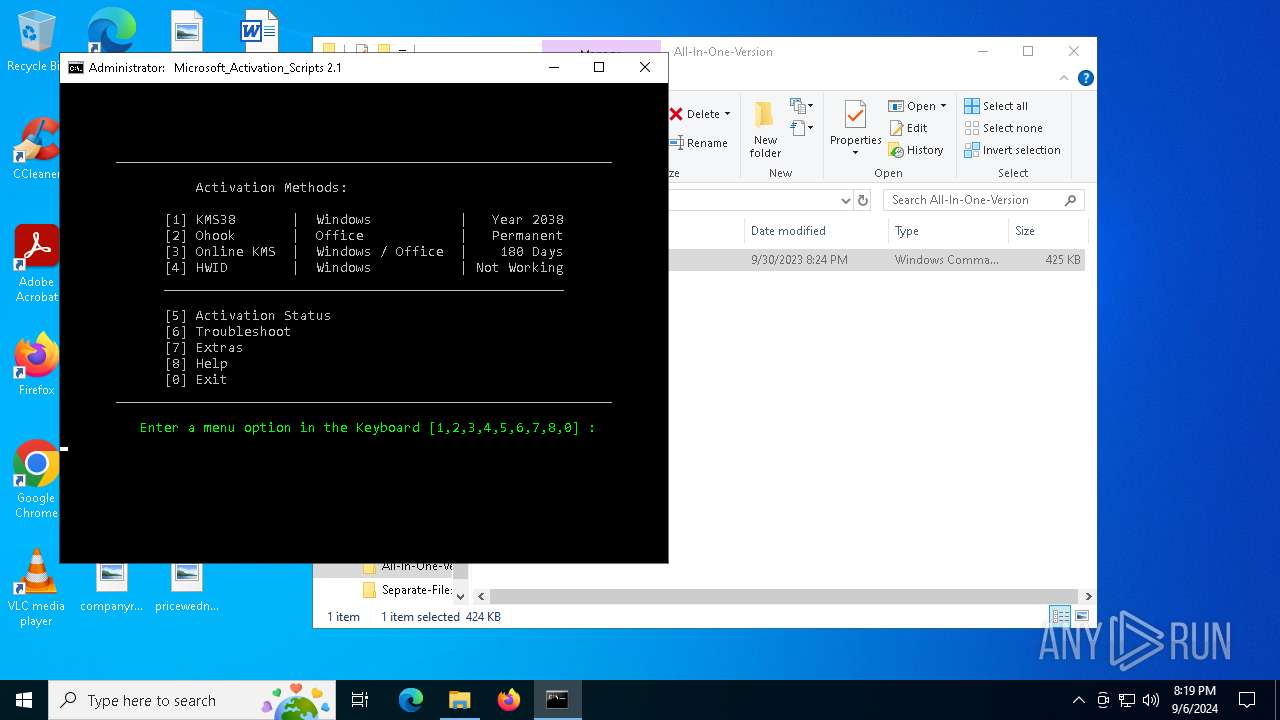
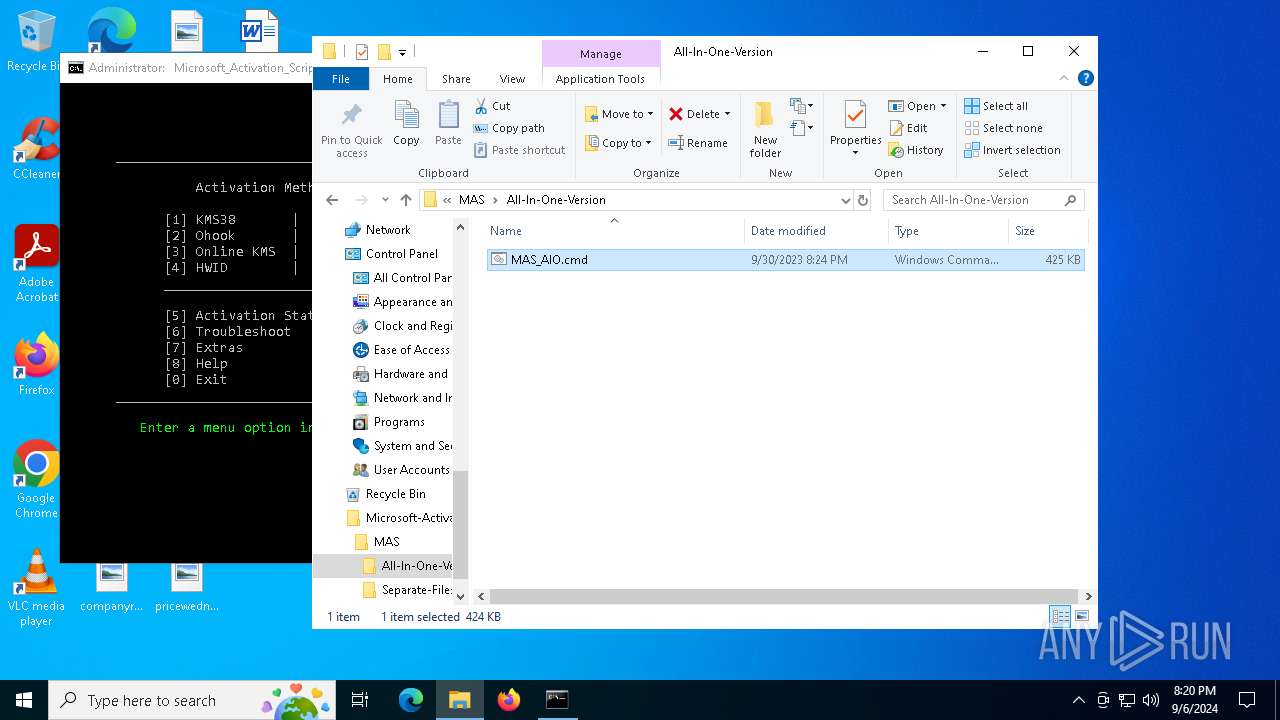
| File name: | Microsoft-Activation-Scripts-2.1.zip |
| Full analysis: | https://app.any.run/tasks/8e247719-b2aa-4481-a95b-d3ef31edf41c |
| Verdict: | Malicious activity |
| Analysis date: | September 06, 2024, 20:18:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 9A3717D2CF853ABE2F96D4E51BF7F4FA |
| SHA1: | 6909BCC2522EE06C71AFFE3021B9674FBDCC359E |
| SHA256: | 11257FF8E758655E4F14AA8A3ECF311D06B62E88518E6D09FFEDAFCB5AA9AF93 |
| SSDEEP: | 12288:PaM8Y9rS6RHO8V80SCdr5eIFtFjChkj3oShUL:P58Y9rtu8scr8ITJCSj3oShUL |
MALICIOUS
No malicious indicators.SUSPICIOUS
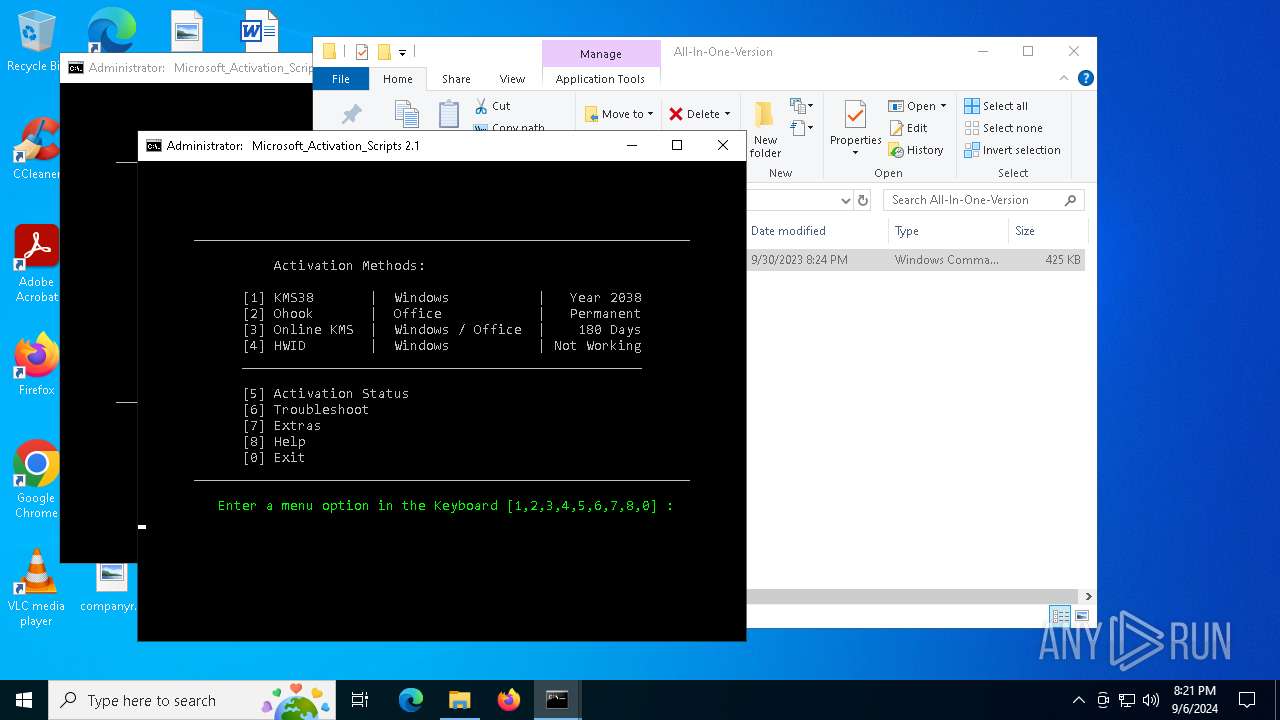
Executing commands from ".cmd" file
- WinRAR.exe (PID: 4680)
- cmd.exe (PID: 4820)
- powershell.exe (PID: 1616)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 4816)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 488)
- powershell.exe (PID: 6332)
- cmd.exe (PID: 4276)
- cmd.exe (PID: 4076)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4680)
Application launched itself
- cmd.exe (PID: 4820)
- cmd.exe (PID: 6584)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 6324)
- cmd.exe (PID: 4816)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 6340)
- cmd.exe (PID: 488)
- cmd.exe (PID: 5468)
- cmd.exe (PID: 5772)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 5908)
- cmd.exe (PID: 4276)
Starts SC.EXE for service management
- cmd.exe (PID: 4820)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 4816)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 488)
- cmd.exe (PID: 4276)
- cmd.exe (PID: 4076)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6584)
- WinRAR.exe (PID: 4680)
- cmd.exe (PID: 4820)
- cmd.exe (PID: 5048)
- powershell.exe (PID: 1616)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 4816)
- cmd.exe (PID: 6324)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 6340)
- cmd.exe (PID: 488)
- cmd.exe (PID: 5468)
- powershell.exe (PID: 6332)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 4276)
- cmd.exe (PID: 5772)
- cmd.exe (PID: 5908)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4820)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 4816)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 488)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 4276)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6988)
- cmd.exe (PID: 488)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4816)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 4276)
- cmd.exe (PID: 4076)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 4680)
- WinRAR.exe (PID: 4732)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 6332)
Checks operating system version
- cmd.exe (PID: 4820)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 4816)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 488)
- cmd.exe (PID: 4276)
- cmd.exe (PID: 4076)
Manual execution by a user
- cmd.exe (PID: 6988)
- WinRAR.exe (PID: 4732)
- cmd.exe (PID: 488)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4732)
Checks supported languages
- mode.com (PID: 6156)
- mode.com (PID: 6320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:09:30 13:24:14 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Microsoft-Activation-Scripts-2.1/ |
Total processes
260
Monitored processes
138
Malicious processes
10
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\All-In-One-Version\MAS_AIO.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 508 | reg query "HKCU\Console" /v ForceV2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | fltmc | C:\Windows\System32\fltMC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Filter Manager Control Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\All-In-One-Version\MAS_AIO.cmd" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo prompt $E " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 499
Read events
11 478
Write events
21
Delete events
0
Modification events
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1.zip | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
2
Suspicious files
1
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\LICENSE | text | |
MD5:1EBBD3E34237AF26DA5DC08A4E440464 | SHA256:3972DC9744F6499F0F9B2DBF76696F2AE7AD8AF9B23DDE66D6AF86C9DFB36986 | |||
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\README.md | text | |
MD5:AA9F08AC18D49B423A744FF07A40ED07 | SHA256:53D49DDC068FFB5567E3C8128E340F2D3986700A06492AFDF365A69860D9DC47 | |||
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\Separate-Files-Version\Activators\Ohook_Activation\BIN\Info.html | html | |
MD5:117C3B2BFA991A881EF5F9E13312B068 | SHA256:A903893A23AE98EAF0905F3206F90334BA0E4894EACE804B9796A793C3EC2874 | |||
| 1616 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mmzakjbd.qtu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\All-In-One-Version\MAS_AIO.cmd | text | |
MD5:2EA7857263E0D07B914E9284B652C5F2 | SHA256:C4AD147B40C34A4458BD9F559587E91F099C1E822E5C122E24B1BD7368FA402C | |||
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\Separate-Files-Version\Check-Activation-Status-vbs.cmd | text | |
MD5:945711798605CA089EBBF216F17867B9 | SHA256:1818E67562F5AFFC6DC8DF40A3C62B64012BD2105F75BEFD372787949D5C2FAE | |||
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\Separate-Files-Version\Activators\KMS38_Activation.cmd | text | |
MD5:C7DD86CA65B29D803226E7F2015DFB33 | SHA256:D34D99DE310658B4C6421362BC76E1A90E51E85EA74E186FD5B2E731E1D44536 | |||
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\Separate-Files-Version\Activators\HWID_Activation.cmd | text | |
MD5:3EE8DEF4C8B0834689DA5EDFCCB46D86 | SHA256:CD0D3B47D7E22AD9F108C15B5EEFDAD8375C0C7C89167B98AA39B024CFB058AE | |||
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\Separate-Files-Version\Activators\Ohook_Activation\BIN\sppc32.dll | executable | |
MD5:8AE2553E91FCAD5C9FB1B89F9DD803BD | SHA256:E6AC83560C19EC7EB868C50EA97EA0ED5632A397A9F43C17E24E6DE4A694D118 | |||
| 4732 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-2.1\MAS\Separate-Files-Version\Activators\ReadMe.txt | text | |
MD5:EE17FDA42CB80554A05CA2F23B6EE405 | SHA256:879B1961415C612F73A28DB8DB647815B002572CA474F4404CD3EAF159734EBF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
18
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6164 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6012 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6164 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6164 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6012 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6012 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |