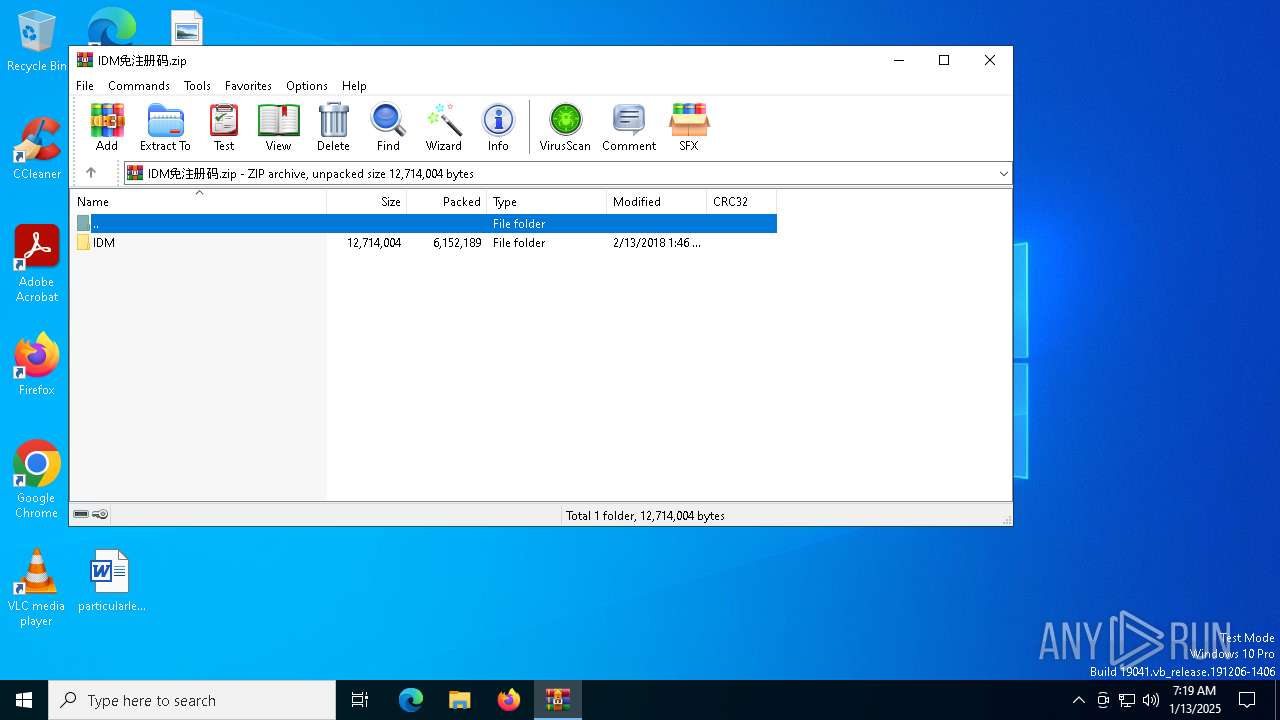
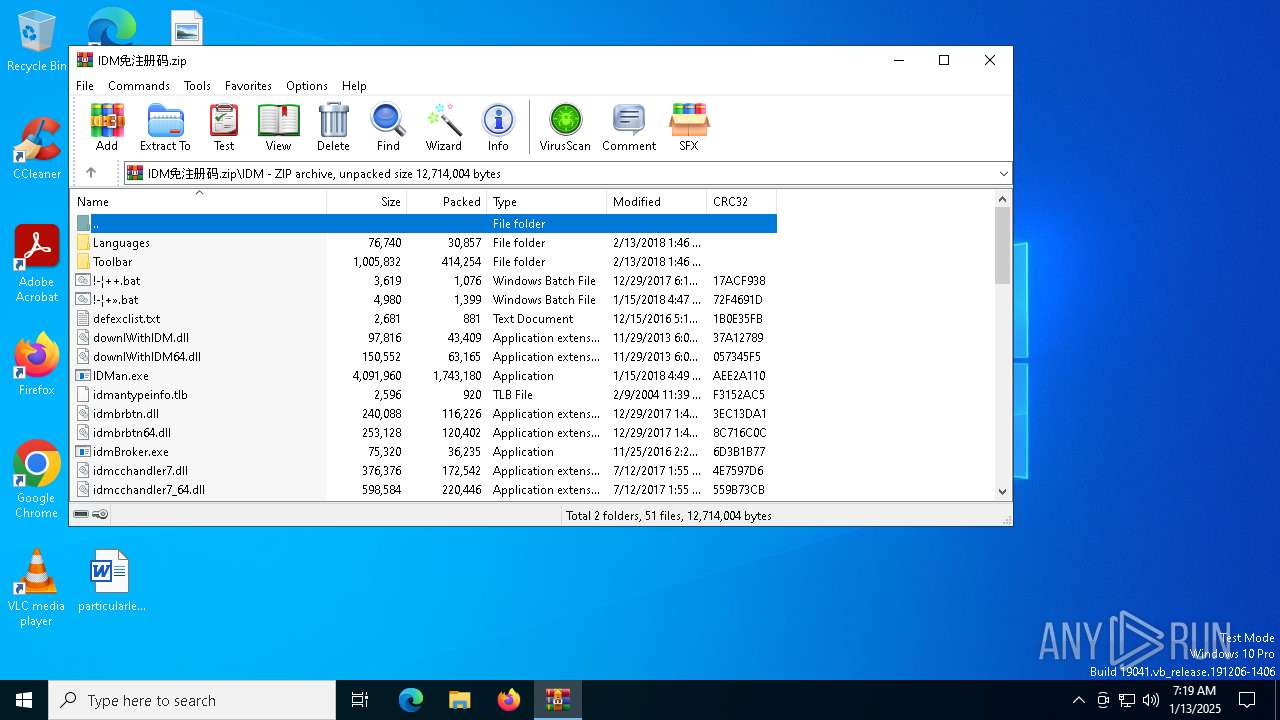
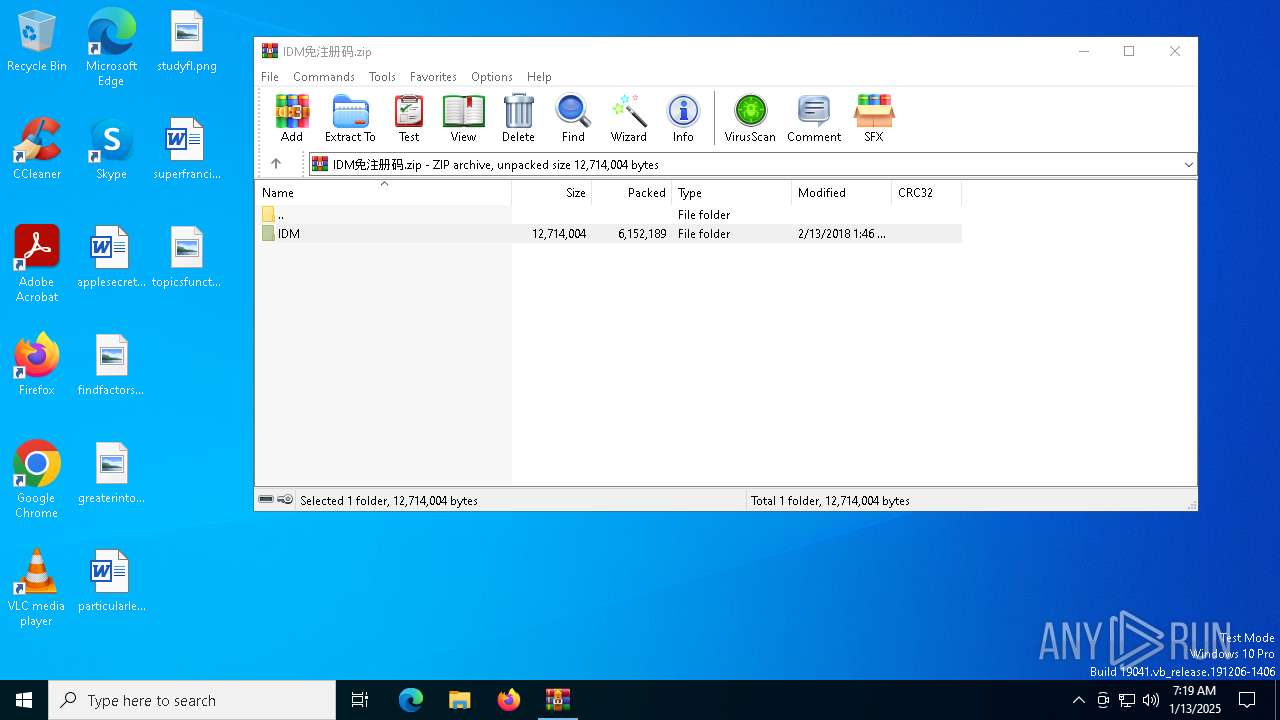
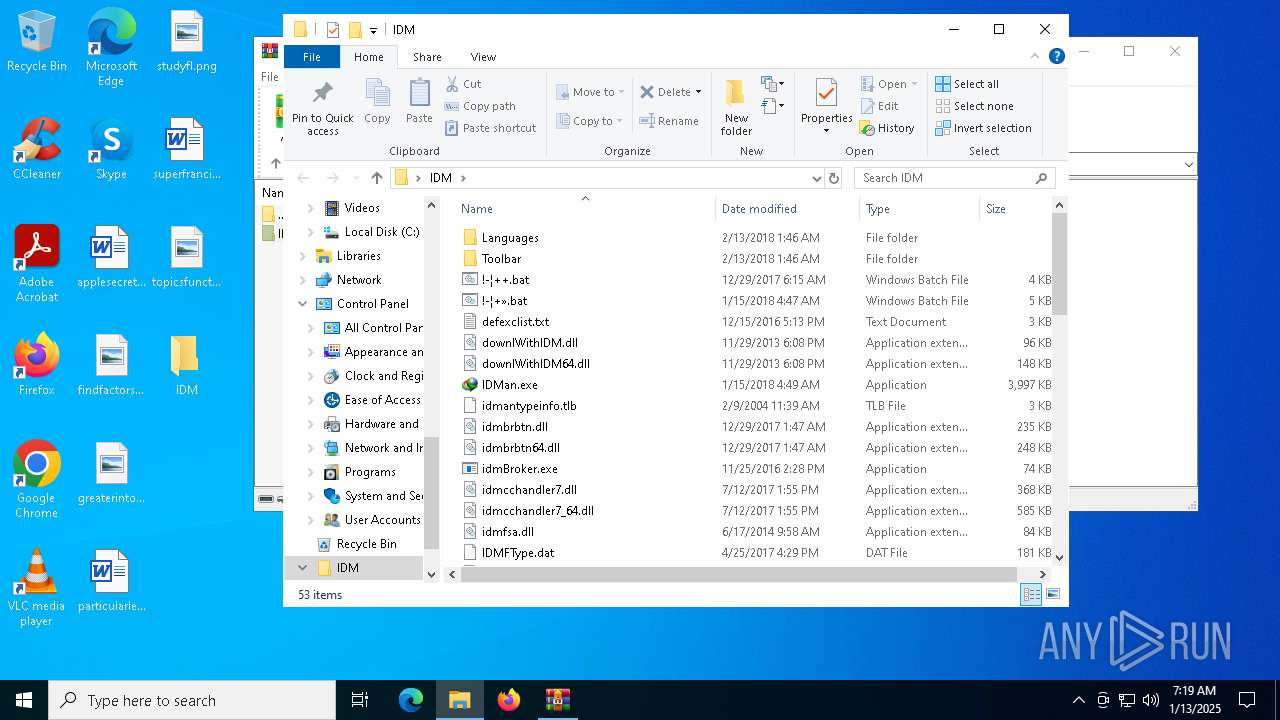
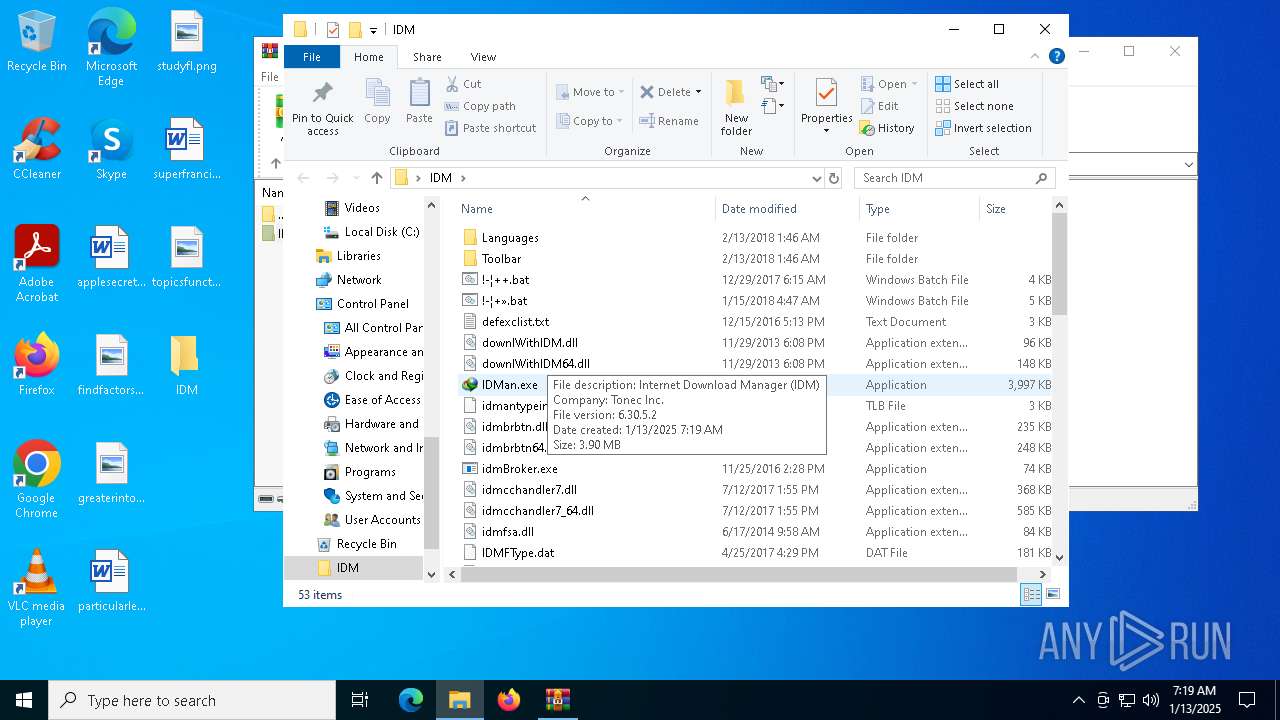
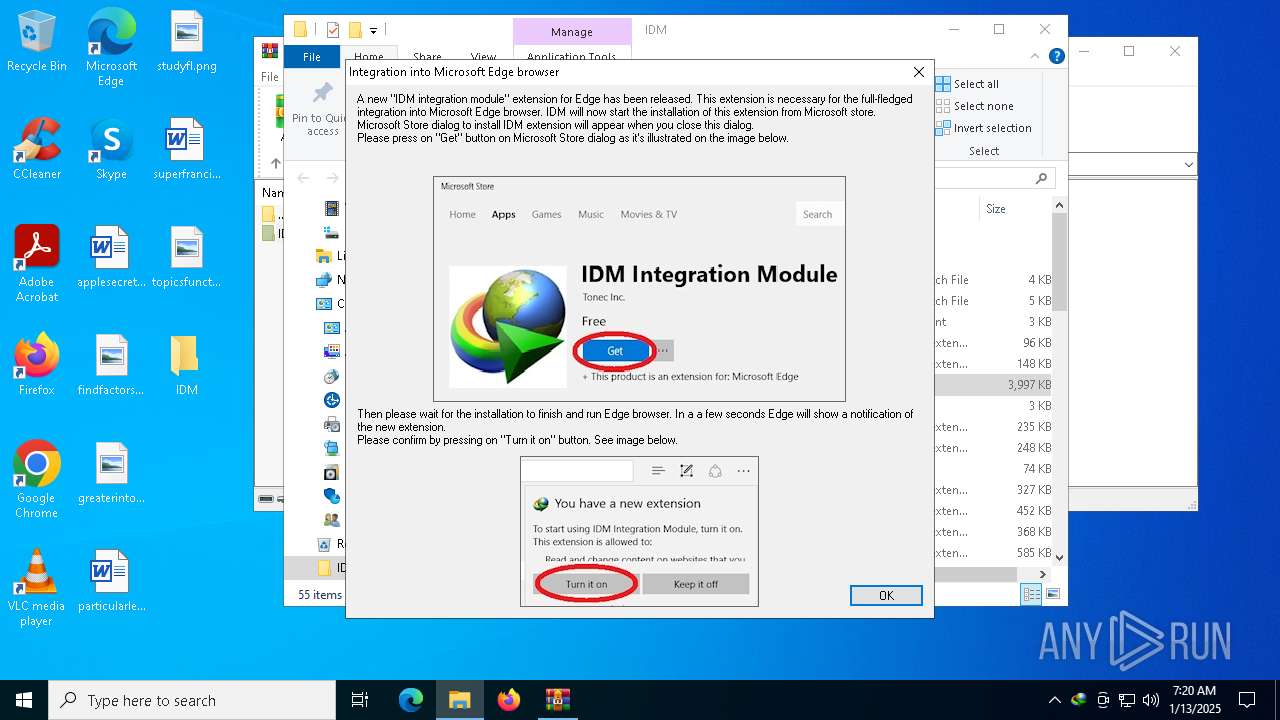
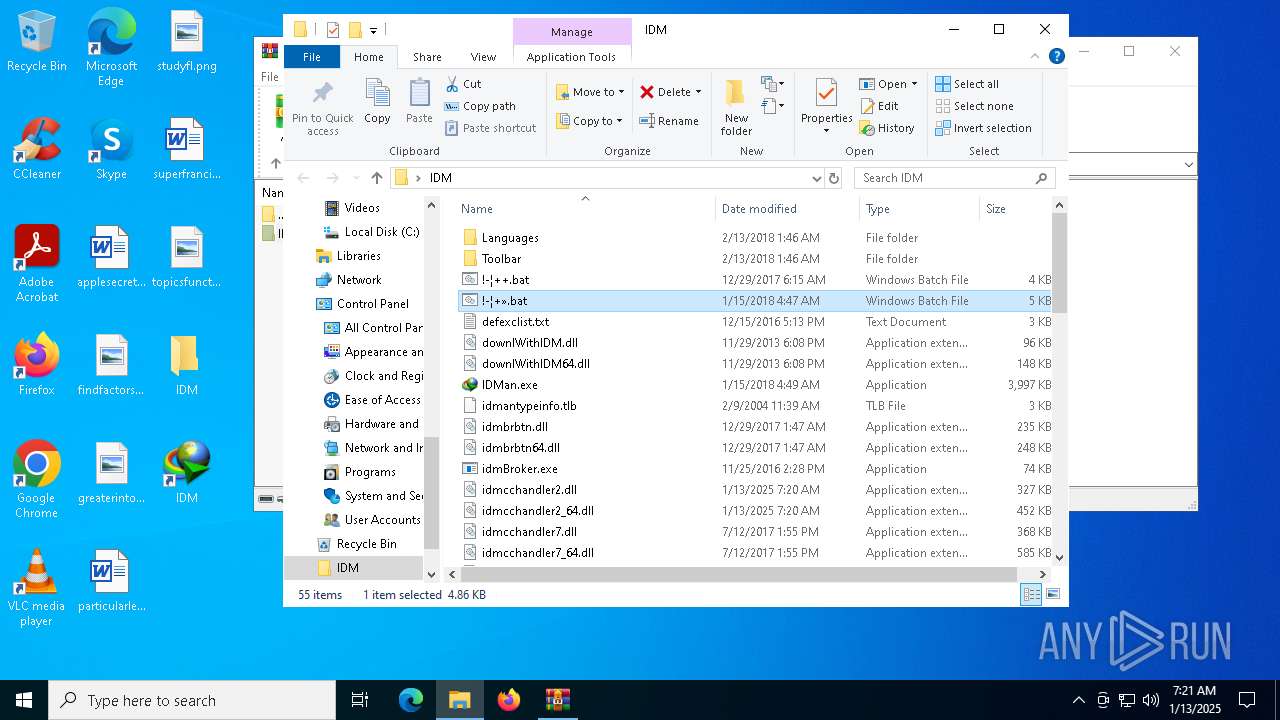
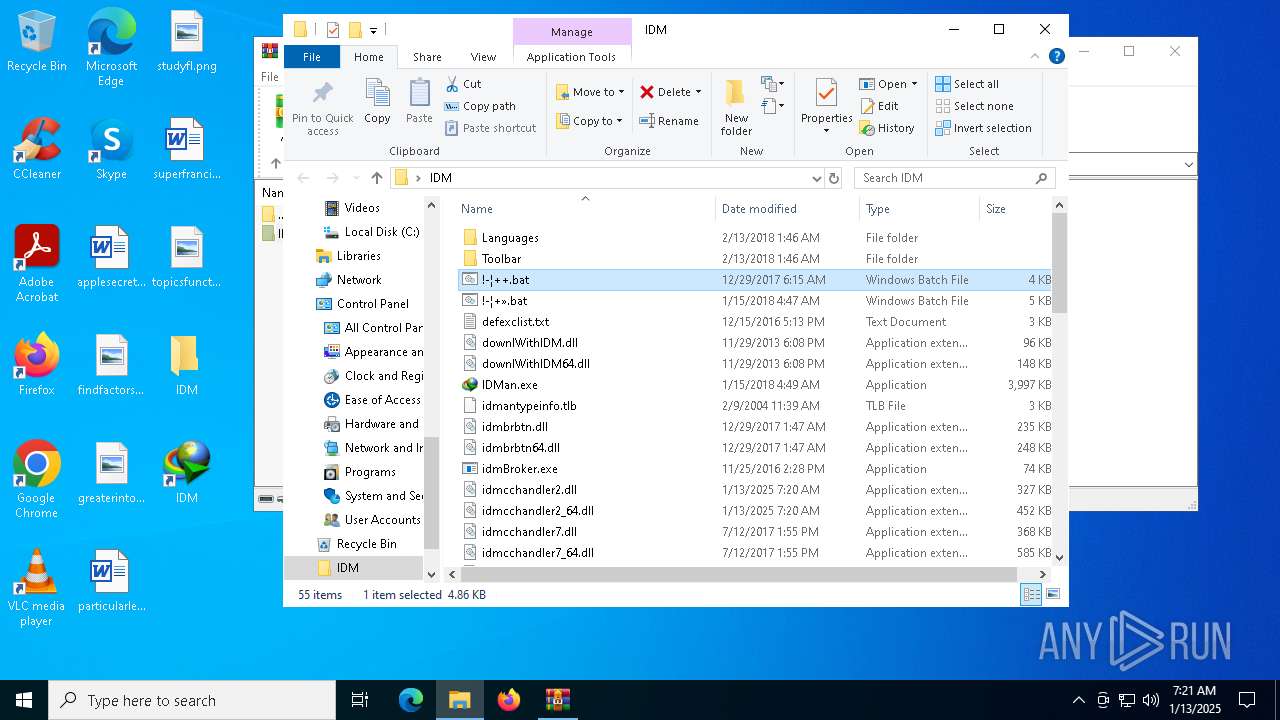
| File name: | IDM免注册码.zip |
| Full analysis: | https://app.any.run/tasks/a6a6e622-8e94-43b7-9f30-c000ea9cc175 |
| Verdict: | Malicious activity |
| Analysis date: | January 13, 2025, 07:19:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 64E435771BC464BB83A645209EF6086A |
| SHA1: | B6E43D1160814291F492CC07E98E3FF8B6566CDB |
| SHA256: | 1053C4ACCCE121455AB6F7DD86A947793E3AE7F03906E987739E572CFDF3D000 |
| SSDEEP: | 98304:K2ls4EEookb9Pp/xnkL4Bfq9i+Sw/jsBYTgMXCoBVvctP7XvjEhK9qoRHj1ZTqOc:h3C1DGFuYUxk/ |
MALICIOUS
Starts NET.EXE for service management
- Uninstall.exe (PID: 5696)
- net.exe (PID: 6608)
- net.exe (PID: 5320)
- Uninstall.exe (PID: 2432)
- cmd.exe (PID: 6824)
- net.exe (PID: 1224)
- net.exe (PID: 7052)
- cmd.exe (PID: 2100)
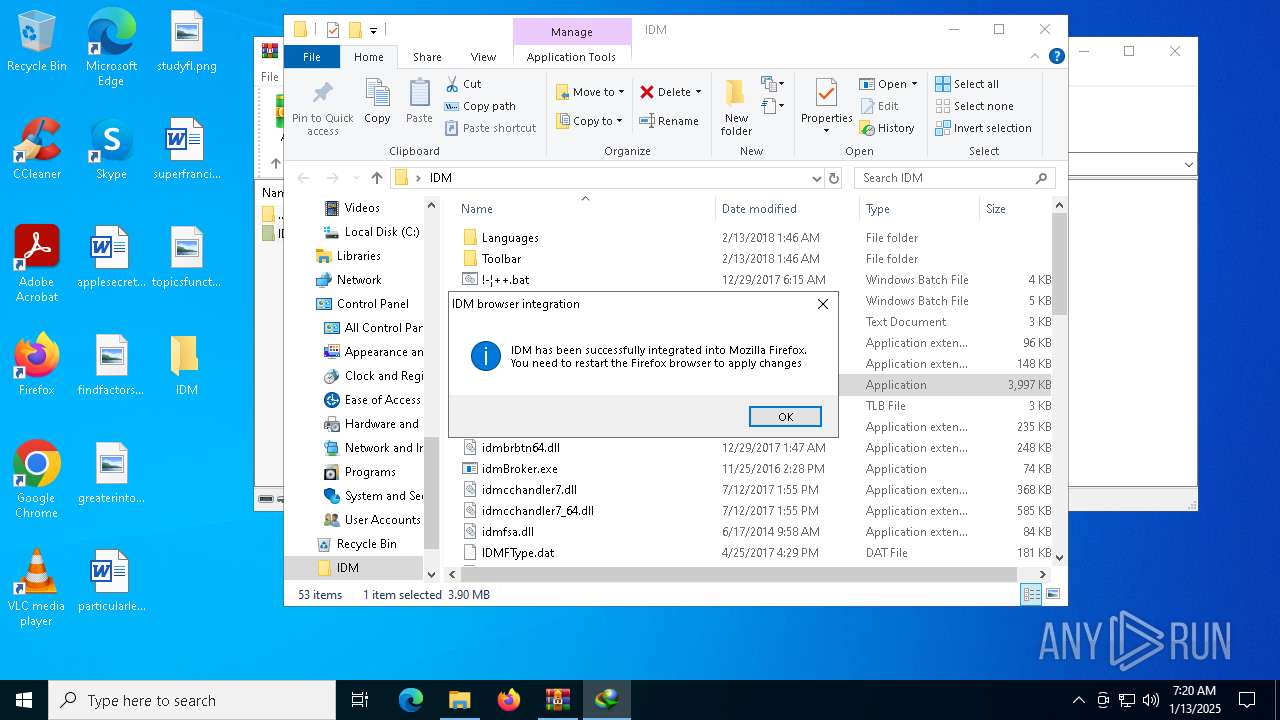
Registers / Runs the DLL via REGSVR32.EXE
- Uninstall.exe (PID: 5696)
- IDMan.exe (PID: 3260)
- cmd.exe (PID: 6824)
- IDMan.exe (PID: 640)
- Uninstall.exe (PID: 2432)
- cmd.exe (PID: 2100)
Changes the autorun value in the registry
- rundll32.exe (PID: 5460)
- rundll32.exe (PID: 848)
Executing a file with an untrusted certificate
- MediumILStart.exe (PID: 5964)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 2632)
- rundll32.exe (PID: 5460)
- rundll32.exe (PID: 6376)
- rundll32.exe (PID: 848)
The process executes VB scripts
- cmd.exe (PID: 5916)
- cmd.exe (PID: 3288)
Executable content was dropped or overwritten
- IDMan.exe (PID: 3260)
- rundll32.exe (PID: 5460)
- rundll32.exe (PID: 6376)
- rundll32.exe (PID: 848)
- rundll32.exe (PID: 6572)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5096)
- wscript.exe (PID: 1220)
- mshta.exe (PID: 420)
Reads security settings of Internet Explorer
- IDMan.exe (PID: 3260)
- Uninstall.exe (PID: 5696)
- Uninstall.exe (PID: 2432)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 5696)
- Uninstall.exe (PID: 2432)
- cmd.exe (PID: 6824)
- cmd.exe (PID: 2100)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 6320)
- regsvr32.exe (PID: 1536)
- regsvr32.exe (PID: 1172)
- regsvr32.exe (PID: 4716)
- IDMan.exe (PID: 640)
- regsvr32.exe (PID: 1576)
- regsvr32.exe (PID: 420)
- regsvr32.exe (PID: 6332)
- regsvr32.exe (PID: 4952)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6824)
- cmd.exe (PID: 2100)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6824)
- cmd.exe (PID: 2100)
The process executes via Task Scheduler
- explorer.exe (PID: 4360)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 2632)
- IDMan.exe (PID: 3260)
- rundll32.exe (PID: 5460)
- rundll32.exe (PID: 6376)
- rundll32.exe (PID: 848)
- rundll32.exe (PID: 6572)
The process uses the downloaded file
- WinRAR.exe (PID: 2632)
- cmd.exe (PID: 5916)
- Uninstall.exe (PID: 5696)
- IDMan.exe (PID: 3260)
- cmd.exe (PID: 3288)
Manual execution by a user
- cmd.exe (PID: 5916)
- IDMan.exe (PID: 3260)
- cmd.exe (PID: 3288)
- idmBroker.exe (PID: 3420)
- cmd.exe (PID: 6824)
- cmd.exe (PID: 2100)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2632)
Creates files or folders in the user directory
- IDMan.exe (PID: 3260)
Checks proxy server information
- IDMan.exe (PID: 3260)
- IDMan.exe (PID: 3544)
Checks supported languages
- Uninstall.exe (PID: 5696)
- IEMonitor.exe (PID: 540)
- IDMan.exe (PID: 3260)
- IDMIntegrator64.exe (PID: 6440)
- idmBroker.exe (PID: 6816)
- IDMan.exe (PID: 640)
- IDMan.exe (PID: 3544)
- Uninstall.exe (PID: 2432)
- TextInputHost.exe (PID: 6252)
- StartMenuExperienceHost.exe (PID: 3364)
Process checks computer location settings
- Uninstall.exe (PID: 5696)
- IDMan.exe (PID: 3260)
- IDMan.exe (PID: 640)
- Uninstall.exe (PID: 2432)
- StartMenuExperienceHost.exe (PID: 3364)
Reads the computer name
- IDMIntegrator64.exe (PID: 6440)
- IEMonitor.exe (PID: 540)
- identity_helper.exe (PID: 1348)
- identity_helper.exe (PID: 4944)
- idmBroker.exe (PID: 3420)
- idmBroker.exe (PID: 6816)
- Uninstall.exe (PID: 2432)
- IDMan.exe (PID: 3544)
Reads the time zone
- runonce.exe (PID: 244)
- runonce.exe (PID: 4336)
Reads Environment values
- identity_helper.exe (PID: 1348)
- identity_helper.exe (PID: 4944)
Reads security settings of Internet Explorer
- runonce.exe (PID: 244)
- runonce.exe (PID: 4336)
Creates files in the driver directory
- rundll32.exe (PID: 5460)
Application launched itself
- msedge.exe (PID: 6632)
- msedge.exe (PID: 4596)
Disables trace logs
- IDMan.exe (PID: 3544)
Create files in a temporary directory
- IDMan.exe (PID: 3544)
Reads Internet Explorer settings
- mshta.exe (PID: 420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (42.1) |
|---|---|---|
| .zip | | | ZIP compressed archive (21) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:02:13 09:46:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | IDM/ |
Total processes
325
Monitored processes
188
Malicious processes
8
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | reg delete HKLM\Software\Classes\CLSID\{D5B91409-A8CA-4973-9A0B-59F713D25671} /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 244 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 372 | C:\WINDOWS\system32\net1 start IDMWFP | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | /s "C:\Users\admin\Desktop\IDM\IDMGetAll64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 420 | mshta VBScript:Execute("Set a=CreateObject(""WScript.Shell""):Set b=a.CreateShortcut(a.SpecialFolders(""Desktop"") & ""\IDM.lnk""):b.TargetPath=""C:\Users\admin\Desktop\IDM\IDMan.exe"":b.WorkingDirectory=""C:\Users\admin\Desktop\IDM\"":b.Save:close") | C:\Windows\System32\mshta.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 540 | "C:\Users\admin\Desktop\IDM\IEMonitor.exe" | C:\Users\admin\Desktop\IDM\IEMonitor.exe | — | IDMan.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: MEDIUM Description: Internet Download Manager agent for click monitoring in IE-based browsers Exit code: 1 Version: 6, 22, 1, 1 Modules
| |||||||||||||||
| 624 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3252 --field-trial-handle=2384,i,4095980262001261192,2091875898381490628,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
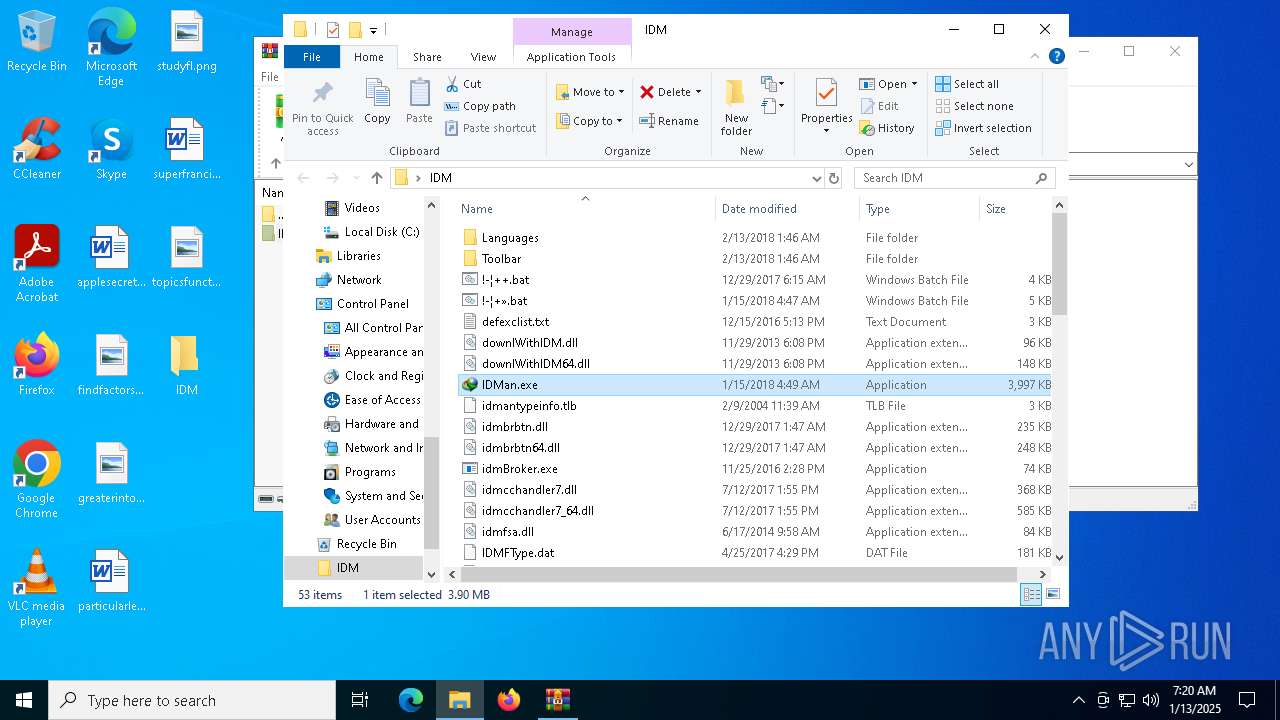
| 640 | "C:\Users\admin\Desktop\IDM\IDMan.exe" /rtr /isupdt /setlngid 2052 /fulllngfile idm_chn2.lng | C:\Users\admin\Desktop\IDM\IDMan.exe | — | cmd.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager (IDM) Exit code: 1 Version: 6, 30, 5, 2 | |||||||||||||||
| 848 | Rundll32 setupapi.dll,InstallHinfSection DefaultInstall 128 .\idmwfp.inf | C:\Windows\System32\rundll32.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1016 | reg delete HKLM\Software\Classes\Wow6432Node\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C} /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
47 502
Read events
46 586
Write events
760
Delete events
156
Modification events
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IDM免注册码.zip | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5916) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (3260) IDMan.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\IDMan_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
60
Suspicious files
342
Text files
239
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
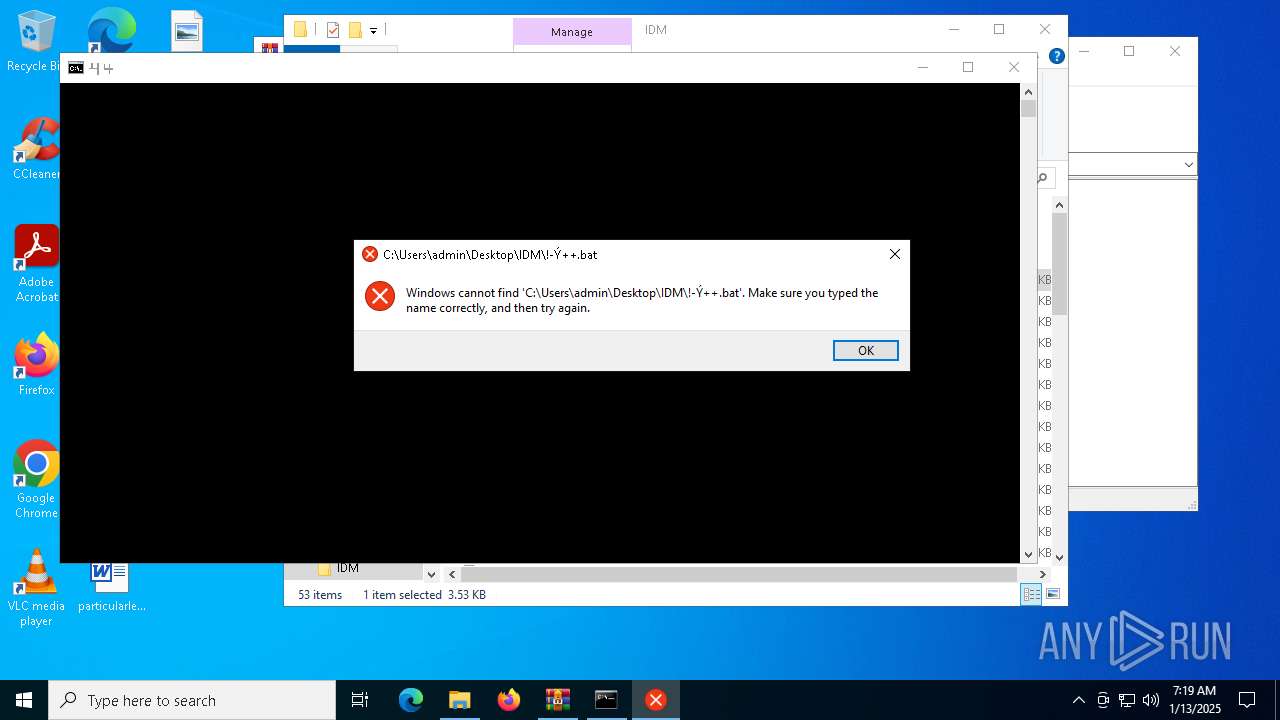
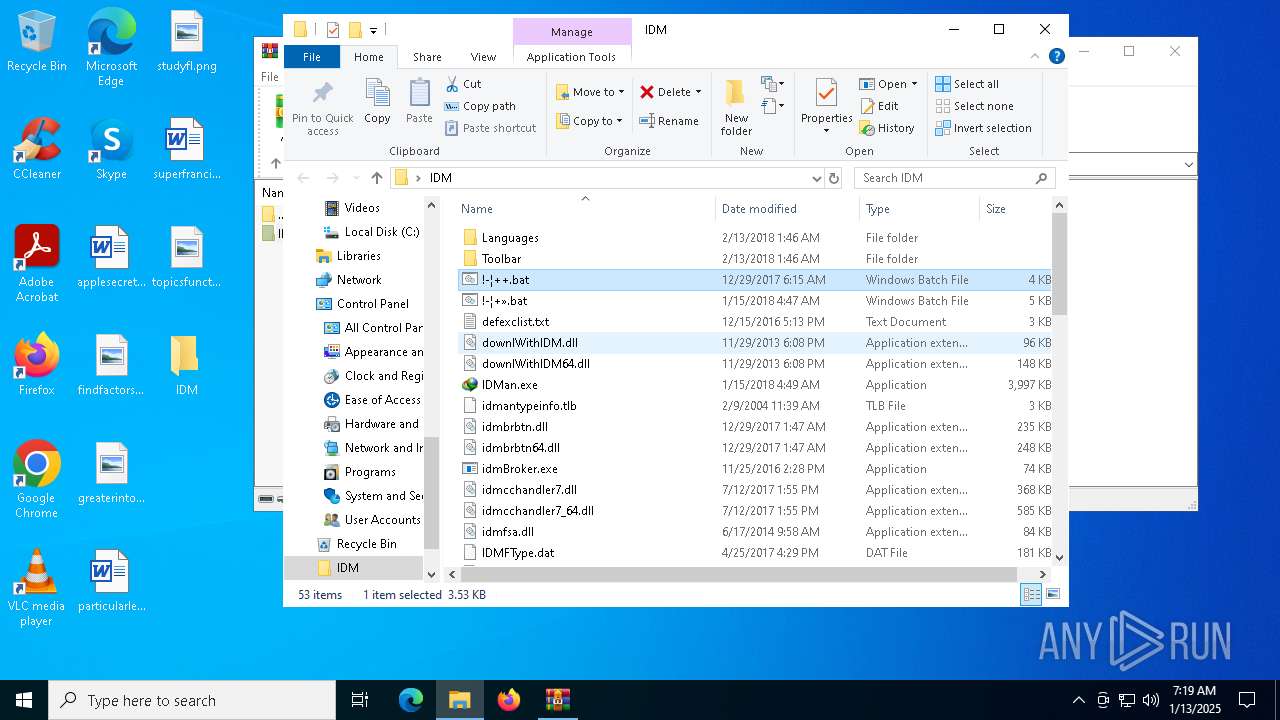
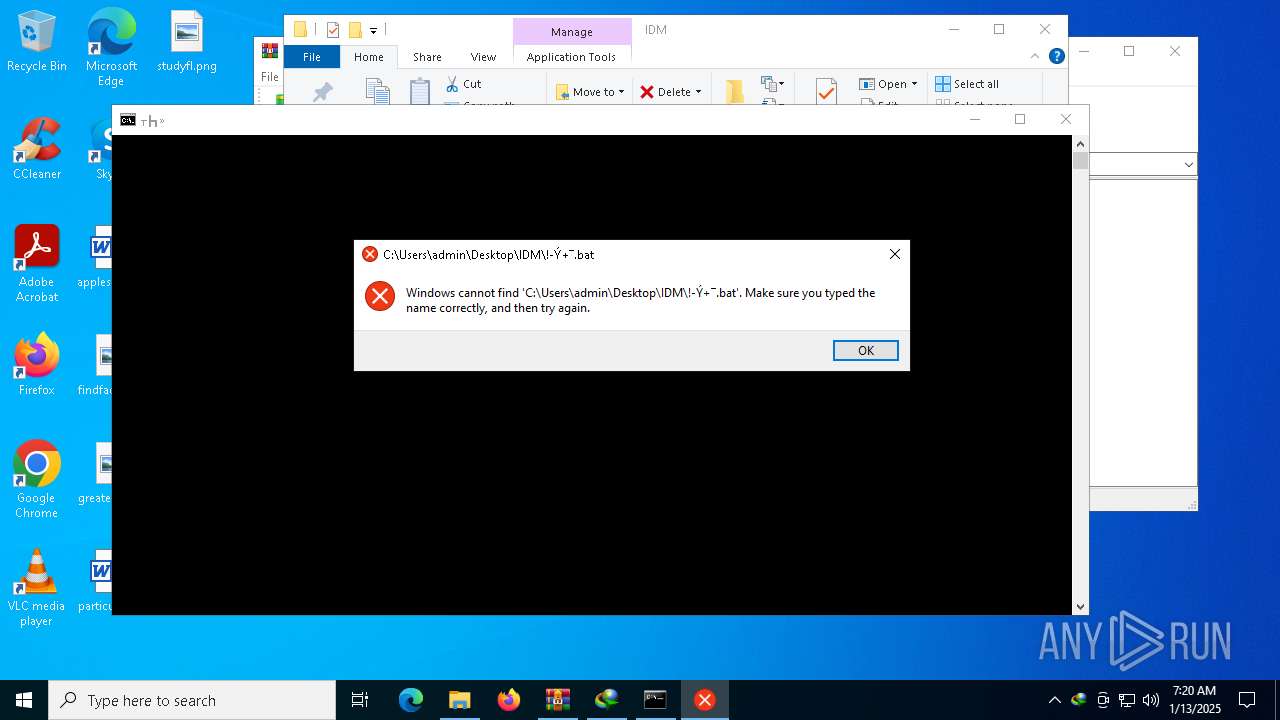
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\!-¦+».bat | text | |
MD5:3D9BC028823535B508EAA1C15625AAAC | SHA256:F274769E3C49438377EE7682D3763280235AAB95F1EB84A9282EB7E1D276CDCB | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\IDMNetMon64.dll | executable | |
MD5:859482B597E50C9EEA305B2E891EC584 | SHA256:97731564563C9AB42FD9AD719CA1E0212AC58739ACDAF31E08D4DDC5A1E6A206 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\IDMFType64.dll | executable | |
MD5:C976CEB4BE1DAF3A848C11A4ADF224BA | SHA256:0479DDA9F82192A7C8881413F8CA6A220E63A4811EFADC497DBEFC0F4C290441 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\IDMIECC64.dll | executable | |
MD5:9AF02944DA6A9C2C82790E4B21A7A470 | SHA256:76C325D67653628DF18A164F9A6A61A1CF991FADF6C29915B402BE139AEFEDED | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\IDMFType.dat | binary | |
MD5:EFFB169483778024B3686508B30ED1FF | SHA256:A21F4D385269A38E5E63F5245D00F6DE864D56392AB40F139DEC0FC9039A8F04 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\!-¦++.bat | text | |
MD5:587F6672E66A6F27B694E168B718CFE8 | SHA256:90D212BBE944A36B160E531BEEDCBDA0DDE07D1B8AB7637522982AE0664DFED7 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\IDMGrHlp.exe | executable | |
MD5:BD6237153F36471800402CBEEA9497B6 | SHA256:923C050E3BCD3B473A5644247D1E5EE970389FC3ADF53B2D73097F7D49D7C0E2 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\IDMIECC.dll | executable | |
MD5:2CC2D84CFD0694CA53FCFF43670F1EBA | SHA256:EA1140016EF88B4F331BFED1D6FDD0DDF1615F8314B814D2D2FA436E0B9F77CD | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\IEExt.htm | html | |
MD5:7EE0CC294B365F8FC4FAB2F06E01AC95 | SHA256:A17FE100C65749018CA05A1B2E600060D83B4490BDDFD3F61B5523C78B9483D7 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.9983\IDM\IDMGetAll.dll | executable | |
MD5:8C6AF35602856595601F3CFFC70317D8 | SHA256:5521835BE4383D57445C0B273057FA7747F3DF26D0C880E00108C32CF5B3CCCC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
77
DNS requests
69
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5400 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6860 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3888 | svchost.exe | GET | 206 | 2.22.242.90:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1736931801&P2=404&P3=2&P4=lHjOuekyoH%2bwZu%2f6wBamEuz0wI3eEufxxThdTQsdGOXkKzj9RLFVLriii0ZXx0vx5UOJS8llD6qWybZRbZHGiQ%3d%3d | unknown | — | — | whitelisted |
6860 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3888 | svchost.exe | HEAD | 200 | 2.22.242.90:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1736931801&P2=404&P3=2&P4=lHjOuekyoH%2bwZu%2f6wBamEuz0wI3eEufxxThdTQsdGOXkKzj9RLFVLriii0ZXx0vx5UOJS8llD6qWybZRbZHGiQ%3d%3d | unknown | — | — | whitelisted |
3888 | svchost.exe | GET | 206 | 2.22.242.90:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1736931801&P2=404&P3=2&P4=lHjOuekyoH%2bwZu%2f6wBamEuz0wI3eEufxxThdTQsdGOXkKzj9RLFVLriii0ZXx0vx5UOJS8llD6qWybZRbZHGiQ%3d%3d | unknown | — | — | whitelisted |
3888 | svchost.exe | GET | 206 | 2.22.242.90:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1736931801&P2=404&P3=2&P4=lHjOuekyoH%2bwZu%2f6wBamEuz0wI3eEufxxThdTQsdGOXkKzj9RLFVLriii0ZXx0vx5UOJS8llD6qWybZRbZHGiQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3040 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |