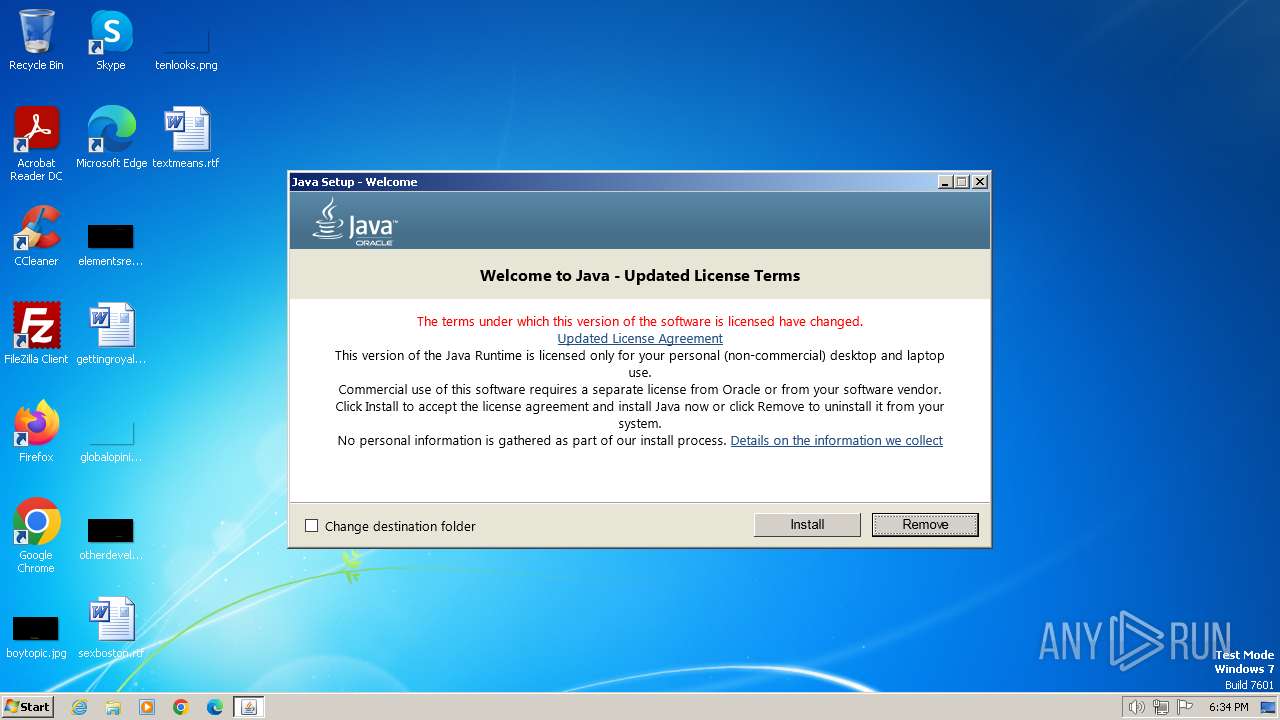
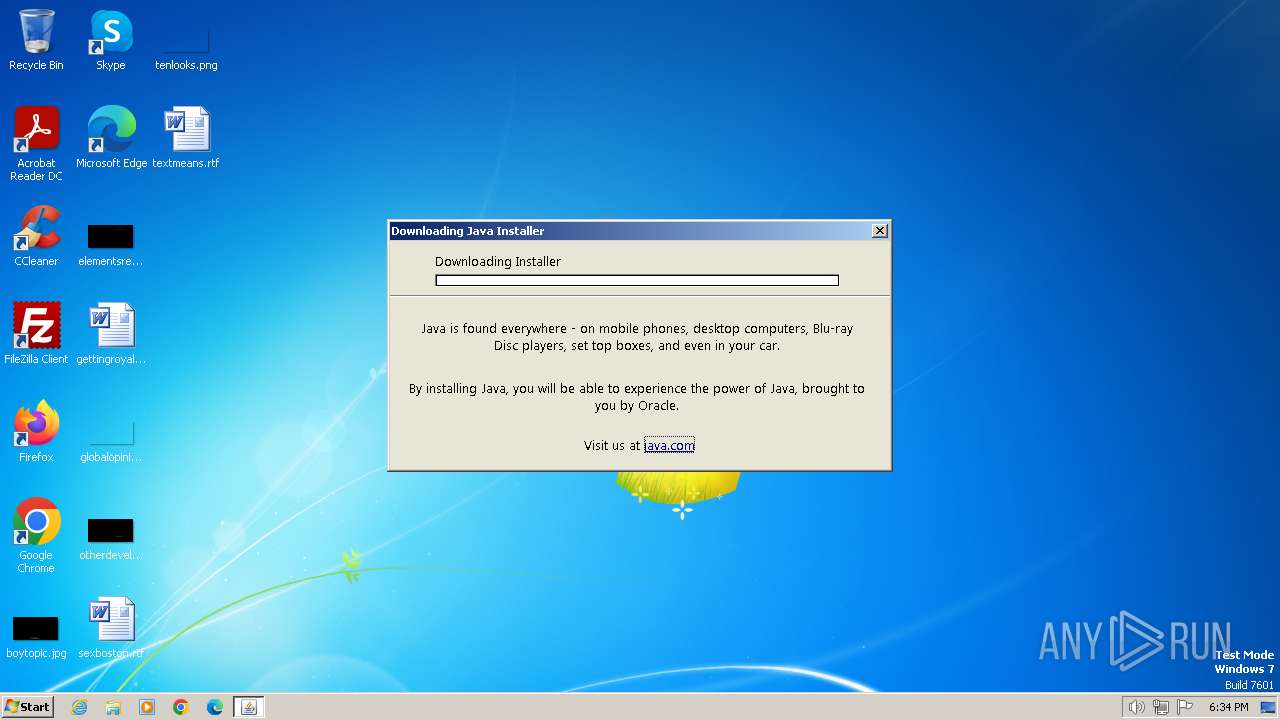
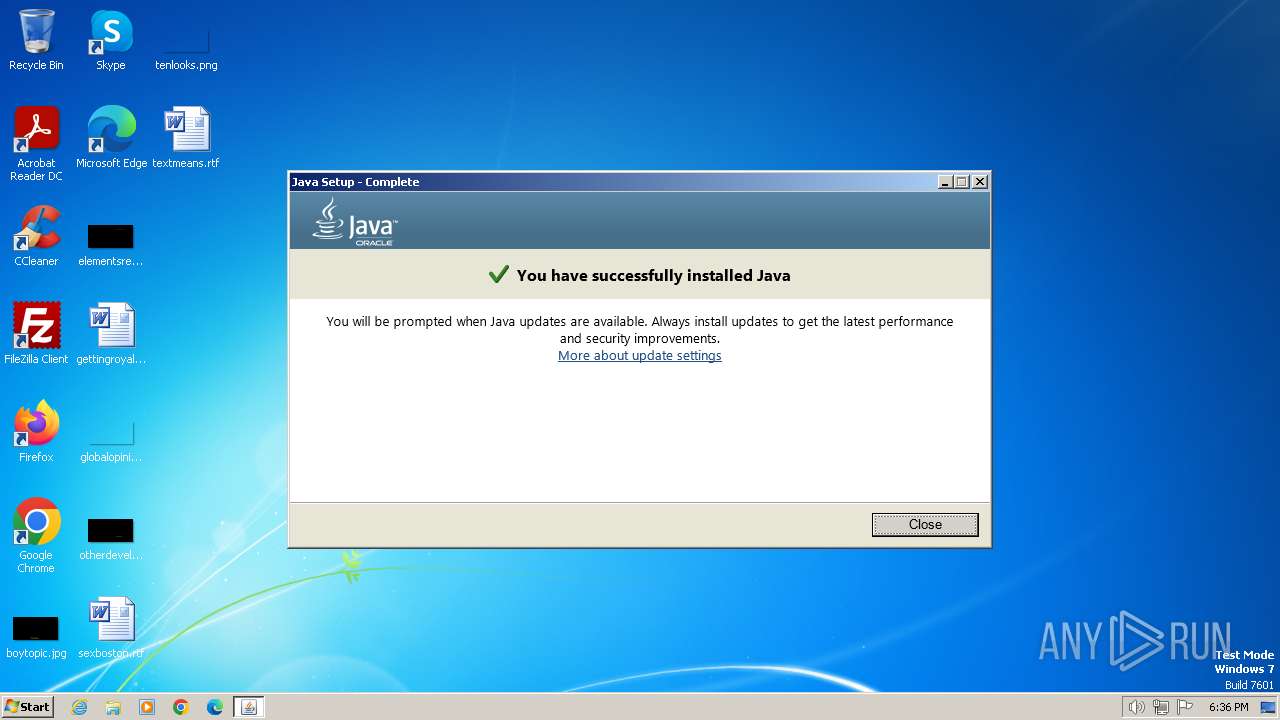
| File name: | jre-8u401-windows-i586-iftw.exe |
| Full analysis: | https://app.any.run/tasks/a990dac4-52dd-4c79-be45-a471a3780450 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2024, 18:34:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2C5491A9A9BA4CF6A24759E4EC371070 |
| SHA1: | 39E1D6BF07474ECD0637D7203796A740C52FA03C |
| SHA256: | 109CBE5B1626FD9577AABC8D2037F32D5DFEE37A4E6288947586250C64DF81EA |
| SSDEEP: | 98304:mfhV9fR8eZt0fsXgdu8UYxd8Dv/hTwMqfZeW3nTZ8aF:h |
MALICIOUS
Drops the executable file immediately after the start
- jre-8u401-windows-i586-iftw.exe (PID: 2848)
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
SUSPICIOUS
Executable content was dropped or overwritten
- jre-8u401-windows-i586-iftw.exe (PID: 2848)
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
- LZMA_EXE (PID: 1656)
Reads security settings of Internet Explorer
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
Reads Microsoft Outlook installation path
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
Reads settings of System Certificates
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
Checks for Java to be installed
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
- ssvagent.exe (PID: 1636)
- jp2launcher.exe (PID: 2584)
- jp2launcher.exe (PID: 2024)
- javaw.exe (PID: 3572)
Reads Internet Explorer settings
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
Reads the Internet Settings
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
Checks Windows Trust Settings
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
Starts application with an unusual extension
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
Creates/Modifies COM task schedule object
- ssvagent.exe (PID: 1636)
INFO
Reads the computer name
- jre-8u401-windows-i586-iftw.exe (PID: 2848)
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
- jp2launcher.exe (PID: 2584)
- javaws.exe (PID: 2640)
- jp2launcher.exe (PID: 2024)
- javaws.exe (PID: 3352)
- javaw.exe (PID: 3572)
- javaw.exe (PID: 3104)
Checks supported languages
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
- jre-8u401-windows-i586-iftw.exe (PID: 2848)
- LZMA_EXE (PID: 1656)
- javaw.exe (PID: 3444)
- jaureg.exe (PID: 2772)
- javaws.exe (PID: 2640)
- ssvagent.exe (PID: 1636)
- LZMA_EXE (PID: 2156)
- jp2launcher.exe (PID: 2584)
- javaws.exe (PID: 3352)
- jp2launcher.exe (PID: 2024)
- javaw.exe (PID: 3572)
- javaw.exe (PID: 3104)
Create files in a temporary directory
- jre-8u401-windows-i586-iftw.exe (PID: 2848)
- javaw.exe (PID: 3444)
- jp2launcher.exe (PID: 2584)
- jp2launcher.exe (PID: 2024)
Reads the machine GUID from the registry
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
- jp2launcher.exe (PID: 2584)
- jp2launcher.exe (PID: 2024)
Checks proxy server information
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
- jp2launcher.exe (PID: 2584)
- jp2launcher.exe (PID: 2024)
Reads the software policy settings
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
Creates files or folders in the user directory
- LZMA_EXE (PID: 2156)
- jre-8u401-windows-i586-iftw.exe (PID: 2752)
- LZMA_EXE (PID: 1656)
Creates files in the program directory
- javaw.exe (PID: 3444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:19 13:18:52+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.31 |
| CodeSize: | 197632 |
| InitializedDataSize: | 2143232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x10ab3 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.0.4010.10 |
| ProductVersionNumber: | 8.0.4010.10 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Oracle Corporation |
| FileDescription: | Java Platform SE binary |
| FileVersion: | 8.0.4010.10 |
| FullVersion: | 1.8.0_401-b10 |
| InternalName: | Setup Launcher |
| LegalCopyright: | Copyright © 2024 |
| OriginalFileName: | online_wrapper-iftw.exe |
| ProductName: | Java Platform SE 8 U401 |
| ProductVersion: | 8.0.4010.10 |
Total processes
67
Monitored processes
15
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1636 | "C:\Program Files\Java\jre-1.8\bin\ssvagent.exe" -doHKCUSSVSetup | C:\Program Files\Java\jre-1.8\bin\ssvagent.exe | — | installer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 11.401.2.10 Modules
| |||||||||||||||
| 1656 | "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\LZMA_EXE" d "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\au.msi" "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\msi.tmp" | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\LZMA_EXE | jre-8u401-windows-i586-iftw.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2024 | "C:\Program Files\Java\jre-1.8\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre-1.8" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlLTEuOFxsaWJcZGVwbG95LmphcgAtRGphdmEuc2VjdXJpdHkucG9saWN5PWZpbGU6QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZS0xLjhcbGliXHNlY3VyaXR5XGphdmF3cy5wb2xpY3kALUR0cnVzdFByb3h5PXRydWUALVh2ZXJpZnk6cmVtb3RlAC1Eam5scHguaG9tZT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlLTEuOFxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUtMS44XGxpYlxqYXZhd3MuamFyO0M6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUtMS44XGxpYlxkZXBsb3kuamFyO0M6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUtMS44XGxpYlxwbHVnaW4uamFyAC1EamF2YS5hd3QuaGVhZGxlc3M9dHJ1ZQAtRGpubHB4Lmp2bT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlLTEuOFxiaW5camF2YXcuZXhl -ma LXdhaXQALWZpeAAtc2hvcnRjdXQALXNpbGVudAAtbm90V2ViSmF2YQ== | C:\Program Files\Java\jre-1.8\bin\jp2launcher.exe | — | javaws.exe | |||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.401.2.10 Modules
| |||||||||||||||
| 2104 | "C:\Windows\system32\msiexec.exe" /x {4A03706F-666A-4037-7777-5F2748764D10} /qn | C:\Windows\System32\msiexec.exe | — | jaureg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2156 | "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\LZMA_EXE" d "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\jre1.8.0_401.msi" "C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\msi.tmp" | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\LZMA_EXE | — | jre-8u401-windows-i586-iftw.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2584 | "C:\Program Files\Java\jre-1.8\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre-1.8" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlLTEuOFxsaWJcZGVwbG95LmphcgAtRGphdmEuc2VjdXJpdHkucG9saWN5PWZpbGU6QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZS0xLjhcbGliXHNlY3VyaXR5XGphdmF3cy5wb2xpY3kALUR0cnVzdFByb3h5PXRydWUALVh2ZXJpZnk6cmVtb3RlAC1Eam5scHguaG9tZT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlLTEuOFxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUtMS44XGxpYlxqYXZhd3MuamFyO0M6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUtMS44XGxpYlxkZXBsb3kuamFyO0M6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUtMS44XGxpYlxwbHVnaW4uamFyAC1EamF2YS5hd3QuaGVhZGxlc3M9dHJ1ZQAtRGpubHB4Lmp2bT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlLTEuOFxiaW5camF2YXcuZXhl -ma LXdhaXQALWZpeAAtcGVybWlzc2lvbnMALXNpbGVudAAtbm90V2ViSmF2YQ== | C:\Program Files\Java\jre-1.8\bin\jp2launcher.exe | — | javaws.exe | |||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.401.2.10 Modules
| |||||||||||||||
| 2640 | "C:\Program Files\Java\jre-1.8\bin\javaws.exe" -wait -fix -permissions -silent | C:\Program Files\Java\jre-1.8\bin\javaws.exe | installer.exe | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.401.2.10 Modules
| |||||||||||||||
| 2752 | "C:\Users\admin\AppData\Local\Temp\jds1570078.tmp\jre-8u401-windows-i586-iftw.exe" | C:\Users\admin\AppData\Local\Temp\jds1570078.tmp\jre-8u401-windows-i586-iftw.exe | jre-8u401-windows-i586-iftw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.4010.10 Modules
| |||||||||||||||
| 2772 | "C:\Program Files\Common Files\Java\Java Update\jaureg.exe" -u auto-update | C:\Program Files\Common Files\Java\Java Update\jaureg.exe | MSIEC2F.tmp | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java Update Registration Exit code: 0 Version: 2.8.271.9 Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\AppData\Local\Temp\jre-8u401-windows-i586-iftw.exe" | C:\Users\admin\AppData\Local\Temp\jre-8u401-windows-i586-iftw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.4010.10 Modules
| |||||||||||||||
Total events
15 528
Read events
11 569
Write events
3 918
Delete events
41
Modification events
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft |
| Operation: | delete value | Name: | InstallStatus |
Value: | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2752) jre-8u401-windows-i586-iftw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
5
Suspicious files
4
Text files
3
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2752 | jre-8u401-windows-i586-iftw.exe | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\jds1571593.tmp | — | |
MD5:— | SHA256:— | |||
| 2752 | jre-8u401-windows-i586-iftw.exe | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\jre1.8.0_401.msi | — | |
MD5:— | SHA256:— | |||
| 2156 | LZMA_EXE | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\msi.tmp | — | |
MD5:— | SHA256:— | |||
| 3444 | javaw.exe | C:\Program Files\Java\jre-1.8\bin\client\classes.jsa | — | |
MD5:— | SHA256:— | |||
| 2752 | jre-8u401-windows-i586-iftw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\KBSW7N4Y.txt | text | |
MD5:873DBD12C29EC3B406399FCC6BB21A7E | SHA256:4C7D04885C2E147BFACB041661E1AC57E7E64DA5B14390C2402BA8CCCBA97553 | |||
| 2752 | jre-8u401-windows-i586-iftw.exe | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_401\LZMA_EXE | executable | |
MD5:3842C46F2FBC7522EF625F1833530804 | SHA256:17CB7CF185355B60D6ED5138A86C78B9FD5A7D6D3C0DD90F2224246E823166E7 | |||
| 2752 | jre-8u401-windows-i586-iftw.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:A6254F8FD8F62A453F555DB5B4A99AE2 | SHA256:5A9E7E95051DF7C5EF8C7B964C232EB4479B57E09A9FFC961F9E49ACE47B7719 | |||
| 2752 | jre-8u401-windows-i586-iftw.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E573CDF4C6D731D56A665145182FD759_A17FACB72EB3AA73551FC148040A47E4 | binary | |
MD5:ACB21A9B98B7DE8A1B162E5E5F34E254 | SHA256:29C09C02BD21E7B4B87212F18285B9AA18CFE792CA8A1C5693C69126DB532196 | |||
| 2752 | jre-8u401-windows-i586-iftw.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E573CDF4C6D731D56A665145182FD759_A17FACB72EB3AA73551FC148040A47E4 | binary | |
MD5:EF1BCC131C23F7697C740B9A5935EC62 | SHA256:4B7DB301B9D4E28C8B6DA3D69B8C374F3D920DAD8BF9F22DCC38A408CD0C7583 | |||
| 2848 | jre-8u401-windows-i586-iftw.exe | C:\Users\admin\AppData\Local\Temp\jds1570078.tmp\jds1570078.tmp | executable | |
MD5:F43378882DB67BB48232F77CDDF2E139 | SHA256:1F0E771C96DB5005DB48EF8D65672F9F1F9E3D8E1B9F1F20D930224E76CF4B56 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2752 | jre-8u401-windows-i586-iftw.exe | GET | 304 | 87.248.202.1:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3e1221cb6058ac68 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c503292d7802e201 | unknown | compressed | 67.5 Kb | unknown |
2752 | jre-8u401-windows-i586-iftw.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
2752 | jre-8u401-windows-i586-iftw.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEA2ypEAZl9ZmFI%2BR0FmZENI%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2752 | jre-8u401-windows-i586-iftw.exe | 23.199.222.107:443 | javadl-esd-secure.oracle.com | AKAMAI-AS | US | unknown |
2752 | jre-8u401-windows-i586-iftw.exe | 87.248.202.1:80 | ctldl.windowsupdate.com | LLNW | NL | unknown |
2752 | jre-8u401-windows-i586-iftw.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2752 | jre-8u401-windows-i586-iftw.exe | 92.123.148.220:443 | javadl.oracle.com | AKAMAI-AS | DE | unknown |
2752 | jre-8u401-windows-i586-iftw.exe | 23.212.88.77:443 | sdlc-esd.oracle.com | AKAMAI-AS | MX | unknown |
1080 | svchost.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2752 | jre-8u401-windows-i586-iftw.exe | 92.122.215.72:443 | www.java.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
javadl-esd-secure.oracle.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
javadl.oracle.com |
| whitelisted |
sdlc-esd.oracle.com |
| whitelisted |
rps-svcs.oracle.com |
| unknown |
www.java.com |
| whitelisted |
sjremetrics.java.com |
| whitelisted |