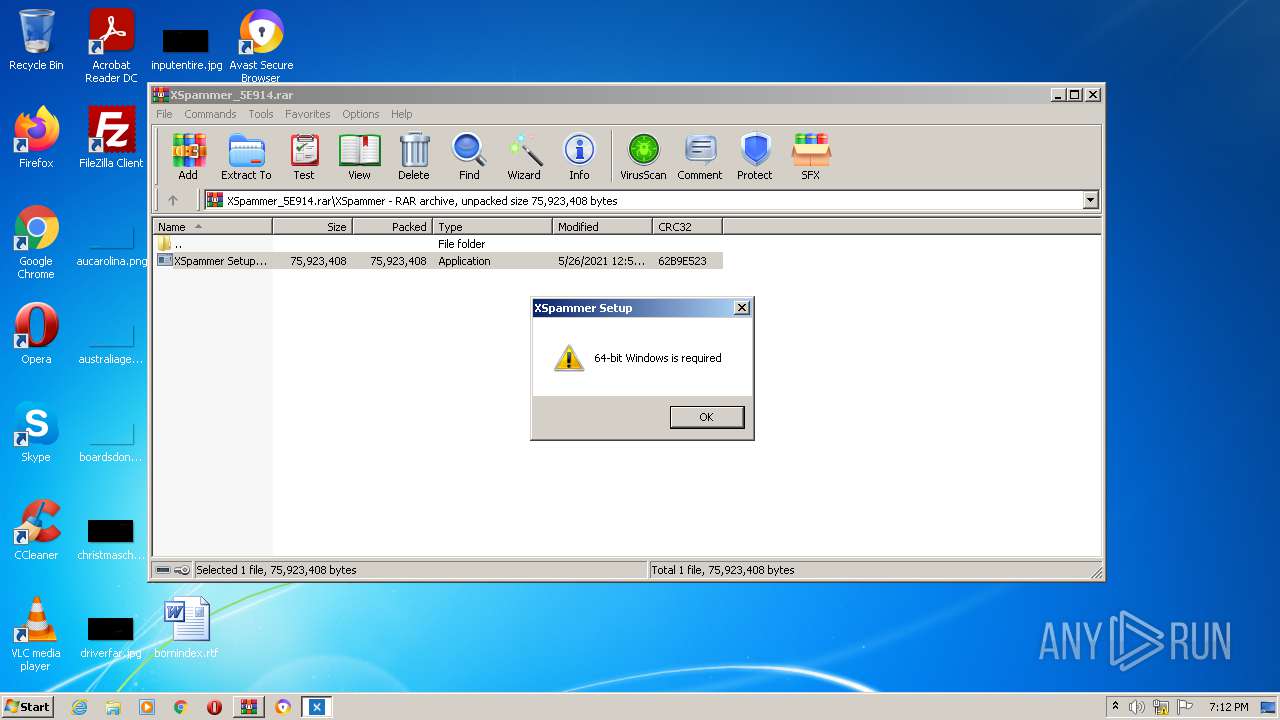
| File name: | XSpammer - Linkvertise Downloader_UE-6gC1.exe |
| Full analysis: | https://app.any.run/tasks/9c4b61de-549d-4896-831f-78c28fc3e2a2 |
| Verdict: | Malicious activity |
| Analysis date: | November 18, 2021, 19:09:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D0CC2D9D58432CF09C6AAC7856F75B93 |
| SHA1: | 8B77F5E6656230001989CC3D828AA43CE445AAAC |
| SHA256: | 10CC2DE88FBBBC389B48BA140B79BFDBCE43173AB2EA5F7ED79B48314802646A |
| SSDEEP: | 49152:+qe3f6atzD7+H98AHaCfu60WmHCL+WuTmuKwEt:vSiwD7E9vButWmHCK5NKXt |
MALICIOUS
Drops executable file immediately after starts
- XSpammer - Linkvertise Downloader_UE-6gC1.exe (PID: 4088)
- XSpammer - Linkvertise Downloader_UE-6gC1.exe (PID: 2992)
- avast_secure_browser_setup.exe (PID: 2844)
- WcInstaller16112020.exe (PID: 3820)
- AvastBrowserUpdateSetup.exe (PID: 3828)
- AvastBrowserUpdate.exe (PID: 1580)
- csc.exe (PID: 2008)
- AvastBrowserInstaller.exe (PID: 2416)
- XSpammer Setup.exe (PID: 2548)
Application was dropped or rewritten from another process
- avast_secure_browser_setup.exe (PID: 2844)
- WcInstaller16112020.exe (PID: 3820)
- WebCompanionInstaller.exe (PID: 2612)
- AvastBrowserUpdateSetup.exe (PID: 3828)
- AvastBrowserUpdate.exe (PID: 1580)
- AvastBrowserUpdate.exe (PID: 2320)
- AvastBrowserUpdate.exe (PID: 2764)
- AvastBrowserUpdate.exe (PID: 2460)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- WebCompanion.exe (PID: 3120)
- WebCompanion.exe (PID: 2444)
- AvastBrowserUpdate.exe (PID: 2660)
- AvastBrowserUpdate.exe (PID: 3156)
- AvastBrowserCrashHandler.exe (PID: 3004)
- setup.exe (PID: 3460)
- setup.exe (PID: 2564)
- AvastBrowser.exe (PID: 1600)
- AvastBrowser.exe (PID: 656)
- AvastBrowser.exe (PID: 3028)
- AvastBrowser.exe (PID: 2788)
- AvastBrowser.exe (PID: 328)
- AvastBrowser.exe (PID: 3532)
- AvastBrowser.exe (PID: 1012)
- AvastBrowser.exe (PID: 3844)
- AvastBrowser.exe (PID: 4020)
- AvastBrowser.exe (PID: 3248)
- AvastBrowser.exe (PID: 3016)
- AvastBrowser.exe (PID: 2644)
- AvastBrowser.exe (PID: 3988)
- chrmstp.exe (PID: 2356)
- chrmstp.exe (PID: 3736)
- AvastBrowser.exe (PID: 3752)
- AvastBrowser.exe (PID: 2460)
- AvastBrowser.exe (PID: 3000)
- AvastBrowser.exe (PID: 3160)
- AvastBrowser.exe (PID: 1804)
- AvastBrowser.exe (PID: 3488)
- AvastBrowser.exe (PID: 1924)
- AvastBrowser.exe (PID: 1976)
Steals credentials from Web Browsers
- avast_secure_browser_setup.exe (PID: 2844)
- WebCompanion.exe (PID: 3120)
- AvastBrowser.exe (PID: 1600)
Loads dropped or rewritten executable
- avast_secure_browser_setup.exe (PID: 2844)
- WebCompanionInstaller.exe (PID: 2612)
- AvastBrowserUpdate.exe (PID: 2460)
- AvastBrowserUpdate.exe (PID: 2764)
- AvastBrowserUpdate.exe (PID: 1580)
- AvastBrowserUpdate.exe (PID: 2320)
- AvastBrowserUpdate.exe (PID: 3156)
- AvastBrowserUpdate.exe (PID: 2660)
- WebCompanion.exe (PID: 3120)
- WebCompanion.exe (PID: 2444)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- XSpammer Setup.exe (PID: 884)
- XSpammer Setup.exe (PID: 2548)
Actions looks like stealing of personal data
- avast_secure_browser_setup.exe (PID: 2844)
- WebCompanion.exe (PID: 3120)
- AvastBrowserInstaller.exe (PID: 2416)
- setup.exe (PID: 3460)
- AvastBrowser.exe (PID: 1600)
Loads the Task Scheduler COM API
- AvastBrowserUpdate.exe (PID: 1580)
- setup.exe (PID: 3460)
Changes settings of System certificates
- AvastBrowserUpdate.exe (PID: 2460)
Changes internet zones settings
- WebCompanionInstaller.exe (PID: 2612)
Changes the autorun value in the registry
- WebCompanion.exe (PID: 3120)
- setup.exe (PID: 3460)
- AvastBrowser.exe (PID: 1600)
Starts Visual C# compiler
- WebCompanion.exe (PID: 3120)
SUSPICIOUS
Executable content was dropped or overwritten
- XSpammer - Linkvertise Downloader_UE-6gC1.exe (PID: 2992)
- XSpammer - Linkvertise Downloader_UE-6gC1.exe (PID: 4088)
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
- avast_secure_browser_setup.exe (PID: 2844)
- WcInstaller16112020.exe (PID: 3820)
- AvastBrowserUpdateSetup.exe (PID: 3828)
- AvastBrowserUpdate.exe (PID: 1580)
- WebCompanionInstaller.exe (PID: 2612)
- csc.exe (PID: 2008)
- AvastBrowserInstaller.exe (PID: 2416)
- setup.exe (PID: 3460)
- XSpammer Setup.exe (PID: 884)
- XSpammer Setup.exe (PID: 2548)
Checks supported languages
- XSpammer - Linkvertise Downloader_UE-6gC1.exe (PID: 4088)
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 3216)
- XSpammer - Linkvertise Downloader_UE-6gC1.exe (PID: 2992)
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
- avast_secure_browser_setup.exe (PID: 2844)
- WcInstaller16112020.exe (PID: 3820)
- WebCompanionInstaller.exe (PID: 2612)
- AvastBrowserUpdateSetup.exe (PID: 3828)
- AvastBrowserUpdate.exe (PID: 1580)
- AvastBrowserUpdate.exe (PID: 2320)
- AvastBrowserUpdate.exe (PID: 2660)
- AvastBrowserUpdate.exe (PID: 2764)
- AvastBrowserUpdate.exe (PID: 2460)
- AvastBrowserUpdate.exe (PID: 3156)
- cmd.exe (PID: 3784)
- WebCompanion.exe (PID: 3120)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- cmd.exe (PID: 2660)
- csc.exe (PID: 2008)
- cvtres.exe (PID: 3068)
- WebCompanion.exe (PID: 2444)
- PresentationFontCache.exe (PID: 2780)
- AvastBrowserInstaller.exe (PID: 2416)
- setup.exe (PID: 3460)
- setup.exe (PID: 2564)
- WinRAR.exe (PID: 2484)
- AvastBrowserCrashHandler.exe (PID: 3004)
- AvastBrowser.exe (PID: 3028)
- AvastBrowser.exe (PID: 2788)
- AvastBrowser.exe (PID: 656)
- AvastBrowser.exe (PID: 1600)
- AvastBrowser.exe (PID: 3532)
- AvastBrowser.exe (PID: 4020)
- AvastBrowser.exe (PID: 328)
- elevation_service.exe (PID: 2608)
- AvastBrowser.exe (PID: 3016)
- AvastBrowser.exe (PID: 2644)
- AvastBrowser.exe (PID: 3248)
- AvastBrowser.exe (PID: 3988)
- AvastBrowser.exe (PID: 1012)
- AvastBrowser.exe (PID: 3844)
- chrmstp.exe (PID: 2356)
- chrmstp.exe (PID: 3736)
- AvastBrowser.exe (PID: 3752)
- elevation_service.exe (PID: 2468)
- AvastBrowser.exe (PID: 2460)
- AvastBrowser.exe (PID: 3160)
- AvastBrowser.exe (PID: 1804)
- elevation_service.exe (PID: 3056)
- AvastBrowser.exe (PID: 3000)
- AvastBrowser.exe (PID: 3488)
- AvastBrowser.exe (PID: 1924)
- cmd.exe (PID: 3172)
- XSpammer Setup.exe (PID: 884)
- AvastBrowser.exe (PID: 1976)
- XSpammer Setup.exe (PID: 2548)
Reads the computer name
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 3216)
- avast_secure_browser_setup.exe (PID: 2844)
- WebCompanionInstaller.exe (PID: 2612)
- AvastBrowserUpdate.exe (PID: 1580)
- AvastBrowserUpdate.exe (PID: 2320)
- AvastBrowserUpdate.exe (PID: 3156)
- AvastBrowserUpdate.exe (PID: 2460)
- AvastBrowserUpdate.exe (PID: 2764)
- WebCompanion.exe (PID: 3120)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- WebCompanion.exe (PID: 2444)
- PresentationFontCache.exe (PID: 2780)
- AvastBrowserInstaller.exe (PID: 2416)
- setup.exe (PID: 3460)
- WinRAR.exe (PID: 2484)
- AvastBrowser.exe (PID: 1600)
- AvastBrowserCrashHandler.exe (PID: 3004)
- AvastBrowser.exe (PID: 656)
- elevation_service.exe (PID: 2608)
- AvastBrowser.exe (PID: 2788)
- AvastBrowser.exe (PID: 2644)
- AvastBrowser.exe (PID: 3988)
- chrmstp.exe (PID: 2356)
- elevation_service.exe (PID: 2468)
- AvastBrowser.exe (PID: 3752)
- AvastBrowser.exe (PID: 3160)
- AvastBrowser.exe (PID: 1804)
- elevation_service.exe (PID: 3056)
- AvastBrowser.exe (PID: 1924)
- XSpammer Setup.exe (PID: 884)
- XSpammer Setup.exe (PID: 2548)
Drops a file with too old compile date
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
Reads the Windows organization settings
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
Drops a file that was compiled in debug mode
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
- avast_secure_browser_setup.exe (PID: 2844)
- WcInstaller16112020.exe (PID: 3820)
- AvastBrowserUpdateSetup.exe (PID: 3828)
- AvastBrowserUpdate.exe (PID: 1580)
- WebCompanionInstaller.exe (PID: 2612)
- AvastBrowserInstaller.exe (PID: 2416)
- setup.exe (PID: 3460)
Reads Windows owner or organization settings
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
Drops a file with a compile date too recent
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
- WcInstaller16112020.exe (PID: 3820)
- WebCompanionInstaller.exe (PID: 2612)
- csc.exe (PID: 2008)
- AvastBrowserInstaller.exe (PID: 2416)
- setup.exe (PID: 3460)
Reads Environment values
- avast_secure_browser_setup.exe (PID: 2844)
- WebCompanionInstaller.exe (PID: 2612)
- netsh.exe (PID: 388)
- WebCompanion.exe (PID: 3120)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- netsh.exe (PID: 4056)
- WebCompanion.exe (PID: 2444)
- AvastBrowser.exe (PID: 1600)
- AvastBrowser.exe (PID: 3752)
Searches for installed software
- avast_secure_browser_setup.exe (PID: 2844)
- WebCompanion.exe (PID: 3120)
- WebCompanion.exe (PID: 2444)
- AvastBrowser.exe (PID: 1600)
- AvastBrowser.exe (PID: 3752)
Creates files in the program directory
- WebCompanionInstaller.exe (PID: 2612)
- AvastBrowserUpdateSetup.exe (PID: 3828)
- AvastBrowserUpdate.exe (PID: 1580)
- WebCompanion.exe (PID: 3120)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- WebCompanion.exe (PID: 2444)
- AvastBrowserInstaller.exe (PID: 2416)
- AvastBrowserUpdate.exe (PID: 2460)
- avast_secure_browser_setup.exe (PID: 2844)
- setup.exe (PID: 3460)
- chrmstp.exe (PID: 2356)
Creates a directory in Program Files
- AvastBrowserUpdateSetup.exe (PID: 3828)
- AvastBrowserUpdate.exe (PID: 1580)
- AvastBrowserUpdate.exe (PID: 2460)
- WebCompanionInstaller.exe (PID: 2612)
- setup.exe (PID: 3460)
- AvastBrowserInstaller.exe (PID: 2416)
Starts itself from another location
- AvastBrowserUpdate.exe (PID: 1580)
Disables SEHOP
- AvastBrowserUpdate.exe (PID: 1580)
Creates/Modifies COM task schedule object
- AvastBrowserUpdate.exe (PID: 2660)
- AvastBrowserUpdate.exe (PID: 1580)
Executed as Windows Service
- AvastBrowserUpdate.exe (PID: 2460)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- PresentationFontCache.exe (PID: 2780)
- elevation_service.exe (PID: 2608)
- elevation_service.exe (PID: 2468)
- elevation_service.exe (PID: 3056)
Adds / modifies Windows certificates
- AvastBrowserUpdate.exe (PID: 2460)
Removes files from Windows directory
- AvastBrowserUpdate.exe (PID: 2460)
- WebCompanionInstaller.exe (PID: 2612)
Creates files in the Windows directory
- AvastBrowserUpdate.exe (PID: 2460)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- WebCompanion.exe (PID: 3120)
- WebCompanionInstaller.exe (PID: 2612)
- setup.exe (PID: 2564)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3784)
- cmd.exe (PID: 2660)
Starts SC.EXE for service management
- WebCompanionInstaller.exe (PID: 2612)
Creates a software uninstall entry
- WebCompanionInstaller.exe (PID: 2612)
- setup.exe (PID: 3460)
- avast_secure_browser_setup.exe (PID: 2844)
- elevation_service.exe (PID: 2608)
- elevation_service.exe (PID: 3056)
Creates files in the user directory
- WebCompanionInstaller.exe (PID: 2612)
- WebCompanion.exe (PID: 3120)
- setup.exe (PID: 3460)
- AvastBrowser.exe (PID: 1600)
- chrmstp.exe (PID: 2356)
Starts CMD.EXE for commands execution
- WebCompanionInstaller.exe (PID: 2612)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- avast_secure_browser_setup.exe (PID: 2844)
Starts Internet Explorer
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1228)
Application launched itself
- setup.exe (PID: 3460)
- AvastBrowser.exe (PID: 1600)
- chrmstp.exe (PID: 2356)
- AvastBrowser.exe (PID: 3752)
Changes default file association
- setup.exe (PID: 3460)
Reads the date of Windows installation
- setup.exe (PID: 3460)
- chrmstp.exe (PID: 2356)
Starts CMD.EXE for self-deleting
- avast_secure_browser_setup.exe (PID: 2844)
INFO
Application was dropped or rewritten from another process
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 3216)
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
Reads settings of System Certificates
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
- WebCompanionInstaller.exe (PID: 2612)
- avast_secure_browser_setup.exe (PID: 2844)
- AvastBrowserUpdate.exe (PID: 2460)
- AvastBrowserUpdate.exe (PID: 3156)
- WebCompanion.exe (PID: 3120)
- iexplore.exe (PID: 1228)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- WebCompanion.exe (PID: 2444)
- chrome.exe (PID: 2164)
- iexplore.exe (PID: 2508)
- AvastBrowser.exe (PID: 1600)
- AvastBrowser.exe (PID: 3752)
Loads dropped or rewritten executable
- XSpammer - Linkvertise Downloader_UE-6gC1.tmp (PID: 2220)
Checks Windows Trust Settings
- WebCompanionInstaller.exe (PID: 2612)
- avast_secure_browser_setup.exe (PID: 2844)
- WebCompanion.exe (PID: 3120)
- iexplore.exe (PID: 1228)
- Lavasoft.WCAssistant.WinService.exe (PID: 4028)
- WebCompanion.exe (PID: 2444)
- iexplore.exe (PID: 2508)
Dropped object may contain Bitcoin addresses
- WebCompanionInstaller.exe (PID: 2612)
Checks supported languages
- sc.exe (PID: 3388)
- sc.exe (PID: 148)
- sc.exe (PID: 3064)
- netsh.exe (PID: 388)
- iexplore.exe (PID: 2508)
- iexplore.exe (PID: 1228)
- netsh.exe (PID: 4056)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 2488)
- chrome.exe (PID: 2164)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 3380)
- chrome.exe (PID: 312)
- chrome.exe (PID: 284)
- chrome.exe (PID: 2304)
- chrome.exe (PID: 2840)
- timeout.exe (PID: 3292)
Reads the computer name
- sc.exe (PID: 3388)
- sc.exe (PID: 148)
- sc.exe (PID: 3064)
- netsh.exe (PID: 388)
- iexplore.exe (PID: 2508)
- iexplore.exe (PID: 1228)
- netsh.exe (PID: 4056)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 2488)
- chrome.exe (PID: 2164)
- chrome.exe (PID: 284)
Application launched itself
- iexplore.exe (PID: 2508)
- chrome.exe (PID: 3320)
Changes internet zones settings
- iexplore.exe (PID: 2508)
Reads the date of Windows installation
- iexplore.exe (PID: 2508)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2508)
Reads the hosts file
- chrome.exe (PID: 2164)
- chrome.exe (PID: 3320)
- AvastBrowser.exe (PID: 1600)
- AvastBrowser.exe (PID: 656)
- AvastBrowser.exe (PID: 3752)
- AvastBrowser.exe (PID: 1804)
Changes settings of System certificates
- chrome.exe (PID: 2164)
- iexplore.exe (PID: 2508)
Adds / modifies Windows certificates
- chrome.exe (PID: 2164)
- iexplore.exe (PID: 2508)
Creates files in the user directory
- iexplore.exe (PID: 2508)
Manual execution by user
- AvastBrowser.exe (PID: 3752)
- XSpammer Setup.exe (PID: 2548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 10:48:30+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 157184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.13 |
| ProductVersionNumber: | 2.0.0.13 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Linkvertise GmbH & Co. KG |
| FileVersion: | 2.0.0.13 |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Linkvertise GmbH & Co. KG |
| ProductVersion: | 2.0.0.13 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 15-Nov-2020 09:48:30 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | - |
| FileDescription: | Linkvertise GmbH & Co. KG |
| FileVersion: | 2.0.0.13 |
| LegalCopyright: | - |
| OriginalFileName: | - |
| ProductName: | Linkvertise GmbH & Co. KG |
| ProductVersion: | 2.0.0.13 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 10 |
| Time date stamp: | 15-Nov-2020 09:48:30 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000B361C | 0x000B3800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.35606 |
.itext | 0x000B5000 | 0x00001688 | 0x00001800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.97275 |
.data | 0x000B7000 | 0x000037A4 | 0x00003800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.0444 |
.bss | 0x000BB000 | 0x00006DE8 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x000C2000 | 0x00000F36 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.8987 |
.didata | 0x000C3000 | 0x000001A4 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.75636 |
.edata | 0x000C4000 | 0x0000009A | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.87222 |
.tls | 0x000C5000 | 0x00000018 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x000C6000 | 0x0000005D | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.38389 |
.rsrc | 0x000C7000 | 0x000216F0 | 0x00021800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.616 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.18295 | 1830 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 2.80552 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 3.40448 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 3.76613 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 4.12824 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 4.64443 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
4086 | 3.16547 | 864 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4087 | 3.40938 | 608 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4088 | 3.31153 | 1116 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4089 | 3.33977 | 1036 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
netapi32.dll |
oleaut32.dll |
user32.dll |
version.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x000BE63C |
__dbk_fcall_wrapper | 2 | 0x0000D0A0 |
TMethodImplementationIntercept | 3 | 0x00054060 |
Total processes
128
Monitored processes
74
Malicious processes
37
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "sc.exe" failure WCAssistantService reset= 30 actions= restart/60000 | C:\Windows\system32\sc.exe | — | WebCompanionInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1144,5313401263576883230,11217598566103782768,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2872 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1144,5313401263576883230,11217598566103782768,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1324 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 328 | "C:\Program Files\AVAST Software\Browser\Application\AvastBrowser.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --field-trial-handle=1044,18295711688628989072,9922035496109016035,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1472 /prefetch:8 | C:\Program Files\AVAST Software\Browser\Application\AvastBrowser.exe | — | AvastBrowser.exe | |||||||||||
User: admin Company: AVAST Software Integrity Level: LOW Description: Avast Secure Browser Exit code: 0 Version: 95.0.12826.70 Modules
| |||||||||||||||
| 388 | netsh http add urlacl url=http://+:9007/ user=Everyone | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 656 | "C:\Program Files\AVAST Software\Browser\Application\AvastBrowser.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1044,18295711688628989072,9922035496109016035,131072 --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1228 /prefetch:8 | C:\Program Files\AVAST Software\Browser\Application\AvastBrowser.exe | AvastBrowser.exe | ||||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Secure Browser Exit code: 0 Version: 95.0.12826.70 Modules
| |||||||||||||||
| 884 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2484.38877\XSpammer\XSpammer Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2484.38877\XSpammer\XSpammer Setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Indxgo Development Integrity Level: HIGH Description: A feature-packed nuke bot with a slick and modern user-interface. Exit code: 2 Version: 1.0.0 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\AVAST Software\Browser\Application\AvastBrowser.exe" --type=renderer --instant-process --display-capture-permissions-policy-allowed --field-trial-handle=1044,18295711688628989072,9922035496109016035,131072 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=1928 /prefetch:1 | C:\Program Files\AVAST Software\Browser\Application\AvastBrowser.exe | — | AvastBrowser.exe | |||||||||||
User: admin Company: AVAST Software Integrity Level: LOW Description: Avast Secure Browser Exit code: 0 Version: 95.0.12826.70 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2508 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1580 | "C:\Program Files\GUM307.tmp\AvastBrowserUpdate.exe" /silent /install "bundlename=Avast Secure Browser&appguid={A8504530-742B-42BC-895D-2BAD6406F698}&appname=Avast Secure Browser&needsadmin=true&lang=en-US&brand=9145&ap=mv:95.0.12826.70&installargs=--make-chrome-default --force-default-win10 --reset-default-win10 --auto-import-data%3Diexplore --import-cookies --auto-launch-chrome --private-browsing" | C:\Program Files\GUM307.tmp\AvastBrowserUpdate.exe | AvastBrowserUpdateSetup.exe | ||||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Browser Exit code: 0 Version: 1.8.1189.1 Modules
| |||||||||||||||
Total events
98 298
Read events
93 841
Write events
4 427
Delete events
30
Modification events
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: AC080000C22C21CDAFDCD701 | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 29F92058134C1834CDB3C185340D1CAC9724844FF43673AB40070F3DC8C00E26 | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E5070B00040012001300090038001503010000001E768127E028094199FEB9D127C57AFE | |||
| (PID) Process: | (2220) XSpammer - Linkvertise Downloader_UE-6gC1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000003E251CE0AFDCD701 | |||
Executable files
257
Suspicious files
301
Text files
233
Unknown types
72
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\is-5L6VF.tmp | image | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\Avast_BRW.png | image | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\WebCompanionCHO.png | image | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\prod1 | compressed | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\prod0_extract\avast_secure_browser_setup.exe | executable | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\prod0 | compressed | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\is-QB1CT.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\is-F86PE.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\prod1.zip | compressed | |
MD5:— | SHA256:— | |||
| 2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | C:\Users\admin\AppData\Local\Temp\is-GVEUN.tmp\prod0.zip | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
87
DNS requests
62
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2844 | avast_secure_browser_setup.exe | GET | 200 | 18.66.107.157:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAXnDF%2BvrZJywhfVUsOKYQA%3D | US | der | 471 b | whitelisted |
2844 | avast_secure_browser_setup.exe | GET | 200 | 52.222.206.35:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
2612 | WebCompanionInstaller.exe | GET | 200 | 104.18.87.101:80 | http://wcdownloadercdn.lavasoft.com/7.0.2348.4179/WebCompanion-7.0.2348.4179-prod.zip | US | compressed | 10.4 Mb | whitelisted |
2844 | avast_secure_browser_setup.exe | GET | 200 | 18.66.92.28:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2844 | avast_secure_browser_setup.exe | GET | 200 | 52.222.206.73:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2612 | WebCompanionInstaller.exe | POST | 200 | 64.18.87.81:80 | http://wc-update-service.lavasoft.com/update.asmx | CA | xml | 1.43 Kb | whitelisted |
2612 | WebCompanionInstaller.exe | POST | 200 | 104.18.88.101:80 | http://flow.lavasoft.com/v1/event-stat-wc?Type=ProgressInstall&ProductID=wc&EventVersion=1 | US | binary | 29 b | whitelisted |
2612 | WebCompanionInstaller.exe | POST | 200 | 104.18.88.101:80 | http://flow.lavasoft.com/v1/event-stat-wc?Type=ProgressInstall&ProductID=wc&EventVersion=1 | US | binary | 29 b | whitelisted |
2612 | WebCompanionInstaller.exe | POST | 200 | 104.18.88.101:80 | http://flow.lavasoft.com/v1/event-stat-wc?Type=ProgressInstall&ProductID=wc&EventVersion=1 | US | binary | 29 b | whitelisted |
2612 | WebCompanionInstaller.exe | POST | 200 | 104.18.88.101:80 | http://flow.lavasoft.com/v1/event-stat-wc?Type=ProgressInstall&ProductID=wc&EventVersion=1 | US | binary | 29 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2220 | XSpammer - Linkvertise Downloader_UE-6gC1.tmp | 18.66.107.23:443 | d17kz3i6hbr7d3.cloudfront.net | Massachusetts Institute of Technology | US | unknown |
2844 | avast_secure_browser_setup.exe | 54.197.240.204:443 | stats.avastbrowser.com | Amazon.com, Inc. | US | unknown |
2844 | avast_secure_browser_setup.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2612 | WebCompanionInstaller.exe | 104.18.88.101:80 | flow.lavasoft.com | Cloudflare Inc | US | shared |
2844 | avast_secure_browser_setup.exe | 18.66.107.157:80 | ocsp.sca1b.amazontrust.com | Massachusetts Institute of Technology | US | whitelisted |
2612 | WebCompanionInstaller.exe | 64.18.87.81:80 | wc-update-service.lavasoft.com | COGECODATA | CA | unknown |
2612 | WebCompanionInstaller.exe | 104.18.87.101:80 | flow.lavasoft.com | Cloudflare Inc | US | shared |
3156 | AvastBrowserUpdate.exe | 54.174.23.53:443 | update.avastbrowser.com | Amazon.com, Inc. | US | unknown |
2460 | AvastBrowserUpdate.exe | 54.174.23.53:443 | update.avastbrowser.com | Amazon.com, Inc. | US | unknown |
2460 | AvastBrowserUpdate.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d17kz3i6hbr7d3.cloudfront.net |
| whitelisted |
stats.avastbrowser.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
flow.lavasoft.com |
| whitelisted |
ocsp.sca1b.amazontrust.com |
| whitelisted |
wc-update-service.lavasoft.com |
| whitelisted |
wcdownloadercdn.lavasoft.com |
| whitelisted |
Threats
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
WebCompanionInstaller.exe | Detecting windows culture
|
WebCompanionInstaller.exe | 11/18/2021 7:10:01 PM :-> Starting installer 7.0.2348.4179 with: .\WebCompanionInstaller.exe --partner=IC201101 --version=7.0.2348.4179 --prod --silent --install --prod --platform=prod --partner=IC201101, Run as admin: True
|
WebCompanionInstaller.exe | Preparing for installing Web Companion
|
WebCompanionInstaller.exe | 11/18/2021 7:10:02 PM :-> Generating Machine and Install Id ...
|
WebCompanionInstaller.exe | 11/18/2021 7:10:02 PM :-> Machine Id and Install Id has been generated
|
WebCompanionInstaller.exe | 11/18/2021 7:10:02 PM :-> Checking prerequisites ...
|
WebCompanionInstaller.exe | 11/18/2021 7:10:02 PM :-> Antivirus not detected
|
WebCompanionInstaller.exe | 11/18/2021 7:10:03 PM :-> vm_check False
|
WebCompanionInstaller.exe | 11/18/2021 7:10:03 PM :-> reg_check :False
|
WebCompanionInstaller.exe | 11/18/2021 7:10:03 PM :-> Installed .Net framework is V40
|