| File name: | hwmonitor_1.52.exe |
| Full analysis: | https://app.any.run/tasks/f4b69463-354d-4d93-a67b-3269d9684c8a |
| Verdict: | Malicious activity |
| Analysis date: | November 28, 2023, 14:37:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C975D8D0CC0F49852DC41FDD2E0B8201 |
| SHA1: | 1FF6A10902D3FD343AAD94243C82DB3AFB9B8E04 |
| SHA256: | 11192B73BC70393F4AC655A49441FA352F52D011CDB3F86C77B73CF1EB7AC7E0 |
| SSDEEP: | 49152:2UJOVLra/ub+GHD0sB8/0xM8ImbiK06E7pqdg0kSKHDsCh5t2F04bMJYHSAgg/KE:9CrF+GHNB8/4TImDFVI/jsDCTX5DwddH |
MALICIOUS
Drops the executable file immediately after the start
- hwmonitor_1.52.exe (PID: 564)
- hwmonitor_1.52.exe (PID: 3008)
- hwmonitor_1.52.tmp (PID: 1988)
- HWMonitor.exe (PID: 3940)
SUSPICIOUS
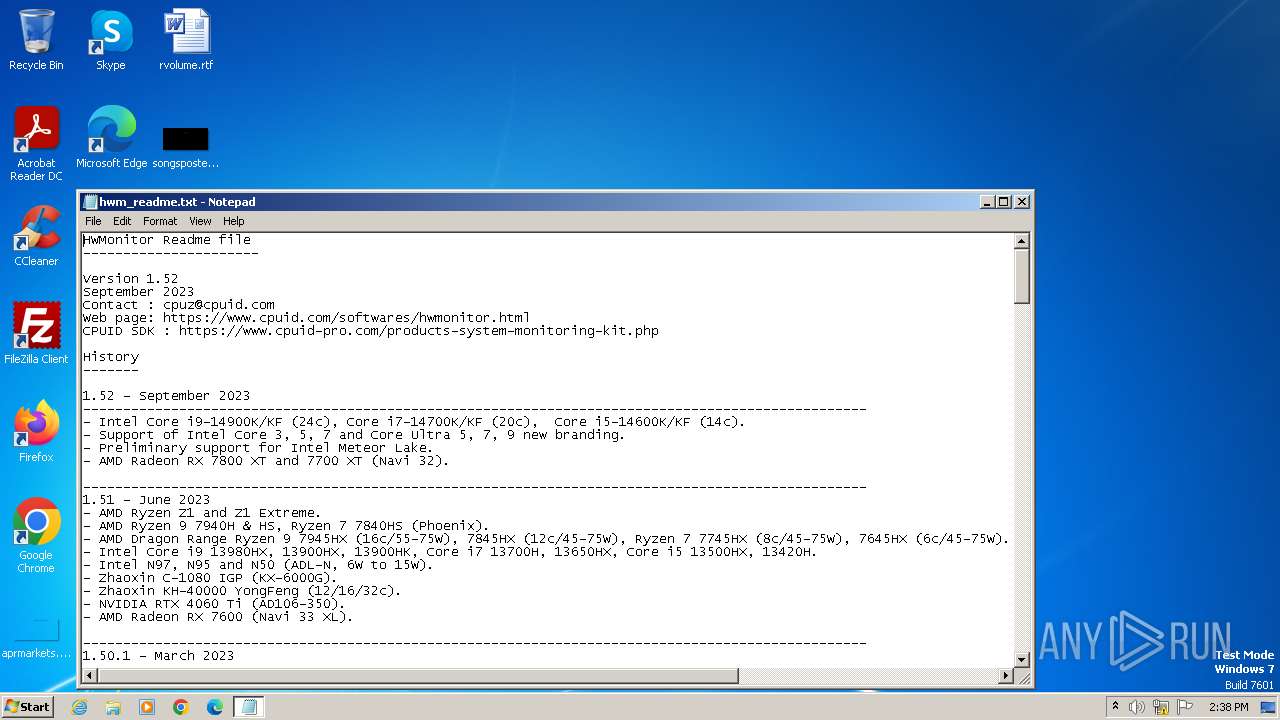
Start notepad (likely ransomware note)
- hwmonitor_1.52.tmp (PID: 888)
Reads the Windows owner or organization settings
- hwmonitor_1.52.tmp (PID: 1988)
Checks Windows Trust Settings
- HWMonitor.exe (PID: 3940)
Reads security settings of Internet Explorer
- HWMonitor.exe (PID: 3940)
Reads settings of System Certificates
- HWMonitor.exe (PID: 3940)
Adds/modifies Windows certificates
- HWMonitor.exe (PID: 3940)
Drops a system driver (possible attempt to evade defenses)
- HWMonitor.exe (PID: 3940)
Reads the Internet Settings
- HWMonitor.exe (PID: 3940)
INFO
Checks supported languages
- hwmonitor_1.52.tmp (PID: 888)
- hwmonitor_1.52.exe (PID: 564)
- hwmonitor_1.52.exe (PID: 3008)
- hwmonitor_1.52.tmp (PID: 1988)
- HWMonitor.exe (PID: 3940)
- wmpnscfg.exe (PID: 1016)
Create files in a temporary directory
- hwmonitor_1.52.exe (PID: 564)
- hwmonitor_1.52.exe (PID: 3008)
- HWMonitor.exe (PID: 3940)
Reads the computer name
- hwmonitor_1.52.tmp (PID: 888)
- hwmonitor_1.52.tmp (PID: 1988)
- HWMonitor.exe (PID: 3940)
- wmpnscfg.exe (PID: 1016)
Creates files in the program directory
- hwmonitor_1.52.tmp (PID: 1988)
Reads the machine GUID from the registry
- HWMonitor.exe (PID: 3940)
- wmpnscfg.exe (PID: 1016)
Creates files or folders in the user directory
- HWMonitor.exe (PID: 3940)
Checks proxy server information
- HWMonitor.exe (PID: 3940)
Manual execution by a user
- HWMonitor.exe (PID: 2400)
- HWMonitor.exe (PID: 3940)
- wmpnscfg.exe (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41984 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaad0 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | CPUID, Inc. |
| FileDescription: | CPUID HWMonitor Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | CPUID HWMonitor |
| ProductVersion: | 1.52 |
Total processes
51
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe" | C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID, Inc. Integrity Level: MEDIUM Description: CPUID HWMonitor Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 888 | "C:\Users\admin\AppData\Local\Temp\is-HGKF5.tmp\hwmonitor_1.52.tmp" /SL5="$7019C,1234407,58368,C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe" | C:\Users\admin\AppData\Local\Temp\is-HGKF5.tmp\hwmonitor_1.52.tmp | — | hwmonitor_1.52.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1988 | "C:\Users\admin\AppData\Local\Temp\is-A6PDD.tmp\hwmonitor_1.52.tmp" /SL5="$90192,1234407,58368,C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe" /SPAWNWND=$D0182 /NOTIFYWND=$7019C | C:\Users\admin\AppData\Local\Temp\is-A6PDD.tmp\hwmonitor_1.52.tmp | — | hwmonitor_1.52.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2400 | "C:\Program Files\CPUID\HWMonitor\HWMonitor.exe" | C:\Program Files\CPUID\HWMonitor\HWMonitor.exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID Integrity Level: MEDIUM Description: HWMonitor Exit code: 3221226540 Version: 1, 5, 2, 0 Modules
| |||||||||||||||
| 3008 | "C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe" /SPAWNWND=$D0182 /NOTIFYWND=$7019C | C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe | hwmonitor_1.52.tmp | ||||||||||||
User: admin Company: CPUID, Inc. Integrity Level: HIGH Description: CPUID HWMonitor Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3100 | "C:\Windows\system32\NOTEPAD.EXE" C:\Program Files\CPUID\HWMonitor\hwm_readme.txt | C:\Windows\System32\notepad.exe | — | hwmonitor_1.52.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3940 | "C:\Program Files\CPUID\HWMonitor\HWMonitor.exe" | C:\Program Files\CPUID\HWMonitor\HWMonitor.exe | explorer.exe | ||||||||||||
User: admin Company: CPUID Integrity Level: HIGH Description: HWMonitor Exit code: 0 Version: 1, 5, 2, 0 Modules
| |||||||||||||||
Total events
6 924
Read events
6 889
Write events
26
Delete events
9
Modification events
| (PID) Process: | (1988) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: E6B186D6D438CC1711A972CE681D9065E9F2E25692355F1D7A6D45F9C73F9E18 | |||
| (PID) Process: | (1988) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Program Files\CPUID\HWMonitor\HWMonitor.exe | |||
| (PID) Process: | (1988) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1988) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: F08376B023B33868776FB4DFD518AFD160FE7FA07734FA55FD465978E6361654 | |||
| (PID) Process: | (1988) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: C4070000EA2B3E820822DA01 | |||
| (PID) Process: | (1988) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3940) HWMonitor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3940) HWMonitor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000059010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3940) HWMonitor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3940) HWMonitor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
7
Suspicious files
15
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1988 | hwmonitor_1.52.tmp | C:\Program Files\CPUID\HWMonitor\HWMonitor.exe | executable | |
MD5:D7F245246F2597F7F23E15EA779CC5AB | SHA256:62CD1A2E8FE364F954F56438F5DB89B54F9F085531833C236C54E9A0AF496BE5 | |||
| 3008 | hwmonitor_1.52.exe | C:\Users\admin\AppData\Local\Temp\is-A6PDD.tmp\hwmonitor_1.52.tmp | executable | |
MD5:318AC5138773AED192C72971D28C3984 | SHA256:1E618C685C04E75291F908E9F7FBE8060F9766E0E9711142ABC2A1E3961A63EB | |||
| 1988 | hwmonitor_1.52.tmp | C:\Program Files\CPUID\HWMonitor\hwm_readme.txt | text | |
MD5:F86BFE7020B639F6A70F20C00CE12F90 | SHA256:E94300217D273F11EBC58EB273E5000EC86471E5C10CA12BB36FFBCDCC9FA666 | |||
| 1988 | hwmonitor_1.52.tmp | C:\Program Files\CPUID\HWMonitor\is-14PKU.tmp | executable | |
MD5:318AC5138773AED192C72971D28C3984 | SHA256:1E618C685C04E75291F908E9F7FBE8060F9766E0E9711142ABC2A1E3961A63EB | |||
| 564 | hwmonitor_1.52.exe | C:\Users\admin\AppData\Local\Temp\is-HGKF5.tmp\hwmonitor_1.52.tmp | executable | |
MD5:318AC5138773AED192C72971D28C3984 | SHA256:1E618C685C04E75291F908E9F7FBE8060F9766E0E9711142ABC2A1E3961A63EB | |||
| 1988 | hwmonitor_1.52.tmp | C:\Program Files\CPUID\HWMonitor\is-NSMLQ.tmp | executable | |
MD5:D7F245246F2597F7F23E15EA779CC5AB | SHA256:62CD1A2E8FE364F954F56438F5DB89B54F9F085531833C236C54E9A0AF496BE5 | |||
| 1988 | hwmonitor_1.52.tmp | C:\Users\Public\Desktop\CPUID HWMonitor.lnk | binary | |
MD5:FE2321D42E5788148DDEA6BC9EFF334C | SHA256:2ED738898761215ED18B60CC652DE91AC6193536397F3EB2685F0D3DDAC32981 | |||
| 1988 | hwmonitor_1.52.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\CPUID\HWMonitor\Uninstall HWMonitor.lnk | binary | |
MD5:755F0AC6BD7C38B187F38BB6A490287F | SHA256:957999304C31023BB9945E2AD73AF0C99F22B6EB3C1FC6784E778C6E832DDF57 | |||
| 3940 | HWMonitor.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3940 | HWMonitor.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
9
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3940 | HWMonitor.exe | GET | 200 | 8.253.207.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f0b394bd62f2437a | unknown | compressed | 4.66 Kb | unknown |
1080 | svchost.exe | GET | 304 | 8.253.207.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5312bc669adcb130 | unknown | — | — | unknown |
3940 | HWMonitor.exe | GET | 200 | 8.253.207.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ccd50f3400864c1d | unknown | compressed | 61.6 Kb | unknown |
3940 | HWMonitor.exe | GET | 200 | 23.53.40.131:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgTN4TiYAHgnmEyPhblHc%2F5gew%3D%3D | unknown | binary | 503 b | unknown |
3940 | HWMonitor.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3940 | HWMonitor.exe | 195.154.81.43:443 | download.cpuid.com | Online S.a.s. | FR | unknown |
3940 | HWMonitor.exe | 8.253.207.120:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3940 | HWMonitor.exe | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
3940 | HWMonitor.exe | 23.53.40.131:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 8.253.207.120:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.cpuid.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |