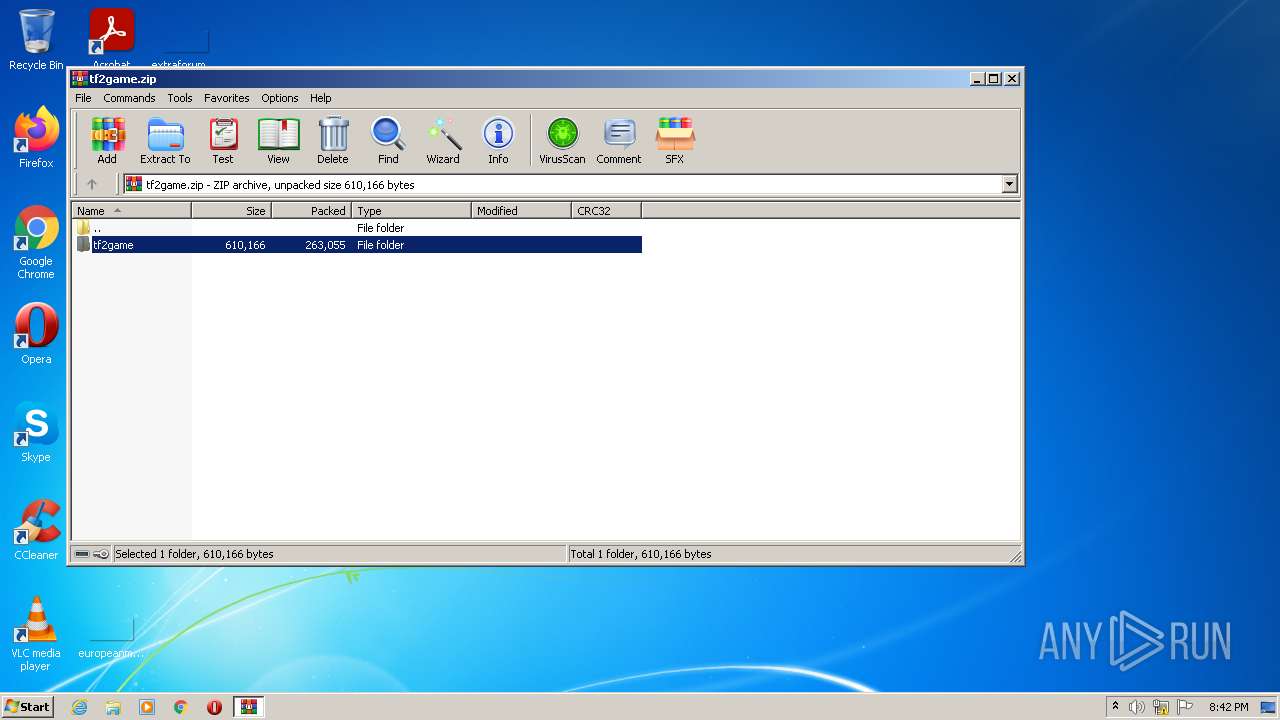
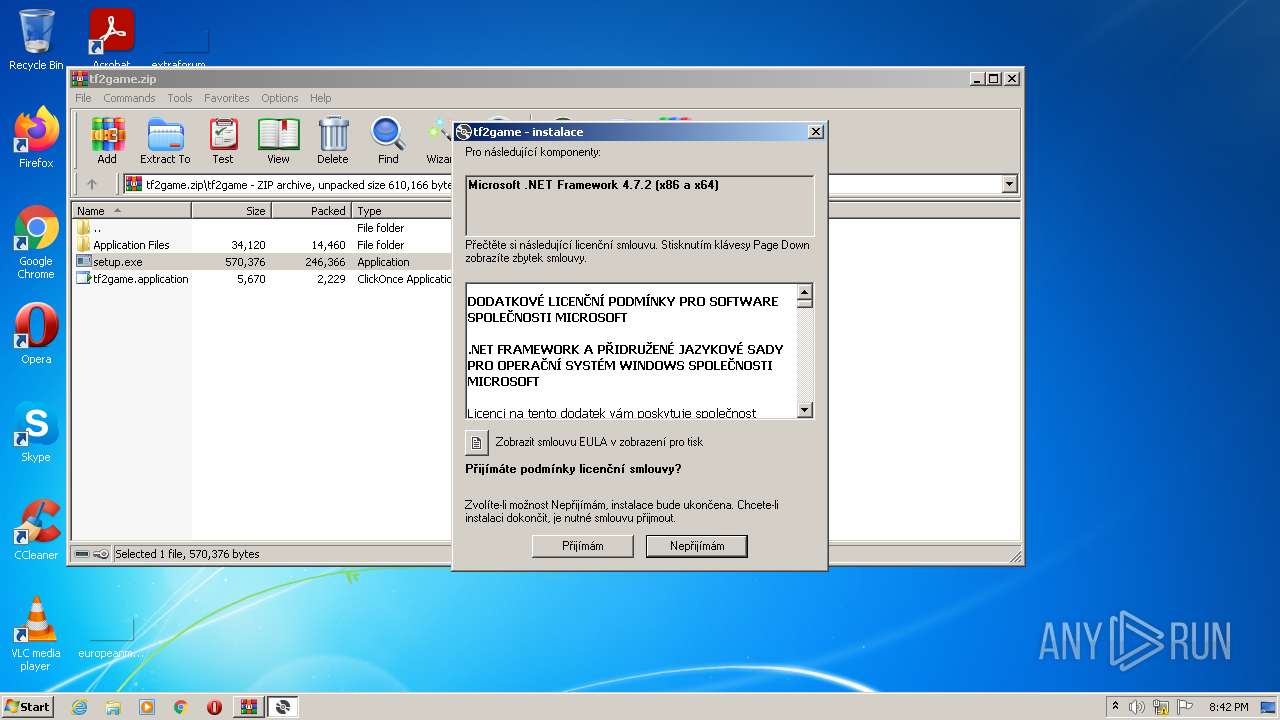
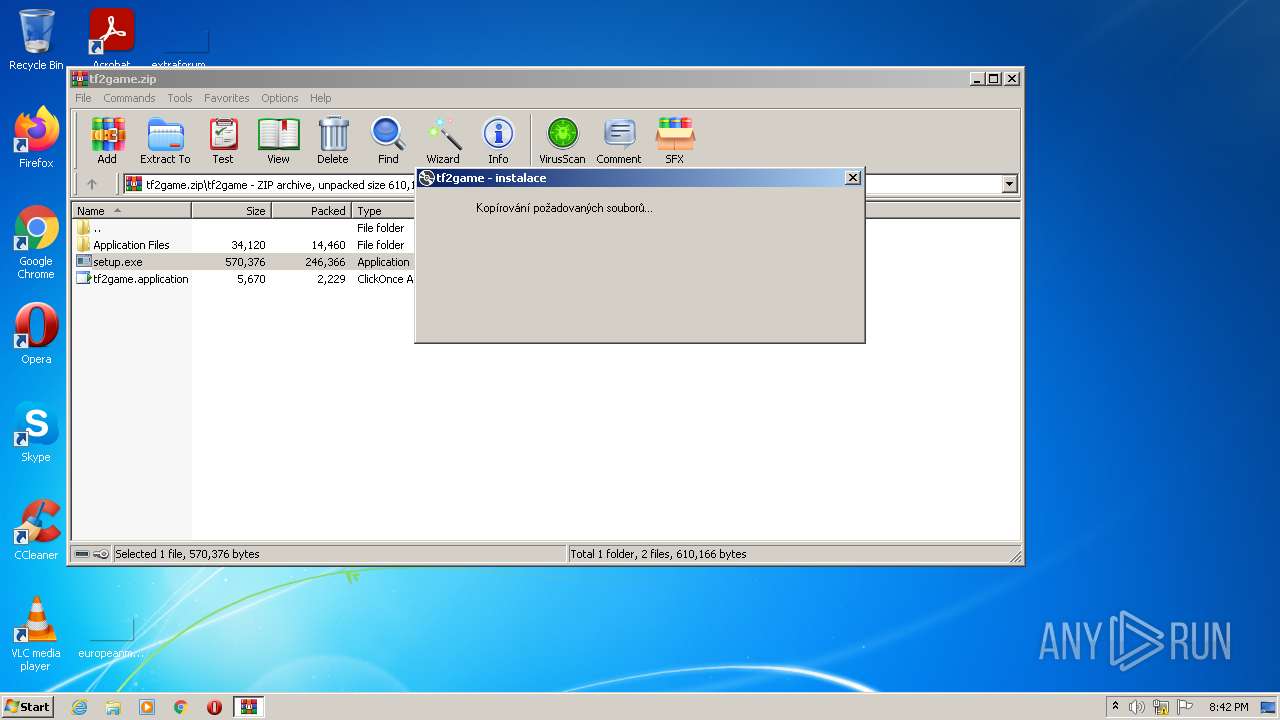
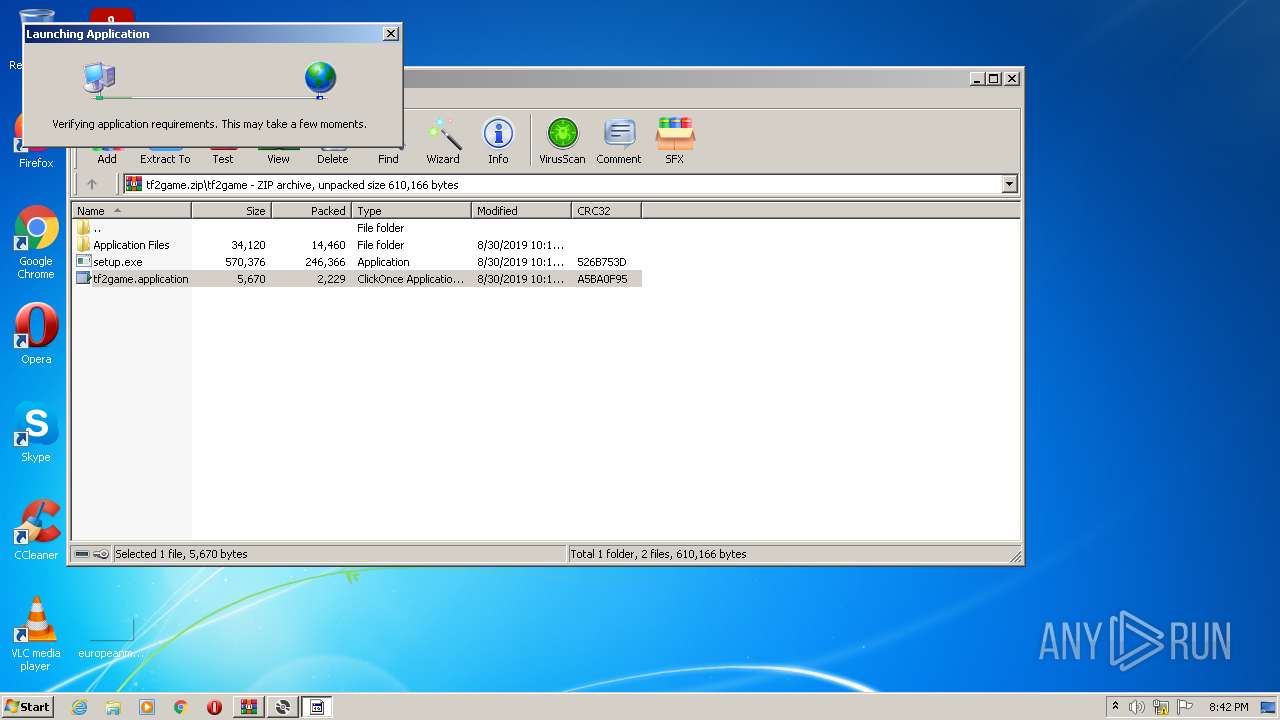
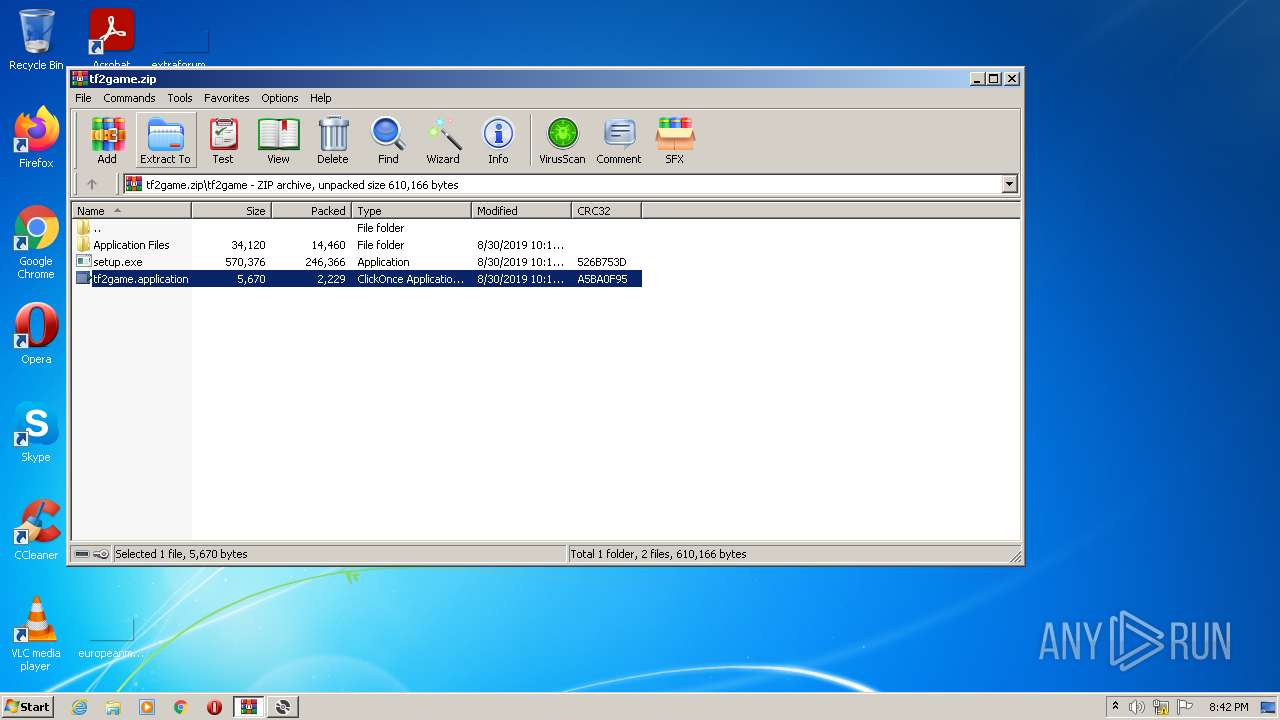
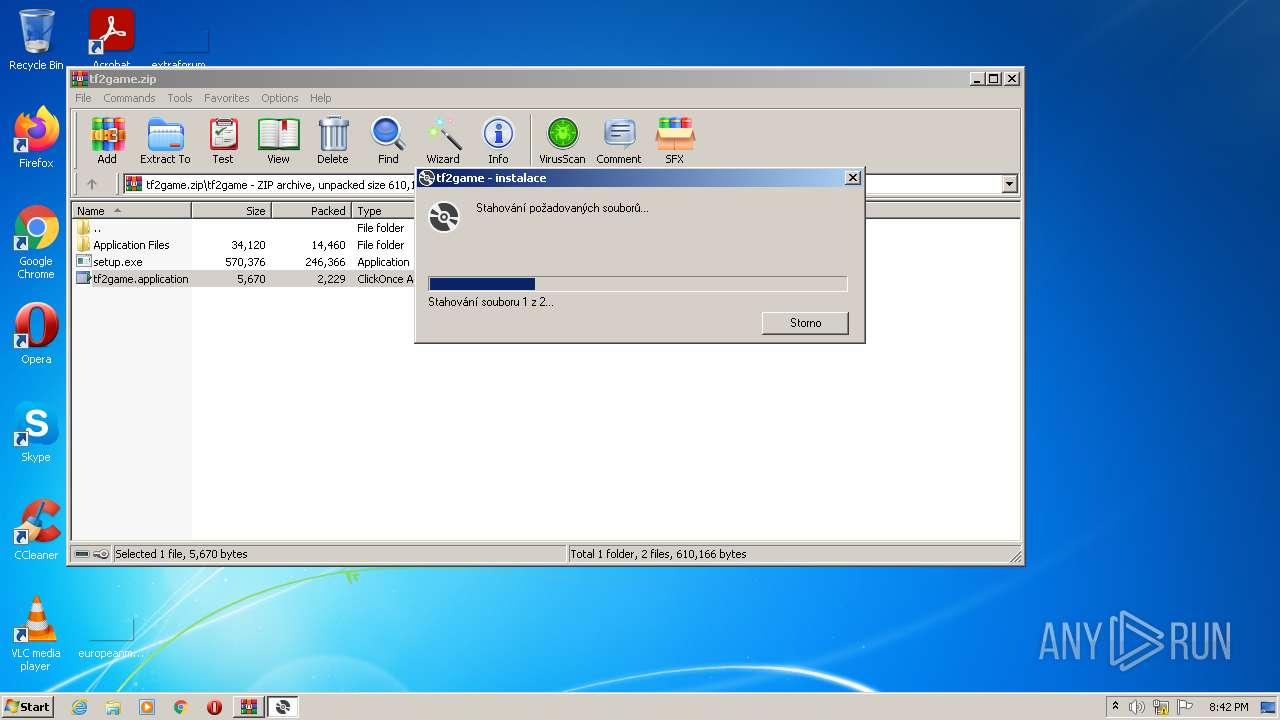
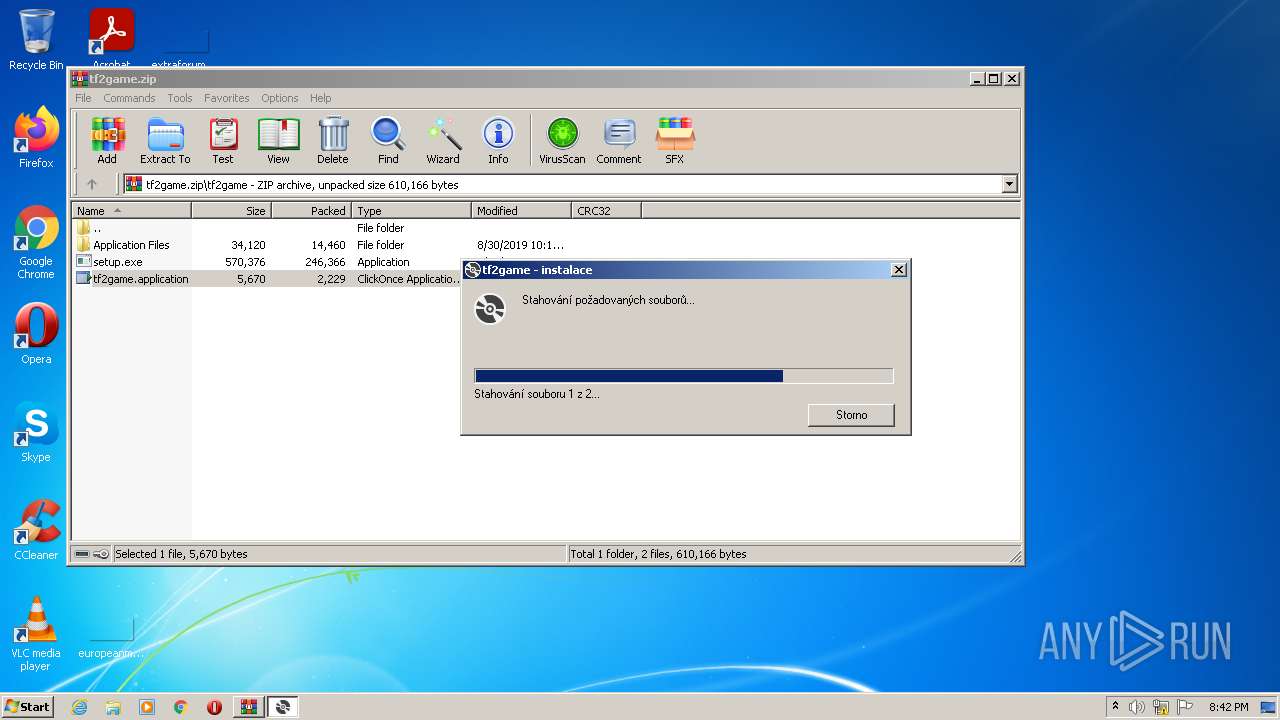
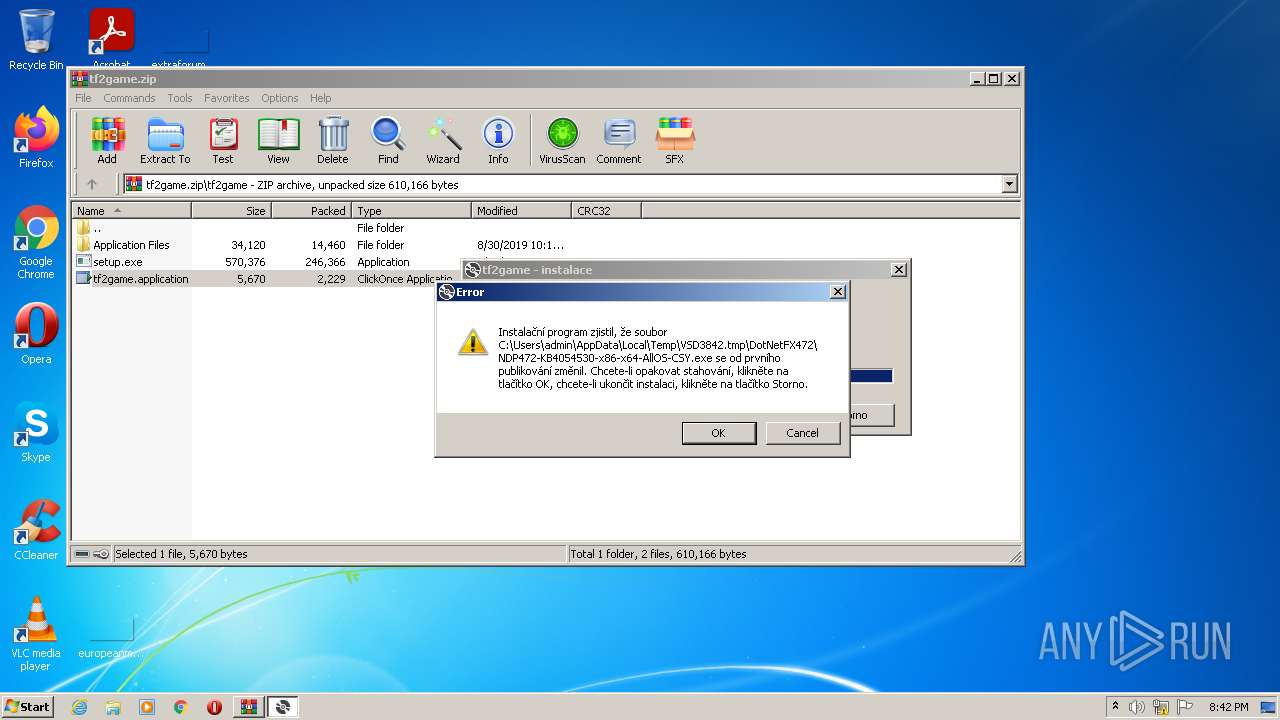
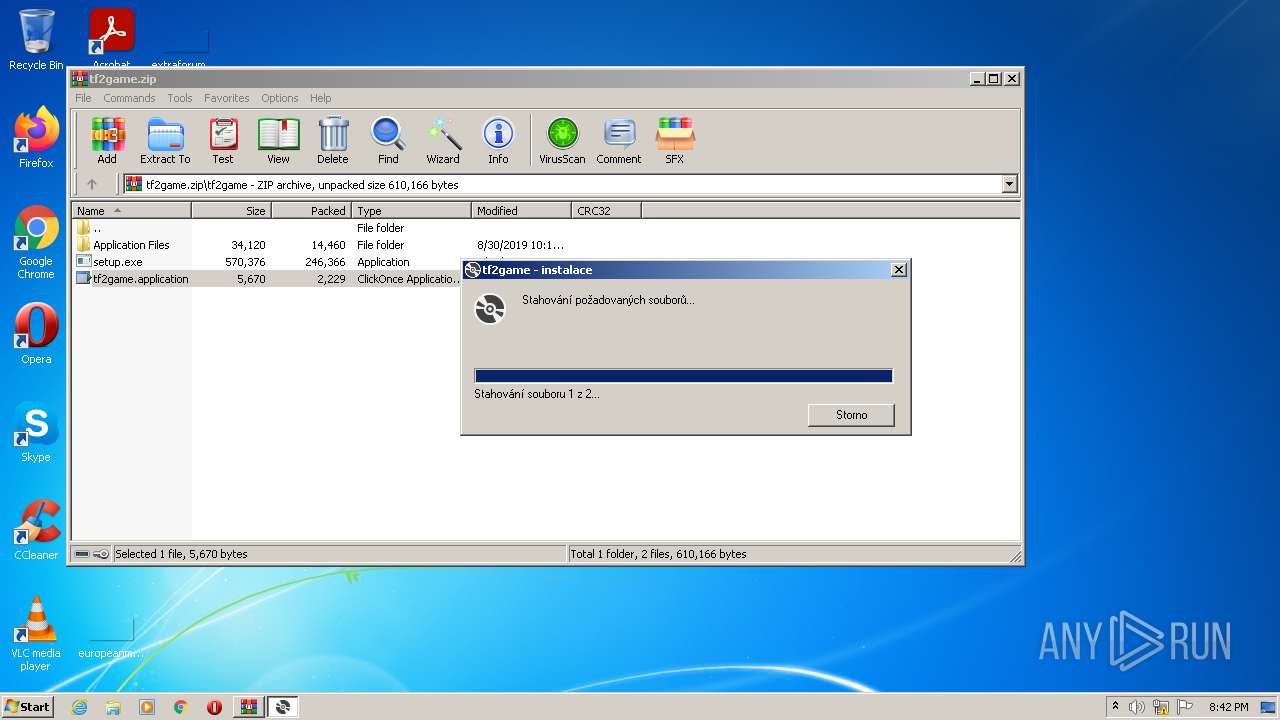
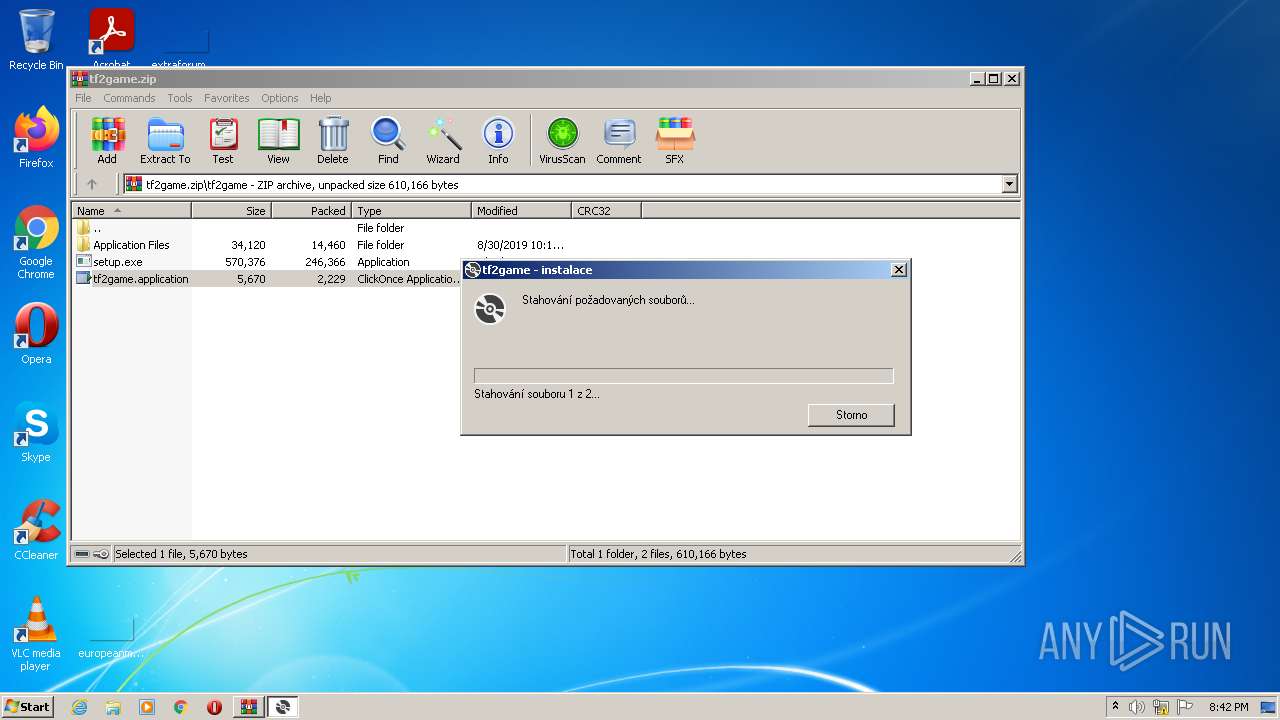
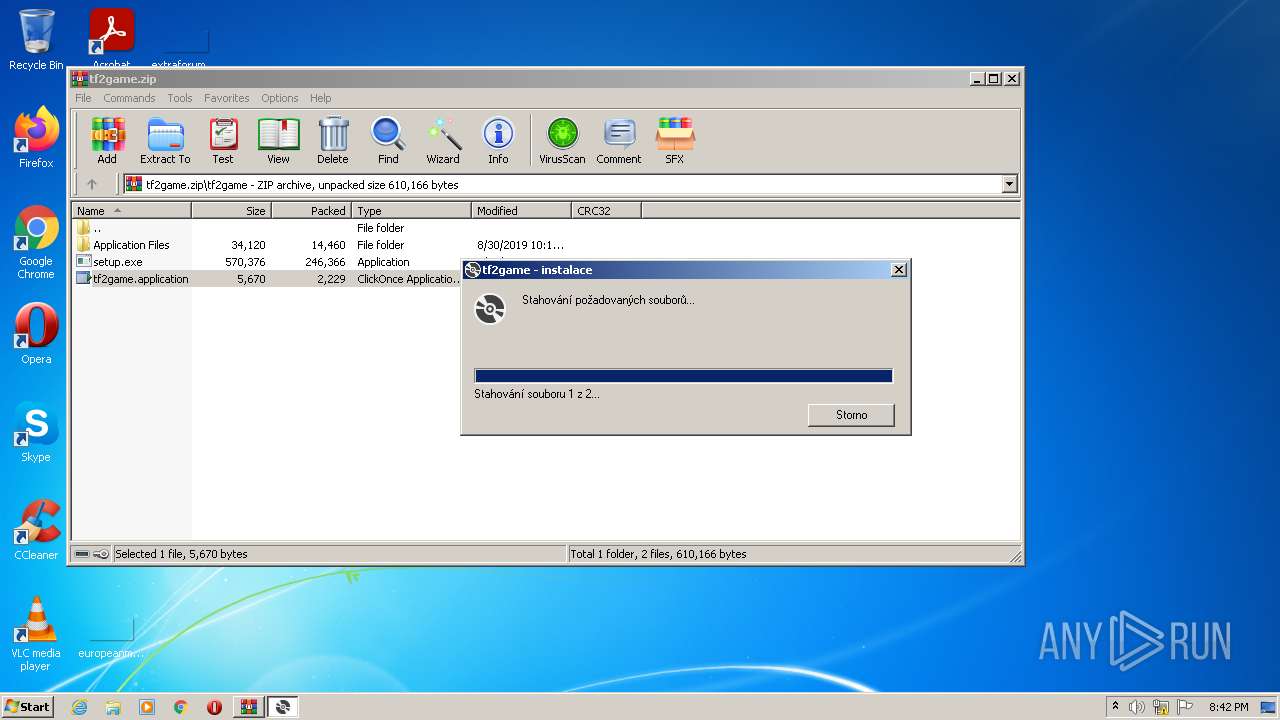
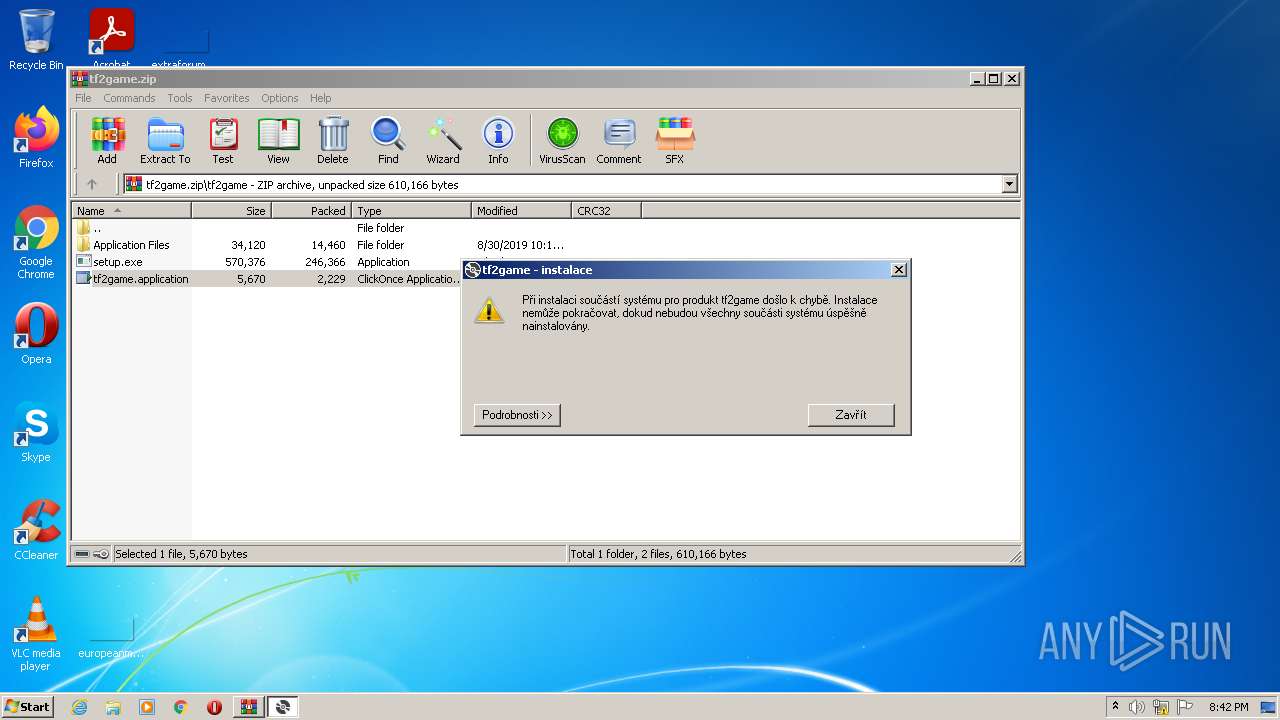
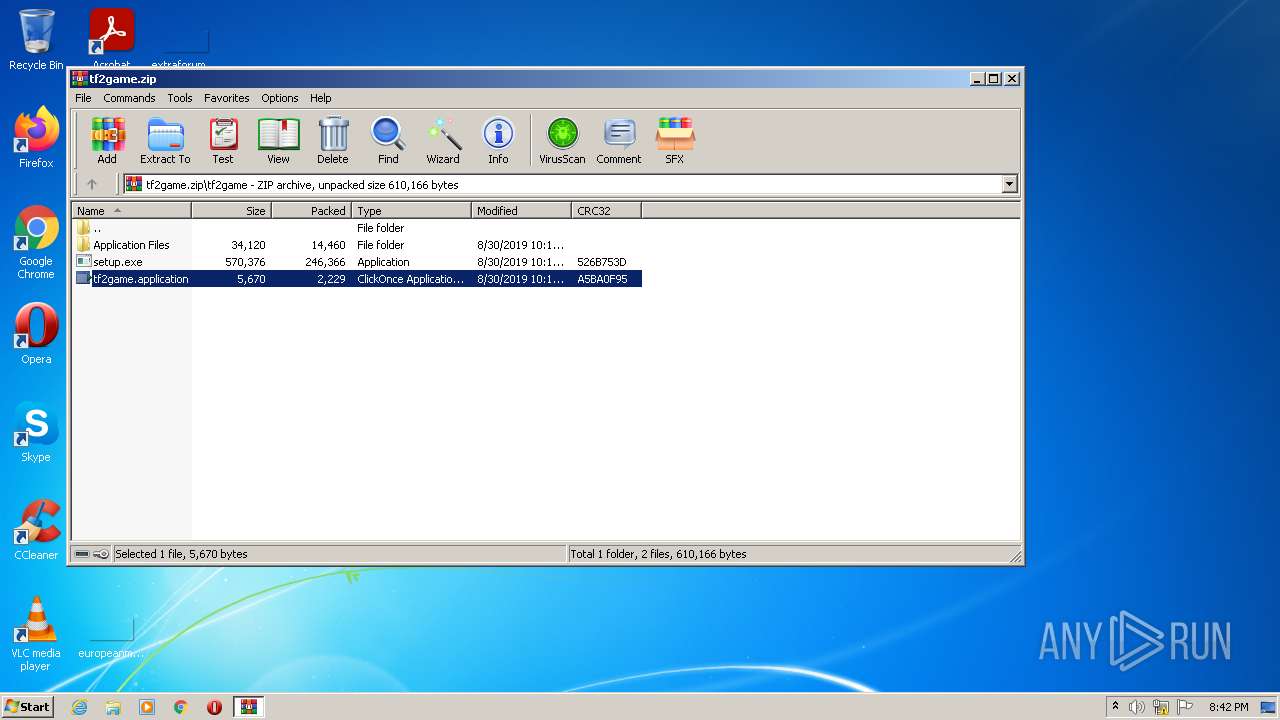
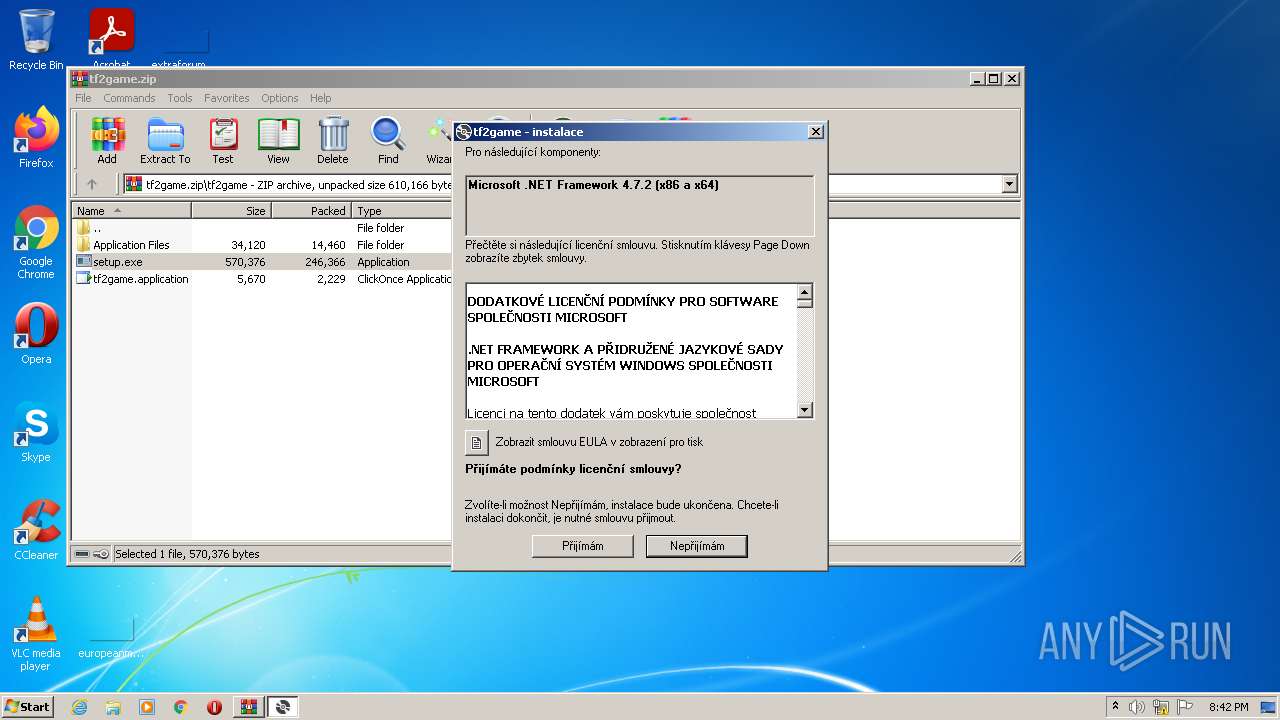
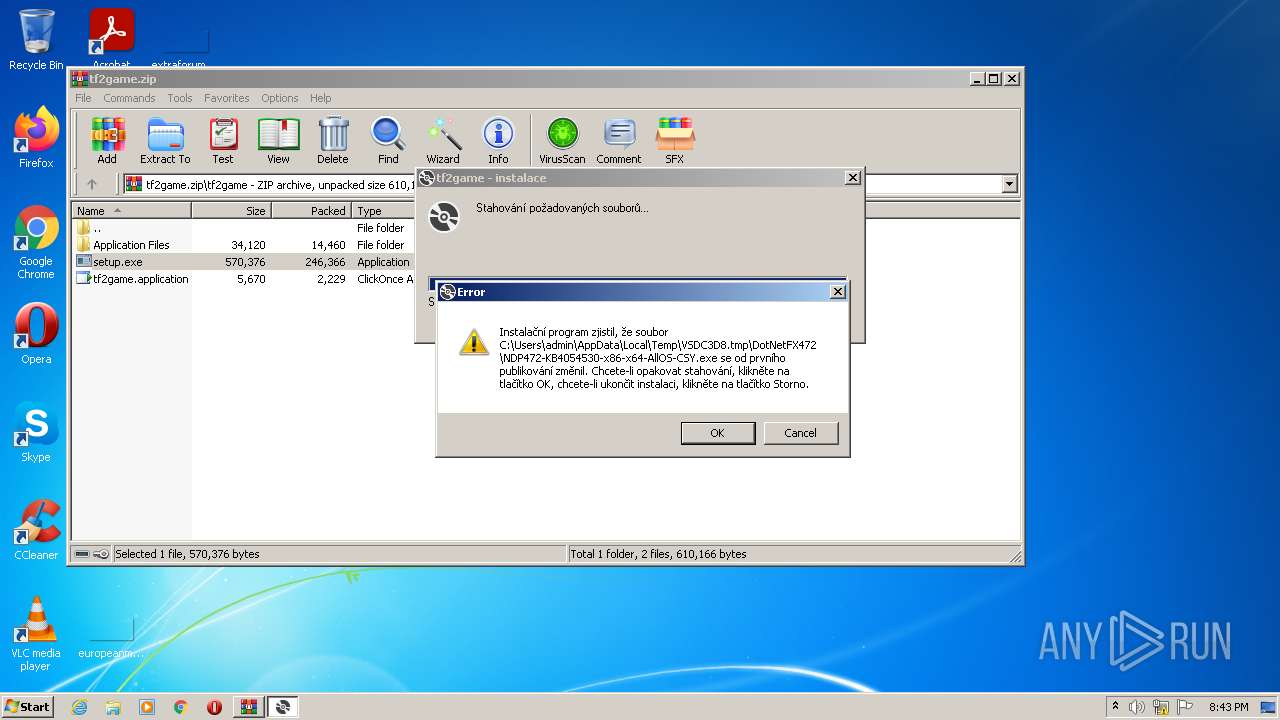
| File name: | tf2game.zip |
| Full analysis: | https://app.any.run/tasks/bbdd7626-af1e-4bc8-a9ce-4e93165f5ffd |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 20:42:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 1E90F32671037A25894B21037F00619B |
| SHA1: | 6D0CD472AE61D9366162A30DF7BDB6109ECAD858 |
| SHA256: | 10CF455D7B1863F8AA40E0E8355326961EA28E3F9D362C8448408C7B7039EE2A |
| SSDEEP: | 6144:/DjamHy7qfanG++ySOd5621pMZxJ0NYtimyD/7/S2Dy596R6X//TYWqW:/D3KqfanGhgLvw0NYtHyPM596R6XwW |
MALICIOUS
Actions looks like stealing of personal data
- WinRAR.exe (PID: 3336)
Application was dropped or rewritten from another process
- setup.exe (PID: 2788)
- setup.exe (PID: 1084)
SUSPICIOUS
Reads the computer name
- setup.exe (PID: 2788)
- WinRAR.exe (PID: 3336)
- setup.exe (PID: 1084)
- dfsvc.exe (PID: 420)
Checks supported languages
- WinRAR.exe (PID: 3336)
- dfsvc.exe (PID: 420)
- setup.exe (PID: 1084)
- setup.exe (PID: 2788)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3336)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3336)
- setup.exe (PID: 2788)
- setup.exe (PID: 1084)
Executable content was dropped or overwritten
- setup.exe (PID: 2788)
- WinRAR.exe (PID: 3336)
- setup.exe (PID: 1084)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3336)
INFO
Checks Windows Trust Settings
- setup.exe (PID: 2788)
- setup.exe (PID: 1084)
Reads settings of System Certificates
- setup.exe (PID: 2788)
- setup.exe (PID: 1084)
Checks supported languages
- rundll32.exe (PID: 496)
Reads the computer name
- rundll32.exe (PID: 496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | tf2game/Application Files/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2019:08:30 22:18:16 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
41
Monitored processes
5
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ClickOnce Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 496 | "rundll32.exe" dfshim.dll,ShOpenVerbApplication C:\Users\admin\AppData\Local\Temp\Rar$DIa3336.10851\tf2game.application | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1084 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.12920\tf2game\setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.12920\tf2game\setup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Exit code: 0 Version: 16.0.28315.86 built by: D16.0 Modules
| |||||||||||||||
| 2788 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.9343\tf2game\setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.9343\tf2game\setup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Exit code: 1603 Version: 16.0.28315.86 built by: D16.0 Modules
| |||||||||||||||
| 3336 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\tf2game.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 230
Read events
10 101
Write events
126
Delete events
3
Modification events
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\tf2game.zip | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
7
Text files
11
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.9343\tf2game\tf2game.application | xml | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.9343\tf2game\Application Files\tf2game_1_0_0_0\tf2game.exe.manifest | xml | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.9343\tf2game\Application Files\tf2game_1_0_0_0\tf2game.application | xml | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.9343\tf2game\Application Files\tf2game_1_0_0_0\tf2game.exe.deploy | executable | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3336.9343\tf2game\setup.exe | executable | |
MD5:— | SHA256:— | |||
| 2788 | setup.exe | C:\Users\admin\AppData\Local\Temp\VSD3842.tmp\setup.exe | executable | |
MD5:— | SHA256:— | |||
| 2788 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 2788 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:— | SHA256:— | |||
| 2788 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ndp472-kb4054530-x86-x64-allos-csy[1].exe | executable | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3336.10851\tf2game.application | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
8
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2788 | setup.exe | GET | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=863258&clcid=0x405 | NL | — | — | whitelisted |
2788 | setup.exe | GET | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=863258&clcid=0x405 | NL | — | — | whitelisted |
2788 | setup.exe | GET | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=863258&clcid=0x405 | NL | — | — | whitelisted |
1084 | setup.exe | GET | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=863258&clcid=0x405 | NL | — | — | whitelisted |
2788 | setup.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2788 | setup.exe | GET | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=863258&clcid=0x405 | NL | — | — | whitelisted |
2788 | setup.exe | GET | 200 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?106f60eccc60ab4c | US | compressed | 4.70 Kb | whitelisted |
2788 | setup.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | US | der | 1.05 Kb | whitelisted |
2788 | setup.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/certs/MicCodSigPCA2011_2011-07-08.crt | US | der | 1.87 Kb | whitelisted |
2788 | setup.exe | GET | 200 | 92.123.194.163:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | der | 1.11 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2788 | setup.exe | 92.123.194.163:80 | crl.microsoft.com | Akamai International B.V. | — | suspicious |
2788 | setup.exe | 68.232.34.200:443 | download.visualstudio.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2788 | setup.exe | 104.89.38.104:80 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
1084 | setup.exe | 104.89.38.104:80 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
2788 | setup.exe | 104.79.89.142:80 | www.microsoft.com | Time Warner Cable Internet LLC | US | unknown |
2788 | setup.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2788 | setup.exe | 8.241.78.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|