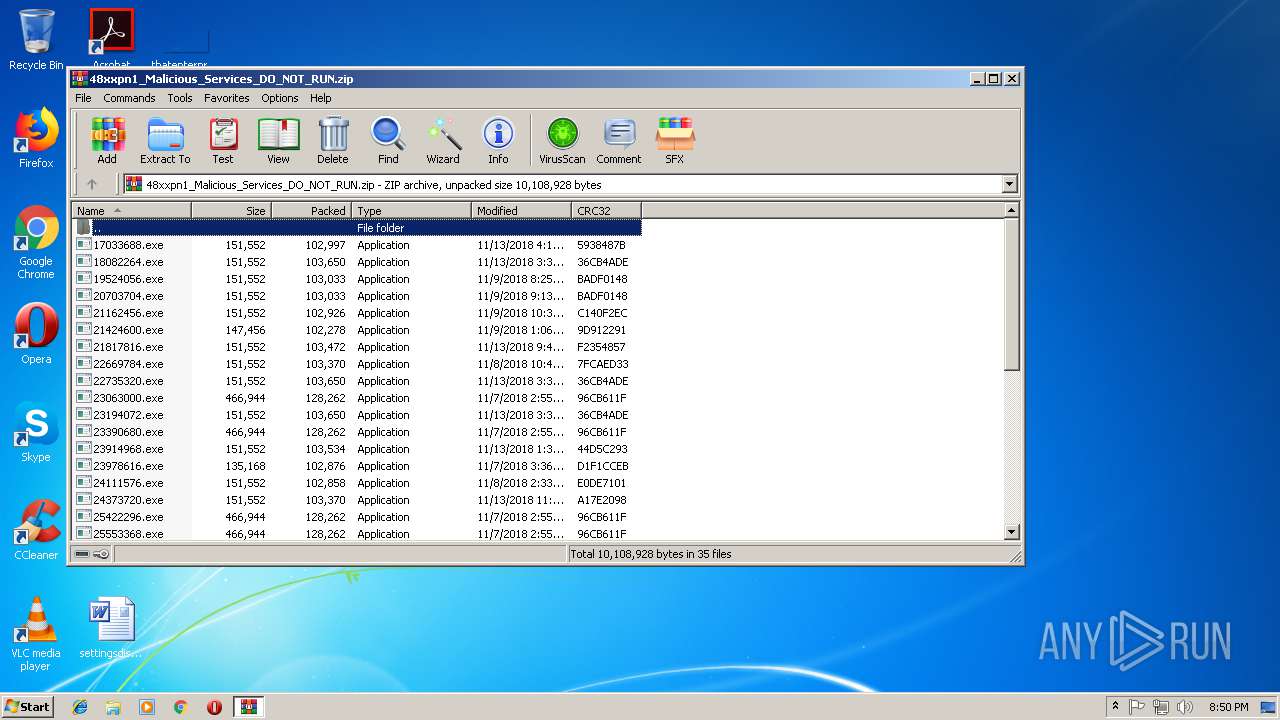
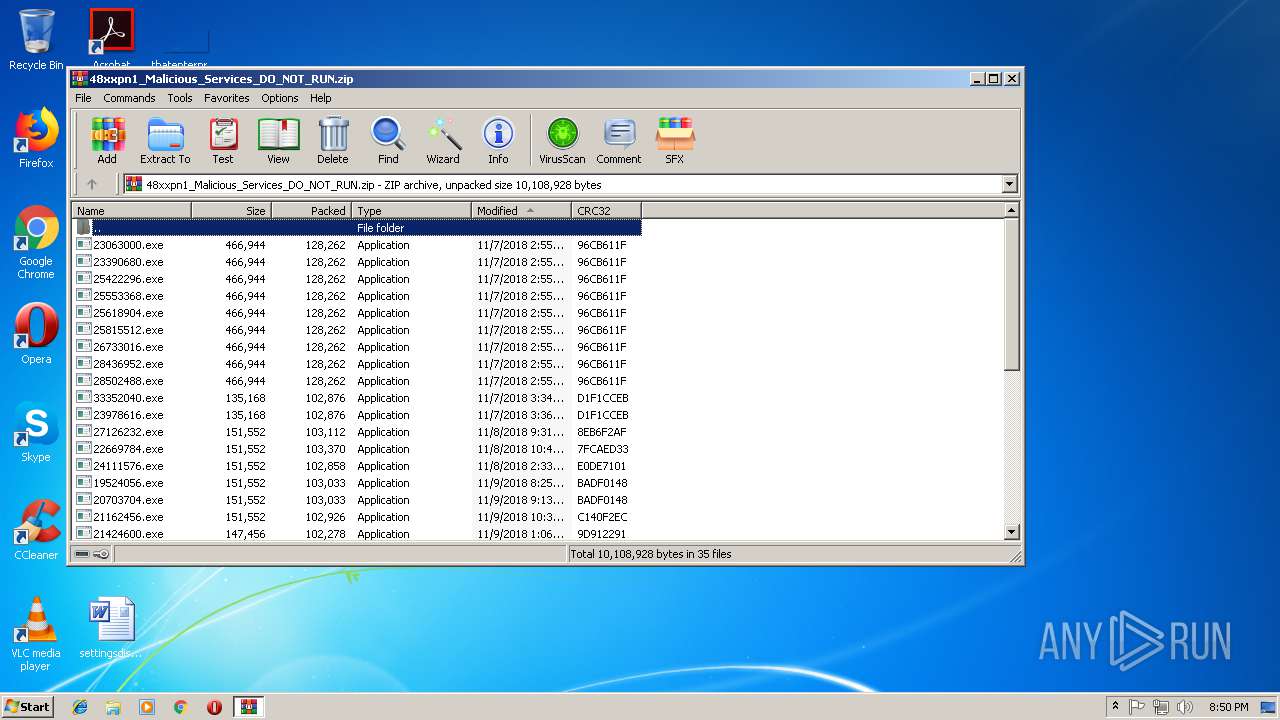
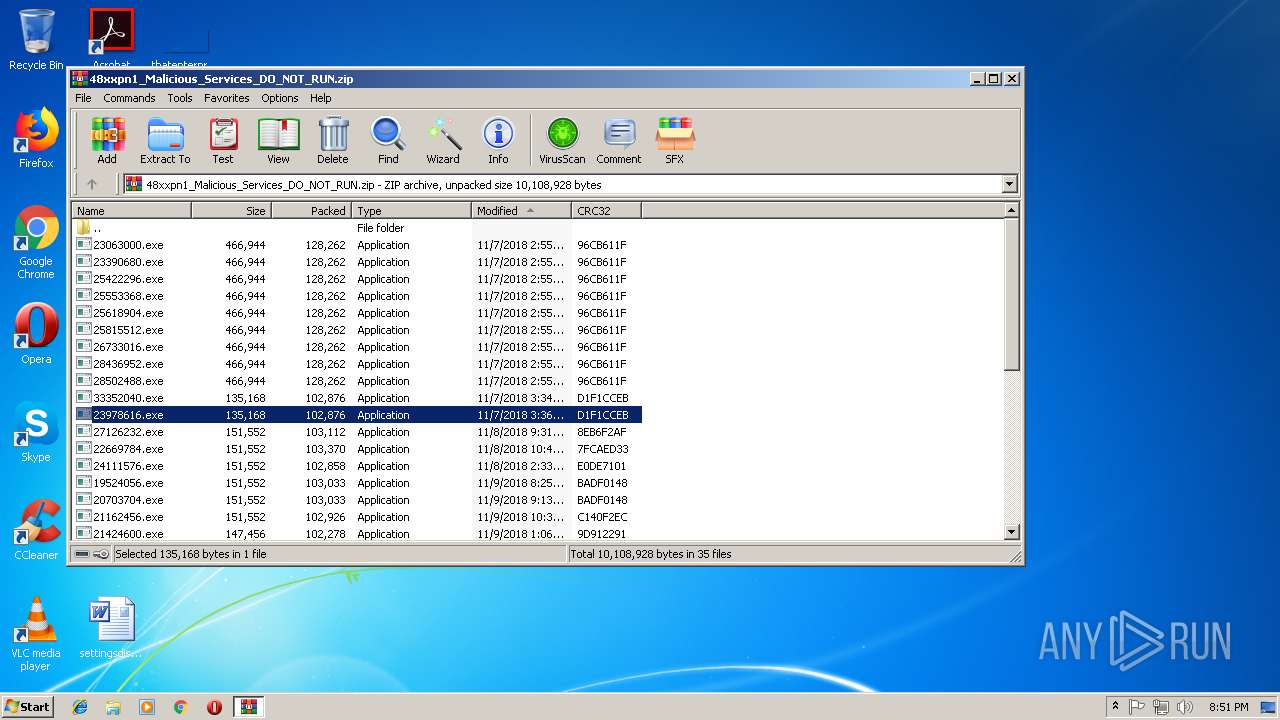
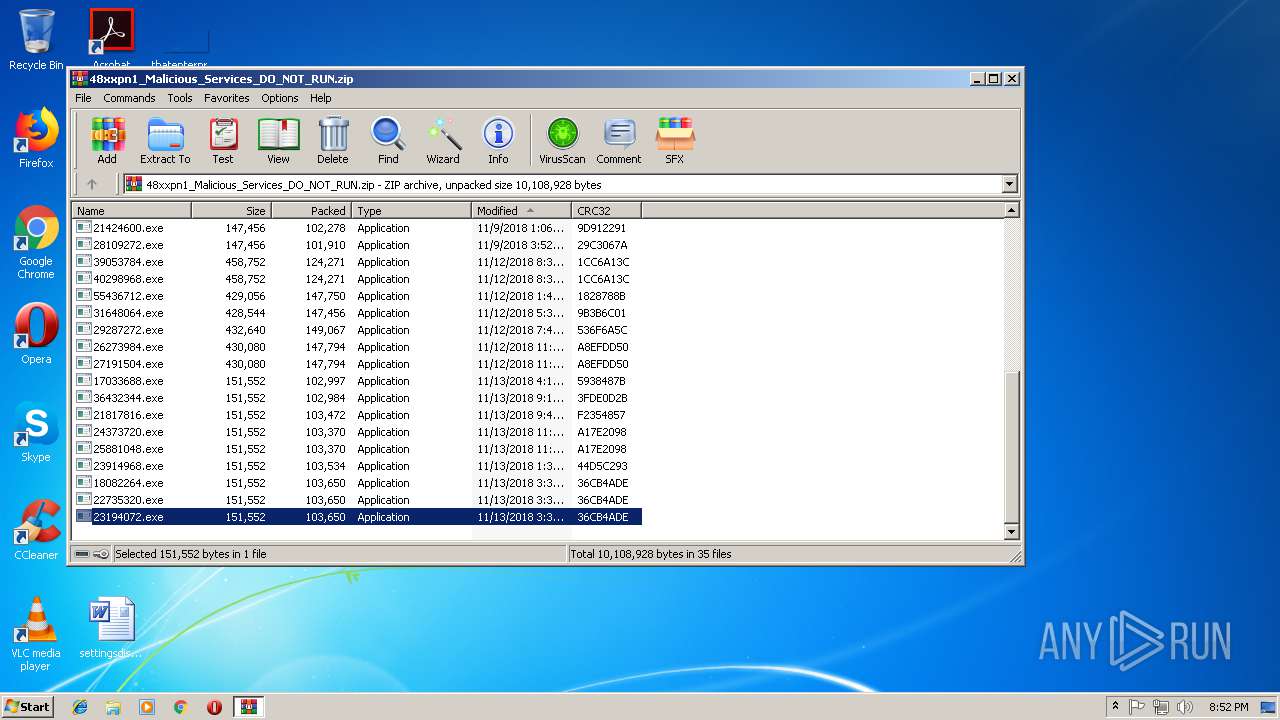
| File name: | 48xxpn1_Malicious_Services_DO_NOT_RUN.zip |
| Full analysis: | https://app.any.run/tasks/c0b6b582-a320-42bb-8261-c0d838e69ebe |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | November 14, 2018, 20:50:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 86D088D8EC7BD9F93FFEDD1FCF8AF3AA |
| SHA1: | D36D03836E893DF065F90E866E4852B30509000B |
| SHA256: | 10DCFC17BF9FE9E66FAA25D722B3451F5ADF2D5AA8F2E0F66C87C68442AA43D6 |
| SSDEEP: | 98304:3Pg4l6l3jfl+APE/2zu6YdBYJYYTHCaJYYTHCzJYYTHCQJYYTHCYJYYTHCQJYYTH:3SlNEoCBYRTiaRTizRTiQRTiYRTiQRTH |
MALICIOUS
Application was dropped or rewritten from another process
- 23978616.exe (PID: 2168)
- 23978616.exe (PID: 3096)
- lpiograd.exe (PID: 996)
- lpiograd.exe (PID: 2620)
- 27126232.exe (PID: 1380)
- 27126232.exe (PID: 2372)
- lpiograd.exe (PID: 676)
- lpiograd.exe (PID: 3996)
- 21162456.exe (PID: 1072)
- 21162456.exe (PID: 2784)
- 55436712.exe (PID: 3756)
- 39053784.exe (PID: 1028)
- 39053784.exe (PID: 1600)
- 55436712.exe (PID: 1192)
- lpiograd.exe (PID: 2356)
- 25881048.exe (PID: 3708)
- 25881048.exe (PID: 3136)
- lpiograd.exe (PID: 3720)
- lpiograd.exe (PID: 1388)
- lpiograd.exe (PID: 2036)
- lpiograd.exe (PID: 3464)
- lpiograd.exe (PID: 3884)
- MVrC7v.exe (PID: 3432)
- 23194072.exe (PID: 3292)
- 23194072.exe (PID: 2808)
- MVrC7v.exe (PID: 1428)
- lpiograd.exe (PID: 2776)
- lpiograd.exe (PID: 3320)
- zAzxlPZwwPUeVPzzH.exe (PID: 1724)
- zAzxlPZwwPUeVPzzH.exe (PID: 2160)
Emotet process was detected
- lpiograd.exe (PID: 996)
- lpiograd.exe (PID: 676)
- lpiograd.exe (PID: 2036)
- lpiograd.exe (PID: 3720)
- lpiograd.exe (PID: 3884)
- lpiograd.exe (PID: 2776)
EMOTET was detected
- lpiograd.exe (PID: 2620)
- lpiograd.exe (PID: 1388)
- lpiograd.exe (PID: 3464)
Connects to CnC server
- lpiograd.exe (PID: 2620)
- lpiograd.exe (PID: 3464)
- lpiograd.exe (PID: 1388)
Changes the autorun value in the registry
- lpiograd.exe (PID: 3464)
- lpiograd.exe (PID: 2620)
SUSPICIOUS
Executable content was dropped or overwritten
- zAzxlPZwwPUeVPzzH.exe (PID: 2160)
- 23978616.exe (PID: 3096)
- WinRAR.exe (PID: 2456)
- 25881048.exe (PID: 3136)
- 55436712.exe (PID: 3756)
- 23194072.exe (PID: 2808)
- lpiograd.exe (PID: 3464)
- MVrC7v.exe (PID: 1428)
- lpiograd.exe (PID: 2620)
Starts itself from another location
- 23978616.exe (PID: 3096)
- 55436712.exe (PID: 3756)
- 25881048.exe (PID: 3136)
- 23194072.exe (PID: 2808)
- MVrC7v.exe (PID: 1428)
- zAzxlPZwwPUeVPzzH.exe (PID: 2160)
Application launched itself
- 27126232.exe (PID: 2372)
- lpiograd.exe (PID: 676)
- lpiograd.exe (PID: 2036)
- zAzxlPZwwPUeVPzzH.exe (PID: 1724)
Connects to unusual port
- lpiograd.exe (PID: 3464)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:11:13 15:39:06 |
| ZipCRC: | 0x36cb4ade |
| ZipCompressedSize: | 103650 |
| ZipUncompressedSize: | 151552 |
| ZipFileName: | 18082264.exe |
Total processes
62
Monitored processes
32
Malicious processes
22
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 676 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | zAzxlPZwwPUeVPzzH.exe | ||||||||||||
User: admin Company: Borland Corporation Integrity Level: MEDIUM Description: Borland C++ Multi-thread RTL (WIN/VCL MT) Exit code: 0 Version: 8.0.0.0 Modules
| |||||||||||||||
| 996 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | 23978616.exe | ||||||||||||
User: admin Company: Micro Integrity Level: MEDIUM Description: Windows M Exit code: 0 Version: 6. Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.19847\39053784.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.19847\39053784.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Micro Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.1 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.19514\21162456.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.19514\21162456.exe | — | 21162456.exe | |||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 1192 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.20128\55436712.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.20128\55436712.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Utility Library Exit code: 0 Version: 3.5.0.1176 Modules
| |||||||||||||||
| 1380 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.18494\27126232.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.18494\27126232.exe | — | 27126232.exe | |||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 1388 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | lpiograd.exe | ||||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 1428 | "C:\Users\admin\AppData\Local\Microsoft\Windows\MVrC7v.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\MVrC7v.exe | MVrC7v.exe | ||||||||||||
User: admin Company: Borland Corporation Integrity Level: MEDIUM Description: Borland C++ Multi-thread RTL (WIN/VCL MT) Exit code: 0 Version: 8.0.0.0 Modules
| |||||||||||||||
| 1600 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.19847\39053784.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.19847\39053784.exe | — | 39053784.exe | |||||||||||
User: admin Company: Micro Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.1 Modules
| |||||||||||||||
| 1724 | "C:\Users\admin\AppData\Local\Microsoft\Windows\zAzxlPZwwPUeVPzzH.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\zAzxlPZwwPUeVPzzH.exe | — | lpiograd.exe | |||||||||||
User: admin Company: Borland Corporation Integrity Level: MEDIUM Description: Borland C++ Multi-thread RTL (WIN/VCL MT) Exit code: 0 Version: 8.0.0.0 Modules
| |||||||||||||||
Total events
756
Read events
721
Write events
35
Delete events
0
Modification events
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\48xxpn1_Malicious_Services_DO_NOT_RUN.zip | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 3 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
253
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\18082264.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\24373720.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\23194072.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\22735320.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\23914968.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\17033688.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\25881048.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\21817816.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\36432344.exe | executable | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.16750\21162456.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
7
DNS requests
0
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3464 | lpiograd.exe | GET | — | 83.110.100.209:443 | http://83.110.100.209:443/ | AE | — | — | malicious |
1388 | lpiograd.exe | GET | — | 83.110.100.209:443 | http://83.110.100.209:443/ | AE | — | — | malicious |
3464 | lpiograd.exe | GET | — | 73.32.166.189:443 | http://73.32.166.189:443/ | US | — | — | malicious |
3320 | lpiograd.exe | GET | — | 83.110.100.209:443 | http://83.110.100.209:443/ | AE | — | — | malicious |
2620 | lpiograd.exe | GET | 200 | 136.56.103.201:80 | http://136.56.103.201/ | US | binary | 148 Kb | malicious |
3464 | lpiograd.exe | GET | 200 | 68.102.169.43:8080 | http://68.102.169.43:8080/ | US | binary | 148 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2620 | lpiograd.exe | 136.56.103.201:80 | — | Google Fiber Inc. | US | malicious |
1388 | lpiograd.exe | 83.110.100.209:443 | — | Emirates Telecommunications Corporation | AE | malicious |
3464 | lpiograd.exe | 83.110.100.209:443 | — | Emirates Telecommunications Corporation | AE | malicious |
3464 | lpiograd.exe | 73.32.166.189:443 | — | Comcast Cable Communications, LLC | US | malicious |
3464 | lpiograd.exe | 69.112.171.184:8443 | — | Cablevision Systems Corp. | US | malicious |
3464 | lpiograd.exe | 68.102.169.43:8080 | — | Cox Communications Inc. | US | malicious |
3320 | lpiograd.exe | 83.110.100.209:443 | — | Emirates Telecommunications Corporation | AE | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
2620 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1388 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3464 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3464 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3464 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
5 ETPRO signatures available at the full report