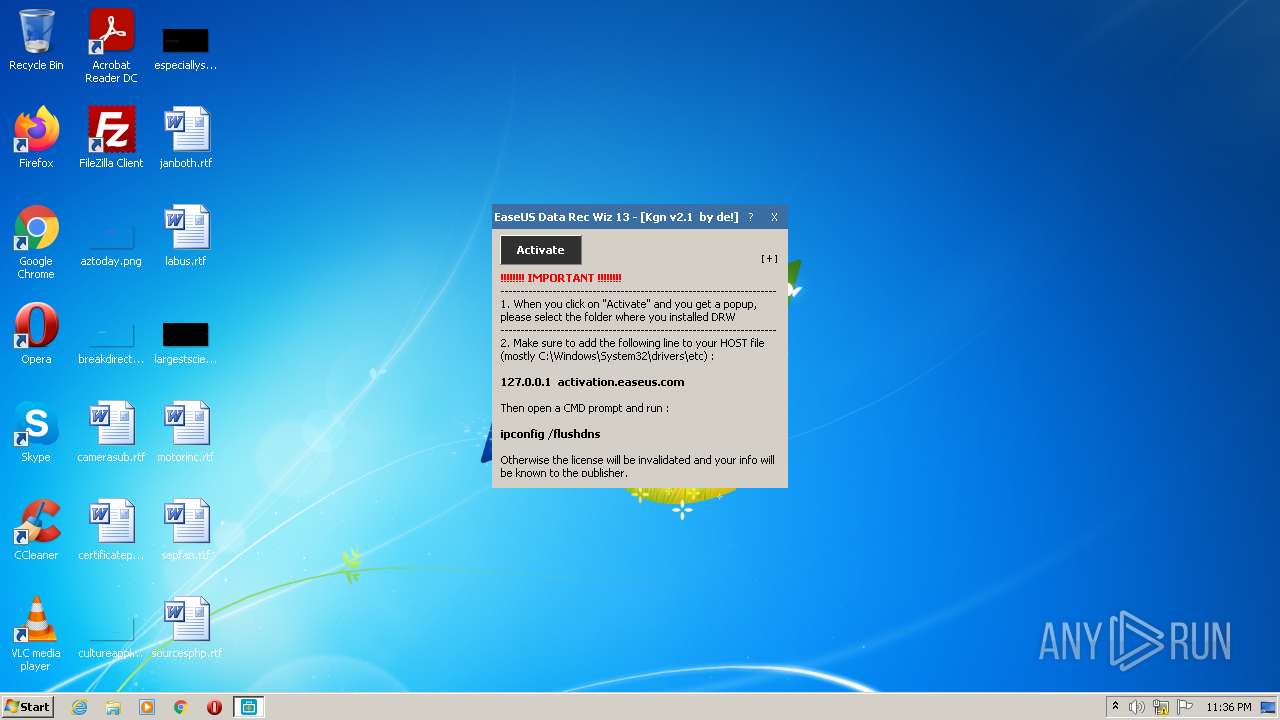
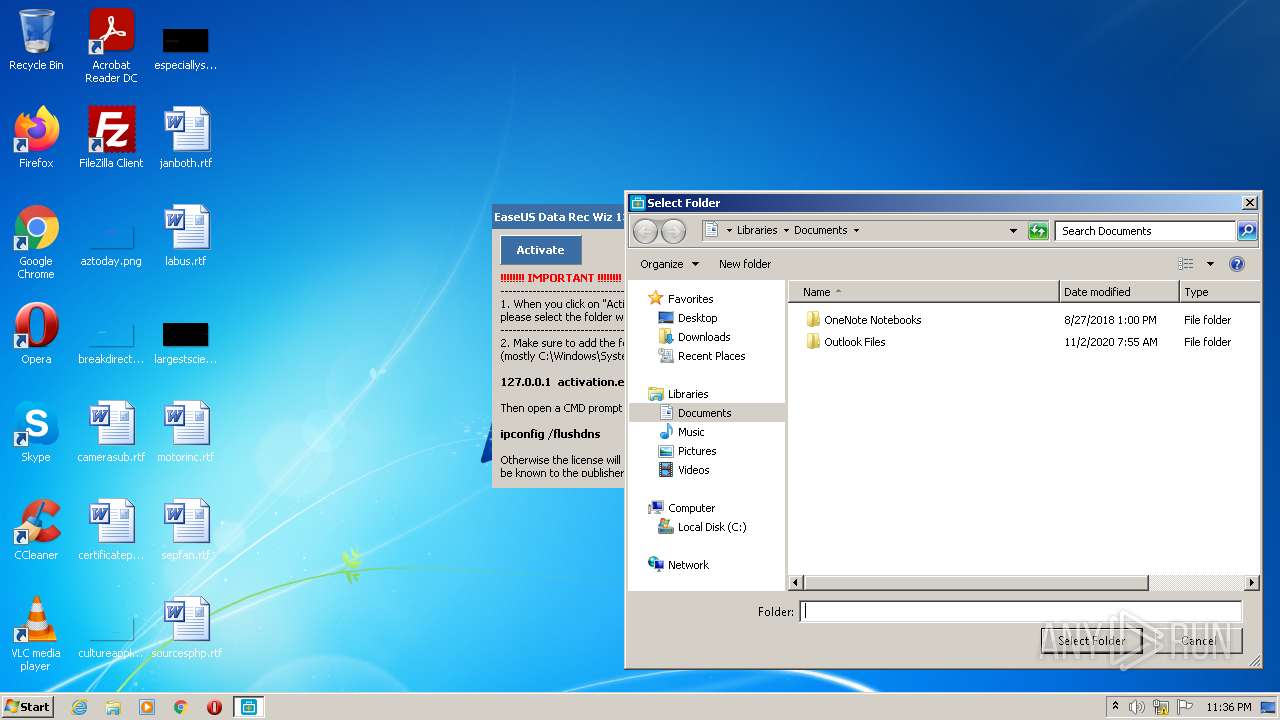
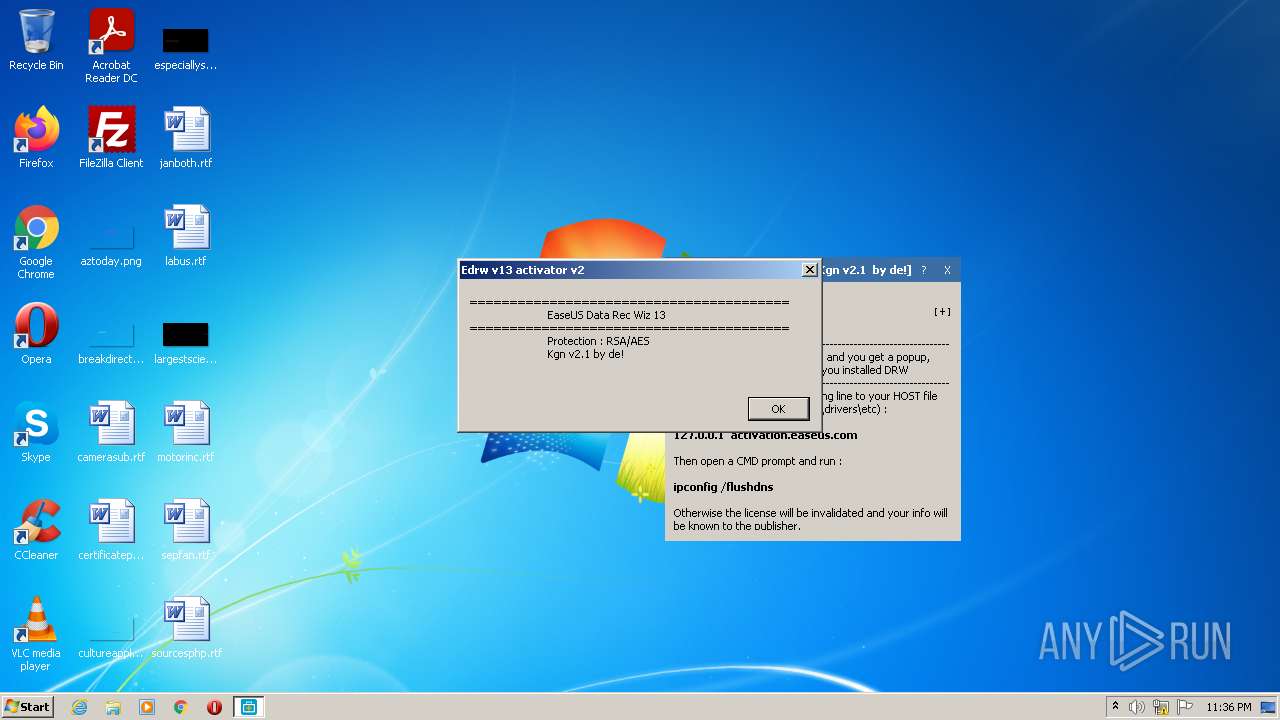
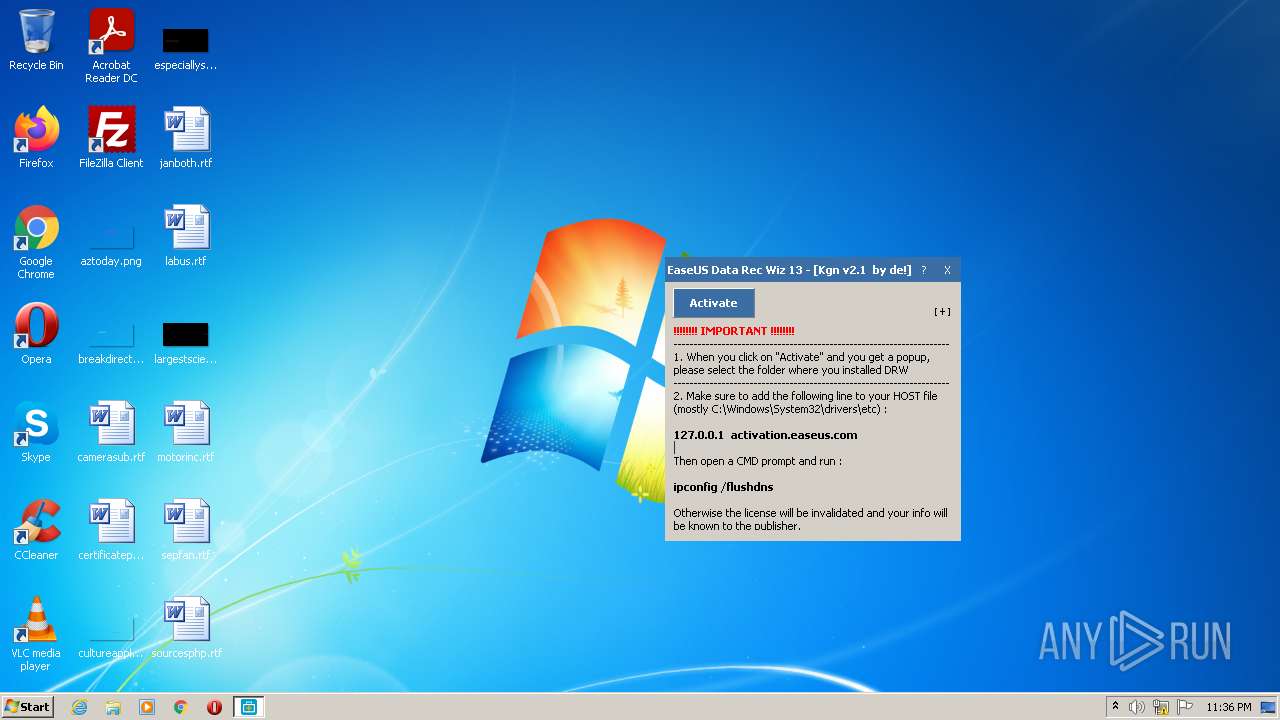
| File name: | EDRW v13 Activator v2.1 - De!.exe |
| Full analysis: | https://app.any.run/tasks/76a96330-7713-416c-900f-04bb33af7533 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2022, 23:36:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 284182F0388FE891ED6B6A1DA5B4196E |
| SHA1: | EE4FFEA0EB3CEEF561C7B02FBCC11F14A8775027 |
| SHA256: | 10BADD3B49C88AC87CE720C47CCD79F0DB4F8125D63B52D328E554FB549C44A8 |
| SSDEEP: | 24576:E3ub5cDzp/Ook9bVHIKAuTVijaUH2AcQNoMJ+CeWwIpA1JeuoSOBRcSrBIMmCpCB:q57cQKauDOTcSrqMmpnF8OMJLjelXl |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- EDRW v13 Activator v2.1 - De!.exe (PID: 2680)
Reads the computer name
- EDRW v13 Activator v2.1 - De!.exe (PID: 2680)
Searches for installed software
- EDRW v13 Activator v2.1 - De!.exe (PID: 2680)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (63.7) |
|---|---|---|
| .scr | | | Windows screen saver (20) |
| .exe | | | Win32 Executable (generic) (6.9) |
| .exe | | | Win16/32 Executable Delphi generic (3.1) |
| .exe | | | Generic Win/DOS Executable (3) |
EXIF
EXE
| ProductName: | EaseUS_DRW |
|---|---|
| FileDescription: | EaseUS_DRW |
| ProgramID: | com.embarcadero.EaseUS_DRW |
| ProductVersion: | 1.0.0.0 |
| FileVersion: | 2.0.0.0 |
| CharacterSet: | Windows, Latin1 |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 2.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | - |
| OSVersion: | 5 |
| EntryPoint: | 0x2305f4 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 1416704 |
| CodeSize: | 2288128 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| TimeStamp: | 2020:04:22 23:21:05+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 22-Apr-2020 21:21:05 |
| Detected languages: |
|
| FileVersion: | 2.0.0.0 |
| ProductVersion: | 1.0.0.0 |
| ProgramID: | com.embarcadero.EaseUS_DRW |
| FileDescription: | EaseUS_DRW |
| ProductName: | EaseUS_DRW |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 11 |
| Time date stamp: | 22-Apr-2020 21:21:05 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0022D1E0 | 0x0022D200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.47679 |
.itext | 0x0022F000 | 0x00001648 | 0x00001800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.09208 |
.data | 0x00231000 | 0x00009098 | 0x00009200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.74739 |
.bss | 0x0023B000 | 0x00006804 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00242000 | 0x00003146 | 0x00003200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.11707 |
.didata | 0x00246000 | 0x00000B6C | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.10436 |
.edata | 0x00247000 | 0x0000009C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.93164 |
.tls | 0x00248000 | 0x00000048 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00249000 | 0x0000005D | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.37218 |
.reloc | 0x0024A000 | 0x000324CC | 0x00032600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.27208 | 1836 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.48392 | 2440 | UNKNOWN | English - United States | RT_ICON |
3 | 3.43755 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 3.38911 | 9640 | UNKNOWN | English - United States | RT_ICON |
5 | 2.78272 | 16936 | UNKNOWN | English - United States | RT_ICON |
6 | 2.8229 | 38056 | UNKNOWN | English - United States | RT_ICON |
7 | 2.40723 | 67624 | UNKNOWN | English - United States | RT_ICON |
8 | 2.46802 | 152104 | UNKNOWN | English - United States | RT_ICON |
9 | 2.25388 | 270376 | UNKNOWN | English - United States | RT_ICON |
4074 | 3.24376 | 920 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
KERNEL32.DLL |
advapi32.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll (delay-loaded) |
netapi32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x0023E63C |
__dbk_fcall_wrapper | 2 | 0x000109D4 |
TMethodImplementationIntercept | 3 | 0x000D85C0 |
Total processes
40
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2680 | "C:\Users\admin\AppData\Local\Temp\EDRW v13 Activator v2.1 - De!.exe" | C:\Users\admin\AppData\Local\Temp\EDRW v13 Activator v2.1 - De!.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: EaseUS_DRW Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 3004 | "C:\Users\admin\AppData\Local\Temp\EDRW v13 Activator v2.1 - De!.exe" | C:\Users\admin\AppData\Local\Temp\EDRW v13 Activator v2.1 - De!.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: EaseUS_DRW Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
Total events
3 307
Read events
3 145
Write events
159
Delete events
3
Modification events
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000010000000D0000000C000000000000000B00000007000000060000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 4 |
Value: 45004400520057002000760031003300200041006300740069007600610074006F0072002000760032002E00310020002D0020004400650021002E0065007800650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000070020000BE000000F00400009E020000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 4 |
Value: 45004400520057002000760031003300200041006300740069007600610074006F0072002000760032002E00310020002D0020004400650021002E0065007800650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000070020000BE000000F00400009E020000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 4 |
Value: 45004400520057002000760031003300200041006300740069007600610074006F0072002000760032002E00310020002D0020004400650021002E0065007800650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800200006801000080020000680100000000000000000000000000000000000070020000BE000000F00400009E020000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (2680) EDRW v13 Activator v2.1 - De!.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000000000000030000000200000001000000FFFFFFFF | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report