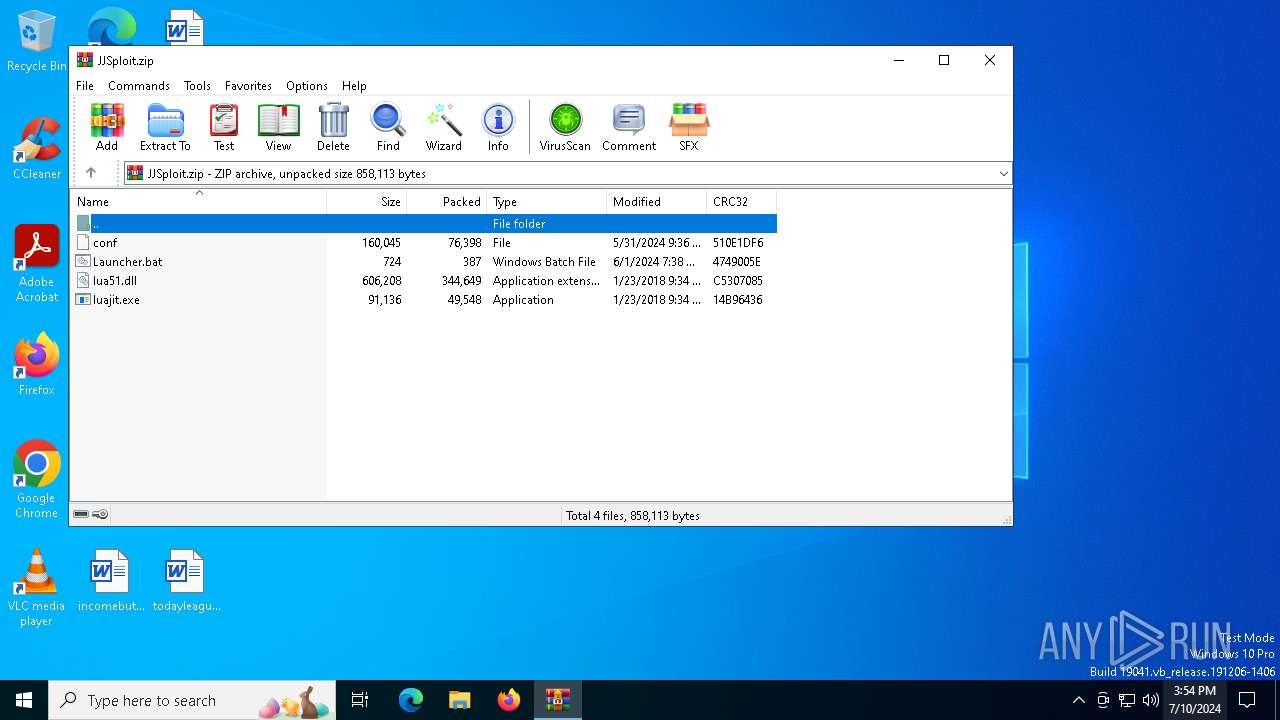
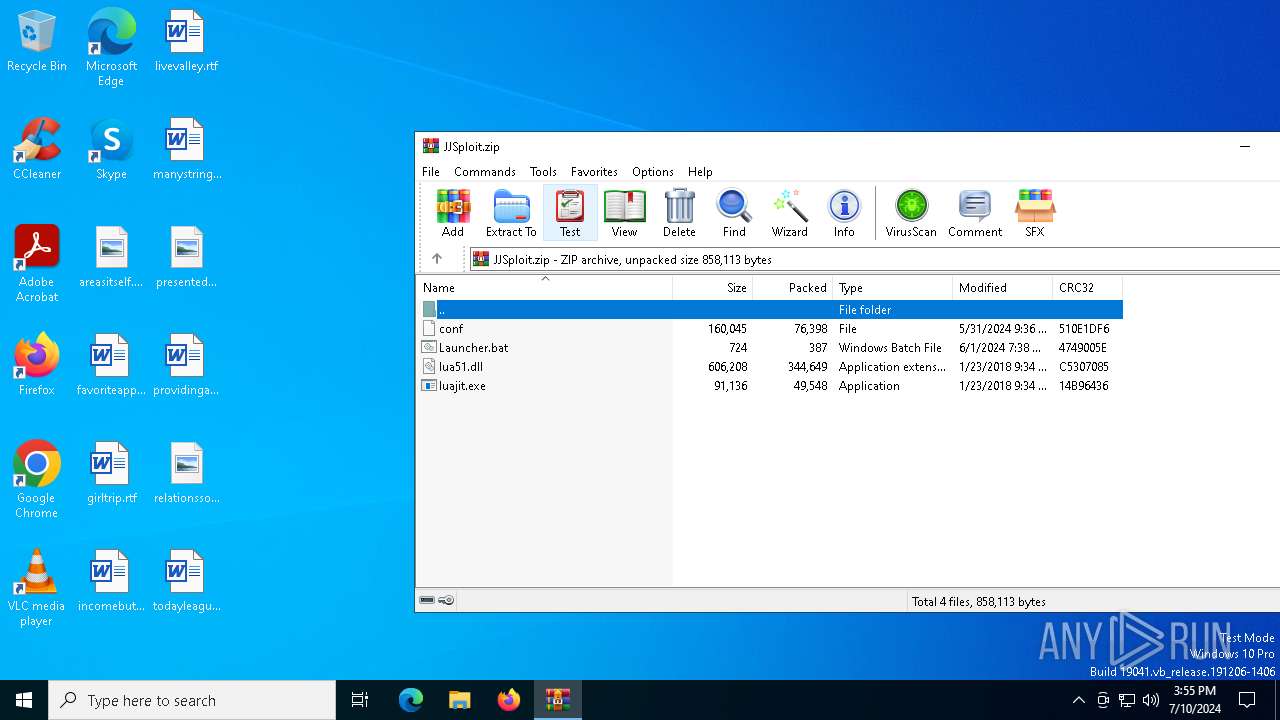
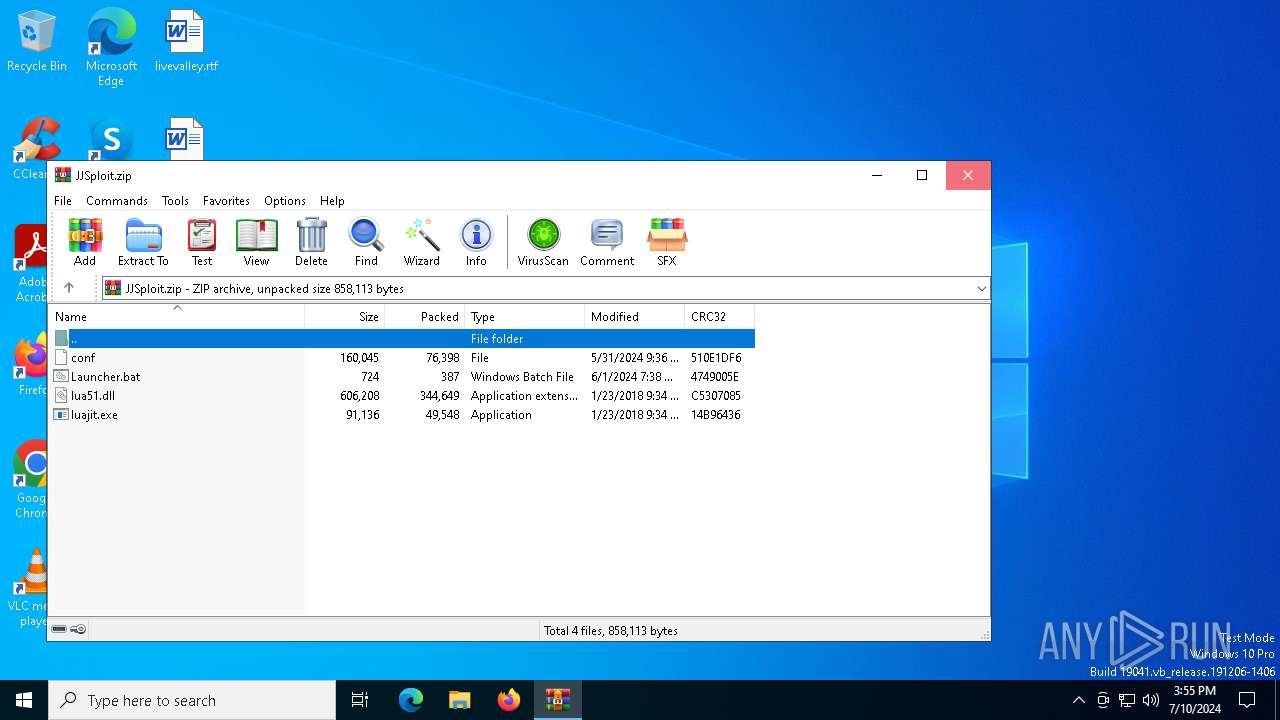
| File name: | JJSploit.zip |
| Full analysis: | https://app.any.run/tasks/e9c05edb-ee2f-4883-8eaa-7e64023dc660 |
| Verdict: | Malicious activity |
| Analysis date: | July 10, 2024, 15:54:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0A6757A13623C4D9840B0ACA6C243B52 |
| SHA1: | 35804C36E9BCCC5CAC2D406D837FCC9E14060AC7 |
| SHA256: | 11202449315D0F2EDB567C5F5E3E4BD403AE0985574344EA8DDF474C1B1FB440 |
| SSDEEP: | 24576:Sso5UhxAoskVSSmGSJFN/qS7r78pTLDdhAgKVA4XfalD:Sso5UhxAoskVSWSJFN/qS7XeTLDdhnKk |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5464)
SUSPICIOUS
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 476)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 6812)
- cmd.exe (PID: 6208)
Executing commands from a ".bat" file
- wscript.exe (PID: 6192)
- wscript.exe (PID: 6188)
The process executes VB scripts
- cmd.exe (PID: 476)
- cmd.exe (PID: 6812)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6192)
- wscript.exe (PID: 6188)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6192)
- wscript.exe (PID: 6188)
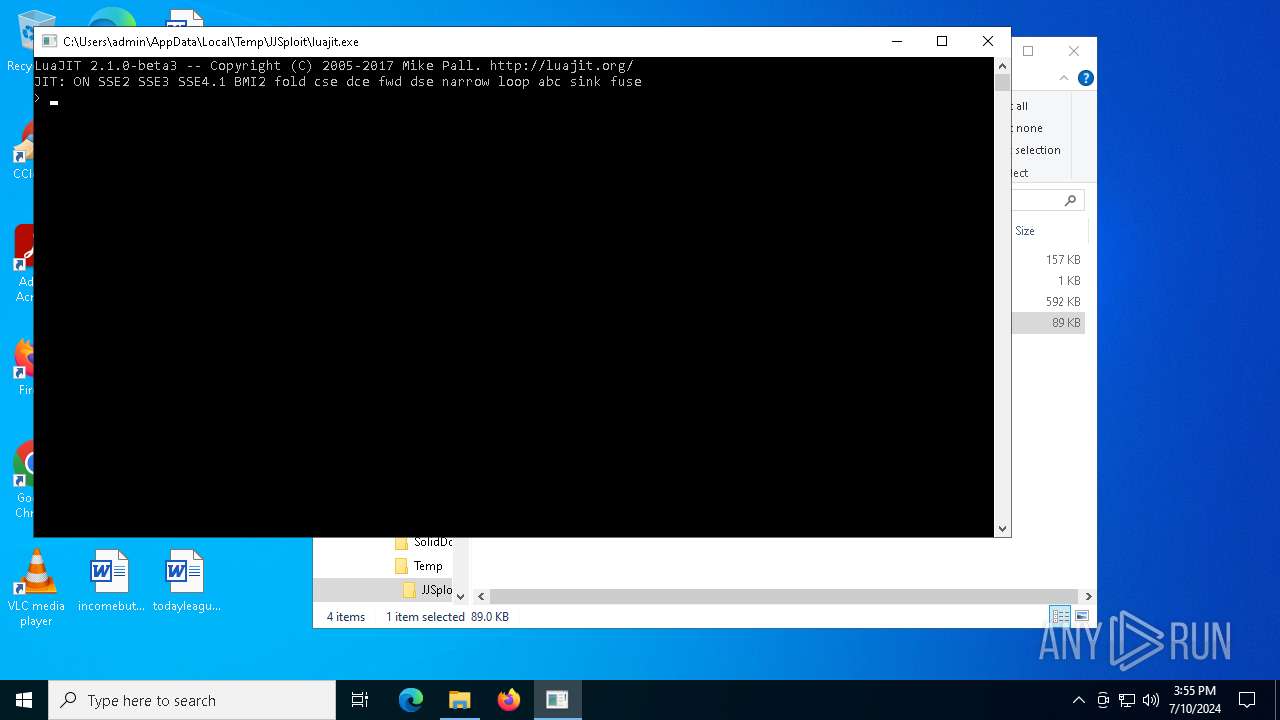
The executable file from the user directory is run by the CMD process
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
Reads security settings of Internet Explorer
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
Checks for external IP
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
Checks Windows Trust Settings
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
Connects to the server without a host name
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
INFO
Manual execution by a user
- luajit.exe (PID: 6536)
- cmd.exe (PID: 476)
- cmd.exe (PID: 6812)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5464)
Checks supported languages
- luajit.exe (PID: 6536)
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
Reads the computer name
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
Checks proxy server information
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
- slui.exe (PID: 6360)
Creates files or folders in the user directory
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
Reads the software policy settings
- luajit.exe (PID: 7132)
- slui.exe (PID: 6360)
- luajit.exe (PID: 692)
Reads the machine GUID from the registry
- luajit.exe (PID: 7132)
- luajit.exe (PID: 692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:01 00:36:18 |
| ZipCRC: | 0x510e1df6 |
| ZipCompressedSize: | 76398 |
| ZipUncompressedSize: | 160045 |
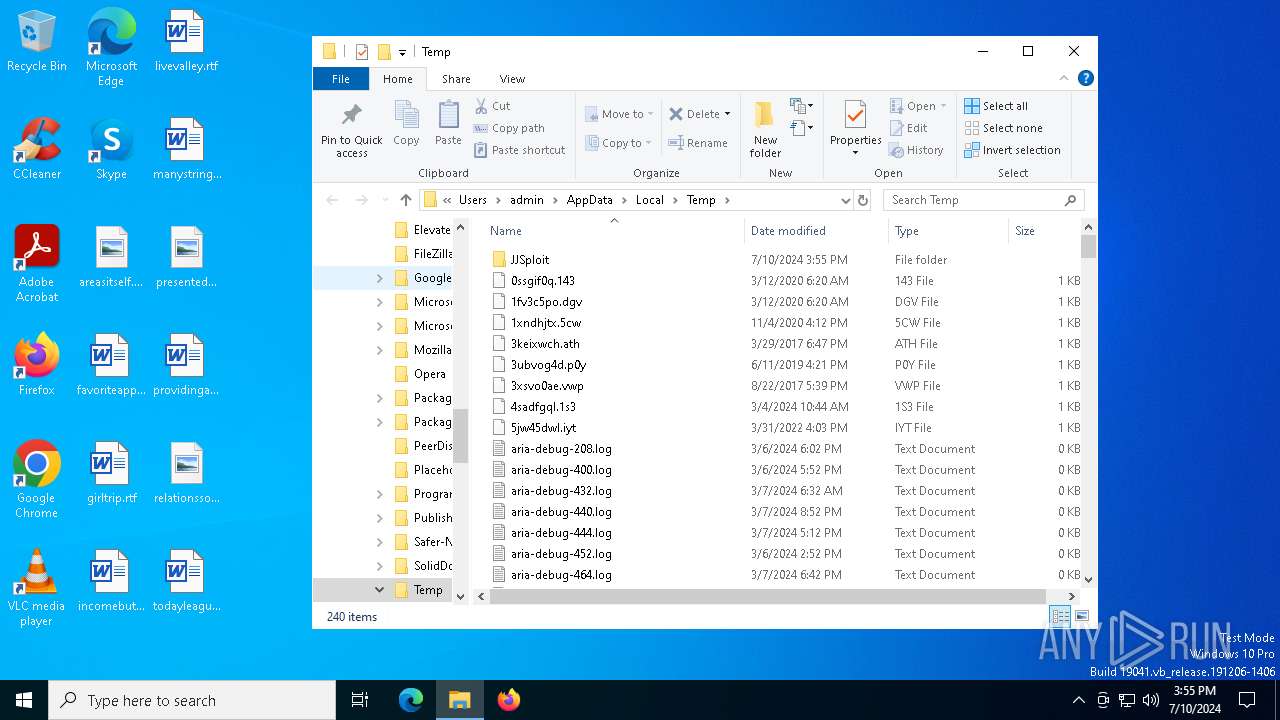
| ZipFileName: | conf |
Total processes
173
Monitored processes
25
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 476 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\JJSploit\Launcher.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
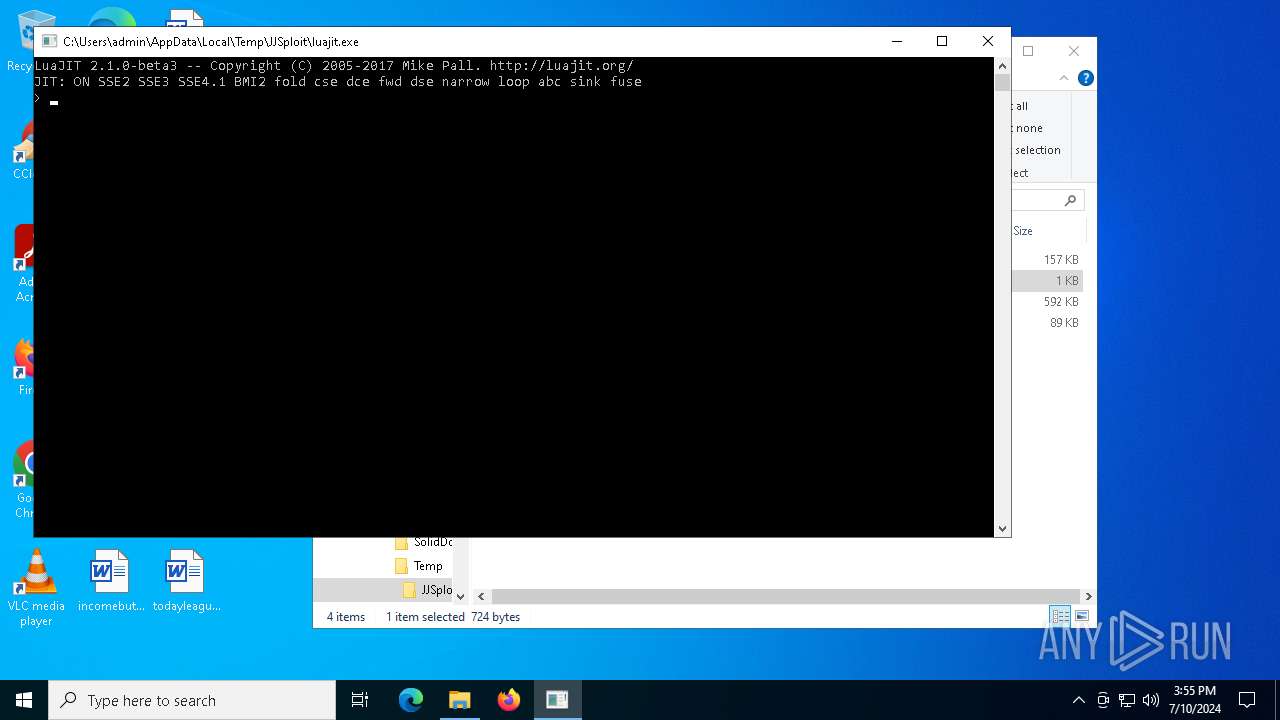
| 692 | luajit.exe conf | C:\Users\admin\AppData\Local\Temp\JJSploit\luajit.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | luajit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2336 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2476 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2628 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3976 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4048 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5228 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5464 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\JJSploit.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
19 603
Read events
19 525
Write events
78
Delete events
0
Modification events
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\JJSploit.zip | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\JJSploit | |||
Executable files
2
Suspicious files
4
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
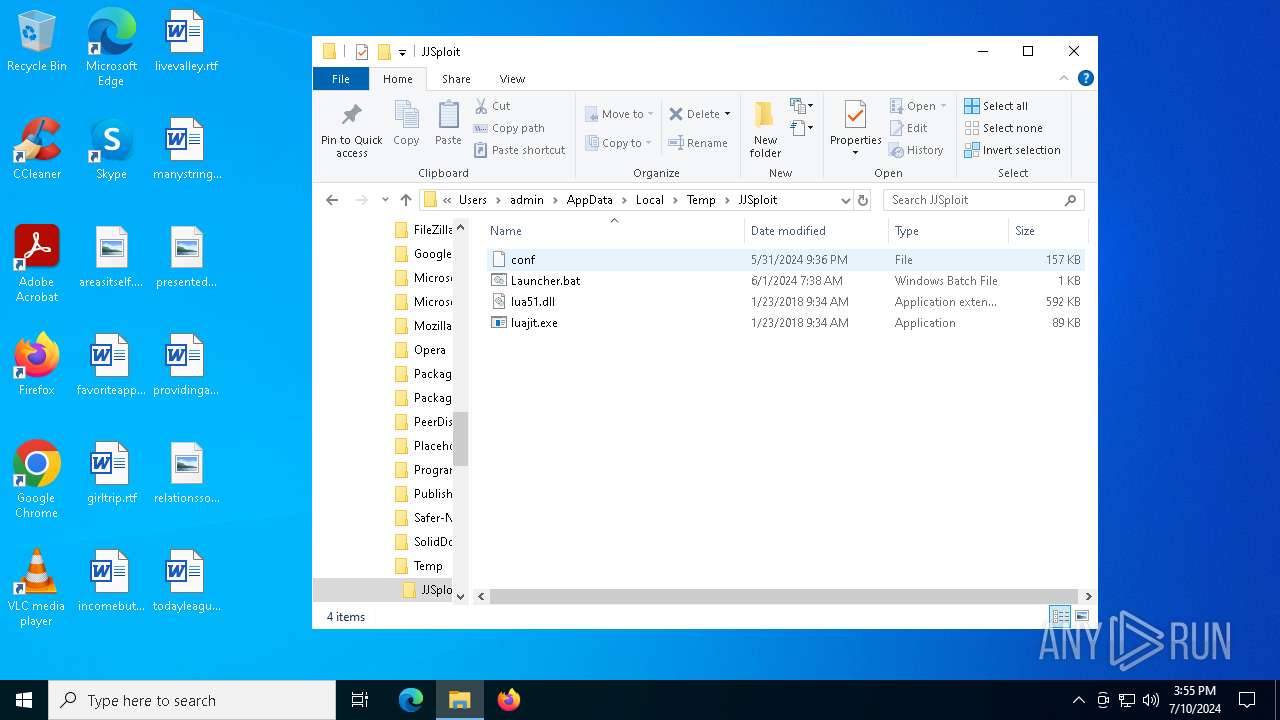
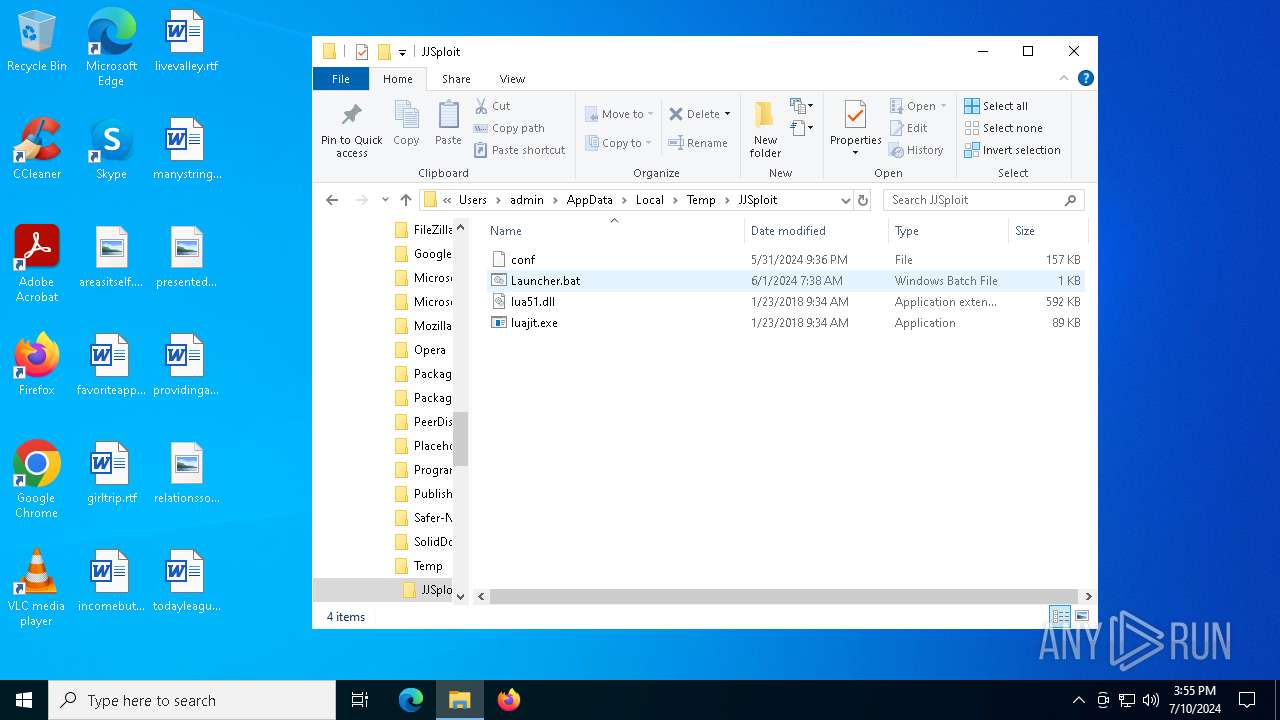
| 5464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\JJSploit\luajit.exe | executable | |
MD5:DD98A43CB27EFD5BCC29EFB23FDD6CA5 | SHA256:1CF20B8449EA84C684822A5E8AB3672213072DB8267061537D1CE4EC2C30C42A | |||
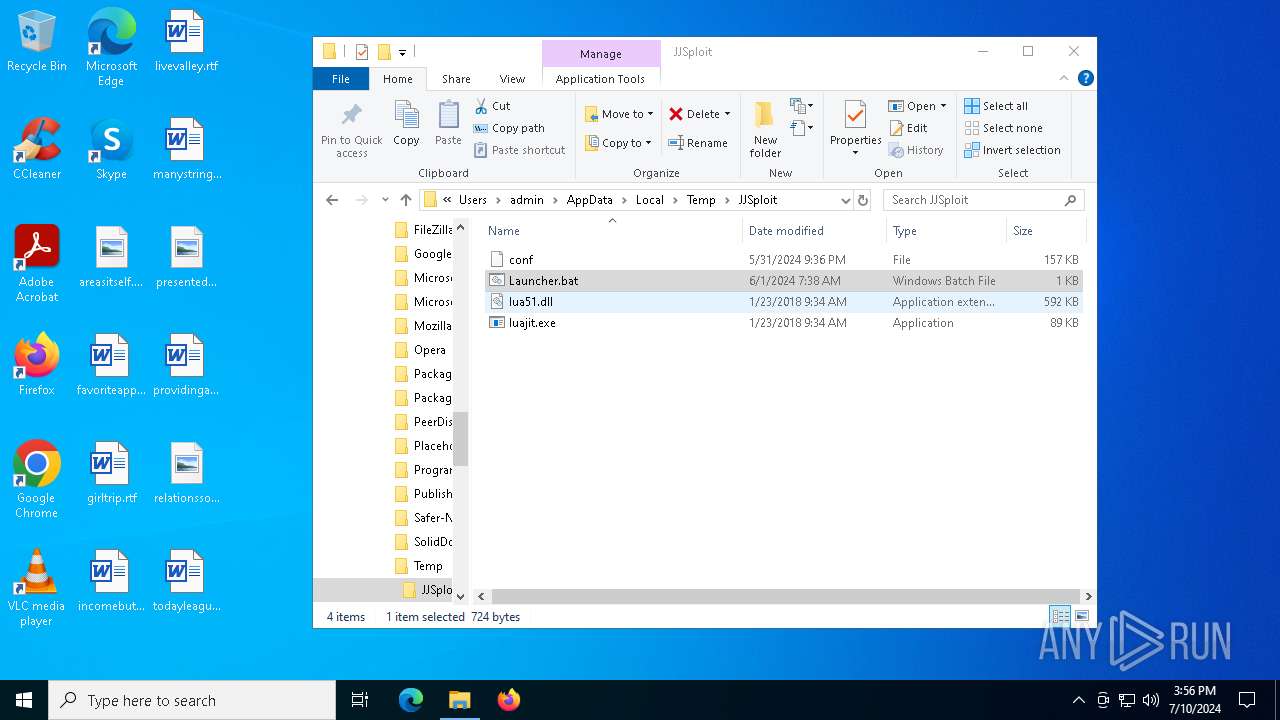
| 5464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\JJSploit\Launcher.bat | text | |
MD5:9EDCC8710E562B5DAEED73ACAA17E2FD | SHA256:F1ED443FAA01092320E04E0231327BD59C6DF7344AD0F46CA4885D28AA2AFD60 | |||
| 5464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\JJSploit\conf | binary | |
MD5:BDEC530C93A6D9DEA9FB4EA147F1F44C | SHA256:4464BE92E1A9C00E808FE6913AFE721743E3E5F7693EDB944499E3700EA6A308 | |||
| 6812 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:D14A6C18536B08C2D91CC10129CEC2CA | SHA256:88F0E55BE41422957E8F4FEC8CAF0F9ED4E68D1F0290171BA8F4BD26C19FA17D | |||
| 476 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:D14A6C18536B08C2D91CC10129CEC2CA | SHA256:88F0E55BE41422957E8F4FEC8CAF0F9ED4E68D1F0290171BA8F4BD26C19FA17D | |||
| 5464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\JJSploit\lua51.dll | executable | |
MD5:3DFF7448B43FCFB4DC65E0040B0FFB88 | SHA256:FF976F6E965E3793E278FA9BF5E80B9B226A0B3932B9DA764BFFC8E41E6CDB60 | |||
| 7132 | luajit.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\json[1].json | binary | |
MD5:39C3A98170FC9A01DD5B3D716F94B308 | SHA256:9D9A6DEE02529B469CEDCF5C17BF05F503B7351C0C2CC373D1C875EFD617BC3D | |||
| 692 | luajit.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\json[1].json | binary | |
MD5:39C3A98170FC9A01DD5B3D716F94B308 | SHA256:9D9A6DEE02529B469CEDCF5C17BF05F503B7351C0C2CC373D1C875EFD617BC3D | |||
| 7132 | luajit.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:931D34B103B35877372A9B6249E9A5F0 | SHA256:C48483B4EB4F03F5B90F528A4D6CE7BAE41DDF19600DEBB157AD3F298D849B59 | |||
| 7132 | luajit.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:DC4BB9EC651864CE853ABAC49EDBF622 | SHA256:EA7C44C08B98097D69A58416CBA1B07556D79CD26B7280B81604AF11F71541DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
87
DNS requests
32
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6440 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6360 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1828 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
7132 | luajit.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
2220 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1828 | svchost.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
692 | luajit.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | unknown |
2220 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1452 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3676 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 2.23.209.171:443 | www.bing.com | Akamai International B.V. | GB | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1828 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3680 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3680 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7132 | luajit.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
692 | luajit.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |