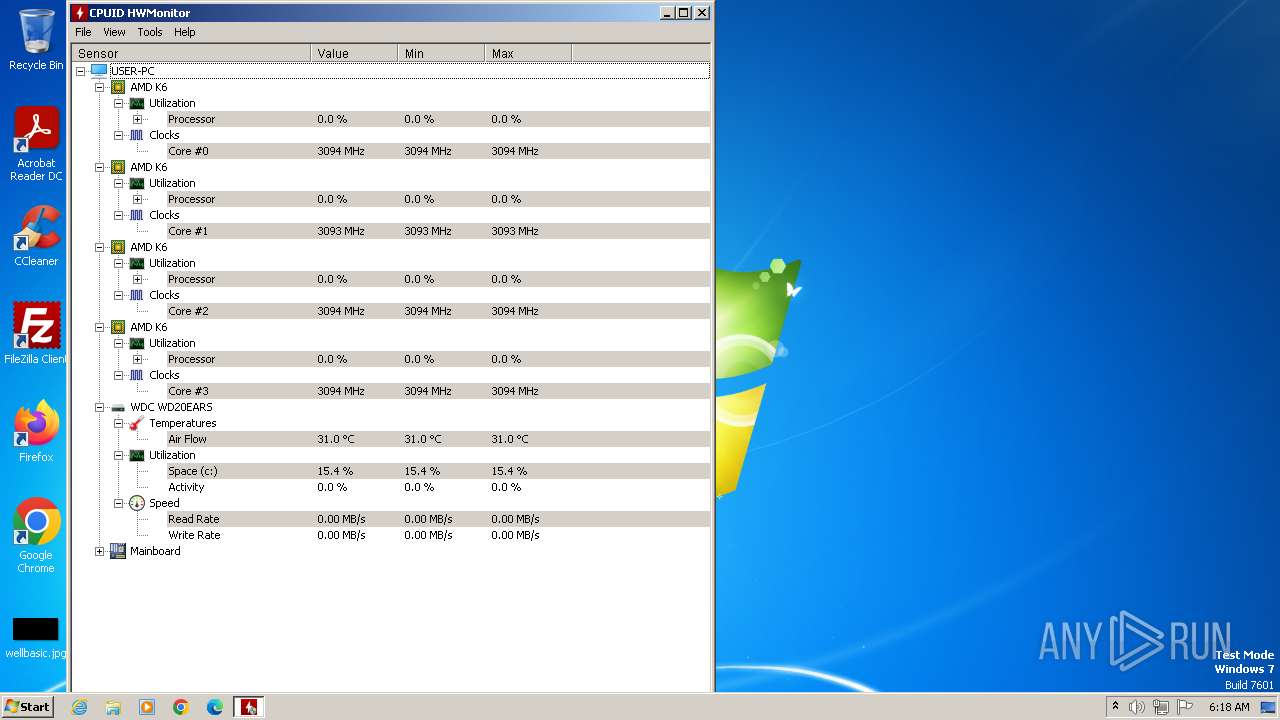
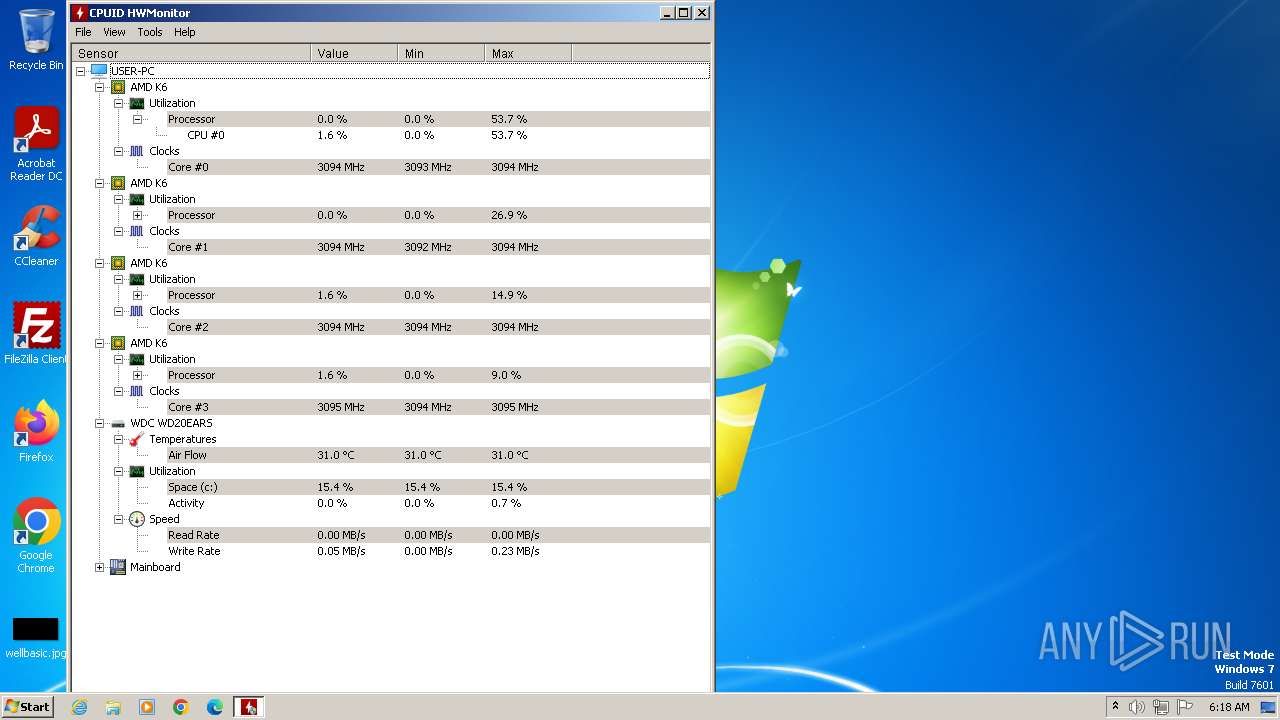
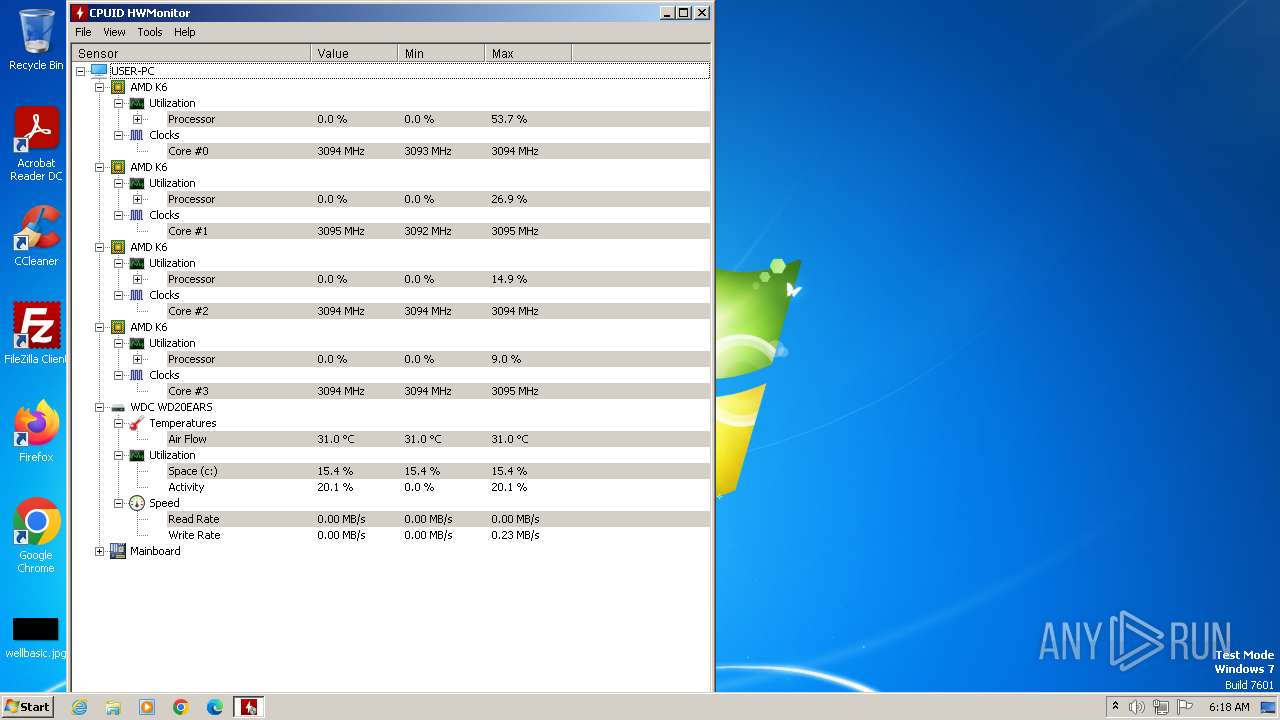
| File name: | hwmonitor_1.52.exe |
| Full analysis: | https://app.any.run/tasks/d8148b9d-6343-4a06-bbc9-f7376293ca2c |
| Verdict: | Malicious activity |
| Analysis date: | October 25, 2023, 05:18:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C975D8D0CC0F49852DC41FDD2E0B8201 |
| SHA1: | 1FF6A10902D3FD343AAD94243C82DB3AFB9B8E04 |
| SHA256: | 11192B73BC70393F4AC655A49441FA352F52D011CDB3F86C77B73CF1EB7AC7E0 |
| SSDEEP: | 24576:9yIRw0hNNgeIoP2cXGM9PidKP8O71ekVpBIM8RH4AP+YvsGf/jwxS3TdusZk:9yv07PIophicPprHBP8RH4AWB2LZu |
MALICIOUS
Drops the executable file immediately after the start
- hwmonitor_1.52.exe (PID: 3820)
- hwmonitor_1.52.exe (PID: 3824)
- hwmonitor_1.52.tmp (PID: 3632)
- HWMonitor.exe (PID: 2216)
Application was dropped or rewritten from another process
- HWMonitor.exe (PID: 2472)
- HWMonitor.exe (PID: 2216)
SUSPICIOUS
Reads the Windows owner or organization settings
- hwmonitor_1.52.tmp (PID: 3632)
Reads the Internet Settings
- HWMonitor.exe (PID: 2216)
Reads settings of System Certificates
- HWMonitor.exe (PID: 2216)
Drops a system driver (possible attempt to evade defenses)
- HWMonitor.exe (PID: 2216)
Reads security settings of Internet Explorer
- HWMonitor.exe (PID: 2216)
Checks Windows Trust Settings
- HWMonitor.exe (PID: 2216)
INFO
Checks supported languages
- hwmonitor_1.52.exe (PID: 3820)
- hwmonitor_1.52.tmp (PID: 1600)
- hwmonitor_1.52.exe (PID: 3824)
- hwmonitor_1.52.tmp (PID: 3632)
- HWMonitor.exe (PID: 2216)
Create files in a temporary directory
- hwmonitor_1.52.exe (PID: 3820)
- hwmonitor_1.52.exe (PID: 3824)
- HWMonitor.exe (PID: 2216)
Reads the computer name
- hwmonitor_1.52.tmp (PID: 1600)
- hwmonitor_1.52.tmp (PID: 3632)
- HWMonitor.exe (PID: 2216)
Application was dropped or rewritten from another process
- hwmonitor_1.52.tmp (PID: 3632)
- hwmonitor_1.52.tmp (PID: 1600)
Creates files in the program directory
- hwmonitor_1.52.tmp (PID: 3632)
Manual execution by a user
- HWMonitor.exe (PID: 2472)
- HWMonitor.exe (PID: 2216)
Checks proxy server information
- HWMonitor.exe (PID: 2216)
Reads the machine GUID from the registry
- HWMonitor.exe (PID: 2216)
Creates files or folders in the user directory
- HWMonitor.exe (PID: 2216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| ProductVersion: | 1.52 |
|---|---|
| ProductName: | CPUID HWMonitor |
| LegalCopyright: | |
| FileVersion: | |
| FileDescription: | CPUID HWMonitor Setup |
| CompanyName: | CPUID, Inc. |
| Comments: | This installation was built with Inno Setup. |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 0.0.0.0 |
| FileVersionNumber: | 0.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | 6 |
| OSVersion: | 1 |
| EntryPoint: | 0xaad0 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 17920 |
| CodeSize: | 41984 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Total processes
50
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1600 | "C:\Users\admin\AppData\Local\Temp\is-4HLSQ.tmp\hwmonitor_1.52.tmp" /SL5="$1001CA,1234407,58368,C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe" | C:\Users\admin\AppData\Local\Temp\is-4HLSQ.tmp\hwmonitor_1.52.tmp | — | hwmonitor_1.52.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2216 | "C:\Program Files\CPUID\HWMonitor\HWMonitor.exe" | C:\Program Files\CPUID\HWMonitor\HWMonitor.exe | explorer.exe | ||||||||||||
User: admin Company: CPUID Integrity Level: HIGH Description: HWMonitor Exit code: 0 Version: 1, 5, 2, 0 Modules
| |||||||||||||||
| 2472 | "C:\Program Files\CPUID\HWMonitor\HWMonitor.exe" | C:\Program Files\CPUID\HWMonitor\HWMonitor.exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID Integrity Level: MEDIUM Description: HWMonitor Exit code: 3221226540 Version: 1, 5, 2, 0 Modules
| |||||||||||||||
| 3632 | "C:\Users\admin\AppData\Local\Temp\is-BI6UL.tmp\hwmonitor_1.52.tmp" /SL5="$60300,1234407,58368,C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe" /SPAWNWND=$4036C /NOTIFYWND=$1001CA | C:\Users\admin\AppData\Local\Temp\is-BI6UL.tmp\hwmonitor_1.52.tmp | — | hwmonitor_1.52.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3820 | "C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe" | C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID, Inc. Integrity Level: MEDIUM Description: CPUID HWMonitor Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3824 | "C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe" /SPAWNWND=$4036C /NOTIFYWND=$1001CA | C:\Users\admin\AppData\Local\Temp\hwmonitor_1.52.exe | hwmonitor_1.52.tmp | ||||||||||||
User: admin Company: CPUID, Inc. Integrity Level: HIGH Description: CPUID HWMonitor Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
6 839
Read events
6 807
Write events
26
Delete events
6
Modification events
| (PID) Process: | (3632) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: BD1C24155A185E1BB31A361D453A071F47CEC706A0D2FAED0023D66C27E15734 | |||
| (PID) Process: | (3632) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Program Files\CPUID\HWMonitor\HWMonitor.exe | |||
| (PID) Process: | (3632) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3632) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 745F8E3974B551170ECD20BFDFA1CDA1D06E63324D506299E18813BDB7B2B9B8 | |||
| (PID) Process: | (3632) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 300E0000F62CC8A70207DA01 | |||
| (PID) Process: | (3632) hwmonitor_1.52.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2216) HWMonitor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2216) HWMonitor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2216) HWMonitor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2216) HWMonitor.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
7
Suspicious files
15
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3632 | hwmonitor_1.52.tmp | C:\Program Files\CPUID\HWMonitor\is-IBGP0.tmp | executable | |
MD5:318AC5138773AED192C72971D28C3984 | SHA256:1E618C685C04E75291F908E9F7FBE8060F9766E0E9711142ABC2A1E3961A63EB | |||
| 3820 | hwmonitor_1.52.exe | C:\Users\admin\AppData\Local\Temp\is-4HLSQ.tmp\hwmonitor_1.52.tmp | executable | |
MD5:318AC5138773AED192C72971D28C3984 | SHA256:1E618C685C04E75291F908E9F7FBE8060F9766E0E9711142ABC2A1E3961A63EB | |||
| 2216 | HWMonitor.exe | C:\Users\admin\AppData\Local\Temp\Cab41E4.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3632 | hwmonitor_1.52.tmp | C:\Program Files\CPUID\HWMonitor\hwm_readme.txt | text | |
MD5:F86BFE7020B639F6A70F20C00CE12F90 | SHA256:E94300217D273F11EBC58EB273E5000EC86471E5C10CA12BB36FFBCDCC9FA666 | |||
| 3632 | hwmonitor_1.52.tmp | C:\Program Files\CPUID\HWMonitor\unins000.dat | binary | |
MD5:89273237D786C9A7EA9928625CCEDC76 | SHA256:17866BEF281839FA6459863DF760D91E459E5B096D19EB64AC23C8B550C170AC | |||
| 3824 | hwmonitor_1.52.exe | C:\Users\admin\AppData\Local\Temp\is-BI6UL.tmp\hwmonitor_1.52.tmp | executable | |
MD5:318AC5138773AED192C72971D28C3984 | SHA256:1E618C685C04E75291F908E9F7FBE8060F9766E0E9711142ABC2A1E3961A63EB | |||
| 3632 | hwmonitor_1.52.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\CPUID\HWMonitor\Uninstall HWMonitor.lnk | binary | |
MD5:6EF4E68053135CA582668DE86B0B8C4A | SHA256:C82A6E9F0EA9977CB0AC97CE25076FC891FB610E15FDA62EA711E78AF14A30CD | |||
| 2216 | HWMonitor.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 3632 | hwmonitor_1.52.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\CPUID\HWMonitor\HWMonitor.lnk | binary | |
MD5:AD30C9515E66C660F4DE748BA4C9FDE4 | SHA256:4DBD89D5A0895CC09EE21D4DA8E6D4898C9B0CB73F46C3C08FA067613F4D68F8 | |||
| 3632 | hwmonitor_1.52.tmp | C:\Users\Public\Desktop\CPUID HWMonitor.lnk | binary | |
MD5:A072B493F4BEFA9950BC67C28061FC51 | SHA256:6BFB8451C8FB6001E00F2BC2613571A6FBA1545C6CA901E209C3AABA7917CB8F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
6
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2216 | HWMonitor.exe | GET | 200 | 46.228.146.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?248fc5525a5da0f0 | unknown | compressed | 4.66 Kb | unknown |
2216 | HWMonitor.exe | GET | 200 | 23.53.40.161:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgOtcy3iHUtqqXerqZ8ymWI%2FoA%3D%3D | unknown | der | 503 b | unknown |
2216 | HWMonitor.exe | GET | 200 | 46.228.146.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?17139c9c5265827d | unknown | compressed | 61.6 Kb | unknown |
2216 | HWMonitor.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2216 | HWMonitor.exe | 195.154.81.43:443 | download.cpuid.com | Online S.a.s. | FR | unknown |
2216 | HWMonitor.exe | 46.228.146.128:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2216 | HWMonitor.exe | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
2216 | HWMonitor.exe | 23.53.40.161:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.cpuid.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |