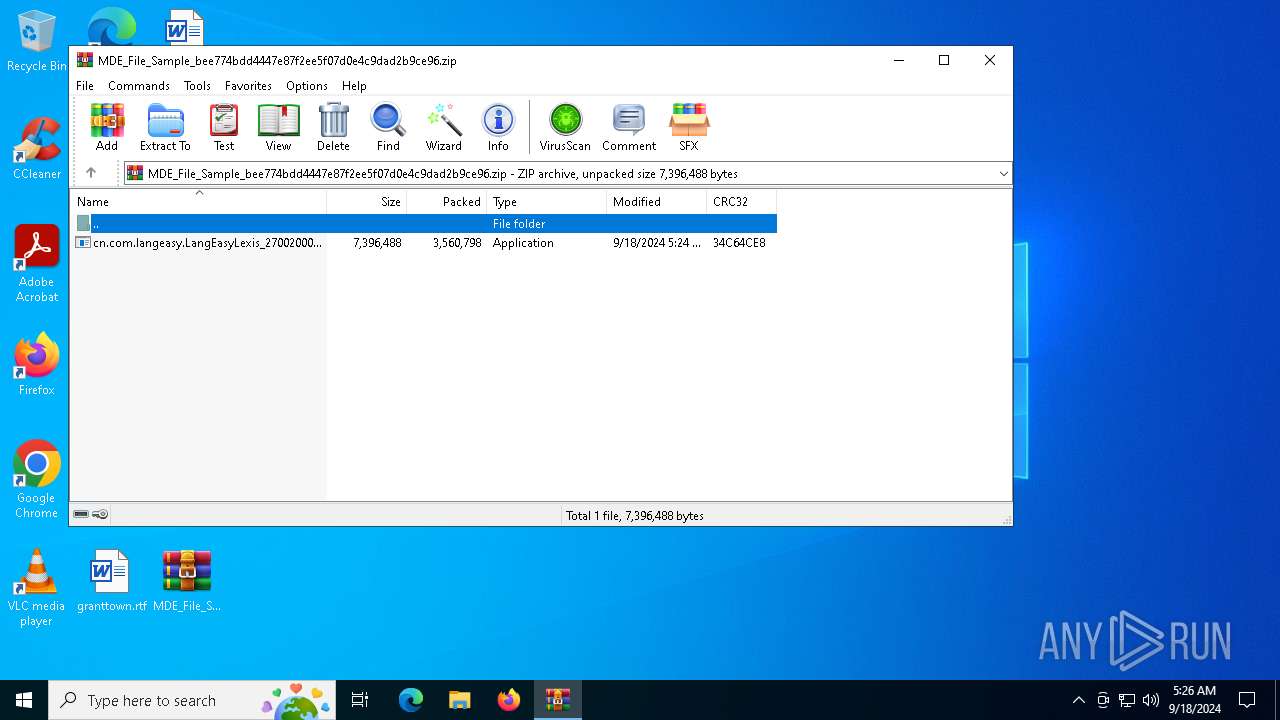
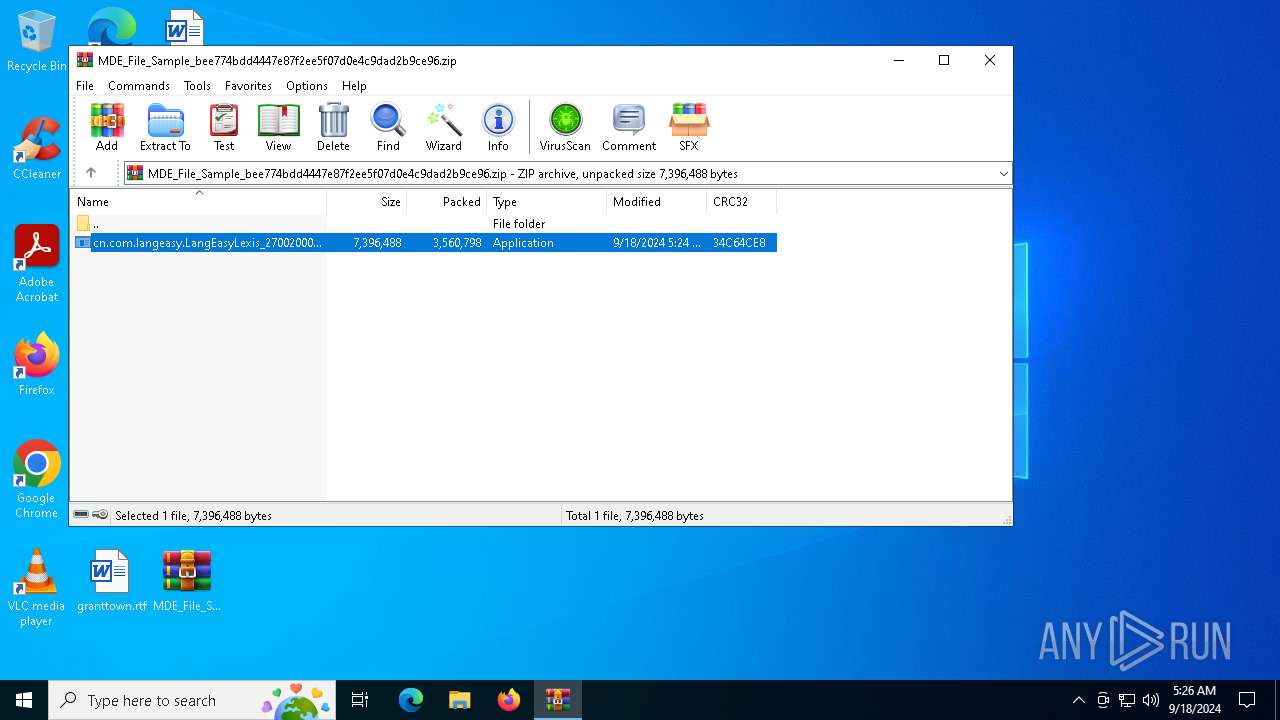
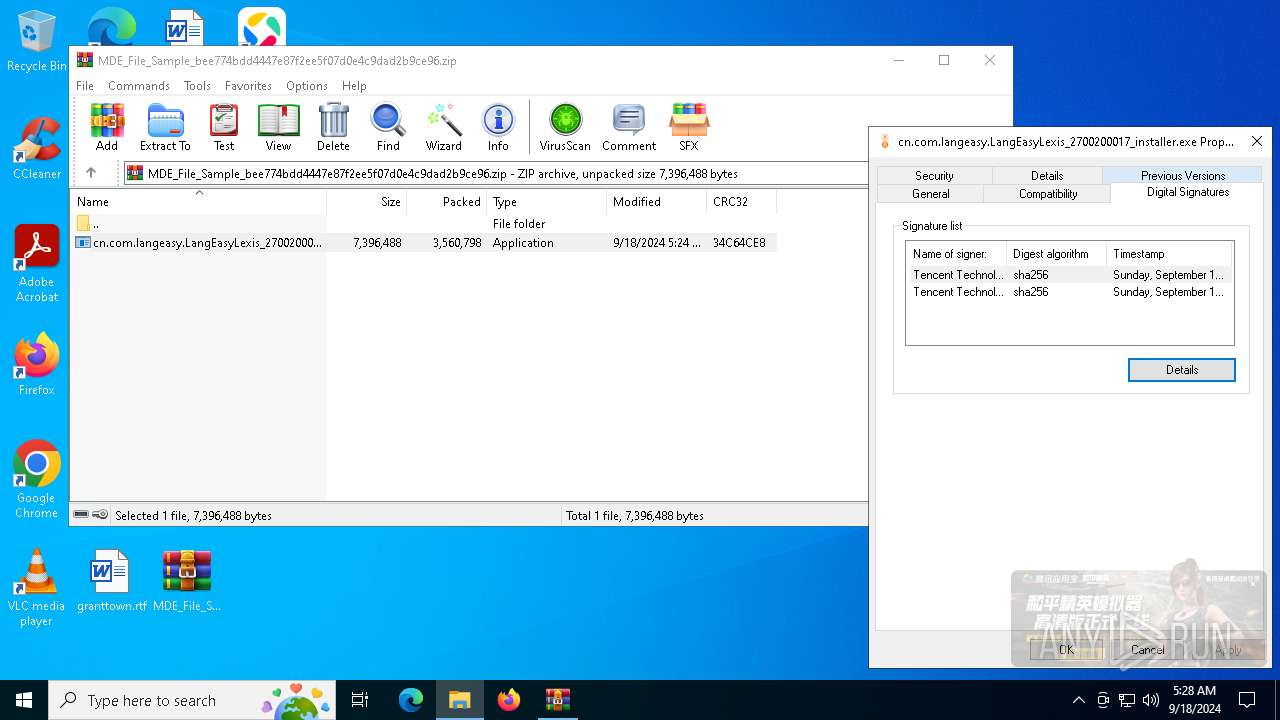
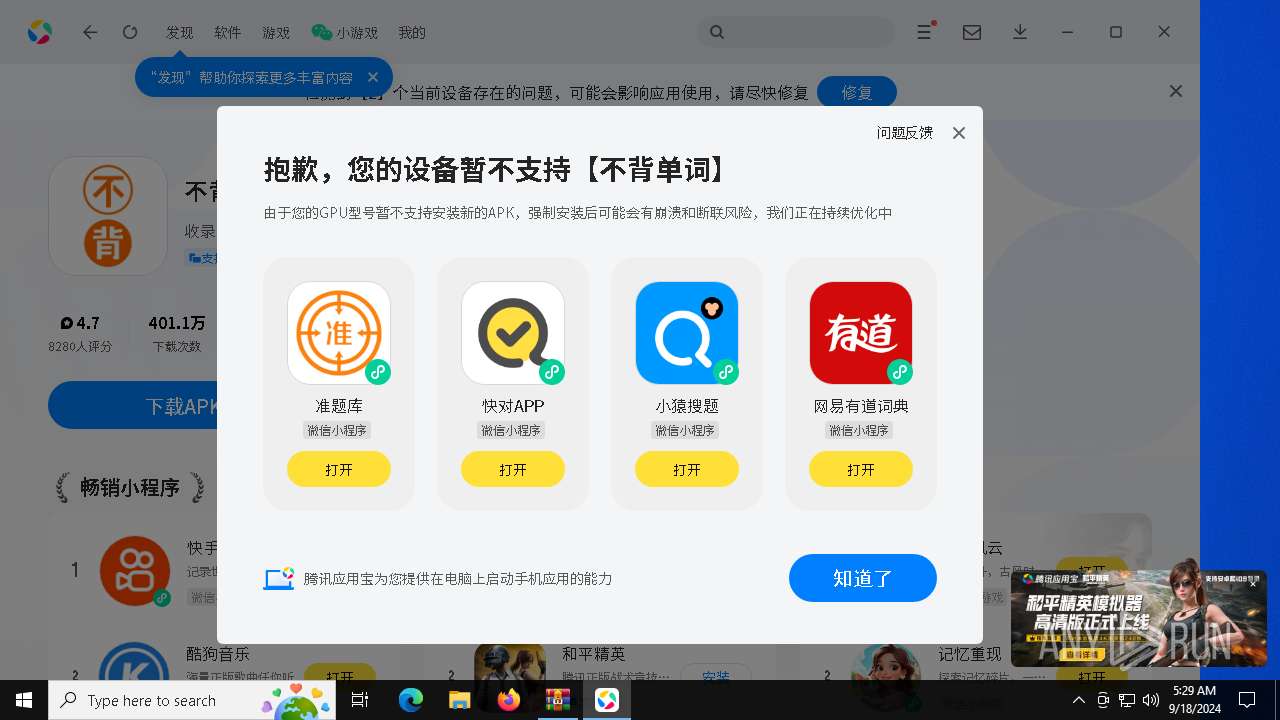
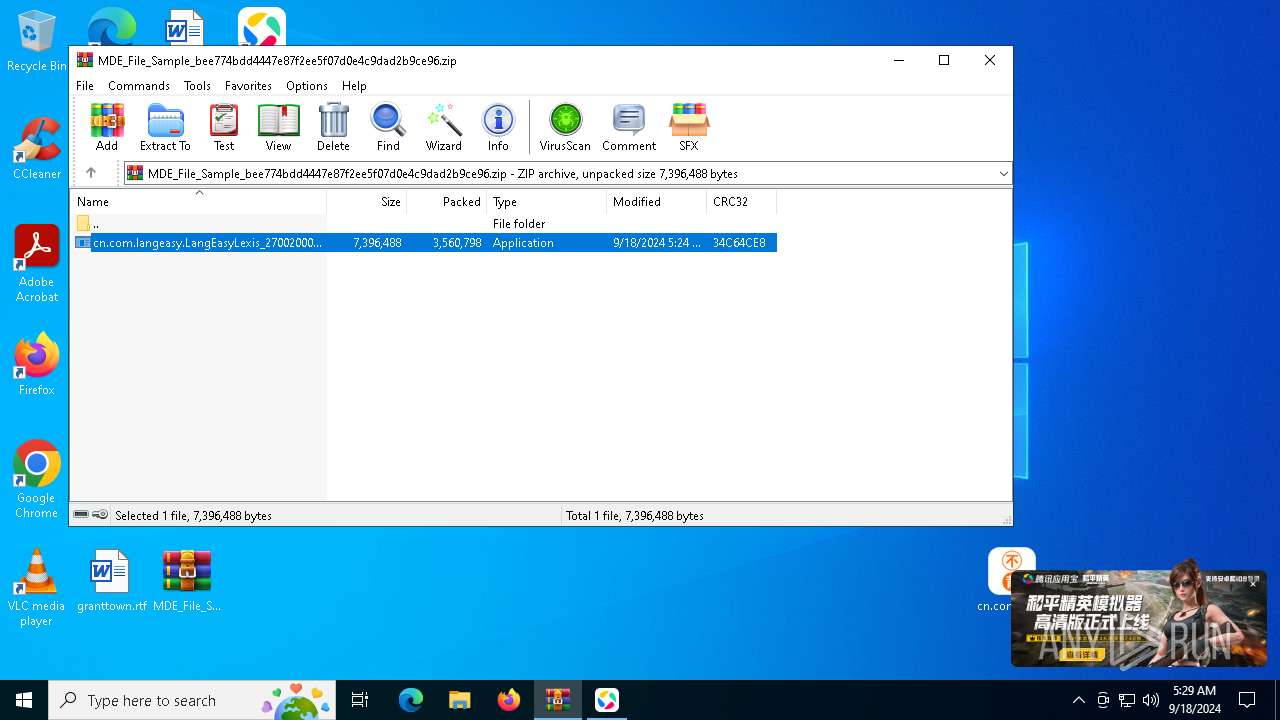
| File name: | MDE_File_Sample_bee774bdd4447e87f2ee5f07d0e4c9dad2b9ce96.zip |
| Full analysis: | https://app.any.run/tasks/bf1b07aa-b480-4981-9269-1b7071a1015a |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2024, 05:26:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 07B6DD6EED4043A6A63EE8798F8E96D2 |
| SHA1: | 08AA70736F390BCC265477A2CDE04517E0AB173C |
| SHA256: | 112772C8F05BFE3EFE2AAD9DC4AE37AB939322CA34A2ABE1B7AFC496077C2AFE |
| SSDEEP: | 98304:86Ir3LzyH1qK3jbErl1n0M+CQ6KLxzq5t/h4KMyGlG43XEcWjY9AR/ZOTk3VqMQw:6RT+K |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- cn.com.langeasy.LangEasyLexis_2700200017_installer.exe (PID: 1104)
- Setup.exe (PID: 4064)
Executable content was dropped or overwritten
- Setup.exe (PID: 4064)
- cn.com.langeasy.LangEasyLexis_2700200017_installer.exe (PID: 1104)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:09:18 05:24:46 |
| ZipCRC: | 0x34c64ce8 |
| ZipCompressedSize: | 3560798 |
| ZipUncompressedSize: | 7396488 |
| ZipFileName: | cn.com.langeasy.LangEasyLexis_2700200017_installer.exe |
Total processes
170
Monitored processes
41
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Tencent\Androws\Application\3.0.3595.0\crashpad_handler.exe" --no-rate-limit --database=C:\WINDOWS\TEMP\Tencent\Androws\ --metrics-dir=C:\WINDOWS\TEMP\Tencent\Androws\ --annotation=app_id=7ebaf51295 --annotation=app_key=3595ca0a-0ac2-42e7-988b-bb08e6767e24 --annotation=app_version=3.0.47.02 --annotation=build_id=3.0.3595.0 --annotation=bundle_id=com.tencent.androws --annotation=database=7ebaf51295 --annotation=format=minidump --annotation=is_need_attach_info=true --annotation=is_need_upload=true --annotation=is_pop_dialog=true --annotation=is_server_process=true --annotation=process_display_name=AndrowsSvr --annotation=process_name=AndrowsSvr --annotation=product=7ebaf51295 --annotation=version=3.0.47.02 --initial-client-data=0x3a4,0x3a0,0x3d8,0x3ac,0x3fc,0x7fffd1631dc0,0x7fffd1631d80,0x7fffd1631d90 | C:\Program Files\Tencent\Androws\Application\3.0.3595.0\crashpad_handler.exe | — | AndrowsSvr.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM | |||||||||||||||
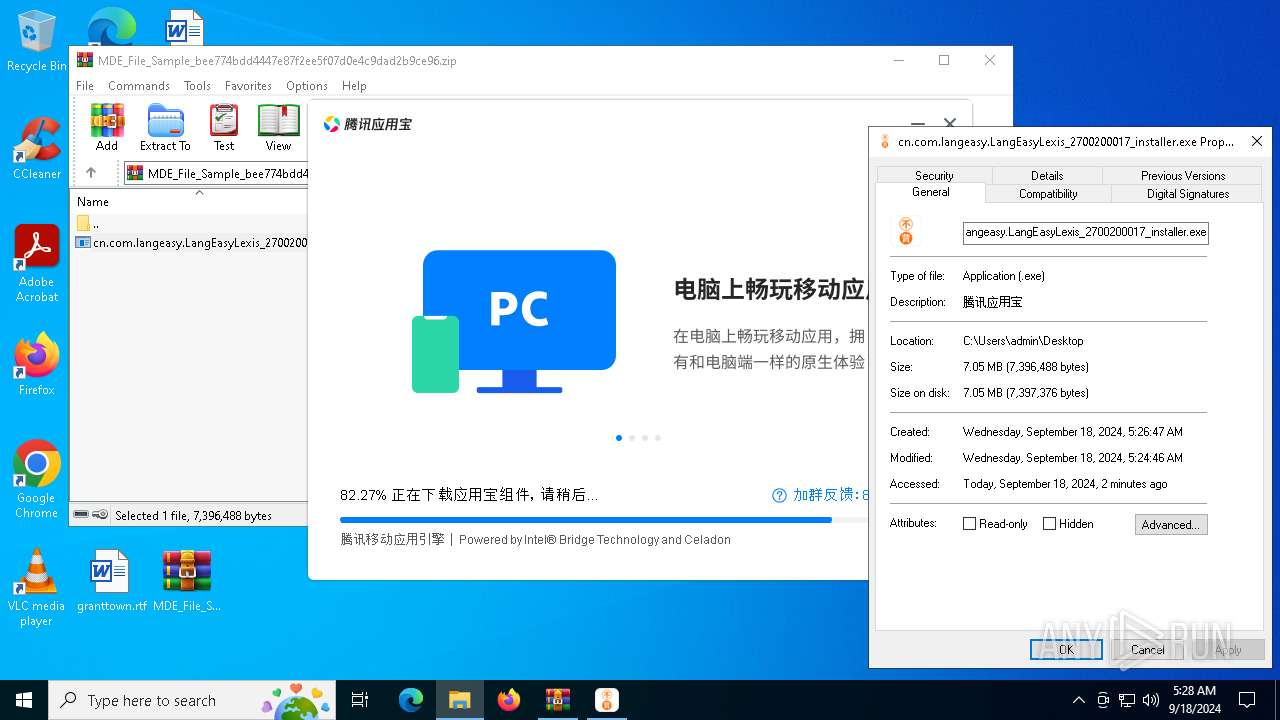
| 448 | "C:\Users\admin\Desktop\cn.com.langeasy.LangEasyLexis_2700200017_installer.exe" | C:\Users\admin\Desktop\cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | — | explorer.exe | |||||||||||
User: admin Company: Tencent Integrity Level: MEDIUM Description: 腾讯应用宝 Exit code: 3221226540 Version: 1.0.44809.0 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Tencent\Androws\Application\AndrowsLauncher.exe" --launch-proc-name "AndrowsAssistant.exe" --monitor-main_window-handle "524794" --monitor-process-id "7140" --monitor-process-name "AndrowsStore.exe" | C:\Program Files\Tencent\Androws\Application\AndrowsLauncher.exe | — | AndrowsStore.exe | |||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯应用宝 Exit code: 0 Version: 3.0.3595.0 | |||||||||||||||
| 936 | "C:\Program Files\Tencent\Androws\Application\3.0.3595.0\AndrowsAssistant.exe" --monitor-main_window-handle "524794" --monitor-process-id "7140" --monitor-process-name "AndrowsStore.exe" | C:\Program Files\Tencent\Androws\Application\3.0.3595.0\AndrowsAssistant.exe | — | AndrowsLauncher.exe | |||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯应用宝 Version: 3.0.3595.0 | |||||||||||||||
| 1044 | "C:\Program Files\Tencent\Androws\Application\3.0.3595.0\crashpad_handler.exe" --no-rate-limit --database=C:\Users\admin\AppData\Local\Temp\Tencent\Androws\ --metrics-dir=C:\Users\admin\AppData\Local\Temp\Tencent\Androws\ --annotation=app_id=7ebaf51295 --annotation=app_key=3595ca0a-0ac2-42e7-988b-bb08e6767e24 --annotation=app_version=3.0.47.02 --annotation=build_id=3.0.3595.0 --annotation=bundle_id=com.tencent.androws --annotation=database=7ebaf51295 --annotation=format=minidump --annotation=is_need_attach_info=true --annotation=is_need_upload=true --annotation=is_pop_dialog=true --annotation=is_server_process=false --annotation=process_display_name=AndrowsStore --annotation=process_name=AndrowsStore --annotation=product=7ebaf51295 --annotation=version=3.0.47.02 --initial-client-data=0x554,0x558,0x55c,0x550,0x594,0x7fffd1631dc0,0x7fffd1631d80,0x7fffd1631d90 | C:\Program Files\Tencent\Androws\Application\3.0.3595.0\crashpad_handler.exe | AndrowsStore.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1104 | "C:\Users\admin\Desktop\cn.com.langeasy.LangEasyLexis_2700200017_installer.exe" | C:\Users\admin\Desktop\cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | explorer.exe | ||||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯应用宝 Exit code: 0 Version: 1.0.44809.0 Modules
| |||||||||||||||
| 1356 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | opengl_checker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1372 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Tencent\Androws\Application\3.0.3595.0\AndrowsDlSvr.exe" --daemon --allow-overwrite=true --conf-path="C:\Program Files\Tencent\Androws\Application\3.0.3595.0\androws_dl_svr.cfg" --log="C:\Program Files\Tencent\Androws\Application\3.0.3595.0\logs\androws_dl_svr.log" --rpc-listen-port=49886 --rpc-secret=androws_1fd45f864ec7416a2567b4bb46214ef7 --stop-with-process=7140 | C:\Program Files\Tencent\Androws\Application\3.0.3595.0\AndrowsDlSvr.exe | — | AndrowsStore.exe | |||||||||||
User: admin Integrity Level: HIGH | |||||||||||||||
| 2844 | "C:\Windows\System32\dxdiag.exe" /t C:\Users\admin\AppData\Local\Temp\Tencent\Androws\AndrowsStore_dxdiag.log | C:\Windows\System32\dxdiag.exe | — | AndrowsStore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft DirectX Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 207
Read events
17 085
Write events
120
Delete events
2
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010012000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000001A000000000000006100640064006900740069006F006E0061006C0063006F006D006D0065007200630065002E006A00700067003E00200020000000130000000000000063006F0073007400730072006100740069006E0067002E007200740066003E002000200000000F00000000000000660061006E0073006F006D0065002E0070006E0067003E0020002000000011000000000000006700720061006E00740074006F0077006E002E007200740066003E002000200000001300000000000000680061007200640077006100720065006200610067002E007200740066003E002000200000001500000000000000690064006500610065006D0065007200670065006E00630079002E007200740066003E0020002000000010000000000000006900740068006F00740065006C0073002E0070006E0067003E00200020000000190000000000000070006100720074006900630075006C00610072006C007900730069007400650073002E007200740066003E00200020000000110000000000000070007500720070006F0073006500640065002E007200740066003E0020002000000040000000000000004D00440045005F00460069006C0065005F00530061006D0070006C0065005F0062006500650037003700340062006400640034003400340037006500380037006600320065006500350066003000370064003000650034006300390064006100640032006200390063006500390036002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001200000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000080410000A0401100 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010012000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000001A000000000000006100640064006900740069006F006E0061006C0063006F006D006D0065007200630065002E006A00700067003E00200020000000130000000000000063006F0073007400730072006100740069006E0067002E007200740066003E002000200000000F00000000000000660061006E0073006F006D0065002E0070006E0067003E0020002000000011000000000000006700720061006E00740074006F0077006E002E007200740066003E002000200000001300000000000000680061007200640077006100720065006200610067002E007200740066003E002000200000001500000000000000690064006500610065006D0065007200670065006E00630079002E007200740066003E0020002000000010000000000000006900740068006F00740065006C0073002E0070006E0067003E00200020000000190000000000000070006100720074006900630075006C00610072006C007900730069007400650073002E007200740066003E00200020000000110000000000000070007500720070006F0073006500640065002E007200740066003E0020002000000040000000000000004D00440045005F00460069006C0065005F00530061006D0070006C0065005F0062006500650037003700340062006400640034003400340037006500380037006600320065006500350066003000370064003000650034006300390064006100640032006200390063006500390036002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001200000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000000400000A0401100 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 8E64EA6600000000 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000003100360000000000 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000402FE |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MDE_File_Sample_bee774bdd4447e87f2ee5f07d0e4c9dad2b9ce96.zip | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6160) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
381
Suspicious files
664
Text files
446
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1104 | cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | C:\AndrowsData\Component\Androws.7z.teemo | — | |
MD5:— | SHA256:— | |||
| 4552 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:AB822F9327D686B6BD847A135B2165BB | SHA256:55F5259090661FAEDCF2BDC029C75C70A59E034C9AF82692AAA54F0D4550B8CF | |||
| 4552 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 4552 | explorer.exe | C:\Users\admin\Desktop\cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | executable | |
MD5:D4A8FF68817F419E10E501A6DB60F8BB | SHA256:89CD973CD6A8FCB1F9BCDCC2650E9F1815B9DF0349E0387A8F0AA5099AEFE73D | |||
| 1104 | cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | C:\Users\admin\AppData\Roaming\Tencent\beacon\GlobalMgr.db | text | |
MD5:B0741997B397B0A2BA15818C5DE66AF6 | SHA256:DA002F07EE8390FCA3D7B1749880260941A916D52F7652195C4B1D8DD89D80FE | |||
| 1104 | cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | C:\Users\admin\AppData\Roaming\Tencent\Androws\db\bc_0WIN0GIA035UNMF7_0e.db-journal | binary | |
MD5:78EF8601555C82B4C5FF469E8D88D9AB | SHA256:3E20DC25BD97BC8F6909EA4E8F49A03C0DA69CFE8F3190560038355646F709FB | |||
| 1104 | cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | C:\Users\admin\AppData\Roaming\Tencent\BeaconConfig\0WIN0GIA035UNMF7.ini | text | |
MD5:226393C3AF27D49BA4CC5FA947AE34FC | SHA256:8F93BEB4BDD17E1F72079D624BBF4F7970701479F1B5232E035A2D6971F3B33C | |||
| 1104 | cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | C:\androws_temp.txt | binary | |
MD5:0D5A9115CA3E62AAC00A5D6B68392C56 | SHA256:6F24BAE6C7B73ED650F4E9777D5420898356B3CB2E08DABB3EDB2253A655F9E6 | |||
| 1104 | cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | C:\Users\admin\AppData\Roaming\Tencent\Androws\db\OTable.db-journal | binary | |
MD5:D06CDC6B2DB0B05134FB2640990248EC | SHA256:6B73CB025E3631DE53F8DF2254E9F38B235DC66EC23DFEA31D7970C464F818DF | |||
| 6160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6160.1347\cn.com.langeasy.LangEasyLexis_2700200017_installer.exe | executable | |
MD5:D4A8FF68817F419E10E501A6DB60F8BB | SHA256:89CD973CD6A8FCB1F9BCDCC2650E9F1815B9DF0349E0387A8F0AA5099AEFE73D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
226
DNS requests
51
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1964 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4600 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4600 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4552 | explorer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4552 | explorer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA3a8v5R87LpTLtpWkpRdPw%3D | unknown | — | — | whitelisted |
4552 | explorer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
4064 | Setup.exe | GET | 200 | 163.181.92.230:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbJNRrm8KxusAb7DCqnMkE%3D | unknown | — | — | whitelisted |
4064 | Setup.exe | GET | 200 | 163.181.92.230:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQhnxEBNL9LgIhfSsTcHsrTt204QgQURNnISjOO01KNp5KUYR%2BayKW37MsCEAKpOeapfqJKkZUvKymOa1k%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7028 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3904 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1964 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1964 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
yybadaccess.3g.qq.com |
| whitelisted |
oth.eve.mdt.qq.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
conf.syzs.qq.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Tencent Cloud Storage Domain in DNS Lookup (myqcloud .com) |
— | — | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
Process | Message |
|---|---|
AndrowsSvr.exe | 09-18 05:28:53.510 [5144.4708](info)[app.launch] [boot::Initialize] (initialize.cpp:103) [Msg]: "C:\Program Files\Tencent\Androws\Application\3.0.3595.0\AndrowsSvr.exe" |
AndrowsSvr.exe | 09-18 05:28:53.510 [5144.4708](info)[app.androwsservice] [WaitForExploreReady] (uac_start.cc:229) [Msg]: Waiting for explore... |
AndrowsSvr.exe | 09-18 05:28:53.526 [5144.2548](info)[app.androwsservice] [service::Initialize::::operator()] (androws_service.cpp:210) [Msg]: Starting ServiceMain... |
AndrowsSvr.exe | 09-18 05:28:53.526 [5144.4708](info)[app.androwsservice] [WaitForExploreReady] (uac_start.cc:239) [Msg]: Waiting for explore done. |
AndrowsSvr.exe | 09-18 05:28:53.526 [5144.6048](info)[app.androwsservice] [service::ServiceMain] (androws_service.cpp:158) [Msg]: [Enter][argc]: 1 |
AndrowsSvr.exe | 09-18 05:28:53.526 [5144.6048](info)[app.androwsservice] [service::ServiceMain] (androws_service.cpp:186) [Msg]: Service Starting... |
AndrowsSvr.exe | 09-18 05:28:53.635 [5144.4708](warning)[default] [unknown] (:0) [Msg]: QObject: Cannot create children for a parent that is in a different thread.
(Parent is CLoginService(0x7ff6cb5ec810), parent's thread is QThread(0x26a19e41550), current thread is QThread(0x26a19dc62f0) |
AndrowsSvr.exe | 09-18 05:28:53.635 [5144.4708](info)[app.clogin] [CLoginService::Initialize] (clogin_service.cc:145) [Msg]: enter. |
AndrowsSvr.exe | 09-18 05:28:55.416 [5144.4708](info)[app.clogin] [CLoginSwitchChecker::FetchSwitch] (clogin_switch_checker.h:177) [Msg]: minVersion: ("0", "0", "0", "0") , mainVersion: ("3", "0", "47", "02") , enable: true |
AndrowsSvr.exe | 09-18 05:28:55.416 [5144.4708](info)[app.clogin] [CLoginSwitchChecker::FetchSwitch] (clogin_switch_checker.h:123) [Msg]: request androws config: "{\"ret_code\":0,\"ret_msg\":\"ok\",\"config\":{\"app_id\":\"cb12b9e8-4af6-496f-8d30-00df31201d4a\",\"items\":[{\"group\":\"com.tencent.androws\",\"version\":\"\",\"event_type\":0,\"key_values\":[{\"key\":\"appconfigjson\",\"value\":\"{\\\"auto_fullscreen\\\":false,\\\"function_config\\\":{\\\"titlebar_config\\\":{\\\"items\\\":[101,108,205,208]},\\\"topbar_config\\\":{\\\"items\\\":[205,207,206,208,203,202,204,201]}},\\\"global_max_notification_count\\\":5,\\\"max_notification_count\\\":1,\\\"media_mini_window\\\":false,\\\"media_tray\\\":false,\\\"report_notification\\\":false,\\\"tp\\\":false}\"},{\"key\":\"configfile\",\"value\":\"{\\\"AppRunningWhiteLists\\\":[\\\"com.tencent.mobileqq\\\",\\\"com.tencent.mm\\\",\\\"com.sina.weibo\\\",\\\"com.ss.android.ugc.aweme\\\",\\\"com.antutu.benchmark.full.lite\\\",\\\"com.android.chrome\\\",\\\"com.quark.browser\\\",\\\"org.mozilla.firefox\\\",\\\"com.cat.readall\\\",\\\"com.heytap.htms\\\",\\\"org.chromium.webview_shell\\\"],\\\"CopyAnrFile\\\":true,\\\"DefaultGrantedPermission\\\":[\\\"android.permExterission.READ_EXTERNAL_STORAGE\\\",\\\"android.permission.POST_NOTIFICATIONS\\\",\\\"android.permission.MANAGE_EXTERNAL_STORAGE\\\"],\\\"IntentActionBlackList\\\":[\\\"android.media.action.IMAGE_CAPTURE\\\"],\\\"alllowRecordTopLog\\\":true,\\\"allowAospReport\\\":true,\\\"allowNewDisplayClosed\\\":true,\\\"display\\\":\\\"hdmi\\\",\\\"dns\\\":[\\\"114.114.114.114\\\",\\\"119.29.29.29\\\"],\\\"enableDelayDestroyDisplay\\\":true,\\\"enableDisplayReparent\\\":false,\\\"enableDropEvent\\\":\\\"com.ss.android.ugc.aweme\\\",\\\"forceStartInput\\\":[\\\"com.ea.game.pvzfree_row\\\",\\\"cn.com.langeasy.LangEasyLexis\\\"],\\\"hookWxForMiniProgramWhiteList\\\":[\\\"com.fenbi.android.servant\\\",\\\"com.ss.android.ugc.aweme\\\",\\\"com.phoenix.read\\\",\\\"com.moonshot.kimichat\\\",\\\"com.dz.hmjc\\\",\\\"com.larus.nova\\\",\\\"me.yidui\\\"],\\\"hookWxForMiniProgramWhiteListV45\\\":[\\\"com.ss.android.article.video\\\",\\\"tv.danmaku.bili\\\",\\\"com.tencent.qqlive\\\",\\\"com.tencent.news\\\",\\\"com.smile.gifmaker\\\",\\\"com.kuaishou.nebula\\\"],\\\"isDefaultGranted\\\":false,\\\"isHookMiniProgramJumpWhileWxInstalled\\\":false,\\\"janks_app_config\\\":\\\"com.imgo.pad\\\",\\\"mockWxBlackPage45\\\":[\\\"com.tencent.qqlive.modules.vb.loginservice.WXFastEntryActivity\\\",\\\"com.yxcorp.login.userlogin.activity.pad.PhoneLoginActivityTablet\\\",\\\"com.smile.gifmaker.wxapi.WXPayEntryActivity\\\",\\\"com.yxcorp.plugin.activity.login.WeChatSSOActivity\\\",\\\"com.yxcorp.plugin.activity.login.pad.WeChatSSOActivityTablet\\\",\\\" com.kuaishou.merchant.transaction.purchase.dynamic.MerchantPurchaseV2Activity\\\",\\\"com.tencent.news.login.module.LoginActivity\\\",\\\"com.kuaishou.merchant.transaction.detail.contentdetail.MerchantContentDetailActivity\\\",\\\"com.ss.android.ugc.aweme.account.business.login.DYLoginActivity\\\",\\\"com.babycloud.hanju.ui.activity.HanjuHomeActivity\\\"],\\\"observer_max_subdir_count\\\":50,\\\"observers_root_dirs\\\":[\\\"DCIM\\\",\\\"Download\\\",\\\"Pictures\\\",\\\"????????\\\"],\\\"permissionAppBlackList\\\":{\\\"test.permission\\\":[\\\"com.test.xxxxx\\\"]},\\\"permissionAppWhiteList\\\":{\\\"test.permission\\\":[\\\"com.test.xxxxx\\\"]},\\\"split_screen_background_url\\\":\\\"https://static.pc.yyb.qq.com/wupload/xy/yyb_management_system/aRdgyNhP.png\\\",\\\"switch_list\\\":[true,true,true,true,true,false,false]}\"},{\"key\":\"globalconfig\",\"value\":\"{\\\"user_machine_state_config\\\":{\\\"update_interval_ms\\\":20000,\\\"user_in_use_last_input_sec\\\":20},\\\"feature_toggle\\\":{\\\"update_graphic_driver\\\":true,\\\"file_transfer\\\":true,\\\"android_pagecache_limit\\\":true,\\\"android_pagecache_limit_hdd\\\":false,\\\"android_pagecache_limit_percent\\\":12,\\\"android_pagecache_limit_percent_upgrade\\\":16,\\\"android_pagecache_limit_flowctl\\\":\\\"80 1842 6\\\",\\\"android_pagecache_low_mem\\\":2048,\\\"cl |