| download: | /CryptoNickSoft/7z-SFX-Constructor/raw/master/upd/7zSFX%20Constructor.7z |
| Full analysis: | https://app.any.run/tasks/3a95bdeb-c125-4a51-b461-aa70f5114d1f |
| Verdict: | Malicious activity |
| Analysis date: | April 13, 2025, 15:10:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
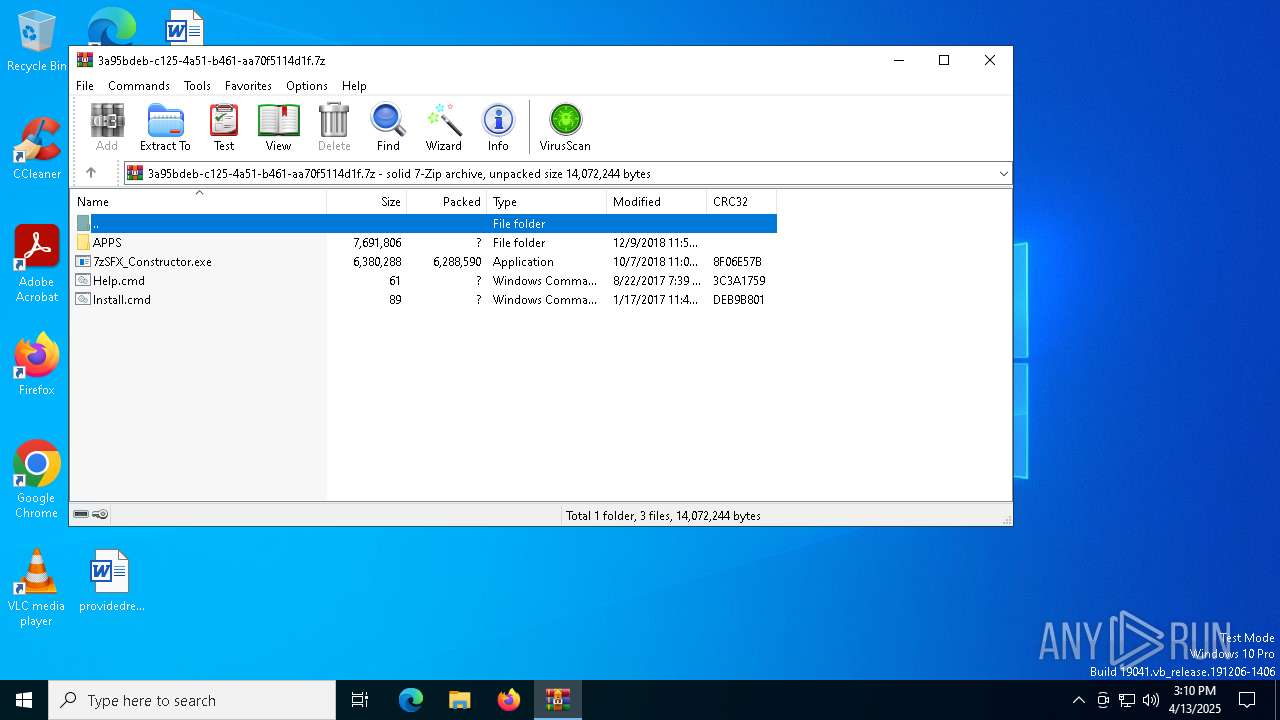
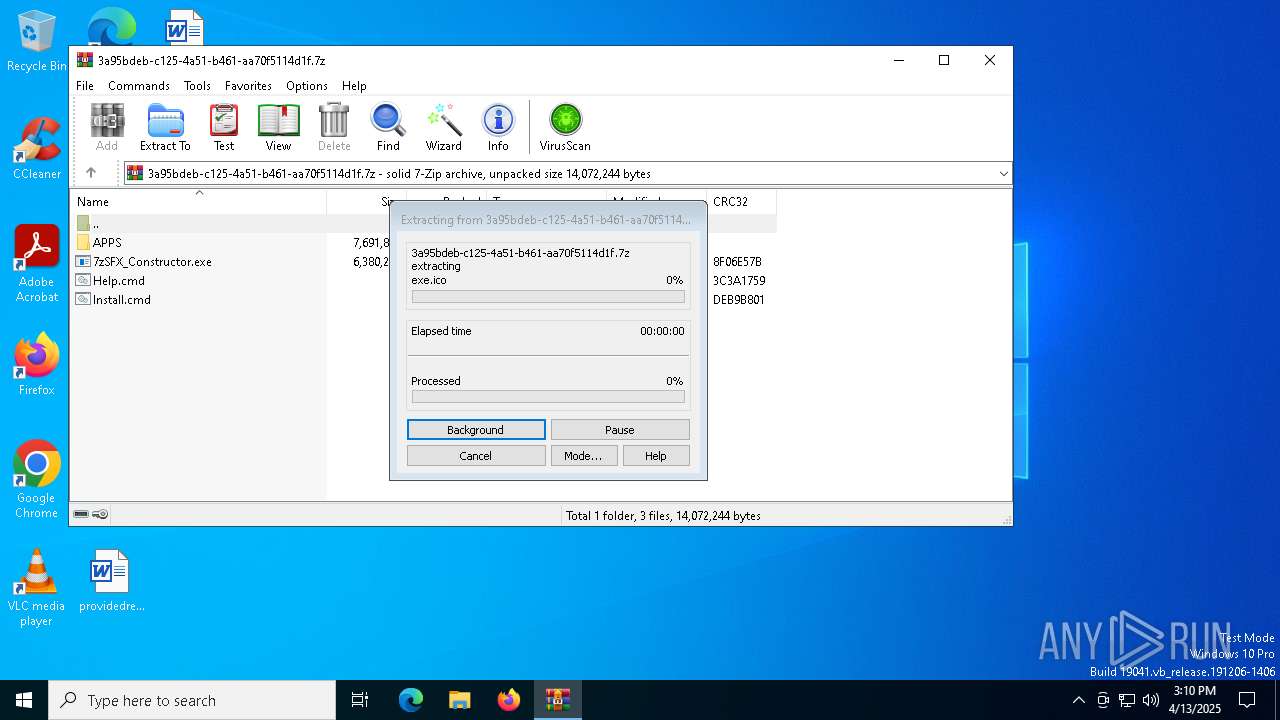
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | D1D742B063729E155DCBC15822178647 |
| SHA1: | 60140553FBF80854E0807569958C742E3F8B6607 |
| SHA256: | 1060C7742E6883F4845D0B81D51A6957523C1C91B579A6BD7232F146982F0D5B |
| SSDEEP: | 98304:/o91ukS5l6A0w4wiSjhKxIGeju+J6hvVRFfiDANk7j6HHVPr6CEqVyszmM7lM7O+:EEQAGekj1gVlcri4iiA |
MALICIOUS
Executing a file with an untrusted certificate
- 7zSFX_Constructor.exe (PID: 896)
- 7zSFX_Constructor.exe (PID: 5228)
- 7zSFX_Constructor.exe (PID: 5968)
Generic archive extractor
- WinRAR.exe (PID: 1452)
SUSPICIOUS
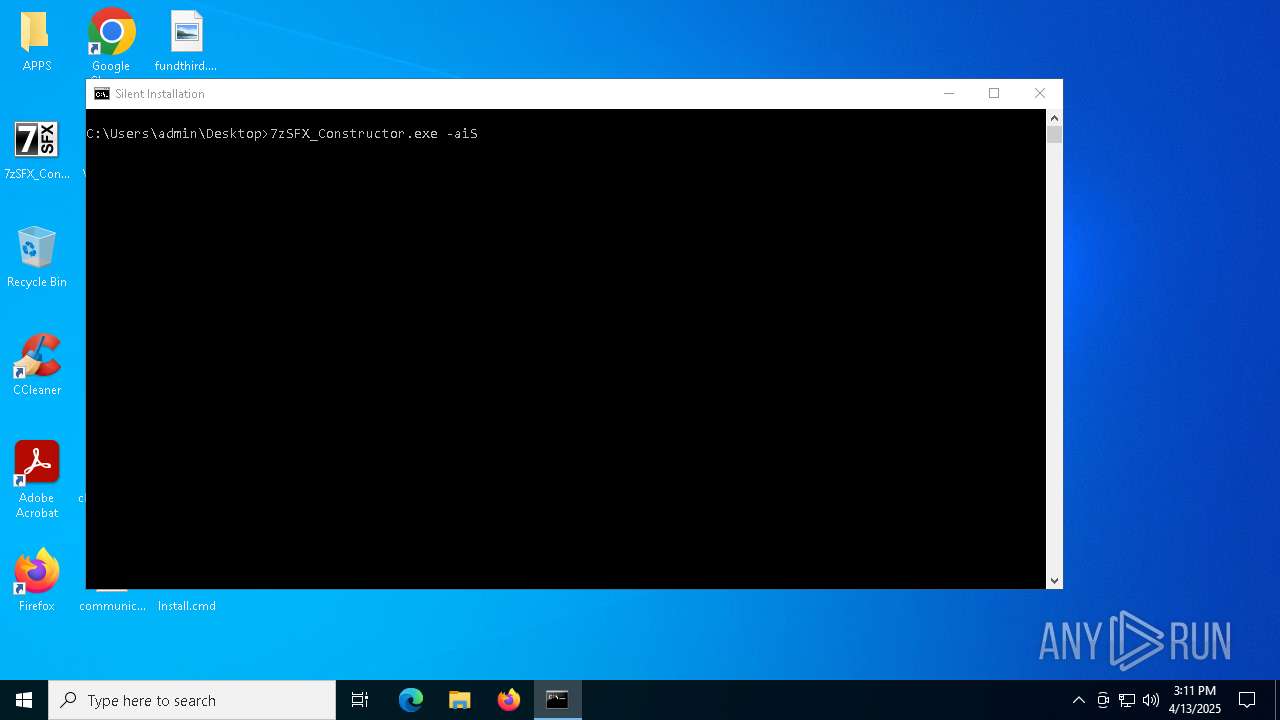
Starts CMD.EXE for commands execution
- 7zSFX_Constructor.exe (PID: 896)
Drops 7-zip archiver for unpacking
- xcopy.exe (PID: 6344)
- 7zSFX_Constructor.exe (PID: 896)
- 7zSFX_Constructor.exe (PID: 5968)
Executable content was dropped or overwritten
- xcopy.exe (PID: 6344)
- 7zSFX_Constructor.exe (PID: 896)
- 7zSFX_Constructor.exe (PID: 5968)
- ap14.dat (PID: 6700)
Reads security settings of Internet Explorer
- 7zSFX_Constructor.exe (PID: 896)
- 7zSFX_Constructor.exe (PID: 5968)
Starts the AutoIt3 executable file
- 7zSFX_Constructor.exe (PID: 5968)
Starts application with an unusual extension
- 7zSFX_Constructor.exe (PID: 5968)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1452)
Manual execution by a user
- cmd.exe (PID: 1012)
- cmd.exe (PID: 5640)
- 7zSFX_Constructor.exe (PID: 5968)
The sample compiled with polish language support
- WinRAR.exe (PID: 1452)
- xcopy.exe (PID: 5228)
The sample compiled with russian language support
- WinRAR.exe (PID: 1452)
- xcopy.exe (PID: 6344)
- 7zSFX_Constructor.exe (PID: 896)
- xcopy.exe (PID: 5228)
The sample compiled with english language support
- xcopy.exe (PID: 6344)
- 7zSFX_Constructor.exe (PID: 896)
- 7zSFX_Constructor.exe (PID: 5968)
The sample compiled with turkish language support
- xcopy.exe (PID: 6344)
- 7zSFX_Constructor.exe (PID: 896)
Checks supported languages
- 7zSFX_Constructor.exe (PID: 5228)
- 7zSFX_Constructor.exe (PID: 896)
- 7zSFX_Constructor.exe (PID: 5968)
- ap30.dat (PID: 5892)
- ap10.dat (PID: 1088)
- ap14.dat (PID: 6700)
- ap30.dat (PID: 1280)
Reads the computer name
- 7zSFX_Constructor.exe (PID: 5228)
- 7zSFX_Constructor.exe (PID: 896)
- 7zSFX_Constructor.exe (PID: 5968)
- ap10.dat (PID: 1088)
- ap30.dat (PID: 5892)
- ap30.dat (PID: 1280)
Create files in a temporary directory
- 7zSFX_Constructor.exe (PID: 896)
Process checks computer location settings
- 7zSFX_Constructor.exe (PID: 896)
Creates files in the program directory
- xcopy.exe (PID: 6344)
- cmd.exe (PID: 4172)
- xcopy.exe (PID: 5228)
- cmd.exe (PID: 2288)
- 7zSFX_Constructor.exe (PID: 5968)
- ap10.dat (PID: 1088)
- ap14.dat (PID: 6700)
- ap30.dat (PID: 5892)
Creates files or folders in the user directory
- 7zSFX_Constructor.exe (PID: 896)
- 7zSFX_Constructor.exe (PID: 5968)
Creates a new folder
- cmd.exe (PID: 4172)
Reads mouse settings
- ap14.dat (PID: 6700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2018:12:09 11:50:31+00:00 |
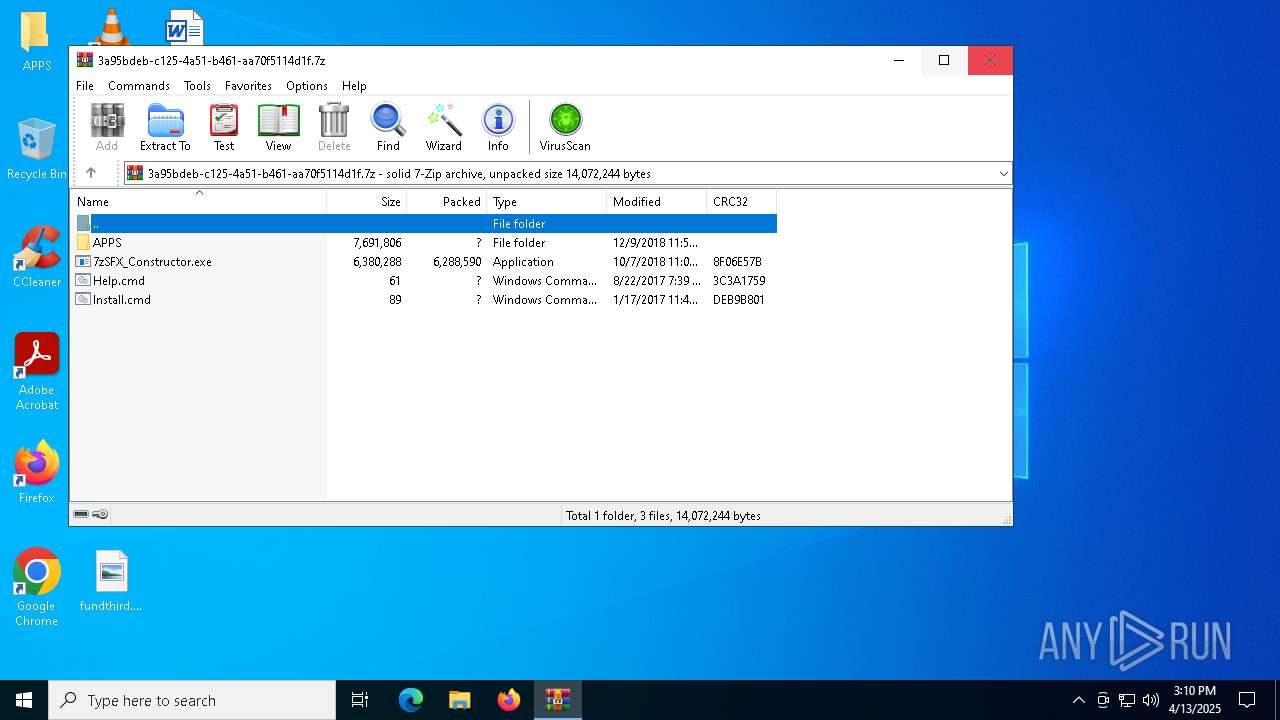
| ArchivedFileName: | APPS |
Total processes
160
Monitored processes
34
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | "C:\Windows\System32\cmd.exe" /c if not exist "C:\ProgramData\7zSFX_Constructor\APPS\Settings\Sert.cer.old" (copy /y "C:\ProgramData\7zSFX_Constructor\APPS\Sert\Sert.cer" "C:\ProgramData\7zSFX_Constructor\APPS\Sert\Sert.cer.old") | C:\Windows\SysWOW64\cmd.exe | — | 7zSFX_Constructor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
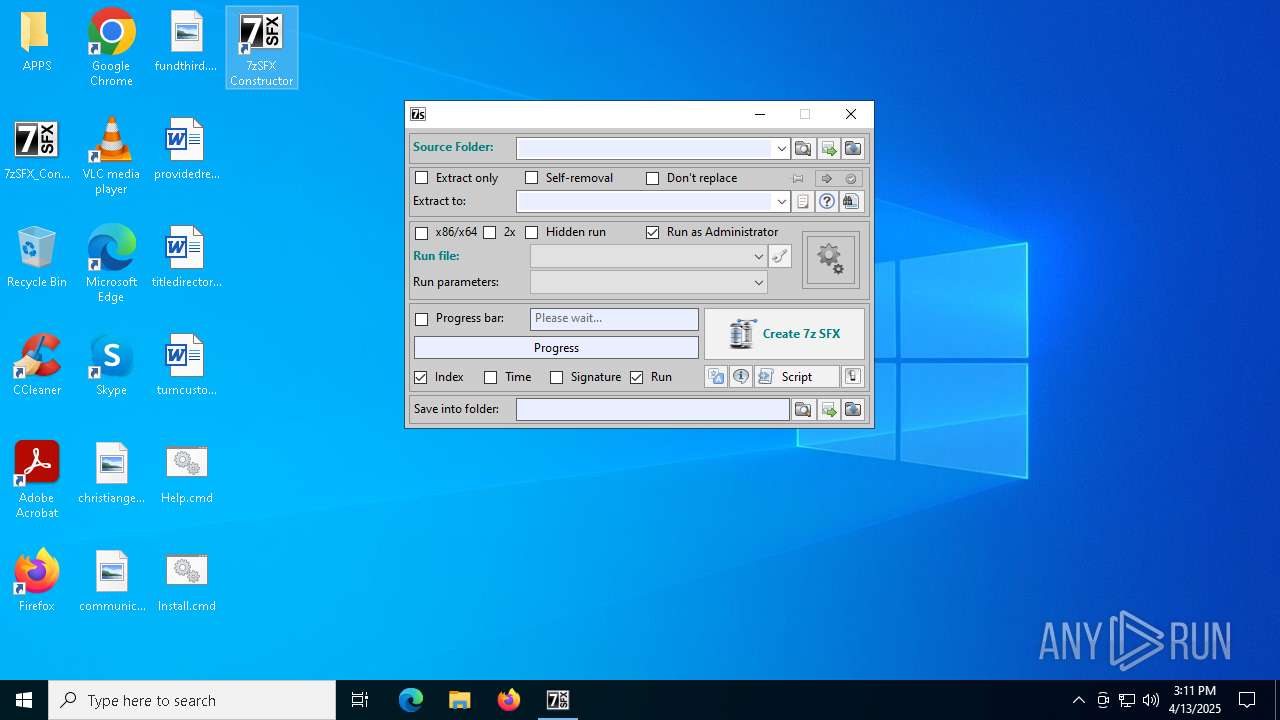
| 896 | 7zSFX_Constructor.exe -aiS | C:\Users\admin\Desktop\7zSFX_Constructor.exe | cmd.exe | ||||||||||||
User: admin Company: CryptoNick Integrity Level: MEDIUM Description: 7z SFX Constructor Exit code: 0 Version: 4.5.0.0 Modules
| |||||||||||||||
| 1012 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Help.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\Windows\System32\cmd.exe" /c xcopy "C:\Users\admin\Desktop\APPS" "C:\ProgramData\7zSFX_Constructor\APPS" /c /i /s /e /r /h /y | C:\Windows\SysWOW64\cmd.exe | — | 7zSFX_Constructor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1088 | "C:\ProgramData\7zSFX_Constructor\data\dat01\ap10.dat" a "unst.7z" "Uninstall.cmd" -m0=LZMA2:d=64m -ms=on -mx=9 -myx=9 | C:\ProgramData\7zSFX_Constructor\data\dat01\ap10.dat | — | 7zSFX_Constructor.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip GUI Exit code: 0 Version: 15.14 Modules
| |||||||||||||||
| 1280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\ProgramData\7zSFX_Constructor\data\dat01\ap30.dat" -addoverwrite "C:\ProgramData\7zSFX_Constructor\stb.sfx", "C:\ProgramData\7zSFX_Constructor\stb.sfx", "Inst.ico", ICONGROUP, 101, 0 | C:\ProgramData\7zSFX_Constructor\data\dat01\ap30.dat | — | 7zSFX_Constructor.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Resource viewer, decompiler & recompiler. Exit code: 0 Version: 3.6.0.92 Modules
| |||||||||||||||
| 1312 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\3a95bdeb-c125-4a51-b461-aa70f5114d1f.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 942
Read events
3 908
Write events
21
Delete events
13
Modification events
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\3a95bdeb-c125-4a51-b461-aa70f5114d1f.7z | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
69
Suspicious files
56
Text files
412
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\03.ico | image | |
MD5:9CCE39CC41B45137E1DF26C80500888B | SHA256:A7857DAFE02CD91699ED67CBDC329623A72BB5D5C5355EFE81C0828DD7538AD1 | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\01.ico | image | |
MD5:3802F70CAA8594D31EE3010E48ABC252 | SHA256:D5CB9C5494A059B37FE7402838001F2F33EE536430ACEF01887D84806A1C9AB2 | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Changelog.txt | text | |
MD5:A42B1D33FC08C288477B38ACD696430F | SHA256:007D561CFB13F6914FE37AA2DCD1412A9BB1C38D9526489AB3271A3D96F2D07E | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\04.ico | image | |
MD5:7FB4DA969F150C834A3B4DE251E27928 | SHA256:47C7D32CE8F8BB3C1751551EC7C62E8A1F851D0853A004653387C92140C54EA6 | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\128.ico | image | |
MD5:F125D75087C3DF3326E64D31F6E2B731 | SHA256:199FDCC2688CD54B356CB11135EBB3B4655183B93E32D30FCBF763EE53C92CF9 | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\09.ico | image | |
MD5:C48D18018157B6C25CF38A78E0C7E742 | SHA256:991F627239A110744C30E8BE8A447C7C9B10913D9B96AEE7F50B01ECC5DD4292 | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\107.ico | image | |
MD5:9F8B4FB338503FC90874DD561E9D7C4C | SHA256:9108F20BDC4ED66CA0A15F627CCF382CADB99148E9E965F416D3565851EC117C | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\11.ico | image | |
MD5:284B99343AAE097F2D9E9D779FB539C1 | SHA256:916ABAAE31E56CAAF467920CA7AB5A8610172C6A854C6AE53FA8FF172E710240 | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\777.ico | image | |
MD5:AD7CB98A3449C43F7168050A6FD9B982 | SHA256:F05D4C218BEE7C590125D960C04FE8EAD663D3FB6A2067EA1B3130CBD61C1F71 | |||
| 1452 | WinRAR.exe | C:\Users\admin\Desktop\APPS\Icon\22.ico | image | |
MD5:4C77C30650E4C5EC389980129C82A095 | SHA256:A229C336F4FC0E64E662E1200EA327716F35BF6928F2C9E59BA39B67BC3A616F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4488 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4488 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4488 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4488 | SIHClient.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |