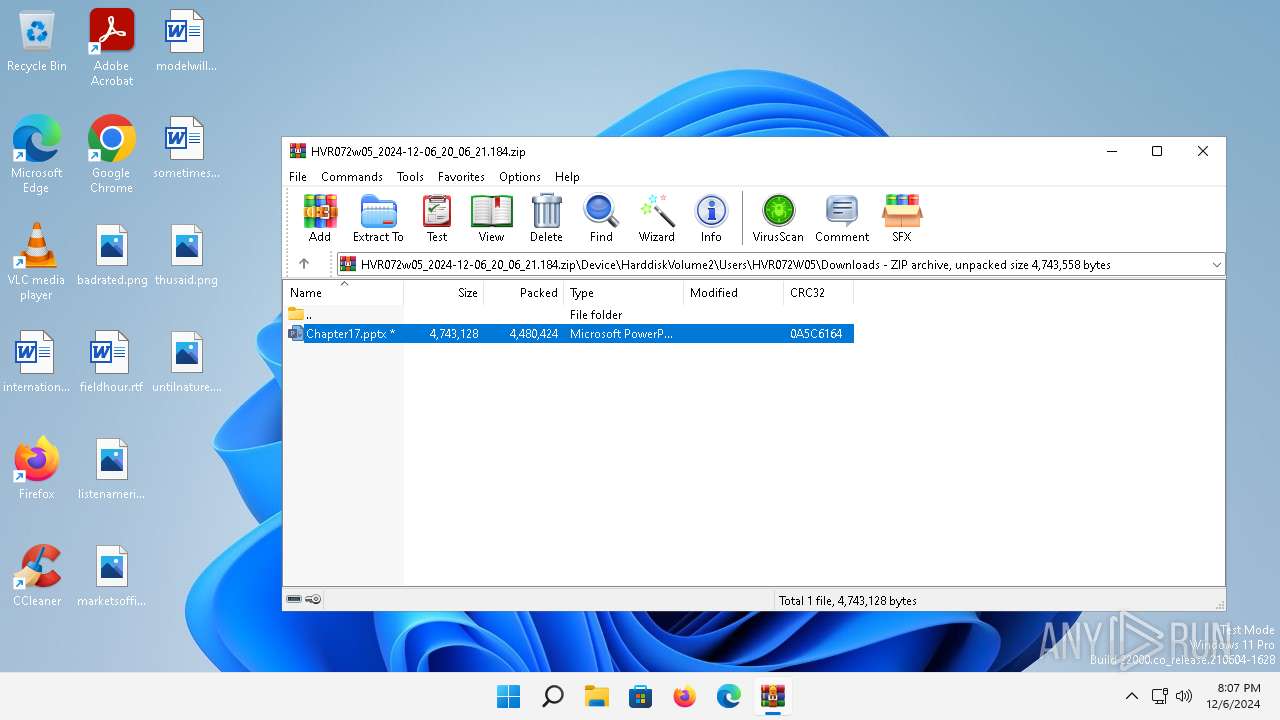
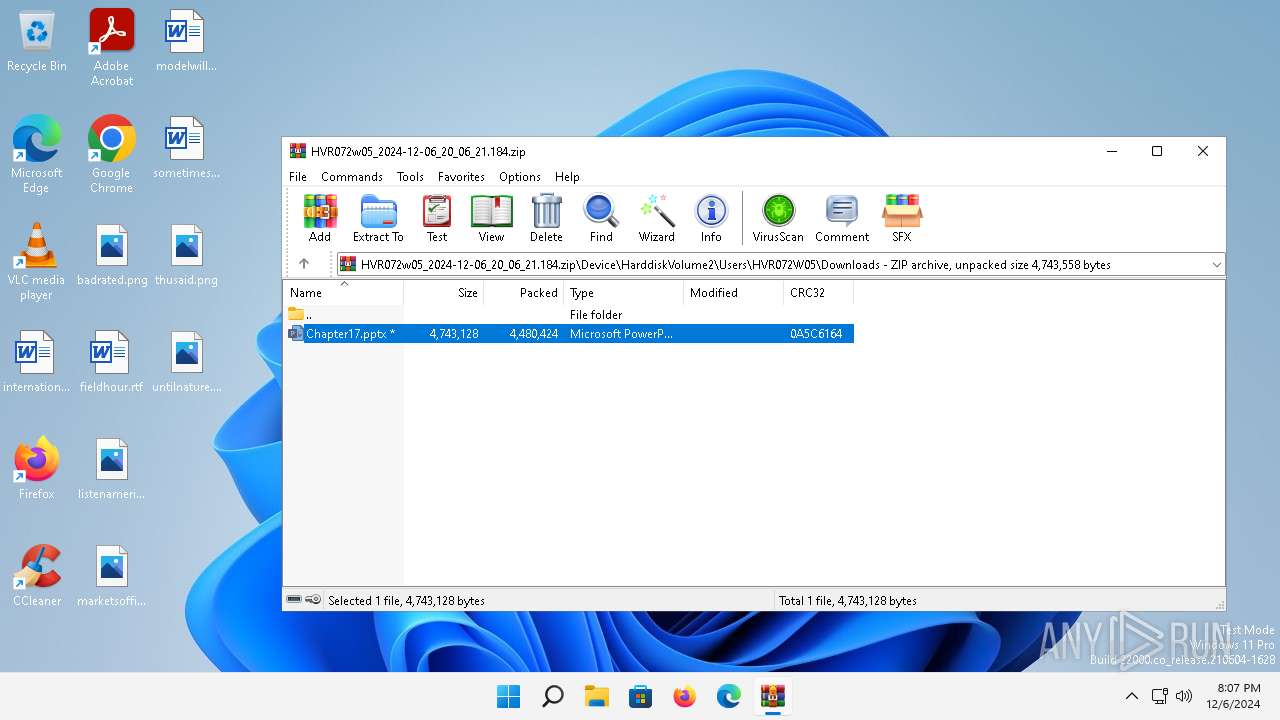
| File name: | HVR072w05_2024-12-06_20_06_21.184.zip |
| Full analysis: | https://app.any.run/tasks/04f67a7d-9768-4bdb-a598-56448646e4fc |
| Verdict: | No threats detected |
| Analysis date: | December 06, 2024, 20:06:59 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | EF23FBEA0186EFC459132AB2F5E9C7B9 |
| SHA1: | F8FC8573DF5B2DE3382D4705E610BA8BDDA99F0E |
| SHA256: | 1125BAECA539C3CB5D00027F857578C0237D97A9166C9FB96313F4180195E6AA |
| SSDEEP: | 98304:mfYhlEVvjcsXquBgTNlyZqsjIqqpUauPCKCMtR3KZpWKJYtdGqcHkcdJ36of3MHz:yzLhOu |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6192)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6192)
- POWERPNT.EXE (PID: 5516)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x0a5c6164 |
| ZipCompressedSize: | 4480424 |
| ZipUncompressedSize: | 4743128 |
| ZipFileName: | Device/HarddiskVolume2/Users/HVR072W05/Downloads/Chapter17.pptx |
Total processes
128
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1840 | "C:\Program Files\Microsoft Office\root\vfs\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "3B4B1370-0427-4C1F-983F-169E361C2721" "A721C341-C815-4343-9FC7-04FB03AFE4D7" "5516" "C:\Program Files\Microsoft Office\Root\Office16\POWERPNT.EXE" | C:\Program Files\Microsoft Office\root\vfs\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.14.4.0 Modules
| |||||||||||||||
| 5516 | "C:\Program Files\Microsoft Office\Root\Office16\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\Rar$DIb6192.44256\Chapter17.pptx" /ou "" | C:\Program Files\Microsoft Office\root\Office16\POWERPNT.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Version: 16.0.16626.20134 Modules
| |||||||||||||||
| 6192 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\HVR072w05_2024-12-06_20_06_21.184.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
15 837
Read events
15 641
Write events
186
Delete events
10
Modification events
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HVR072w05_2024-12-06_20_06_21.184.zip | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
0
Suspicious files
31
Text files
933
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\powerpnt.exe_Rules\rule100069v1.xml | xml | |
MD5:8279DE7A54DC506ED68199AC880C2920 | SHA256:40AD004C81F69364A2017FD3B758DC4C7834BC47A4A1340BED54594AF13F5B58 | |||
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\powerpnt.exe_Rules\rule100042v2.xml | xml | |
MD5:414277D4E3F104F55B935AB02A9BA9BF | SHA256:B8F1C0D81E44F9FEAB83DC2749B7807121F9BF8AB6AE82C01F8077FC05CA3FE1 | |||
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\powerpnt.exe_Rules\rule100075v1.xml | xml | |
MD5:6E76DCB19FB44EA1E65014E0CE218AB0 | SHA256:735879C44400699786304B87916667E37F35A3B26331C41B2366FEA88033B070 | |||
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\powerpnt.exe_Rules\rule100074v0.xml | xml | |
MD5:B5F555AC798495BD8A6B4E254745EDA0 | SHA256:1C79426930C54765CB7B121361D58839DDDBCED8F37502FAB16903274414AB21 | |||
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\powerpnt.exe_Rules\rule100068v2.xml | xml | |
MD5:B9B2CA56A048BDBFE74315BAC8FEFAF0 | SHA256:3C4A4929450C661680E8B674867368D76A71AA0A5FE6B1541E0CAB2EAECC2F2D | |||
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\powerpnt.exe_Rules\rule100071v0.xml | xml | |
MD5:3DF0BABC8132291994D448B40582DB90 | SHA256:6FB9BDDDA6B632428391FAFE9CE78D58CD0986B6571D8BB4C9691496070F3F19 | |||
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\powerpnt.exe_Rules\rule100070v0.xml | xml | |
MD5:D6DAF9F991EB87EB13BE13E79B869750 | SHA256:4CD12BB7EED5FE69ACC9E7A1EE29515CAEE4C453AB088F765ACB304DC882227C | |||
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:231DA7E6DBCA23228A658B15DDBA703F | SHA256:866A4BDA4969544C1682BDE0EE79BD2A39F51FF4B86F862292FD3C2DFC93E486 | |||
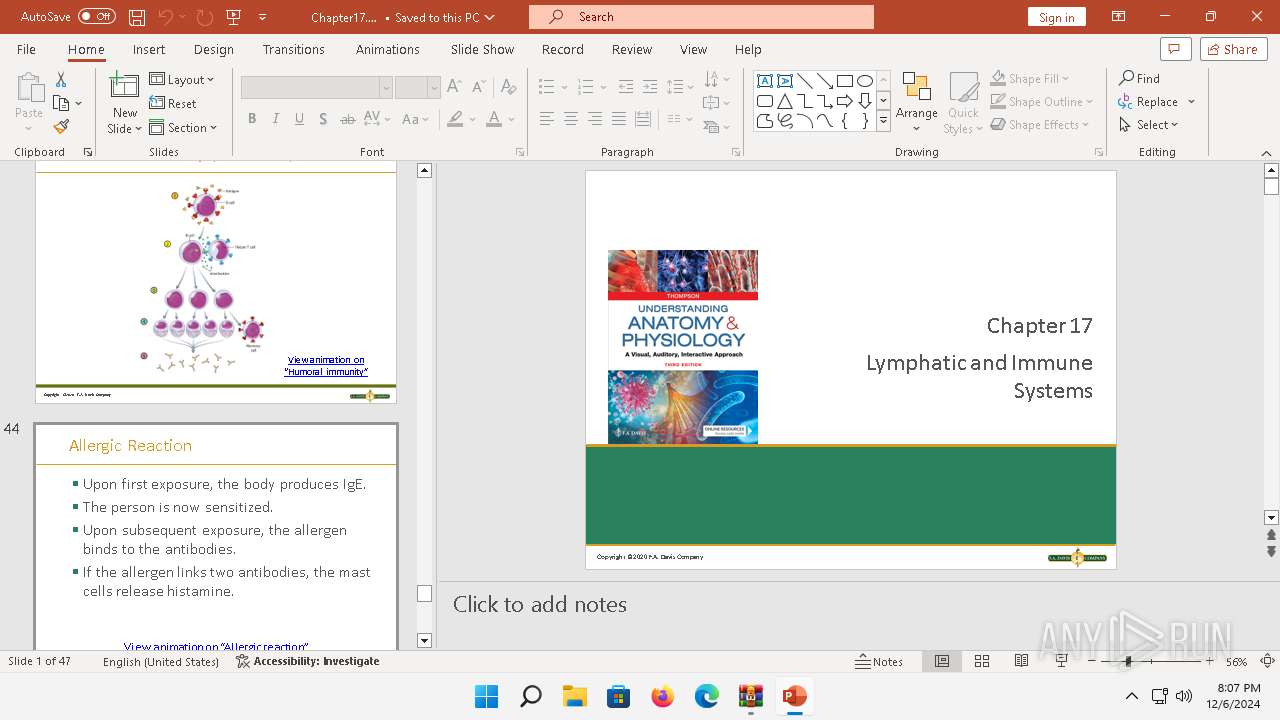
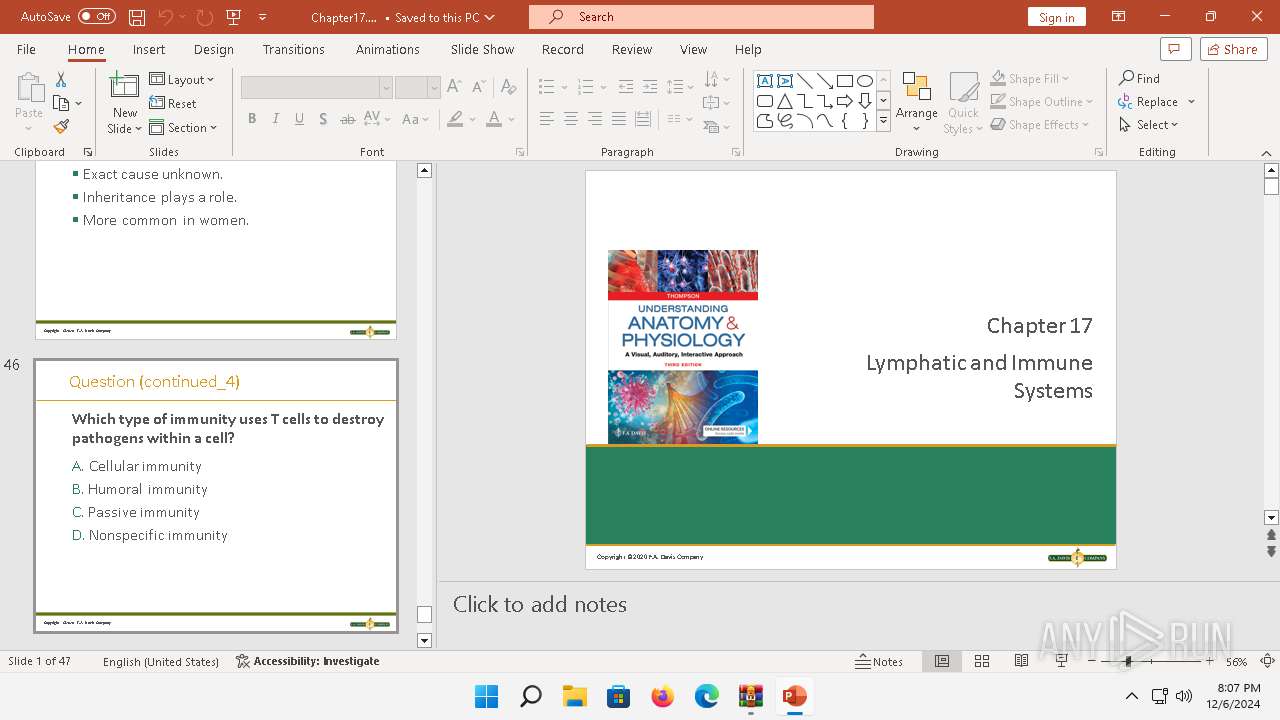
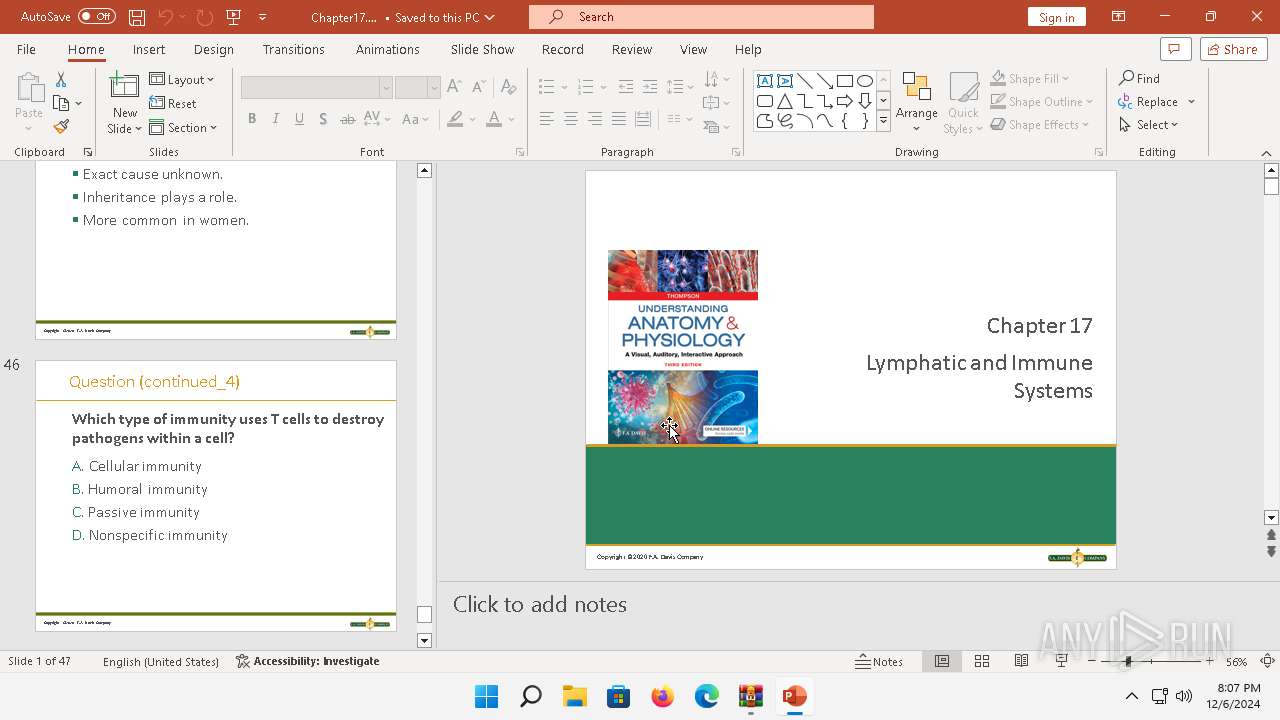
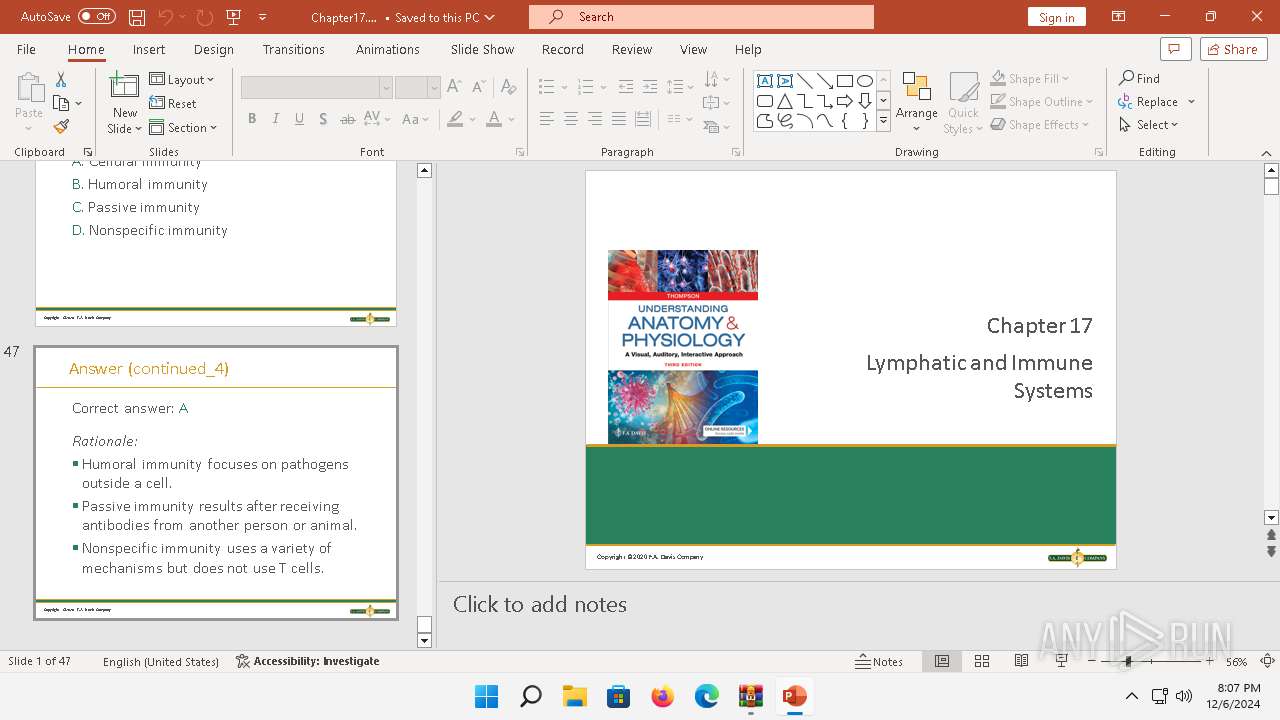
| 6192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb6192.44256\Chapter17.pptx | document | |
MD5:F740239EE70DF3BAA294E2D7F781530F | SHA256:2CD54AD7299CF4E289C4E8E536751470B74A14AA346AEA12A38454E103D97228 | |||
| 5516 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\D469C5C7-184D-435B-A739-7C23D4D7AD11 | xml | |
MD5:59B9F40AA3118DFBA37ACE0CECE9DA6F | SHA256:FBE78B9477D5AF59235C04BB71CF4DD0CB17210AE5448C568B8FF22EDB513345 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
53
DNS requests
35
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 146.75.122.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e7e8e0ff86be79ee | unknown | — | — | whitelisted |
2096 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2096 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2096 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAo1CNVcKSsBffitZcAP9%2BQ%3D | unknown | — | — | whitelisted |
2096 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAOav%2F2w8K4jHzmTOaTzWTM%3D | unknown | — | — | whitelisted |
4856 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1296 | svchost.exe | GET | 200 | 184.24.77.24:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
5516 | POWERPNT.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
— | — | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
2096 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
2096 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
2096 | firefox.exe | 184.24.77.56:80 | r10.o.lencr.org | Akamai International B.V. | DE | whitelisted |
2096 | firefox.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5552 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2096 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
— | — | 35.190.72.216:443 | location.services.mozilla.com | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
firefox.settings.services.mozilla.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
prod.remote-settings.prod.webservices.mozgcp.net |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
r10.o.lencr.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
a1887.dscq.akamai.net |
| whitelisted |
fp2e7a.wpc.phicdn.net |
| whitelisted |
google.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1296 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |