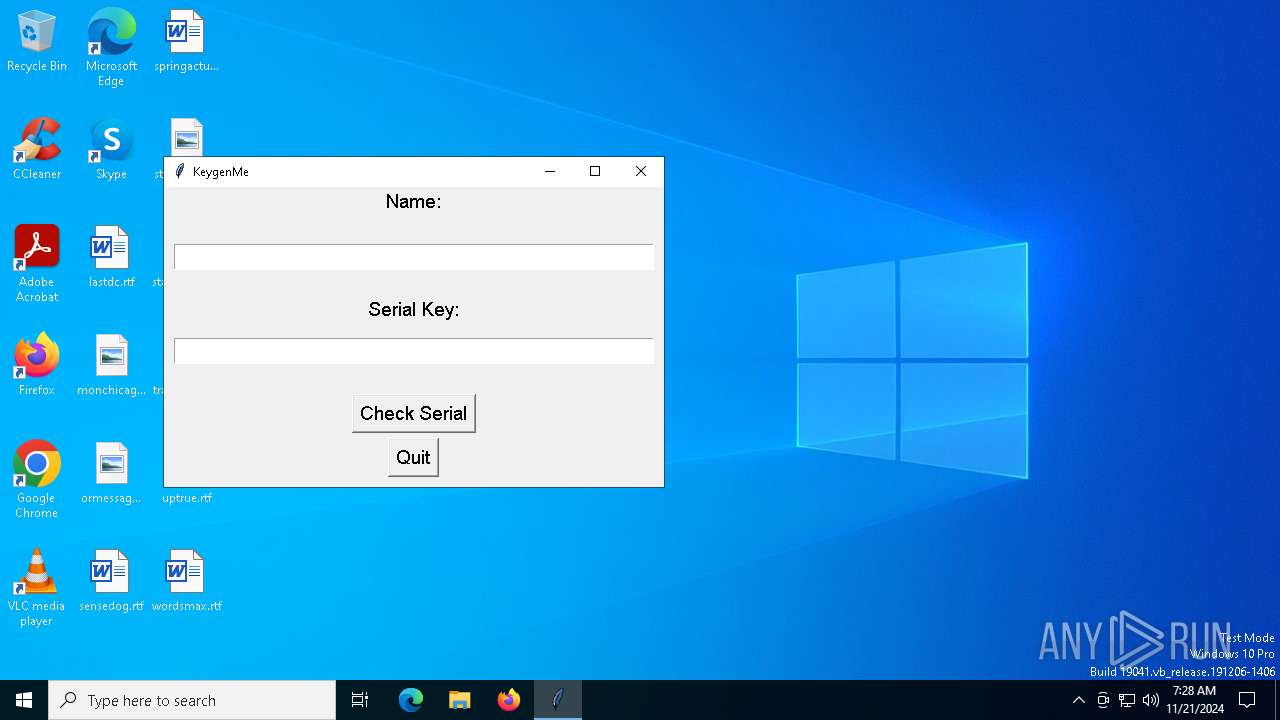
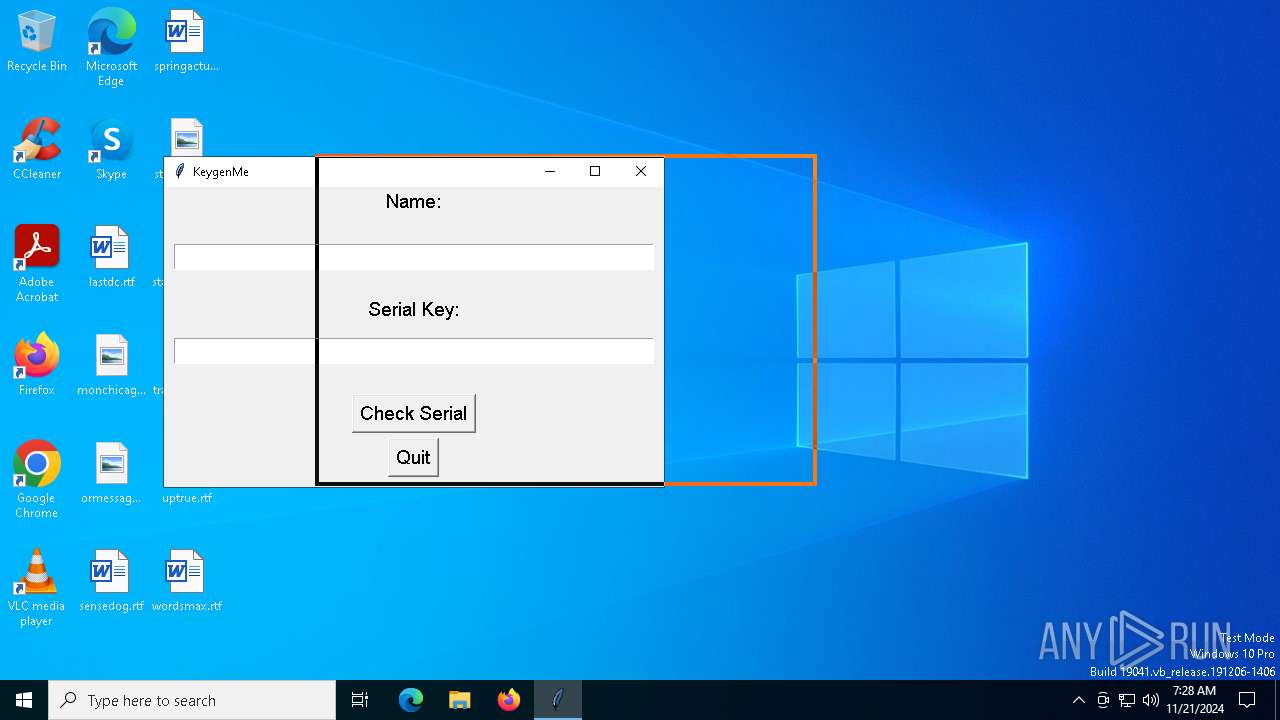
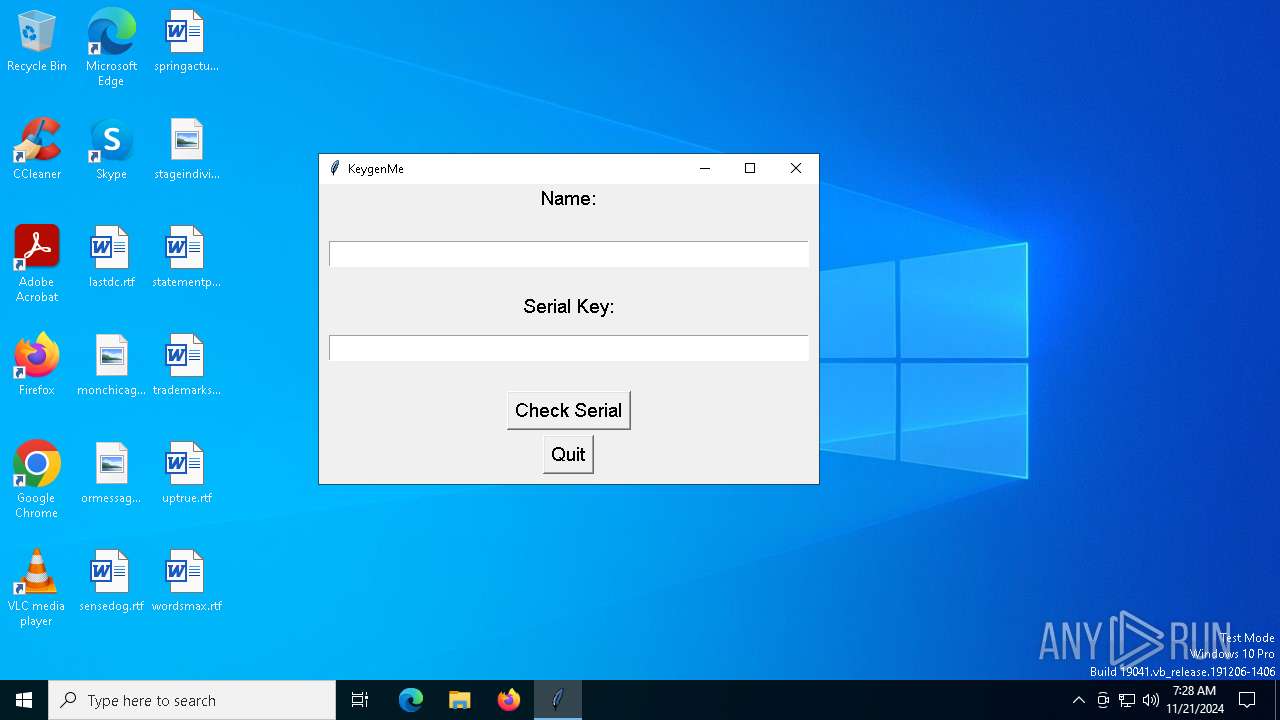
| File name: | Invitation 2.exe |
| Full analysis: | https://app.any.run/tasks/f4fba7dc-13eb-4853-a447-d6c9c6c5897e |
| Verdict: | Malicious activity |
| Analysis date: | November 21, 2024, 07:27:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | E564B030B054264BF772BF8D6DB7F959 |
| SHA1: | EB5E1F3DE56FE9D0E47785ED95EC721AD342B18D |
| SHA256: | 10F5DA850017F03008D61E4D3A58503370097F31224FA7C660E403E434D015A3 |
| SSDEEP: | 98304:PbX30suDFqWXAz+SnzHpAbYpB4RplQ94geo7HNR9dIofyxmxqMogIn/B25cQgDnc:vYYhji+GQzDGI4Y |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- Invitation 2.exe (PID: 4428)
Process drops python dynamic module
- Invitation 2.exe (PID: 4428)
Process drops legitimate windows executable
- Invitation 2.exe (PID: 4428)
Application launched itself
- Invitation 2.exe (PID: 4428)
Executable content was dropped or overwritten
- Invitation 2.exe (PID: 4428)
INFO
Checks supported languages
- Invitation 2.exe (PID: 4428)
Reads the computer name
- Invitation 2.exe (PID: 4428)
PyInstaller has been detected (YARA)
- Invitation 2.exe (PID: 4428)
Create files in a temporary directory
- Invitation 2.exe (PID: 4428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:05:09 15:05:45+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.34 |
| CodeSize: | 165888 |
| InitializedDataSize: | 154624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb310 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
123
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2380 | "C:\Users\admin\AppData\Local\Temp\Invitation 2.exe" | C:\Users\admin\AppData\Local\Temp\Invitation 2.exe | — | Invitation 2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4428 | "C:\Users\admin\AppData\Local\Temp\Invitation 2.exe" | C:\Users\admin\AppData\Local\Temp\Invitation 2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5888 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
Total events
573
Read events
573
Write events
0
Delete events
0
Modification events
Executable files
15
Suspicious files
3
Text files
920
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\python311.dll | executable | |
MD5:E2BD5AE53427F193B42D64B8E9BF1943 | SHA256:C4844B05E3A936B130ADEDB854D3C04D49EE54EDB43E9D36F8C4AE94CCB78400 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\_hashlib.pyd | executable | |
MD5:787B82D4466F393366657B8F1BC5F1A9 | SHA256:241322647BA9F94BDC3AE387413FFB57AE14C8CF88BD564A31FE193C6CA43E37 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\_ssl.pyd | executable | |
MD5:AB0E4FBFFB6977D0196C7D50BC76CF2D | SHA256:680AD2DE8A6CFF927822C1D7DD22112A3E8A824E82A7958EE409A7B9CE45EC70 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\_socket.pyd | executable | |
MD5:26DD19A1F5285712068B9E41808E8FA0 | SHA256:EAABF6B78840DAEAF96B5BDBF06ADF0E4E2994DFEEE5C5E27FEFD824DBDA5220 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\_lzma.pyd | executable | |
MD5:0C7EA68CA88C07AE6B0A725497067891 | SHA256:F74AAF0AA08CF90EB1EB23A474CCB7CB706B1EDE7F911DAF7AE68480765BDF11 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\_decimal.pyd | executable | |
MD5:692C751A1782CC4B54C203546F238B73 | SHA256:C70F05F6BC564FE400527B30C29461E9642FB973F66EEC719D282D3D0B402F93 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\unicodedata.pyd | executable | |
MD5:58F7988B50CBA7B793884F580C7083E1 | SHA256:E36D14CF49CA2AF44FAE8F278E883341167BC380099DAC803276A11E57C9CFA1 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\libcrypto-1_1.dll | executable | |
MD5:9D7A0C99256C50AFD5B0560BA2548930 | SHA256:9B7B4A0AD212095A8C2E35C71694D8A1764CD72A829E8E17C8AFE3A55F147939 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\_tkinter.pyd | executable | |
MD5:6352DB60D88705CE62B5665764529006 | SHA256:4536D9092A366426AA01E1800D9D4DE669928BBCB277F2363D54DF44DA096C31 | |||
| 4428 | Invitation 2.exe | C:\Users\admin\AppData\Local\Temp\_MEI44282\libssl-1_1.dll | executable | |
MD5:BEC0F86F9DA765E2A02C9237259A7898 | SHA256:D74CE01319AE6F54483A19375524AA39D9F5FD91F06CF7DF238CA25E043130FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6096 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6096 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3220 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4036 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4932 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.204.147:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4932 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4932 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |