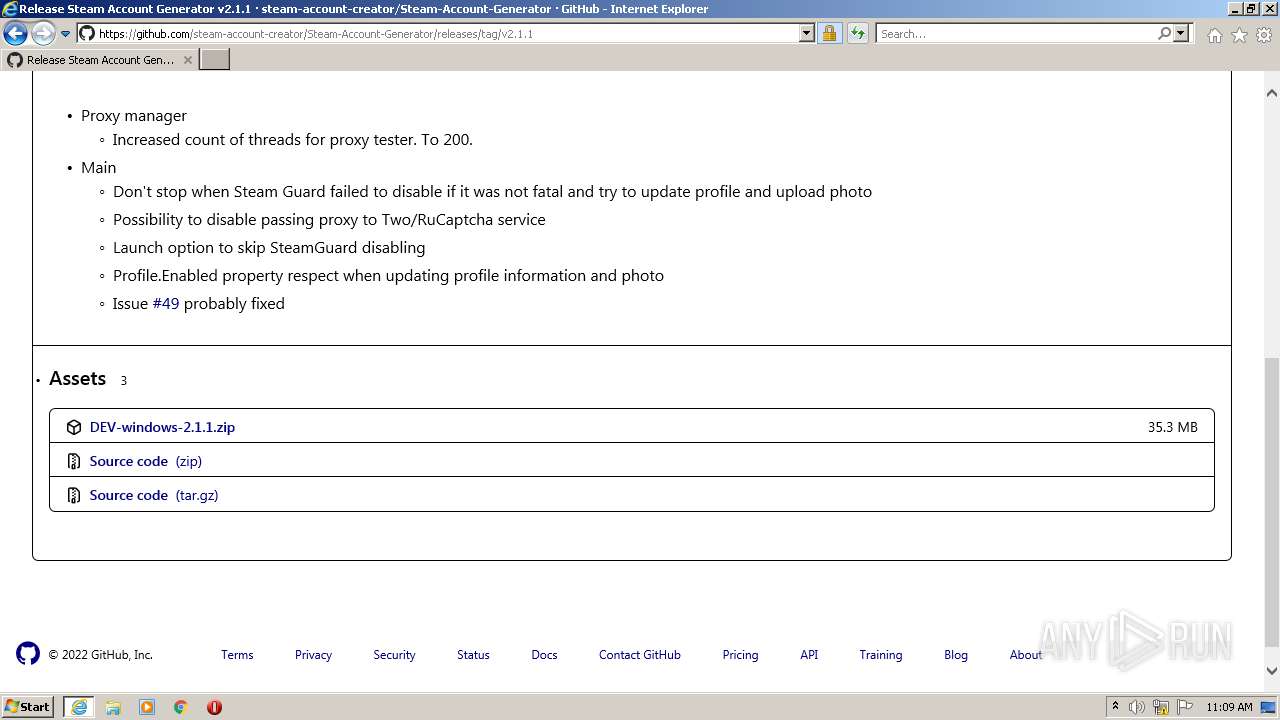
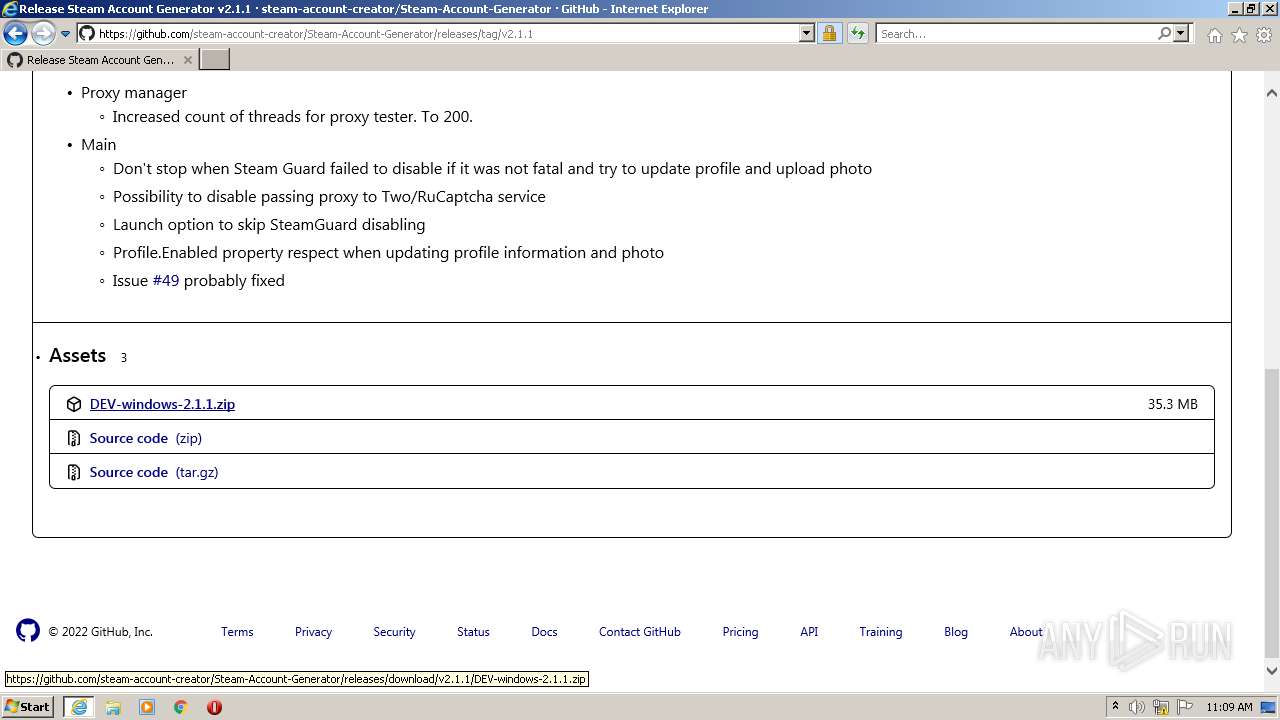
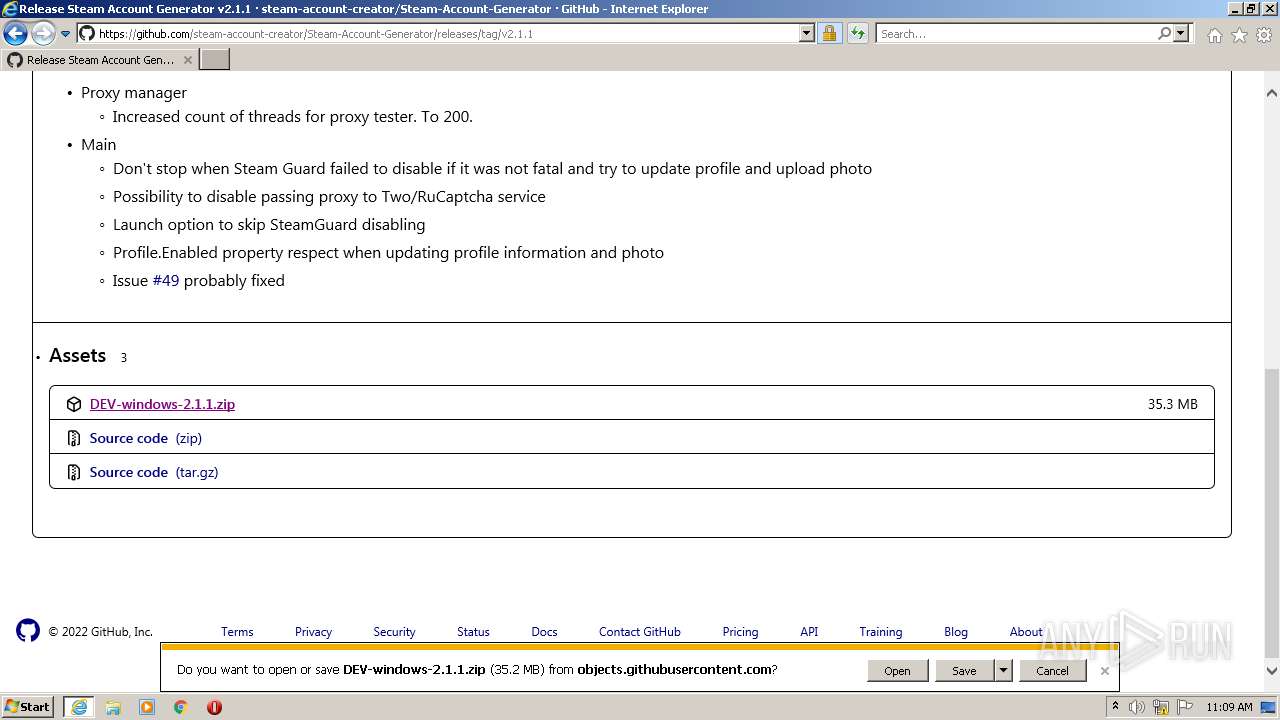
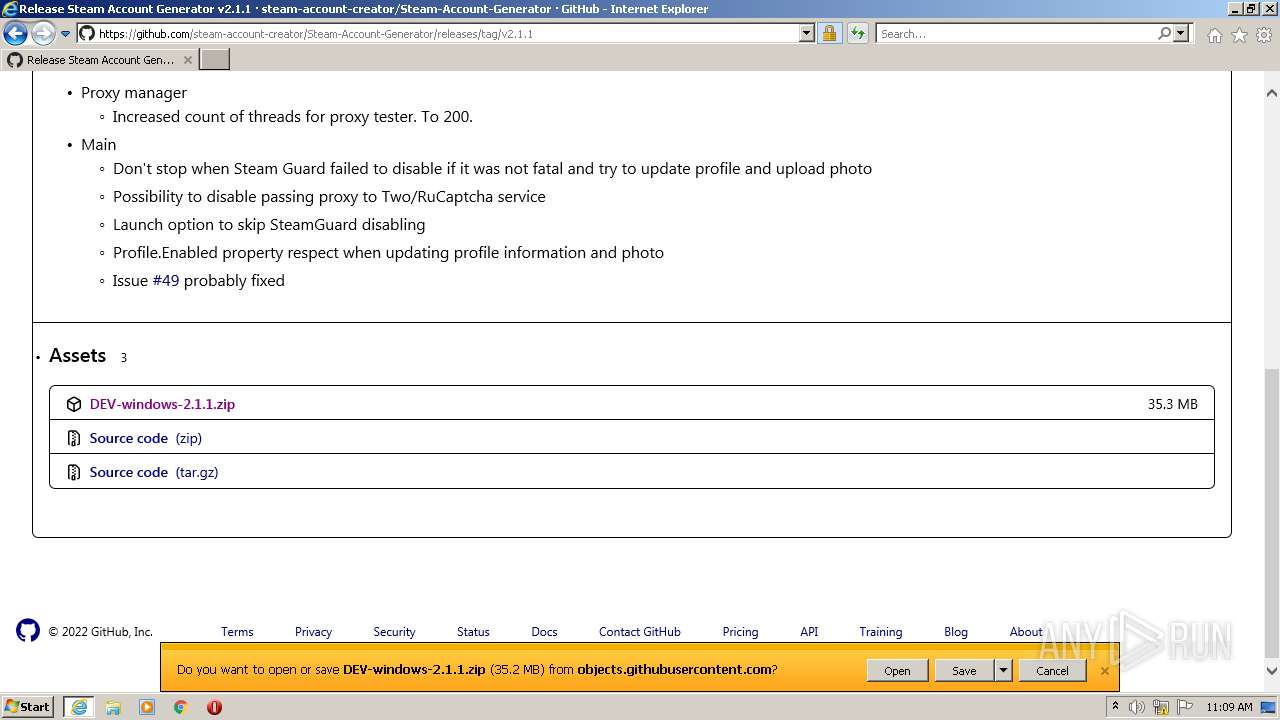
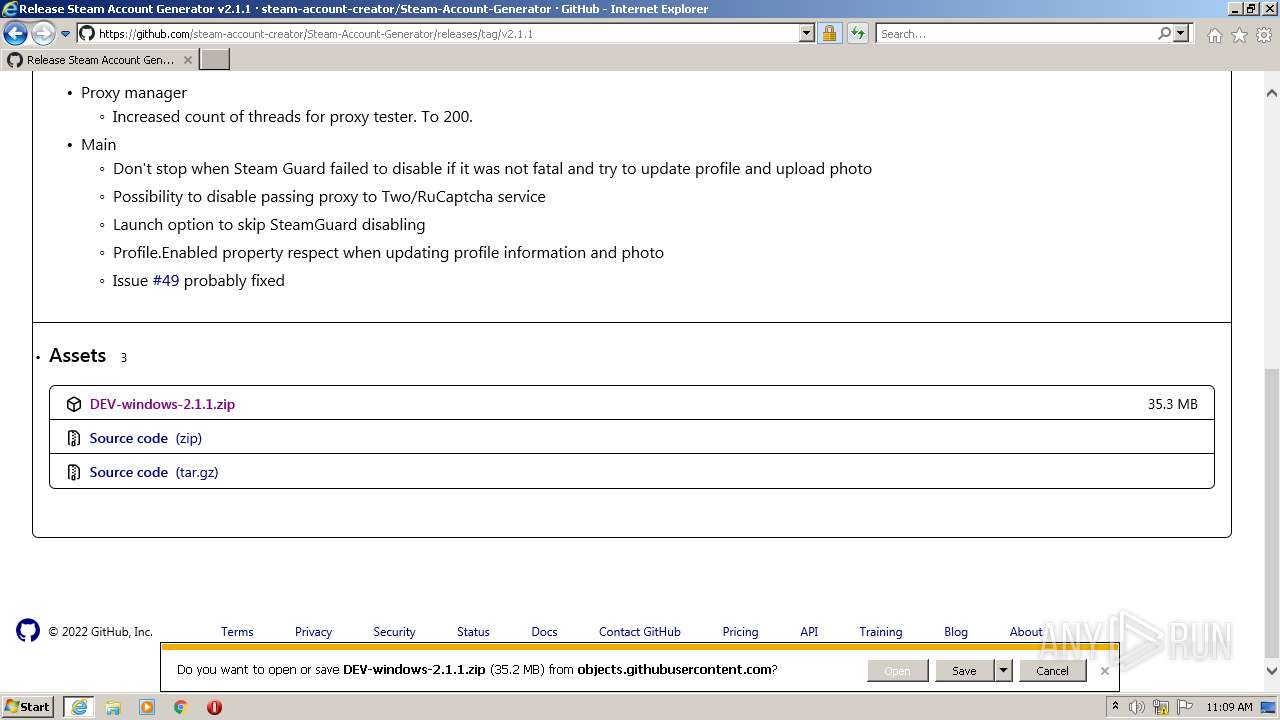
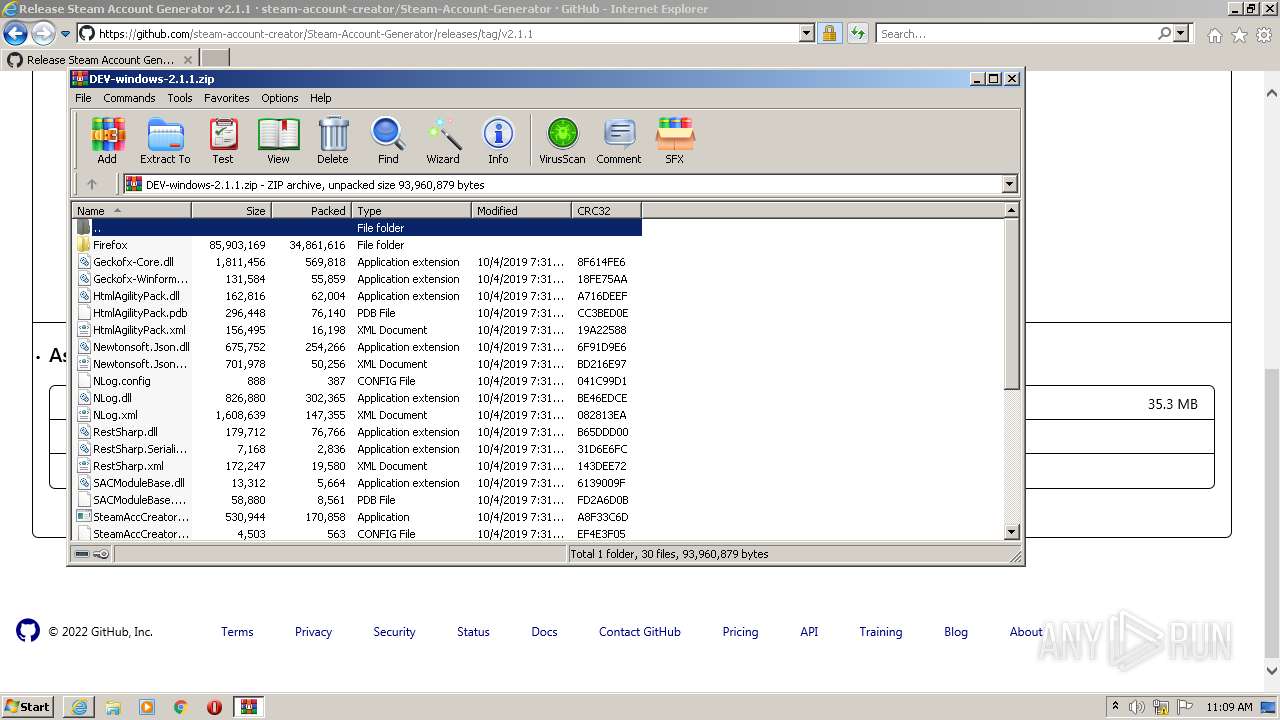
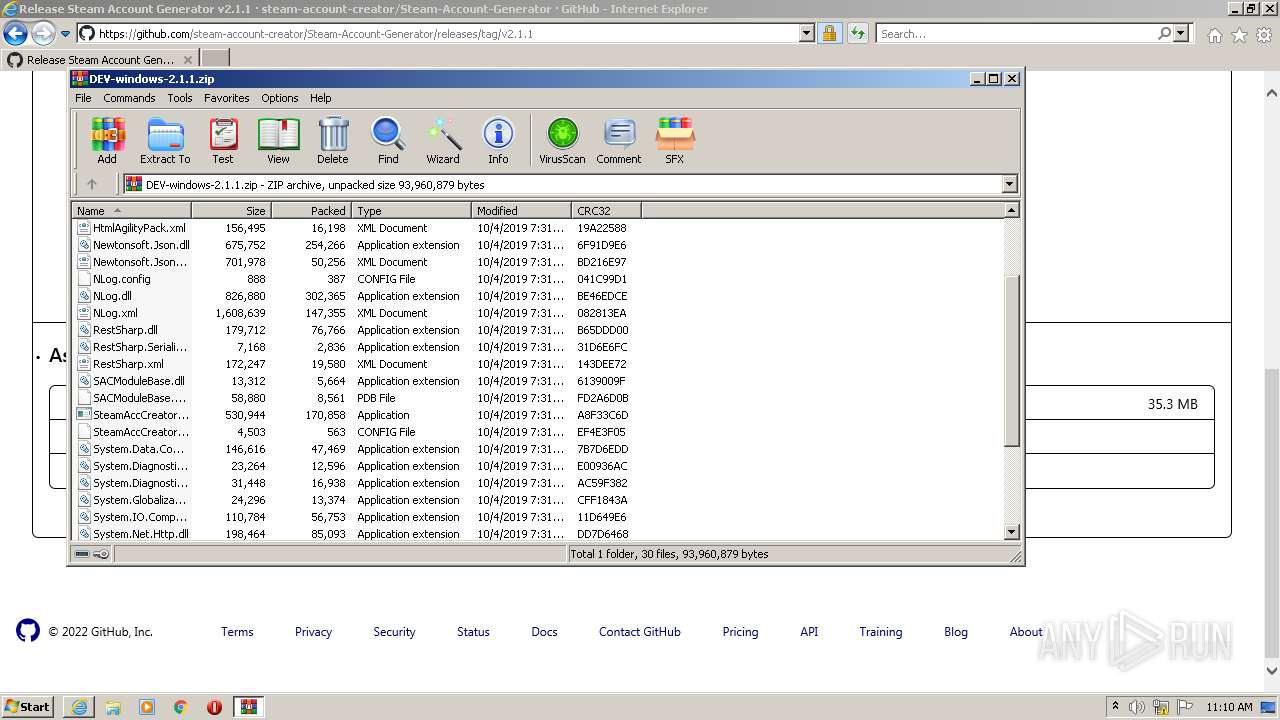
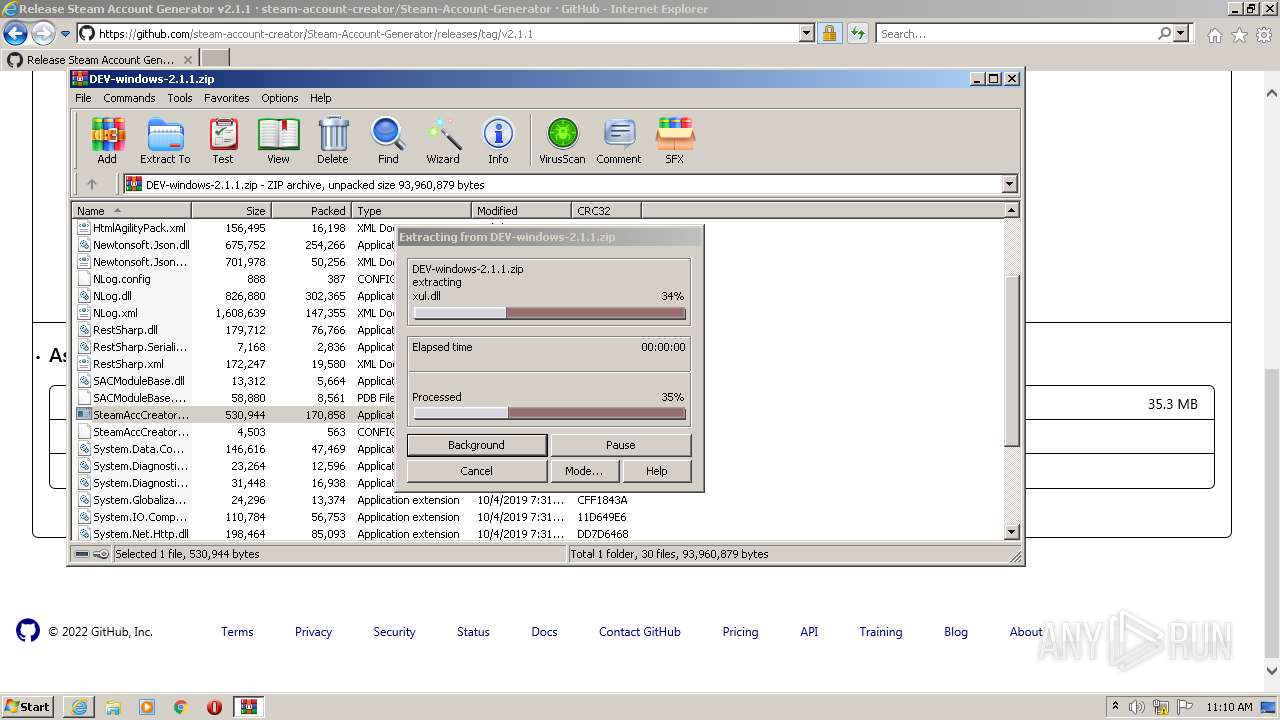
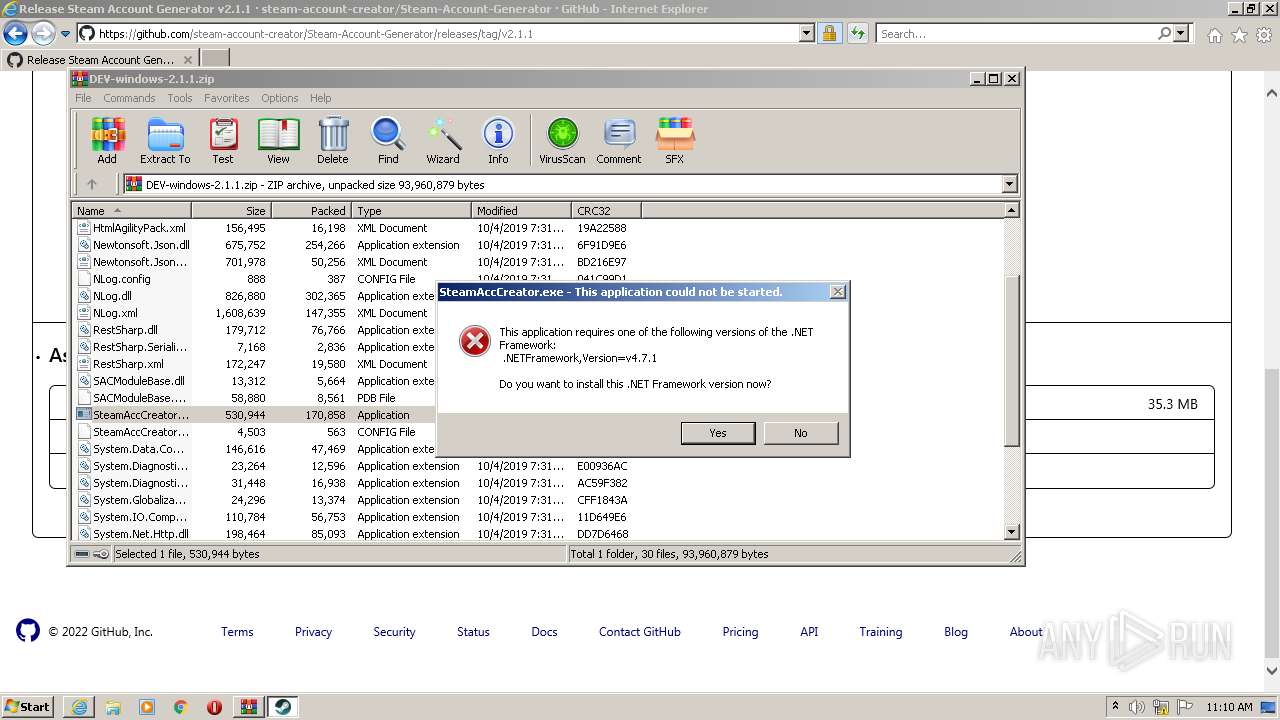
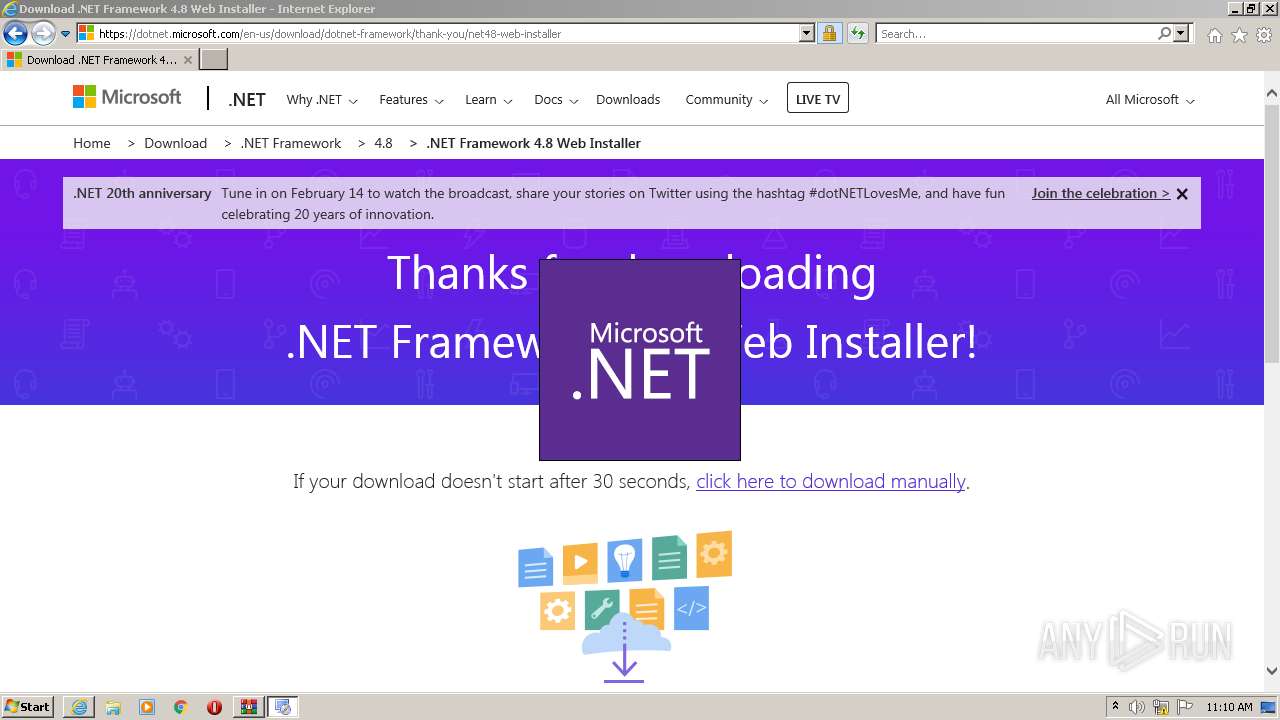
| URL: | https://github.com/EarsKilla/Steam-Account-Generator/releases |
| Full analysis: | https://app.any.run/tasks/a151ea93-f9aa-4963-ac12-c3fcba7185eb |
| Verdict: | Malicious activity |
| Analysis date: | February 04, 2022, 11:09:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0D4F27DBD9B44FD92E81B828EE534788 |
| SHA1: | A53B57C309D00E919BF58DD5013FE18AAEAB96E5 |
| SHA256: | 10F67C94F21D094158DF1C5D37F32EC21670A7CC6834433FA037BE48A07AE0AC |
| SSDEEP: | 3:N8tEd3mhd0aOE2n:2u5knOrn |
MALICIOUS
Application was dropped or rewritten from another process
- SteamAccCreator.exe (PID: 976)
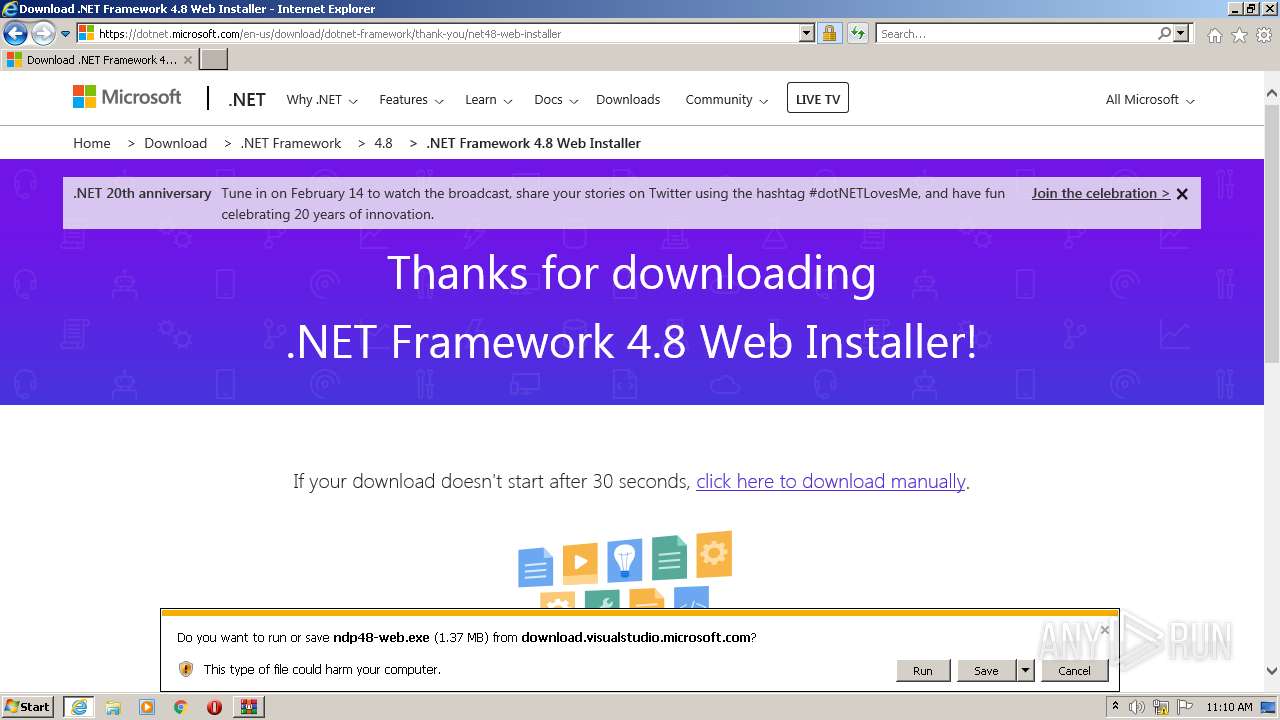
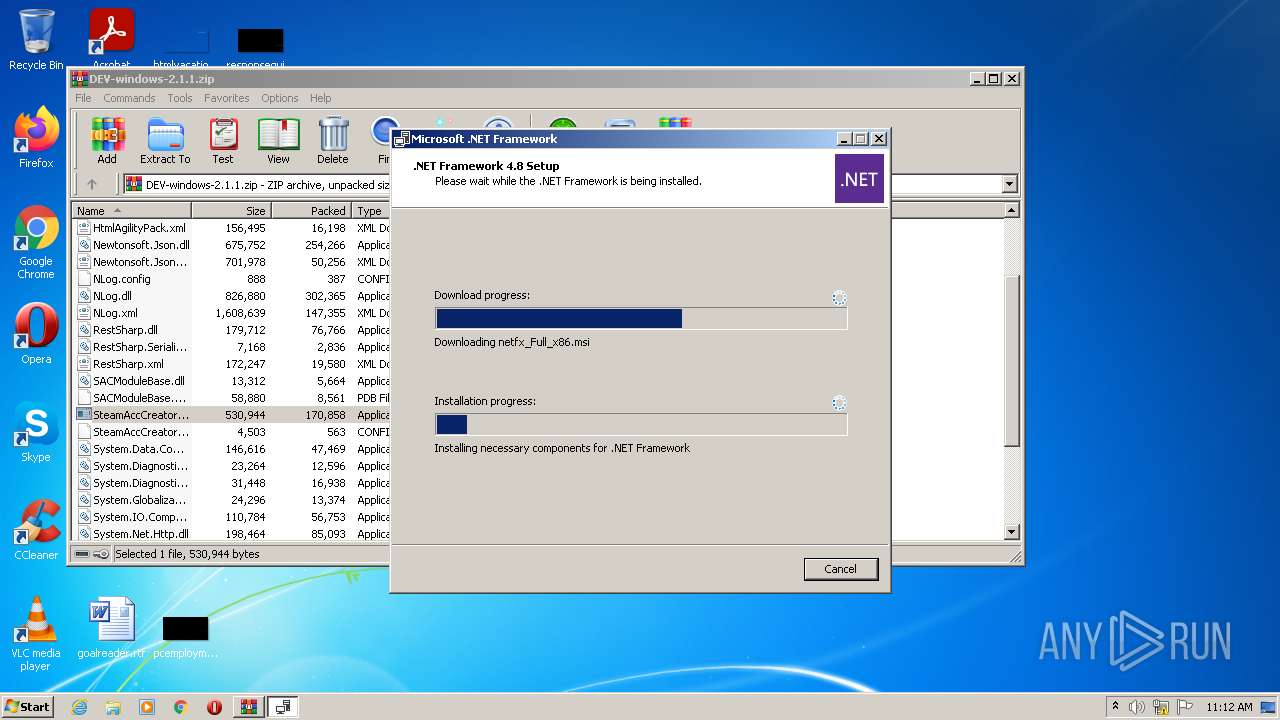
- ndp48-web.exe (PID: 3768)
- ndp48-web.exe (PID: 3044)
- Setup.exe (PID: 1376)
- SetupUtility.exe (PID: 912)
- SetupUtility.exe (PID: 2860)
Drops executable file immediately after starts
- ndp48-web.exe (PID: 3768)
Actions looks like stealing of personal data
- ndp48-web.exe (PID: 3768)
Loads dropped or rewritten executable
- Setup.exe (PID: 1376)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3952)
- ndp48-web.exe (PID: 3768)
- Setup.exe (PID: 1376)
- SetupUtility.exe (PID: 912)
- SetupUtility.exe (PID: 2860)
- TMPD2CA.tmp.exe (PID: 2072)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2244)
- iexplore.exe (PID: 3128)
Checks supported languages
- SteamAccCreator.exe (PID: 976)
- WinRAR.exe (PID: 3952)
- ndp48-web.exe (PID: 3768)
- Setup.exe (PID: 1376)
- SetupUtility.exe (PID: 912)
- SetupUtility.exe (PID: 2860)
- TMPD2CA.tmp.exe (PID: 2072)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3952)
- iexplore.exe (PID: 3128)
- iexplore.exe (PID: 3744)
- ndp48-web.exe (PID: 3768)
- TMPD2CA.tmp.exe (PID: 2072)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3952)
- iexplore.exe (PID: 3744)
- iexplore.exe (PID: 3128)
- ndp48-web.exe (PID: 3768)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3952)
Reads CPU info
- Setup.exe (PID: 1376)
Reads Environment values
- Setup.exe (PID: 1376)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3744)
Checks supported languages
- iexplore.exe (PID: 2244)
- iexplore.exe (PID: 3744)
- iexplore.exe (PID: 3128)
Reads settings of System Certificates
- iexplore.exe (PID: 3744)
- iexplore.exe (PID: 2244)
- iexplore.exe (PID: 3128)
- Setup.exe (PID: 1376)
Reads internet explorer settings
- iexplore.exe (PID: 2244)
- iexplore.exe (PID: 3128)
Reads the computer name
- iexplore.exe (PID: 3744)
- iexplore.exe (PID: 2244)
- iexplore.exe (PID: 3128)
Application launched itself
- iexplore.exe (PID: 3744)
Checks Windows Trust Settings
- iexplore.exe (PID: 2244)
- iexplore.exe (PID: 3744)
- iexplore.exe (PID: 3128)
- Setup.exe (PID: 1376)
Creates files in the user directory
- iexplore.exe (PID: 2244)
- iexplore.exe (PID: 3128)
- iexplore.exe (PID: 3744)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3744)
Changes settings of System certificates
- iexplore.exe (PID: 3744)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3744)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3128)
- SetupUtility.exe (PID: 912)
Reads the date of Windows installation
- iexplore.exe (PID: 3744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
11
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 912 | SetupUtility.exe /aupause | C:\58e1eeaac7ba15117a\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.8.4110.0 built by: NET48REL1LAST_B Modules
| |||||||||||||||
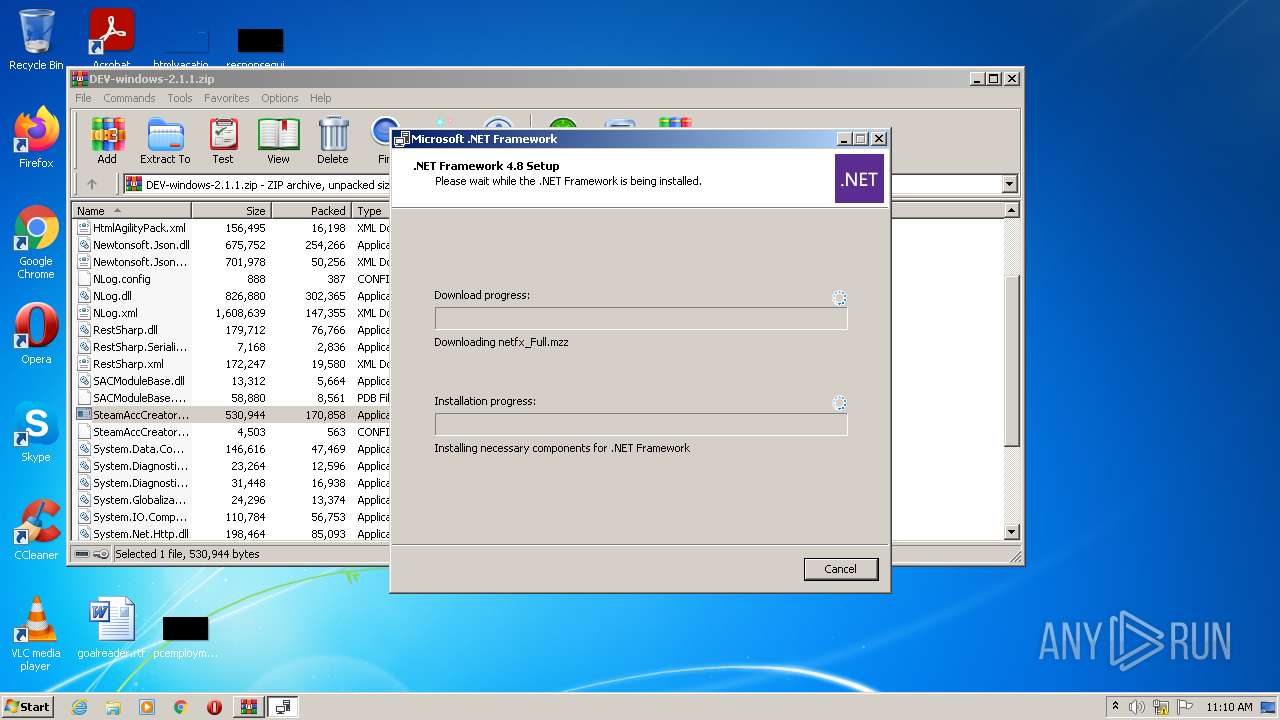
| 976 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3952.15927\SteamAccCreator.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3952.15927\SteamAccCreator.exe | — | WinRAR.exe | |||||||||||
User: admin Company: @DedSec1337 Integrity Level: MEDIUM Description: SteamAccountGenerator Exit code: 2148734720 Version: 2.1.1 Modules
| |||||||||||||||
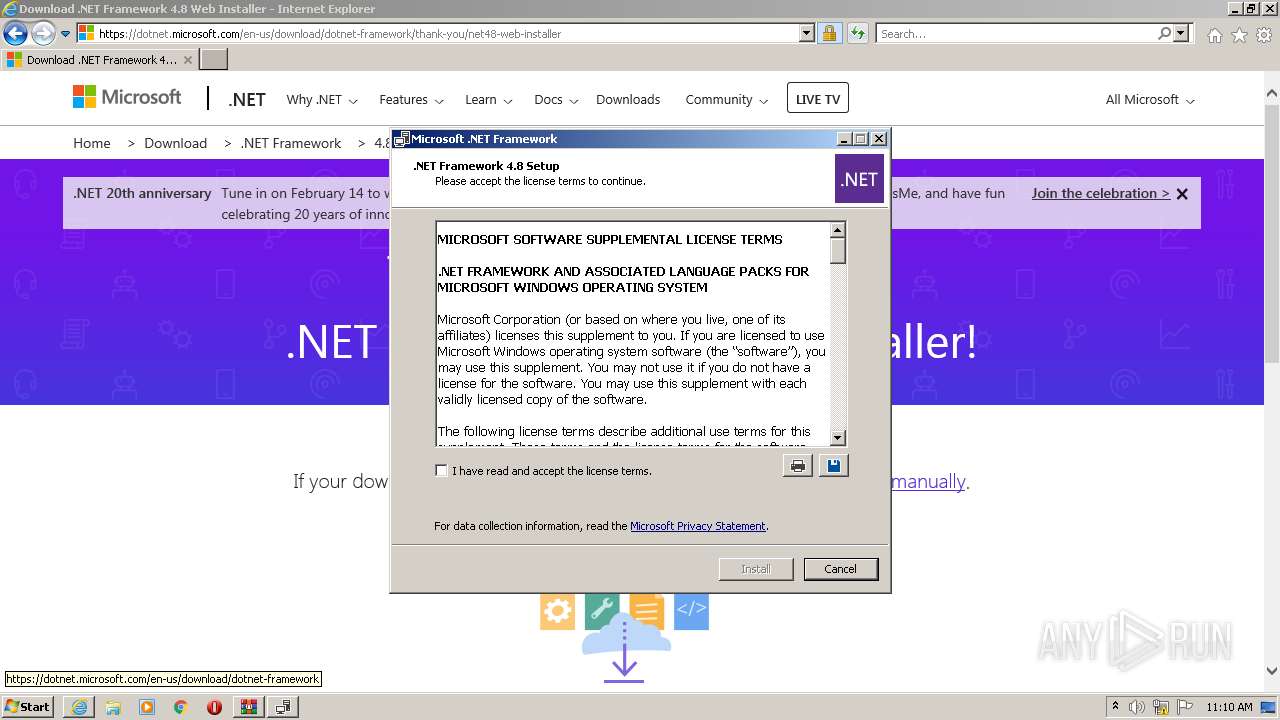
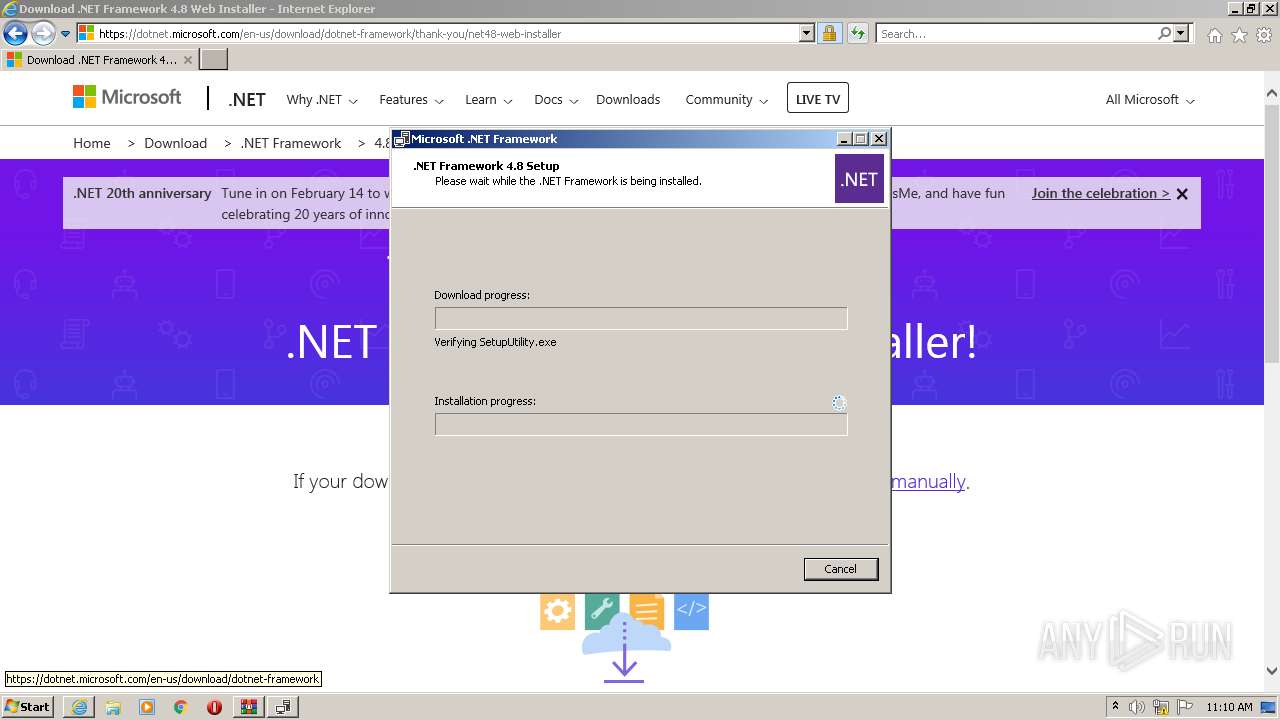
| 1376 | C:\58e1eeaac7ba15117a\\Setup.exe /x86 /x64 /web | C:\58e1eeaac7ba15117a\Setup.exe | ndp48-web.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 0 Version: 14.8.4110.0 built by: NET48REL1LAST_B Modules
| |||||||||||||||
| 2072 | TMPD2CA.tmp.exe /Q /X:C:\58e1eeaac7ba15117a\TMPD2CA.tmp.exe.tmp | C:\58e1eeaac7ba15117a\TMPD2CA.tmp.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.8 Setup Exit code: 0 Version: 4.8.03761.00 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3744 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2860 | SetupUtility.exe /screboot | C:\58e1eeaac7ba15117a\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.8.4110.0 built by: NET48REL1LAST_B Modules
| |||||||||||||||
| 3044 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ndp48-web.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ndp48-web.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.8 Setup Exit code: 3221226540 Version: 4.8.04115.00 Modules
| |||||||||||||||
| 3128 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3744 CREDAT:3544365 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3744 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/EarsKilla/Steam-Account-Generator/releases" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3768 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ndp48-web.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ndp48-web.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.8 Setup Exit code: 0 Version: 4.8.04115.00 Modules
| |||||||||||||||
Total events
28 631
Read events
28 362
Write events
266
Delete events
3
Modification events
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30939575 | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30939575 | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3744) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
74
Suspicious files
29
Text files
158
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2A7611428D62805A3E4E5BC4103D82E4_D0FA13DADFB59BDF00C474952E166CC1 | der | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\releases[1].htm | html | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\NUFVLZQ1.txt | text | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\12B578593FDE07EC53D020B1D5DEBF3B_5D74C2DB556F94499BCD6D74A36958A3 | der | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | der | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2A7611428D62805A3E4E5BC4103D82E4_D0FA13DADFB59BDF00C474952E166CC1 | binary | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\12B578593FDE07EC53D020B1D5DEBF3B_5D74C2DB556F94499BCD6D74A36958A3 | binary | |
MD5:— | SHA256:— | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
74
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
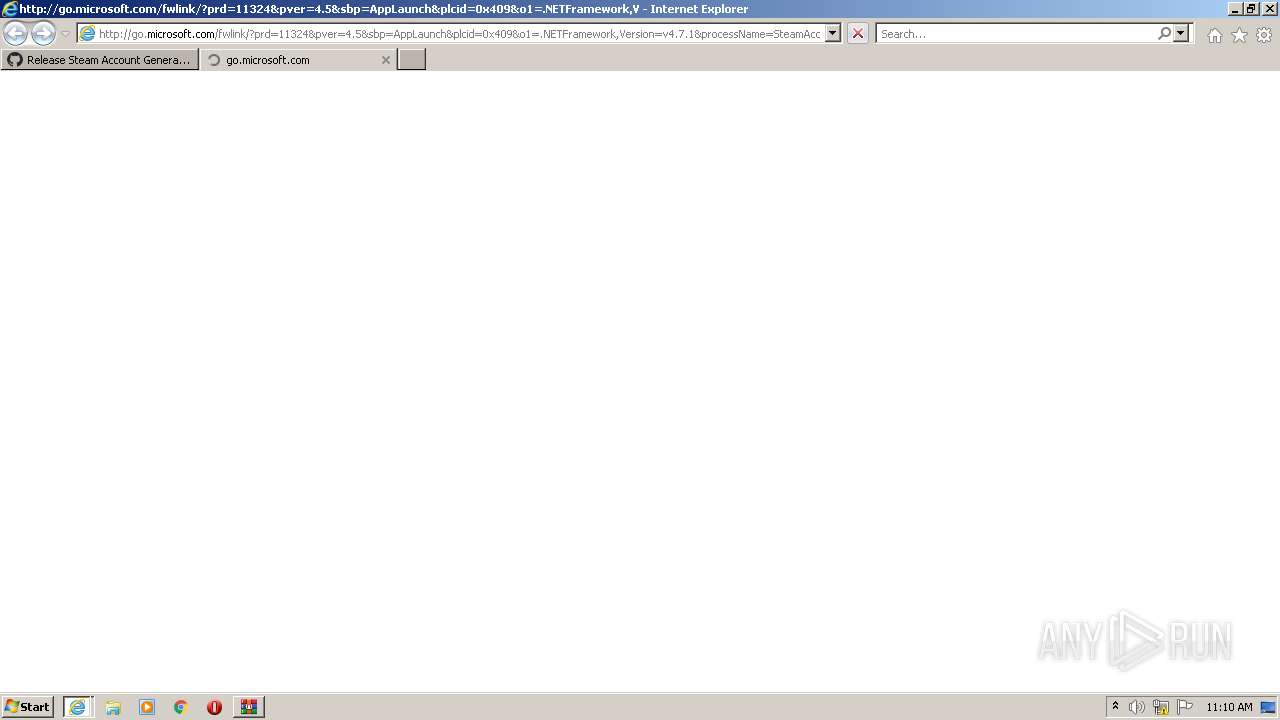
872 | svchost.exe | GET | 302 | 104.111.242.51:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=amd64&o1=netfx_Full_x86.msi | NL | — | — | whitelisted |
872 | svchost.exe | HEAD | 302 | 104.111.242.51:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=amd64&o1=netfx_Full_x86.msi | NL | — | — | whitelisted |
872 | svchost.exe | HEAD | 302 | 104.111.242.51:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=x86&o1=netfx_Full.mzz | NL | — | — | whitelisted |
872 | svchost.exe | GET | 302 | 104.111.242.51:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=x86&o1=netfx_Full.mzz | NL | — | — | whitelisted |
2244 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
2244 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
2244 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAZnA1u7FP1jr8DWqFNO%2FhY%3D | US | der | 471 b | whitelisted |
3744 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2244 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTGMlruL6P9M9B3if1rTM7wyj%2FQKQQUUGGmoNI1xBEqII0fD6xC8M0pz0sCEA6L83cNktGW8Lth%2BTxBZr4%3D | US | der | 279 b | whitelisted |
3128 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2244 | iexplore.exe | 140.82.121.4:443 | github.com | — | US | malicious |
2244 | iexplore.exe | 95.140.236.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | GB | malicious |
3744 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2244 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2244 | iexplore.exe | 185.199.108.154:443 | github.githubassets.com | GitHub, Inc. | NL | suspicious |
3744 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3744 | iexplore.exe | 185.199.108.154:443 | github.githubassets.com | GitHub, Inc. | NL | suspicious |
2244 | iexplore.exe | 185.199.109.133:443 | avatars.githubusercontent.com | GitHub, Inc. | NL | malicious |
2244 | iexplore.exe | 185.199.111.133:443 | avatars.githubusercontent.com | GitHub, Inc. | NL | suspicious |
3744 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
objects.githubusercontent.com |
| shared |