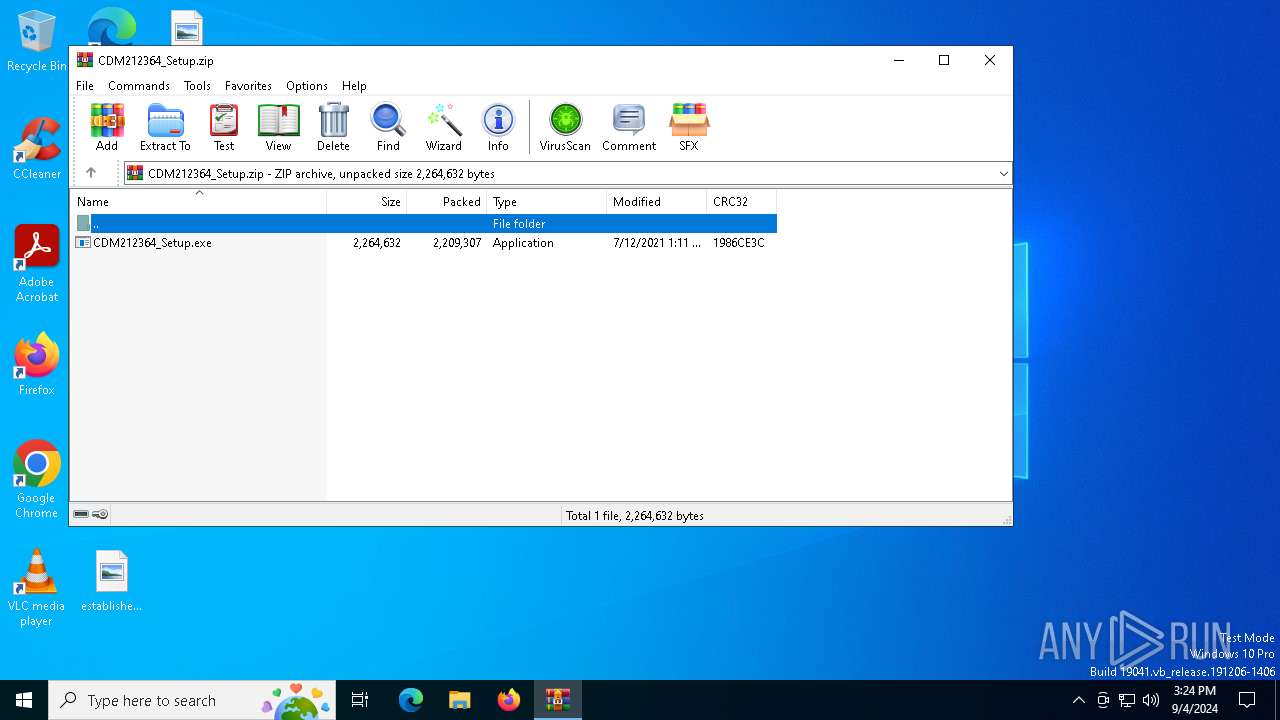
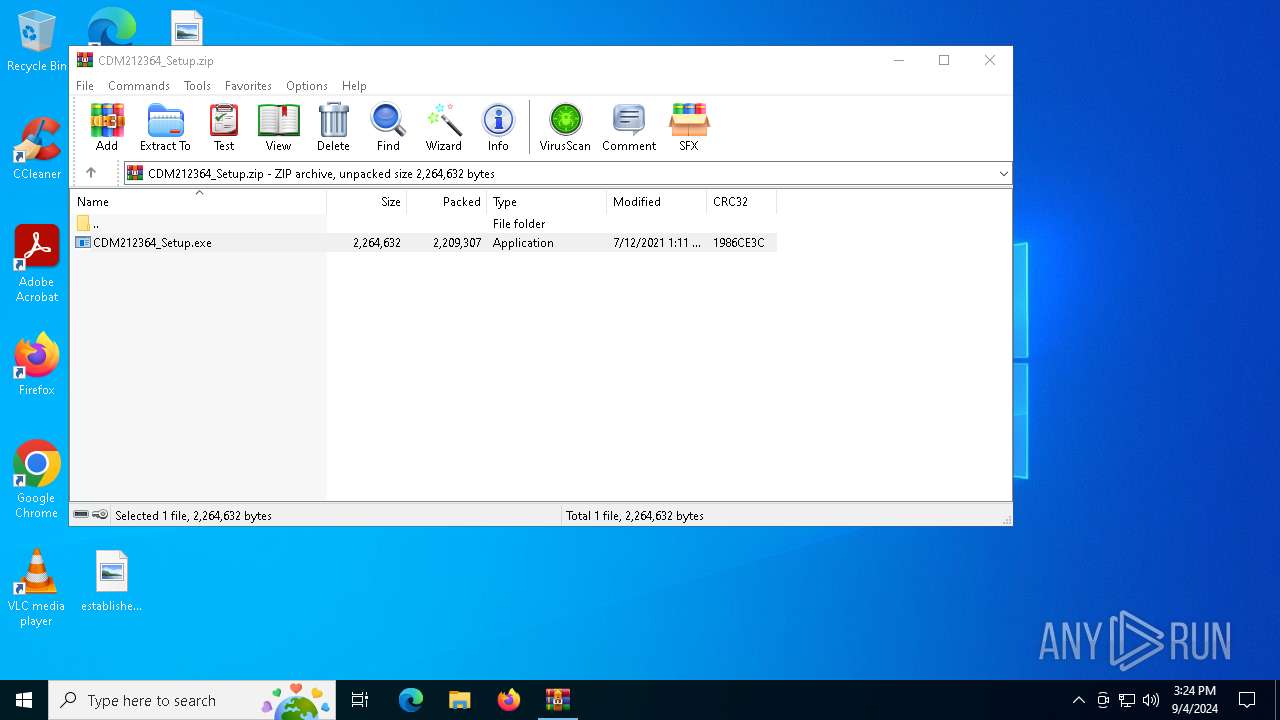
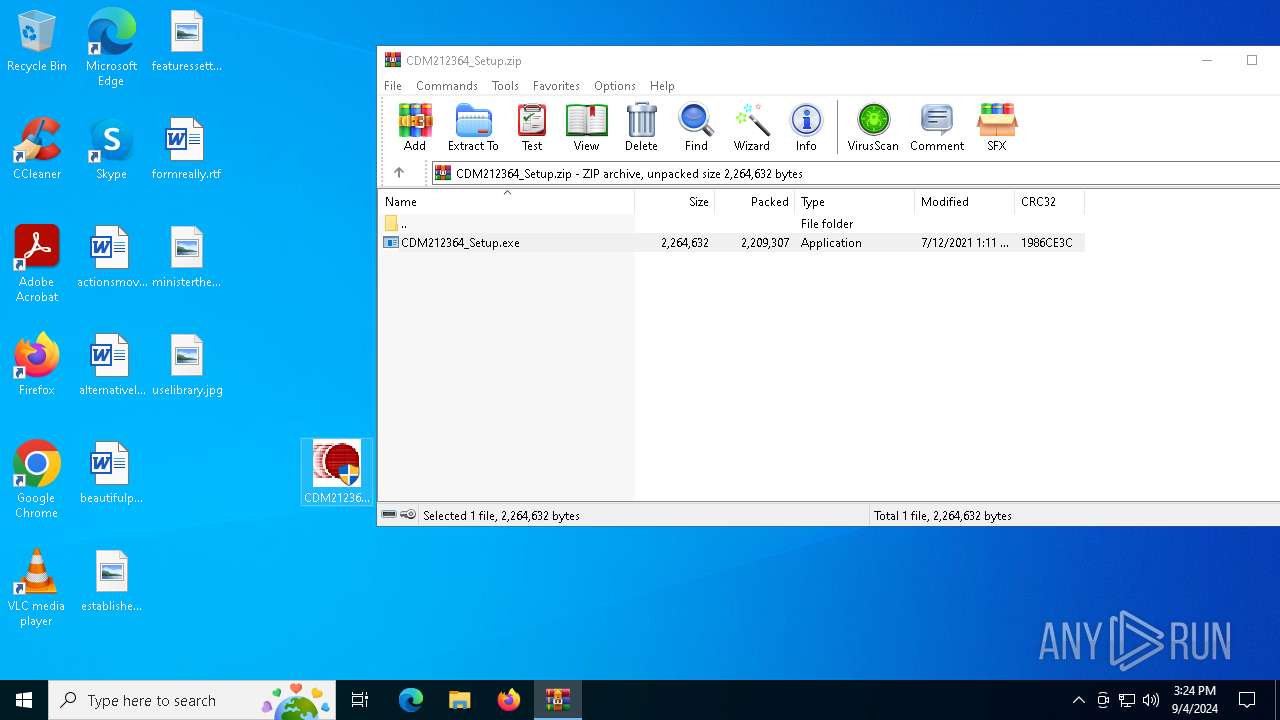
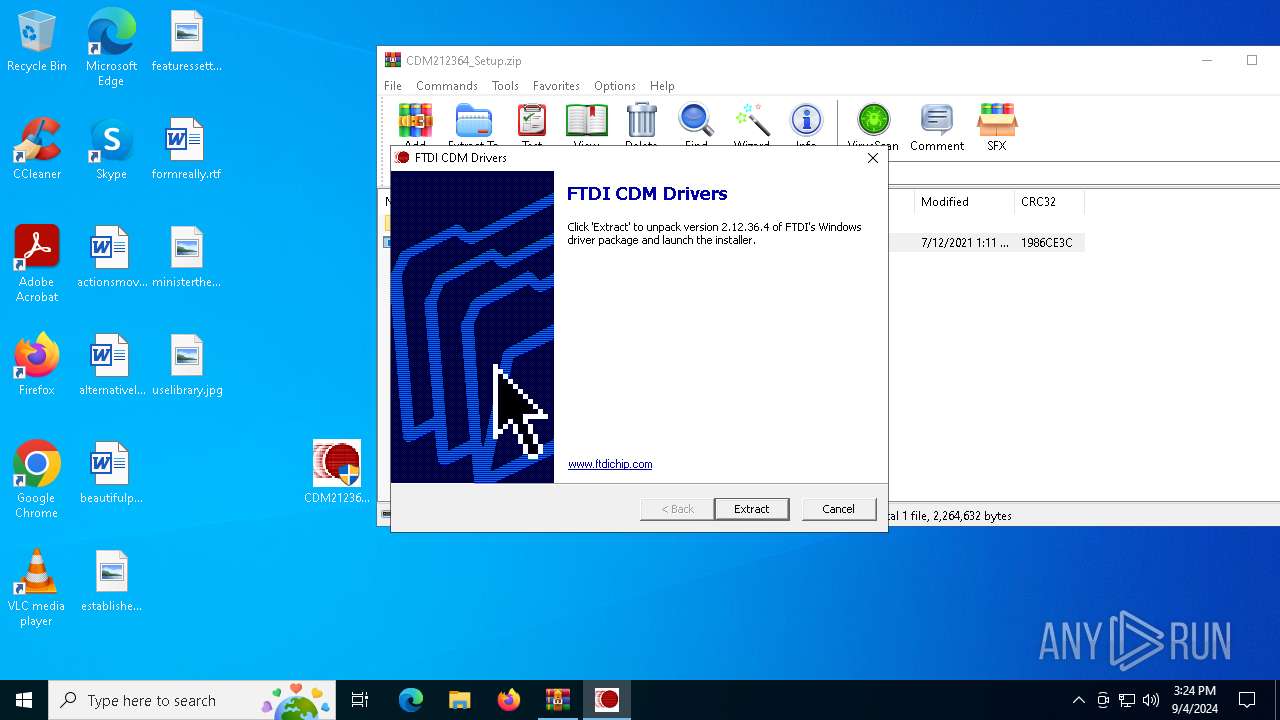
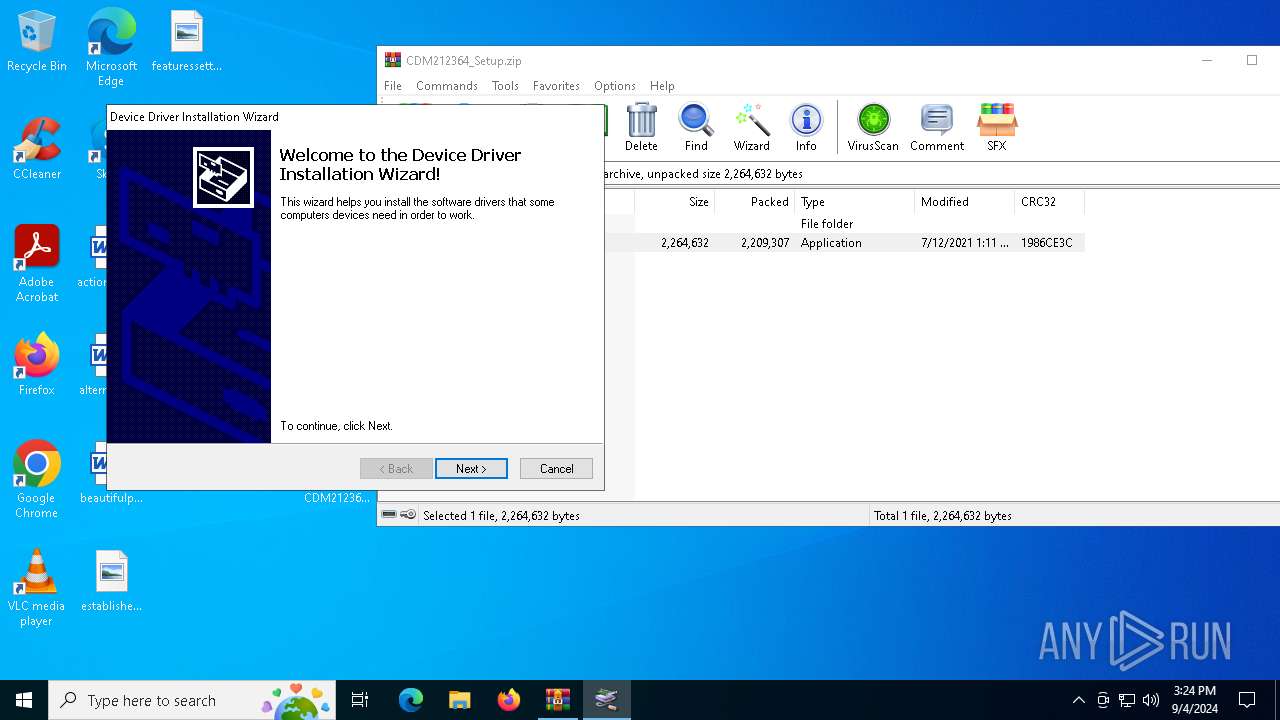
| download: | /wp-content/uploads/2021/08/CDM212364_Setup.zip |
| Full analysis: | https://app.any.run/tasks/e7af8fc4-286d-489a-9f99-dc63416a48e1 |
| Verdict: | Malicious activity |
| Analysis date: | September 04, 2024, 15:24:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 09B8D1E4F64828A2012AE54A7746D6D5 |
| SHA1: | 1B1FA041EFF7B6FAB10E9FE73D3149C4DB750886 |
| SHA256: | 10C399AC784D2B68B1BB2BA598BAB7FE00CFDFD267B4CC14A3E3240FE9499FB1 |
| SSDEEP: | 49152:8GehdaQ/cr5lWZGiPsM3eg2FF56gtGRzDHaNTC4jt92Wh:padfioGiUMH2bLt6LaNTCGt92Wh |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- drvinst.exe (PID: 6052)
- CDM212364_Setup.exe (PID: 5468)
- dpinst-amd64.exe (PID: 4704)
- drvinst.exe (PID: 1840)
Drops a system driver (possible attempt to evade defenses)
- CDM212364_Setup.exe (PID: 5468)
- dpinst-amd64.exe (PID: 4704)
- drvinst.exe (PID: 6052)
- drvinst.exe (PID: 1840)
Process drops legitimate windows executable
- CDM212364_Setup.exe (PID: 5468)
Starts a Microsoft application from unusual location
- dpinst-amd64.exe (PID: 4704)
Checks Windows Trust Settings
- drvinst.exe (PID: 6052)
- drvinst.exe (PID: 1840)
Creates files in the driver directory
- drvinst.exe (PID: 1840)
- drvinst.exe (PID: 6052)
INFO
Create files in a temporary directory
- CDM212364_Setup.exe (PID: 5468)
- dpinst-amd64.exe (PID: 4704)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3728)
Checks supported languages
- CDM212364_Setup.exe (PID: 5468)
- dp-chooser.exe (PID: 6840)
- dpinst-amd64.exe (PID: 4704)
- drvinst.exe (PID: 6052)
- drvinst.exe (PID: 1840)
The process uses the downloaded file
- WinRAR.exe (PID: 3728)
Manual execution by a user
- CDM212364_Setup.exe (PID: 6660)
- CDM212364_Setup.exe (PID: 5468)
Reads the computer name
- CDM212364_Setup.exe (PID: 5468)
- drvinst.exe (PID: 6052)
- drvinst.exe (PID: 1840)
- dpinst-amd64.exe (PID: 4704)
Reads the machine GUID from the registry
- drvinst.exe (PID: 6052)
- drvinst.exe (PID: 1840)
Reads the software policy settings
- drvinst.exe (PID: 1840)
- drvinst.exe (PID: 6052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:07:12 13:11:30 |
| ZipCRC: | 0x1986ce3c |
| ZipCompressedSize: | 2209307 |
| ZipUncompressedSize: | 2264632 |
| ZipFileName: | CDM212364_Setup.exe |
Total processes
133
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1840 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{c2d9b399-96af-6444-b0c8-b9b167c63d96}\ftdiport.inf" "9" "461a5a59f" "00000000000001EC" "WinSta0\Default" "00000000000001E8" "208" "c:\users\admin\appdata\local\temp\ftdi-driver" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3728 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\CDM212364_Setup.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4704 | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\dpinst-amd64.exe /sa | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\dpinst-amd64.exe | dp-chooser.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 512 Version: 2.1 Modules
| |||||||||||||||
| 5468 | "C:\Users\admin\Desktop\CDM212364_Setup.exe" | C:\Users\admin\Desktop\CDM212364_Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 6052 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{087e8e6c-3c3b-b543-a2b4-3305ea07a0b6}\ftdibus.inf" "9" "4a9ba6403" "00000000000001CC" "WinSta0\Default" "00000000000001DC" "208" "c:\users\admin\appdata\local\temp\ftdi-driver" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6660 | "C:\Users\admin\Desktop\CDM212364_Setup.exe" | C:\Users\admin\Desktop\CDM212364_Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6840 | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\dp-chooser.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\dp-chooser.exe | — | CDM212364_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
7 799
Read events
7 782
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CDM212364_Setup.zip | |||
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4704) dpinst-amd64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000100002E000000C004000017020000 | |||
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (3728) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
51
Suspicious files
8
Text files
18
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3728.29018\CDM212364_Setup.exe | executable | |
MD5:0C97E7B5DE1B46FB723BED38F0DE28A2 | SHA256:835DD64B199190D20DC37C0CADEB064B7EAAAEF271703781B2B259B7085437A4 | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\amd64\ftcserco.dll | executable | |
MD5:AA69BF96E10F463082A0664B7A2E9FAE | SHA256:C0224B9EF14365F6DDA96134CC77D978E69FBD61EFDADE6FD1EB676418C41023 | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\amd64\ftd2xx.lib | obj | |
MD5:2C6C133941002E602D1AC6831CBB7368 | SHA256:7C3A73D3A2441B460F03358BC8CC81E5F3FB43523BFA35E4EEF3BBE8BAD5788D | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\amd64\ftserui2.dll | executable | |
MD5:3E5BCD980AF8B20313005D9A492CEC8A | SHA256:55A23A2AC263E10B77D7E95601439F771062F2C248A8D93039A968D66100C39C | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\ftd2xx.h | text | |
MD5:08FBBF757A92B079CA66FF62D99A6C82 | SHA256:EE0C6358BA2F13015EC7B07AEA16BF3ADA33508851CC494FC256A8B28AF31147 | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\dpinst-x86.exe | executable | |
MD5:C2F2C1398C5CDB55A67676527EA29404 | SHA256:2BCA1650E3F7B9F98B06ED894CFD5EBC758E2B96EEB5D6C340D96E3F137D4472 | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\dpinst.xml | xml | |
MD5:BBB46E3360F3FCABC5D03CA33DC10458 | SHA256:65E9BC1F59DE53462ED2E6B002C0BE26CD3F37B1E360938A0A32AA452ED58030 | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\ftdibus.cat | binary | |
MD5:B392C785B9C2AA31187D1BD0A4F5EBA5 | SHA256:B286055896DEA79D4521368293DEEE801930F3FB503CC3076AC97716B338B0F7 | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\ftdibus.inf | text | |
MD5:B404B591DCAE1E28603479A7963CB6F6 | SHA256:FF361CDD7C814DB0BEA98578A731EF5C03BF457E06BCA9950FDBAB57A4D3C7F6 | |||
| 5468 | CDM212364_Setup.exe | C:\Users\admin\AppData\Local\Temp\FTDI-Driver\i386\ftbusui.dll | executable | |
MD5:107815287E29854DEF48BFB8341B9453 | SHA256:CE0B628933BECB2060A3B11A85C06146807ED03949F756036E6F93F597EC54C2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
36
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6856 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1780 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5180 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5180 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEASGp3XRNgzfylEWBFW6KKc%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6856 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4316 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6856 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1780 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1780 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
www.bing.com |
| whitelisted |