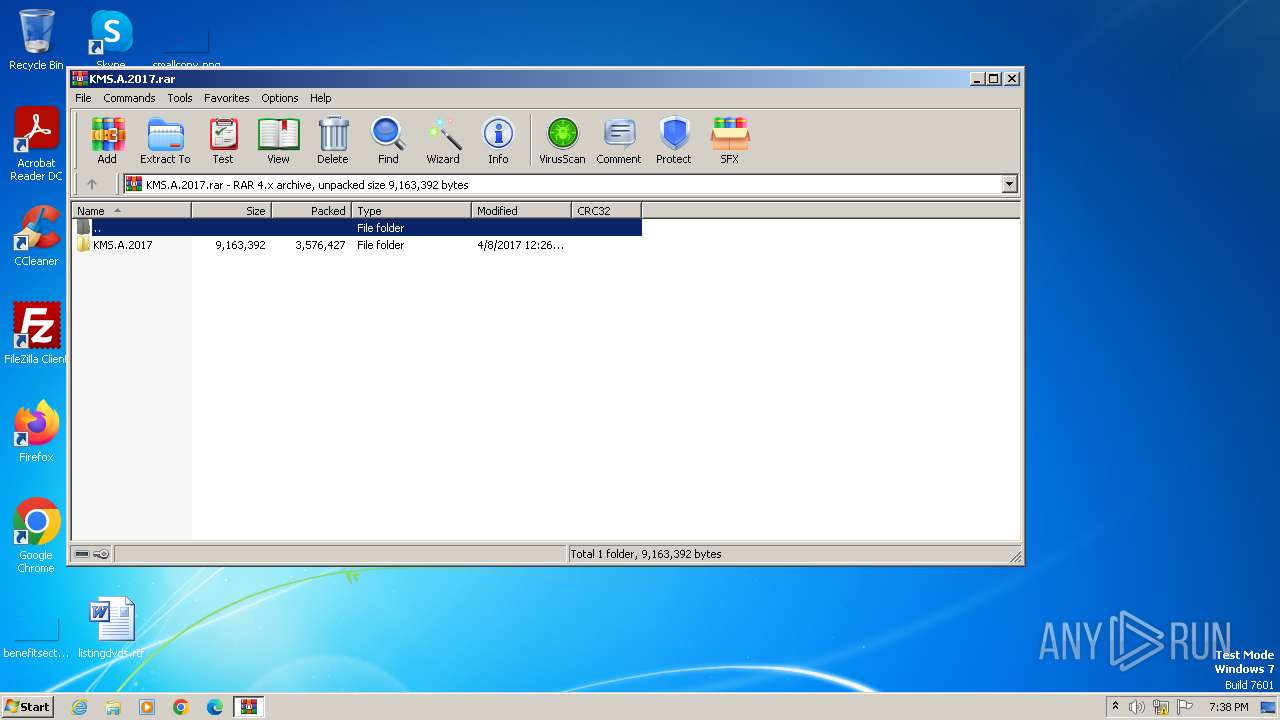
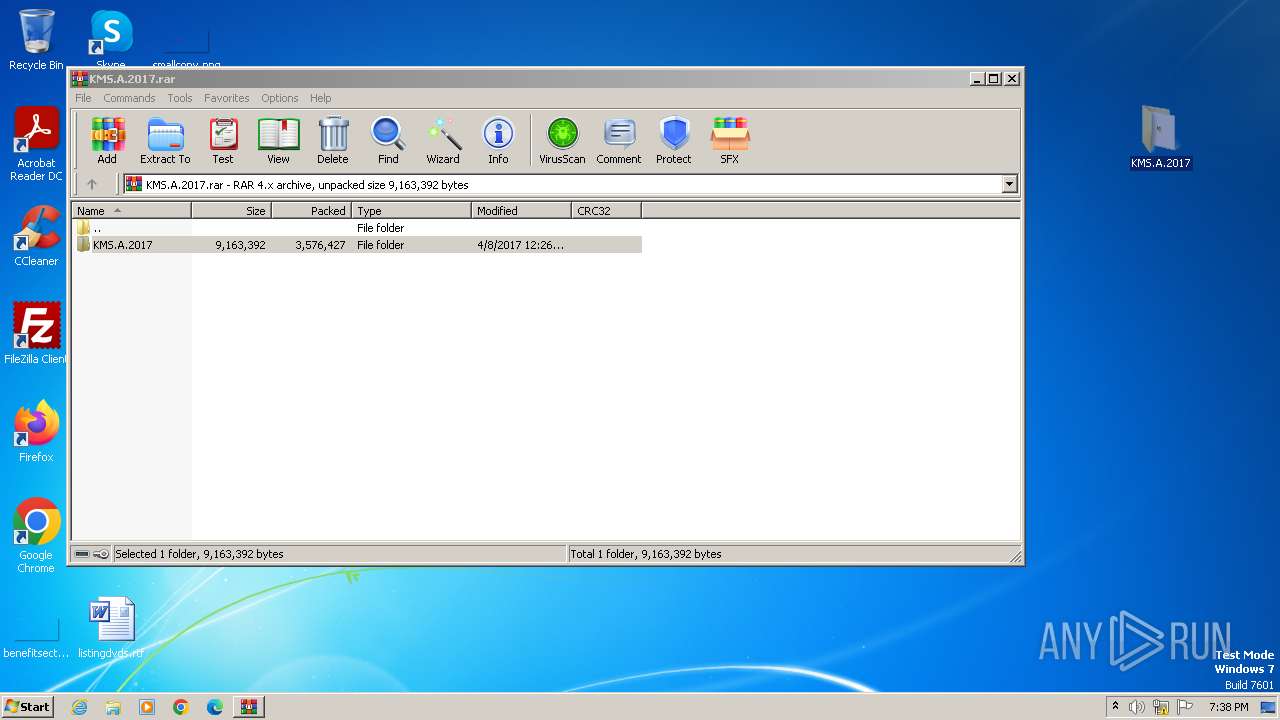
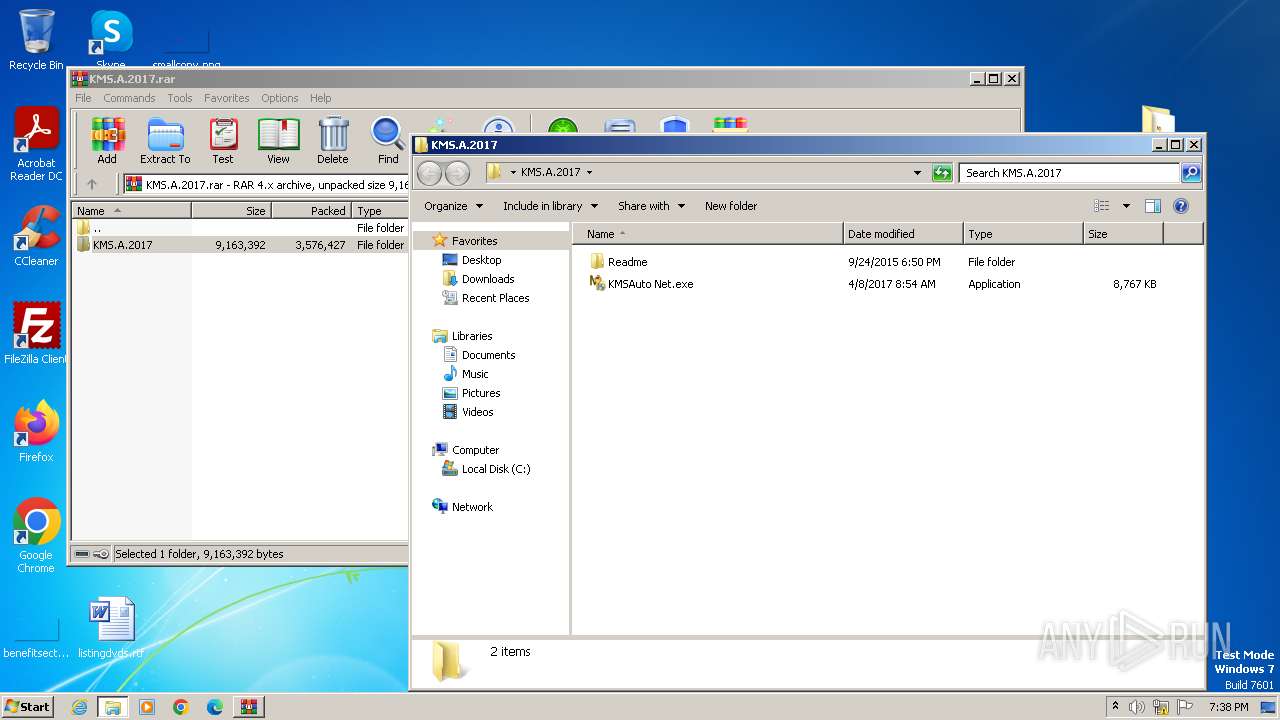
| File name: | KMS.A.2017.rar |
| Full analysis: | https://app.any.run/tasks/14085024-9e0c-4025-9dc5-20a42b7e6163 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2023, 19:37:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 8EDE910F58FADCB44F97CD50207FB818 |
| SHA1: | 27A2F00BB5E09B58E89B3E332F98D9D1BA18999F |
| SHA256: | 105D3A69121C173309BF924EE69AC95ED6FC89837143DE90DA13CCB9B5FC7CB9 |
| SSDEEP: | 98304:aenXXmQCgslG8Hkzv9cQ/5hYbWpGcWOV7IdGE5dssuOnTIxnQD6lc4Ne6pGld215:ru+TVJOXbl2 |
MALICIOUS
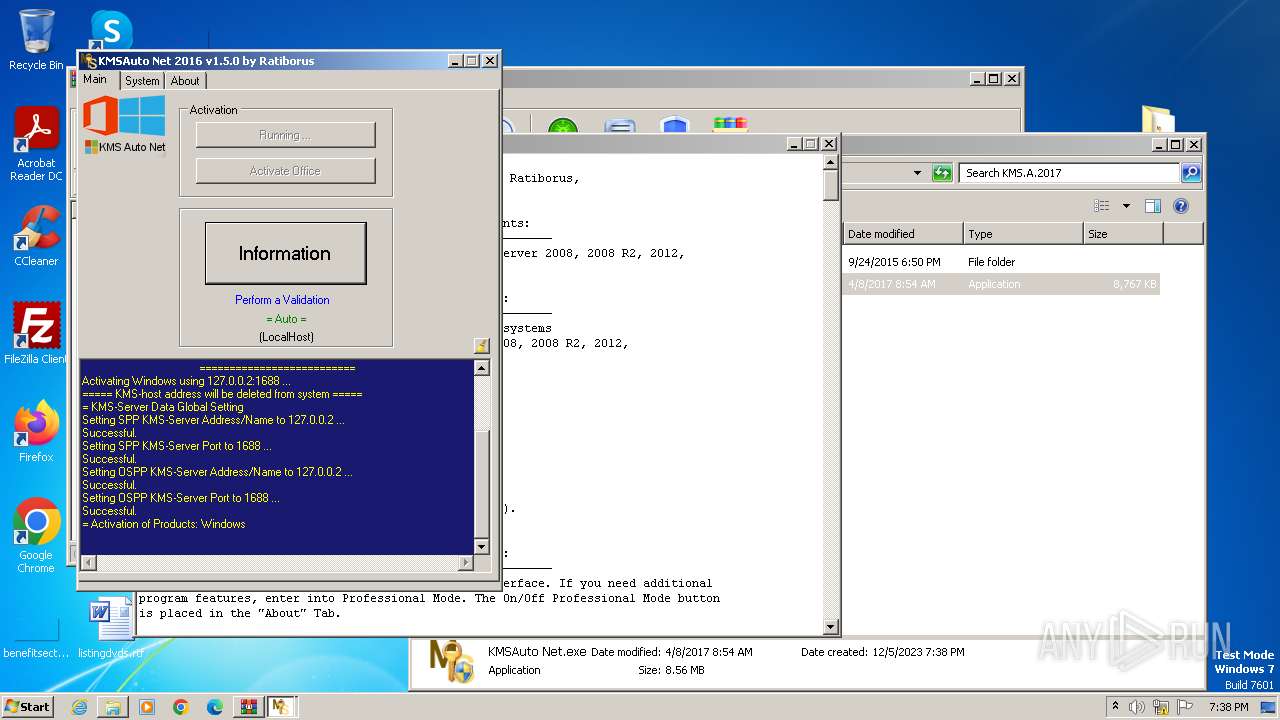
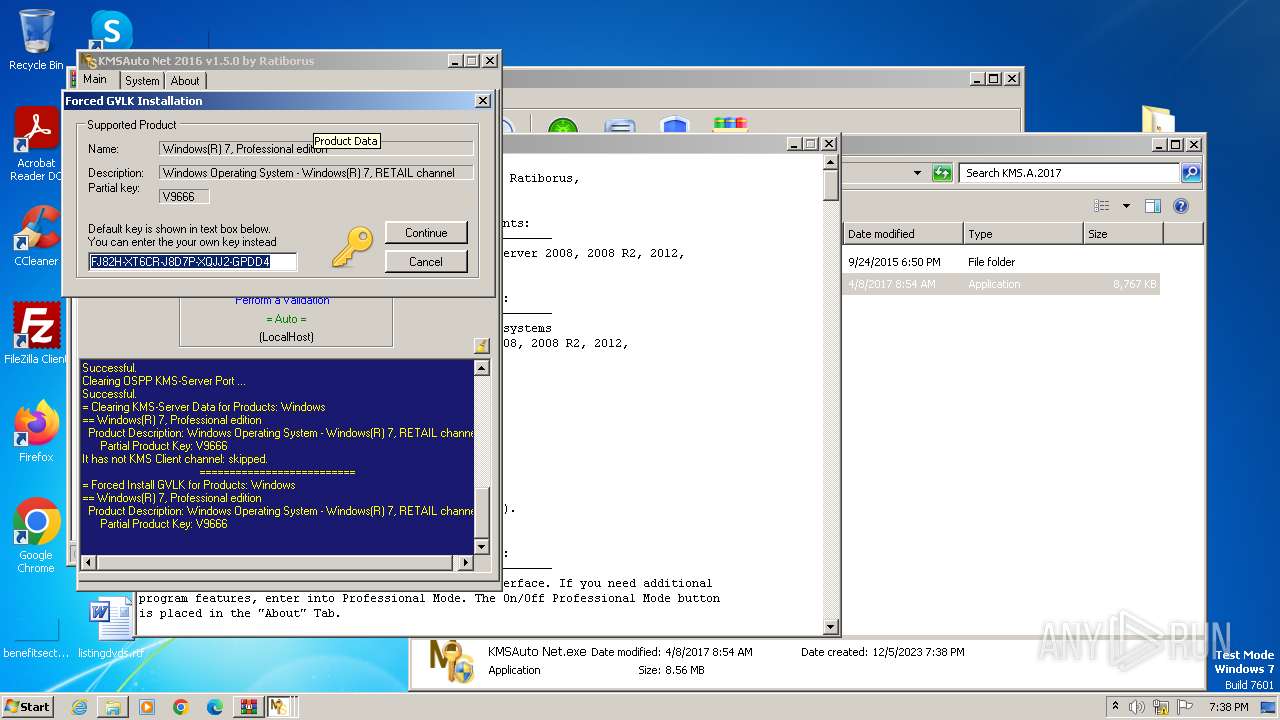
Drops the executable file immediately after the start
- KMSAuto Net.exe (PID: 604)
- wzt.dat (PID: 3512)
- AESDecoder.exe (PID: 3268)
- bin.dat (PID: 3928)
- bin_x86.dat (PID: 2128)
SUSPICIOUS
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 604)
- cmd.exe (PID: 3460)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 604)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 604)
Starts application with an unusual extension
- cmd.exe (PID: 3252)
- cmd.exe (PID: 3408)
- cmd.exe (PID: 2456)
Process drops legitimate windows executable
- wzt.dat (PID: 3512)
- bin_x86.dat (PID: 2128)
Application launched itself
- cmd.exe (PID: 3460)
Drops a system driver (possible attempt to evade defenses)
- bin_x86.dat (PID: 2128)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 604)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 604)
Executes as Windows Service
- KMSSS.exe (PID: 3748)
Starts SC.EXE for service management
- KMSAuto Net.exe (PID: 604)
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 604)
Uses REG/REGEDIT.EXE to modify registry
- KMSAuto Net.exe (PID: 604)
- cmd.exe (PID: 3428)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 564)
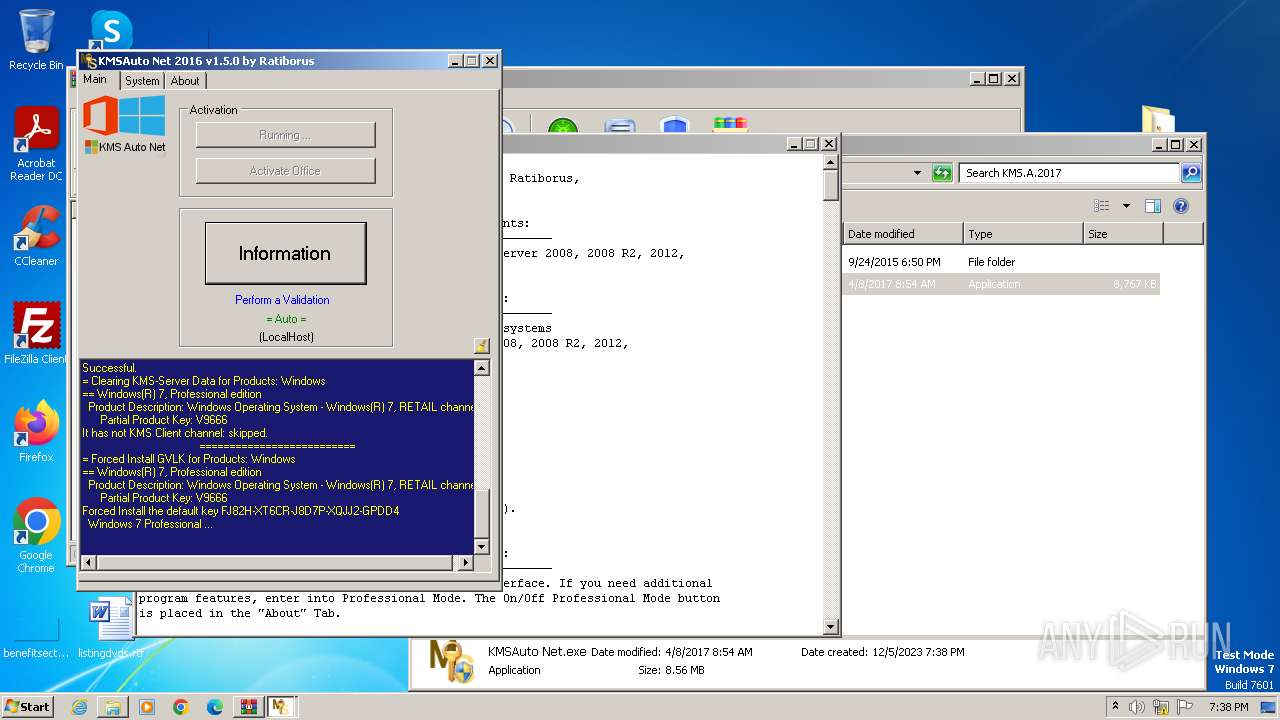
Manual execution by a user
- KMSAuto Net.exe (PID: 604)
- KMSAuto Net.exe (PID: 2956)
Checks supported languages
- KMSAuto Net.exe (PID: 604)
- wzt.dat (PID: 3512)
- certmgr.exe (PID: 1984)
- bin.dat (PID: 3928)
- AESDecoder.exe (PID: 3268)
- KMSSS.exe (PID: 3748)
- certmgr.exe (PID: 4008)
- bin_x86.dat (PID: 2128)
Reads Environment values
- KMSAuto Net.exe (PID: 604)
Reads the computer name
- KMSAuto Net.exe (PID: 604)
- KMSSS.exe (PID: 3748)
Reads the machine GUID from the registry
- KMSAuto Net.exe (PID: 604)
- KMSSS.exe (PID: 3748)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 604)
Reads product name
- KMSAuto Net.exe (PID: 604)
Creates files in the program directory
- cmd.exe (PID: 3092)
- KMSAuto Net.exe (PID: 604)
- wzt.dat (PID: 3512)
- bin.dat (PID: 3928)
- bin_x86.dat (PID: 2128)
- KMSSS.exe (PID: 3748)
- AESDecoder.exe (PID: 3268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 3519860 |
|---|---|
| UncompressedSize: | 8976672 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:04:08 08:54:30 |
| PackingMethod: | Normal |
| ArchivedFileName: | KMS.A.2017\KMSAuto Net.exe |
Total processes
132
Monitored processes
51
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\KMS.A.2017.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 604 | "C:\Users\admin\Desktop\KMS.A.2017\KMSAuto Net.exe" | C:\Users\admin\Desktop\KMS.A.2017\KMSAuto Net.exe | explorer.exe | ||||||||||||
User: admin Company: MSFree Inc. Integrity Level: HIGH Description: KMSAuto Net Exit code: 0 Version: 1.5.0 Modules
| |||||||||||||||
| 684 | C:\Windows\System32\cmd.exe /c echo test>>"C:\Users\admin\Desktop\KMS.A.2017\test.test" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1016 | C:\Windows\System32\reg delete "HKEY_USERS\S-1-5-20\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0ff1ce15-a989-479d-af46-f275c6370663" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1128 | C:\Windows\System32\reg delete "HKEY_USERS\S-1-5-20\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1296 | C:\Windows\System32\cmd.exe /D /c del /F /Q "wzt.dat" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1376 | C:\Windows\System32\Netsh Advfirewall Firewall add rule name="0pen Port KMS" dir=in action=allow protocol=TCP localport=1688 | C:\Windows\System32\netsh.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1496 | C:\Windows\System32\cmd.exe /D /c del /F /Q "bin.dat" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1556 | C:\Windows\System32\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55C92734-D682-4D71-983E-D6EC3F16059F" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | cmd /c md "C:\Users\admin\AppData\Local\MSfree Inc" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
4 642
Read events
4 493
Write events
141
Delete events
8
Modification events
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1904) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1376) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
19
Suspicious files
11
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa564.7893\KMS.A.2017\KMSAuto Net.exe | executable | |
MD5:D02B35945C18E89DC3BB43BC7F6153BE | SHA256:0B05EA08028F239B11F8C30249B0F0AA86966EE4974D03B01BAE2EE88BEFBBEB | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa564.7893\KMS.A.2017\Readme\readme_fr.txt | text | |
MD5:59168B67B69B95DDACF6C845FBA47D2A | SHA256:4B218858BC9848C2CFF531FCDCEEB546E8C7EB1C8F3D237C3299984ABE492D10 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa564.7893\KMS.A.2017\Readme\readme_kms.txt | text | |
MD5:352709B6AED3902D4399F6615A7A7E70 | SHA256:D3BEF0FEF19603B33B86E1CA431A25CB8A6DF047058E073BBF8BB931533217AA | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa564.7893\KMS.A.2017\Readme\readme_vi.txt | text | |
MD5:25FCE528C81065CD5309083A0B3F1B5E | SHA256:64F1907B2B2414E4BFD14C367E3A0014F3BBF1E0EEA3319154054F9C1B26E324 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa564.7893\KMS.A.2017\Readme\readme_es.txt | text | |
MD5:38E4EC7368615767BF358BE81D95935D | SHA256:7C86BCA7A776AA99FE581D689F6C22676EAFF41D64082FEEF71E0080A049EA13 | |||
| 604 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\wzt.dat | executable | |
MD5:822DA2319294F2B768BFE9ED4EEBAC15 | SHA256:17B74D4EA905FAC0BA6857F78F47EE1E940675AF1BC27DED69FE2941318106EF | |||
| 3512 | wzt.dat | C:\ProgramData\KMSAuto\wzt\wzteam.cer | binary | |
MD5:76B56D90E6F1DA030A8B85E64579F25A | SHA256:FD2D7DF0220DD65EE23D0090299DFCC356F6F8F7167BAE9ADF7D08CEFAF39D02 | |||
| 604 | KMSAuto Net.exe | C:\Users\admin\AppData\Local\MSfree Inc\kmsauto.ini | text | |
MD5:AF6A20FD7DFADCD582CCF2B1BFAAF82B | SHA256:0BEE97833A70AA9BA271E93226DACE849836C64919FBFE15543D694E219D4AF2 | |||
| 684 | cmd.exe | C:\Users\admin\Desktop\KMS.A.2017\test.test | text | |
MD5:9F06243ABCB89C70E0C331C61D871FA7 | SHA256:837CCB607E312B170FAC7383D7CCFD61FA5072793F19A25E75FBACB56539B86B | |||
| 604 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\bin.dat | executable | |
MD5:2A96E417738225FA806A6EF275443BC8 | SHA256:839D31305D8FA842C832E8EC0F61D6BC575734449EB774B7C8DD79669594E25B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |