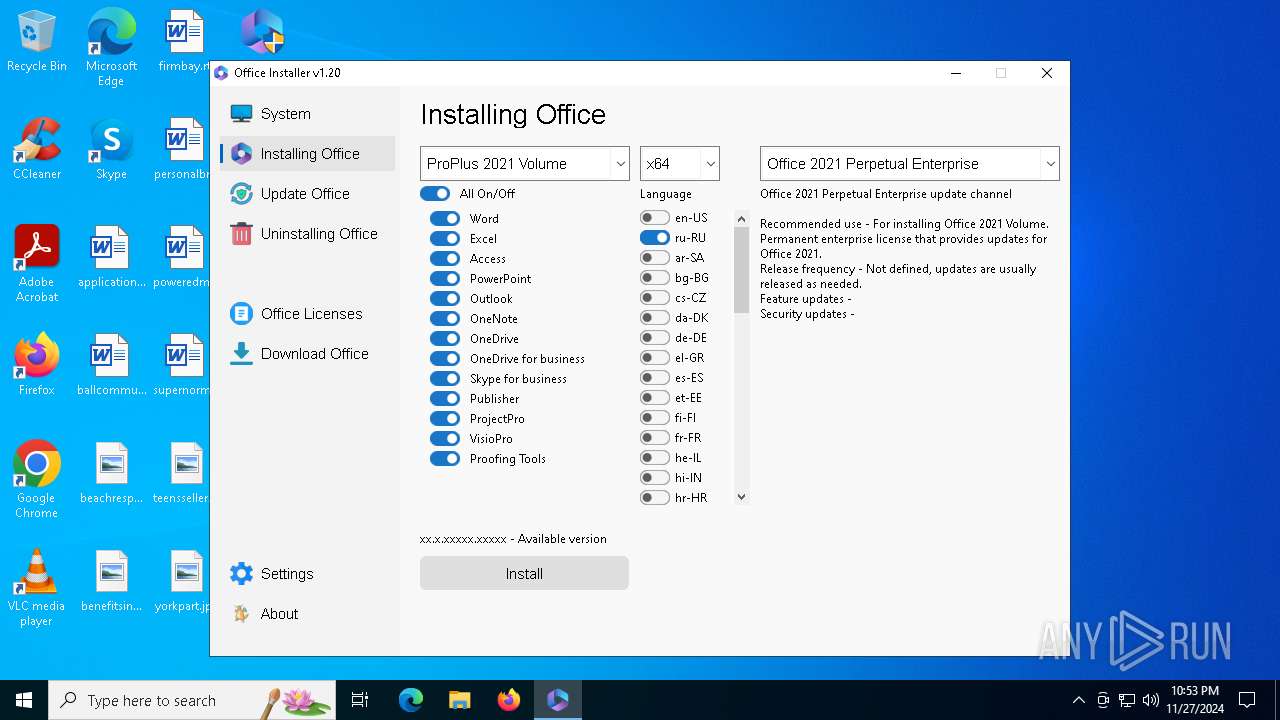
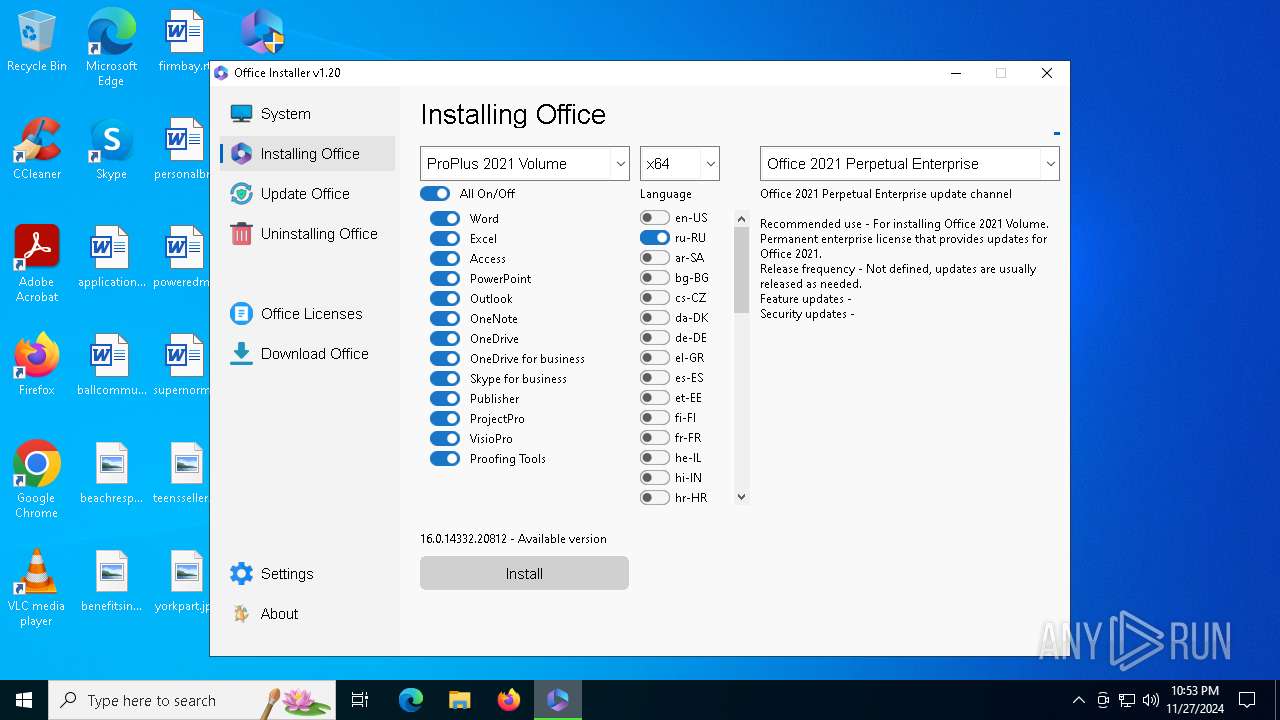
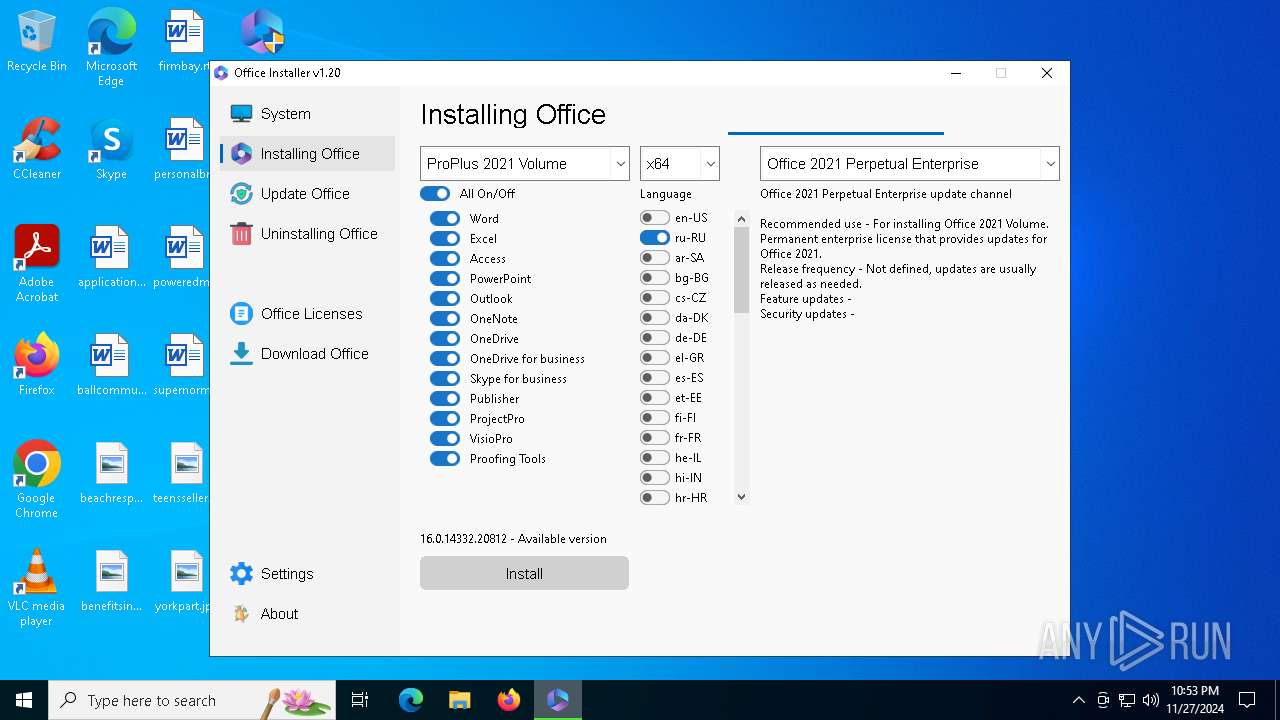
| File name: | 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk |
| Full analysis: | https://app.any.run/tasks/a12c0952-eb96-43ff-b4e1-523d3e8ddbdd |
| Verdict: | Malicious activity |
| Analysis date: | November 27, 2024, 22:52:44 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 9 sections |
| MD5: | 9D2CE8D5BFC7E6A1E7E4EC73ABA8CD5D |
| SHA1: | 7C97168F0A3E8F929A4B4E7C86470D8E33C4BEA2 |
| SHA256: | 10AA90EC6547F6BA676A962CC9C09408D31AFFF2C226F76A854A80980D8975F4 |
| SSDEEP: | 98304:xw15XVl7NvUMLlX0kHjVd6T+7RbrTYaE6p7AbP3DddvSYtlD6S80yjBJPYAOkn2r:G3ZKeZPfBIz |
MALICIOUS
XORed URL has been found (YARA)
- OfficeClickToRun.exe (PID: 6520)
SUSPICIOUS
Executes script without checking the security policy
- powershell.exe (PID: 6956)
Uses REG/REGEDIT.EXE to modify registry
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Probably download files using WebClient
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Starts POWERSHELL.EXE for commands execution
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
The process bypasses the loading of PowerShell profile settings
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Starts SC.EXE for service management
- cmd.exe (PID: 6236)
Starts CMD.EXE for commands execution
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Uses TASKKILL.EXE to kill process
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Unpacks CAB file
- expand.exe (PID: 3732)
- expand.exe (PID: 6412)
Executable content was dropped or overwritten
- expand.exe (PID: 3732)
The process drops C-runtime libraries
- expand.exe (PID: 3732)
Process drops legitimate windows executable
- expand.exe (PID: 3732)
INFO
Reads Environment values
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Checks supported languages
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Reads product name
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Reads the computer name
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Disables trace logs
- powershell.exe (PID: 6956)
Checks proxy server information
- powershell.exe (PID: 6956)
UPX packer has been detected
- 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe (PID: 6760)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 6852)
Manual execution by a user
- OfficeC2RClient.exe (PID: 4400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:11:26 00:44:14+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 1529856 |
| InitializedDataSize: | 9049600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x17543c |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.0.0 |
| ProductVersionNumber: | 1.2.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
Total processes
147
Monitored processes
27
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2736 | "taskkill.exe" /t /f /IM IntegratedOffice.exe | C:\Windows\System32\taskkill.exe | — | 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3436 | "taskkill.exe" /t /f /IM OfficeC2RClient.exe | C:\Windows\System32\taskkill.exe | — | 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | "expand" i640.cab -F:* "C:\Program Files\Common Files\Microsoft Shared\ClickToRun" | C:\Windows\System32\expand.exe | 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20812/i640.cab', 'C:\Users\admin\AppData\Local\Temp\i640.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe" /progressandlaunch AppTargets="root\office16\excel.exe|root\office16\lync.exe|root\office16\msaccess.exe|root\office16\mspub.exe|root\office16\onenote.exe|root\office16\outlook.exe|root\office16\powerpnt.exe|root\office16\visio.exe|root\office16\winproj.exe|root\office16\winword.exe" ManualUpgrade=False ScenarioToTrack="Scenario:{477E0208-58BD-4F33-978A-09BCC9AA9EB1}@INSTALL" | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeC2RClient.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Click-to-Run Client Version: 16.0.14332.20810 Modules
| |||||||||||||||
| 4536 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20812/i641049.cab', 'C:\Users\admin\AppData\Local\Temp\i641049.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | expand.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
51 853
Read events
51 575
Write events
169
Delete events
109
Modification events
| (PID) Process: | (6792) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
| (PID) Process: | (6520) OfficeClickToRun.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ru-ru |
Value: 2 | |||
Executable files
223
Suspicious files
100
Text files
81
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4076 | powershell.exe | C:\Users\admin\AppData\Local\Temp\i640.cab | — | |
MD5:— | SHA256:— | |||
| 4076 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_c0p4dlfn.hu0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_didhme4d.es2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6956 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:5168B946A6836D5977169108D1A76A2E | SHA256:20151BA03C0CB3693AC45F0441292DCF338F9C3F37FB70D163AAEC10333889BE | |||
| 4076 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cut3ytj5.3jy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6760 | 2024-11-27_9d2ce8d5bfc7e6a1e7e4ec73aba8cd5d_cobalt-strike_ryuk.exe | C:\Users\admin\Desktop\Office Installer.ini | text | |
MD5:2A8204CFB0C0B6B7D73880F70FF4DCE7 | SHA256:9A3CCCA43D3BFE395820E58E478A1CFC1A5D9CF606B7F63000E03C8EF63C81C9 | |||
| 6956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_scojvoey.3o4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3732 | expand.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-crt-heap-l1-1-0.dll | executable | |
MD5:5D409D47F9AEBD6015F7C71D526028C3 | SHA256:7050043B0362C928AA63DD7800E5B123C775425EBA21A5C57CBC052EBC1B0BA2 | |||
| 3732 | expand.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-synch-l1-2-0.dll | executable | |
MD5:B9BC664A451424342A73A8B12918F88D | SHA256:0C5C4DFEA72595FB7AE410F8FA8DA983B53A83CE81AEA144FA20CAB613E641B7 | |||
| 3732 | expand.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-crt-convert-l1-1-0.dll | executable | |
MD5:AFC20D2EF1F6042F34006D01BFE82777 | SHA256:CD5256B2FB46DEAA440950E4A68466B2B0FF61F28888383094182561738D10A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
65
TCP/UDP connections
55
DNS requests
49
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5892 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5892 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4076 | powershell.exe | GET | 200 | 2.19.198.59:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20812/i640.cab | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.151.58.88:443 | https://geo.prod.do.dsp.mp.microsoft.com/geo?doClientVersion=10.0.19041.3996&profile=3145984&callId=443433242 | unknown | — | — | unknown |
4536 | powershell.exe | GET | 200 | 2.19.198.59:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20812/i641049.cab | unknown | — | — | whitelisted |
6884 | svchost.exe | GET | 206 | 23.32.238.155:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20812/s640.cab | unknown | — | — | whitelisted |
6884 | svchost.exe | GET | 206 | 23.32.238.155:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20812/s640.cab | unknown | — | — | whitelisted |
6884 | svchost.exe | GET | 206 | 2.19.198.59:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20812/s640.cab | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5892 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5892 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5892 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6956 | powershell.exe | 52.109.89.117:443 | mrodevicemgr.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
geo.prod.do.dsp.mp.microsoft.com |
| whitelisted |