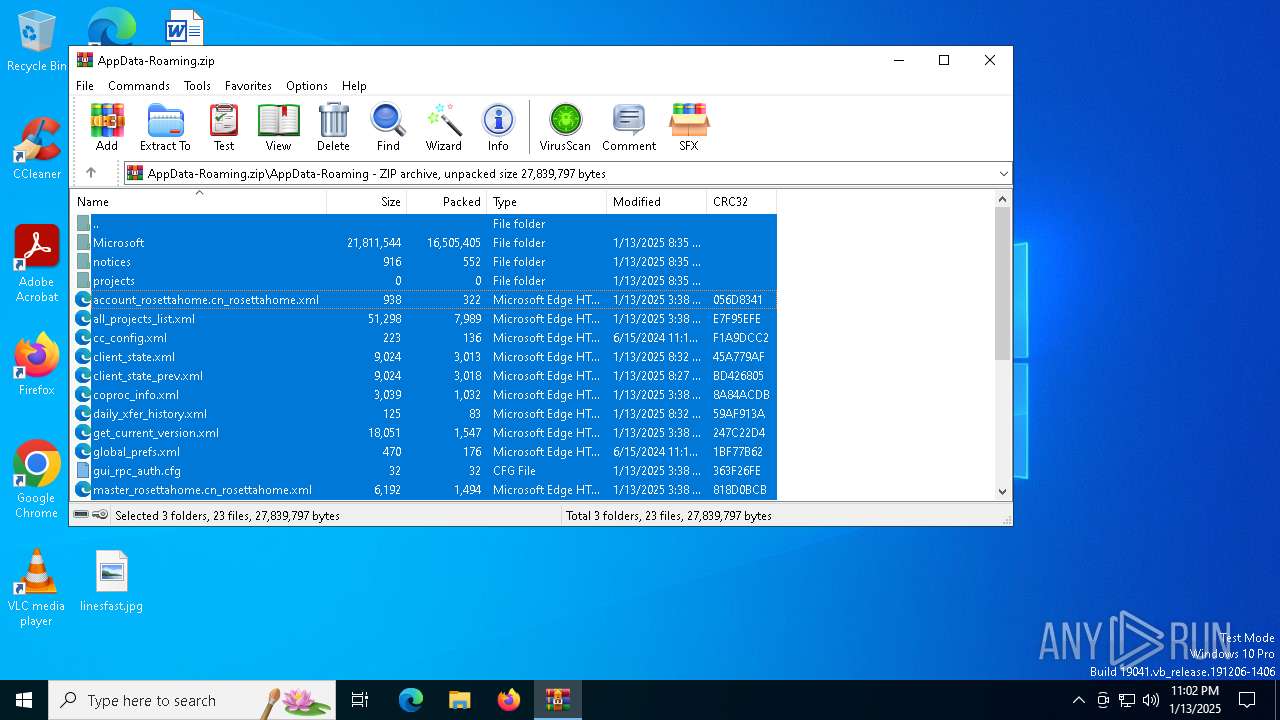
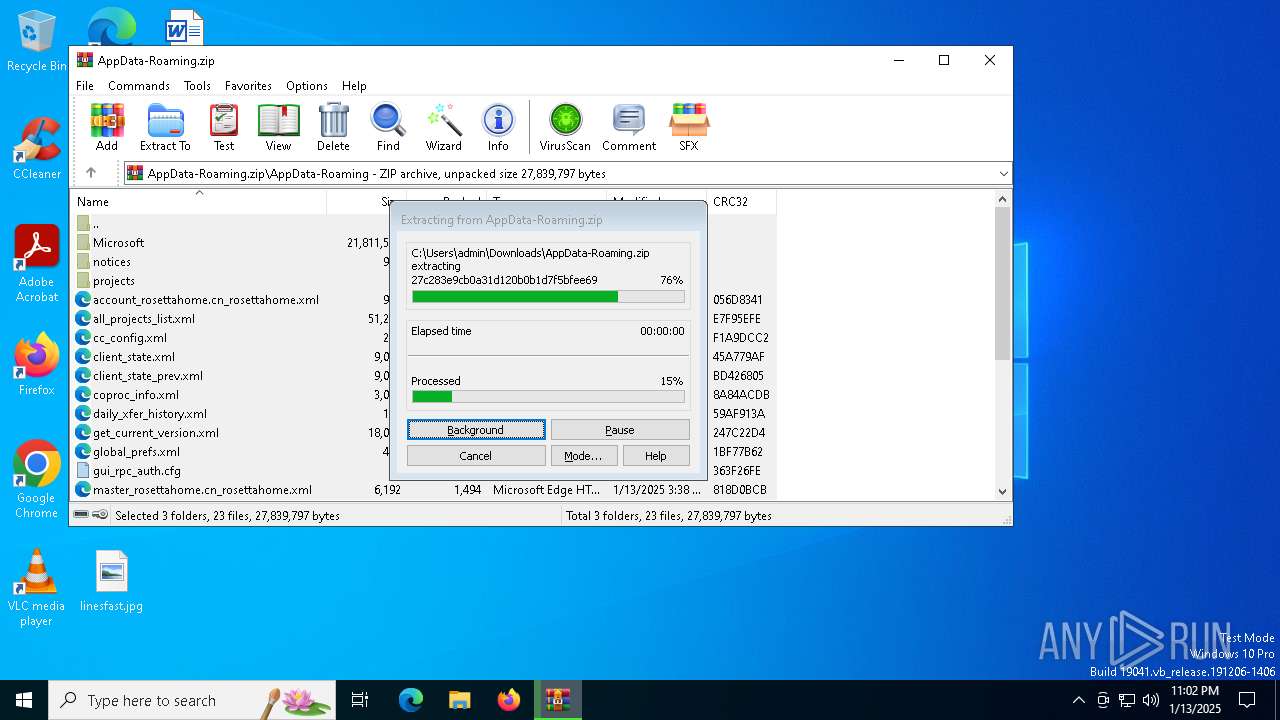
| File name: | AppData-Roaming.zip |
| Full analysis: | https://app.any.run/tasks/18e80612-b44f-47c5-8bcc-42e657bfe045 |
| Verdict: | Malicious activity |
| Analysis date: | January 13, 2025, 23:02:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 174F9F9A9D24EA4471D625445124BEF2 |
| SHA1: | B3709AA78244978AC89791ABAF84E4E0D34FBC0B |
| SHA256: | 10D8718E2E74DE224760061ADC7BB11B058CF7BEDD8507C3FB70C909BCEA386D |
| SSDEEP: | 196608:YnxkaEKaDknZLXcP0OMSqzefrt4nhfmt6IcvIc:YnxkaE7YlMPPfrkh+t5aJ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6656)
SUSPICIOUS
Application launched itself
- SecurityHealthService.exe (PID: 2800)
There is functionality for VM detection antiVM strings (YARA)
- SecurityHealthService.exe (PID: 2800)
There is functionality for VM detection VirtualBox (YARA)
- SecurityHealthService.exe (PID: 2800)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6656)
- WinRAR.exe (PID: 7116)
The process uses the downloaded file
- WinRAR.exe (PID: 6656)
- WinRAR.exe (PID: 7116)
The sample compiled with english language support
- WinRAR.exe (PID: 6656)
- WinRAR.exe (PID: 7116)
Manual execution by a user
- SecurityHealthService.exe (PID: 2800)
- WinRAR.exe (PID: 7116)
Checks supported languages
- SecurityHealthService.exe (PID: 2800)
- SecurityHealthService.exe (PID: 6456)
Creates files or folders in the user directory
- SecurityHealthService.exe (PID: 6456)
- SecurityHealthService.exe (PID: 2800)
Reads the computer name
- SecurityHealthService.exe (PID: 2800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:13 22:51:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | AppData-Roaming/ |
Total processes
121
Monitored processes
7
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
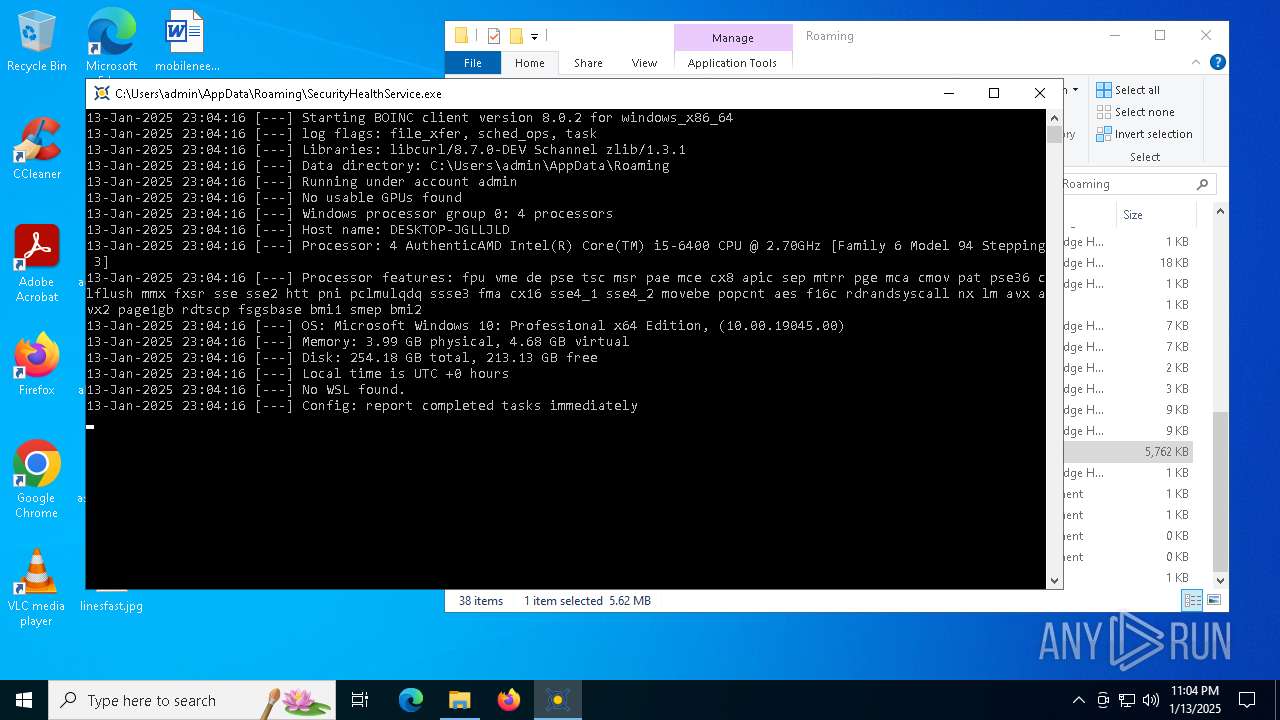
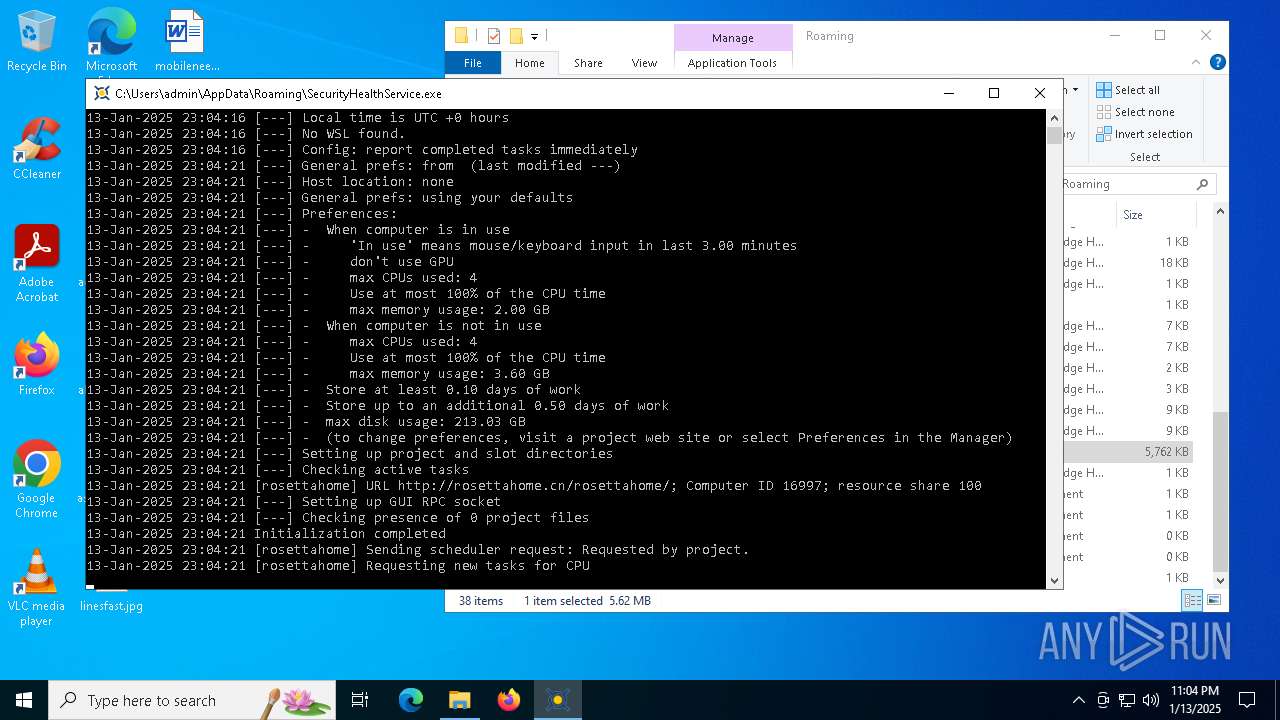
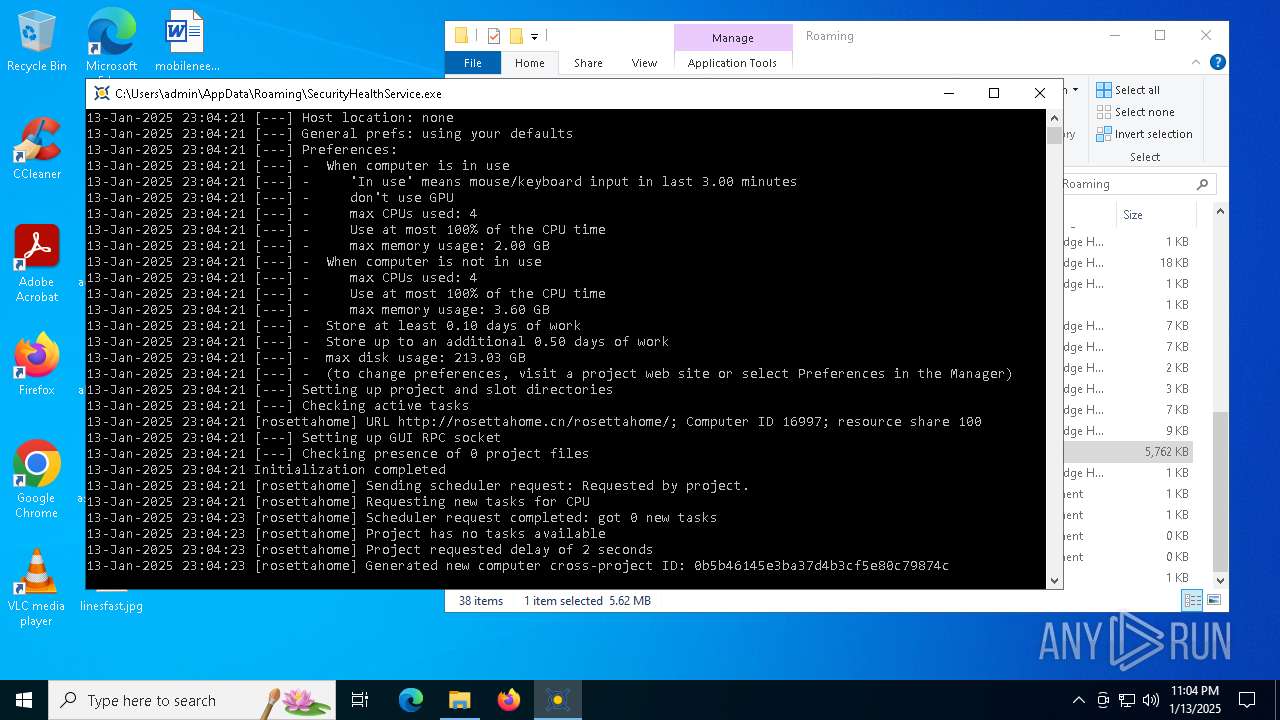
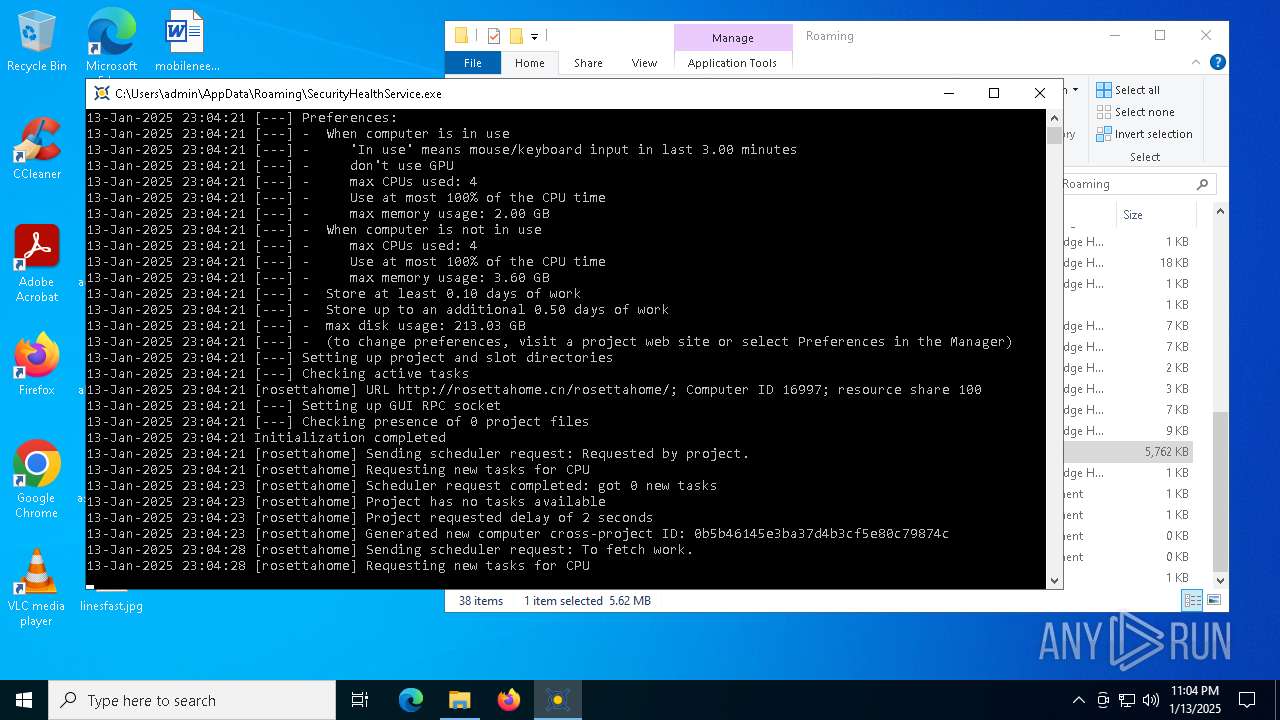
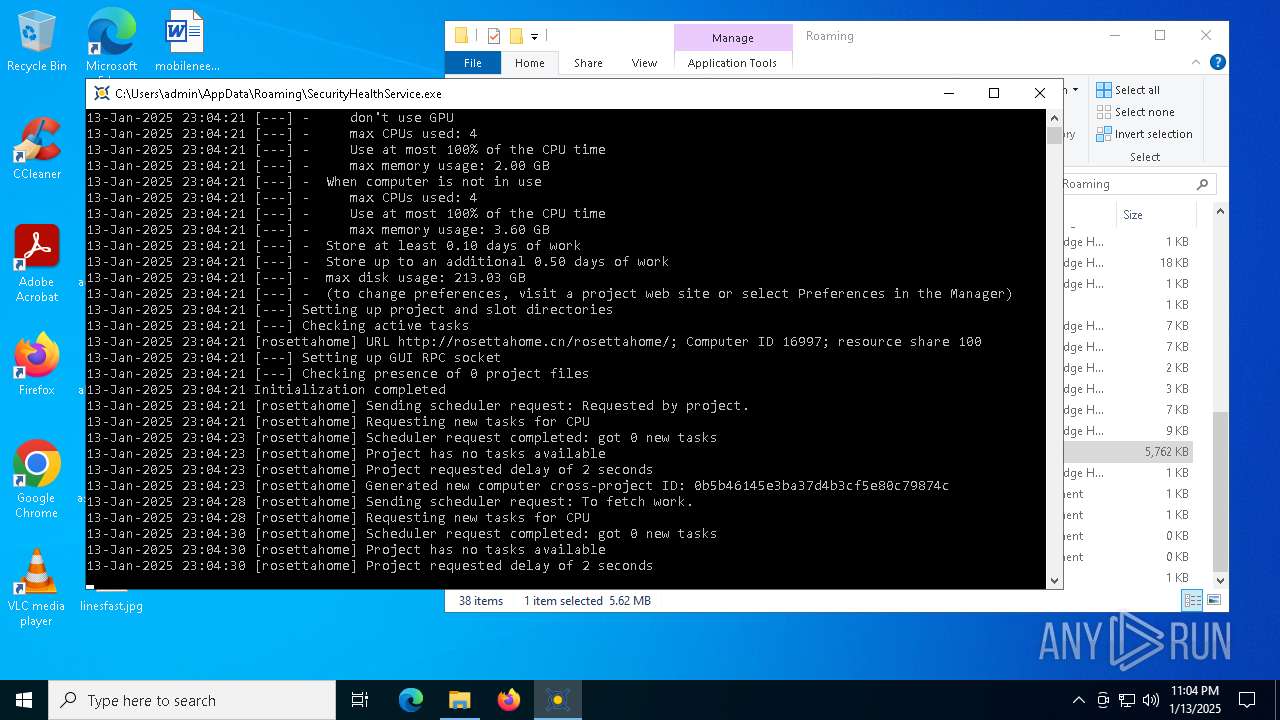
| 2800 | "C:\Users\admin\AppData\Roaming\SecurityHealthService.exe" | C:\Users\admin\AppData\Roaming\SecurityHealthService.exe | explorer.exe | ||||||||||||
User: admin Company: Space Sciences Laboratory Integrity Level: MEDIUM Description: BOINC client Exit code: 0 Version: 8.0.2 Modules
| |||||||||||||||
| 5720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SecurityHealthService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6456 | "C:\Users\admin\AppData\Roaming\SecurityHealthService.exe" --detect_gpus --dir "C:\Users\admin\AppData\Roaming" | C:\Users\admin\AppData\Roaming\SecurityHealthService.exe | — | SecurityHealthService.exe | |||||||||||
User: admin Company: Space Sciences Laboratory Integrity Level: MEDIUM Description: BOINC client Exit code: 0 Version: 8.0.2 Modules
| |||||||||||||||
| 6656 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\AppData-Roaming.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6932 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\AppData-Roaming.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 030
Read events
2 997
Write events
33
Delete events
0
Modification events
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\AppData-Roaming.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
3
Suspicious files
0
Text files
97
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\Microsoft\27c283e9cb0a31d120b0b1d7f5bfee69 | — | |
MD5:— | SHA256:— | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\sched_request_rosettahome.cn_rosettahome.xml | text | |
MD5:12C6B6B06DFF3B9CA7093388D442E322 | SHA256:2B80324F0DE9CC32946B9BB3CB1952006C6056A63AF9FBF69818811171D294A0 | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\daily_xfer_history.xml | text | |
MD5:98F8CA18B368AEE93BBB363E194D4321 | SHA256:D233BA2CA3ED4F45AE09C5A9A4368CF80FC4547E1E7B695E097002A946802D8E | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\get_current_version.xml | xml | |
MD5:5B4F78E069418E6AF6752FD88292F5B8 | SHA256:C7AC04D285AE055053BED8CD2E8B4B6FAF7CFB158129E7147E46BF2B57853985 | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\notices\rosettahome.cn_rosettahome_notices.php.xml | xml | |
MD5:91738730CD7D140D4C8F317F610EA2DF | SHA256:24D2B02D9108915E90B12B0A4352E8582048282527BE73354E4BC4652A17F798 | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\sched_request_rosettahome.top_rosettahome.xml | text | |
MD5:F14ADFF6E3099570E2D16786155C3D19 | SHA256:6B20BD5462A4AC91BB284D09BCE674A043BD3BB5BD7D1D04801CD14E8470E515 | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\statistics_rosettahome.cn_rosettahome.xml | text | |
MD5:8BFDA7C3BF44F9A7811850909557B58F | SHA256:9A1789F6228F8B43F2FF9B1E5D8AF7A2B998C2BD41AEBA094456F5D179C6A72E | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\notices\archive_rosettahome.cn_rosettahome_notices.php.xml | text | |
MD5:6B0A8CC3F90BFEA8C69440F259D95BA4 | SHA256:269B3AD12D598980B0EB1673443E84FAC6D7F2B66639B2B72F284DDFB38FD7D9 | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\account_rosettahome.cn_rosettahome.xml | text | |
MD5:2D2869CF40771468F523051ED737CB33 | SHA256:191E62287F8136AEAED806639F7FFFCBA7404575C5AF12108582831200450AF9 | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6656.15683\AppData-Roaming\gui_rpc_auth.cfg | text | |
MD5:F5E609423F89FA115319D39DDB4DE923 | SHA256:315E9B79ADC0D69835F5506319470262076A8C5C4BE1971ADEB7A815F19A368C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
57
DNS requests
16
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2800 | SecurityHealthService.exe | GET | 200 | 104.238.61.8:80 | http://rosettahome.cn/rosettahome/notices.php?userid=1&auth=1_1a362b2ad50985e203845fe44682096e | unknown | — | — | unknown |
2800 | SecurityHealthService.exe | POST | 200 | 104.238.61.8:80 | http://rosettahome.top/rosettahome_cgi/cgi | unknown | — | — | unknown |
2800 | SecurityHealthService.exe | POST | 200 | 104.238.61.8:80 | http://rosettahome.top/rosettahome_cgi/cgi | unknown | — | — | unknown |
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 13.85.23.206:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
3560 | SIHClient.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3560 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | POST | 403 | 23.218.209.163:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.138:443 | https://login.live.com/RST2.srf | unknown | xml | 1.25 Kb | whitelisted |
3560 | SIHClient.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2800 | SecurityHealthService.exe | 104.238.61.8:80 | rosettahome.cn | ASN-QUADRANET-GLOBAL | US | unknown |
5064 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3560 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
3560 | SIHClient.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3560 | SIHClient.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
rosettahome.cn |
| unknown |
rosettahome.top |
| unknown |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2800 | SecurityHealthService.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2800 | SecurityHealthService.exe | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |