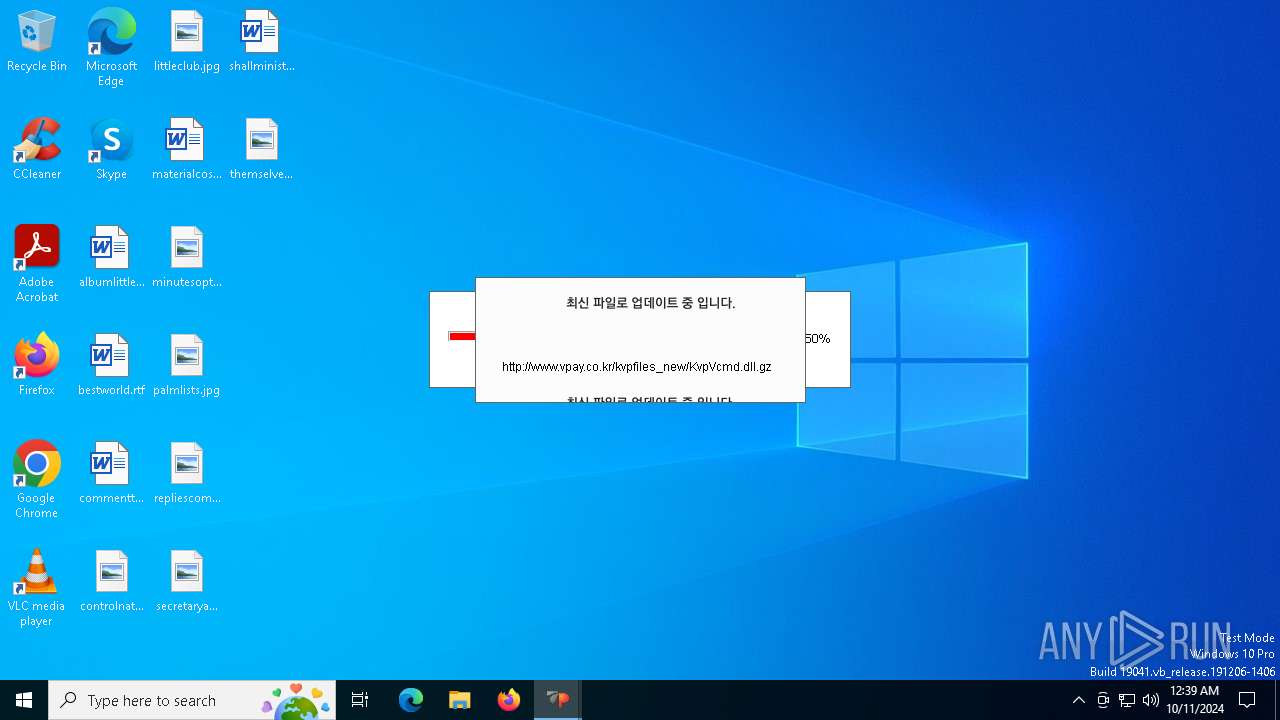
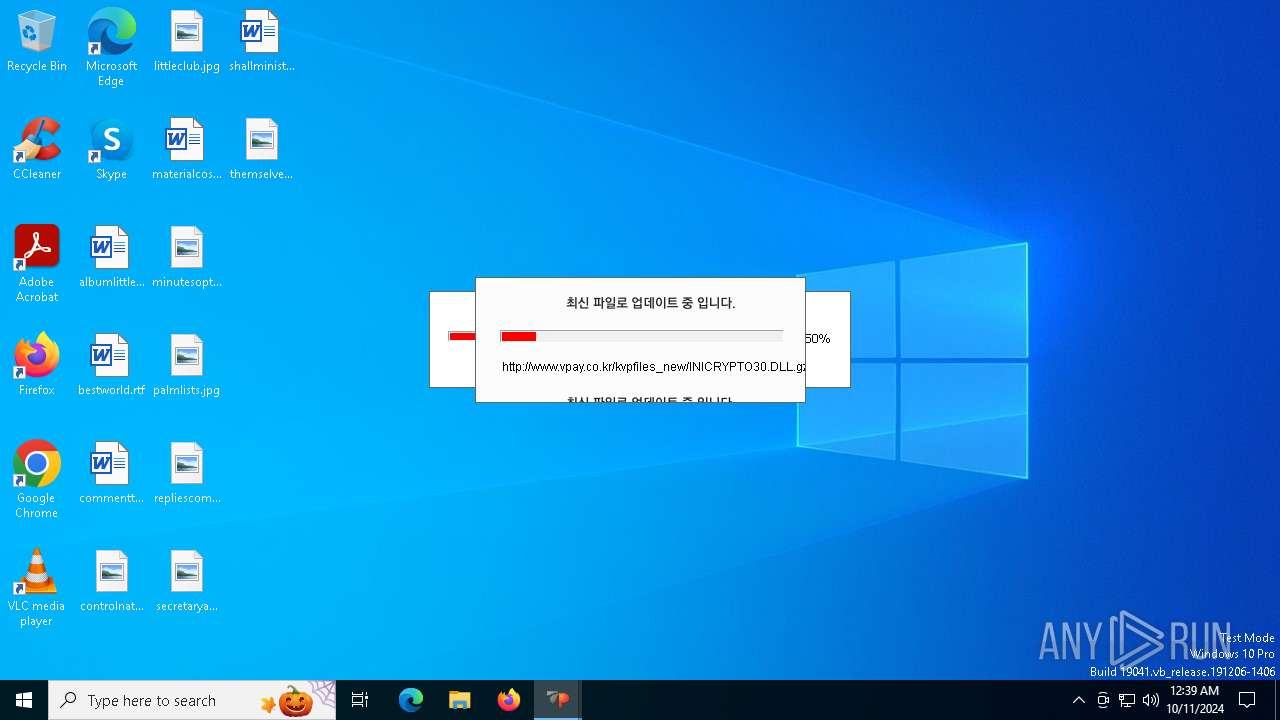
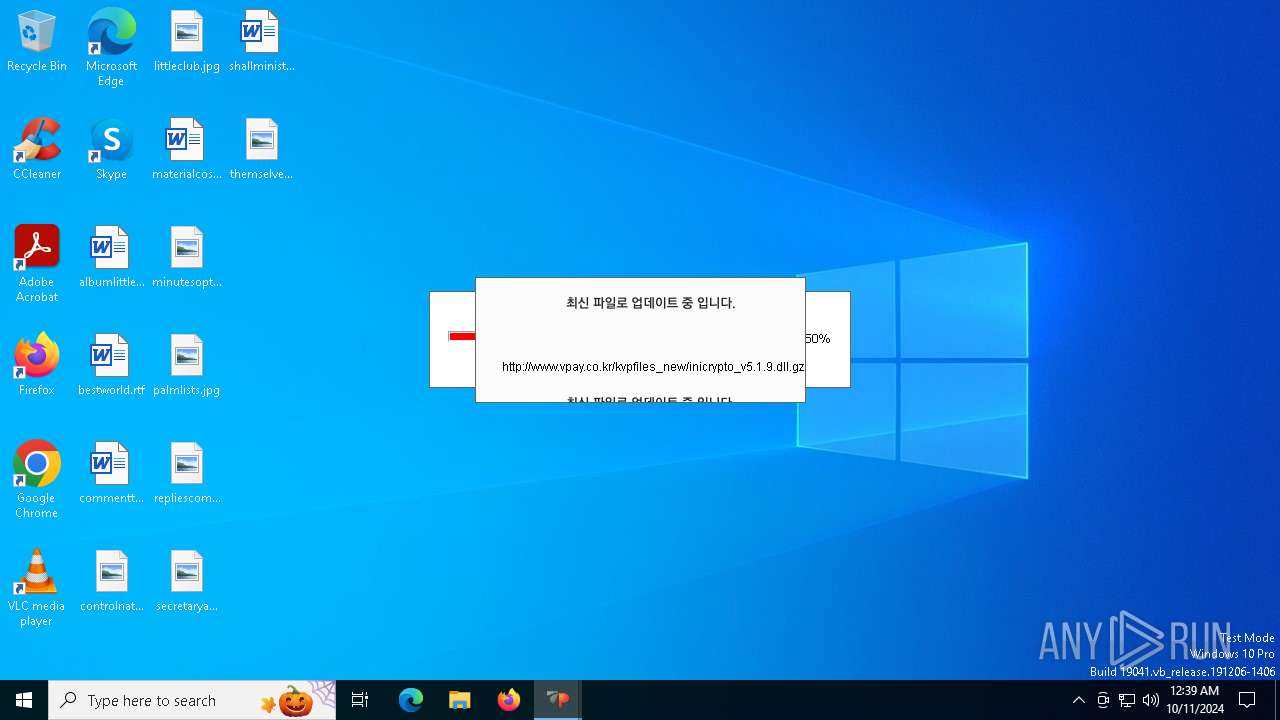
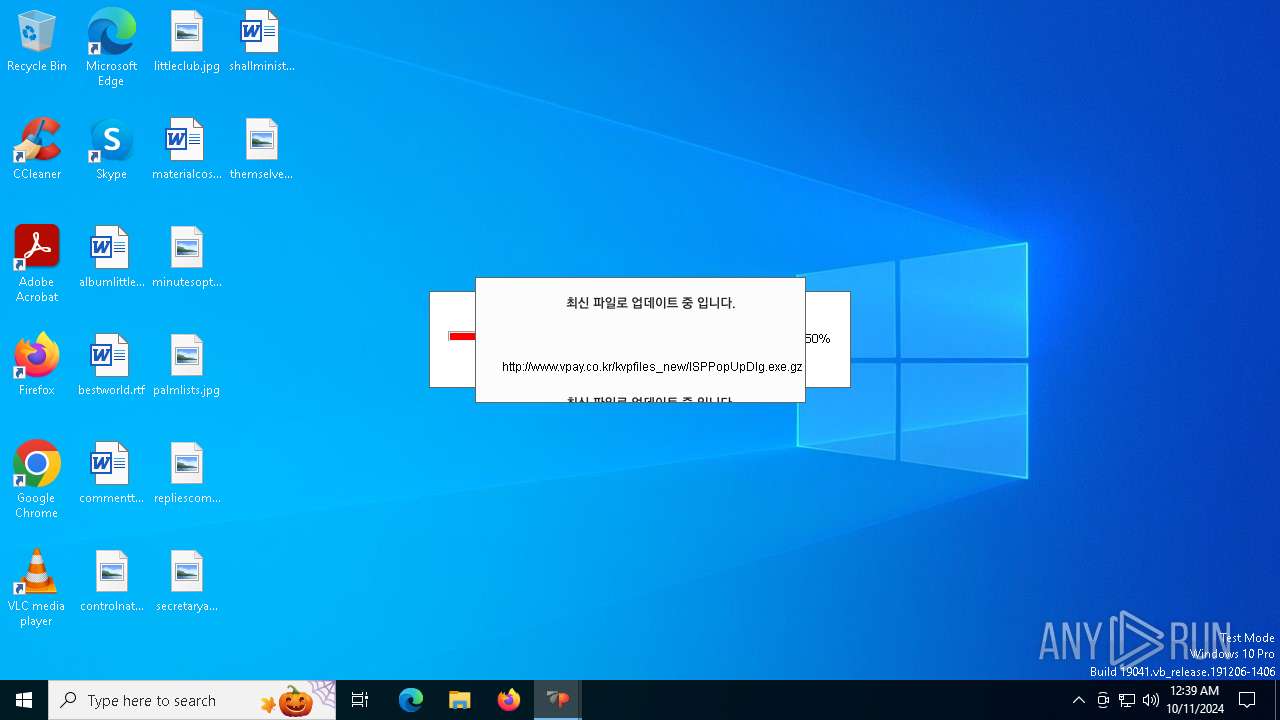
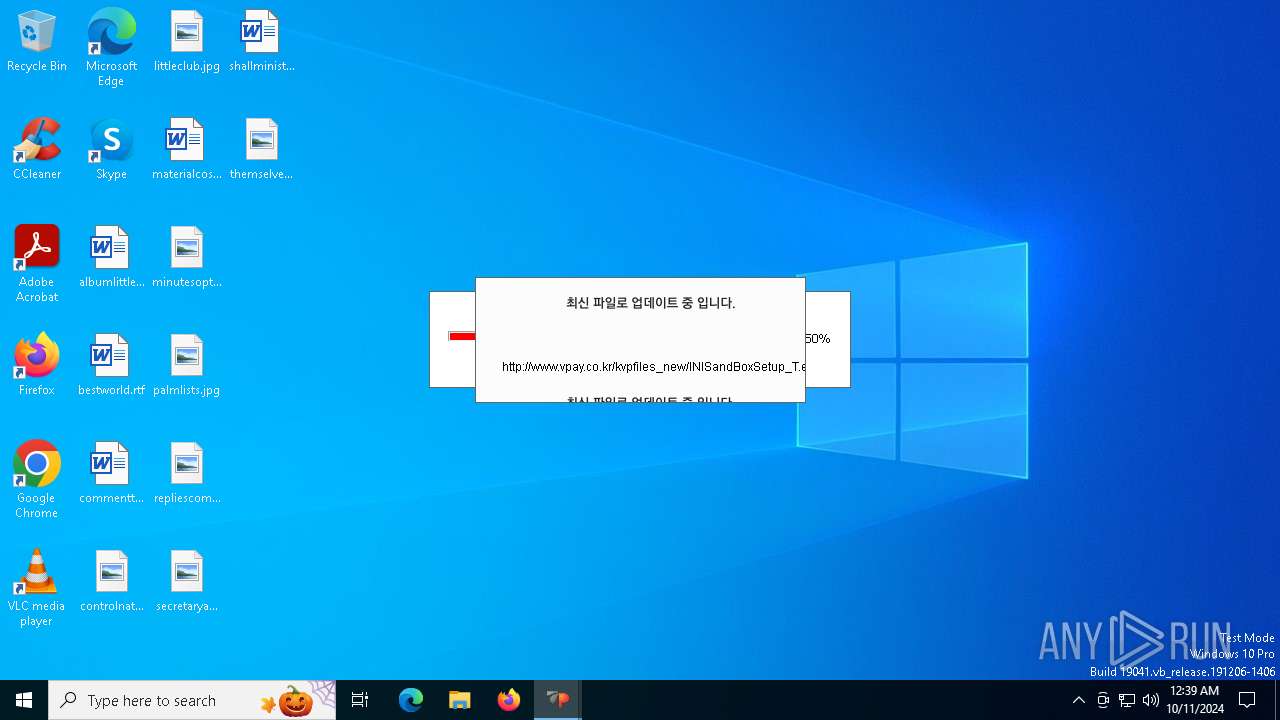
Process requests binary or script from the Internet
- VPWSSetup.exe (PID: 528)
INFO
Reads the computer name
- VPWSSetup_V2112.exe (PID: 3844)
- VPWSSetup.exe (PID: 528)
Checks supported languages
- VPWSSetup_V2112.exe (PID: 3844)
- VPWSSetup.exe (PID: 528)
Create files in a temporary directory
- VPWSSetup_V2112.exe (PID: 3844)
The process uses the downloaded file
- VPWSSetup_V2112.exe (PID: 3844)
Process checks computer location settings
- VPWSSetup_V2112.exe (PID: 3844)
Sends debugging messages
- VPWSSetup.exe (PID: 528)
Creates files in the program directory
- VPWSSetup.exe (PID: 528)
Checks proxy server information
- VPWSSetup.exe (PID: 528)
Reads the software policy settings
- VPWSSetup.exe (PID: 528)
Reads the machine GUID from the registry
- VPWSSetup.exe (PID: 528)
Creates files or folders in the user directory
- VPWSSetup.exe (PID: 528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:08:11 13:54:06+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 188928 |
| InitializedDataSize: | 102912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1cec9 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
134
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\VPWSSetup.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\VPWSSetup.exe | VPWSSetup_V2112.exe | ||||||||||||
User: admin Company: VP Inc. Integrity Level: HIGH Description: VPWalletSetup for payment Version: 2.1.1.2 Modules
| |||||||||||||||
| 884 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3844 | "C:\Users\admin\AppData\Local\Temp\VPWSSetup_V2112.exe" | C:\Users\admin\AppData\Local\Temp\VPWSSetup_V2112.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 5004 | "C:\Users\admin\AppData\Local\Temp\VPWSSetup_V2112.exe" | C:\Users\admin\AppData\Local\Temp\VPWSSetup_V2112.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6596 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 500
Read events
2 496
Write events
4
Delete events
0
Modification events
| (PID) Process: | (3844) VPWSSetup_V2112.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Program Files (x86)%VP |
Value: C:\Users\admin\AppData\Local\Temp\RarSFX0 | |||
| (PID) Process: | (528) VPWSSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (528) VPWSSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (528) VPWSSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
92
Suspicious files
56
Text files
16
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\VPWalletLauncherC.exe | executable | |
MD5:5C91763F6E9E541A0A343E58FA0820D4 | SHA256:15892F1F7EBA9DB72DE6EF6D2A9AFD9520BBBCF20631AA104B8202C6760E1ABF | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\bin\certutil.exe | executable | |
MD5:F8DA06687FB47CA2C355C38CA2766262 | SHA256:64AD18F4D9BEF01B86E39CA1E774DFA37DB46BC8267453C418DD7F723D6D014C | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\bin\freebl3.dll | executable | |
MD5:F474DD91BB12F230209EC3163CE7E6C4 | SHA256:F63B2CAB4B77AC63A1BECA66872A991E1F8233F2C513D42460DBF28C733B138C | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\bin\nssutil3.dll | executable | |
MD5:C19416E9CF9E571068CA14276C6E0620 | SHA256:BA9341807B42E90BB0380D51A83D3D6A0DE7D57B6820A8B0CBE5E36E978860FA | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\VPWSSetup.exe | executable | |
MD5:3B5F305A1CE21E4842063FA120ACFA35 | SHA256:C6B0B07C5A56A6C8074819F2A16E284C844223042C11B2AC240609EEAC04C91E | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\bin\plc4.dll | executable | |
MD5:88B4DF8D7D536A195F866B70C48ED534 | SHA256:09F01488A002915B8472A4E82ADB7A3E8CB43BD77DB347B0178EAE614F846A0A | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\bin\msvcr120.dll | executable | |
MD5:034CCADC1C073E4216E9466B720F9849 | SHA256:86E39B5995AF0E042FCDAA85FE2AEFD7C9DDC7AD65E6327BD5E7058BC3AB615F | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\bin\nspr4.dll | executable | |
MD5:BD0E897DBC2DCC0CF1287FFD7C734CF0 | SHA256:2D2096447B366D6640F2670EDB474AB208D8D85B5650DB5E80CC985D1189F911 | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\bin\nss3.dll | executable | |
MD5:54F3932864EED803BD1CB82DF43F0C76 | SHA256:96E068E6162A98D212B57C86B14FC539F1BBDCCD363F68EFD8CDFECC90C699D3 | |||
| 3844 | VPWSSetup_V2112.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\bin\nssdbm3.dll | executable | |
MD5:8CC6A31974A175A65D6C090FEED39F42 | SHA256:F64111FAA9966D7B7859C6467BEDBD64559284B049F55FFADC54DFC50A3A4264 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
78
DNS requests
26
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
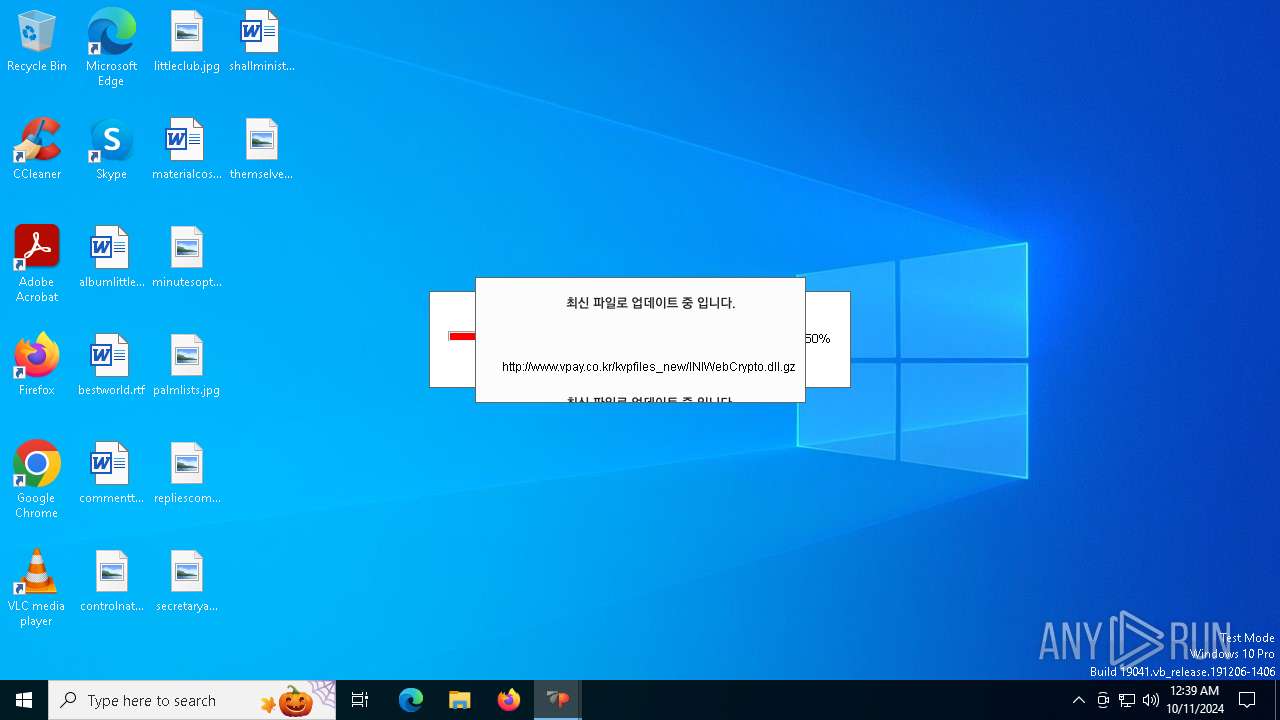
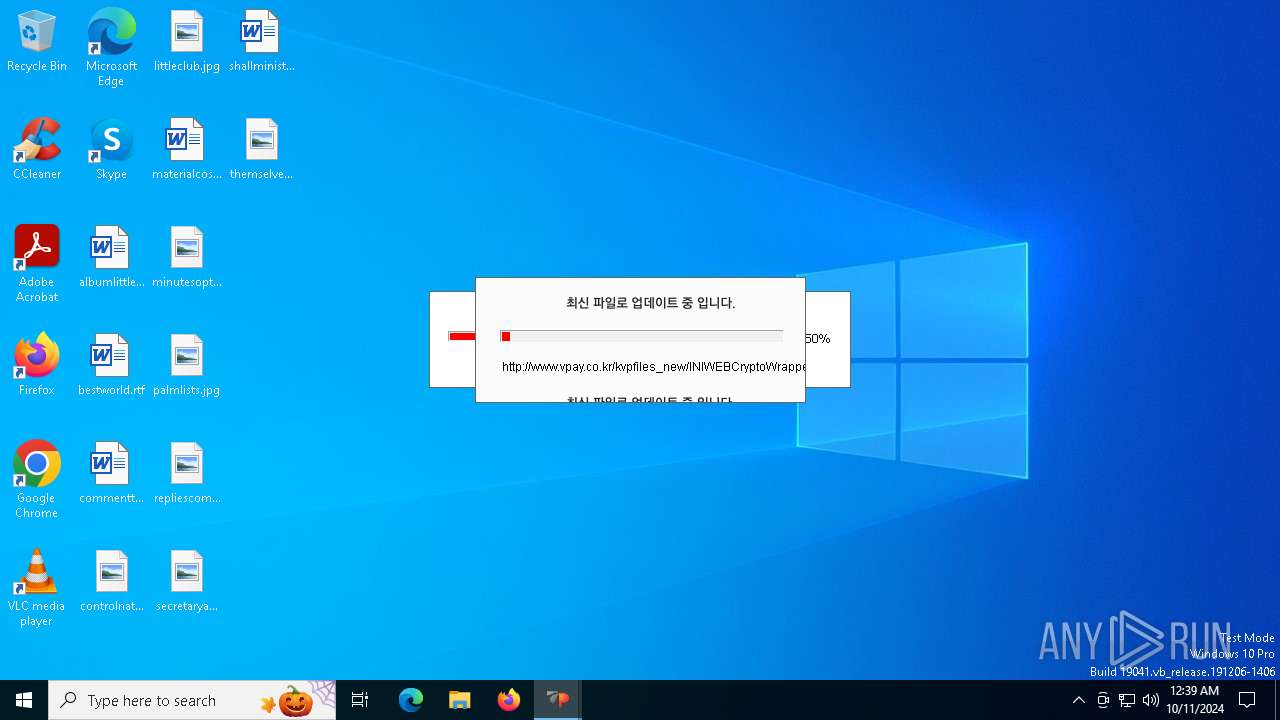
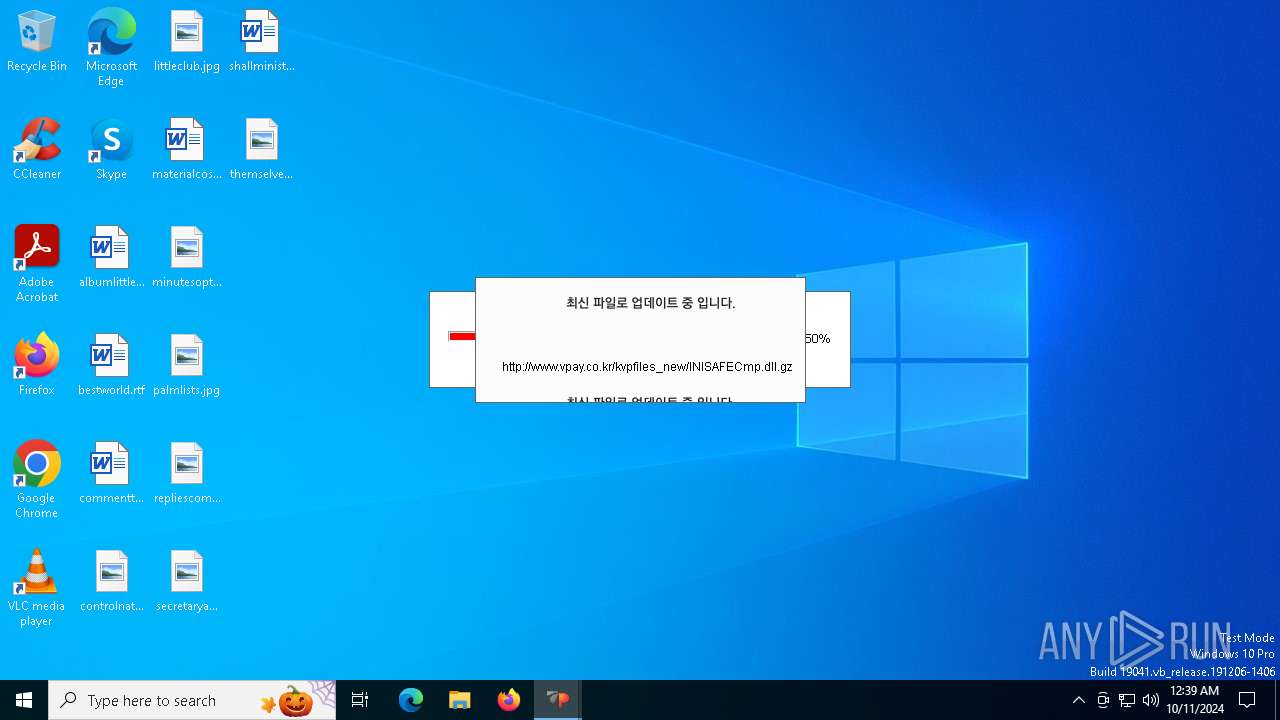
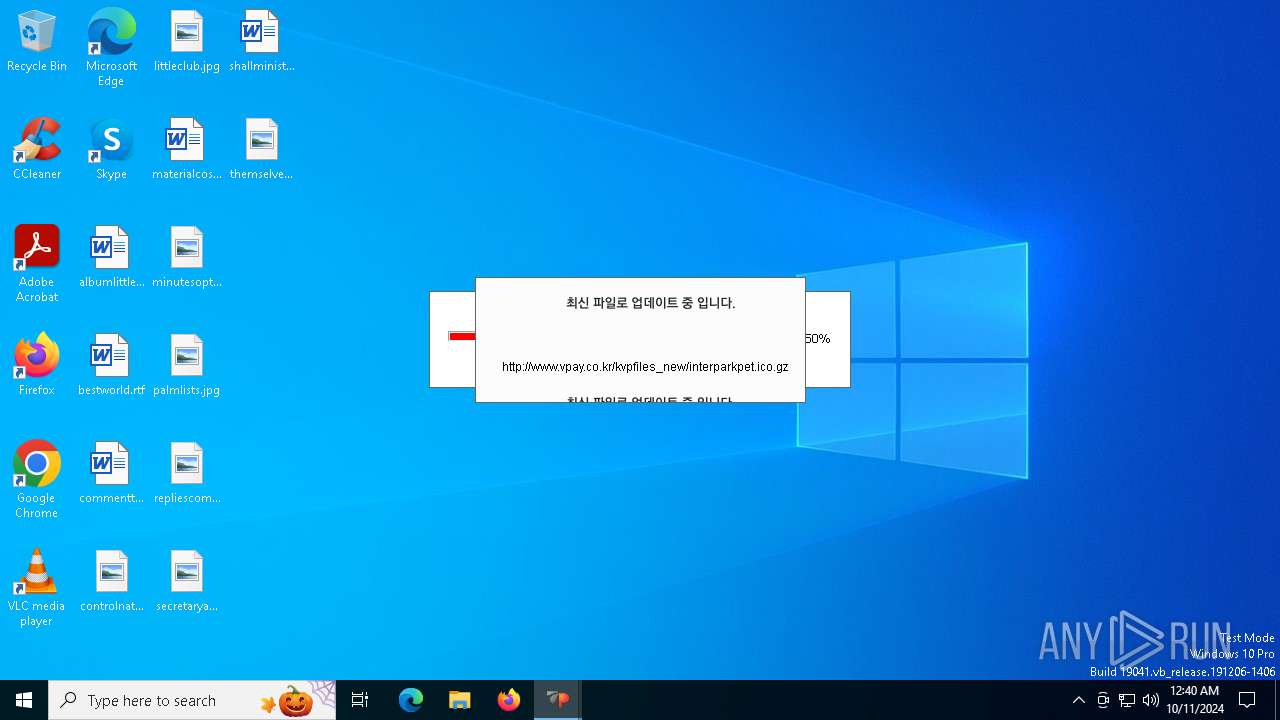
528 | VPWSSetup.exe | GET | — | 14.0.113.100:80 | http://www.vpay.co.kr/kvpfiles_new/KvpVcmd.dll.gz | unknown | — | — | whitelisted |
528 | VPWSSetup.exe | GET | 200 | 151.101.194.133:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | — | — | whitelisted |
528 | VPWSSetup.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDDOdcVWyWqbeuaWiuA%3D%3D | unknown | — | — | whitelisted |
528 | VPWSSetup.exe | GET | — | 14.0.113.100:80 | http://www.vpay.co.kr/kvpfiles_new/KvpVcmd.dll.gz | unknown | — | — | whitelisted |
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
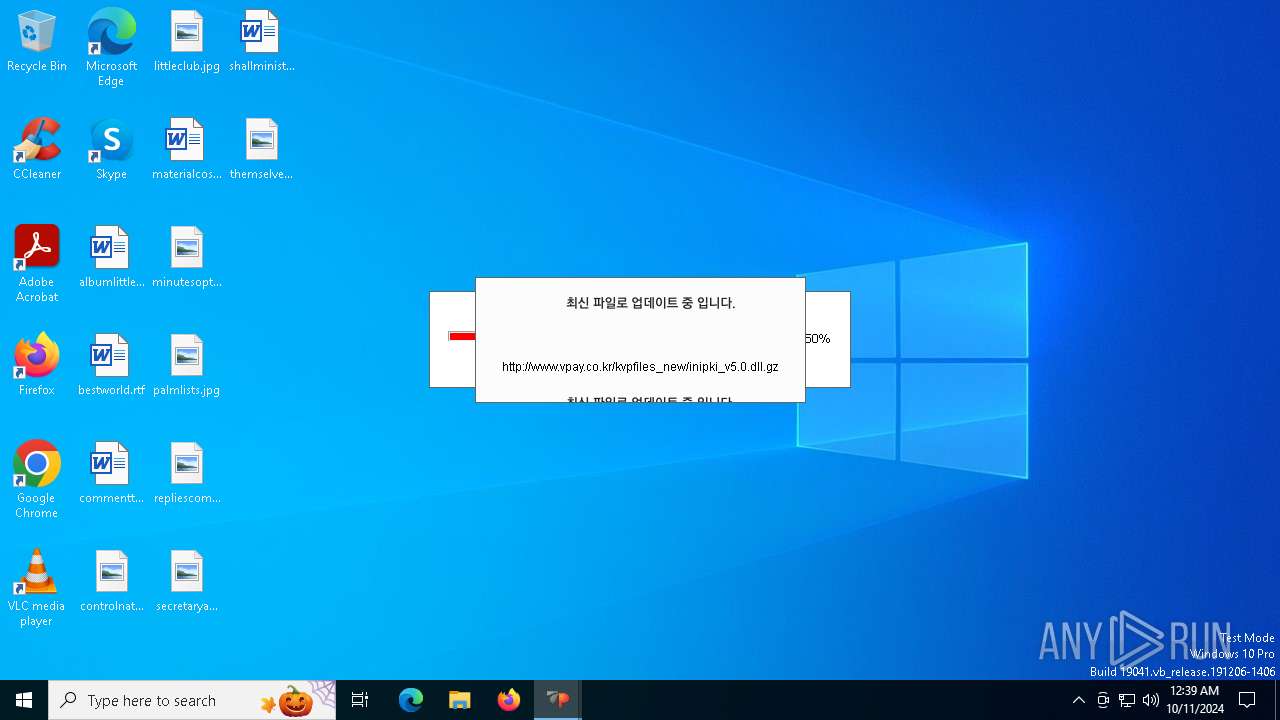
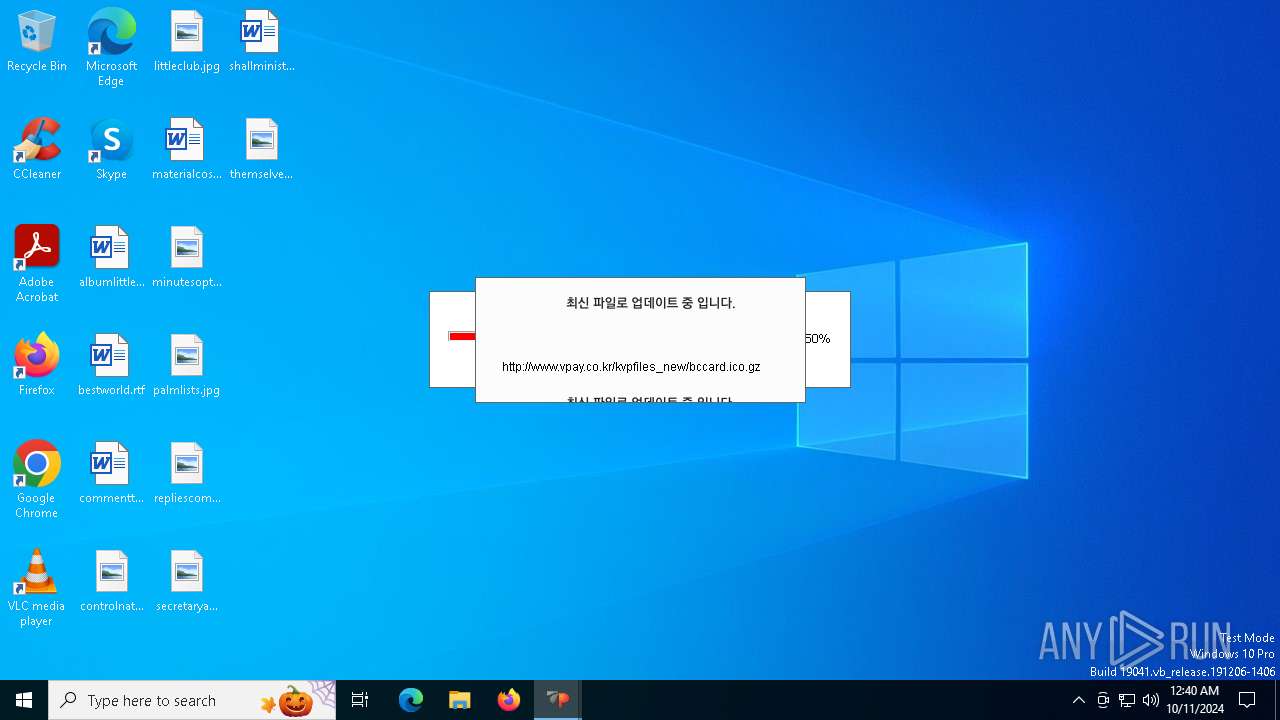
528 | VPWSSetup.exe | GET | — | 14.0.113.100:80 | http://www.vpay.co.kr/kvpfiles_new/ISP_crgen.dll.gz | unknown | — | — | whitelisted |
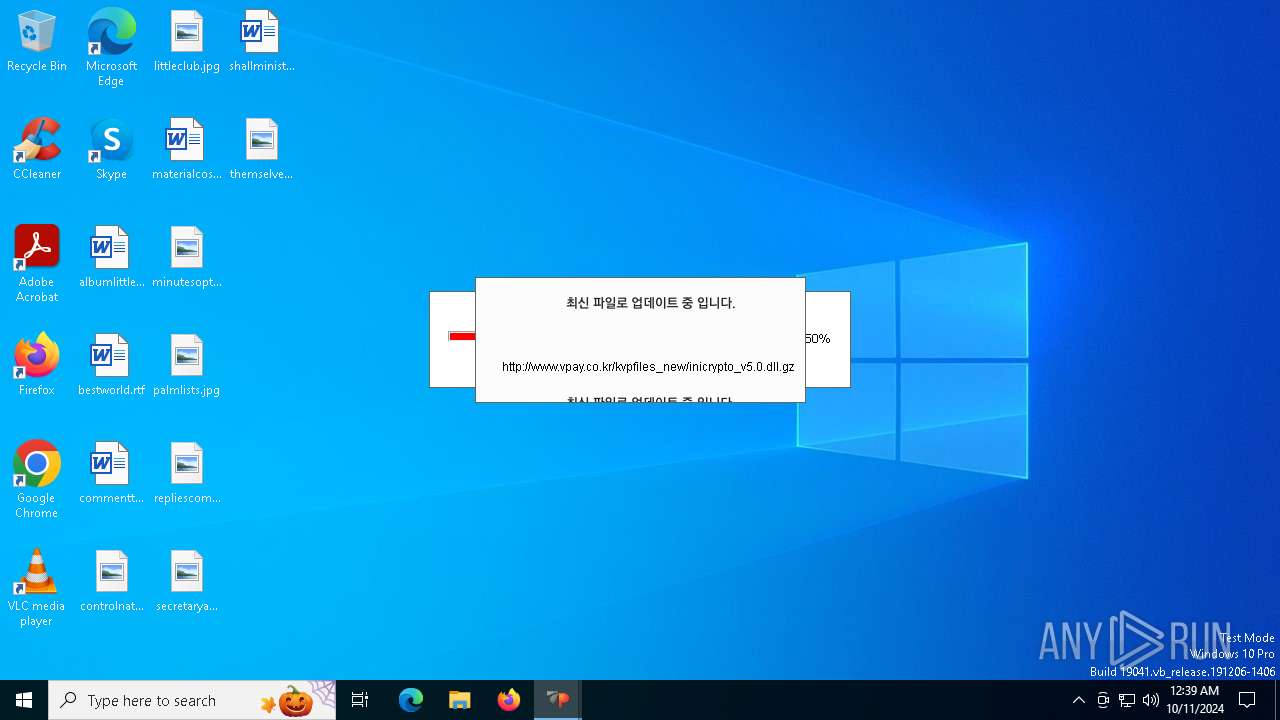
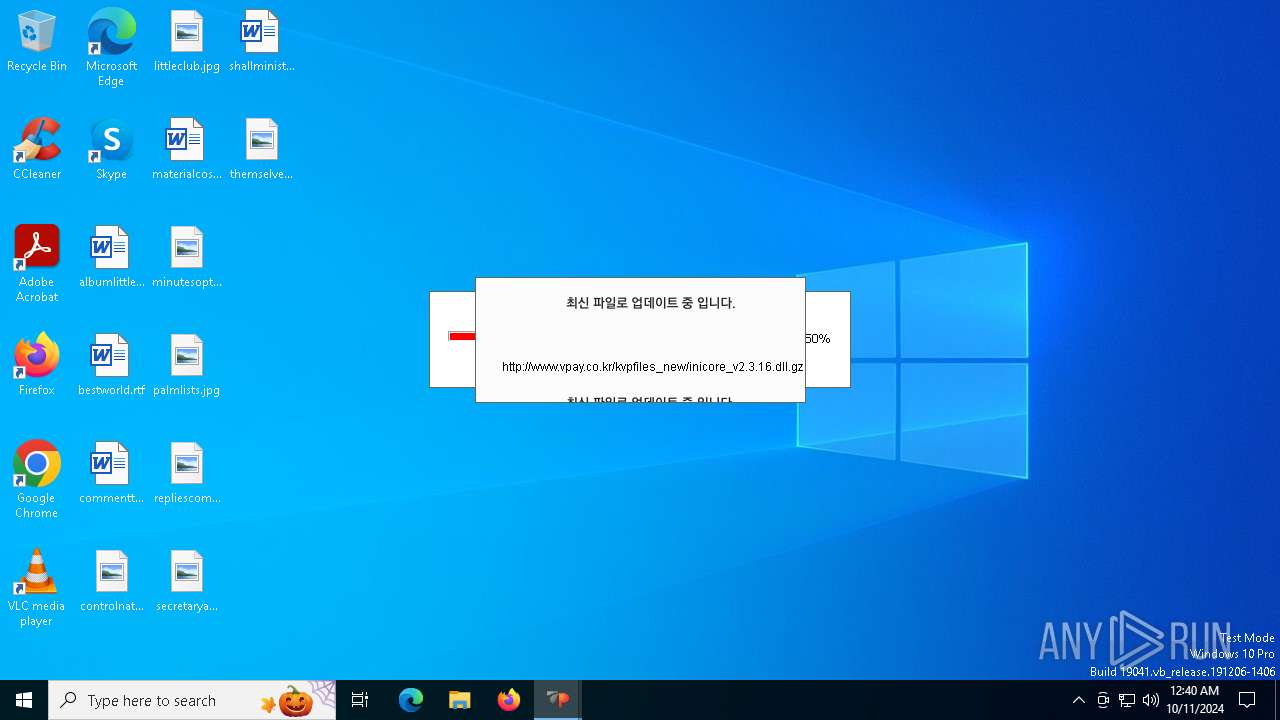
528 | VPWSSetup.exe | GET | 200 | 14.0.113.100:80 | http://www.vpay.co.kr/kvpfiles_new/ISP_INISafeNet.dll.gz | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4360 | SearchApp.exe | 184.86.251.22:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
528 | VPWSSetup.exe | 14.0.113.100:443 | www.vpay.co.kr | CDNetworks | KR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
www.vpay.co.kr |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
528 | VPWSSetup.exe | Potentially Bad Traffic | ET INFO Compressed Executable SZDD Compress.exe Format Over HTTP |
Process | Message |
|---|---|
VPWSSetup.exe | [VPWalletService] [6804] (TRAC) **** [Setup] Thread_InformDlg_Install Start
|
VPWSSetup.exe | [VPWalletService] [6804] (TRAC) **** [Setup] Thread_InformDlg_Install Step. 1
|
VPWSSetup.exe | [VPWalletService] [6804] (TRAC) **** [Setup] Thread_InformDlg_Install Step. 1 Check for and remove existing files.., OK
|
VPWSSetup.exe | [VPWalletService] [6804] (TRAC) **** [Setup] Thread_InformDlg_Install Step. 1 Check for and installation folder.., OK
|
VPWSSetup.exe | [VPWalletService] [6804] (INFO) 0[
|
VPWSSetup.exe | [VPWalletService] [6804] (INFO) 0[
|
VPWSSetup.exe | [VPWalletService] [6804] (INFO) 0[
|
VPWSSetup.exe | [VPWalletService] [6804] (INFO) 0[
|
VPWSSetup.exe | [VPWalletService] [6804] (TRAC) **** [Setup] Thread_InformDlg_Install Step. 3 Skip.., OK
|
VPWSSetup.exe | [VPWalletService] [6804] (TRAC) **** [Setup] Thread_InformDlg_Install Step. 4 Install files.., OK
|