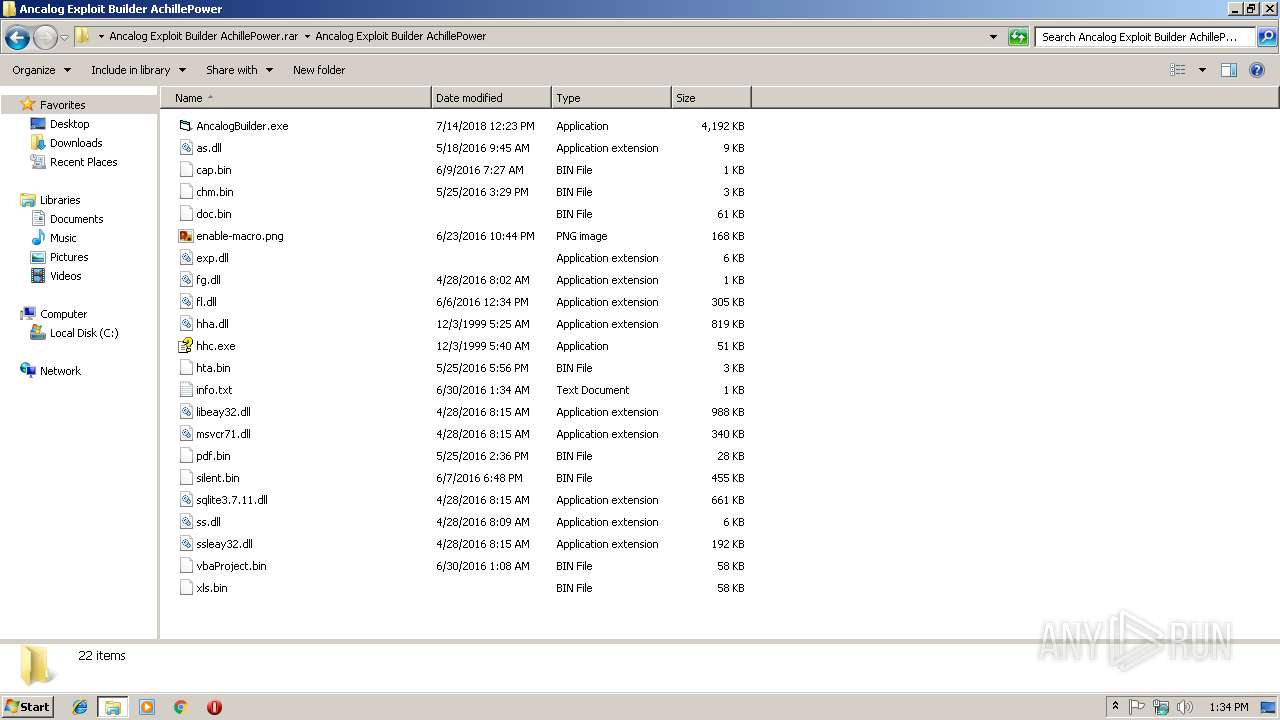
| File name: | Desktop.rar |
| Full analysis: | https://app.any.run/tasks/1be426c6-33ba-4ad4-9ce0-b7410e99e5c9 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2019, 13:33:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | ED56EF81342380D616ADDBD11DEF972F |
| SHA1: | BC85D7CC8C81BDCA9674022C35FEFC5810BF7B3E |
| SHA256: | 102C6409B237288006F63F5EB2FD1B9FE785D219419FB231162DDDD9FC66D165 |
| SSDEEP: | 98304:boAMMZBE7gOIWSq0P7RhWt/c/1lLMDgORgPmwqVZ8iRH9y12hb1OT:0k3jOIWSqoits3MUE6hdil9j1+ |
MALICIOUS
Application was dropped or rewritten from another process
- AncalogBuilder.exe (PID: 2640)
- AncalogBuilder.exe (PID: 3912)
- AncalogBuilder.exe (PID: 2628)
- svchost.exe (PID: 2392)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 968)
- AncalogBuilder.exe (PID: 2628)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2700)
- WinRAR.exe (PID: 2184)
- AncalogBuilder.exe (PID: 2640)
Creates executable files which already exist in Windows
- AncalogBuilder.exe (PID: 2640)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
44
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 968 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
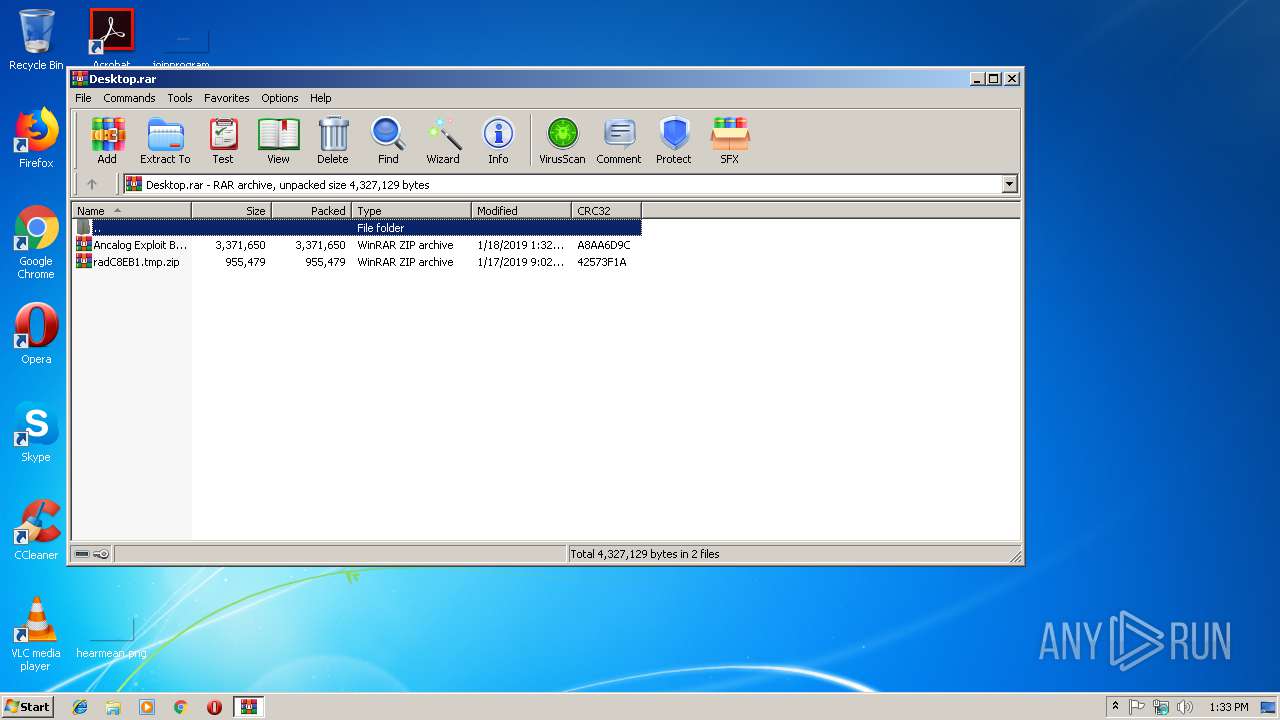
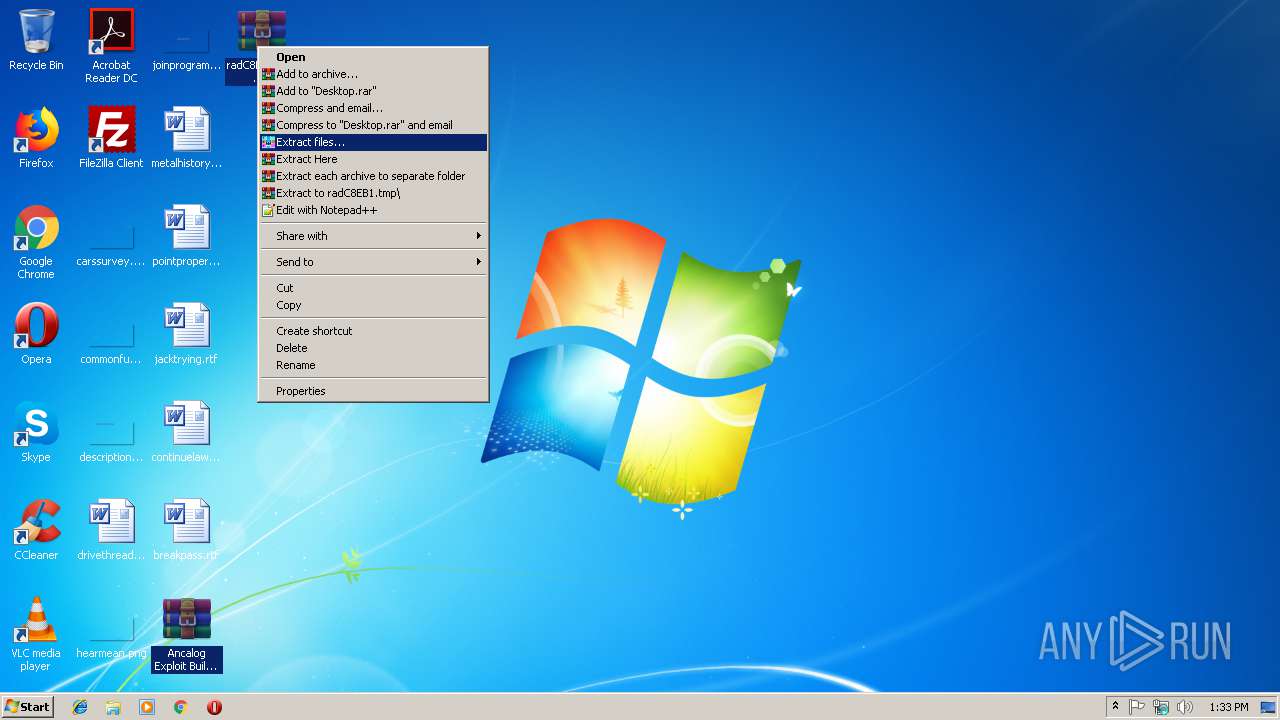
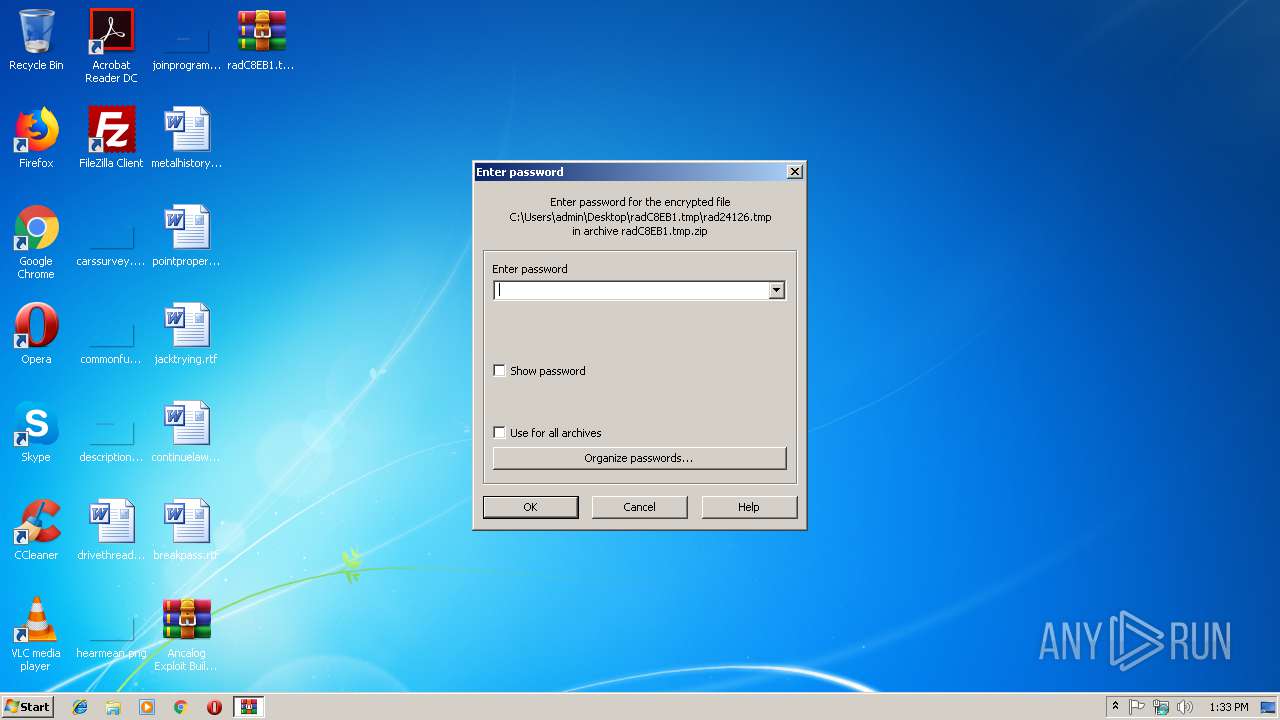
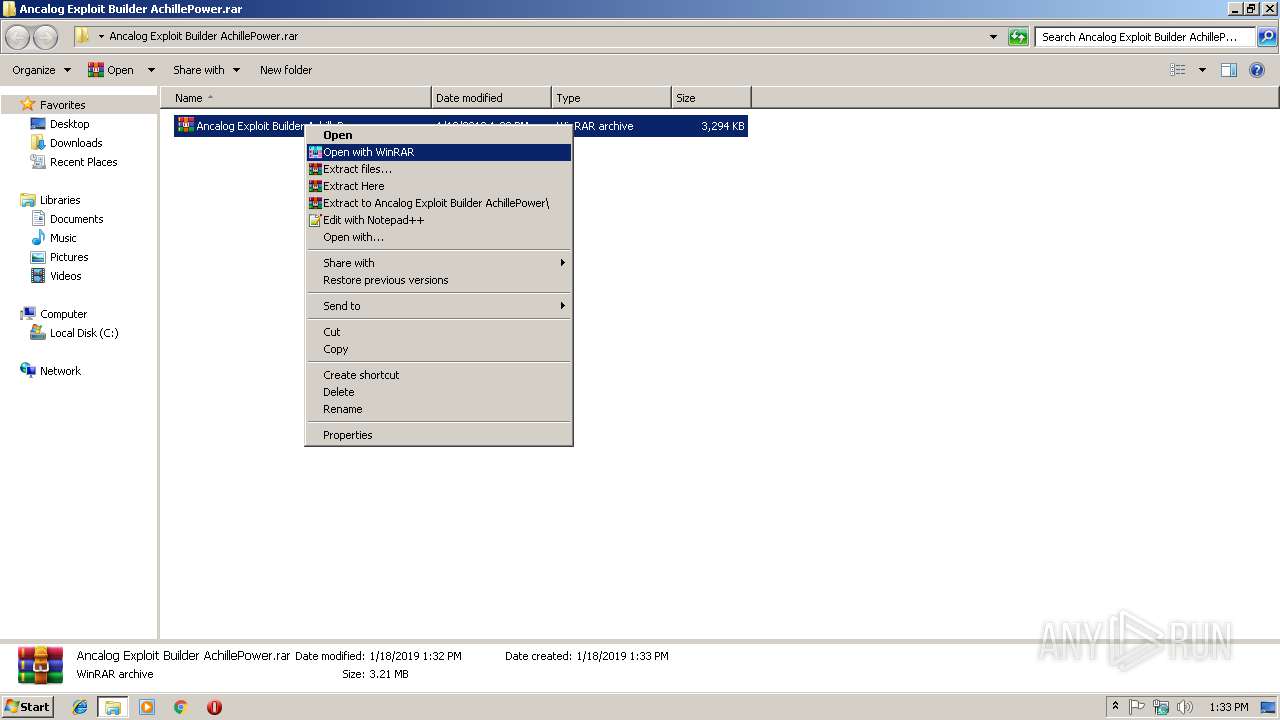
| 2184 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver "-an=C:\Users\admin\Desktop\radC8EB1.tmp.zip" -ad -- "C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2392 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" 0 | C:\Users\admin\AppData\Local\Temp\svchost.exe | — | AncalogBuilder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Phulli Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
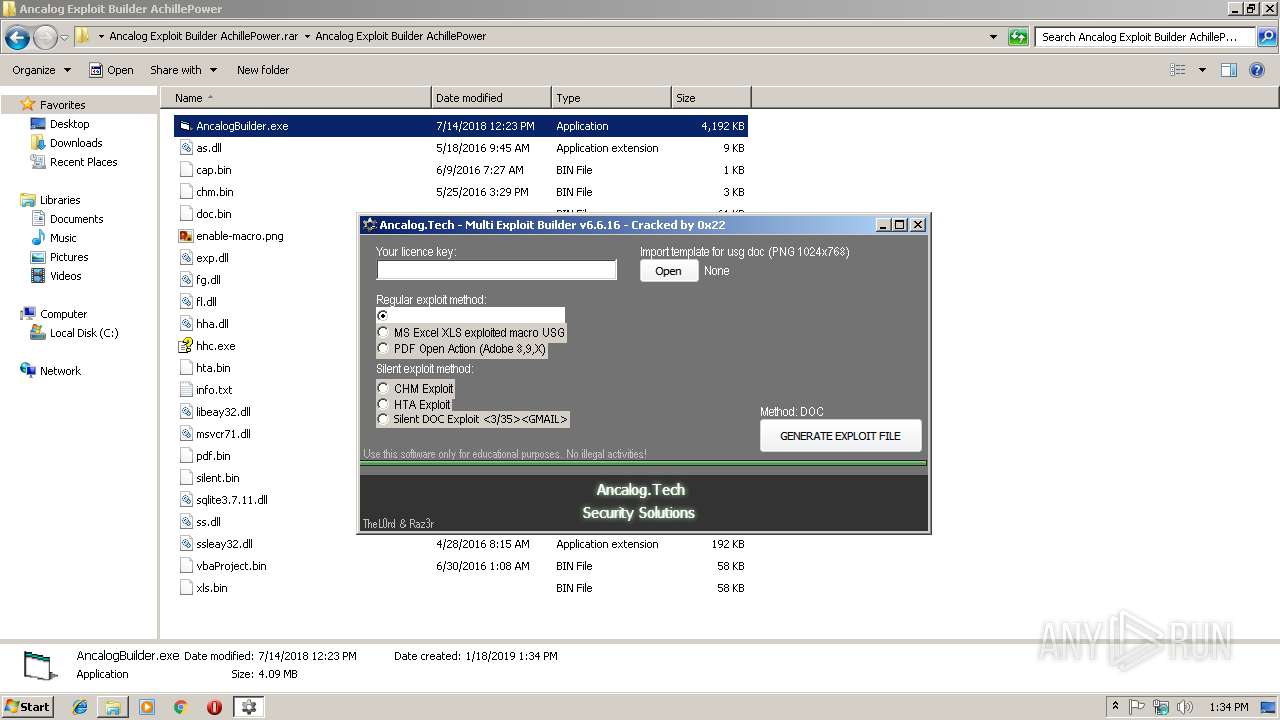
| 2628 | "C:\Users\admin\AppData\Local\Temp\AncalogBuilder.exe" 0 | C:\Users\admin\AppData\Local\Temp\AncalogBuilder.exe | AncalogBuilder.exe | ||||||||||||
User: admin Company: ancalog.tech Integrity Level: HIGH Description: Ancalog Multi Exploit Builder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
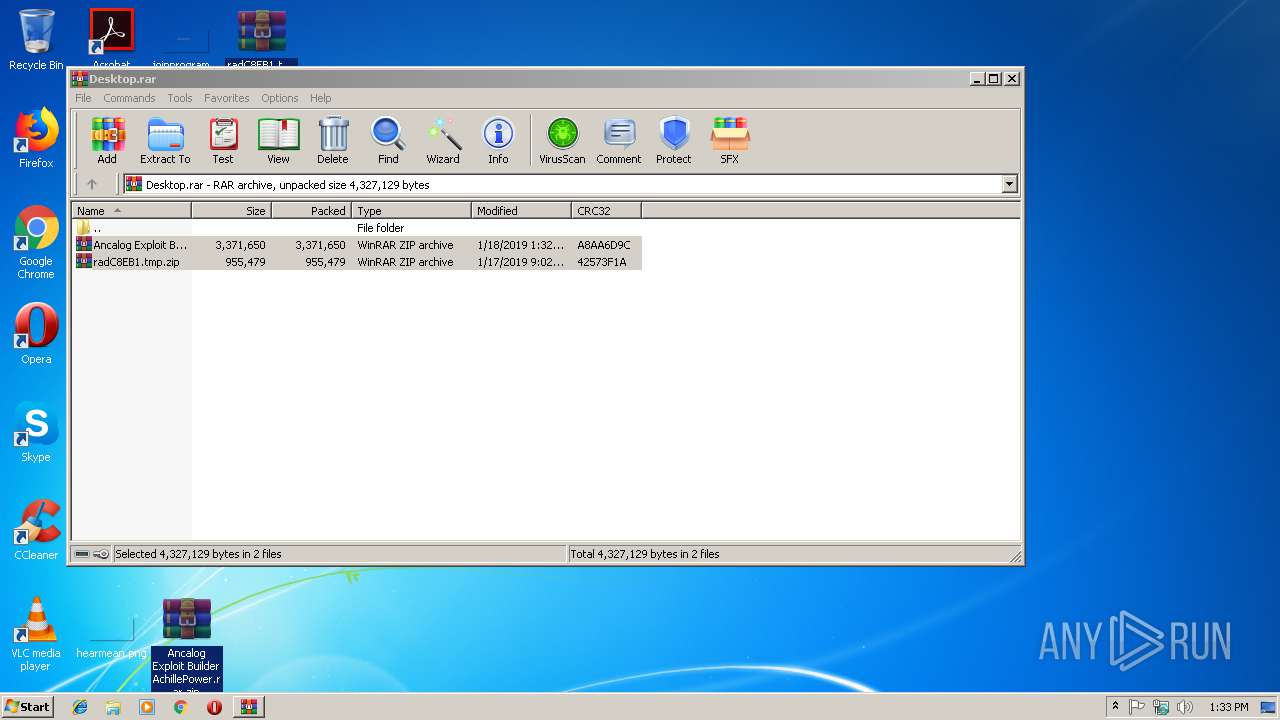
| 2640 | "C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower\AncalogBuilder.exe" | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower\AncalogBuilder.exe | explorer.exe | ||||||||||||
User: admin Company: BreakingSecurity.net Integrity Level: MEDIUM Exit code: 0 Version: 1.01.0001 Modules
| |||||||||||||||
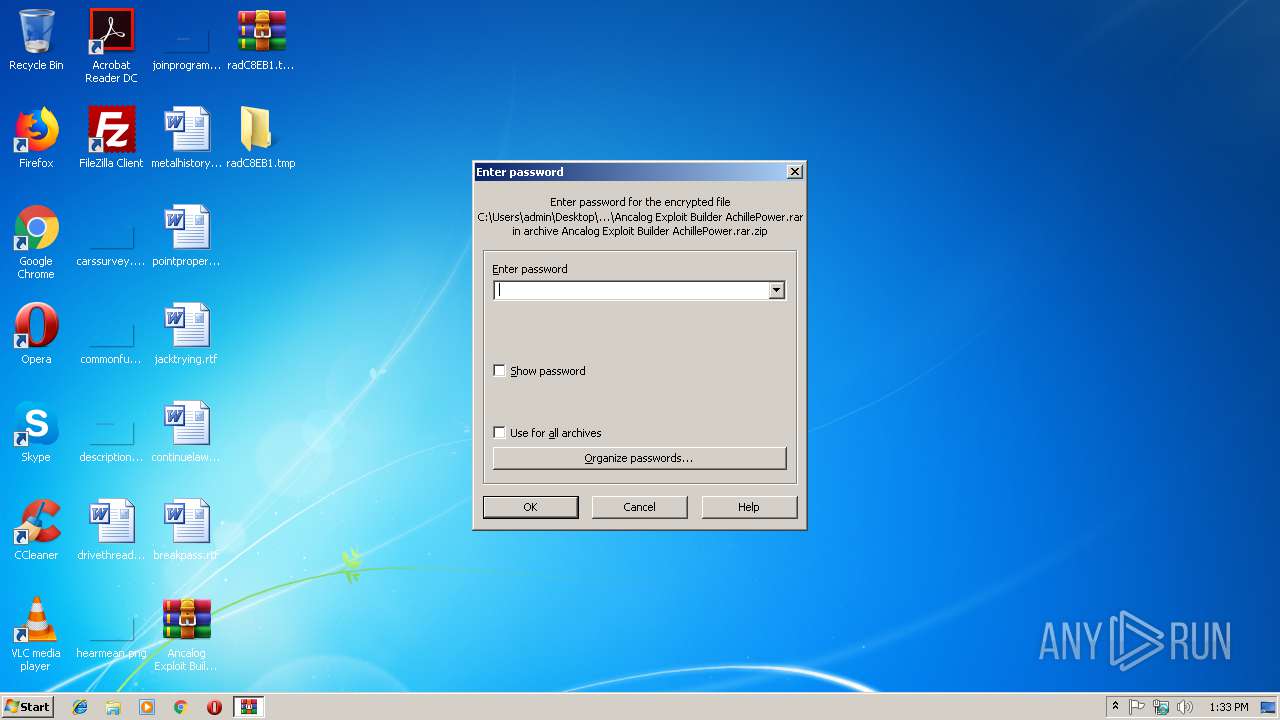
| 2700 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower.rar" "C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3096 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Desktop.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3912 | "C:\Users\admin\AppData\Local\Temp\AncalogBuilder.exe" 0 | C:\Users\admin\AppData\Local\Temp\AncalogBuilder.exe | — | AncalogBuilder.exe | |||||||||||
User: admin Company: ancalog.tech Integrity Level: MEDIUM Description: Ancalog Multi Exploit Builder Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 196
Read events
1 155
Write events
41
Delete events
0
Modification events
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Desktop.rar | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
10
Suspicious files
6
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3096.40598\radC8EB1.tmp.zip | — | |
MD5:— | SHA256:— | |||
| 3096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3096.40598\Ancalog Exploit Builder AchillePower.rar.zip | — | |
MD5:— | SHA256:— | |||
| 2184 | WinRAR.exe | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower.rar | compressed | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower\AncalogBuilder.exe | executable | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower\cap.bin | text | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower\doc.bin | binary | |
MD5:— | SHA256:— | |||
| 2184 | WinRAR.exe | C:\Users\admin\Desktop\radC8EB1.tmp\rad24126.tmp | executable | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower\enable-macro.png | image | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower\chm.bin | html | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower.rar\Ancalog Exploit Builder AchillePower\hta.bin | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report