| URL: | http://note.youdao.com/yws/api/personal/file/WEBd69657b362034dc5dbc8ec373a041359?method=download&inline=true&shareKey=d3c788ae34c5aac180a1bcbf1061e42e |
| Full analysis: | https://app.any.run/tasks/e246fef0-6484-41a4-af6e-ba21cc86e052 |
| Verdict: | Malicious activity |
| Analysis date: | December 08, 2023, 05:17:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FF879381B86B49111BA4FBFDC091A718 |
| SHA1: | 3E68546F14F914CE7E8F9ADCD767523D35F4FC54 |
| SHA256: | 108E5E75629A4150CBF0ED876DB9D3C5A5A3C458B3C495C7E9059D441C33854E |
| SSDEEP: | 3:N1KQbcdbDM7Hp2BmF/RUtKOKEtSAXVWsYrAojEZHDMYP:CQYdMjT/y4lCSAlWrA5dMU |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2220)
- wmpnscfg.exe (PID: 3636)
Checks supported languages
- wmpnscfg.exe (PID: 2220)
- wmpnscfg.exe (PID: 3636)
Application launched itself
- iexplore.exe (PID: 1864)
Reads the computer name
- wmpnscfg.exe (PID: 2220)
- wmpnscfg.exe (PID: 3636)
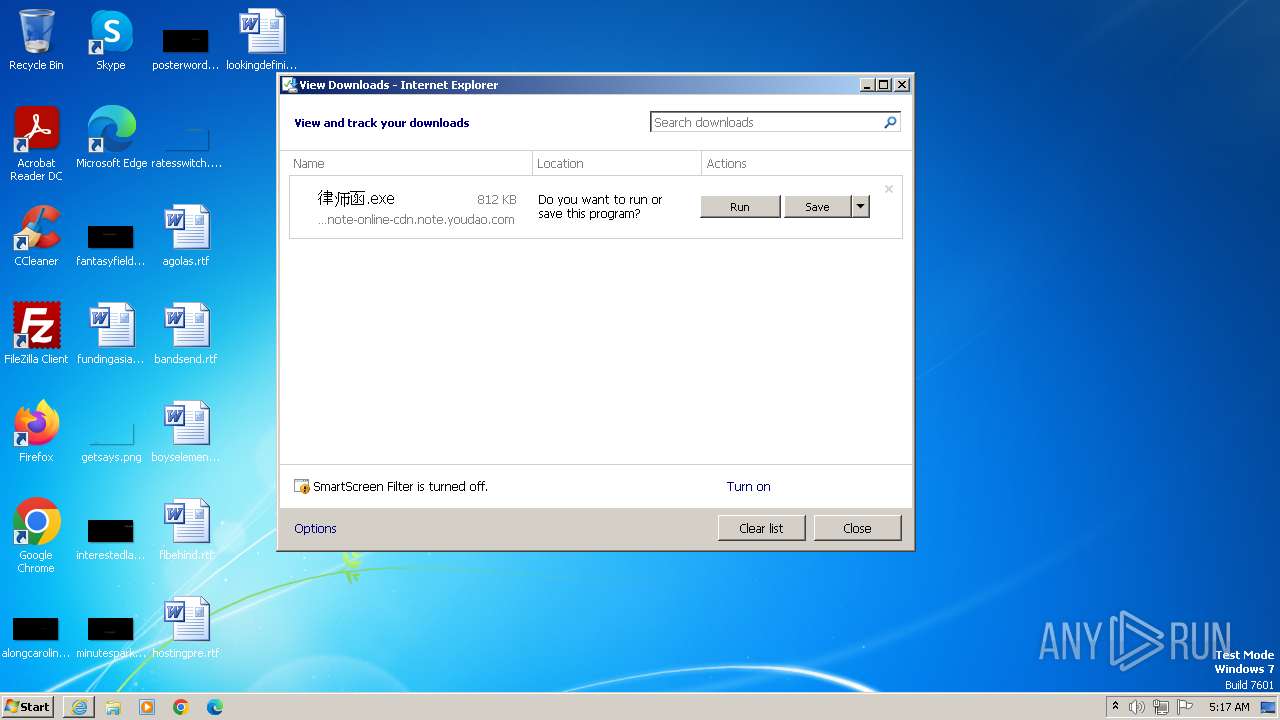
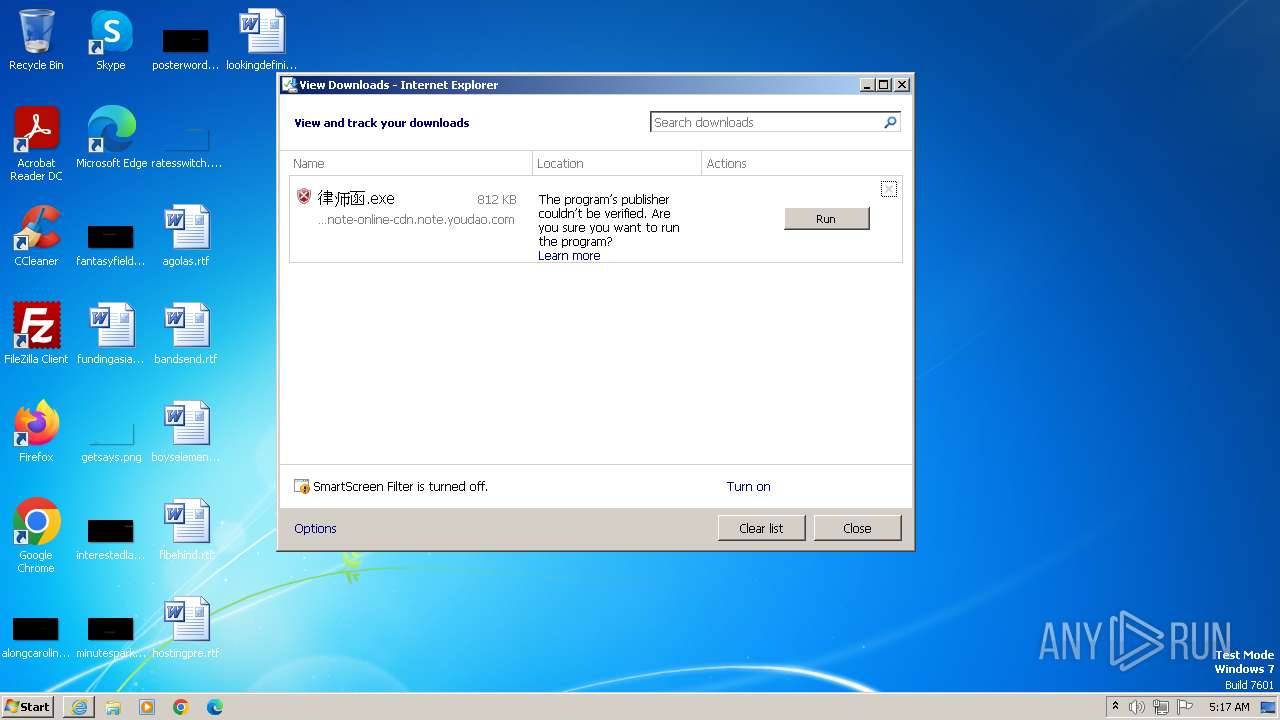
Drops the executable file immediately after the start
- iexplore.exe (PID: 3028)
- iexplore.exe (PID: 1864)
The process uses the downloaded file
- iexplore.exe (PID: 1864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1864 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://note.youdao.com/yws/api/personal/file/WEBd69657b362034dc5dbc8ec373a041359?method=download&inline=true&shareKey=d3c788ae34c5aac180a1bcbf1061e42e" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3028 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1864 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3636 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
14 416
Read events
14 361
Write events
54
Delete events
1
Modification events
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005A010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
3
Suspicious files
13
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\律师函.exe.o9a0h0s.partial | executable | |
MD5:18B3D96986C113C3E428B15AB40D26A0 | SHA256:E786B32921CA768DB5B77CB647137100636ED8C5C10BF8FC5A9CD26BAF084889 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:6E71B513687E0D4CC4E11AEAD2D6EFCD | SHA256:6A9C083FC640CA4216C182939A10A72A9EC02774295B0A3818672C5A48BCC022 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7229E30BCFD0992128433D951137A421_76EBFC12D6FD7EE9DD82775C12CF3BD5 | binary | |
MD5:03C475ACD59229559E494A66BDA1948E | SHA256:0D867DA4F17E8671E87C0D42F819E37184AD3A539768BAC54E71CCC817D724DE | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3FE2BD01AB6BC312BF0DADE7F797388F_F7F9B7BDCC367A8E3539D28F7D4D4BA2 | der | |
MD5:2E7F56E78DD3CD23C426CC151E7FDB42 | SHA256:477B2B4929FB55ECBA4A52A31536AA62817A1FDEC32AC8FB65EEE87C75DA6485 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\律师函[1].exe | executable | |
MD5:19F373847BD499E112FB3A413328A528 | SHA256:E598DA1051A9A744A1E2F40936D36DAB3904BA485BBF469256444B3AF6AE602F | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3FE2BD01AB6BC312BF0DADE7F797388F_F7F9B7BDCC367A8E3539D28F7D4D4BA2 | binary | |
MD5:B03DDA4C198B85A6D6E3A7E3D46D5A93 | SHA256:198691B762DC6758390B9CF4CF018E0DE17C6A50D56002EC3D03950D4274EAA7 | |||
| 1864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:5CE146F479FC95E4E6C230C5B90038D7 | SHA256:888A49DBF470546176CCBE0A940BB0EF7D34997581E21DBD9C719D09293700DE | |||
| 1864 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA25FC158A9D4F397.TMP | binary | |
MD5:CCDBCD5664AC0AE9CDA9ADB3F0810D42 | SHA256:E364C1AEC369F218D38308DEC185A9B50AB8EAF560C61F243BCB091C379391AE | |||
| 1864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
16
DNS requests
14
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3028 | iexplore.exe | GET | 302 | 163.181.92.238:80 | http://note.youdao.com/yws/api/personal/file/WEBd69657b362034dc5dbc8ec373a041359?method=download&inline=true&shareKey=d3c788ae34c5aac180a1bcbf1061e42e | unknown | — | — | unknown |
3028 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6a3142f400022d08 | unknown | compressed | 4.66 Kb | unknown |
3028 | iexplore.exe | GET | 200 | 47.246.3.20:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAsTYrbuap0%2Blokw8W4gfTk%3D | unknown | binary | 471 b | unknown |
3028 | iexplore.exe | GET | 200 | 47.246.3.20:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTRXf%2BqAIajMnZeiQcx27p1CzET2wQUJG%2BRP4mHhw4ywkAY38VM60%2FISTICEARpHnniO1nFqCOqTkLgf1Q%3D | unknown | binary | 471 b | unknown |
1864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?abdc0569852e700a | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3028 | iexplore.exe | 163.181.92.238:80 | note.youdao.com | Zhejiang Taobao Network Co.,Ltd | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3028 | iexplore.exe | 180.163.207.102:443 | bucket-ynote-online-cdn.note.youdao.com | China Telecom Group | CN | unknown |
3028 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3028 | iexplore.exe | 47.246.3.20:80 | ocsp.digicert.cn | Zhejiang Taobao Network Co.,Ltd | RU | unknown |
3028 | iexplore.exe | 114.80.179.172:443 | bucket-ynote-online-cdn.note.youdao.com | China Telecom Group | CN | unknown |
1864 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
note.youdao.com |
| malicious |
bucket-ynote-online-cdn.note.youdao.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.cn |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET POLICY Pastebin-style service note .youdao .com in DNS query |
1080 | svchost.exe | Misc activity | ET POLICY Pastebin-style service note .youdao .com in DNS query |
1080 | svchost.exe | Misc activity | ET POLICY Pastebin-style service note .youdao .com in DNS query |
3028 | iexplore.exe | Misc activity | ET POLICY Pastebin-style service (note .youdao .com) in TLS SNI |
3028 | iexplore.exe | Misc activity | ET POLICY Pastebin-style service (note .youdao .com) in TLS SNI |