| File name: | procexp.exe |
| Full analysis: | https://app.any.run/tasks/997b9ab6-adf2-47d7-9a84-292bc19ad329 |
| Verdict: | Malicious activity |
| Analysis date: | September 14, 2024, 13:00:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 94C60E6704B5DD11A139F2FFEBDE9135 |
| SHA1: | CD89F1CF9428A3EAB554A3EB9FF6CA869E5BC368 |
| SHA256: | 106BF123359D03963B1DF1011FB8560AAF1C5E811DE775DCE1D8A53758A69102 |
| SSDEEP: | 98304:kQ/qdW5SWBJdgKwBFip2LytbxPiei81/mxKkAcEgHboS3FdF:Keiqo |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- procexp.exe (PID: 2876)
- procexp64.exe (PID: 5388)
The process checks if it is being run in the virtual environment
- procexp.exe (PID: 2876)
- procexp64.exe (PID: 5388)
Drops a system driver (possible attempt to evade defenses)
- procexp64.exe (PID: 5388)
Reads security settings of Internet Explorer
- procexp64.exe (PID: 5388)
Detected use of alternative data streams (AltDS)
- procexp64.exe (PID: 5388)
Checks Windows Trust Settings
- procexp64.exe (PID: 5388)
INFO
Reads the computer name
- procexp.exe (PID: 2876)
- procexp64.exe (PID: 5388)
Create files in a temporary directory
- procexp.exe (PID: 2876)
- procexp64.exe (PID: 5388)
Checks supported languages
- procexp.exe (PID: 2876)
- procexp64.exe (PID: 5388)
Reads Environment values
- procexp64.exe (PID: 5388)
Reads product name
- procexp64.exe (PID: 5388)
Reads Microsoft Office registry keys
- procexp64.exe (PID: 5388)
Reads the machine GUID from the registry
- procexp64.exe (PID: 5388)
Creates files or folders in the user directory
- procexp64.exe (PID: 5388)
Checks proxy server information
- procexp64.exe (PID: 5388)
Reads the software policy settings
- procexp64.exe (PID: 5388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:05:28 15:50:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.39 |
| CodeSize: | 1014272 |
| InitializedDataSize: | 3712512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc43ce |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 17.6.0.0 |
| ProductVersionNumber: | 17.6.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Sysinternals Process Explorer |
| FileVersion: | 17.06 |
| InternalName: | Process Explorer |
| LegalCopyright: | Copyright © 1998-2024 Mark Russinovich |
| LegalTrademarks: | Copyright © 1998-2024 Mark Russinovich |
| OriginalFileName: | Procexp.exe |
| ProductName: | Process Explorer |
| ProductVersion: | 17.06 |
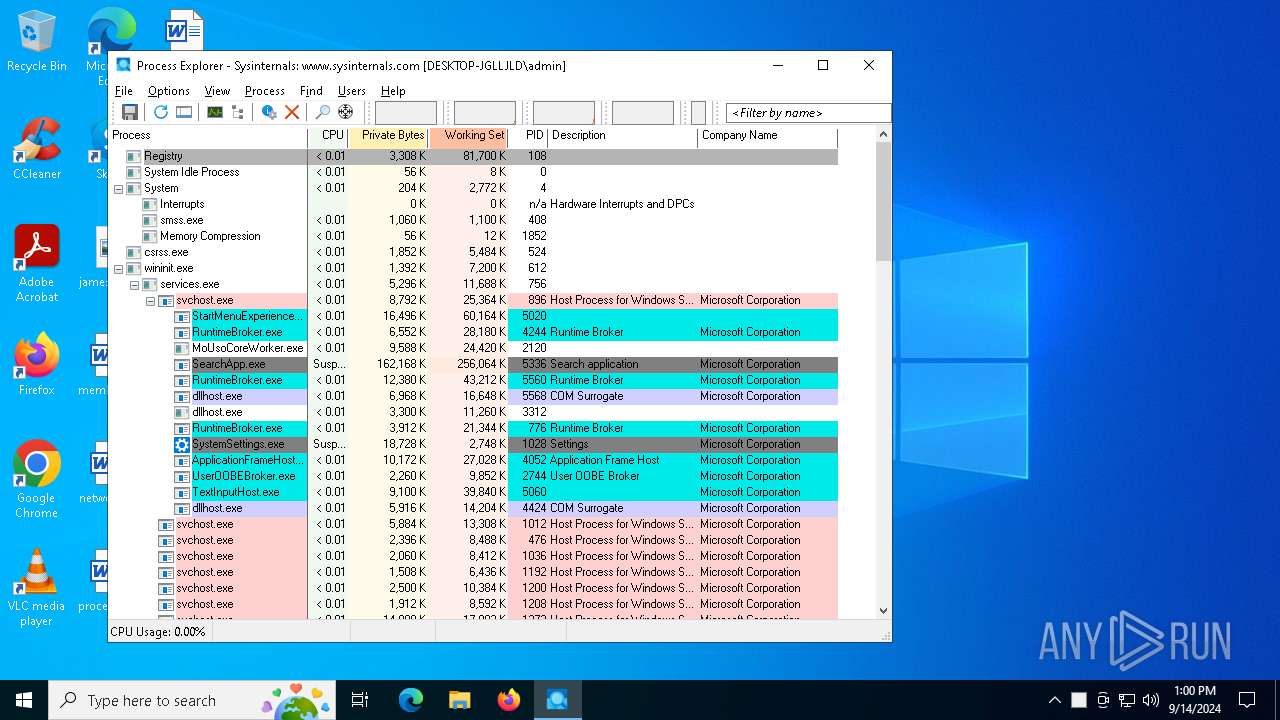
Total processes
122
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2876 | "C:\Users\admin\Desktop\procexp.exe" | C:\Users\admin\Desktop\procexp.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals Process Explorer Version: 17.06 Modules
| |||||||||||||||
| 5388 | "C:\Users\admin\Desktop\procexp.exe" | C:\Users\admin\AppData\Local\Temp\procexp64.exe | procexp.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals Process Explorer Version: 17.06 Modules
| |||||||||||||||
Total events
45 397
Read events
45 394
Write events
3
Delete events
0
Modification events
| (PID) Process: | (2876) procexp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Explorer |
| Operation: | write | Name: | OriginalPath |
Value: C:\Users\admin\Desktop\procexp.exe | |||
| (PID) Process: | (2876) procexp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Explorer |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\AppData\Local\Temp\procexp64.exe | |||
| (PID) Process: | (5388) procexp64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Explorer |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
Executable files
2
Suspicious files
56
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:D86772D4AFC9C066A8319470A613A8E4 | SHA256:12430C159B4EB649E7A72C23B7A7300455096A29B037ECB9B5C191AB86990D96 | |||
| 2876 | procexp.exe | C:\Users\admin\AppData\Local\Temp\procexp64.exe | executable | |
MD5:DFEEA73E421C76DEB18D5CA0800DCCF2 | SHA256:8158DC0569972C10056F507CF9E72F4946600CE163C4C659A610480585CD4935 | |||
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\45AE547469FB7137480E06153457A2DD | binary | |
MD5:1087469BC9A5DAA468679C271B148D37 | SHA256:67B78F9CDD8B79FDA53EF1ED9DE0AF79FDE2BA7357F1C3FD1D73B526B5C1887D | |||
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0B8A20E1F3F4D73D52A19929F922C892 | binary | |
MD5:0840F3C261E695105CD15C84EA85BEED | SHA256:F60632399A87485A7417DDF8B407DA66794C37347B3AA9E995EC389ECD091947 | |||
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:C7D1234376F3389D6C220F0DCF24341B | SHA256:F67F7E62B47D1C4D9059F9F01FF40D52044EE81F594C5B8C8925C254381061E5 | |||
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:C835DB964BDE343C7B2750FDC41E06A6 | SHA256:4A97DE4E93906D5C25B861F7A8627717132017C4B28B8B9E490D77611A7D8B46 | |||
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:36D521B125123B5A13BB17A0C38149B0 | SHA256:B5067CEB18B6BF0F442433A061597E92917A5345CD4A536FB6B1EBA67A038643 | |||
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:F87FBB6A7D9A5E7B0DAD6331F8F08A6D | SHA256:A1AF469546E87A867D5DD08DEBBBCD8C6310BA86FC2DB3DAF58406C6F32A6C5A | |||
| 5388 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_EB45B4DDD2CA201E87E40B2FB5245AEF | binary | |
MD5:3238DF72FE392B9EE0274A2B4C059E2E | SHA256:C3CFF12896B4197F648440CA0B35C90B1D6DD6B08E8309345464E69E722DE3EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
31
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6232 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2016 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5388 | procexp64.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5388 | procexp64.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
5388 | procexp64.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
5388 | procexp64.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
5388 | procexp64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
5388 | procexp64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
5388 | procexp64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEARSlvj82CmnXclClPWkFaQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6232 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2016 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6232 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2016 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6232 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.verisign.com |
| whitelisted |
ocsp.verisign.com |
| whitelisted |
csc3-2004-crl.verisign.com |
| whitelisted |
ocsp.trust-provider.com |
| whitelisted |
crl.trust-provider.com |
| whitelisted |