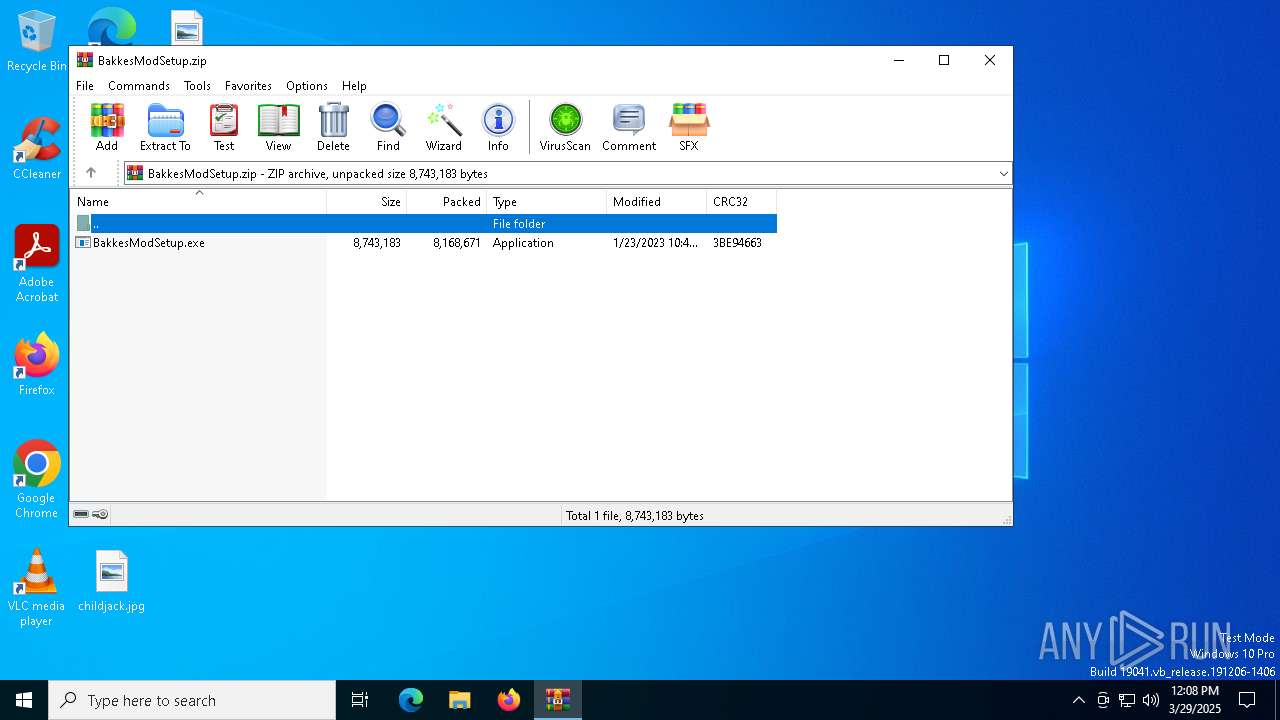
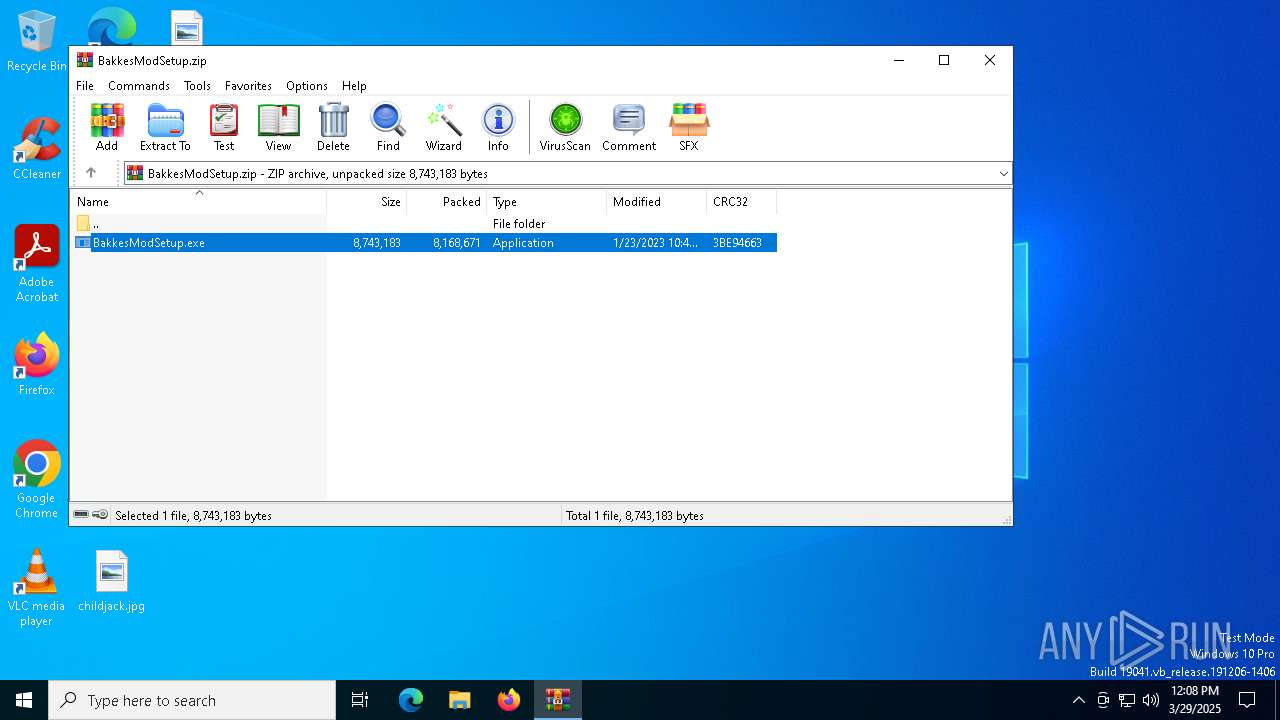
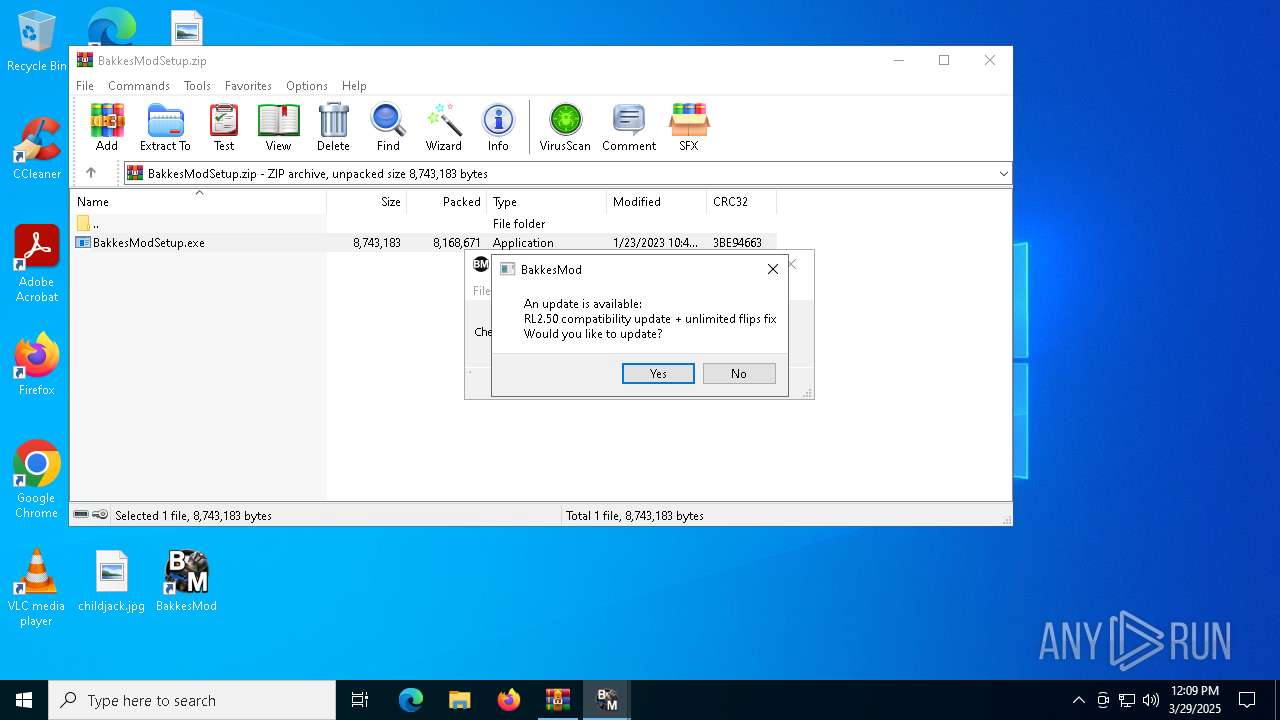
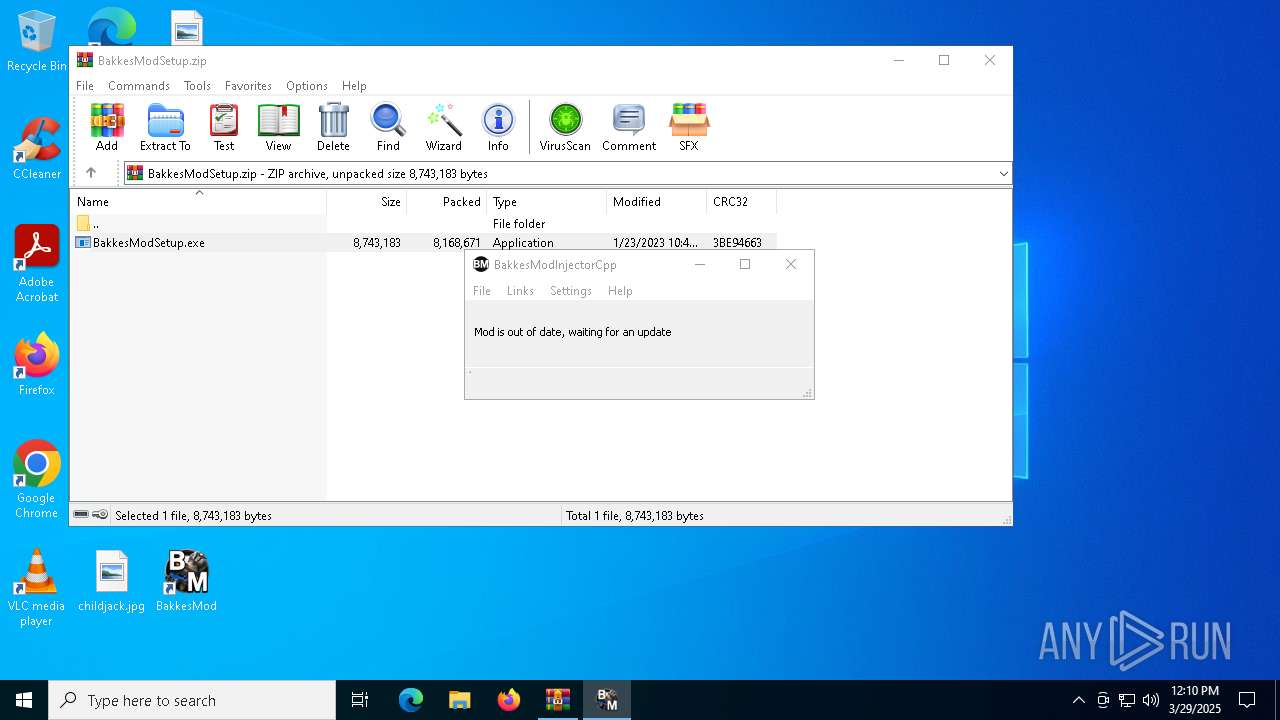
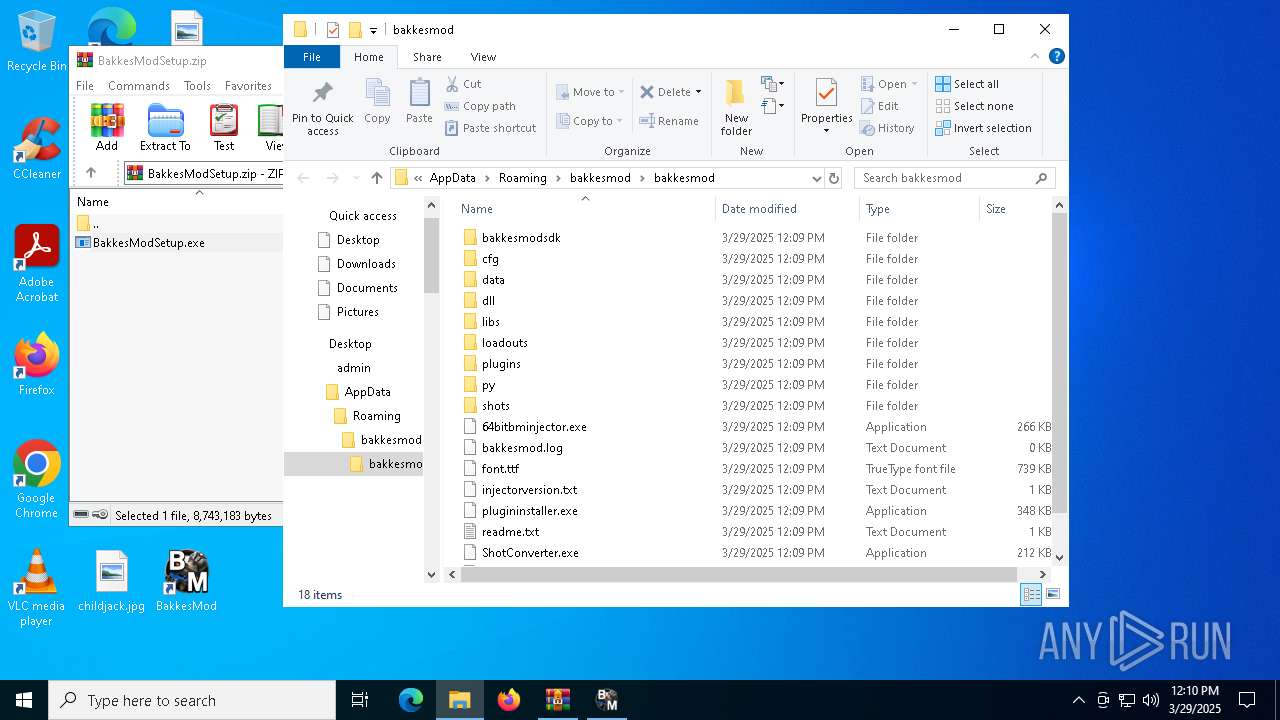
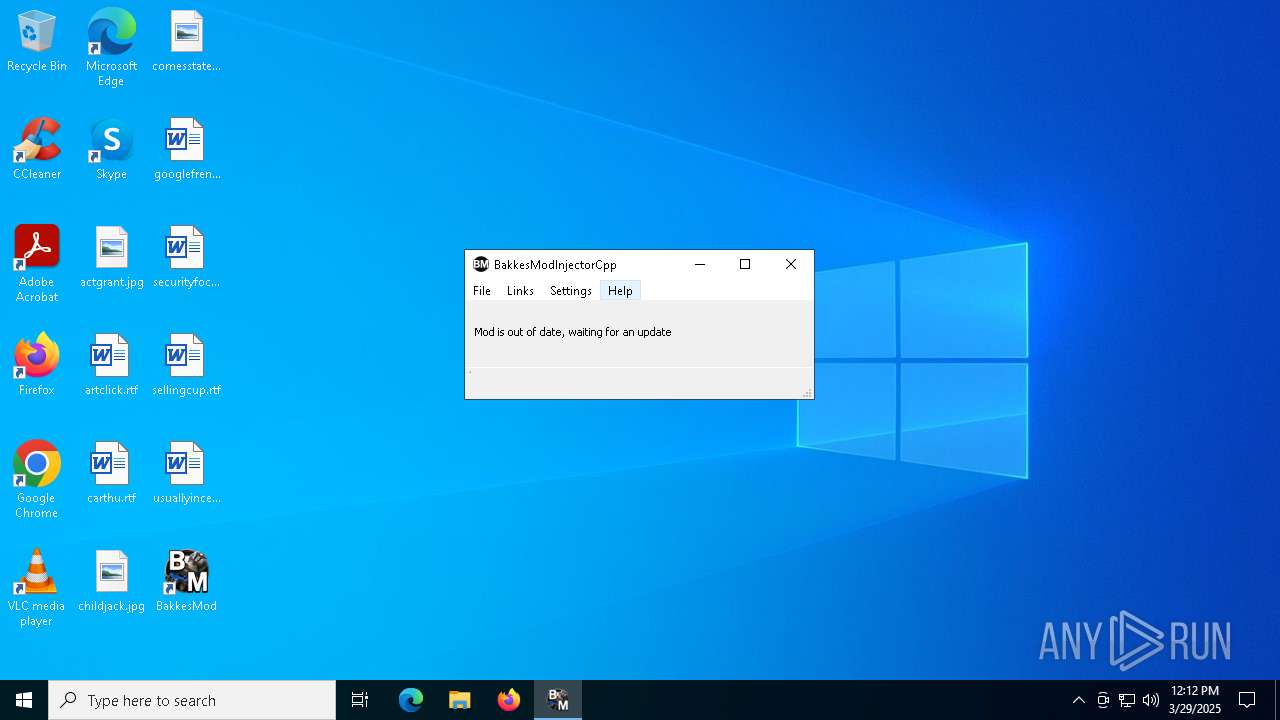
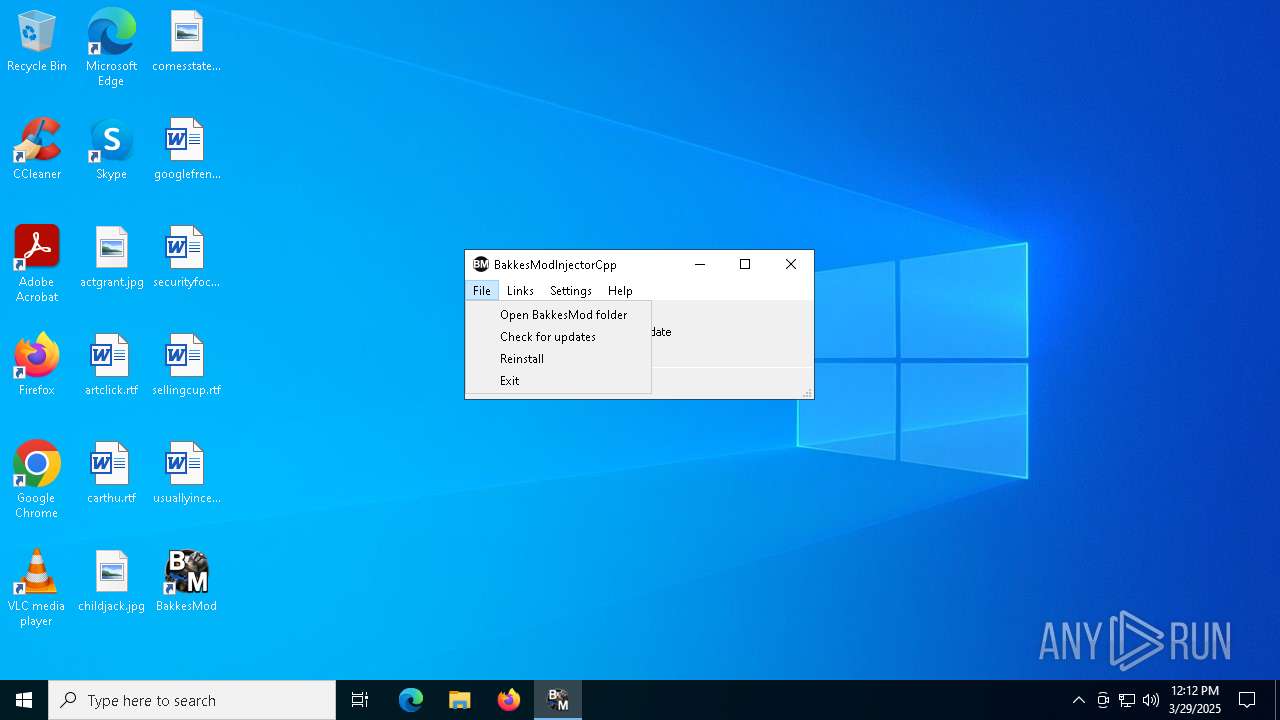
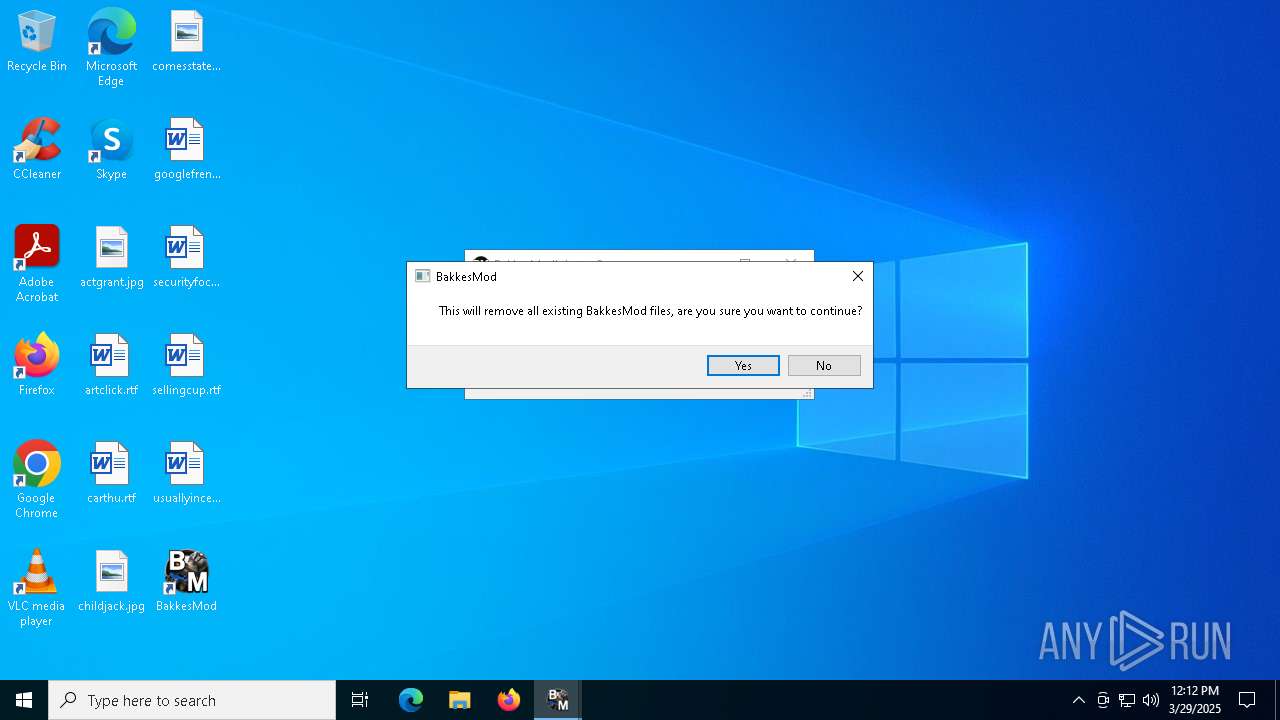
| File name: | BakkesModSetup.zip |
| Full analysis: | https://app.any.run/tasks/50acc429-f3de-4064-85a7-636e8788657e |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2025, 12:08:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C6E0152420E778581A0C6365A2A9B3D6 |
| SHA1: | C148956612DDD7EE5710E2CDD36CE0AA10AA9026 |
| SHA256: | 10C80FB4040AAA2FD66C1E46AC2A5D08E8992A60784DF68E5086EB9DEB585F17 |
| SSDEEP: | 98304:/tllry4KhrBNlQWwHo5wBBizXeqISj6m+giJxGPidk0Mh8DsmFNTjGdxvaHkDuQk:KthCeew7iagTfakx |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6184)
Changes the autorun value in the registry
- BakkesMod.exe (PID: 3132)
- BakkesMod.exe (PID: 1052)
SUSPICIOUS
Executable content was dropped or overwritten
- BakkesModSetup.exe (PID: 6476)
- BakkesModSetup.exe (PID: 3100)
- BakkesModSetup.tmp (PID: 2148)
- BakkesMod.exe (PID: 3132)
- BakkesMod.exe (PID: 1052)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6184)
- BakkesModSetup.tmp (PID: 1132)
- BakkesMod.exe (PID: 3132)
- BakkesMod.exe (PID: 7084)
Reads the Windows owner or organization settings
- BakkesModSetup.tmp (PID: 2148)
Uses TASKKILL.EXE to kill process
- BakkesModSetup.tmp (PID: 2148)
Creates file in the systems drive root
- BakkesMod.exe (PID: 7084)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6184)
Create files in a temporary directory
- BakkesModSetup.exe (PID: 6476)
- BakkesModSetup.exe (PID: 3100)
- BakkesMod.exe (PID: 3132)
- BakkesMod.exe (PID: 7084)
- BakkesMod.exe (PID: 1052)
- BakkesModSetup.tmp (PID: 2148)
Checks supported languages
- BakkesModSetup.exe (PID: 6476)
- BakkesModSetup.tmp (PID: 1132)
- BakkesModSetup.exe (PID: 3100)
- BakkesModSetup.tmp (PID: 2148)
- BakkesMod.exe (PID: 3132)
- BakkesMod.exe (PID: 7084)
- BakkesMod.exe (PID: 1052)
Reads the computer name
- BakkesModSetup.tmp (PID: 1132)
- BakkesModSetup.tmp (PID: 2148)
- BakkesMod.exe (PID: 3132)
- BakkesMod.exe (PID: 7084)
- BakkesMod.exe (PID: 1052)
Process checks computer location settings
- BakkesModSetup.tmp (PID: 1132)
Detects InnoSetup installer (YARA)
- BakkesModSetup.exe (PID: 6476)
- BakkesModSetup.tmp (PID: 1132)
- BakkesModSetup.exe (PID: 3100)
- BakkesModSetup.tmp (PID: 2148)
Compiled with Borland Delphi (YARA)
- BakkesModSetup.exe (PID: 6476)
- BakkesModSetup.exe (PID: 3100)
- BakkesModSetup.tmp (PID: 2148)
- BakkesModSetup.tmp (PID: 1132)
Creates files in the program directory
- BakkesModSetup.tmp (PID: 2148)
Reads the software policy settings
- slui.exe (PID: 1088)
- slui.exe (PID: 728)
Creates a software uninstall entry
- BakkesModSetup.tmp (PID: 2148)
Creates files or folders in the user directory
- BakkesMod.exe (PID: 3132)
- BakkesMod.exe (PID: 1052)
Manual execution by a user
- notepad.exe (PID: 4696)
- BakkesMod.exe (PID: 7084)
- BakkesMod.exe (PID: 1052)
- Taskmgr.exe (PID: 4200)
- Taskmgr.exe (PID: 5984)
Checks proxy server information
- slui.exe (PID: 728)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:01:23 23:49:32 |
| ZipCRC: | 0x3be94663 |
| ZipCompressedSize: | 8168671 |
| ZipUncompressedSize: | 8743183 |
| ZipFileName: | BakkesModSetup.exe |
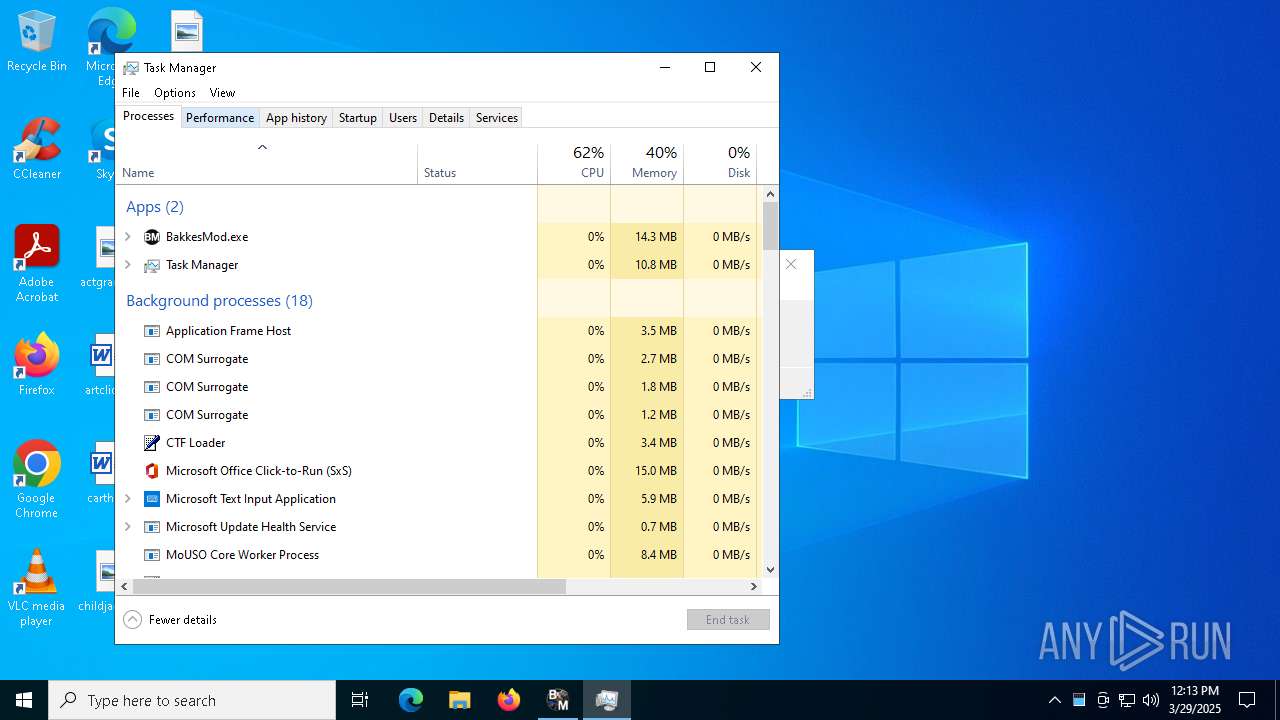
Total processes
153
Monitored processes
19
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Program Files\BakkesMod\BakkesMod.exe" | C:\Program Files\BakkesMod\BakkesMod.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1088 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
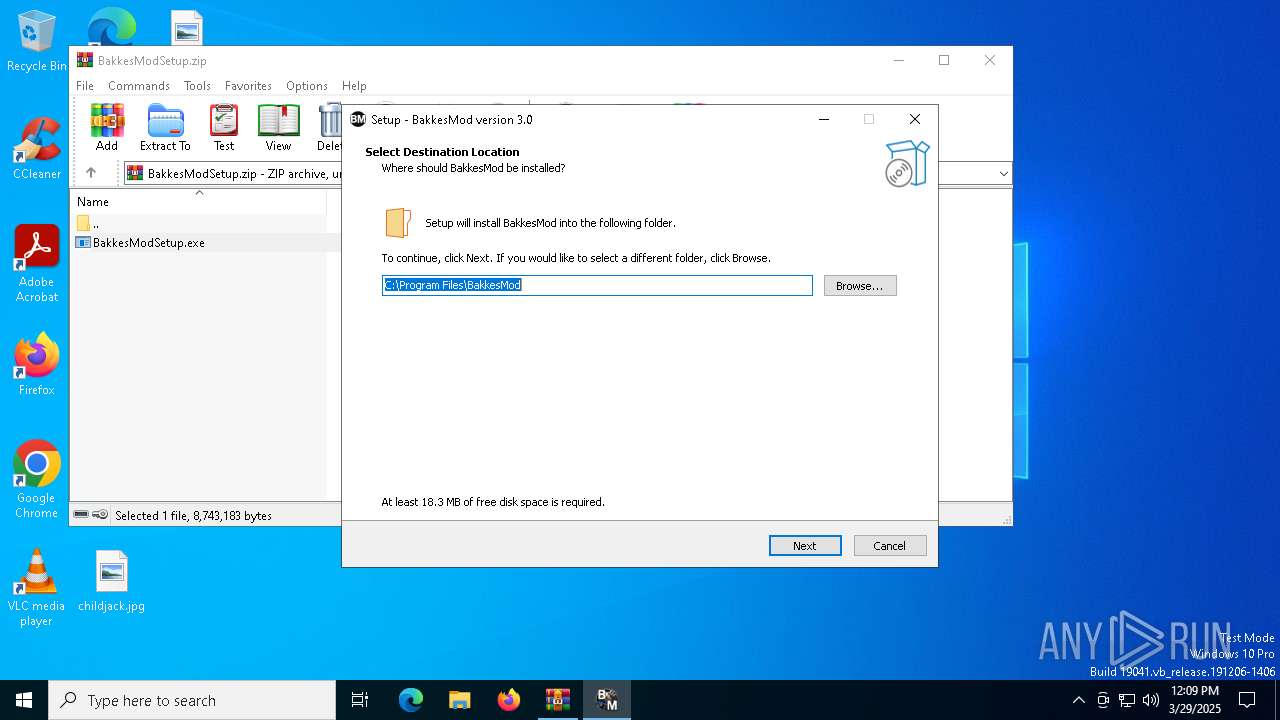
| 1132 | "C:\Users\admin\AppData\Local\Temp\is-QTD3I.tmp\BakkesModSetup.tmp" /SL5="$30264,7803864,941056,C:\Users\admin\AppData\Local\Temp\Rar$EXa6184.44598\BakkesModSetup.exe" | C:\Users\admin\AppData\Local\Temp\is-QTD3I.tmp\BakkesModSetup.tmp | — | BakkesModSetup.exe | |||||||||||
User: admin Company: BakkesMod Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\AppData\Local\Temp\is-5J1LS.tmp\BakkesModSetup.tmp" /SL5="$80306,7803864,941056,C:\Users\admin\AppData\Local\Temp\Rar$EXa6184.44598\BakkesModSetup.exe" /SPAWNWND=$40270 /NOTIFYWND=$30264 | C:\Users\admin\AppData\Local\Temp\is-5J1LS.tmp\BakkesModSetup.tmp | BakkesModSetup.exe | ||||||||||||
User: admin Company: BakkesMod Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2384 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6184.44598\BakkesModSetup.exe" /SPAWNWND=$40270 /NOTIFYWND=$30264 | C:\Users\admin\AppData\Local\Temp\Rar$EXa6184.44598\BakkesModSetup.exe | BakkesModSetup.tmp | ||||||||||||
User: admin Company: BakkesMod Integrity Level: HIGH Description: BakkesMod Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3132 | "C:\Program Files\BakkesMod\BakkesMod.exe" | C:\Program Files\BakkesMod\BakkesMod.exe | BakkesModSetup.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
8 153
Read events
8 037
Write events
101
Delete events
15
Modification events
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BakkesModSetup.zip | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2148) BakkesModSetup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\BakkesMod |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files\BakkesMod | |||
| (PID) Process: | (2148) BakkesModSetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{BF029534-4334-4CFC-B771-50B7EE54346F}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.0 | |||
Executable files
53
Suspicious files
37
Text files
481
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2148 | BakkesModSetup.tmp | C:\Program Files\BakkesMod\unins000.exe | executable | |
MD5:AEA069292728AE441A5EE55729DD46B6 | SHA256:AB8FA587AA83FC0526B29DCA0F342268721460F9EC31CEC2938547F81D583FCA | |||
| 6476 | BakkesModSetup.exe | C:\Users\admin\AppData\Local\Temp\is-QTD3I.tmp\BakkesModSetup.tmp | executable | |
MD5:8F4A51F9A89E8E04FC8A465436B5BBA9 | SHA256:6C0C57A9DEA98D5A31DBF99D880DD828D094965397FE453F20FE186C55B33265 | |||
| 2148 | BakkesModSetup.tmp | C:\Users\admin\AppData\Local\Temp\is-NQ1LN.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 2148 | BakkesModSetup.tmp | C:\Program Files\BakkesMod\is-ST81B.tmp | executable | |
MD5:AEA069292728AE441A5EE55729DD46B6 | SHA256:AB8FA587AA83FC0526B29DCA0F342268721460F9EC31CEC2938547F81D583FCA | |||
| 3100 | BakkesModSetup.exe | C:\Users\admin\AppData\Local\Temp\is-5J1LS.tmp\BakkesModSetup.tmp | executable | |
MD5:8F4A51F9A89E8E04FC8A465436B5BBA9 | SHA256:6C0C57A9DEA98D5A31DBF99D880DD828D094965397FE453F20FE186C55B33265 | |||
| 2148 | BakkesModSetup.tmp | C:\Users\Public\Desktop\BakkesMod.lnk | binary | |
MD5:14FD1B4E11CF75D8BBDD5E9062762CD1 | SHA256:8A9E36CDBE9713F76DA867B6E834F010BD6E8EA65DA522E7F32A84165EF72FBD | |||
| 2148 | BakkesModSetup.tmp | C:\Program Files\BakkesMod\BakkesMod.exe | executable | |
MD5:11EFF18A407E2764C198D7B1E7DADB14 | SHA256:7A6B97BF43453C47D905C6F49E3CC6EE8B70F0E289700AA6145F40577CA7B5D4 | |||
| 6184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6184.44598\BakkesModSetup.exe | executable | |
MD5:B2554EFC048201C086D7BE46F42D00BD | SHA256:D4581C971CA9DA0B40B609ED356A986B33E4E81289EDACD31DC7AB8348A14D20 | |||
| 2148 | BakkesModSetup.tmp | C:\Program Files\BakkesMod\is-F62ML.tmp | executable | |
MD5:11EFF18A407E2764C198D7B1E7DADB14 | SHA256:7A6B97BF43453C47D905C6F49E3CC6EE8B70F0E289700AA6145F40577CA7B5D4 | |||
| 3132 | BakkesMod.exe | C:\Users\admin\AppData\Roaming\bakkesmod\bakkesmod\bakkesmodsdk\bakkesmod-patch.exe | executable | |
MD5:70808566413A9E0F96496381AF7B120E | SHA256:34706EF576F97BE93A917D80EC8952521020ADA1B481AAC23525C13C620BFE72 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
41
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
664 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
664 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 184.24.77.50:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgQ02IdIIbAc4DlYPDoBfAmajw%3D%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
664 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
664 | SIHClient.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
664 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3132 | BakkesMod.exe | 149.210.150.107:443 | updater.bakkesmod.com | Signet B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
updater.bakkesmod.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r10.o.lencr.org |
| whitelisted |